
On Decomposing Formal Verification of CTL-based Properties on IaaS
Cloud Environment
Chams Eddine Choucha
1,3 a
, Mohamed Ramdani
1,3 b
, Mohamed Khalgui
1 c
and Laid Kahloul
2 d
1
National Institute of Applied Sciences and Technology, University of Carthage, Tunis, Tunisia
2
Computer Science Department, Biskra University, Biskra, Algeria
3
University of Tunis El Manar, Tunis, Tunisia
Keywords:
Discrete-event System, Reconfiguration, R-TNCES, Computation Tree Logic, CTL, Cloud Computing,
Formal Verification.
Abstract:
This paper deals with reconfigurable discrete event/control systems (RDECSs) that dynamically change their
structures due to external changes in environment or user requirements. RDECSs are complex and critical.
The verification of these systems continues to challenge experts in both academia and industry since the
generated state spaces are much bigger and the properties to be verified are more complex. Reconfigurable
Timed Net Condition/Event Systems (R-TNCESs) are proposed as an extension of the Petri nets formalism for
the optimal functional and temporal specification of RDECSs. Real systems model can encompass millions of
transitions which, implies huge state spaces and complex properties to be verified. To control the complexity
and to reduce the verification time, a new method of CTL properties verification in a cloud-based architecture
is proposed. The novelty consists in a new method for state space generation and the decomposition of the
complex properties for running an efficient verification. An algorithm is proposed for the incremental state
space generation. A case study is exploited to illustrate the impact of using this technique. The current results
show the benefits of the paper’s contribution.
1 INTRODUCTION
Nowadays, Reconfigurable discrete event control sys-
tems are invading international markets in several
domains (e.g., medical, aerospace or smart grids)
(Hafidi et al., 2019) (Naidji et al., 2019). Any
failure of such systems will cause disastrous conse-
quences. Formal verification is, therefore, impera-
tive. RDECSs have flexible configurations that al-
low them to switch from a configuration to another
due to user requirements or to prevent system mal-
functions (Hafidi et al., 2018). This verification con-
sists of two major steps: state-space generation and
state-space analysis. Mentioned steps applications are
usually expensive in terms of computation time and
memory occupation (i.e., huge accessibility graph to
be generated and complex properties to be verified)
(Zhang et al., 2015). The authors in (Ramdani et al.,
a
https://orcid.org/0000-0003-0194-4890
b
https://orcid.org/0000-0002-8723-5827
c
https://orcid.org/0000-0001-6311-3588
d
https://orcid.org/0000-0002-9739-7715
2018) proposed to classify properties automatically
and to introduce a priority order during RDECSs ver-
ification to control the high number of properties to
be verified. The mentioned method improves veri-
fication by reducing the number of properties to be
verified by exploiting relationships among properties
(equivalence, composition and dominance). How-
ever, when the property relationship rate is low which
is frequent while verifying complex RDECSs, the said
method is equivalent to the classic ones. The authors
in (Hafidi et al., 2018) proposed a method for accessi-
bility graph generation with less computing time and
less required memory, while preserving the graph se-
mantics. They start by computing the initial TNCES
accessibility graph classically, then making updates
on it to compute the remaining TNCESs accessibility
graphs, while considering similarities between them.
Previous methods improve classical ones. However,
with large scale systems, their application using a
unique machine (i.e., a centralized system) may be
expensive in terms of time and calculation (Koub
ˆ
aa
et al., 2017). Authors in (Camilli et al., 2014) initiate
the cloud-based solution for formal method problems.
544
Choucha, C., Ramdani, M., Khalgui, M. and Kahloul, L.
On Decomposing Formal Verification of CTL-based Properties on IaaS Cloud Environment.
DOI: 10.5220/0009972605440551
In Proceedings of the 15th International Conference on Software Technologies (ICSOFT 2020), pages 544-551
ISBN: 978-989-758-443-5
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

Authors have proposed a distributed fixed-point algo-
rithm to check CTL properties with basic operators.
The said algorithm can analyze DECS efficiently.
However, RDECSs complexity forced us to move for-
ward with big data solutions for formal method prob-
lems. To cope with RDECSs, Petri nets has been ex-
tended and developed by several works (Padberg and
Kahloul, 2018). Reconfigurable Timed Net Condi-
tion/Event System (R-TNCES) is a novel formalism
proposed in (Zhang et al., 2013a), where reconfig-
uration and time properties with modular specifica-
tion are provided in the same formalism. This Pa-
per deals with RDECSs modeled by R-TNCES. In
our previous works, we propose a method for state
space generation which, considers similarities that an
R-TNCES can contain, thanks to an ontology-based
history. Also, we proposed in (Choucha et al., 2019)
to perform CTL properties verification in a parallel
way on a cloud-based architecture while consider-
ing relationships among properties. The said meth-
ods are efficient; However, the first work is only fo-
cused on state space generation, and the second one
presents limits when properties are complex and prop-
erties relationship rate is low. Therefore, we propose
in this paper a new work that comes to fill the lim-
its of precedent ones. Hence, we proposed a new
method that aims to improve R-TNCES formal ver-
ification. RDECSs formal verification may be expen-
sive in terms of computation power and memory oc-
cupation, therefore, we resort to a cloud-based so-
lution to increase computation power (resp. mem-
ory occupation) thank to the Infrastructure as a ser-
vice IaaS (reps. Simple Storage Service S3) proposed
by Amzon (Hayes, 2008). To control RDECSs for-
mal verification complexity we propose the following
contributions:
1. Incremental state space generation to facilitate the
access to different parts of the accessibility graph;
Certain properties do not require the entire explo-
ration of the accessibility graph in order to be vali-
dated or not, therefore, a partial exploration of the
accessibility graph is sufficient. Indeed, we in-
troduce the modularity concept to the state-space
generation step, which allows us to access dif-
ferent parts of the accessibility graph (modules).
This contribution allows us to proceed to a tar-
geted verification.
2. Decomposition of CTL properties to control com-
plexity during the state-space analysis. Due to the
RDECSs complexity, properties to be verified in
order to ensure the correctness of the system be-
havior are more complex. Thereby, increasing the
complexity of the analysis step. In order to fix the
mentioned issue, we check the possibility of de-
composition of the complex properties into sev-
eral simple or less complex properties that can be
verified in less computation time using fewer re-
sources.
3. Development of a distributed cloud-based archi-
tecture to perform parallel computations during
formal verification and to store large scale data.
The huge generated state spaces and the high
number of properties to be verified forced us to
opt for a big data solution to control the complex-
ity of RDECSs formal verification. Computation
tasks are ensured by the master and the workers
via virtual machines allocated thanks to the EC2
product proposed by amazon. Data storage is en-
sured by S3.
The main objective of this paper is to propose a new
formal verification method that improves the classical
ones by controlling complexity. As a running exam-
ple, a formal case study is provided to demonstrate
the relevance of our contributions. The obtained re-
sults are compared with different works. The compar-
ison shows that the verification is improved in terms
of execution time (i.e., less complexity to perform
RDECSs formal verification).
The remainder of the paper is organized as fol-
lows. Section 2 presents some required concepts. The
distributed formal verification is presented in Section
3. Section 4 presents the evaluation of the proposed
method. Finally, Section 5 concludes this paper and
gives an overview about our future work.
2 BACKGROUND
In this section, we present basic concepts which are
required to follow the rest of the paper.
2.1 Reconfigurable Timed Net
Condition/Event System
R-TNCES is a modeling formalism used to specify
and verify reconfigurable discrete event control sys-
tems (RDECSs). R-TNCES is based on Petri nets
and control components CCs. A control component
(CC) is defined as a software unit. Control compo-
nents are applied as a formal model of the controller
of a physical process and are modeled by TNCES as
shown in Figure 1. Each CC resumes the physical
process in three actions: Activation, working and ter-
mination. An R-TNCES RT N is defined in (Zhang
et al., 2013b) as a couple RT N = (B, R), where R is
the control module and B is the behavior module. B
On Decomposing Formal Verification of CTL-based Properties on IaaS Cloud Environment
545
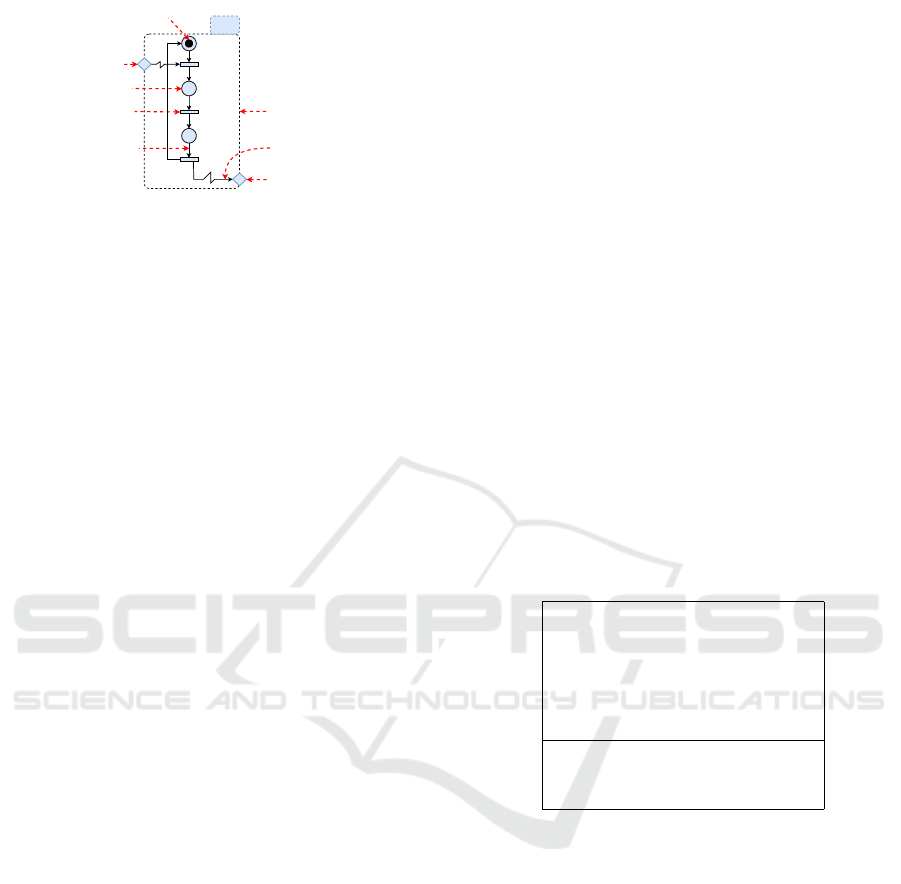
CC
i
P
1
P
2
P
3
t
1
t
2
t
3
Event output
Signal arc /
Event arc
Event input
Place
Transition
Flow arc
Module boundary
Token
Figure 1: Graphical model of a generic control component
modeled by TNCES.
is a union of multi TNCES-based CC modules, repre-
sented by
B = (P; T ; F;W ;CN; EN; DC;V ; Z
0
)
where,
a) P (resp, T ) is a superset of places (resp, transi-
tions),
b) F is a superset of flow arcs,
c) W : (P ×T )∪(T ×P) → {0, 1} maps a weight to a
flow arc, W (x, y) > 0 if (x, y) ∈ F, and W (x, y) = 0
otherwise, where x, y ∈ P ∪ T,
d) CN (resp, EN) is a superset of condition signals
(resp, event signals),
e) DC is a superset of time constraints on input arcs
of transitions,
f) V : T → ∧, ∨ maps an event-processing mode for
every transition;
g) Z
0
= (M
0
, D
0
), where M
0
is the initial marking,
and D
0
is the initial clock position.
R is a set of reconfiguration functions R = {r
1
, ..., r
n
}.
r is structured as follow: r = (Cond, s, x) such that:
1. Cond→ {true, false} is the pre-condition of r,
which means specific external instructions, gusty
component failures, or the arrival of certain states.
2. s : T N(
∗
r) → T N(r
∗
) such that TN(
∗
r)(resp.
T N(r
∗
)) be the original (resp. target) TNCES before
(resp. after) r application is the structure modification
instruction. 3. x : last
state
(T N(
∗
r))→ initial
state
(r
∗
) is
the state processing function, where last
state
(T N(
∗
r))
(resp. initial
state
(T N(r
∗
))) is the last (resp. the initial)
state of T N(
∗
r) (resp. T N(r
∗
)).
2.2 Computation Tree Logic CTL
Computational tree logic CTL is a temporal logic for
branching-time based on propositional logic used by
(Baier and Katoen, 2008) for model checking. CTL
can describe the context and branching of the sys-
tem state, it models system evaluation as a tree-like
structure where each state can evolve in several ways
(i.e., specify behavior systems from an assigned state
in which the formula is evaluated by taking paths).
CTL has a two-stage syntax where formulae in CTL
are classified into state and path formulae. The former
is formed according to the following grammar:
Φ ::= true|AP|Φ
1
∧ Φ
2
|Φ
1
∨ Φ
2
|¬Φ|Eϕ|Aϕ
While path formulae which express temporal proper-
ties of paths are formed according to the following
grammar:
ϕ ::= X Φ|FΦ|GΦ|Φ
1
UΦ
2
where Φ, Φ
1
and Φ
2
are state formulae. AP is the
set of atomic propositions. The CTL syntax include
several operators for describing temporal properties
of systems: A (for all paths), E (there is a path), X(at
the next state), F (in future), G (always) and U (until).
Definition 1. Equivalence of CTL Formulae: CTL
formulae σ
1
and σ
2
(over AP) are called equiva-
lent, denoted σ
1
≡ σ
2
whenever they are seman-
tically identical. Therefore, σ
1
≡ σ
2
ifSat(σ
1
) =
Sat(σ
2
) for all transition systems TS over AP such
that Sat(σ)={s ∈ S|s |= σ}. Table 1 presents an im-
portant set of equivalences rules (expansion and dis-
tributive laws).
Table 1: Some equivalence rules for CTL.
expansion laws:
EGφ ≡ φ ∧ EXEGφ
AFφ ≡ φ ∨ AXAFφ
EFφ ≡ φ ∨ EX EFφ
A[φUψ] ≡ ψ ∨ (φ ∧ AXA[φUψ])
E[φUψ] ≡ ψ ∨ (φ∧ EX E[φUψ])
distributive laws:
AG(σ
1
∧ σ
2
) ≡ AGσ
1
∧ AGσ
2
EF(σ
1
∨ σ
2
) ≡ EFσ
1
∨ EFσ
2
2.3 Infrastructure as a Service IaaS
Cloud computing is an increasingly popular paradigm
for ubiquitous, convenient, on-demand network ac-
cess to a shared pool of configurable computing
resources. In practice, cloud service providers tend
to offer services that can be grouped into three
categories as follows: (i) software as a service,
(ii) platform as a service, and (iii) infrastructure as
a service. IaaS is defined by (Hayes, 2008) as web
service that provides provision processing, storage,
networks, administrative services needed to store
applications and a platform for running applications.
It is designed to make web-scale cloud computing
easier for developers. Amazon Web Services Elastic
Compute Cloud (EC2) and Secure Storage Service
(S3) are examples of IaaS offerings (Hayes, 2008).
ICSOFT 2020 - 15th International Conference on Software Technologies
546
3 DISTRIBUTED CLOUD BASED
FORMAL VERIFICATION
We present in this section the proposed distributed
cloud-based formal verification of R-TNCESs.
3.1 Motivation
R-TNCES is an expressive formalism, which allows
considering different aspects of RDECS (time, proba-
bility, reconfigurability and concurrency) (Housseyni
et al., 2017). The correctness of RDECSs modeled
by R-TNCES can be ensured by formal verification.
However, such a formalism makes the verification
process complex, due to the combinatorial growth of
the state space according to the model size, and due
to the high number and complexity of the properties
that the designer wants to verify. Thus, we aim to
make model checking more efficient by reducing the
time validation of properties to be verified. Therefore,
we propose a new method for R-TNCES verification,
which facilitates both generation and analysis of state
space. To ensure our objective, we implement differ-
ent tasks as follows: a) Incremental state space gen-
eration, which is to construct the state space by part,
b) the complex properties are decomposed to simple
or less complex ones, then c) if possible, we assign
a partial graph to the property to be verified. d) Fi-
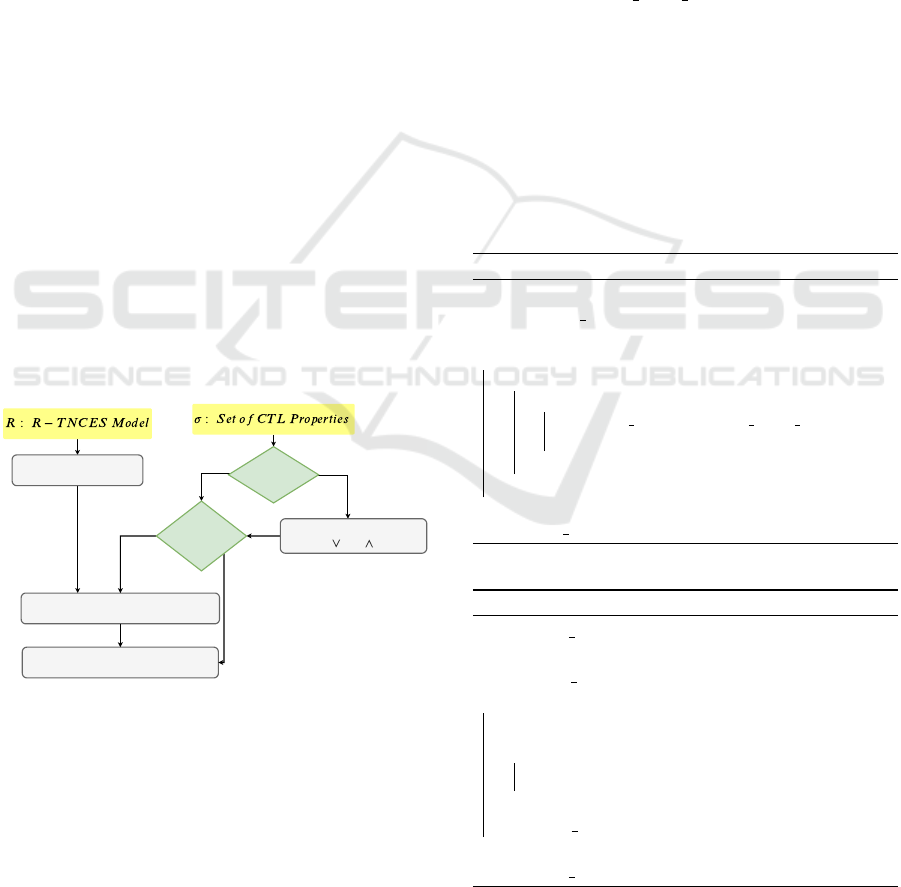
nally, we proceed to properties verification. Figure 2
presents scheduling of the presented tasks.
Incremental
State Space Generation
CTL property decomposition
( and )
Assignment PAG to Sub-property
Verification result
Complex
property?
No
YES
Possible
Assignment
YES
NO
Figure 2: Global idea for the formal verification according
to the distributed cloud based verification.
3.2 Formalization
In this section, we present formal verification steps
according to the distributed cloud-based formal
verification of R-TNCESs.
3.2.1 Incremental State Space Generation
Incremental state space generation consists of gener-
ating accessibility graphs by part, while preserving
models semantics. Let RT N(R, B) be an R-TNCES
model, this task consists in two steps:
(i) Basic accessibility graph genera-
tion BAG, which consists of generating ac-
cessibility graphs for each CC
i
∈ T NCES
j
where, i ∈ 0. . . NumberCC(T NCES
j
) and
j ∈ 0 . . . NumberT N(B). This step is implemented
in algorithm 1. It takes an R-TNCESs as input and
proceed to BAGs generation through several function
including Generate State Space(CC) which, take a
CC modeled by TNCES and return its accessibility
graph using SESA tool (Patil et al., 2012).
(ii) Partial accessibility graphs (PAGs) compo-
sition: This step is implemented in Algorithm 2.
It consists of composing pair of graphs computed
during the first step (BAGs) and throughout iterations
of the second step (PAGs), mainly by using the
function Compose(AG, AG) that takes two graphs and
composes them and returns a new composed graph.
Algorithm 1: Basic accessibility generation.
Input: RT N: R-TNCES; T N
0
: TNCES;
Output: S BAG: Set of elementary accessibility
graphs;
for int i = 0 to |
∑
T N | do
for each CC ∈ T N do
if ( !Tagged (CC)) then
Insert(S BAG, Generate State Space(CC));
tag(CC);
end
end
end
return S BAG
Algorithm 2: Accessibility graph construction.
Input: S BAG: Set of Elementary accessibility
graphs ;
∑
CChain: Set of Cchains;
Output: S AG: Set Accessibility graphs;
for int i = 0 to |
∑
CChain | do
AG ← BAG
CC
0
i
;
for int j = 0 to |
∑
CC
i
| do
AG ← Compose(AG,BAG
CC
j
i
);
end
Insert(S AG, AG)
end
return S AG
On Decomposing Formal Verification of CTL-based Properties on IaaS Cloud Environment
547
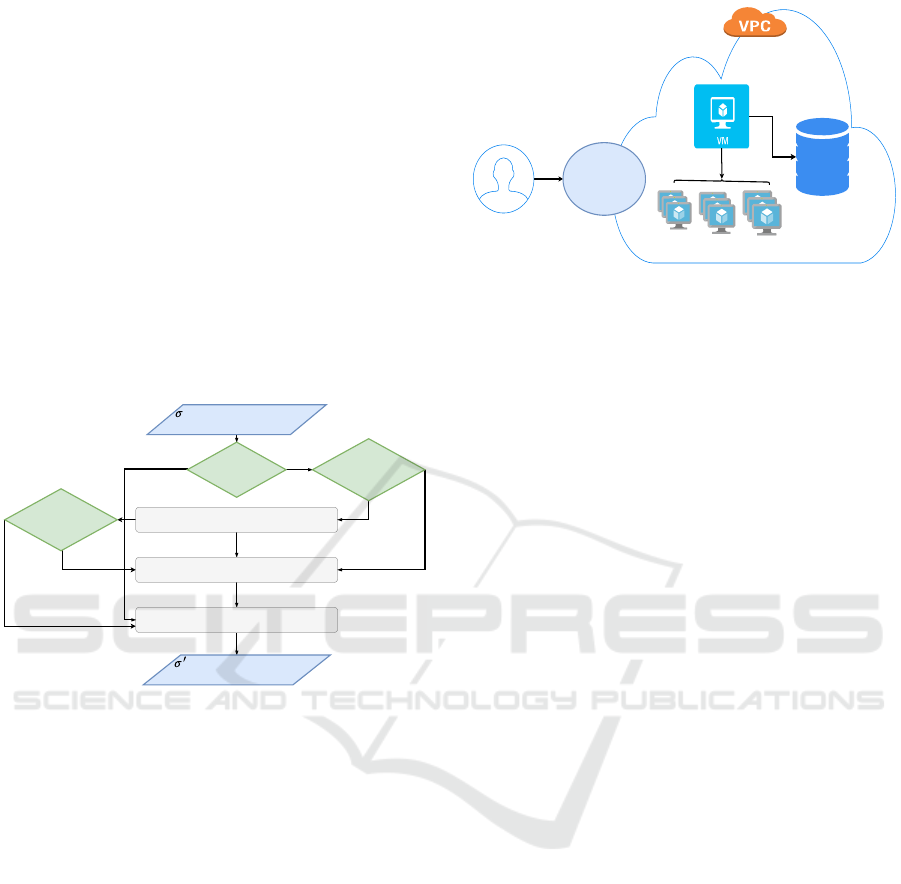
3.2.2 Complex CTL Properties Decomposition
We assume that properties that contain the operators
(∧) or (∨) are complex. Two kinds of complex prop-
erties are distinguished as follows:
• Decomposable: The operators (∧) or (∨) are not
linked to factors (State operators or path quanti-
fiers ). This kind of properties are directly splited
into a set of sub-properties (e.g., Φ = P
1
∧P
2
gives
σ
1
= P
1
and σ
2
= P
2
).
• Non-decomposable: The operators (∧) or (∨) are
linked to factors. For this kind of properties, we
firstly applied expansion or distribution laws and
then re-check if they are decomposable or not.
Figure 3 shows the majors steps of complex CTL
properties decomposition task.
: Set of CTL properties
to be verified
Appliedexpansion & distributive laws
Split property to atomic sub-properties
Update set of CTLproperties to be
verified
Atomic
Property ?
Decomposable ?
YES
: Updated Set of CTL
properties to be verified
NO
YES
NO
Decomposable ?
YES
NO
Figure 3: Complex CTL properties decomposition.
3.2.3 Properties Assignment to PAGs
We assign to each property one or several state spaces
computed during incremental state space generation.
The assignment is done based on two criteria: (i) Path
quantifier and state operators, and (ii) places con-
cerned by the property such that we assign the small-
est state space that contains the concerned places.
3.3 Distributed Architecture for Formal
Verification
In this subsection, we present the proposed distributed
cloud-based architectures shown in Figure 4. The idea
that motivates the development of this architecture is
to increase computation power and storage availabil-
ity. It is composed of computational and storage re-
sources. To develop the architecture shown in Figure
4, we use IaaS to allocate the following resources:
• Computation resources: which represent the mas-
ter that coordinates the executed tasks, and the
workers that execute the presented tasks above.
Internet
GATEWAY
Workers
Database
Master
User
Figure 4: Distributed cloud-based architecture.
• Storage resources: represents the allocated cloud
database that stores accessibility graphs computed
during verification.
4 EXPERIMENTATION
In this section, to validate and demonstrate the gain
of our proposed contributions, we use a formal case
study.
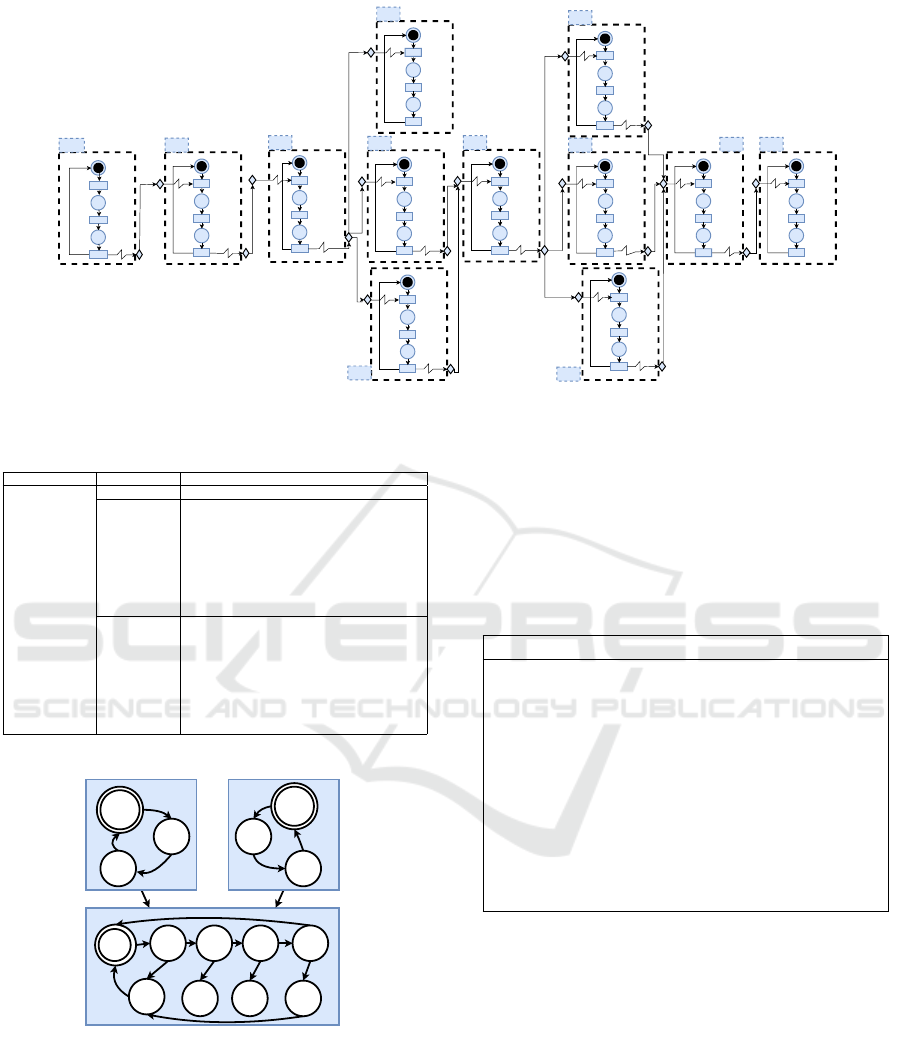
4.1 Case Study
To demonstrate the performance and the gain of
the proposed contribution, we use an R-TNCES to
model a sequential system S
01
, to be denoted by
RT N
S
01
(B
S
01
, R
S
01
). S
01
is composed of 11 physical
processes modeled by 11 CCs. The behavior module
of the system (B
S
01
) is modeled graphically as shown
in Figure 5. This model covers three configurations
(C
1
,C
2
,C
3
). It is assumed that every configuration has
one control chain (C
Chain
i
) as follows.
• C
Chain
1
: CC
1
,CC
2
,CC
3
,CC
9
.
• C
Chain
2
: CC
1
,CC
2
,CC
3
,CC
4
,CC
5
,CC
11
,CC
7
,CC
8
.
• C
Chain
3
: CC
1
,CC
2
,CC
3
,CC
10
,CC
5
,CC
6
,CC
7
,CC
8
.
This behavior module can be reconfigured au-
tomatically and timely between the three con-
figurations (C
i
, i = 1, .., 3), according to the en-
vironment changes or to the user requirements.
RT N
S
01
can apply six different reconfigura-
tion scenarios according to the control module
R
S
01
, which are described as follows: R
S
01
=
(C
1
,C
2
);(C
1
,C
3
);(C
2
,C
1
);(C
2
,C
3
);(C
3
,C
1
);(C
3
,C
2
).
4.2 Application
In this section, we present the application of the for-
mal verification of RT N
S
01
according to the cloud-
based formal verification.
ICSOFT 2020 - 15th International Conference on Software Technologies
548
P7
P8
P9
CC3
t7
t8
t9
[2,4] [2,4]
[5,7]
p13
P14
CC5
[4,6]
P16
P17
CC6
[4,6]
P22
P23
[3,5]
P19
P20
CC8CC7
P15
P18
P24P21
t13
t14
t15
t16
t18
t17
t22
t23
t24
t19
t21
t20
[5,7]
P10
P11
CC4
P12
t10
t11
t12
[1,3]
P1
P2
P3
CC1
t1
t3
t2
[2,4]
P4
P5
P6
CC2
t4
t5
t6
[5,7]
P25
P26
CC9
P27
t25
t26
t27
[5,7]
P28
P29
CC10
P30
t28
t29
t30
[5,7]
P31
P32
C11
P33
t31
t32
t33
[4,6]
P34
P35
CC12
P36
t34
t35
t36
Figure 5: Behavior model with three configurations process.
Table 2: Incremental state space generation.
R-TNCES Model Control Chains PAGs
RT N
S
01
CChain
1
(CC
1
,CC
2
);(CC
1
,CC
2
,CC
3
);(CC
1
,CC
2
,CC
3
,CC
9
).
CChain
2
(CC
1
,CC
2
,CC
3
,CC
4
),
(CC
1
,CC
2
,CC
3
,CC
4
,CC
5
),
(CC
1
,CC
2
,CC
3
,CC
4
,CC
5
,CC
11
),
(CC
1
,CC
2
,CC
3
,CC
4
,CC
5
,CC
11
,CC
7
),
(CC
1
,CC
2
,CC
3
,CC
4
,CC
5
,CC
11
,CC
7
,CC
8
).
CChain
3
(CC
1
,CC
2
,CC
3
,CC
10
),
(CC
1
,CC
2
,CC
3
,CC
10
,CC
5
),
(CC
1
,CC
2
,CC
3
,CC
10
,CC
5
,CC
6
),
(CC
1
,CC
2
,CC
3
,CC
4
,CC
5
,CC
6
,CC
7
),
(CC
1
,CC
2
,CC
3
,CC
4
,CC
5
,CC
6
,CC
7
,CC
8
).
S'
0
S'
1
S'
2
S''
0
S''
1
S''
2
S
1
S
2
S3 S4
S5
S
7
S
8
S
6
S0
CC
1
CC
2
PAG(CC
1
,CC
2
)
Figure 6: Example of composition of two accessibility
graphs.
4.2.1 Incremental State Space Generation
In order to generates RT N
S
01
accessibility graph
AG
RT N
S
01
, we apply algorithms 1 and 2. First, we gen-
erates accessibility graphs for each physical process,
which are denoted by (BAG
i
, i =
1
, ..,
11
). Then, we
proceed to successive pair graphs compositions until
we constitute AG
RT N
S
01
. Table 2 shows PAGs com-
puted during the first step of the system verification.
note that each computed PAG is stored in the cloud
database. Moreover, Figure 6 shows an example of a
pair graphs composition.
Table 3: Set of CTL properties to be verified.
σ: Set of CTL Properties
P
1
: EF(p
3
), P
2
: AF(p
9
),
P
3
: AF(p
15
), P
4
: AF(p
21
),
P
5
: AF(p
24
), P
6
: AF(p
17
),
P
7
: AF(p
32
), P
8
: AF(p
35
).
P
9
: EF(p
12
∧ EG(p
24
)),
P
11
: EG(p
12
∧ EGp
35
)),
P
12
: EG(p
12
∧ EG(p
33
)),
P
13
: ¬EF(p
27
∧ EG(p
24
)),
P
14
: EF(p
12
) ∧ EF(p
18
),
P
15
: AF(p
12
) ∧ EG(p
33
) ∧ EG(p
21
) ∧ AF(p
24
),
P
16
: AF(p
12
) ∧ EG(p
33
) ∧ EG(p
21
) ∧ AF(p
24
).
4.2.2 Decomposition and CTL Properties
Assignment to PAGs
In order to validate the basic behavior of the system
and to guarantee that system model satisfies the good
requirements, we must ensure the CTL functional
properties. In particular, to ensure: a) The safety, the
system allows only one process to be executed at any
time, i.e., no activation of two CCs from two differ-
ent configurations at the same time, b) the liveness,
whenever any process wants to change the configura-
tion, it will eventually be allowed to do so, and c) the
non-blocking, any active CC is eventually ended.
Table 3 presents the above mentioned properties
On Decomposing Formal Verification of CTL-based Properties on IaaS Cloud Environment
549
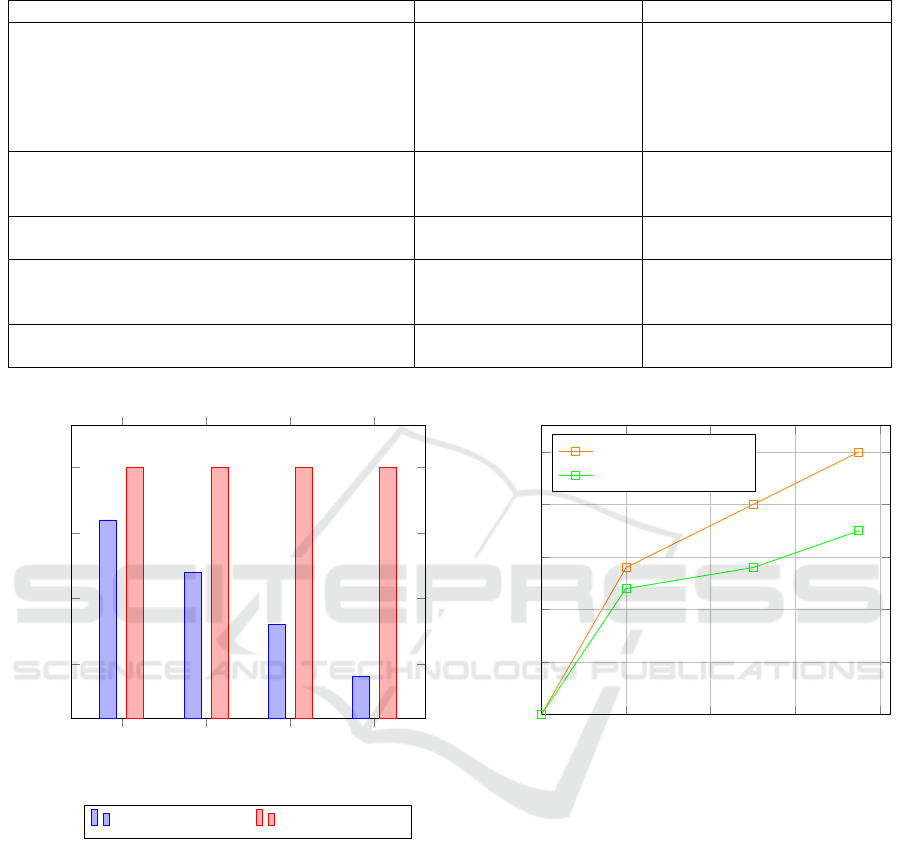
Table 4: CTL properties decomposition and assignment.
σ: Set of CTL Properties Decomposition Assignment
P
1
: EF(p
3
), P
2
: AF(p
9
), P
3
: AF(p
15
),
P
4
: AF(p
21
), P
5
: AF(p
24
), P
6
: AF(p
17
),
P
7
: AF(p
32
), P
8
: AF(p
35
).
Non-decomposable
P
1
: EAG
1
, P
2
: CC
1
,CC
2
,CC
3
,
P
3
: CC
1
, ..,CC
5
,
P
4
: CC
1
, ..,CC
7
,
P
5
: CC
1
, ..,CC
8
,
P
6
: CC
,
..,CC
6
,
P
7
: CC
,
..,CC
11
.
P
9
: EF(p
12
∧ EG(p
24
)),
P
12
: EG(p
12
∧ EG(p
33
)),
P
13
: ¬EF(p
27
∧ EG(p
24
)),
Non-decomposable
P
9
: CC
1
, ..,CC
8
,
P
12
: CC
1
, ..,CC
11
,
P
13
: CC
1
, ..,CC
8
.
P
14
: EF(p
12
) ∧ EF(p
18
).
P
0
14
: EF(p
12
).
P
00
14
: EF(p
18
).
P
0
14
: CC
1
, ..,CC
4
P
00
14
: CC
1
, ..,CC
6
.
P
15
: AF((p
12
) ∧ EG((p
33
)) ∧ EG(p
21
)) ∧ AF(p
24
).
P
0
15
: AF(p
12
).
P
00
15
: EG((p
33
) ∧ EG(p
21
)).
P
000
15
: AF(p
24
.
P
0
15
: CC
1
, ..,CC
4
,
P
00
15
: CC
1
, ..,CC
7
,
P
000
15
: CC
1
, ..,CC
8
.
P
16
: AF(p
12
) ∧ EG(p
33
) ∧ EG(p
21
) ∧ AF(p
24
).
P
0
16
: AF(P
12
).
P
00
16
: ¬AF(p
30
).
P
0
16
: CC
1
, ..,CC
4
,
P
00
16
: CC
1
, ..,CC
10
.
20% 40% 60% 80%
1.5
2
2.5
3
·10
4
Decomposable Properties rates(%)
Time Units
Proposed method Classic method
Figure 7: Classic method VS Proposed method.
specified by CTL. We apply the possible decomposi-
tion to the CTL properties in σ, then we assign each
property to be verified to the correspondent accessi-
bility graph (BAG or PAG). The results are shown in
Table 4.
4.3 Evaluation
Let assume we have to verify a system model with
2500 TNCESs. In order to ensure the well-behave
of the system we have to verify at least 4 proper-
ties for each TNCES. Thus, we need to verify 10000
CTL properties. We assume that the properties to
be verified are complex and the rate of decompos-
0 20 40
60
80
0
0.5
1
1.5
2
2.5
·10
4
Complex CTL properties rate(%)
Time Units
Sequential method
Parallel method
Figure 8: Improved performance of Parallel verification.
able one can be: (i) Low in 0, 20%, (ii) Medium in
20, 60%, or (iii) High when more than 60%. Figure
7 presents the result of properties verification using
the classic method presented in (Hafidi et al., 2018)
and the proposed method. The results show that the
gain increases proportionally to decomposable prop-
erties rate. Thus, the gain is clearly shown when
rate is High. Moreover, in Figure 8 we can observe
an important gain when performing parallel verifica-
tion thanks to the proposed architecture. The pro-
posed architecture allows us to reduce considerably
times execution by (i) Avoiding redundant calcula-
tion, (ii) Avoiding wait time execution, (iii) Perform-
ing several properties verification at the same time.
ICSOFT 2020 - 15th International Conference on Software Technologies
550

5 CONCLUSION
This work deals with the formal verification of
RDECSs modeled by R-TNCES using CTL specifi-
cations. In this paper, we present a big data solu-
tion for the formal verification problem. A distributed
cloud-based architecture is developed with two hier-
archical levels (Master and worker) where, data stor-
age is ensured by Amazon Simple Storage S3 (Murty,
2008)). It allows us to increase computational power,
data availability, and to perform parallel execution.
We introduce the modularity concept to the generated
state spaces which allow us to execute the generation
step in a parallel way via several workers (virtual ma-
chines). We detect the complex CTL properties and
decompose them into several simple or less complex
properties, then proceed to their verification via work-
ers using the SESA tool (Patil et al., 2012). Incremen-
tal state space generation and the decomposition of
CTL properties allow us to run a targeted verification,
which is less complex and more efficient in terms of
execution time. This work opens several perspectives;
first, we plan to apply our approach in verification of
real-case with a complex properties to check the func-
tional and the temporal specifications. Then, automa-
tize the detection of complex properties by using the
IA thanks to ontologies.
REFERENCES
Baier, C. and Katoen, J.-P. (2008). Principles of model
checking. MIT press.
Camilli, M., Bellettini, C., Capra, L., and Monga, M.
(2014). Ctl model checking in the cloud using mapre-
duce. In Symbolic and Numeric Algorithms for Sci-
entific Computing (SYNASC), 2014 16th International
Symposium on, pages 333–340. IEEE.
Choucha, C. E., Ougouti, N. S., Khalgui, M., and Kahloul.,
L. (2019). R-tnces verification: Distributed state space
analysis performed in a cloud-based architecture. In
Proceedings of the the 33rd Annual European Simu-
lation and Modelling Conference, pages 96–101. ETI,
EUROSIS.
Hafidi, Y., Kahloul, L., Khalgui, M., Li, Z., Alnowibet, K.,
and Qu, T. (2018). On methodology for the verifica-
tion of reconfigurable timed net condition/event sys-
tems. IEEE Transactions on Systems, Man, and Cy-
bernetics: Systems, (99):1–15.
Hafidi, Y., Kahloul, L., Khalgui, M., and Ramdani, M.
(2019). On improved verification of reconfigurable
real-time systems. In Proceedings of the 14th In-
ternational Conference on Evaluation of Novel Ap-
proaches to Software Engineering, pages 394–401.
SCITEPRESS-Science and Technology Publications,
Lda.
Hayes, B. (2008). Cloud computing. Communications of
the ACM, 51(7):9–11.
Housseyni, W., Mosbahi, O., Khalgui, M., Li, Z., Yin, L.,
and Chetto, M. (2017). Multiagent architecture for
distributed adaptive scheduling of reconfigurable real-
time tasks with energy harvesting constraints. IEEE
Access, 6:2068–2084.
Koub
ˆ
aa, A., Qureshi, B., Sriti, M.-F., Javed, Y., and To-
var, E. (2017). A service-oriented cloud-based man-
agement system for the internet-of-drones. In 2017
IEEE International Conference on Autonomous Robot
Systems and Competitions (ICARSC), pages 329–335.
IEEE.
Naidji, I., Ben Smida, M., Khalgui, M., Bachir, A., Li, Z.,
and Wu, N. (2019). Efficient allocation strategy of en-
ergy storage systems in power grids considering con-
tingencies. IEEE Access, 7:186378–186392.
Padberg, J. and Kahloul, L. (2018). Overview of reconfig-
urable petri nets. In Graph Transformation, Specifica-
tions, and Nets, pages 201–222. Springer.
Patil, S., Vyatkin, V., and Sorouri, M. (2012). Formal verifi-
cation of intelligent mechatronic systems with decen-
tralized control logic. In Proceedings of 2012 IEEE
17th International Conference on Emerging Technolo-
gies & Factory Automation (ETFA 2012), pages 1–7.
IEEE.
Ramdani, M., Kahloul, L., and Khalgui, M. (2018). Au-
tomatic properties classification approach for guiding
the verification of complex reconfigurable systems. In
ICSOFT, pages 625–632.
Zhang, Jiafen, and et al. (2013a). ”r-tnces: A novel for-
malism for reconfigurable discrete event control sys-
tems. Systems, Man, and Cybernetics: Systems, IEEE
Transactions on 43.4, pages 757–772.
Zhang, J., Khalgui, M., Boussahel, W. M., Frey, G., Hon,
C., Wu, N., and Li, Z. (2015). Modeling and veri-
fication of reconfigurable and energy-efficient manu-
facturing systems. Discrete Dynamics in Nature and
Society, 2015.
Zhang, J., Khalgui, M., Li, Z., Mosbahi, O., and Al-Ahmari,
A. M. (2013b). R-tnces: a novel formalism for recon-
figurable discrete event control systems. IEEE Trans-
actions on Systems, Man, and Cybernetics: Systems,
43(4):757–772.
On Decomposing Formal Verification of CTL-based Properties on IaaS Cloud Environment
551
