
Practical Predicate Encryption for Inner Product
Yi-Fan Tseng, Zi-Yuan Liu
∗
and Raylin Tso
Department of Computer Science, National Chengchi University, Taipei, Taiwan
Keywords:
Predicate Encryption, Inner Product Encryption, Constant-size Private Key, Efficient Decryption, Constant
Pairing Computations.
Abstract:
Inner product encryption is a powerful cryptographic primitive, where a private key and a ciphertext are both
associated with a predicate vector and an attribute vector, respectively. A successful decryption requires the
inner product of the predicate vector and the attribute vector to be zero. Most of the existing inner product
encryption schemes suffer either long private key or heavy decryption cost. In this manuscript, an efficient
inner product encryption is proposed. The length for a private key is only an element in G and an element in
Z
p
. Besides, only one pairing computation is needed for decryption. Moreover, both formal security proof and
implementation result are demonstrated in this manuscript. To the best of our knowledge, our scheme is the
most efficient one in terms of the private key length and the number of pairings computation for decryption.
1 INTRODUCTION
Traditional public key encryption provides only
coarse-grained access control. That is, given a cipher-
text encrypted under a public key, only the owner of
the corresponding private key can obtain the plaintext.
However, in many applications, such as distributed
file systems and cloud services, more complex ac-
cess policies may be necessary. Compared with tra-
ditional public key encryption, predicate encryption
Boneh and Waters (2007); Katz et al. (2008) can pro-
vide fine-grained access control over encrypted data.
Such encryption is suitable for various applications,
for instance, searching over encrypted data. In a pred-
icate encryption scheme, the ciphertext for message
M is associated with an attribute x, and the private
key is associated with a predicate f . A successful de-
cryption requires that f (x) = 1.
Katz et al. (2008) first considers the predicate for
the computation of inner product over Z
N
, where N
is a composite number. They also gave an instance
for inner product predicate, called inner product en-
cryption (IPE). In an IPE scheme, the ciphertext asso-
ciated with an attribute vector x can be decrypted by
the private key associated with a predicate vector y,
if and only if hx,yi = 0 (Here hx, yi denotes the stan-
dard inner product operation for vectors x, y). Due
to its flexibleness, lots of works on IPE scheme have
been proposed, such as pairing-based IPE schemes
∗
Corresponding author
Okamoto and Takashima (2009, 2015); Kurosawa and
Phong (2017); Chen et al. (2018); Zhang et al. (2019)
and lattice-based IPE schemes Agrawal et al. (2011);
K. Xagawa (2013); Li et al. (2017); Wang et al.
(2018).
Although many IPE schemes have been proposed,
these schemes suffer from either large private key
sizes or heavy computation costs, as described below:
• Pairing-based IPE schemes: existing pairing-
based IPE schemes are generally computationally
inefficient because of the large number of pair-
ings (linear to vector lengths) used during decryp-
tion. In addition, the private key length of most
schemes is also linear to vector lengths, so it is
not practical enough.
• Lattice-based IPE schemes: though lattice-based
IPE schemes are believed to be quantum-resistant,
nearly all of them suffer from either large key size,
or small message space.
All the problems mentioned above will make an IPE
scheme impractical and brings us to the following
open question:
Can we optimize the length of the private key and
reduce the cost of decryption, and further make them
constant in relation to vector lengths?
Tseng, Y., Liu, Z. and Tso, R.
Practical Predicate Encryption for Inner Product.
DOI: 10.5220/0009804605530558
In Proceedings of the 17th International Joint Conference on e-Business and Telecommunications (ICETE 2020) - SECRYPT, pages 553-558
ISBN: 978-989-758-446-6
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
553

1.1 Contributions
In this manuscript, we give a positive answer to the
above question by proposing an effective inner prod-
uct encryption scheme. More preciously, in the pro-
posed scheme, the length of a private key is only an
element in G and an element in Z
p
, i.e., independent
of the length of the predicate vector. Besides, the
decryption is efficient since only one pairing is nec-
essary (also independent of the length of the predi-
cate vector). We also provide rigours proof to show
that our proposed scheme is co-selective IND-CPA
secure under modified decisional Diffie-Hellman as-
sumption. Furthermore, Table 1 and Table 3 show the
comparison with other state-of-the-art schemes, illus-
trating that our proposed scheme is not only secure,
but also very practical.
2 PRELIMINARIES
2.1 Notations
Given a set S, “choose an element x randomly from
the set S” will be denoted as “x
$
←− S”. We use x ← A to
denote “x is the output of the algorithm A”. The bold
lowercase latter, e.g., s, is used to denote a vector. For
a vector s, s
i
denotes the i-th entry of vector s. Given
two vectors x,y, we denote the inner product of these
two vectors as hx, yi. The set of positive integer and
integer are represented by N and Z, respectively. For
a prime p, Z
p
denotes the set of integers module p.
2.2 Bilinear Maps
Let G be an additive cyclic group and G
T
be a mul-
tiplicative cyclic group, where the order of G and G
T
is a large prime p (i.e., |G| = |G
T
| = p). Besides,
let P be a generator of G. A bilinear map (pairing)
e : G ×G → G
T
is a mapping with the following prop-
erties.
• Bilinearity. For a,b ∈ Z
p
, e(aP, bP) = e(P, P)
ab
.
• Non-Degeneracy. ∃P ∈ G, such that e(P,P) 6=
1
G
T
.
• Computability. The mapping e is efficiently
computable.
2.3 Complexity Assumption
In this work, we take advantage of the generalized de-
cisional Diffie-Hellman exponent (GDDHE) problem
due to Boneh et al. (2005). The GDDHE problem
is a generic framework to create new complexity as-
sumptions. We first give an overview of the GDDHE
problem. Let
• p be a prime;
• s, n be two positive integers;
• P, Q ∈ F
p
[X
1
,. . ., X
n
]
s
be two s-tuple of n-variate
polynomials over F
p
;
• f be a n-variate polynomial in F
p
[X
1
,. . ., X
n
].
Note that Q, Q
T
are two ordered sets with multi-
variate polynomials, and thus we denote Q =
(q
1
,q
2
,. . ., q
s
) and R = (r
1
,r
2
,. . ., r
s
). As stated in
Boneh et al. (2005), we require p
1
= q
1
= 1 to be
two constant polynomials. Consider a bilinear map
e : G × G → G
T
with the generator P of G and g
T
=
e(P, P) ∈ G
T
. For a vector (x
1
,x
2
,. . ., x
n
) ∈ F
n
p
, we
define
Q(x
1
,x
2
,. . ., x
n
)P
= (q
1
(x
1
,x
2
,. . ., x
n
)P, . . ., q
s
(x
1
,x
2
,. . ., x
n
)P) ∈ G
s
,
and
g
R(x
1
,x
2
,...,x
n
)
T
= (g
r
1
(x
1
,x
2
,...,x
n
)
T
,. . ., g
r
s
(x
1
,x
2
,...,x
n
)
T
) ∈ G
s
T
.
By “ f depends on (Q, R)” we mean that there are s
2
+
s constants {a
i, j
}
s
i, j=1
and {b
k
}
s
k=1
such that
f =
s
∑
i, j=1
a
i, j
q
i
q
j
+
s
∑
k=1
b
k
r
k
.
We say that f is independent of (Q, R) if f is not de-
pend on (Q,R).
Definition 1 (The (Q, R, f )-GDDHE Problem).
Given (Q(x
1
,. . ., x
n
)P, g
R(x
1
,...,x
n
)
T
,Z) ∈ G
s
×G
s
T
×G
T
,
decide if Z
?
= g
f (x
1
,...,x
n
)
T
. For an algorithm A , the ad-
vantage of A in solving the (Q, R, f )-GDDHE prob-
lem is defined as
Adv
(Q,R, f )-GDDHE
(A)
=
A(Q(x
1
,. . ., x
n
)P, g
R(x
1
,...,x
n
)
T
,g
f (x
1
,...,x
n
)
T
)
− A(Q(x
1
,. . ., x
n
)P, g
R(x
1
,...,x
n
)
T
,Z
$
←− G
T
)
.
Definition 2 (The Decisional Diffie-Hellman Problem
over G
T
(DDH
G
T
problem)). Let g
T
= e(P, P) be a
generator of G
T
. Given (P,g
T
,A = g
a
T
,B = g
b
T
,C) ∈
G × G
4
T
, where a, b
$
←− Z
p
, decide whether C = g
ab
T
or
an random element from G
T
.
Definition 3 (The Modified Decisional Diffie-Hell-
man Problem over G
T
(M-DDH
G
T
problem)). Let
g
T
= e(P,P) be a generator of G
T
. Given (P,A
0
=
aP, g
T
,A = g
a
T
,B = g
b
T
,C) ∈ G
2
× G
4
T
, where a, b
$
←−
Z
p
, decide whether C = g
ab
T
or an random element
from G
T
.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
554

Theorem 1 (The Modified Decisional Diffie-Hellman
Assumption over G
T
(M-DDH
G
T
assumption)). We
say that the M-DDH
G
T
assumption holds if there is
no algorithm D solving the M-DDH
G
T
problem with
a non-negligible advantage.
Proof. Due to limited space, we give the proof in the
full version of this paper Tseng et al. (2020).
2.4 Definition of Inner Product
Encryption
An inner product encryption scheme consists of four
algorithms: Setup, KeyGen,Encrypt, and Decrypt.
The details of the algorithms are shown below.
Setup(1
λ
,1
`
). Given the security parameters (1
λ
,1
`
),
where λ, ` ∈ N, the algorithm outputs the system pa-
rameter params and the master secret key msk. Note
that the description of the attribute vector space A
and the predicate vector space P will be implicitly
included in params. Besides, we require that the in-
ner product operation over A and P should be well-
defined.
Encrypt(params,x, M). Given the system parameter
params, an attribute vector x ∈ A, and a message M,
the algorithm outputs a ciphertext C
x
for the attribute
vector x.
KeyGen(params,msk, y). Given the system parame-
ter params, a predicate vector y ∈ P, the algorithm
outputs the private key K
y
for the predicate vector y.
Decrypt(params,C
x
,K
y
). Given the system parame-
ter params, a ciphertext C
x
, and the private key K
y
,
the algorithm output a message M or a error symbol
⊥.
The correctness is defined as follows. For all λ,` ∈
N, let C
x
← Encrypt(params, x ∈ A,M) and let K
y
←
KeyGen(params,msk, y ∈ P), we have
M ← Decrypt(params, C
x
,K
y
) if hx,yi = 0;
⊥ ← Decrypt(params,C
x
,K
y
) if hx,yi 6= 0,
where (params,msk) ← Setup(1
λ
,1
`
).
2.5 Security Model
Here, we first introduce the IND-CPA security for
inner product encryption. The IND-CPA game of an
inner product encryption for attribute vector space A
and predicate vector space P is defined as an interac-
tive game between a challenger C and an adversary A .
Setup. The challenger C runs Setup(1
λ
,1
`
) and
sends the system parameter params to the adversary
A.
Query Phase 1. The challenger answers polynomi-
ally many private key queries for y ∈ P for the adver-
sary A by returning K
y
← KeyGen(params,msk, y).
Challenge. The adversary A submits an attribute
vector x
∗
∈ A such that hx
∗
,yi 6= 0 for all y
which has been queried in Query Phase 1, and
two massages M
0
,M
1
with the same length to the
challenger C . Then C randomly chooses β ∈
{0,1} and returns a challenge ciphertext C
x
∗
←
Encrypt(params,x
∗
,M
β
).
Query Phase 2. This phase is the same as Query
Phase 1, except that the adversary is not allowed to
make a query with y ∈ P such that hx
∗
,yi 6= 0.
Guess. The adversary A outputs a bit β
0
and wins the
game if β
0
= β. The advantage of an adversary for
winning the IND-CPA game is defined as
Adv
IND-CPA
(A) =
Pr[β
0
= β] −
1
2
.
Definition 4 (IND-CPA Security for Inner Product
Encryption). We say that an inner product encryp-
tion is IND-CPA secure if there is no probabilis-
tic polynomial-time adversary A wins the IND-CPA
game with a non-negligible advantage.
We then present the co-selective security Attra-
padung and Libert (2010); Attrapadung (2014) for in-
ner product encryption. The co-selective IND-CPA
(csIND-CPA) game is defined as the same of the IND-
CPA game, except that the adversary A is forced to
commit ahead before Setup phase q predicate vectors
y
(1)
,. . ., y
(q)
for the private key queries, where q is a
polynomial in the security parameter λ, and A is re-
quired to invoke Challenge phase with an attribute
vector x
∗
∈ A where hx
∗
,y
( j)
i 6= 0 for j = 1, . .. , q.
Definition 5 (Co-Selective IND-CPA Security for In-
ner Product Encryption). An inner product encryption
scheme is said to be csIND-CPA secure if no prob-
abilistic polynomial-time adversary wins the csIND-
CPA game with non-negligible advantage.
3 THE PROPOSED INNER
PRODUCT ENCRYPTION
SCHEME
Our IPE scheme consists of four algorithms: Setup,
KeyGen, Encrypt, and Decrypt. The details of the
proposed scheme are demonstrated below.
Setup(1
λ
,1
`
). Given the security parameters (1
λ
,1
`
),
where λ,` ∈ N, the algorithm performs as follows.
1. Choose bilinear groups G, G
T
of prime order p >
2
λ
. Let P and g
T
= e(P, P) be the generator of G
and G
T
, respectively.
Practical Predicate Encryption for Inner Product
555

2. Set the predicate vector space and the attribute
vector space to Z
`
p
.
3. Choose s = (s
1
,s
2
,. . ., s
`
)
$
←− Z
`
p
.
4. Compute
b
h = (g
s
i
T
)
`
i=1
= (
b
h
1
,. . .,
b
h
`
).
5. Output the system parameter params = (P, g
T
,
b
h),
and the master secret key msk = s.
Encrypt(params,x, M). Given the system parameter
params, a vector x = (x
1
,x
2
,. . ., x
`
) ∈ Z
`
p
, and a mes-
sage M ∈ G
T
, the algorithm performs as follows.
1. Choose r,δ
$
←− Z
p
.
2. Compute C
0
= rP, and
b
C
0
= g
r
T
.
3. Compute C
i
=
b
h
r
i
· g
δx
i
T
· M for i = 1 to `.
4. Output the ciphertext C
x
= (C
0
,
b
C
0
,C
1
,C
2
,. . ., C
`
)
KeyGen(params,msk, y). Given the system param-
eter params, a master secret key msk, and a vector
y = (y
1
,y
2
,. . ., y
`
) ∈ Z
`
p
, where
∑
`
i=1
y
i
6= 0, the algo-
rithm performs as follows.
1. Choose k
$
←− Z
p
.
2. Compute K
0
= kP, and K
1
= hs,yi + k mod p.
3. Output the private key K
y
= (K
0
,K
1
).
Decrypt(params,C
x
,K
y
). Given the system parame-
ter params, a ciphertext C
x
, and the private key K
y
,
where y = (y
1
,y
2
,. . ., y
`
) the algorithm performs as
follows.
1. Compute D
0
= e(K
0
,C
0
).
2. Compute D
1
=
∏
`
i=1
C
y
i
i
.
3. Compute D =
D
0
· D
1
b
C
K
1
0
.
4. Compute d = (
∑
`
i=1
y
i
)
−1
mod p.
5. Compute M = D
d
.
3.1 Correctness
The correctness of the proposed scheme is shown as
follows.
• D
0
= e(K
0
,C
0
) = e(kP, rP) = g
kr
T
.
•
D
1
=
∏
`
i=1
C
y
i
i
=
∏
`
i=1
(
b
h
r
i
· g
δx
i
T
· M)
y
i
=
∏
`
i=1
(
b
h
r
i
)
y
i
· (g
δx
i
y
i
T
) · (M
y
i
)
=
∏
`
i=1
((g
r
T
)
s
i
)
y
i
∏
`
i=1
(g
δx
i
y
i
T
)
∏
`
i=1
(M
y
i
)
= g
rhs,yi
T
· g
δhx,yi
T
· M
∑
`
i=1
y
i
.
•
b
C
K
1
0
= g
rK
1
T
= g
rhs,yi+rk
T
•
D =
D
0
· D
1
b
C
K
1
0
=
g
rhs,yi
T
· g
δhx,yi
T
· M
∑
`
i=1
y
i
· g
kr
T
g
rhs,yi+rk
T
= g
δhx,yi
T
· M
∑
`
i=1
y
i
• We have that D = M
∑
`
i=1
y
i
iff hx,yi = 0.
• Thus D
d
= M
∑
`
i=1
y
i
·((
∑
`
i=1
y
i
)
−1
mod p)
= M.
3.2 Security Proof
Theorem 2. The proposed scheme is csIND-CPA se-
cure for q private key queries, where q is a polynomial
in the security parameter λ, under the M-DDH
G
T
as-
sumption.
Proof. Due to limited space, we give the proof in the
full version of this paper Tseng et al. (2020).
4 COMPARISON AND
IMPLEMENTATION
In this section, we compare the efficiency of the pro-
posed IPE scheme with the previous works, where the
result is shown in Table 1. The comparison focuses on
two parts, one is the private key length, and another
is the number of pairing operations in the decryption
algorithm. Since the efficiency of composite order bi-
linear groups is much lower than that of prime order
groups, the order types of bilinear groups used in each
scheme are also marked in the comparison table.
We also implement our scheme and the schemes
of Attrapadung and Libert (2012); Kim et al. (2016);
Ramanna (2016), in order to show the efficiency com-
parison. The environment of the implementation is
shown in Table 2 and the implementation result is
shown in Table 3. We note that due to limited space,
please refer to the full version Tseng et al. (2020) for
more comparison details and implementation details.
5 CONCLUSION
This paper propose a practical inner product encryp-
tion scheme with constant-size private keys and con-
stant pairing computations for decryption. More
concretely, the private key of the proposed scheme
has only an element in G and an element in Z
p
,
and decryption requires only one pairing calculation.
The security proof shows that our proposed scheme
SECRYPT 2020 - 17th International Conference on Security and Cryptography
556
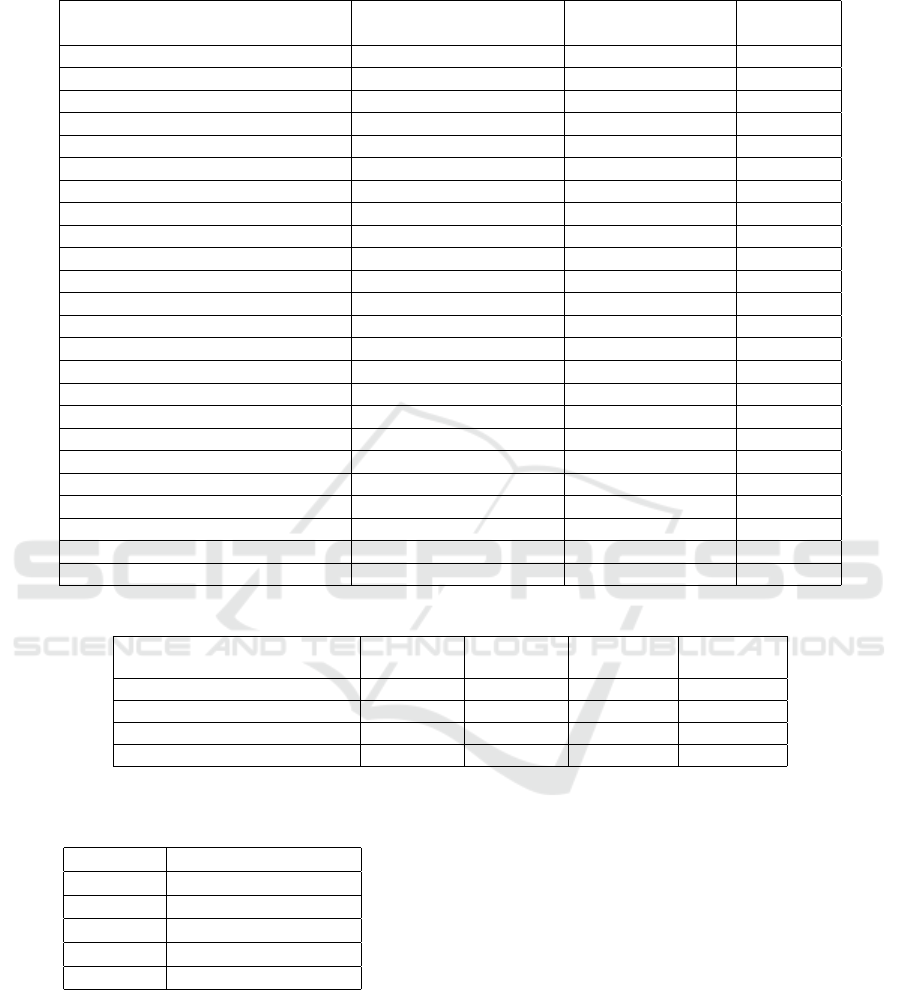
Table 1: Efficiency Comparison. Here, ` denotes the vector length for an IPE scheme; |Z
p
| and |G| denote the bit length of
the representations for an element in Z
p
and G, respectively; m denotes the leakage-resilience parameter.
Private Key Number of Pairings Group
Length for Decryption Order
Katz et al. (2008) (2` + 1)|G| 2` + 1 Composite
Okamoto and Takashima (2009) (` + 3)|G| ` + 3 Prime
Attrapadung and Libert (2010)-1 (` + 1)|G| 2 Prime
Attrapadung and Libert (2010)-2 (` + 6)|G| + (` − 1)|Z
p
| 9 Prime
Lewko et al. (2010) (2` + 3)|G| 2` + 3 Prime
Okamoto and Takashima (2011)-1 (4` + 1)|G| 9 Prime
Okamoto and Takashima (2011)-2 9|G| 9 Prime
Okamoto and Takashima (2011)-3 11|G| 11 Prime
Park (2011) (4` + 2)|G| 4` + 2 Prime
Okamoto and Takashima (2012a) (4` + 2)|G| 4` + 2 Prime
Okamoto and Takashima (2012b)-1 (15` + 5)|G| 15` + 5 Prime
Okamoto and Takashima (2012b)-2 (21` + 9)|G| 21` + 9 Prime
Kawai and Takashima (2014) 6`|G| 6` Prime
Zhenlin and Wei (2015) `|G| ` Composite
Kim et al. (2016) 3|G| 3 Prime
Huang et al. (2016) (4` + 2)|G| 4` + 4 Prime
Ramanna (2016)-1 (2` + 1)|G| + (` − 1)|Z
p
| 3 Prime
Ramanna (2016)-2 5|G| 3 Prime
Kurosawa and Phong (2017) 2m|G| 2m Prime
Xiao et al. (2017) (4` + 5)|G| 4` + 5 Prime
Chen et al. (2018)-1 5|G| 5 Prime
Chen et al. (2018)-2 7|G| 7 Prime
Zhang et al. (2019) (` + 1)|G| ` + 1 Composite
Ours 1|G| + 1|Z
p
| 1 Prime
Table 3: The Implementation Result.
Encryption Decryption Private Key Ciphertext
Time (ms) Time (ms) Length (kb) Length (kb)
Attrapadung and Libert (2010) 100 100 31.7 0.937
Kim et al. (2016) 170 140 0.955 17.5
Ramanna (2016) 260 140 1.59 25.9
Ours 20 10 0.37 31.3
Table 2: The Environment of the Implementation.
Specification
OS Ubuntu 18.04 LTS
CPU Intel i7-4790 3.6GHz
RAM 8 gb
Language Python 3.6
Library Charm-Crypto v0.50
is co-selective IND-CPA secure under modified de-
cisonal Diffie-Hellman assumption. Experimental re-
sults show that comparing with other schemes, our
proposed scheme can effectively reduce the encryp-
tion and decryption time and private key length.
ACKNOWLEDGMENT
This research was supported by the Ministry of Sci-
ence and Technology, Taiwan (ROC), under Project
Numbers MOST 108-2218-E-004-001-, MOST 108-
2218-E-004-002-MY2, and by Taiwan Information
Security Center at National Sun Yat-sen University
(TWISC@NSYSU).
REFERENCES
Agrawal, S., Freeman, D. M., and Vaikuntanathan, V.
(2011). Functional Encryption for Inner Product Pred-
icates from Learning with Errors. In Lee, D. H. and
Wang, X., editors, Advances in Cryptology – ASI-
Practical Predicate Encryption for Inner Product
557

ACRYPT 2011, pages 21–40. Springer, Berlin, Hei-
delberg.
Attrapadung, N. (2014). Dual System Encryption via
Doubly Selective Security: Framework, Fully Secure
Functional Encryption for Regular Languages, and
More. In Nguyen, P. Q. and Oswald, E., editors,
Advances in Cryptology – EUROCRYPT 2014, pages
557–577. Springer, Berlin, Heidelberg.
Attrapadung, N. and Libert, B. (2010). Functional Encryp-
tion for Inner Product: Achieving Constant-Size Ci-
phertexts with Adaptive Security or Support for Nega-
tion. In Nguyen, P. Q. and Pointcheval, D., editors,
Public Key Cryptography – PKC 2010, pages 384–
402. Springer, Berlin, Heidelberg.
Attrapadung, N. and Libert, B. (2012). Functional Encryp-
tion for Public-attribute Inner Products: Achieving
Constant-size Ciphertexts with Adaptive Security or
Support for Negation. J. Mathematical Cryptology,
5(2):115–158.
Boneh, D., Boyen, X., and Goh, E.-J. (2005). Hierarchical
Identity Based Encryption with Constant Size Cipher-
text. In Cramer, R., editor, Advances in Cryptology –
EUROCRYPT 2005, pages 440–456. Springer, Berlin,
Heidelberg.
Boneh, D. and Waters, B. (2007). Conjunctive, Subset,
and Range Queries on Encrypted Data. In Vadhan,
S. P., editor, Theory of Cryptography, pages 535–554.
Springer, Berlin, Heidelberg.
Chen, J., Gong, J., and Wee, H. (2018). Improved Inner-
Product Encryption with Adaptive Security and Full
Attribute-Hiding. In Peyrin, T. and Galbraith, S., ed-
itors, Advances in Cryptology - ASIACRYPT 2018,
pages 673–702, Springer, Cham.
Huang, S.-Y., Fan, C.-I., and Tseng, Y.-F. (2016). En-
abled/Disabled Predicate Encryption in Clouds. Fu-
ture Generation Computer Systems, 62:148 – 160.
K. Xagawa, K. (2013). Improved (Hierarchical) Inner-
Product Encryption from Lattices. In Kurosawa, K.
and Hanaoka, G., editors, Public-Key Cryptography –
PKC 2013, pages 235–252. Springer, Berlin, Heidel-
berg.
Katz, J., Sahai, A., and Waters, B. (2008). Predicate En-
cryption Supporting Disjunctions, Polynomial Equa-
tions, and Inner Products. In Smart, N., editor, Ad-
vances in Cryptology – EUROCRYPT 2008, pages
146–162. Springer, Berlin, Heidelberg.
Kawai, Y. and Takashima, K. (2014). Predicate- and
Attribute-Hiding Inner Product Encryption in a Pub-
lic Key Setting. In Cao, Z. and Zhang, F., editors,
Pairing-Based Cryptography – Pairing 2013, pages
113–130, Cham. Springer International Publishing.
Kim, I., Hwang, S. O., Park, J. H., and Park, C. (2016). An
Efficient Predicate Encryption with Constant Pairing
Computations and Minimum Costs. IEEE Transac-
tions on Computers, 65(10):2947–2958.
Kurosawa, K. and Phong, L. T. (2017). Anonymous and
Leakage Resilient IBE and IPE. Designs, Codes and
Cryptography, 85(2):273–298.
Lewko, A., Okamoto, T., Sahai, A., Takashima, K., and
Waters, B. (2010). Fully Secure Functional Encryp-
tion: Attribute-Based Encryption and (Hierarchical)
Inner Product Encryption. In Gilbert, H., editor, Ad-
vances in Cryptology – EUROCRYPT 2010, pages 62–
91. Springer, Berlin, Heidelberg.
Li, J., Zhang, D., Lu, X., and Wang, K. (2017). Com-
pact (Targeted Homomorphic) Inner Product Encryp-
tion from LWE. In Qing, S., Mitchell, C., Chen, L.,
and Liu, D., editors, International Conference on In-
formation and Communications Security, pages 132–
140. Springer.
Okamoto, T. and Takashima, K. (2009). Hierarchical Pred-
icate Encryption for Inner-Products. In Matsui, M.,
editor, Advances in Cryptology – ASIACRYPT 2009,
pages 214–231. Springer, Berlin, Heidelberg.
Okamoto, T. and Takashima, K. (2011). Achieving Short
Ciphertexts or Short Secret-Keys for Adaptively Se-
cure General Inner-Product Encryption. In Lin, D.,
Tsudik, G., and Wang, X., editors, Cryptology and
Network Security, pages 138–159. Springer, Berlin,
Heidelberg.
Okamoto, T. and Takashima, K. (2012a). Adaptively
Attribute-Hiding (Hierarchical) Inner Product En-
cryption. In Pointcheval, D. and Johansson, T., ed-
itors, Advances in Cryptology – EUROCRYPT 2012,
pages 591–608. Springer, Berlin, Heidelberg.
Okamoto, T. and Takashima, K. (2012b). Fully Secure Un-
bounded Inner-Product and Attribute-Based Encryp-
tion. In Wang, X. and Sako, K., editors, Advances
in Cryptology – ASIACRYPT 2012, pages 349–366.
Springer, Berlin, Heidelberg.
Okamoto, T. and Takashima, K. (2015). Achieving Short
Ciphertexts or Short Secret-keys for Adaptively Se-
cure General Inner-product Encryption. Designs,
Codes and Cryptography, 77(2):725–771.
Park, J. H. (2011). Inner-Product Encryption under Stan-
dard Assumptions. Designs, Codes and Cryptogra-
phy, 58(3):235–257.
Ramanna, S. C. (2016). More Efficient Constructions for
Inner-Product Encryption. In Manulis, M., Sadeghi,
A.-R., and Schneider, S., editors, Applied Cryptogra-
phy and Network Security, pages 231–248. Springer,
Cham.
Tseng, Y.-F., Liu, Z.-Y., and Tso, R. (2020). Practical Pred-
icate Encryption for Inner Product. Cryptology ePrint
Archive, Report 2020/270.
Wang, Z., Fan, X., and Wang, M. (2018). Compact Inner
Product Encryption from LWE. In Qing, S., Mitchell,
C., Chen, L., and Liu, D., editors, Information and
Communications Security, pages 141–153. Springer,
Cham.
Xiao, S., Ge, A., Zhang, J., Ma, C., and Wang, X. (2017).
Asymmetric Searchable Encryption from Inner Prod-
uct Encryption. In Xhafa, F., Barolli, L., and Amato,
F., editors, Advances on P2P, Parallel, Grid, Cloud
and Internet Computing, pages 123–132. Springer,
Cham.
Zhang, Y., Li, Y., and Wang, Y. (2019). Efficient Inner Prod-
uct Encryption for Mobile Client with Constrained
Capacity. International Journal of Innovative Com-
puting, Information and Control, 15(1):209–226.
Zhenlin, T. and Wei, Z. (2015). A Predicate Encryption
Scheme Supporting Multiparty Cloud Computation.
In 2015 International Conference on Intelligent Net-
working and Collaborative Systems, pages 252–256.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
558
