
Towards Secure Edge-assisted Image Sharing for Timely Disaster
Situation Awareness
Jing Yao
1,2
, Yifeng Zheng
3
, Cong Wang
1,2
and Surya Nepal
3
1
City University of Hong Kong, Hong Kong, China
2
City University of Hong Kong, Shenzhen Research Institute, Shenzhen, China
3
CSIRO Data61 & CSCRC, Australia
Keywords:
Edge Computing, Data Security, Image Sharing.
Abstract:
To save human lives and reduce injury and property loss in disasters, it is important to collect real-time situa-
tion awareness information such as the surroundings, road conditions, resource information, and more. Among
others, images carry rich information and can easily provide a comprehensive view of the disaster situations.
This is nowadays greatly facilitated with the prevalence of camera-embedded smartphones. However, high
redundancy typically exists among the images gathered from different users during disasters. Given that band-
width is dearer in disaster situations, it would be valuable to detect the image redundancy during transmission
so that bandwidth allocation can be prioritized for unique images, enabling the timely delivery of useful in-
formation. In light of the above, in this position paper, we propose the design of an image sharing system
architecture for timely disaster situation awareness. Our system architecture takes advantage of the emerging
edge computing paradigm to perform image redundancy detection and prioritize the transmission of unique
images, optimizing the amount of useful information delivered within a certain period of time. Meanwhile, to
prevent images from being exposed to the intermediate edge infrastructure, our protocol is devised in a manner
that the edge infrastructure can perform image redundancy detection without seeing the images in the clear.
1 INTRODUCTION
Rapid relief is of paramount importance to save hu-
man lives and reduce injury and property loss in dis-
asters (earthquakes, fires, tornadoes, etc). To facilitate
the rescue workers to effectively and rapidly perform
the work, it is essential to collect real-time situation
awareness information such as the surroundings and
individuals, disaster events, road conditions, resource
information, and more (Zuo et al., 2019).
Among others, images are a carrier of rich in-
formation and could easily present a comprehen-
sive view and description of the disaster situations.
With the prevalence of camera-embedded and cost-
effective smartphones (Zheng et al., 2018), it is very
easy for smartphone users to report and share visual
information about their surroundings through photos.
Indeed, it is quite common for users to take photos
and share them to help reflect the situation of disas-
ters. For example, in Typhoon Haiyan (2013), a huge
amount of images had been shared by users, which
had been leveraged by volunteers to explore which
place is in the greatest need of help (Zuo et al., 2019).
While the images shared during disasters provide
valuable information for timely situation awareness,
there usually exists large redundancy among the im-
ages uploaded by different users. Here, the redun-
dancy refers to images that capture observations on
the same objects/events. For example, a research
study (Weinsberg et al., 2012) shows that 22% of the
images taken by users during the Haiti earthquake
(2010) are similar to each other, and the percentage
even reaches 52% in the image set regarding the San
Diego fire (2007).
Such high redundancy poses challenges on the
timely delivery of useful information for situation
awareness in disaster. In particular, if all images are
treated equally and directly transferred to the disaster
management service (DMS), it poses an obstacle for
gaining unique information in real-time. A lot of re-
sources and efforts would have to be put into the dis-
covery of unique images. Meanwhile, the transfer of
all images at the same time also imposes a heavy load
on the network, which would be highly challenging
given that network bandwidth is dearer in disasters. It
would be much more practical to prioritize the band-
Yao, J., Zheng, Y., Wang, C. and Nepal, S.
Towards Secure Edge-assisted Image Sharing for Timely Disaster Situation Awareness.
DOI: 10.5220/0009801602950301
In Proceedings of the 17th International Joint Conference on e-Business and Telecommunications (ICETE 2020) - SECRYPT, pages 295-301
ISBN: 978-989-758-446-6
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reser ved
295

width allocation on unique images. Therefore, how
to properly prioritize the upload of images from dif-
ferent users for the DMS in disaster scenarios is of
critical importance for timely situation awareness.
To support this, one promising direction is to take
advantage of edge computing, an emerging paradigm
which extends the capabilities of cloud computing
to the network edge (NetworkWorld, 2017). Among
others, one notable advantage of edge computing for
disaster response is that it would allow routers, smart-
phones, and other devices to keep collecting data
even without Internet connections (StorageCraft.com,
2020). So, with edge computing deployed between
the cloud-based DMS and the users, this opens up
the opportunities of giving fast responses to users and
performing redundancy detection before images are
uploaded to the DMS. As the edge infrastructure and
the DMS could be in different trust domains and the
service is set up by the DMS, a crucial requirement
here is that the processing at the intermediate edge
infrastructure should be done over images in the ci-
phertext domain, which prevents third-parties from
accessing/learning about the images.
In this position paper, we propose the design of
a system architecture enabling secure edge-assisted
image sharing for the DMS to gain timely situation
awareness in disasters. At a high level, our architec-
ture takes advantage of the emerging edge computing
architecture to perform image redundancy detection
and prioritize the transmission of the unique images
to the DMS, so as to optimize the amount of useful in-
formation from image sharing within a certain period
of time. For redundancy detection, we mainly rely
on global features extracted from images and lever-
age them to perform similarity measurement between
different images. To support secure redundancy de-
tection efficiently, we resort to an effective similar-
ity search technique called locality-sensitive hashing
(LSH) so that the problem of similarity measurement
of encrypted images can be transformed into equality
testing over the protected image features.
With this as a basis, we then propose to perform
secure in-batch redundancy detection and cross-batch
redundancy detection, with the goal of minimizing the
redundancy per image delivery from the edge server
to the DMS. Here, protected in-batch redundancy de-
tection allows the edge server to detect image redun-
dancy across a batch of images uploaded from dif-
ferent users with a certain period of time and out-
put some candidates of representative images. And
secure cross-batch redundancy detection allows the
edge server to further detect image redundancy be-
tween the representative images and the images previ-
ously uploaded to the DMS via the edge server. With
Edge Server
Mobile Client
Edge Server
Mobile Client
Disaster Management Service
Figure 1: Overview of the system architecture.
the synergy of these protected redundancy detection
strategies, it could provide as much useful and unique
information as possible per image delivery from the
edge server to the DMS.
The rest of this position paper is organized as fol-
lows. Section 2 presents our problem statement. Sec-
tion 3 introduces some preliminaries. Section 4 gives
the details of our design. Section 5 describes the re-
lated work. Section 6 makes conclusions and indi-
cates the future work for this position paper.
2 PROBLEM STATEMENT
2.1 System Architecture
Fig. 1 shows the envisioned system architecture of
secure edge-assisted image sharing for timely situa-
tional awareness in disasters. There are three types
of actors: the mobile client, the cloud-based disas-
ter management service (DMS), and the edge server.
The mobile client is a software application which en-
ables one to share photos captured about disaster situ-
ations to the DMS. The DMS could be setup by re-
lated organization such as the emergency organiza-
tion, the local government, or a social media provider
(Nishiyama et al., 2017), which wants to gather rich
information rapidly so as to facilitate the arrangement
of the rescue activities and decision making for disas-
ter response. The edge server, which could be hosted
by an Internet Service Provider (ISP), is located at the
network edge and closer to the mobile clients. It facil-
itates the mobile clients to quickly share images dur-
ing disasters (NetworkWorld, 2017) without the need
to directly contact the remote DMS. The edge server
collects the images from the mobile clients in the dis-
aster area, and directly performs image redundancy
detection so as to optimize the amount of useful infor-
mation delivered from image sharing for timely situ-
ational awareness in disasters.
From practical considerations, it would be the
DMS’s desire to prevent the intermediate edge server
from directly accessing and learning about the im-
SECRYPT 2020 - 17th International Conference on Security and Cryptography
296
Moblie clients
Image capture
Edge server
Image feature index
DMS
Image storage
Image encryption
Image fingerprint
generation
Image fingerprint
encryption
Image redundancy detection
Enc. in-batch detection
Enc. cross-batch detection
Image transmission
Delay
transmission
Immediate
transmission
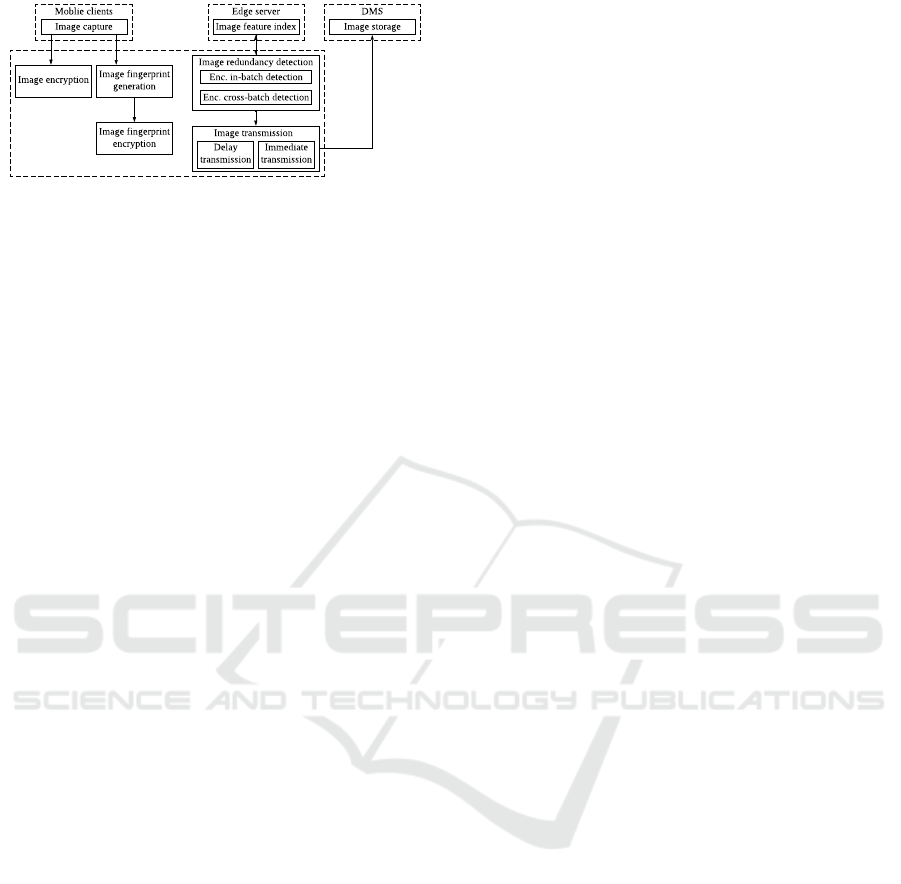
Figure 2: Service workflow.
ages, while still being able to perform the image re-
dundancy detection. This is because the whole service
is setup by the DMS, and the DMS and the edge server
could belong to different trust domains. Therefore,
we craft our design to support processing without dis-
closing the information of images. At a high level, as
shown in Fig. 2, the service flow in our system is as
follows. In an initialization stage, each mobile client
signs up at DMS and obtains secret keys. In disas-
ter environments, to share images, each mobile client
first generates fingerprints for images , and then lever-
ages hash function to protect the fingerprints. At last,
each mobile client encrypts images. The protected
fingerprints and encrypted images are then sent to the
nearby edge server. Upon receiving a batch of pro-
tected fingerprints and encrypted images from possi-
bly multiple clients within a certain period of time, the
edge server will prioritize the image transmission so
as to decide which images should be uploaded with
high priority. Specifically, for this batch of images,
the edge server leverages the protected fingerprints to
do redundancy (similarity) detection, so as to select
a subset of representative encrypted images. We call
this procedure secure in-batch redundancy detection.
For these representative encrypted images, the
edge server then performs similarity detection based
on their protected fingerprints, against the set A of
protected fingerprints of images previously uploaded
via the edge server. We call this secure cross-batch
similarity detection. For those non-similar encrypted
images, the edge server places them ino a set B, and
also adds their protected fingerprints to the set A. Af-
ter secure cross-batch similarity detection, the edge
server puts the images in B into the transmission
queue, in the order of their arrival, and initiates the
image transmission to the DMS. For the remaining
images, the edge server puts them into another queue
pending transmission, in the order of their arrival.
2.2 Threat Model
We consider that the threats in our system architecture
mainly come from the engagement of the edge server.
Our security goal is to protect the confidentiality of
the images as well as the fingerprints, against the in-
termediate edge server. It is assumed to be honest-
but-curious, which means that it will follow our pro-
tocol faithfully yet attempt to obtain the images. We
note that this assumption is widely adopted in the lit-
erature so our adoption is consistent with prior work
(Ma et al., 2019). Note that the fingerprint of an im-
age could be used to infer some information of that
image (Ferreira et al., 2017), so all the fingerprints
also demand protection. Additionally, we assume that
the mobile client and the DMS are fully trusted. We
deem attacks like DDoS attacks and data integrity at-
tacks out of the scope.
3 PRELIMINARIES
3.1 Image Features
Image features could provide a short summary of the
content of an image, i.e., acting as a fingerprint. In
general, image features can be divided into two cate-
gories: (1) local features and (2) global features. A
local feature only describes an interesting point of
an image. So, for an image, multiple local features
need to be computed. Different from local features, a
global feature can represent the whole content of an
image. It is usually computed by the color histogram,
texture values of an image, etc. In comparison with
local features, global features are advantageous due
to their high efficiency in feature extraction as well as
in use for similarity detection (Chamoso et al., 2018).
Therefore, we use global features to detect image sim-
ilarity.
3.2 Locality-sensitive Hashing
A locality-sensitive hashing distributes a hash func-
tion family over a dataset, enabling similar data points
to have hash collisions with high probability and dis-
similar data to have hash collisions with little proba-
bility. It is generally used for similarity search(Zheng
et al., 2017; Cui et al., 2016), with the formal defini-
tion stated as follows.
Definition 1. (Locality-sensitive Hashing) Let F be a
hash function family and R be the range of hash re-
sults of the dataset D. The distance function is de-
noted as dis(x, y), where x, y ∈ D. Given the two
distance values {(r
1
, r
2
)|r
1
< r
2
} and the two prob-
ability values {(p
1
, p
2
)|p
1
> p
2
}, the family F =
{h : D → R} is a (r
1
, r
2
, p
1
, p
2
)-locality sensitive
hash function family if for any {(d
1
, d
2
)|dis(d
1
, d
2
) ≤
r
1
∧ d
1
, d
2
∈ D}, then Pr[h(d
1
) = h(d
2
)] ≥ p
1
; if
Towards Secure Edge-assisted Image Sharing for Timely Disaster Situation Awareness
297

for any {(d
1
, d
2
)|dis(d
1
, d
2
) > r
2
∧ d
1
, d
2
∈ D}, then
Pr[h(d
1
) = h(d
2
)] ≤ p
2
.
4 DESIGN OF SECURE
EDGE-ASSISTED IMAGE
SHARING IN DISASTERS
In this section, we start with the description of our de-
sign intuition on secure edge-assisted image sharing
in disasters. Then, we move on to the introduction of
the detailed scheme.
4.1 Design Intuition
Our main design insight is to prioritize the transmis-
sion of the unique images via fingerprint-based sim-
ilarity detection at the edge server, so as to optimize
the amount of useful information per image delivery
for timely situational awareness in disasters. As we
aim to protect the confidentiality of images and fin-
gerprints, all the processing should be done with the
prerequisite of protecting the confidentiality of im-
ages and fingerprints. To instantiate our main idea,
some design considerations need to be addressed.
The first consideration is how to efficiently sup-
port similarity detection for two encrypted images.
Recall that we resort to global features as fingerprints
for similarity detection. The straightforward way of
doing this is to compute the distance (under a com-
mon metric like Hamming distance or Euclidean dis-
tance) between the fingerprints of two images. A
smaller distance means a higher similarity between
the two images. If the distance is less than a pre-
defined threshold, the two images are considered as
similar images. However, such a plausible approach
would demand the use of advanced and expensive
cryptographic primitives like homomorphic encryp-
tion in our scenario. To avoid pairwise distance com-
putation between the fingerprints as well as achieve
high efficiency in similarity detection, we leverage a
set of LSH functions to hash global features of im-
ages. According to the definition of LSH, an LSH
function can map the features of similar images to
identical LSH values with high probability. In this
case, the similarity of any two images can be ef-
ficiently measured by counting the number of their
matched LSH values.
The second consideration is on the confidential-
ity of the image fingerprints. As LSH does not have
the one-way property from a cryptographic perspec-
tive (Partridge et al., 2012), the adversary might still
be able to infer information about the image finger-
prints. To preserve the confidentiality of the finger-
prints, our design hashes LSH values before the mo-
bile client’s uploading them to the edge server. Con-
sidering the resource constraints of mobile devices,
we take advantage of a lightweight mechanism, i.e.,
one-way hash, for mobile clients to protect the finger-
prints. In order to preserve the characteristic of LSH
that maps similar data to the identical hash result with
high probability, each LSH value of the fingerprint
is hashed separately. Note that the similarity detec-
tion is only based on the fingerprints so the images
could be independently encrypted under standard en-
cryption mechanisms.
The third consideration is how to properly perform
secure in-batch redundancy detection and cross-batch
redundancy detection. As mentioned before, secure
in-batch redundancy detection refers to select a sub-
set of representative encrypted images from a batch
of encrypted images collected by the edge server over
a certain period of time. In contrast, secure cross-
batch redundancy detection aims to select images
from the representative image set so that the selected
images ware not similar to the images previously up-
loaded by the edge server. It is noted that most of
the existing designs only consider the detection of
cross-batch redundancy, such as SmartEye(Hua et al.,
2015) and MRC(Dao et al., 2017). The only design
that takes into account both cross-batch redundancy
and in-batch redundancy is the design due to Zuo et
al. (Zuo et al., 2019). Their design works under a
different scenario where only the cloud is engaged.
Besides, they first detect the cross-batch similar im-
ages, followed by the detection of the in-batch similar
images. Given that the similar images will be trans-
mitted in the same time period with high probability
under the disaster scenario, our belief is that it would
be much more efficient to first perform in-batch simi-
larity detection and then cross-batch similarity detec-
tion. Through this delicate consideration, the number
of images involved in cross-batch similarity detection
would be largely reduced, leading to efficiency im-
provement on the cost-dominant cross-batch redun-
dancy detection.
4.2 Our Proposed Design
We now present the detailed design for secure edge-
assisted image sharing in disasters. Overall, there are
three key modules, i.e., data preparation, secure in-
batch redundancy detection, and secure cross-batch
redundancy detection. We elaborate on each of them
as follows.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
298

Algorithm 1: Data Preparation at the Mobile Client.
Input: Image I and secret key k.
Output: Encrypted image c and protected feature v.
1: f ← f Extract (I).
2: w ← LSH ( f ), where w =
{
w
1
, · · · , w
l
}
;
3: for i ∈
{
1, · · · , l
}
do
4: v
i
← H (w
i
).
5: end for
6: c ← E
k
(Im).
4.2.1 Data Preparation
Fig. 1 shows the data preparation module. The mo-
bile client first calls the feature extraction function
f Extract (·) to extract the fingerprint f from the im-
age Im to be uploaded. Examples of global features as
fingerprints include dhash and ahash(Neal Krawetz,
2013). The mobile client then applies l LSH func-
tions to the fingerprint and generates a set w of LSH
values. At last, the mobile client hashes w with a one-
way hash function H (·) and outputs the protected fin-
gerprint v =
{
v
1
, · · · , v
l
}
. For the image I, the mobile
client calls an encryption scheme E (·) which could be
the standard AES encryption scheme, and outputs the
encrypted image c. Finally, the mobile client uploads
all encrypted images and protected fingerprints to the
nearby edge server.
4.2.2 Secure In-batch Redundancy Detection
In disaster scenarios, it is very likely that there are
similar images in the batch of images collected the
edge server over a certain period of time. Therefore,
we perform in-batch redundancy detection so as to se-
lect a representative image set from these images. The
high-level idea is to first divide the batch of images
into groups according to the similarity between each
of two encrypted images in the batch. In particular,
the edge server first calculates the similarity between
each of any two images in the batch. Let the protected
fingerprints of two images I
1
and I
2
be v
1
and v
2
re-
spectively. The distance between the two images is
computed via dis (I
1
, I
2
) = ||v
1
− v
2
||
1
, where || · ||
1
denotes the L1 distance. The two images I
1
and I
2
are considered to be similar, if dis (I
1
, I
2
) < ε, where
ε is a pre-defined similarity threshold. Based on this,
the edge server then divides the in-batch images into
groups. We use k to denote the number of groups.
According to the grouping result, the edge server
then proceeds to select a set of representative images
in the batch. There are several intuitive strategies that
could be adopted here. The first strategy is to select
from each group the image that arrives at the edge
server the earliest, following the general principles of
packet forwarding for routers and switches, i.e., first-
in, first-out (FIFO). However, this strategy may lead
to an excessive content loss, given that it is very likely
that the content of the first image may not well sum-
marize the information contained in this group of im-
ages. The second possible strategy is to select the im-
age with the highest resolution in each group. How-
ever, this also does not guarantee that the largest im-
age is the most informative one in the group.
In short, although these intuitive strategies are
simple and relatively easy to realize, they may not
produce a good representative set that could well
represent the whole batch of images. We note that
an alternative choice is to adapt a more advanced
optimization-based strategy inspired by (Zuo et al.,
2019) in our scenario, which allows to select a sub-
set T of images that could best represent the whole
batch S of images. At a high level, the selection
of a subset of representative images is formulated as
an optimization problem, where the objective is for-
mulated as: T
∗
∈ argmax
T ⊂S
F(T ). Here, F is a
scoring function that can quantitatively represent the
quality of a summary (i.e., the subset of representa-
tive images). The realization of the function F is a
weighted sum of two sub-functions: a coverage func-
tion f
c
and diversity function f
d
. That is, F(T ) =
λ
1
· f
c
(T ) + λ
2
· f
d
(T ), where λ
1
and λ
2
are non-
negative. Specifically, the coverage function is for-
mulated as f
c
=
∑
i∈S
max
j∈T
w
i, j
, where the intuition
is to use the sum of the similarity between an image
i in S and its most similar image in T . For the diver-
sity function, it is formulated as f
d
=
∑
k
i=1
N (T, I
i
),
where I
i
refers to the set of images in a i-th group,
and N (T, I
i
) takes the value 0 if T and I
i
have empty
intersection, and the value 1 otherwise. Solving the
above optimization needs a constraint on the size of
the selected subset, for which we set it to the number
of groups, i.e., |T | ≤ k.
Algorithm 2 shows the procedure of in-batch re-
dundancy detection, which allows the edge server to
select a representative subset of images from a batch
of images collected over a certain period of time. The
edge server first calculates the similarity between any
two images in the batch. Then, it uses the similar-
ity threshold ε to partition the batch of images into
several groups. Finally, the edge server solves the op-
timization problem via a greedy algorithm to output a
subset of representative images.
4.2.3 Secure Cross-batch Redundancy Detection
In secure cross-batch redundancy detection, we aim
to further select a subset from the encrypted represen-
tative images obtained from in-batch similarity detec-
Towards Secure Edge-assisted Image Sharing for Timely Disaster Situation Awareness
299

Algorithm 2: Secure In-batch Redundancy Detection at the
Edge Server.
Input: The batch S of encrypted images C
S
=
{c
1
, · · · , c
|S|
} and the batch of protected features
V
S
= {v
1
, · · · , v
|S|
}.
Output: T
n
(n is the number of iterations).
1: Compute pairwise similarity w
i, j
among the im-
ages C
S
in the batch S according to the batch of
protected features V
S
.
2: Divide the batch S of images into several groups
according to the principle of whether w
i, j
< ε.
3: Denote the number of groups as k.
4: Choose an image S
1
arbitrarily.
5: T
1
← S
1
.
6: While |T
i
| ≤ k
7: Choose S
i
∈ argmax
S
i
∈S\T
i
F(T
i
∪ {S
i
}).
8: T
i+1
← T
i
∪ {S
i
}.
9: i ← i + 1.
10: end while
tion, ensuring that each of the selected images is not
similar to any image uploaded to the DMS before via
the edge server. The high-level idea of secure cross-
batch redundancy detection is to query the protected
fingerprints of the encrypted images previously up-
loaded to the DMS, and check if some encrypted rep-
resentative images are similar to them.
A simple approach for the edge server is to send
the protected fingerprints of all the representative im-
ages to the DMS, which then performs the redun-
dancy detection and returns the detection result to the
edge server. However, this could lead to high latency.
To alleviate this problem, our design is to let the edge
server build and maintain an index using efficient and
succinct data structures over the protected fingerprints
of images previously uploaded to the DMS. In this
case, the edge server can perform cross-batch redun-
dancy detection locally. When the edge server sends
an image to DMS, it also inserts the protected finger-
print of that image to the index.
4.3 Security Guarantees
The security of our proposed design directly follows
from that of the one-way hash and the image encryp-
tion scheme. Specifically, as we use a one-way hash
function to hash the LSH values of image fingerprints,
this makes it computationally infeasible to reveal the
fingerprint from the protected fingerprints (Partridge
et al., 2012). Therefore, the proposed design can pro-
tect the image fingerprints against the edge server. For
the images, recall they are encrypted via either stan-
dard encryption schemes. So the confidentiality of the
images is well protected against the edger server. Ad-
ditionally, we remark that revealing the similarity of
images in the ciphertext domain is necessary to sup-
port the target functionality of redundancy detection.
5 RELATED WORK
Our work is closely related to the existing works on
content-aware redundancy elimination in disaster en-
vironments, where the ultimate goal is to ask mobile
clients to only upload unique images after image re-
dundancy detection. Some works ((Dao et al., 2017;
Zuo et al., 2019), to just list a few) have proposed
to perform redundancy detection at the remote server
side (e.g., the cloud). In these designs, the mobile
client is typically required to send all features and
wait for the detection result. This might greatly re-
duce user experience when the database of images at
the remote server side is very large, which could be
the norm in disaster scenarios.
Instead of doing redundancy detection at the re-
mote server side, some works ((Hua et al., 2015; Zuo
et al., 2019; Weinsberg et al., 2012), to just list a
few) have proposed to take advantage of advanced
networking architectures like software-defined net-
working (SDN) or delay tolerant network (DTN) to
perform in-network redundancy detection. Our work
differs from prior work mainly from several aspects.
Firstly, our design takes into account the security of
images and fingerprints so the redundancy detection
is all performed while protecting the confidentiality of
images. Secondly, our design takes advantage of the
emerging edge computing architecture to perform se-
cure redundancy detection. With the assistance of the
edge server, the mobile clients in our system archi-
tecture do not need to wait for the redundancy detec-
tion results. Thirdly, while most of the existing works
only consider cross-batch redundancy detection, our
design support both (secure) in-batch redundancy de-
tection and cross-batch redundancy detection, which
is customized for our scenario as well.
6 CONCLUSIONS AND FUTURE
WORK
In this position paper, we explore and propose a sys-
tem architecture for the DMS, enabling secure edge-
assisted image sharing for timely disaster awareness.
Aiming for redundancy detection as well as image se-
curity against the intermediate edge infrastructure, we
propose to apply the strategies of in-batch redundancy
SECRYPT 2020 - 17th International Conference on Security and Cryptography
300

detection and cross-batch redundancy detection, and
design from the ground up so as to do all the effec-
tive processing while ensuring protection of images.
Our customized design comes from a synergy of a se-
ries of techniques including image processing, data
encryption, efficient similarity search, and optimiza-
tion.
As future work, we plan to implement a proof-
of-concept system prototype and conduct a compre-
hensive evaluation over real-world datasets. Specif-
ically, we will measure the effectiveness of our se-
cure redundancy detection design over some real-
world disaster image datasets. We will also evalu-
ate the cost efficiency on different ends along the ser-
vice flow. We also intend to define formal security
definitions and provide formal proofs. Besides, we
will explore the design space of emerging security so-
lutions like trusted execution environments, for effi-
ciently defending against malicious adversaries that
compromise the edge server and deviate arbitrarily.
ACKNOWLEDGEMENTS
This work was supported in part by the Research
Grants Council of Hong Kong under Grants CityU
11202419, CityU 11212717, CityU 11217819, and
CityU C1008-16G.
REFERENCES
Chamoso, P., Rivas, A., S
´
anchez-Torres, R., and Rodr
´
ıguez,
S. (2018). Social computing for image matching. PloS
one, 13(5):e0197576.
Cui, H., Yuan, X., Zheng, Y., and Wang, C. (2016). En-
abling secure and effective near-duplicate detection
over encrypted in-network storage. In Proc. of IEEE
INFOCOM.
Dao, T., Roy-Chowdhury, A. K., Madhyastha, H. V., Krish-
namurthy, S. V., and Porta, T. L. (2017). Managing
redundant content in bandwidth constrained wireless
networks. IEEE/ACM TON, 25(2):988–1003.
Ferreira, B., Rodrigues, J., Leitao, J., and Domingos, H.
(2017). Practical privacy-preserving content-based
retrieval in cloud image repositories. IEEE TCC,
13(9):1–14.
Hua, Y., He, W., Liu, X., and Feng, D. (2015). Smarteye:
Real-time and efficient cloud image sharing for disas-
ter environments. In Proc. of IEEE INFOCOM.
Ma, L., Liu, X., Pei, Q., and Xiang, Y. (2019). Privacy-
preserving reputation management for edge comput-
ing enhanced mobile crowdsensing. IEEE Trans. Ser-
vices Computing, 12(5):786–799.
Neal Krawetz (2013). Kind of Like That.
http://www.hackerfactor.com/blog/?/archives/
529-Kind-of-Like-That.html/.
NetworkWorld (2017). When disasters strike,
edge computing must kick in. https:
//www.networkworld.com/article/3228884/
when-disasters-strike-edge-computing-must-kick-in.
html.
Nishiyama, J., Tabata, S., and Shigeno, H. (2017). An effi-
cient image gathering scheme with quality control in
disaster. In Proc. of IEEE AINA.
Partridge, K., Pathak, M. A., Uzun, E., and Wang, C.
(2012). Picoda: Privacy-preserving smart coupon de-
livery architecture. In Proc. of HotPETs.
StorageCraft.com (2020). Edge Computing vs.
Cloud Computing. https://blog.storagecraft.com/
edge-computing-cloud-computing/.
Weinsberg, U., Li, Q., Taft, N., Balachandran, A., Sekar,
V., Iannaccone, G., and Seshan, S. (2012). CARE:
content aware redundancy elimination for challenged
networks. In Proc. of ACM HotNets.
Zheng, Y., Cui, H., Wang, C., and Zhou, J. (2017).
Privacy-preserving image denoising from external
cloud databases. IEEE Trans. Information Forensics
and Security, 12(6):1285–1298.
Zheng, Y., Duan, H., and Wang, C. (2018). Learn-
ing the truth privately and confidently: Encrypted
confidence-aware truth discovery in mobile crowd-
sensing. IEEE Trans. Information Forensics and Se-
curity, 13(10):2475–2489.
Zuo, P., Hua, Y., Sun, Y., Liu, X. S., Wu, J., Guo, Y., Xia,
W., Cao, S., and Feng, D. (2019). Bandwidth and en-
ergy efficient image sharing for situation awareness in
disasters. IEEE TPDS, 30(1):15–28.
Towards Secure Edge-assisted Image Sharing for Timely Disaster Situation Awareness
301
