
A White-Box Encryption Scheme using Physically Unclonable Functions
Sandra Rasoamiaramanana
1,2
, Marine Minier
1
and Gilles Macario-Rat
2
1
Universit
´
e de Lorraine, CNRS, Inria, LORIA, F-54000 Nancy, France
2
Orange Labs, Applied Crypto Group, Ch
ˆ
atillon, France
Keywords:
White-Box Cryptography, Code Lifting Attack, Device Binding, Physically Unclonable Functions.
Abstract:
When a cryptographic algorithm is executed in a potentially hostile environment, techniques of White-Box
Cryptography are used to protect a secret key from a fully-privileged adversary. However, even if the adversary
is not able to extract the secret key from the implementation, they might lift the entire white-box code and
execute it (this is called a code lifting attack). In this work, we introduce an encryption scheme that can be
implemented on an untrusted environment and is still secure even if the white-box code has been lifted. We
base our proposal on a Physically Unclonable Function (PUF) to ensure the execution context of our so-called
PUF-based encryption scheme. This way, the encryption is “locked” by a particular device.
1 INTRODUCTION
White-Box Cryptography (WBC) was first introduced
by Chow et al. in
2002
(Chow et al., 2002a; Chow
et al., 2002b) as an obfuscation technique for a cryp-
tographic algorithm. Thus, the purpose of WBC is
to produce an implementation of a cryptographic al-
gorithm which hides the key in the data such that a
fully-privileged adversary which controls the execu-
tion environment of the algorithm and has access to the
implementation cannot extract the key from it. This
statement refers to the key extraction security. How-
ever, Chow et al. also pointed out that in this context,
an adversary might lift the implementation and exe-
cute the algorithm without knowing the key. Thus,
the security of an implementation in the white-box
model brings together the resistance to key extraction
and the resistance to a code lifting attack. Two no-
tions are generally used to capture those security goals:
unbreakability and incompressibility/space-hardness
(Delerabl
´
ee et al., 2013; Biryukov et al., 2014; Fouque
et al., 2016; Bogdanov et al., 2016). While unbreak-
ability defines the basic requirement for a white-box
implementation which is to merge the secret key inside
the implementation, space-hardness ensures that an ad-
versary having a portion of the code cannot execute
the algorithm and aims to mitigate code lifting without
preventing it. Following this approach, white-box ded-
icated block ciphers such as SPACE or SPNbox have
been proposed in (Biryukov et al., 2014; Bogdanov
and Isobe, 2015; Bogdanov et al., 2016; Fouque et al.,
2016; Cho et al., 2017). Yet, if the adversary is able to
copy the white-box code, they can take advantage of
the code functionality without any restriction.
In this work, we address this issue and attempt to
avoid code lifting by binding the white-box code to
its environment. The idea is that even if the adversary
lifts the entire white-box code, they will not take ad-
vantage of the code functionality. For that, we make
use of a Physically Unclonable Function (PUF) (Maes,
2012) to reinforce the security against code lifting.
A PUF is a physical system that can be challenged
with a stimuli and which reacts: the so-called response
depends on manufacturing variations which induce a
structural disorder that cannot be cloned or reproduced
exactly. Thanks to such a device-specific behavior, a
PUF might be used for identification, authentication,
and even key generation.
We formalize the concept of PUF in Section 2.
In Section 3, we introduce the notion of PUF-based
encryption scheme as an encryption scheme which
takes three inputs: a secret key, a plaintext and a PUF
response. Thus, the PUF response adds a variability
mechanism to the encryption scheme. First, we formal-
ize the notion of lockability
1
to guarantee the security
of the scheme when implemented in the white-box
model: lockability states the difficulty of executing
a lifted white-box code on a different device. Then,
we instantiate the scheme with the tweakable Even-
Mansour construction of (Cogliati et al., 2015) and
1
Neologism to define the possibility to lock a cipher to
an execution environment.
Rasoamiaramanana, S., Minier, M. and Macario-Rat, G.
A White-Box Encryption Scheme using Physically Unclonable Functions.
DOI: 10.5220/0009781002790286
In Proceedings of the 17th International Joint Conference on e-Business and Telecommunications (ICETE 2020) - SECRYPT, pages 279-286
ISBN: 978-989-758-446-6
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
279

the white-box dedicated block cipher SPNbox-
8
(Bog-
danov et al., 2016).
2 PHYSICALLY UNCLONABLE
FUNCTIONS
This section gives an overview of the concept of PUF
without being exhaustive. We refer to (Maes, 2012)
for a complete description and analysis.
2.1 Characterization of a Physically
Unclonable Function
A PUF is a physical entity (e.g. an integrated cir-
cuit) that presents random imperfections in its struc-
ture. The imperfections result from the manufactur-
ing process and are expected to be instance specific
and unclonable. The term PUF also refers to the “ex-
pression” (the challenge-response behavior) of these
random imperfections. To characterize a PUF, the
physical disorder (e.g. a current or a voltage) is gen-
erally measured under a specific condition (stimuli)
and converted into digital form. Thus, a PUF performs
a probabilistic functional operation: given a certain
input (a stimuli, also called a challenge) it produces
a measurable output (the response). Consequently, a
PUF is seen as a physical realization of a probabilistic
mapping
puf : X → Y
where
X
is the domain space
called the challenge set and
Y
is an output range called
the response set. The creation of a PUF is expressed
by invoking a manufacturing process on a set of pa-
rameters param. We write
puf ←$ CREATE(param)
to
signify that a PUF instance is created. The set of all
instances created according to a set of parameters is
called a PUF class and denoted by
P
. An instance of
P
can be evaluated on a challenge
x ∈ X
using an eval-
uation procedure EVAL: we write
y ← EVAL(puf,x)
or simply
y ← puf(x)
for the evaluation of
puf
on the
challenge
x
. The outputs of a PUF instance are gen-
erally noisy, i.e.,
puf
outputs two distinct responses
y, y
0
when evaluated twice on the same challenge
x
.
Thus, a PUF response is considered as a random vari-
able, and information about the distribution of the
PUF responses is obtained through experiment. An
experiment on a PUF class is parametrized by
t,q
c
,
and
q
r
which are the number of evaluations of one
instance on the same challenge, the number of created
instances, and the number of distinct evaluations on
an instance, respectively. The experiment gives esti-
mated descriptive statistics of the intra-distance
δ
1
,
of the instance inter-distance
δ
2
and of the PUF inter-
distance
δ
3
. The intra-distance is the distance between
two distinct responses of an instance evaluated on the
same challenge. In the same manner, the instance
inter-distance and the PUF inter-distance characterize
the distance between any two responses
y, y
0
of an in-
stance puf evaluated on two distinct challenges
x,x
0
and
the distance between two outputs
y, y
0
of two distinct
instances puf, puf’ evaluated on the same challenge
x
, respectively. On the one hand, the intra-distance
property estimates the reproducibility of a PUF out-
put. Thus, low intra-distance ensures that the PUF
outputs are highly reproducible. On the other hand,
the PUF inter-distance estimates the uniqueness of an
instance’s output while the instance inter-distance en-
sures the uniqueness of a response given a challenge.
The intra-distance
δ
1
should be lower than
δ
2
and
δ
3
to
uniquely distinguish outputs from different instances
and outputs from different challenges. For the rest
of the paper, we denote by dist the distance. Another
property of PUF outputs that should be estimated is
the min-entropy. The min-entropy of a binary string
represents the number of uniform bits and measures
the uncertainty one has on the output. The conditional
min-entropy is more relevant for the distribution of
PUF outputs since an adversary should not deduce
enough information about an unknown output given
many outputs. These properties characterize the out-
put distribution of PUF instances and give an idea of
the reliability of a PUF class. A PUF class may ver-
ify other properties (Maes, 2012). We focus on the
unclonability and unforgeability properties.
2.2 Security Notions
We use the formal definitions of unforgeability and
unclonability that have been introduced in the paper of
Armknecht et al. (Armknecht et al., 2016).
We denote by
A
a Probabilistic Polynomial Time
(PPT) adversary. If
λ
is the security parameter then the
running time of
A
is polynomial in
λ
. Let
ε: N → R
be a negligible function, i.e. for any polynomial func-
tion
p: N → N
there exists
n
0
such that
ε(n) < 1/p(n)
for any
n > n
0
. The following unforgeability game
states the advantage of an adversary
A
to guess one
output of a PUF without having access to the device.
We assume that the challenger has access to the man-
ufacturing process and thus can invoke the creation
procedure on a set of parameters param. The adver-
sary can only choose a set of parameters to obtain new
instances from an oracle. Thus, they can get instances
of one PUF class or instances of different PUF classes
depending on the chosen set of parameters. We assume
that there exists a recovery procedure that recovers a
noise-free response from noisy ones. Thus, the adver-
sary is only required to guess a noisy response at a
SECRYPT 2020 - 17th International Conference on Security and Cryptography
280

distance not more than δ
1
from the correct response.
Set Up.
The challenger selects a manufacturing pro-
cess and initial parameters param. The challenger
sends
(1
λ
,param)
to the adversary
A
and initial-
izes two counters c
0
,c
1
.
Learning. A
adaptively issues two types of oracle
query: a creation query to create a new instance un-
der some chosen parameters and a response query
to get the output of an instance of their choice.
A
is allowed to issue at most
q
c
creation queries and
q
r
response queries.
•
When
A
issues a creation query with
param
0
,
the challenger creates
puf
c
0
← CREATE(param)
if
param
0
= param
and increments
c
0
, or creates
puf
0
c
1
← CREATE(param
0
)
if
param
0
6= param
but is a valid creation parameter and increments
c
1
. Otherwise the challenger responds ⊥.
•
When
A
issues a response query with
(b,i,x
j
)
,
the challenger sends
y
i, j
← puf
i
(x
j
)
if
b = 0
and
i 6 c
0
or sends
y
0
i, j
← puf
0
i
(x
j
)
if
b = 1
and
i 6 c
1
.
Otherwise the challenger returns ⊥.
Guess. A outputs (i
∗
,x
∗
,y
∗
).
The index
i
∗
denotes the instance chosen by
A
such
that
y
∗
is probably the result of the evaluation of
puf
i
∗
on
x
∗
. We denote by EUF-CICA the Existential Un-
forgeability under Chosen Instance and Challenge At-
tack defined as follows.
Definition 1
(EUF-CICA)
.
Let
Adv
euf-cica
A,P
(λ,δ
1
)
be the
advantage of an adversary
A
playing the unforgeabil-
ity game. We have Adv
euf-cica
A,P
(λ,δ
1
) =
Pr [dist(y
∗
,puf
i
∗
(x
∗
)) 6 δ
1
|
x
∗
∈ X \ X
i
∗
] −
|
B
|
|
Y
|
where
puf
i
∗
is a PUF instance that has been created
by the challenger in the learning phase,
X
i
∗
is the set
of challenges that have been issued for the instance
i
∗
and
B = {y | y
i
∗
← puf
i
∗
(x
∗
) and dist(y
i
∗
,y) 6 δ
1
}
is the set of outputs
y
that are at a distance at most
δ
1
from puf
i
∗
(x
∗
).
A PUF provides
(q
c
,q
r
,δ
1
,ε)
-EUF-CICA security
if for any PPT adversary A we have
Pr
h
Adv
euf−cica
A,P
(λ,δ
1
) > 0
i
6 ε(λ).
The adversary wins the game if their guess
y
∗
belongs
to the set
B
with probability higher than randomly
picking an element of B.
A stronger notion is unclonability which expresses
the hardness of constructing two PUF instances that
show the same input-output behavior. The unclonabil-
ity game is as follows.
Set Up.
The setup phase is the same as in the unforge-
ability game.
Learning. A
issues oracle queries as in the learning
phase of the unforgeability game.
Guess. A outputs (i
∗
,b, j
∗
).
The output
(i
∗
,b, j
∗
)
is interpreted as follows:
i
∗
gives
the index of an instance created under the paramater
param. If
b = 0
then
j
∗
is the index of an instance
created under the parameter
param
; otherwise
j
∗
is
the index of an instance created under the parameter
param
0
. To win,
A
should exhibit two clones either
from the same class or from two distinct classes. In
other words, the unclonability should garantee that it
is both hard to construct two clones using the same
set of parameters and to find a set of parameters that
enables the construction of clones.
We denote by UUC-CICA the Universal Unclon-
ability security defined by the following.
Definition 2
(UUC-CICA)
.
Let
Adv
uuc−cica
A,P
(λ,δ
1
)
be
the advantage of an adversary
A
playing the unclon-
ability game. Let
puf
i
∗
and
puf’
j
∗
be the PUF instances
which correspond to the output
(i
∗
,b, j
∗
)
of
A
. We
have Adv
uuc−cica
A,P
(λ,δ
1
) =
Pr
∀x ∈ X ,dist(puf
i
∗
(x),puf’
j
∗
(x)) 6 δ
1
.
A PUF provides
(q
c
,q
r
,δ
1
,ε)
-UUC-CICA if for any
PPT adversary A we have Adv
uuc−cica
A,P
(λ,δ
1
) 6 ε(λ).
3 GENERAL CONSTRUCTION
In the following, we introduce the PUF-based encryp-
tion scheme which is used to define a PUF-based white-
box encryption scheme when provided with a white-
box compiler.
3.1 PUF-based Encryption Scheme
In the definition of a PUF-based encryption scheme
below, the encryption and the decryption algorithms
take three arguments, the additional argument being
the PUF output. We denote by
M
and
C
the sets of
plaintexts and ciphertexts, respectively.
Definition 3
(PUF-based Encryption Scheme (PES))
.
Let
P = {puf : X → Y }
be a PUF class. A PUF-
based encryption scheme consists of polynomial time
algorithms (KGen, EVAL,Enc,Dec) such that
• KGen
is a probabilistic algorithm which outputs a
key: K ←$ KGen(1
λ
).
• Eval
is a probabilistic algorithm that evaluates a
PUF instance: y ←$ EVAL(puf, x).
• Enc
is a probabilistic algorithm:
C ←$ Enc(K,y,M).
A White-Box Encryption Scheme using Physically Unclonable Functions
281

• Dec
is a deterministic algorithm:
M ←
Dec(K,y,C).
A PUF-based encryption scheme satisfies correct-
ness for an instance puf if
∀M ∈ M
and
∀x ∈ X
,
Pr [Dec(K,y, Enc(K,y, M)) = M
|
y ← puf(x) ] = 1.
Definition 4
(White-Box Compiler)
.
Let
E =
(KGen,Enc,Dec)
be a symmetric encryption scheme.
A white-box compiler for
E
is a probabilistic algo-
rithm Comp that outputs a white-box program
P
of the
cipher for a fixed key K.
•
If
P
implements
Enc
K
then
∀M ∈ M
,
Pr [P(M) = Enc(K, M)] = 1
. We say that
(KGen,Enc,Dec,Comp)
is a white-box encryp-
tion scheme.
•
If
P
implements
Dec
K
then
∀C ∈ C
,
Pr [P(C) = Dec(K,C)] = 1
. We say that
(KGen,Enc,Dec,Comp)
is a white-box decryp-
tion scheme.
If Comp is a white-box compiler defined for the PES
of Definition 3, then the white-box program
P
is such
that, for any
y
and
M
,
P(y, M) = Enc(K,y,M)
in the
case of a white-box encryption scheme and
P(y,C) =
Dec(K,y,C)
for a white-box decryption scheme. The
PES and the white-box compiler form a PUF-based
white-box encryption scheme (PWE).
3.2 Security Models
We consider the white-box setting and state the security
of a PWE. We consider a white-box implementation of
the encryption algorithm, i.e. the program
P
outputted
by the white-box compiler implements
Enc
K
for a
fixed key
K
. The adversary
A
is divided into two
adversaries
(A
1
,A
2
)
such that
A
2
is run on
A
1
’s output.
A
1
is allowed to make at most
q
c
creation queries and
q
r
response queries while
A
2
is allowed to make at
most q decryption queries.
3.2.1 Unbreakability
In the unbreakability game, we only consider the ad-
versary
A
2
whose goal is to recover the secret key
K
.
We consider the Chosen-Plaintext Attack (CPA) where
the adversary chooses
q
plaintexts (and the input
y
)
and encrypts them with the program
P
and the Chosen-
Ciphertext Attack (CCA) where they are allowed to
query a decryption oracle with
q
chosen ciphertexts
(and input
y
) in addition to
q
chosen-plaintexts. The
advantage of the adversary
A
2
in the UBK-ATK secu-
rity game is the probability that
A
2
outputs the key
K
. As in (Delerabl
´
ee et al., 2013), the white-box en-
cryption scheme is secure in the sense of UBK-ATK
for
ATK ∈ {CPA,CCA}
, if the advantage of any PPT
adversary is negligible.
Moreover, even if full break is not possible, the
adversary can lift the code and encrypt without know-
ing the key. We define the notion of lockability to
capture the difficulty of executing a lifted white-box
code without a PUF instance.
3.2.2 Lockability
We assume that the adversary has access to the white-
box program
P
. Their goal is to correctly encrypt a
random plaintext given a random challenge
x
.
A
1
plays
an EUF-CICA or an UUC-CICA game while the attack
model for the adversary A
2
is either CPA or CCA.
We define two security notions, depending on the
attack model used against the PUF: either a forging
attack or a cloning attack.
We write LCK-FORGE for the lockability security
under CPA or CCA which is described by the following
security game.
Set Up.
The challenger selects a manufacturing pro-
cess and initial parameters
param
. They generate
K ←$ KGen(1
λ
)
uniformly at random and compile
P ←$ Comp(K)
. They send
(1
λ
,param,P)
to the
adversary and initializes two counters c
0
,c
1
.
Learning 1. A
1
issues creation queries and response
queries. As in the unforgeability game, the
challenger creates
puf
c
0
← CREATE(param)
or
puf’
c
1
← CREATE(param’)
when receiving cre-
ation queries and sends
y
i, j
← puf
i
(x
j
)
or
y
i, j
←
puf
0
i
(x
j
) when receiving response queries.
A
1
outputs
(i
∗
,x
∗
,y
∗
)
and sends
(i
∗
,x
∗
)
to the chal-
lenger. The challenger evaluates y ← puf
i
∗
(x
∗
).
Learning 2. A
2
chooses
q
plaintexts and encrypts
them with
P
and
y
∗
. In the CCA model,
A
2
is-
sues decryption queries with
q
chosen ciphertexts
C
j
and gets M
j
← Dec(K,y,C
j
).
Challenge.
The challenger draws
M ←$ M \ {M
j
}
uniformly at random, computes
C ← Enc(K,y,M)
and sends M.
Guess. A
2
outputs C
∗
.
Definition 5
(LCK-FORGE)
.
Let
P
be a PUF class
with an intra-distance
δ
1
. Let
E
be the PUF-based
white-box encryption scheme. Let
Adv
lck−forge
A,E
(λ,δ
1
)
be the advantage of an adversary playing the
game above. We have
Adv
lck−forge
A,E
(λ,δ
1
) =
Pr
"
C
∗
= C : C
∗
← A
O
2
(1
λ
,r,P)
r=(i
∗
,x
∗
,y
∗
)←A
1
(1
λ
,param)
#
where
O
de-
notes the decryption oracle in the CCA model. A
PUF-based white-box encryption scheme
E
provides
SECRYPT 2020 - 17th International Conference on Security and Cryptography
282

(q
c
,q
r
,q,ε
0
)
-LCK-FORGE security if for any PPT ad-
versary A it holds that:
Adv
lck−forge
A,E
(λ,δ
1
) 6 ε
0
(λ).
In the above security game, the adversary is required
to output a PUF challenge
x
∗
for which they can forge
a valid output
y
∗
for an instance
puf
i
∗
. The second
learning phase allows the adversary to interact with a
decryption oracle (in the CCA model). If the attack
model for
A
2
is the CPA model, then in learning
2
,
A
2
is only allowed to choose at most
q
plaintexts and
to encrypt them with
P
and
y
∗
. For both models, the
adversary wins if
A
1
is able to forge a valid pair
(x
∗
,y
∗
)
for a chosen instance
i
∗
or if the pair returned by
A
1
is
not valid but A
2
guesses C.
Remark 1.
In the CCA model,
A
2
can compute
C
j
←
P(y
∗
,M
j
)
and send
C
j
to the decryption oracle. Thus,
A
2
is able to verify if the guess of
A
1
is correct. Other-
wise,
A
1
is allowed to restart the learning
1
and makes
a new guess. This way the attack model is adaptive.
However, the total number of queries made by
A
1
is
still bounded by
q
r
and
q
c
and the total number of
queries made by
A
2
is bounded by
q
. Consequently,
the advantage of the adversary regarding LCK-FORGE
is the same if the model is adaptive or not.
Theorem 1.
If the PUF class
P
provides
(q
c
,q
r
,δ
1
,ε)
-
EUF-CICA security then
E
provides
(q
c
,q
r
,q,ε
0
)
-LCK-
FORGE security with
• ε
0
: λ 7→
1 −
1
|
C
|
· ε(λ) +
1
|
C
|
for CPA.
• ε
0
: λ 7→
1 −
1
|
C
|
−q
· ε(λ) +
1
|
C
|
−q
for CCA.
Proof.
Let
E
be the event “
Adv
euf−cica
A
1
,P
(λ,δ
1
) > 0
”.
Adv
lck−forge
A,E
(λ,δ
1
) =
Pr [C
∗
= C
|
E ] × Pr [E ] + Pr
C
∗
= C
E
× Pr
E
Since
P
provides
(q
c
,q
r
,δ
1
,ε)
-EUF-CICA security
then
Pr [E ] 6 ε(λ)
and
Pr [C
∗
= C
|
E ] = 1
. This re-
flects the fact that once the PUF response is guessed
correctly, the adversary inevitably finds the correct ci-
phertext. Besides,
Pr
C
∗
= C
E
=
1
|
C
|
in the CPA
model and
Pr
C
∗
= C
E
=
1
|
C
|
−q
in the CCA model.
Adv
lck−forge
A,E
(λ,δ
1
) 6
1 −
1
|
C
|
· ε(λ) +
1
|
C
|
under CPA and,
Adv
lck−forge
A,E
(λ,δ
1
) 6
1 −
1
|
C
|
− q
· ε(λ) +
1
|
C
|
− q
under CCA.
The notion of lockability under cloning attack LCK-
CLONE expresses the situation in which we verify the
lockability except if the adversary exhibits two distinct
instances that have the same input-output behavior.
The security game for LCK-CLONE under CPA or CCA
is described as follows:
Set Up. The set up is the same as in LCK-FORGE.
Learning 1.
The learning phase is as in LCK-FORGE.
A
1
outputs (i
∗
,b, j
∗
).
Learning 2. A
2
chooses
q
plaintexts and challenges
and encrypts them with
P
. In the CCA model,
in addition
A
2
issues decryption queries with
q
chosen ciphertexts
C
j
and challenges
x
j
and gets
M
j
← Dec(K,y
j
,C
j
) where y
j
← puf
i
∗
(x
j
).
Challenge.
The challenger picks
M ←$ M \ {M
j
}
and
x ←$ X \ {x
j
}
uniformly at random, computes
C ← Enc(K,y,M)
where
y ← puf
i
∗
(x)
and sends
(M,x).
Guess. A
2
outputs C
∗
.
Definition 6.
Let
P
be a PUF class with an intra-
distance
δ
1
. Let
E
be the PUF-based white-
box encryption scheme. Let
Adv
lck−clone
A,E
(λ,δ
1
)
be the advantage of an adversary playing the
game above. We have
Adv
lck−clone
A,E
(λ,δ
1
) =
Pr
"
C
∗
= C : C
∗
← A
O
2
(1
λ
,r,P)
r=(i
∗
,b, j
∗
)←A
1
(1
λ
,param)
#
where
O
denotes
the decryption oracle in the CCA model. A PUF-based
white-box encryption scheme provides
(q
c
,q
r
,q,δ
1
,ε
0
)
-
LCK-CLONE security if for any PPT adversary
A
it
holds that: Adv
lck−clone
A,E
(λ,δ
1
) 6 ε
0
(λ).
Theorem 2.
If the PUF class
P
provides
(q
r
,q
c
,δ
1
,ε)
-
UUC-CICA security then the PUF-based white-box
encryption scheme provides
(q
c
,q
r
,q,δ
1
,ε
0
)
-LCK-
CLONE security with
• ε
0
: λ 7→
1 −
1
|
C
|
· ε(λ)
1/(
|
X
|
−q)
+
1
|
C
|
for CPA.
• ε
0
: λ 7→
1 −
1
|
C
|
−q
· ε(λ)
1/(
|
X
|
−q)
+
1
|
C
|
−q
for CCA.
Proof.
Let
E
be the event “
dist(puf
i
∗
(x),puf’
j
∗
(x)) 6
δ
1
”. Adv
lck−clone
A,E
(λ,δ
1
) =
Pr [C
∗
= C
|
E ] × Pr [E ] + Pr
C
∗
= C
E
× Pr
E
Since,
P
provides
(q
r
,q
c
,δ
1
,ε)
-UUC-CICA security
then
Pr [E ] 6 ε(λ)
1/(
|
X
|
−q)
and
Pr [C
∗
= C
|
E ] =
1
.
Pr
C
∗
= C
E
=
1
|
C
|
in the CPA model and
Pr
C
∗
= C
E
=
1
|
C
|
−q
in the CCA model. Hence,
Adv
lck−clone
A,E
(λ,δ
1
) 6
1 −
1
|
C
|
· ε(λ)
1
(
|
X
|
−q)
+
1
|
C
|
A White-Box Encryption Scheme using Physically Unclonable Functions
283

under CPA and,
Adv
lck−clone
A,E
(λ,δ
1
) 6
1 −
1
|
C
|
− q
· ε(λ)
1
(
|
X
|
−q)
+
1
|
C
|
− q
, under CCA.
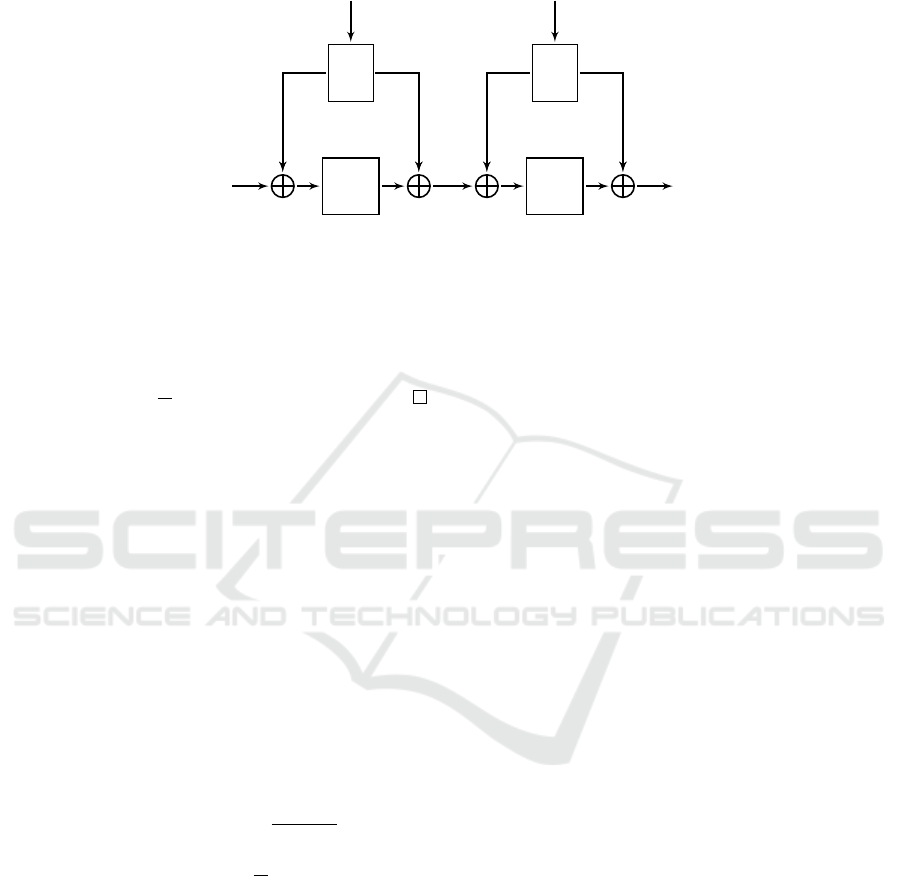
3.3 Construction of a PUF-based Block
Cipher
In this section, we provide one instantiation of the en-
cryption scheme using a tweakable block cipher. A
tweakable block cipher takes three inputs: the plain-
text, the secret key, and a public value called the tweak.
We refer to (Liskov et al., 2002) for more details. Thus,
it matches the Definition 3 when combined with a PUF
class. We use the
2
rounds Tweakable Even-Mansour
(
2
-TEM) of (Cogliati et al., 2015). This construction
applies an almost XOR universal (AXU) hash func-
tion to the tweak value. Since the tweak inputs are
noise-free PUF responses, they are obtained after a
recovery procedure. Thereby, the hash function takes
a noise-free but non-uniform input
y
and transforms it
to a nearly uniform value xored with the plaintext.
PES with 2 Rounds of TEM.
Let
P = {puf : X →
Y }
be a PUF class. Let
H = {H
K
: Y → F
n
2
}
K∈K
be
a family of
ρ
1
-uniform and
ρ
2
-AXU hash functions in-
dexed by a set of keys
K
. Let
Enc : K × Y ×F
n
2
→ F
n
2
be a
2
-TEM block cipher (see Figure 1). For any key
K = (K
1
,K
2
)
,
H
K
1
,H
K
2
are two hash functions of the
family
H
and
P
1
,P
2
are two public permutations. For
any PUF response
y ∈ Y
corresponding to a challenge
x ∈ X
, the encryption function is defined, for any plain-
text M ∈ F
n
2
, by
Enc(K,y,M) = P
2
(P
1
(M ⊕ H
K
1
(y)) ⊕ H
K
1
(y)
⊕ H
K
2
(y)) ⊕ H
K
2
(y).
In the same way, the decryption function is defined for
any ciphertext C ∈ F
n
2
by
Dec(K,y,C) = P
−1
1
(P
−1
2
(C ⊕ H
K
2
(y))
⊕ H
K
2
(y) ⊕ H
K
1
(y)) ⊕ H
K
1
(y).
We denote by
2
-TEM
(P ) = (F
2n
2
,F
n
2
,F
n
2
,Enc,Dec,P )
the constructed PES.
Keyed Hash Functions.
We construct the following
family of keyed hash functions:
Definition 7.
Let
E : F
n
2
× F
n
2
→ F
n
2
be a block cipher.
Let
H = {H
K
: (F
n
2
)
2
→ F
n
2
}
K∈F
n
2
be a family of hash
functions indexed by a set of keys where any hash
function
H
K
is defined as follows: for any
x = (x
1
,x
2
)
,
H
K
(x) = E
K
(x
1
) ⊕ E
K
2
(x
2
)
with
K
2
= K ⊗ K
is a mul-
tiplication in the finite field F
2
n
.
Remark 2.
The function
K 7→ K
2
is a permutation in
F
2
n
, thus E
K
2
is a permutation.
We show that the above family of hash functions is
almost uniform and XOR universal.
Definition 8.
Let
E : F
n
2
×: F
n
2
→ F
n
2
be an
r
rounds
iterative block cipher and let
F
i
K
i
be the
i
-th round
function with a round key
K
i
derived from a master key
K.
•
A differential characteristic is a sequence of
r + 1
differences
(∆
0
,...,∆
r
)
where
∆
0
is the difference
between two inputs and
∆
r
is the output difference.
•
For a key
K
, the fixed-key differential characteristic
probability
π
K
is the probability for a pair of inputs
to follow a given differential characteristic:
π
K
= Pr
X
h
F
i
K
i
(X) ⊕ F
i
K
i
(X ⊕∆
0
) = ∆
i
,1 6 i 6 r
i
.
•
The expected differential characteristic probabil-
ity
π
is the differential characteristic probability
averaged over all round keys:
π = Pr
X,K
h
F
i
K
i
(X) ⊕ F
i
K
i
(X ⊕∆
0
) = ∆
i
,1 6 i 6 r
i
= E
K
[π
K
].
Let
Π
denotes an upper bound on the expected differ-
ential characteristic probability of the block cipher
E
introduced in Definition 7.
Theorem 3.
The family of Definition 7 is
34
2
n
-uniform
and Π-AXU.
Proof.
We first prove the XOR universality. Let
x 6=
x
0
∈ (F
n
2
)
2
and
b ∈ F
n
2
. Without loss of generality,
we assume that
x
1
6= x
0
1
. Otherwise, interchange the
subscript
1
with the subscript
2
in the following. Let
A = {K ∈ F
n
2
: H
K
(x) ⊕ H
K
(x
0
) = b}, we have:
Pr
K
H
K
(x) ⊕ H
K
(x
0
) = b
=
|
A
|
2
n
with
|
A
|
=
{K,K
2
: E
K
(x
1
) ⊕ E
K
2
(x
2
) ⊕ E
K
(x
0
1
) ⊕ E
K
2
(x
0
2
) = b}
=
|
B
|
, with
|
B
|
=
∑
K
2
|
{K : E
K
(x
1
) ⊕ E
K
(x
0
1
) = b ⊕ E
K
2
(x
2
) ⊕ E
K
2
(x
0
2
)}
|
Since
|
{K ∈ F
n
2
: E
K
(x
1
) ⊕ E
K
(x
1
⊕ a) = b
0
|
6 Π · 2
n
for any
b
0
∈ F
n
2
and
K 7→ K
2
is a bijection then
|
A
|
6 Π · 2
n
.
Now, we prove that the family
H
is
34
2
n
-uniform.
Let
x ∈ (F
n
2
)
2
and
y ∈ F
n
2
. We compute the cardinal-
ity of
A = {K ∈ K : H
K
(x) = E
K
(x
1
) ⊕ E
K
2
(x
2
) = y}
given
x = (x
1
,x
2
)
and
y
. As the probability of pick-
ing randomly a key is equal to 1/2
n
, it means that the
number of keys verifying properties of
A
follows a
Poisson distribution with parameter
λ = 1
as it could
SECRYPT 2020 - 17th International Conference on Security and Cryptography
284
H
K
1
H
K
2
y ← puf(x) y ← puf(x)
PUF response PUF response
M
P
1
P
2
C
R
1
R
1
R
2
R
2
Figure 1: TEM(P ) construction with 2 rounds and PUF responses as tweak inputs.
be considered as a sum of Bernoulli events with a very
low probability. Thus, it corresponds with the mod-
elling of the law of rare events. For
n = 128
, we obtain
an upper bound equal to 34 for the cardinal of
A
di-
rectly applying the density of the Poisson law. Thus,
Pr
K
[H
K
(x) = y] 6
34
2
n
.
Remark 3
(Estimation of the Probability when
K
is
Fixed.)
.
In the white-box setting, the key
K
is fixed.
Consequently, we need to estimate the XOR univer-
sality for a fixed key
K
.
Π
is an upper bound on
the expected differential characteristic probability of
the block cipher
E
over all keys. When a key
K
is
fixed, we consider the fixed-key differential character-
istic probability
π
K
which is the probability that an
input pair
(x,x ⊕ a)
fulfills a differential characteristic
(∆
0
= a,∆
1
,...,∆
r
= b).
Let
N(a,b) =
|
{x : E
K
(x) ⊕ E
K
(x ⊕ a) = b}
|
, i.e.
N(a,b)
is the number of pairs
(x,x
0
)
that fulfill the
differential characteristic
(∆
0
= a,∆
1
,...,∆
r
= b)
for
a fixed key
K
. Let
q
B
be the probability that all non
trivial characteristics are fulfilled by at most
B
in-
put pairs, i.e.
q
B
= Pr
a,b
a6=0
[N(a,b) 6 B]
. According to
(Blondeau et al., 2013):
q
B
> 1 −
Π
B
2
(n−1)B
(B+1)!
2
2n
. Hence,
for a fixed key
K
: if
q
B
u 1
then
N(a,b) 6 B
, and
Pr
x
[E
K
(x) ⊕ E
K
(x ⊕ a) = b] 6
B
2
n
.
White-Box Implementation of 2-TEM(P).
We use
the
8
-bit instantiation of SPNbox (Bogdanov et al.,
2016) as block cipher
E
. SPNbox-
8
operates on
t = 16
blocks of
m = 8
bits and applies
R = 10
rounds of the
following transformations:
•
A substitution
γ: F
16
2
8
→ F
16
2
8
applies a S-box
S
to
each block as follows:
γ(X) = (S(X
0
),...,S(X
15
))
.
•
A linear transformation
θ: F
16
2
8
→ F
16
2
8
multi-
plies the state
(X
0
,...,X
15
)
by a Maximum Dis-
tance Separable matrix as follows:
θ(X) =
(X
0
,...,X
15
) · M
8
where:
M
8
= had(0x08,0x16,0x8a,0x01,0x70,
0x8d,0x24,0x76,0xa8,0x91,0xad,0x48,
0x05,0xb5,0xaf,0xf8)
is an Hadamard-Cauchy matrix.
•
A round-dependent transformation
σ
r
: F
16
2
8
→ F
16
2
8
adds a round-dependent constant to the state as fol-
lows:
σ
r
(X) = (X
0
⊕C
r
0
,...,X
15
⊕C
r
15
)
for
C
r
i
=
(r − 1) ·t + i + 1.
For any key
K
the S-box of the substitution layer is
computed as follows: for any
8
-bit input
X
, encrypt
X
with a small-scale variant of the AES cipher using
K
as a master key and expanded using the SHAKE
key derivation function. The variant of the AES cipher
is composed of
64
rounds of the following transfor-
mations: SubBytes, AddRoundKey and MixColumns.
The SubBytes transformation is composed of only one
AES S-box and the Mixcolumns transformation applies
the identity matrix to the state. If the S-box is pre-
computed and implemented by a lookup table then
SPNbox-8 satisfies the unbreakability security.
Since
K = (K
1
,K
2
)
and
2
-TEM
(P )
needs four
block cipher calls, the white-box implementation
makes use of four pre-computed S-boxes with
K
1
,K
2
1
,K
2
, and K
2
2
.
White-Box Security.
The PWE satisfies the UBK-
ATK security, for
ATK ∈ {CPA,CCA}
because of the
unbreakability of SPNbox-
8
. Regarding the lockabil-
ity security, it is guaranteed by the unforgeability and
unclonability of the PUF instance. Hence, a tight esti-
mation of the security bounds for a specific PUF class
is necessary to get the security bounds for lockability.
A White-Box Encryption Scheme using Physically Unclonable Functions
285

3.4 Application
Our scheme is designed for exchange of encrypted
data between a trusted server and a client on a mo-
bile device. The server and the client share a secret
key for the encryption: the client is given a white-box
program with a fixed key. In addition, if a secure
2
PUF exists on the client’s device, it is used to rein-
force the security of the white-box program. Because
of the uniqueness of a PUF instance, an enrollment
phase is needed to “characterize” it. In other words,
the trusted server stores some challenge-response pairs
corresponding to the PUF thanks to an evaluation pro-
gram SECURE.EVAL executed on the client device.
Such an enrollment phase is used for PUF-based au-
thentication. During the enrollment, some helper data
are computed to enable the client to recover the en-
rolled responses from noisy ones. A helper data is
computed by a SECURE.SKETCH procedure and stored
by the server. It is a public side information that en-
ables one to recover a string
y
from any noisy but
close enough
y
0
. Assume that the server sends some
encrypted data to the client and the client needs to
decrypt them. The server randomly picks a pair of
challenge-response and encrypts the data using the
shared key and the PUF response. Then the server
sends the ciphertext together with the challenge and
the helper data to the client. The client evaluates the
PUF instance on the challenge and gets a noisy re-
sponse. Thanks to a recovery procedure REC and the
helper data, the client recovers the correct response
and decrypts the ciphertext. We refer to (Dodis et al.,
2008) for precise definitions of a secure sketch and a
recovery procedure for noisy data.
REFERENCES
Armknecht, F., Moriyama, D., Sadeghi, A., and Yung, M.
(2016). Towards a unified security model for physically
unclonable functions. In Topics in Cryptology - CT-
RSA 2016 - The Cryptographers’ Track at the RSA
Conference 2016, volume 9610 of Lecture Notes in
Computer Science, pages 271–287. Springer.
Biryukov, A., Bouillaguet, C., and Khovratovich, D. (2014).
Cryptographic schemes based on the ASASA structure:
Black-box, white-box, and public-key (extended ab-
stract). In Advances in Cryptology - ASIACRYPT 2014
- 20th International Conference on the Theory and
Application of Cryptology and Information Security,
volume 8873 of Lecture Notes in Computer Science,
pages 63–84. Springer.
Blondeau, C., Bogdanov, A., and Leander, G. (2013).
Bounds in shallows and in miseries. In Advances in
Cryptology - CRYPTO 2013 - 33rd Annual Cryptology
2
Unpredictable and unclonable.
Conference, volume 8042 of Lecture Notes in Com-
puter Science, pages 204–221. Springer.
Bogdanov, A. and Isobe, T. (2015). White-box cryptogra-
phy revisited: Space-hard ciphers. In Proceedings of
the 22nd ACM SIGSAC Conference on Computer and
Communications Security, pages 1058–1069. ACM.
Bogdanov, A., Isobe, T., and Tischhauser, E. (2016). To-
wards practical whitebox cryptography: Optimizing
efficiency and space hardness. In Advances in Cryptol-
ogy - ASIACRYPT 2016, Proceedings, Part I, volume
10031 of LNCS, pages 126–158.
Cho, J., Choi, K. Y., Dinur, I., Dunkelman, O., Keller, N.,
Moon, D., and Veidberg, A. (2017). WEM: A new
family of white-box block ciphers based on the even-
mansour construction. In Topics in Cryptology - CT-
RSA 2017 - The Cryptographers’ Track at the RSA
Conference 2017, volume 10159 of Lecture Notes in
Computer Science, pages 293–308. Springer.
Chow, S., Eisen, P. A., Johnson, H., and van Oorschot, P. C.
(2002a). White-box cryptography and an AES imple-
mentation. In Selected Areas in Cryptography - SAC
2002, volume 2595 of Lecture Notes in Computer Sci-
ence, pages 250–270. Springer.
Chow, S., Eisen, P. A., Johnson, H., and van Oorschot, P. C.
(2002b). A white-box DES implementation for DRM
applications. In Security and Privacy in Digital Rights
Management, ACM CCS-9 Workshop, DRM 2002, vol-
ume 2696 of Lecture Notes in Computer Science, pages
1–15. Springer.
Cogliati, B., Lampe, R., and Seurin, Y. (2015). Tweaking
even-mansour ciphers. In Advances in Cryptology -
CRYPTO 2015, volume 9215 of LNCS, pages 189–208.
Springer Berlin Heidelberg.
Delerabl
´
ee, C., Lepoint, T., Paillier, P., and Rivain, M. (2013).
White-box security notions for symmetric encryption
schemes. In Selected Areas in Cryptography - SAC
2013, volume 8282 of Lecture Notes in Computer Sci-
ence, pages 247–264. Springer.
Dodis, Y., Ostrovsky, R., Reyzin, L., and Smith, A. D. (2008).
Fuzzy extractors: How to generate strong keys from
biometrics and other noisy data. SIAM J. Comput.,
38(1):97–139.
Fouque, P., Karpman, P., Kirchner, P., and Minaud, B. (2016).
Efficient and provable white-box primitives. In Ad-
vances in Cryptology - ASIACRYPT 2016 - Proceed-
ings, Part I, volume 10031 of LNCS, pages 159–188.
Liskov, M. D., Rivest, R. L., and Wagner, D. A. (2002).
Tweakable block ciphers. In Advances in Cryptology -
CRYPTO 2002, 22nd Annual International Cryptology
Conference, volume 2442 of Lecture Notes in Com-
puter Science, pages 31–46. Springer.
Maes, R. (2012). Physically Unclonable Functions: Con-
structions, Properties and Applications. PhD thesis,
Katholieke Universiteit Leuven - Faculty of Engineer-
ing.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
286
