
cipherPath: Efficient Traversals over Homomorphically Encrypted Paths
Georg Bramm
a
and Julian Sch
¨
utte
b
Fraunhofer AISEC, Lichtenbergstrasse 11, Garching near Munich, Germany
Keywords:
Somewhat Homomorphic Encryption, Structured Encryption, Order Preserving Encryption,
Geospatial Encryption, Dijkstra, Floyd, Shortest Path.
Abstract:
We propose cipherPath, a novel graph encryption scheme that enables exact shortest distance queries on
encrypted graphs. Shortest distance queries are very useful in a vast number of applications, including medical,
social or geospatial. Our approach using somewhat homomorphic encryption in combination with structured
encryption enables exact shortest distance queries on outsourced and encrypted graph data. Our approach
upholds provable security against a semi-honest provider. We demonstrate our framework by means of two
different shortest path algorithms on encrypted graphs: Dijkstra and Floyd. Finally, we evaluate the leakage
profile of cipherPath.
1 INTRODUCTION
Nowadays service online map service providers tend
to offer public and free services in order to be able
to collect data from users trusting such a service. A
very prominent example is Google Maps. While of-
fering routing and shortest path services, they collect
various information about your request. By collect-
ing and aggregating those requests, an attacker might
be able to identify your work or home place. Us-
ing cipherPath, we enable users to query such ser-
vices without revealing the precise location. In or-
der to achieve this, various new cryptographic tech-
niques have been combined like structured encryption
(SE), order preserving encryption (OPE) and some-
what homomorphic encryption (SHE). Utilizing these
techniques, we can provide confidentiality for users in
location-based services against an honest-but-curious
provider. We want users being able to calculate short-
est paths in real world applications without giving up
their privacy concerns. We therefore present cipher-
Path, a new shortest path query processing algorithm
over encrypted graphs in unstructured databases. Our
algorithm guarantees the confidentiality of both the
encrypted graph data and the query history against
an honest-but-curious provider. To this end, we pro-
pose a structured encryption scheme utilizing some-
what homomorphic order preserving ciphertexts. Our
contribution can be summarized as follows:
a
https://orcid.org/0000-0002-9020-5856
b
https://orcid.org/0000-0002-3007-6538
• We devise an interactive, yet very efficient SHE-
OPE scheme, capable of adding, subtracting, mul-
tiplying, dividing, and comparing encrypted num-
bers.
• We present a generic framework of protocols for
the generation, outsourcing and computation on
an encrypted graph.
• We apply our framework to implement a classic
shortest path finding technique by Dijkstra.
• We evaluate and discuss the information leakage
of our framework.
After introducing some preliminaries we present our
OPE-SHE scheme ehOPE in section 2. Building
upon eHOPE, we introduce our framework cipher-
Path in section 3. After presenting a secure protocol
for path finding in section 4, we discuss the leakage
of our construction in section 5 and conclude in sec-
tion 6.
2 FOUNDATION AND
EXTENSIONS
We give a description of our notation and foundational
preliminaries for this paper, followed by an introduc-
tion into ehOPE, an OPE-SHE scheme used in our
framework.
Bramm, G. and Schütte, J.
cipherPath: Efficient Traversals over Homomorphically Encrypted Paths.
DOI: 10.5220/0009777802710278
In Proceedings of the 17th International Joint Conference on e-Business and Telecommunications (ICETE 2020) - SECRYPT, pages 271-278
ISBN: 978-989-758-446-6
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
271

2.1 Notation
[n] donates the set of integers from zero up to n. A
graph G = (V,E) consists of a set of vertices V and
a set of edges E =
{
(i, j)
}
where i, j ∈ V . Any edge
e = (i, j) with i, j /∈ V is called ∞ and is represented
by randomly chosen integer values from a range that
is invalid in the respective application domain
1
.
2.1.1 Distance Norm
As a distance metric we use the L
1
2
norm on en-
crypted nodes, as it requires less computational and
interaction overhead, compared to the L
2
norm. For a
real number p ≥ 1, the p-norm or L
p
distance norm of
is defined by
k
x
k
p
= (|x
1
|
p
+ |x
2
|
p
+ · ·· + |x
n
|
p
)
1/p
.
When we calculate the L
p
distance d between the two
nodes a and b, we write d = L
p
(a,b). When we calcu-
late the L
1
distance between a node b and the starting
node, then we abbreviate this by writing d = dist(b).
2.2 Cryptographic Preliminaries
We now introduce all necessary cryptographic prelim-
inaries.
2.2.1 Pairing
Our work is partly based on the notion of bilinear
pairing maps: suppose G is an additive cyclic group
and H is a multiplicative cyclic group, both of the
same order q. A bilinear pairing map ˆe : G × G → H
satisfies the following properties:
• Bilinearity, i.e. for any P,Q ∈ G and any a,b ∈ Z
∗
q
,
we have ˆe(P
a
,Q
b
) = ˆe(P
b
,Q
a
) = ˆe(P,Q)
ab
.
• Non-degeneracy, which means that there exists a
P, Q ∈ G, such that ˆe(P,Q) 6= I ∈ H, where I is
the identity element.
• Computable, which means that for any P,Q ∈
G, there exists an efficient algorithm to compute
ˆe(P,Q) ∈ H.
2.2.2 Induced Permutation
Let π be the permutation over [n] such that ∀i ∈
[n],m
i
= Dec
K
c
π(i)
, then we refer to π as the per-
mutation induced by m and c. Accordingly, we re-
fer to Φ as the permutation induced by M and C,
if Φ is the permutation over [λ
1
] × [λ
2
] such that
1
For earth-bound navigation applications an integer in
the interval ]40075000,2
31
− 1] cloud be used, which is the
earth’s radius in meter and Integer max value.
2
Sometimes also called Manhattan distance
∀(i, j) ∈ [λ
1
] × [λ
2
],M
(i, j)
= Dec
K
C
Φ(i, j)
. By in-
ducing a pseudorandom permutation between m and
c our construction is able to hide parts of the access
pattern, as (Chase and Kamara, 2010) describe.
2.2.3 Somewhat Homomorphic Encryption
Besides hiding the structure of the graph we also need
to hide the sequence of data values along a path from
the server while doing calculations on it. We there-
fore integrated Pailliers scheme together with the El-
Gamal scheme into our own adoption of hOPE origi-
nally written by (Peng et al., 2017).
Paillier. The Paillier scheme (Paillier, 1999) allows
additive homomorphic operations on ciphertexts in
a probabilistic asymmetric encryption scheme. The
scheme can be modified to allow signed values and
subtraction by reducing the range of m to −
n
4
< m <
n
4
. The modified Paillier cryptosystem has the follow-
ing properties:
• Addition: The product of two ciphertexts ct
1
=
E
k
(m
1
) and ct
2
= E
k
(m
2
) results in the encryp-
tion of the sum of their plaintexts: (ct
1
× ct
1
)
mod n
2
= E
k
(m
1
+ m
1
)
• Subtraction: The product of a ciphertext ct
1
=
E
k
(m
1
) with the modular inverse of another ci-
phertext ct
2
= E
k
(m
2
) computed modulo n
2
re-
sults in the encryption of the subtraction of their
plaintexts: (ct
1
× ct
−1
1
) mod n
2
= E
k
(m
1
− m
1
)
• Constant multiplication: The b
th
power of ci-
phertext ct
1
= E
k
(m
1
) results in the encryption of
the product of b and m
1
: E
k
(m
1
× b) = E
k
(m
1
)
b
mod n
2
• Semantic security: The generated ciphertexts are
non-deterministic.
ElGamal. In 1985 Taher ElGamal published a
schme with multiplicative homomorphic properties
(ElGamal, 1985). Besides multiplication, ElGamal
also allows division by multiplying with the modu-
lar inverse. As (Lipmaa, 2010) state, the ElGamal
cryptosystem is IND − CCA1 and has the following
properties:
• Multiplication: The product of two ciphertexts
ct
1
= E
k
(m
1
) and ct
2
= E
k
(m
2
) results in the en-
cryption of the product of their plaintexts: (ct
1
×
ct
1
) = E
k
(m
1
· m
1
).
• Division: The product of a ciphertext
ct
1
= E
k
(m
1
) with the multiplicative inverse
of another ciphertext ct
2
= E
k
(m
2
) results in the
encryption of the division of their plaintexts:
ct
1
ct
2
=
ct
1
· (ct
2
)
−1
= E
k
(
m
1
m
2
)
SECRYPT 2020 - 17th International Conference on Security and Cryptography
272

• Semantic security: The generated ciphertexts are
non-deterministic.
2.3 homomorphic Order Preserving
Encryption (hOPE)
A new technique called hOPE was introduced by
(Peng et al., 2017). The authors combine Pailliers
scheme with an OPE approach based on a B
+
code
tree. In cipherPath we need to compute additions,
subtractions, multiplications, as well as inequality
tests, so we extend hOPE by also incorporating El-
Gamal. The additional interactivity with the client in
our scheme is needed when translating values from
one SHE to the other, like in Add(SP,L
1
,L
2
) (5). The
encrypted value is given to the client, who decrypts it
using K, encrypts it into the opposite SHE scheme and
uploads it again to the server. We achieve the same
mathematical expressiveness as the Peng’s PhOPE,
but without integrating a fully homomorphic encryp-
tion (FHE) scheme. Instead we integrate two SHE
schemes. Our construction ehOPE is given by:
Select a bilinear pairing e : G × G → H with the
order q ∈ Z
∗
for G and H. Pick an additive
∏
+
= (Gen,Enc,Dec,Add,Sub) and a multiplicative SHE
scheme
∏
∗
= (Gen, Enc,Dec,Mul). Then ehOPE =
(Setup,Gen,Enc, Dec,Add,Sub, MulDiv,Comp) is defined
by:
Gen(): Generate key pairs for both SHE schemes
EK
+
,DK
+
←
∏
+
Gen
(1
k
) and.
{
EK
∗
,DK
∗
}
←
∏
∗
Gen
(1
k
) and return them as key pair {SK, PK}, with
SK =
DK
+
,DK
∗
and PK =
EK
+
,EK
∗
.
Enc(SP, EK, m): Ciphertext CT = hp,e,G,H, oi is ob-
tained as follows:
(1) Using EK compute p =
∏
+
Enc
(m), e =
∏
∗
Enc
(m), G =
m · P ∈ G and H = ˆe(P,P)
m
∈ H.
(2) Look up L
i
= hp
i
,e
i
,G
i
,H
i
,o
i
i in L by matching G
or H. If found, skip to (3); otherwise skip to (4).
(3) Return CT = L
i
= hp
i
,e
i
,G
i
,H
i
,o
i
i, where G
i
= G
or H
i
= H. The process is now terminated.
(4) o is determined using an interactive code location al-
gorithm based on tree T .
(5) Insert L = hp, e,G, H,oi into the cache L, and insert
c into T . Then update both and go to (2).
Add(SP, L
1
, L
2
): Take as input SP, L
1
=
hp
1
,e
1
,G
1
,H
1
,o
1
i and L
2
= hp
2
,e
2
,G
2
,H
2
,o
2
i.
The sum L = L
1
+ L
2
is generated as follows:
(1) Compute p = p
1
+ p
2
, G = G
1
+ G
2
and H =
ˆe(G,P).
(2) Look up L
i
= hp
i
,e
i
,G
i
,H
i
,o
i
i in L by matching G
or p. If found, skip to (3); otherwise, skip to (4).
(3) ,(4) Same as in Enc (3) and Enc (4).
(5) ask client to translate p to e, i.e. calculate e =
∏
∗
Enc
(
∏
+
Dec
(p)).
(6) Same as in Enc (5).
Sub(SP, L
1
, L
2
): Take as input SP, L
1
= hp
1
,e
1
,G
1
,H
1
,o
1
i
and L
2
= hp
2
,e
2
,G
2
,H
2
,o
2
i. The subtraction L = L
1
−
L
2
is generated as follows:
(1) Compute p = p
1
− p
2
, G = G
1
+ (G
2
)
−1
and H =
ˆe(G,P).
(2) Look up L
i
= hp
i
,e
i
,G
i
,H
i
,o
i
i in L by matching G
or H. If found, skip to (3); otherwise, skip to (4).
(3) ,(4) Same as in Enc (3) and Enc (4).
(5) ask client to translate p to e, i.e. calculate e =
∏
∗
Enc
(
∏
+
Dec
(p)).
(6) Same as in Enc (5).
Mul(SP,L
1
, L
2
): Take as input SP, L
1
= hp
1
,e
1
,G
1
,H
1
,o
1
i
and L
2
= hp
2
,e
2
,G
2
,H
2
,o
2
i. The multiplication L =
L
1
· L
2
is generated as follows:
(1) Compute e = e
1
· e
2
and H = ˆe(G
1
,G
2
).
(2) Look up L
i
= hp
i
,e
i
,G
i
,H
i
,o
i
i in L by matching H.
If found, skip to (3); otherwise, skip to (4).
(3) ,(4) Same as in Enc (3) and Enc (4).
(5) Ask client to compute G =
∏
∗
Dec
(e) · P and translate
p =
∏
+
Enc
(
∏
∗
Dec
(e)).
(6) Same as in Enc (5).
Div(SP,L
1
, L
2
): Take as input SP, L
1
= hp
1
,e
1
,G
1
,H
1
,o
1
i
and L
2
= hp
2
,e
2
,G
2
,H
2
,o
2
i. The division L =
L
1
L
2
is
generated as follows:
(1) Compute e = e
1
· e
−1
2
and H = ˆe(G
1
,G
2
)
−1
.
(2) Look up L
i
= hp
i
,e
i
,G
i
,H
i
,o
i
i in L by matching H.
If found, skip to (3); otherwise, skip to (4).
(3) ,(4) Same as in Enc (3) and Enc (4).
(5) Ask client to compute G =
∏
∗
Dec
(e) · P and translate
p =
∏
+
Enc
(
∏
∗
Dec
(e)).
(6) Same as in Enc (5).
COMP(L
1
, L
2
): Take as input L
1
and L
2
. Output the result
of the binary comparison o
1
and o
2
. Return 0 if they
are equal. Returns 1 if L
1
≥ L
2
or −1 if L
1
≤ L
2
.
Dec(DK, L
1
): Take as input L
1
= hp
1
,e
1
,G
1
,H
1
,o
1
i. Out-
put m =
∏
+
Dec
(p
1
).
The security analysis for hOPE is given by (Peng
et al., 2017). As long as we pick at least IND −
O2CPA secure SHE schemes, our modified scheme
upholds the same security features as the FHE ver-
sion, with the disadvantage of more interactivity and
the advantage of a higher efficiency.
2.4 Related Work
Searchable encryption was initially introduced by
(Song et al., 2000). They propose a novel, provably
secure scheme that enables searching on encrypted
data without decrypting it. Their technique is based
on a stream cipher. Many secure searchable encryp-
tion schemes followed like (Curtmola et al., 2011),
(Cash et al., 2014) or (Bost, 2016). The schemes
were mainly focusing on text based queries. (Meng
et al., 2015) proposed GRECS, a encrypted graph
scheme that supported very efficient, but only approx-
imate, shortest distance queries. It was a big step
forward, but parts of the calculation, the intermedi-
ate distance matching, is still calculated on the client
side. Distances were precalculated and only approx-
imate. Other approaches to calculate paths on en-
crypted graphs include attempts to use secure multi-
party computation (SMC), like (Failla, 2010). In this
scenario two parties try to find the shortest path in a
cipherPath: Efficient Traversals over Homomorphically Encrypted Paths
273

privacy preserving way. One party knows the weights
on the edges of the graph, the other party knows an
heuristic to find the best path and together they try
to solve the quest. As each party must have infor-
mation about the graph or the heuristic, before any
query is sent, this approach is not comparable to ours.
In 2015, (Samanthula et al., 2015) also tried to ap-
proach this problem by applying SHE to adjacency
lists, instead of a adjacency matrix as in our case. An-
other huge difference in their approach is the calcu-
lation of path subsets on the client side, instead of
the server side. (Chase and Kamara, 2010) showed
a novel way to construct a scheme that was taking
care not only of the data values, but the structure
of the adjacency matrix as well. The structured en-
cryption scheme showed a way how to efficiently and
privately query encrypted graphs, while at the same
time keeping the data and the structure hidden. Struc-
tured encryption, which generalizes previous work on
symmetric searchable encryption (SSE) to the setting
of arbitrarily-structured data is, besides ehOPE, is a
foundational building block of this paper.
3 FRAMEWORK
Our framework cipherPath is based on multiple mod-
ifications of the associative structured encryption
scheme for labeled data by Chase. It was modified
in order to incorporate SHE operations on ciphertexts
instead of simple symmetrically encrypted cipher-
texts. Besides changes in the token and lookup algo-
rithms, the replacement of symmetrically encrypted
ciphertexts with ehOPE ciphertexts is a fundamental
change. This allows us to keep path lengths confiden-
tial, while still being able to compute on them.
3.1 Scheme Setting
The intention of our work is to keep the graph, the
shortest path queries as well as the results hidden from
an attacker. If some client itself holds the entire graph,
he could run various path searching algorithms lo-
cally, way faster. But this implies that he holds all the
necessary resources, including the graph data as well
as the computational power. In a setting with mul-
tiple mobile lightweight clients, like smartphones or
tablets, we advise the following procedure: A honest
but curious provider sets up the scheme and generates
SP using cipherPath.Setup. Afterwards the provider
makes SP publicly available. A trusted entity gener-
ate a single key K using cipherPath.Gen and encrypts
the routing graph G regularly using cipherPath.Enc.
The trusted entity uploads the generated CT regularly
to the provider. The trusted entity gives out key K to
multiple, eligible users over a secure channel. The el-
igible users generate queries Q
i
using K and SP and
query the scheme using Di j(Q
i
). Finally the eligible
users can decrypt the routing result locally using K.In
such a setting the query leakage is kept low by reg-
ularly renewing CT and thus rendering older leakage
useless. The users are able to query the system effi-
ciently and their privacy concerns is taken care of.
3.2 Information Model
We need a way to not only store our permutated and
encrypted edges, but also information on the permu-
tated and encrypted nodes. Therefore we use the en-
crypted edge matrix C and an encrypted node vec-
tor D. The message space of our main framework
takes as input a matrix M and a set of nodes N
together with two sequence m and n consisting of
((x
1
,l
1
),. ..,(x
n
,l
n
)), with a data item x
i
and a label
l
i
. In case of m, a data item is composed of an identi-
fier and a length. In case of n, a data item is composed
of an identifier and a coordinate composed of a longi-
tude and latitude value.
3.3 Scheme Architecture
In order to enable queries for both edges and nodes,
we adopted the corresponding algorithms that are ei-
ther index based (T
I
) or label based (T
L
). Likewise,
lookup algorithms are also available for both types of
token requests. In a real world location-based sce-
nario, we are dealing with two different kinds of arith-
metic data in a navigation graph, namely node coor-
dinates, composed of longitude and latitude values,
given as double precision floating point values on the
one hand and edge lengths in meters or minutes as
integer values on the other hand. As there is no rea-
son to compare lengths and coordinates, we decided
to include in our framework two ehOPE schemes for
each data type.ehOPE
R
for floating point values and
ehOPE
Z
for integer values.
3.3.1 Setup
This algorithm runs once on the provider side and
generates the system parameters (SP) for the ehOPE
schemes depending on security parameter k. Setup is
run by the provider, as he has to sets up cache L and
code tree T . The random value of P might also be
chosen by the client, but this is irrelevant, as SP is
public knowledge.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
274
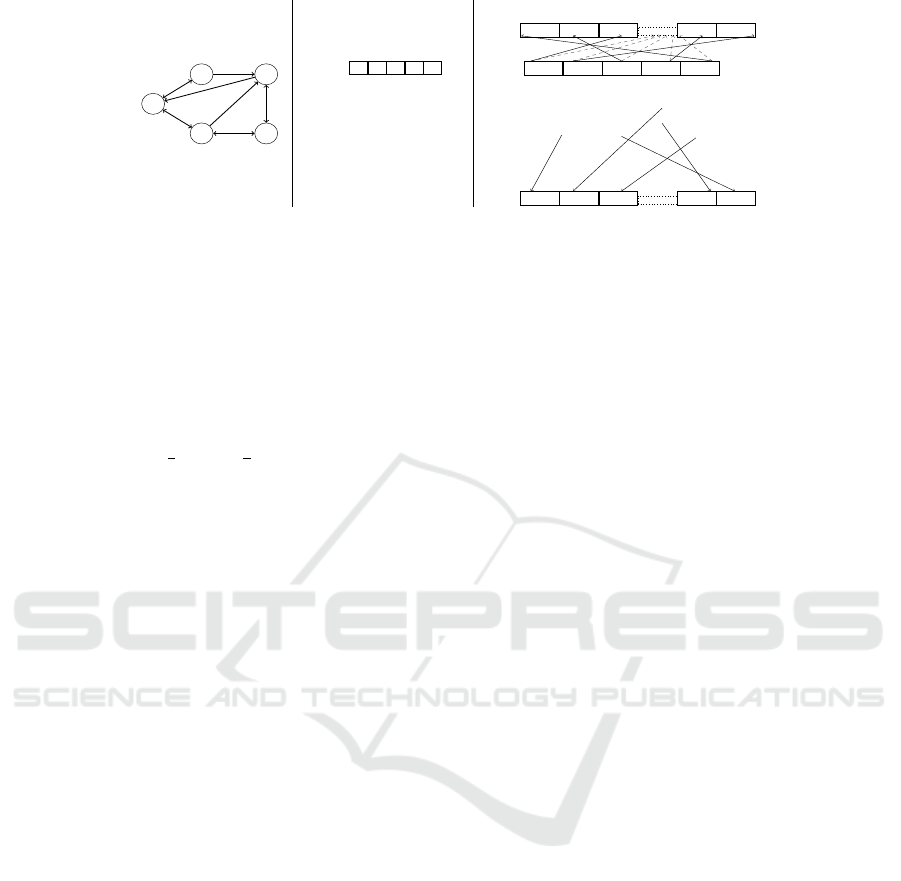
n
2
n
3
n
4
n
0
n
1
1
2
3
5
6
7
8
N =
M =
0 1 2 3 4
n
0
n
1
n
2
n
3
n
4
0 2 ∞ 7 8
2 0 5 ∞ ∞
∞ 5 0 1 ∞
∞ 6 ∞ 0 3
8 ∞ ∞ 3 0
D =
d =
C =
c =
H
K
2
(n
4
) H
K
2
(n
1
) H
K
2
(n
3
) H
K
2
(n
2
) H
K
2
(n
0
)
Π
R
.E(l o
0
) Π
R
.E(l o
3
) Π
R
.E(l o
4
) ... Π
R
.E(l a
2
) Π
R
.E(l a
1
)
H
K
2
(e
24
) H
K
2
(e
20
) H
K
2
(e
23
) H
K
2
(e
22
) H
K
2
(e
21
)
H
K
2
(e
9
) H
K
2
(e
5
) H
K
2
(e
8
) H
K
2
(e
7
) H
K
2
(e
6
)
H
K
2
(e
19
) H
K
2
(e
15
) H
K
2
(e
18
) H
K
2
(e
17
) H
K
2
(e
16
)
H
K
2
(e
14
) H
K
2
(e
10
) H
K
2
(e
13
) H
K
2
(e
12
) H
K
2
(e
11
)
H
K
2
(e
4
) H
K
2
(e
0
) H
K
2
(e
3
) H
K
2
(e
2
) H
K
2
(e
1
)
Π
Z
.E(∞) Π
Z
.E(∞) Π
Z
.E(8) ... Π
Z
.E(5) Π
Z
.E(0)
Figure 1: A graphical representation of steps (1), (3) and (4) during the encryption of a graph in cipherPath.
3.3.2 Key Generation
While SP is public knowledge, K must be kept secret.
K is composed of K
1
, the controlled disclosure key, K
2
the permutation key, and K
3
,K
4
the object keys. The
key K is used to encrypt a graph at the client side, as
well as to decrypt single object values, i.e. lengths or
coordinates. As mentioned in section 2.2.3, the range
of m is reduced to −
k
4
< m <
k
4
.
3.3.3 Encryption
Encryption in cipherPath means to encrypt and per-
mutate edges and nodes of a graph in such a way
that only L
Enc
and L
Query
will be leaked to the server.
Further information about the graph, the query shell
be hidden from the provider completely. The length
of an edge is encrypted using an ehOPE scheme re-
sponsible for integer values called Π
Z
and is linked
to an permutated entry in C, as in the algorithm
cipherPath.Enc(SP, K,M,N) step (3). The longi-
tude (lo) and latitude (la) values are encrypted using
Π
R
.Enc a second floating point instance of ehOPE.
Nodes are then linked to two permutated entries in D
for the lo and la value, as can be seen in step (4).
Note, that permutation Q of vector D and permutation
P of matrix D result in the same arrangement, when
comparing the order of the vector to the order of the
rows. Finally all ciphertext elements, matrix C and
its values c
i
as well as vector D and its values d
i
are
returned as ciphertext (CT ).
3.3.4 Token
In a real world scenario no one will know the exact
index of a specific edge or node of a graph, whilst
street (edge) or building (node) names are easy to re-
member. Therefore we introduce a trapdoor T
L
for
label based searches. By embedding an object identi-
fier together with a hashed and row- and column-wise
encrypted label inside the matrix C we are able to in-
dex all edges. The node vector also embeds two iden-
tifiers (lo,la) together with a hashed and index-wise
encrypted label in D.
3.3.5 Lookup
In the lookup algorithms we parse the index (T
I
) or
label based (T
L
) token calculate the pointer i to the
correct position in c respectively d. Afterwards we
return the pointer together with the object ciphertext
(
{
CT
i
,i
}
). This behavior can be seen in Figure 2. The
matrix C and the vector D can be thought of a kind
of a searchable encrypted index with pointers to the
corresponding data items c
i
and d
i
.
3.3.6 Decryption
To decrypt c
i
or d
i
the client utilizes the corresponding
decrypt functions Dec
Z
(SP,K, c
i
) for integer values or
Dec
R
(SP,K, d
i
) for floating point values.
4 SHORTEST PATH
The shortest path problem is sometimes also called
single-source shortest path problem (SSSP), to dis-
tinguish it from other variations like the single-
destination shortest path (SDSP) or the all-pairs short-
est path problem (APSP). Before we inspect (Dijkstra
et al., 1959) on cipherPath, we want to make clear that
it is also possible to take the APSP approach, for ex-
ample using (Floyd, 1962) on cipherPath. Additional
sets d for distances, p for predecessors as well as Q
are needed to run the algorithm by Dijkstra, as can be
seen in Figure 3. First of all the label based trapdoors
for start (1) and end (2) need to be looked up. After an
initialization of d (1,3), p (3,4) and Q (4) we look for
the shortest path of the current node to another node u
(4.a) until we reached our target (4.b) or there are no
more nodes left (4).
Otherwise we inspect each neighbor of u by ask-
ing the client to disclose the u
th
row in CT.C (5.c.I)
and looking up the corresponding lengths (5.c.II).
Using the disclosed information we are able to run
update (5.c.III). As we are proceeding to disclose
nodes on the path between T
S
L
and T
T
L
, we are leak-
ing information that is helping the attacker.
cipherPath: Efficient Traversals over Homomorphically Encrypted Paths
275

Let H :
{
0,1
}
k
×
{
0,1
}
∗
→
{
0,1
}
h
and F :
{
0,1
}
k
×
{
0,1
}
∗
→
{
0,1
}
k
be pseudo-random func-
tions, Q :
{
0,1
}
k
× [n] → [n] and P :
{
0,1
}
k
× [λ
1
] × [λ
2
] → Q (K,[λ
1
]) × Q
K
−1
,[λ
2
]
be pseudo-
random permutations and let Π
Z
= (Setup,Gen,Enc,Dec,Add, Sub,Mul,Comp) be an ehOPE
Z
and Π
R
=
(Setup,Gen, Enc,Dec,Add,Sub, Mul,Comp) be an ehOPE
R
encryption scheme. Our encrypted shortest path
framework cipherPath = (Setup,Gen, Enc,Token
I
,Token
L
,Lookup
I
,Lookup
L
,Dec) is then defined as follows:
{SP} ← Setup(1
k
,h): Setup both ehOPE schemes
{
SP
}
←
Π
R
.Setup(1
k
),Π
Z
.Setup(1
k
),h, h
1
,h
2
with k be-
ing the security parameter and h = h
1
+,h
2
(with h
1
and h
2
being the bit length of pointers to d and c) Return
the SP.
{K} ← Gen(SP): generate two random k-bit strings K
1
,K
2
and key K
3
= (EK, DK) ← Π
R
.Gen() and K
4
=
(EK,DK) ← Π
Z
.Gen(). Output K = (K
1
,K
2
,K
3
,K
4
).
{CT } ← Enc(SP, K,M,N): Construct ciphertext CT as follows:
(1) Parse the edge matrix M as m with label l
m
and parse the node vector N as n with label l
n
.
(2) Choose a k-bit random key K
4
.
(3) Generate matrix C and vector c by:
(a) Choose a pseudo-random permutation G :
{
0,1
}
k
× [m] → [m].
(b) Generate a λ
1
× λ
2
matrix C as follows:
∀(α,β) ∈ [λ
1
] × [λ
2
]: store hG
K
4
(i),H
K
2
(l
i
)i ⊕ F
K
1
(α,β) where i = M
α,β
at (α
0
,β
0
) = P
K
2
(α,β) in C.
(c) If M
α,β
=⊥, then hG
K
4
(i),H
K
2
(l
i
)i is replaced with a random, large enough value h∞,H
K
2
(∞)i.
(d) ∀(i) ∈ [m]: Let j = G
K
4
(i) and set c
i
← Π
Z
.Enc
K
3
(m
j
).
(4) Generate index vector D of length n and data vector d of length 2n:
(a) Choose a pseudo-random permutation I :
{
0,1
}
k
× [n] → [n].
(b) Generate vector D of length n as follows:
∀(i) ∈ [n]: store hI
K
4
(i),I
K
4
(i + n),H
K
2
(l
i
)i ⊕ F
K
1
(i) at location n
0
= Q
K
2
(i) in D
(c) Generate vector d of length 2n as follows:
∀(i) ∈ [n]: Let j = I
K
4
(i) and set d
i
← Π
R
.Enc
K
3
(n
lo
i
).
∀(i) ∈ [n]: Let j = I
K
4
(i + n) and set d
j
← Π
R
.Enc
K
3
(n
la
i
).
(5) Output CT =
{
C, c, D,d
}
.
{T
L
} ← Token
L
(SP,K, l): generate ∀(i) ∈ [n]: set t
i
= h0,0,H
K
2
(l)i ⊕ F
K
1
(i). Output T
L
=
{
t
0
,t
1
,. ..,t
n
}
.
{T
L
} ← Token
L
(SP,K, l): generate ∀(α,β) ∈ [λ
1
] × [λ
2
]: set t
i
= h0, 0,H
K
2
(l)i ⊕ F
K
1
(α,β). Output T
L
=
{
t
0
,t
1
,. ..,t
m
}
.
{T
I
} ← Token
I
(SP,K, α,β): output T
I
= (s,α
0
,β
0
), where s = F
K
1
(α,β) and (α
0
,β
0
) = P
K
2
(α,β).
{T
I
} ← Token
I
(SP,K, α): output T
I
= (s,α
0
,⊥), where s = F
K
1
(α) and α
0
= Q
K
2
(α).
{CT
∗
,i} ← Lookup
I
(SP,CT,T
I
): parse T
I
as (s,α
0
,β
0
);
(1) If β
0
==⊥, this is a node token:
compute i = (s ⊕CT .D
α
0
) (h
2
+ h
1
) and j = (s ⊕CT .D
α
0
) h
1
and output
{
CT .d
i
,i
}
,
CT .d
j
, j
.
(2) If there is a β
0
value, compute j =
s ⊕CT .C
α
0
,β
0
h and output
CT .c
j
, j
.
{CT
∗
,i} ← Lookup
L
(SP,CT,T
L
): parse T
L
as (t
0
,t
1
,. ..t
x
);
(1) If x == n, this is a node lookup. Compute ∀(i) ∈ [n]:
(a) compute h = CT .D
i
(k − h).
(b) if h == (t
i
(k − h)) compute j = (t
i
⊕CT .D
i
) (h
2
+ h
1
) and k = (t
i
⊕CT .D
i
) h
1
and output
i,
CT .c
j
, j
,
{
CT .c
k
,k
}
.
(c) Otherwise there is no node. output
{
⊥,⊥
}
.
(2) Otherwise this is an edge lookup. Compute ∀(i) ∈ [m]:
(a) compute α
0
= (i mod n) and β
0
= b
i
n
c
(b) compute h = CT .C
α
0
,β
0
(k − h).
(c) if h == t
i
(k − h): compute j =
t
i
⊕CT .C
α
0
,β
0
h and output
CT .c
j
, j
.
{PT
lo
V
,PT
la
V
} ← Dec
R
(SP,K,CT
V
): Decrypt vertex coordinates PT
lo
V
= Π
R
.Dec
K
3
CT
lo
V
and PT
la
V
=
Π
R
.Dec
K
3
(CT
a
V
).
{PT
E
} ← Dec
Z
(SP,K,CT
E
): Decrypt edge length CT
E
using Π
Z
.Dec
K
4
(CT
E
).
Figure 2: Steps Setup, Gen, Enc, Token, Lookup, Dec of our encrypted geospatial framework.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
276

(CT
Z
1
,n
1
),.. .,(CT
Z
T
,n
T
)
← Di j(SP,CT,T
S
L
,T
T
L
):
(1)
CT
T
,s
= cipherPath.Lookup
I
(SP,CT,T
S
L
),
d[s] = 0.
(2)
CT
S
,t
= cipherPath.Lookup
I
(SP,CT,T
T
L
).
(3) ∀n ∈ CT.D \
{
s,t
}
:
d[n] = ∞. p[n] =⊥. add n to Q.
(4) While Q 6=
/
0:
(a) u ← min
q∈p
(Q).
(b) If u == t return p[].
(c) Otherwise remove u from Q and
(I) disclose T = {T
1
I
,.. .,T
n
I
} ← ∀i ∈ [n] :
cipherPath.Token
I
(SP,K, u,i).
(II) CT =
CT
0
,i
0
,.. .,
{
CT
n
,i
n
}
← ∀i ∈ T :
cipherPath.Lookup
I
(SP,CT,T
i
I
).
(III) ∀i
0,...,n
∈ CT : I f n
i
∈ Q :
a ← Π
Z
.Add(SP,d[u],dist(u,v))
If Π
Z
.Comp(a,d[v]) == −1: Set d[v] := a and
p[v] := u.
Figure 3: Dijkstra based on cipherPath.
5 LEAKAGE
We now present our simulation-based security def-
inition against malicious adversaries. Please recall
the definition of (L
Enc
,L
Query
) −CQA2 security. In
a CQA2 attack, we assume that the adversary is al-
lowed to make multiple adaptive queries to the data
structure. We seek to guarantee that the adversary
can only learn what was accessed and the result of
the query. All other information is to be kept secret.
Theorem 5.1.
Let Λ = (Setup,Gen,Enc,Token
∗
,Lookup
∗
,Dec
∗
) be
an cipherPath scheme for message space m, query
space q, result space r and the query F : m × q → r.
Consider the following two experiments for the leak-
age functions L
Enc
and L
Query
, adversary A, chal-
lenger C, and simulator S:
Real
Λ
A,C
(λ): C begins by running Λ.Gen(1
λ
) to gener-
ate K. A outputs a graph G. C runs Λ.Enc(K, G)
to generate CT . Afterwards he sends CT to A. A
adaptively makes a polynomial number of Dijk-
stra queries q
0
,. ..,q
t
. For each query q
i
, A inter-
acts with C. C plays the part of the client in the
protocol with input (K,q
i
) and sends its output to
A. Finally, A outputs a bit b.
Ideal
Λ
A,C,S
(λ): Initially, A outputs graph G. S is given
L
Enc
(G), and outputs CT . A adaptively makes a
polynomial number of queries q
0
,. ..,q
t
. For each
query q
i
, S is given L
Query
(m,q
0
,. ..,q
i
) and inter-
acts with A. S produces a flag f ; i f f =
/
0 ,the chal-
lenger sends
/
0 to A, otherwise it sends F(m,q
i
).
Finally, A outputs a bit b.
We say that Λ is (L
Enc
,L
Query
)−CQA2 secure against
malicious adversaries if, for all PPT adversaries A,
there exists a simulator S such that:
|Pr[Real
Λ
A,C
(λ) = 1] − Pr[Ideal
Λ
A,C,S
(λ) = 1]| ≤ negl(λ)
The information that is leaked about the message
m is given by L
Enc
(m) and is analyzed in subsec-
tion 5.1. The shortest path query also leaks informa-
tion, which is given by L
Query
(m,q
0
,. ..,q
n
). It do-
nates the leakage of L
Enc
(m) in combination with all
executed queries from (q
0
) up to now (q
n
). This be-
havior is analyzed in subsection 5.2.
5.1 Leakage Analysis of Encryption
The encryption leakage L
Enc
of our construction out-
puts (N,O
1D
(CT.d),O
1D
(CT.c)), which is defined
by:
• the total number of encrypted nodes N = |d| in the
underlying graph G.
• the 1D order of all edges by length, given as
O
1D
(CT.c) = Ord
1D
(c
x
< ... < c
y
).
• the 1D order of all coordinate values lo and la ,
given as O
1D
(CT.d) = Ord
1D
(d
x
< ... < d
y
).
The order of all values of Π
Z
and Π
R
is leaked on the
server, but as long as the server is not able to correlate
those values to nodes or edges we are safe.
5.2 Leakage Analysis for Queries
The probability to reconstruct G is higher, when ad-
ditional leakage by the query algorithms can be corre-
lated to leaked information by L
Enc
(G). As Dijkstra
and Floyd both intentionally leak the 2D as well as
the path pattern, including the L
1
distance between
multiple nodes along the path, an honest but curi-
ous adversary could collect this information to fur-
ther refine his knowledge about the plaintext graph
G. The query leakage L
Query
of our construction gives
(s,O
2D
(n),e), which is defined by:
• the length pattern s, which is the number of edges
and nodes between the start and the target node.
• the 2D order of all nodes n along
a path P, given as by O
2D
(n) =
Ord
2D
(
{
n
S
,. ..,n
T
}
) = Ord
1D
n
lo
S
< ... < n
lo
T
×
Ord
1D
n
la
S
< ... < n
la
T
. This is leaked, because
the server is now able to correlate the 2D order of
nodes along P by their lo and la order.
• the edge pattern e along a path P , which allows an
attacker to link the 1D order of edges to specific
nodes. This information helps the attacker to even
further refine his information about G.
As there is no frequency in Π
+
and Π
∗
, we leak the
ideal profile according to (Durak et al., 2016). The
order of the coordinates may be abused to reconstruct
G in a 2-D sort attack. By the metrics of (Naveed
cipherPath: Efficient Traversals over Homomorphically Encrypted Paths
277

et al., 2015), such an attack does not work a hundred
percent, yet it is obvious that much of the structural
behavior is revealed, including relatively fine details
like the density of points in specific areas of the graph.
In order to prevent such an attack, we can restrict the
number of nodes. As CT is only used for routing and
not display purposes, we can reduce the attack vec-
tor by limiting the number of encrypted nodes, while
parsing an OSM map. This can be done by throw-
ing away unnecessary intermediate nodes, for exam-
ple nodes with a degree ≤ 2.
6 CONCLUSION
We presented cipherPath: Efficient Traversals over
Homomorphically Encrypted Paths, a framework for
the computation of the shortest path in an encrypted
graph. We showed how to construct our framework
based on cryptographic preliminaries and how find
the shortest paths between encrypted nodes. Finally
we analyzed the security and the leakage of our con-
struction. A future direction might be the defense
against more sophisticated graph similarity attacks,
like the neural network approach given by (Bai et al.,
2018). Our goal is to find an upper barrier on the num-
ber of nodes, from which on neural network attacks
become feasible. Another direction of research might
be the sharding of a CT into multiple subsets spread
accross multiple provider.
ACKNOWLEDGEMENTS
This work has been funded by the Fraunhofer Cluster
of Excellence ’Cognitive Internet Technologies’
3
.
REFERENCES
Bai, Y., Ding, H., Sun, Y., and Wang, W. (2018). Convolu-
tional set matching for graph similarity. arXiv preprint
arXiv:1810.10866.
Bost, R. (2016).
∑
oϕoς: Forward secure searchable en-
cryption. In Proceedings of the 2016 ACM SIGSAC
Conference on Computer and Communications Secu-
rity, pages 1143–1154.
Cash, D., Jaeger, J., Jarecki, S., Jutla, C. S., Krawczyk, H.,
Rosu, M.-C., and Steiner, M. (2014). Dynamic search-
able encryption in very-large databases: data struc-
tures and implementation. In NDSS, volume 14, pages
23–26. Citeseer.
3
https://www.cit.fraunhofer.de
Chase, M. and Kamara, S. (2010). Structured encryption
and controlled disclosure. In International Conference
on the Theory and Application of Cryptology and In-
formation Security, pages 577–594. Springer.
Curtmola, R., Garay, J., Kamara, S., and Ostrovsky, R.
(2011). Searchable symmetric encryption: improved
definitions and efficient constructions. Journal of
Computer Security, 19(5):895–934.
Dijkstra, E. W. et al. (1959). A note on two problems
in connexion with graphs. Numerische mathematik,
1(1):269–271.
Durak, F. B., DuBuisson, T. M., and Cash, D. (2016). What
else is revealed by order-revealing encryption? In
Proceedings of the 2016 ACM SIGSAC Conference
on Computer and Communications Security, pages
1155–1166.
ElGamal, T. (1985). A public key cryptosystem and a signa-
ture scheme based on discrete logarithms. IEEE trans-
actions on information theory, 31(4):469–472.
Failla, P. (2010). Heuristic search in encrypted graphs.
In 2010 Fourth International Conference on Emerg-
ing Security Information, Systems and Technologies,
pages 82–87. IEEE.
Floyd, R. W. (1962). Algorithm 97: shortest path. Commu-
nications of the ACM, 5(6):345.
Lipmaa, H. (2010). On the cca1-security of elgamal and
damg
˚
ard’s elgamal. In International Conference on
Information Security and Cryptology, pages 18–35.
Springer.
Meng, X., Kamara, S., Nissim, K., and Kollios, G. (2015).
Grecs: Graph encryption for approximate shortest
distance queries. In Proceedings of the 22nd ACM
SIGSAC Conference on Computer and Communica-
tions Security, pages 504–517. ACM.
Naveed, M., Kamara, S., and Wright, C. V. (2015).
Inference attacks on property-preserving encrypted
databases. In Proceedings of the 22nd ACM SIGSAC
Conference on Computer and Communications Secu-
rity, pages 644–655.
Paillier, P. (1999). Public-key cryptosystems based on com-
posite degree residuosity classes. In International
conference on the theory and applications of crypto-
graphic techniques, pages 223–238. Springer.
Peng, Y., Li, H., Cui, J., Zhang, J., Ma, J., and Peng,
C. (2017). hope: improved order preserving en-
cryption with the power to homomorphic operations
of ciphertexts. Science China Information Sciences,
60(6):062101.
Samanthula, B. K., Rao, F.-Y., Bertino, E., and Yi, X.
(2015). Privacy-preserving protocols for shortest path
discovery over outsourced encrypted graph data. In
2015 IEEE International Conference on Information
Reuse and Integration, pages 427–434. IEEE.
Song, D. X., Wagner, D., and Perrig, A. (2000). Practical
techniques for searches on encrypted data. In Pro-
ceeding 2000 IEEE Symposium on Security and Pri-
vacy. S&P 2000, pages 44–55. IEEE.
SECRYPT 2020 - 17th International Conference on Security and Cryptography
278
