
Overview of Enterprise IoT Security System based on Edge
Computing
Liyun Lan, Jiujun Bai and Xuebo Chen
a
School of Electronic and Information Engineering, University of Science and Technology Liaoning,
Qianshan road, Anshan 114051, Liaoning, China
Keywords: Internet of Things, Edge Computing, Enterprise Security System.
Abstract: The topic of security runs through the development of human society, and it exists in all aspects of our lives
and work. In order to better ensure the safety of the employees in enterprises, the enterprise IoT security
system should be established. With the development of technology, the application of IoT in enterprise
security has made some progress. Since more and more devices are connected to the Internet and generate big
data, cloud computing is no longer sufficient to process and analyse IoT devices in real time. Especially the
data is generated by different digital platforms involving enterprise production, management and safety.
Therefore, edge computing can be taken into account. This paper briefly introduces the development status
of Internet of Things technology and edge computing technology comparing with cloud computing. It should
be helpful for us that edge computing is proposed to apply to enterprise IoT security system.
1 INTRODUCTION
The process of production in the enterprise is
complex, the operation line is long and it has strong
continuity. During the production process, it not only
has the characteristics of high temperature, high
pressure and high energy, but also involves the toxic,
harmful, flammable and explosive substances in the
production process. Meanwhile, there is also the
hidden danger of mechanical injuries such as high-
rise buildings, mechanical processing and so on,
which are prone to fall from high places and objects
to strike (Wang Shuming, 2016, Pan Zhixing, 2015).
With the acceleration of China's modernization
process, enterprises have developed at a high speed,
but at the same time, the probability of serious
accidents such as fires, explosions, poisonings, and
leakages has also increased year by year. Starting
from the regularity of accidents, effective early
warning of accident symptoms has become an
important way to reduce accident losses (Xu
Yangguang, Chen Xuebo, Sun Qiubai, 2017).
With the increasing progress of technology, there
have been many cases of Internet of Things (IoT)
applied to enterprise security. However, because
a
https://orcid.org/0000-0001-6799-7667
more and more devices are connected to the Internet
and generate data, cloud computing is no longer
sufficient to process and analyze data generated or to
be generated by IoT devices and other digital
platforms in real time, especially in the case of safe
production in enterprises. In order to make up for the
shortcomings of both the amount of data and the
transmission rate of cloud computing in the security
system, so that it can process the received data faster
and more efficiently, it is necessary to "sink" some
functions of cloud computing. Edge computing came
into being at the historic moment.
2 IoT TECHNOLOGY RELATED
RESEARCH
This section summarizes the development and
application research of IoT technology.
2.1 Development History of Internet of
Things Technology
The Internet of Things originated in the 1990s. In the
early 1990s, the MIT Auto-ID Laboratory set the
Lan, L., Bai, J. and Chen, X.
Overview of Enterprise IoT Security System based on Edge Computing.
DOI: 10.5220/0009407103210326
In Proceedings of the 5th International Conference on Internet of Things, Big Data and Security (IoTBDS 2020), pages 321-326
ISBN: 978-989-758-426-8
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
321

Electronic Coding Standard (EPC). The designation
of this standard makes the radio frequency
identification technology (RFID) more widely used in
various fields. Build an EPC real-time tracking
information system based on the EPC standard, which
can virtually connect objects to the Internet (Liu
Qibiao, Chen Zhiming, 2015, Gui Jinsong, 2013). In
1995, Bill Gates first proposed the rudiment of the
Internet of Things concept connected by "thing to
thing", which is the idea of interconnection. And it is
also known as the "Internet of Things" in English
(Bill Gates book, 1996). In 1998, the Massachusetts
Institute of Technology put forward the concept of the
Internet of Things. In the same year, the Automatic
Identification Center put forward the preliminary
concept of the Internet of Things. At the WSIS
Information World Summit in 2005, the International
Telecommunication Union formally proposed the
concept of the "Internet of Things" in its report (ITU
Internet Reports, 2005), stating that the Internet of
Things includes the networking and application of all
items.
Since its inception, the Internet of Things has
sustained innovation and strong impetus, and its
applications involve defense military (Furtak, J.,
Zielinski, Z., Chudzikiewicz, J., 2016,Wang J, Jiang
F, Xie C, 2012), intelligent transportation (Zhang G
W., 2013), smart grid (Zeng Li, Xu Xin, Zeng Dajun,
2017, Yang W, Peng Z, Yu H, et al, 2013, Liu B W,
Zhou H, 2013), smart home, medical and health (Li
Cuijin, 2017, Liu Qibiao, Chen Zhiming, 2015) and
many other fields. It played an active role in them.
2.2 The Application Status of Internet
of Things Technology
Sun Qibo et al. summarized the key technologies
which are involved in the Internet of things and
proposed the technology system model of the Internet
of things (Sun Qibo, Liu Jie, Li Li Li, Fan Chunxiao,
Sun Juanjuan, 2010). The architecture system of the
Internet of things technology is shown in figure 1.
Yan Tao and Lv Limin applied the Internet of things
technology to the enterprise safety production
monitoring system, and elaborated the design process
from the aspects of the Internet of things architecture,
the overall design of the security monitoring system,
and the realization of functions (Yan Tao, Lv Limin,
2012). Literature (Chen Xuebo, sun Qiubai, 2015)
established the framework of the behavioral safety
management system consisting of people, things and
environment, and established an early warning
system for unsafe behaviors to dynamically track and
monitor human behaviors by utilizing the Internet of
things technology, complex system theory and
behavioral safety management method. Liu Zude and
Li Pengfei proposed to apply the Internet of things
technology to the accident early warning system of
metallurgical enterprises, and proposed the basic
framework of the enterprise accident early warning
system based on the Internet of things architecture,
(Liu Zude, Li Pengfei, 2015). Based on the existing
traditional video monitoring, the paper (Su Huo, Liu
Xiaodong, 2016) used OpenCV visual library and
C++ to realize face recognition, and implemented the
judgment of suspicious persons in the prohibited area.
Literature (Zhang Li, 2013) used video analysis
technology and Internet of things technology to
develop an intelligent video monitoring system with
multiple functions including area invasion, object
detection, smoke detection, direction and path
detection of moving objects. In literature (Zhang Yi,
2010, Wang Yucheng, 2016), intelligent video
recognition algorithm was studied in depth to
improve the feature extraction algorithm of moving
target detection. It also defined the abnormal
behavior, recognized the behavior of moving objects,
and rose them to the height of the event. Literature
(Hu Dongtao, 2014, Qin Jianwang, 2012)
respectively established a set of underground mine
behavior safety monitoring and warning system based
on Internet of things technology. The real-time
dynamic detection subsystem was established to
collect personnel positioning information and
underground mine environment information in real
time. Ground monitoring subsystem was built to
analyze online information and warn timely. And it
also designed personnel location, environment
detection terminal software, hardware, and ground
hand-held security information query terminal
equipment. The above researches are the applications
of Internet of things technology in video recognition,
and the algorithm and model are given in detail.
However, they are only one part of the whole
enterprise security system, which needs to consider
other subsystem.
In literature (Sun, E., Zhang, X., & Li, Z.,
2012), the monitoring and early warning system
(TDMPAS) of tailing dam based on Internet of
things and cloud computing was realized, and the
system structure of the early warning system was
given to realize the real-time monitoring of
saturation line, stagnant water level and dam
deformation of tailing dam. In literature (Wu, Y.,
Chen, M., Wang, K., & Fu, G., 2019), the
underground dynamic information platform of coal
mine based on Internet of things
technology was
established. The platform was divided into six
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
322

functional layers: support layer, perception layer,
transmission layer, service layer, data extraction layer
and application layer. This platform can monitor and
record the working condition data of coal mine
production system, as well as the location information
of underground equipment and miners. Based on
cloud computing technology, it can quickly analyze
the big data related to underground coal mines and
accurately extract the key data related to users' needs.
Literature (Chen, L. R. Cao, J. F., 2018) described the
architecture and key technologies of industrial
Internet of things. Literature (2017) introduced
outliers detection and spatiotemporal statistical
analysis based on cluster analysis. It also presented a
real-time monitoring, event reporting and early
warning platform based on RSS distance weighted
centroid localization algorithm. The platform used the
Internet of things, cloud computing, real-time
operation database, application gateway and
application program interface to seamlessly integrate
the monitoring, analysis and localization methods. In
literature (Dong, L.J., Shu, W.W., Sun, D.Y., Li, X.B.,
Zhang, L.Y., 2017), a multiple key information
system of tailing pond was constructed based on the
Internet of things and wireless network, and also
utilizing the sensor data including the stability
indicators such as diving line, reservoir water level,
internal and external deformation of tailing pond. The
basic system was given and the simulation analysis
was carried out. In reference (Bo, C., Xin, C.,
Zhongyi, Z., Chengwen, Z., & Junliang, C, 2014), a
remote monitoring system was proposed based on the
Internet of things, which made full use of wireless
sensor network and combined with CAN bus
communication technology to abstract the data and
capabilities of underground sensors into WoT
resources, and services were provided through
representational state transfer (REST). The above
researches are all based on the applications of Internet
of things technology in enterprises, such as
metallurgical enterprises, underground mines, etc.,
but they are all about the framework research, lacking
in-depth study of specific models and algorithms.
3 RESEARCH ON EDGE
COMPUTING TECHNOLOGY
In 2004, Pang (PANG H H, TAN K L, 2004)
proposed edge computing in the open literature for
the first time in the 20th IEEE International
Conference. It mentioned that "Edge computing is to
implement extensible and highly available web
services, which will promote the logic and data
processing center of the enterprise to the edge side of
proxy services. Its advantage is that the operation of
applications on the edge side reduces network latency
and produces faster web service response". Shi
Weisong and others systematically introduced the
concept and principle of edge computing. It
instantiated the concept of edge computing through
existing cases as well (Shi Weisong, Sun Hui, Cao
Jie, Zhang Quan, Liu Wei, 2017). Edge computing
refers to a distributed open platform that integrates
the core capabilities of network, computing, storage
and applications on the edge of the network close to
the object or data source to provide edge intelligent
services nearby (SHI W S, CAO J, ZHANG Q, et al,
2016, HU Y C, PATEL M, SABELLA D, et al, 2015).
Reference (Li Linzhe, Zhou Peilei, Cheng Peng, Shi
Zhiguo, 2019) introduced the concept and general
architecture of edge computing. Its general
architecture is shown in Figure 2, which introduces
the application of edge computing. The general
architecture of edge computing is divided into three
layers , that is terminal layer, edge computing layer
and cloud computing layer. Each layer can
communicate with each other and across layers. The
composition of each layer determines the computing
and storage capacity of each layer, and thus it
determines the functions of each layer.
(1) Terminal layer
The terminal layer is composed of various Internet of
things devices such as sensors, RFID tags, cameras,
smart phones and the like, which mainly completes
the function of collecting original data and reporting.
In the terminal layer, only the perception ability of
various IOT devices is considered, but not their
computing ability. Billions of Internet of things
devices in the terminal layer continuously collect all
kinds of data, taking the form of event source as the
input of application services.
(2) Edge computing layer
Edge computing layer is composed of network edge
nodes, which are widely distributed between terminal
equipment and computing center. It can be intelligent
terminal equipment itself, such as smart bracelet,
smart camera, etc., or it can be deployed in network
connection, such as gateway, router and so on.
Obviously, the computing and storage resources of
the edge node are quite different, and the resources of
the edge node are dynamic. For example, the
available resources of the intelligent bracelet are
dynamic with the use of people. Therefore, how to
allocate and schedule computing tasks in dynamic
network topology is worth studying. The edge
computing layer realizes the basic service response by
Overview of Enterprise IoT Security System based on Edge Computing
323
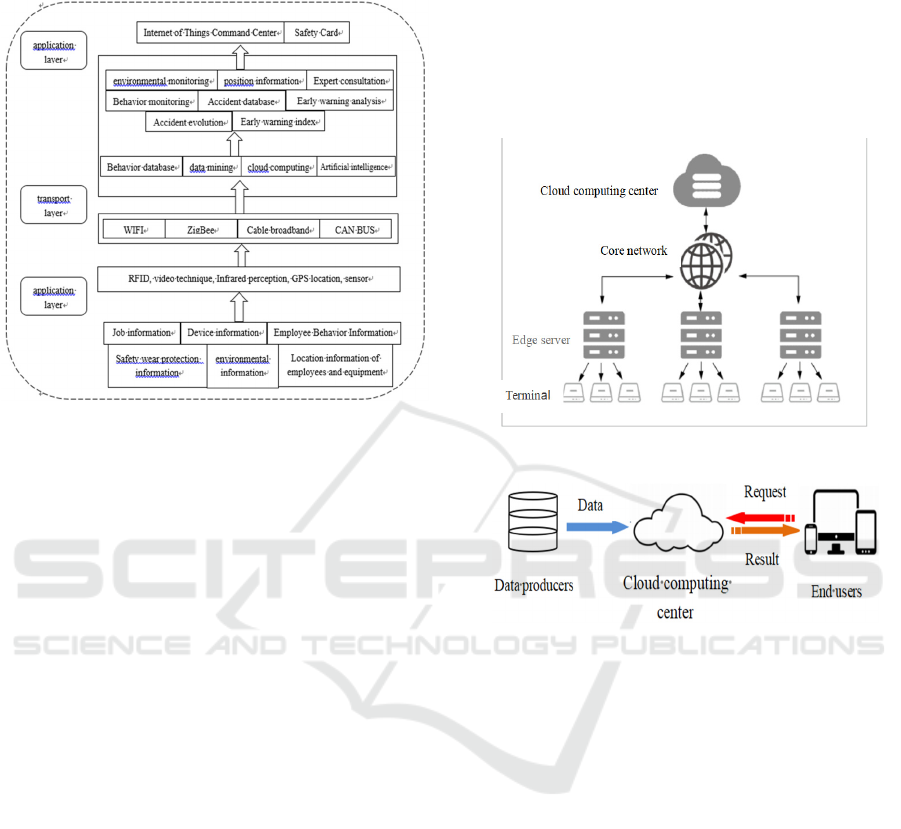
reasonably deploying and deploying the computing
and storage capabilities on the edge of the network.
Figure 1: Basic structure of enterprise safety system based
on Internet of Things.
(3) Cloud computing layer
In the joint services of cloud edge computing, cloud
computing is still the most powerful data processing
center. The reported data of the edge computing layer
will be stored permanently in the cloud computing
center. The analysis tasks and comprehensive global
information processing tasks that cannot be processed
by the edge computing layer still need to be
completed in the cloud Computing Center. In
addition, cloud computing center can dynamically
adjust the deployment strategy and algorithm of edge
computing layer according to the distribution of
network resources.
In reference (Qi Bing, Xia Yan, Li Bin, Shi Kun,
Xue Mingfeng, 2018), a family energy system
framework based on edge computing was proposed, a
four-tier architecture based on data fusion and
operation collaboration between heterogeneous
platforms was designed, and detailed design schemes
of several common subsystems were given, which
provides new ideas for the application of edge
computing technology in the field of intelligent
energy use. Reference (An Xingshuo, Cao Guixing,
Miao Li, Ren Shubo, Lin Fuhong, 2018) introduced
the basic concept, system architecture and the
relationship with other computing paradigms of edge
computing, analyzed the security threats existing in
current edge computing, and discussed the
corresponding security technology issues for various
security threats. In reference (Sun Jie, Qian Lei,
2019), it was proposed to add moving object detection
algorithm to the webcam to process the collected
original video data, remove redundant information,
and analyze the behavior in the video, and only
transmit the most valuable data to the cloud
computing center. Yu Tianqi and others proposed the
monitoring system framework of the Internet of
things based on edge computing (Yu Tianqi, Zhu
Yongxu, Wang Xianbin, 2018).
Figure 2: General architecture of edge computing.
Figure 3: Cloud computing paradigm.
4 COMPARISON BETWEEN
CLOUD COMPUTING AND
EDGE COMPUTING
This chapter mainly compares cloud computing
and edge computing from the models based on
existing research.
4.1 Cloud Computing
Figure 3 shows the traditional cloud computing
model. In this model, the source data is sent by the
producers to the cloud computing center and the
end users send the usage request to the cloud
computing center (Shi Weisong, Sun Hui, Cao Jie,
Zhang Quan, Liu Wei, 2017). In figure 3, The solid
blue line represents the data producers sending the
source data to the cloud computing center, the
dashed red line represents the end users sending the
usage requests to the cloud computing center, and
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
324
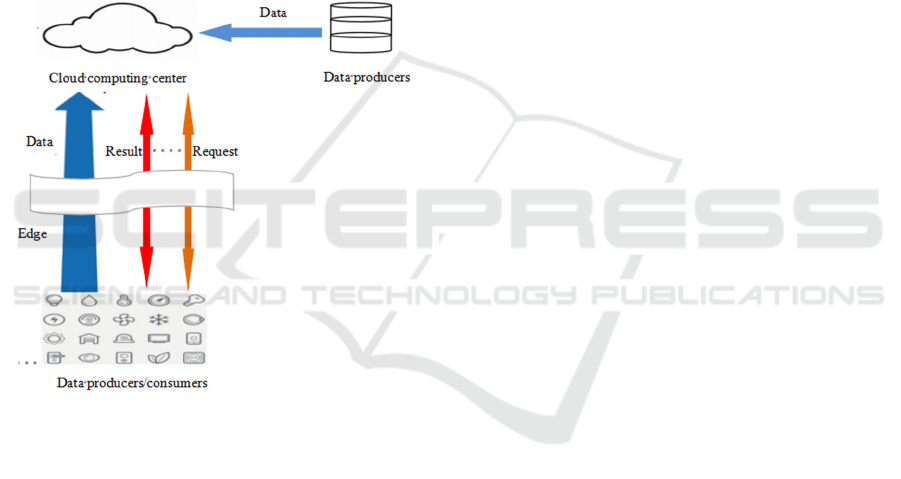
the dashed brown line represents the cloud
computing center feeding back the data result to the
end users.
4.2 Edge Computing
Edge computing refers to an open platform that
integrates network, computing, storage and
application core capabilities on the side close to the
objects or data source to provide the nearest terminal
services. Its applications are launched on the edge,
generating faster network service responses to meet
the industry's basic needs in real-time business,
application intelligence, security and privacy
protection. Edge computing is located between the
physical entity and the industrial connection, or at the
top of the physical entity.
Figure 4: Edge computing paradigm.
From the above model, we can find that the edge
computing model is to migrate some or all of the
computing tasks from the original cloud computing
center to execute near the source data. Therefore, it
has advantages in some aspects, for instance, data
transmission performance and real-time data
processing. However, it has higher requirements on
data privacy protection and security, service
management, data abstraction and other aspects.
These aspects deserve our in-depth study.
5 SUMMARY
With the rapid development of Internet of things
technology, edge computing has been highly
concerned and recognized by the government,
industry and academia at home and abroad because it
provides new solutions to the complex challenges in
the field of Internet of things, such as massive data
transmission and real-time service response. This
paper introduces the development and applications of
Internet of things technology and edge computing
technology. Edge computing extends the computing
and storage capabilities of cloud computing to the
edge of the network, provides local computing
services with low latency, high availability and
privacy protection, and solves the problems of cloud
computing such as high latency and network
environment constraints. Therefore, we can apply
edge computing to the enterprise IOT security
system, providing a new method for the security of
employees, environment and equipment.
ACKNOWLEDGEMENTS
The research reported herein is supported by the
NSFC of China under Grants Nos. 71571091,
71771112 and 71371092, and by University of
Science and Technology Liaoning Talent Project
Grants No. 601011507-03.
REFERENCES
Wang Shuming, 2016. Management of major hazard
sources in safety production in China [J]. Journal of
Jinling University of science and technology.
Pan Zhixing, 2015. Study on Hazard Management in
construction safety production [J]. Building materials
and decoration.
Xu Yangguang, Chen Xuebo, sun Qiubai, 2017. Early
warning system construction of unsafe behaviors of
employees [J]. Automation instrument.
Liu Qibiao, Chen Zhiming, 2015. Internet of things
engineering and practice (M). Higher education press.
Gui Jinsong, 2013. Internet of things system design [M].
Electronic Industry Press.
Bill Gates book, 1996.The Road Ahead [M].Peking
University press.
ITU Internet Reports, 2005. The Internet of Things[R].
International Telecommunication Union.
Furtak, J., Zielinski, Z., Chudzikiewicz, J., 2016. Security
techniques for the WSN link layer within military IoT.
2016 IEEE 3rd World Forum on Internet of Things
(WF-IoT).
Wang J, Jiang F, Xie C, 2012. The application of IOT to
military logistics[M]. The Application of IOT to
Military Logistics.
Zhang G W., 2013. IOT-based Intelligent Transportation
Systems and the Integrated Transport Information
Overview of Enterprise IoT Security System based on Edge Computing
325

Service[J]. Journal of Transportation Systems
Engineering & Information Technology.
Zeng Li, Xu Xin, Zeng Dajun, 2017. Research on
Application of Internet of things technology in safety
production process of power plant [J]. Electrical
technology.
Yang W, Peng Z, Yu H, et al, 2013. Energy Tree Dynamics
of Smart Grid Based on Industrial Internet of Things[J].
International Journal of Distributed Sensor Networks.
Liu B W, Zhou H, 2013. Analysis and Research of Smart
Grid System Based on Internet of Things[J]. China
Business & Market.
Li Cuijin, 2017. Design of hypertension smart health watch
based on onenet cloud platform [J]. Reading digest.
Liu Qibiao, Chen Zhiming, 2015. Internet of things
engineering and practice [M]. Higher education press.
Sun Qibo, Liu Jie, Li Li Li, Fan Chunxiao, Sun Juanjuan,
2010. Internet of things: a review of research on concept,
architecture and key technologies [J]. Journal of
Beijing University of Posts and telecommunications.
Yan Tao, LV Limin, 2012. Application of Internet of things
technology in enterprise safety production [J].
Computer technology and development.
Chen Xuebo, sun Qiubai, 2015. Reconstruction of
emergence inhibition of unsafe behaviors based on
safety awareness [J]. Journal of Liaoning University of
science and technology.
Liu Zude, Li Pengfei, 2015. Study on accident early
warning system of metallurgical enterprises based on
Internet of things [J]. Safety and environmental
engineering.
Su Huo, Liu Xiaodong, 2016. Research on OpenCV based
intelligent video monitoring alarm system [J].
Electronic design engineering.
Zhang Li, 2013. Research on event discovery technology in
intelligent video monitoring [D]. Xiamen University.
Zhang Yi, 2010. Object recognition and abnormal behavior
modeling and analysis in intelligent video monitoring
[D]. Shanghai Jiaotong University.
Wang Yucheng, 2016. Design and implementation of
human body and crowd behavior analysis system in
video monitoring [D]. Xiamen University.
Hu Dongtao, 2014. Research on the platform of safety
monitoring and early warning decision-making for non
coal underground mines based on the Internet of things
[D]. Wuhan University of technology.
Duan Yinlian, 2009. Research on the positioning and
monitoring system of mine personnel based on RFID
technology [D]. Anhui University of technology.
Qin Jianwang, 2012. Design and implementation of mine
safety production monitoring system based on Internet
of things [D]. Northeast University.
Sun, E., Zhang, X., & Li, Z., 2012. The internet of things
(IOT) and cloud computing (CC) based tailings dam
monitoring and pre-alarm system in mines. Safety
Science
.
Wu, Y., Chen, M., Wang, K., & Fu, G., 2019. A dynamic
information platform for underground coal mine safety
based on internet of things. Safety Science.
Chen, L. R. Cao, J. F., 2018. Industrial Internet of Things
Technology in Intelligent Factory [J]. Automation
Panorama.
2017. An Event Reporting and Early-Warning Safety
System Based on the Internet of Things for
Underground Coal Mines: A Case Study. Applied
Sciences.
Dong, L.J., Shu, W.W., Sun, D.Y., Li, X.B., Zhang, L.Y.,
2017. Pre-Alarm System Based on Real-Time
Monitoring and Numerical Simulation Using Internet
of Things and Cloud Computing for Tailings Dam in
Mines [J]. IEEE ACCESS.
Bo, C., Xin, C., Zhongyi, Z., Chengwen, Z., & Junliang, C,
2014. Web of Things-Based Remote Monitoring
System for Coal Mine Safety Using Wireless Sensor
Network. International Journal of Distributed Sensor
Networks.
PANG H H, TAN K L, 2004. Authenticating query results
in edge computing[C]. 20th International Conference
on Data Engineering.
Shi Weisong, sun Hui, Cao Jie, Zhang Quan, Liu Wei, 2017.
Edge computing: a new computing model in the age of
Internet of all things [J]. Computer research and
development.
SHI W S, CAO J, ZHANG Q, et al, 2016. Edge computing:
vision and challenges[J]. IEEE Internet of Things
Journal.
HU Y C, PATEL M, SABELLA D, et al, 2015. Mobile edge
computing-a key technology towards 5G[M]. ETSI
White Paper.
Li linzhe, Zhou Peilei, Cheng Peng, Shi Zhiguo, 2019.
Architecture, challenge and application of edge
computing [J]. Big data.
Qi Bing, Xia Yan, Li Bin, Shi Kun, Xue Mingfeng, 2018.
Household energy management system based on edge
computing: architecture, key technology and
implementation mode [J]. Electric power construction.
An Xingshuo, Cao Guixing, Miao Li, Ren Shubo, Lin
Fuhong, 2018. Summary of smart edge computing
security [J]. Telecommunication science.
Sun Jie, Qian Lei, 2019. Research on intelligent video
monitoring based on edge computing model [J].
Computer and digital engineering.
Yu Tianqi, Zhu Yongxu, Wang Xianbin, 2018. Anomaly
detection using self coding neural network in IOT
monitoring system based on edge computing [J].
Journal of IOT.
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
326
