A Review of Edge Computing Nodes based on the Internet of Things
Yunqi Dong, Jiujun Bai and Xuebo Chen
a
School of Electronic and Information Engineering, University of Science and Technology Liaoning,
Qianshan Road, Anshan 114051, Liaoning, China
Keywords: Edge Computing Nodes, Trust, Virtualization Technology, Isolation Technology.
Abstract: Due to the limitations of resources on the IoT device side, it is necessary to provide users with services not
only by means of a long-distance cloud computing center node, but also by some edge computing nodes. If
all the data on the device side is transmitted to the cloud center node, it will be returned to the device side
after unified processing. This transmission method will bring great pressure to the network link and data
center, and it will also cause the cloud center node to overload and refuse service. In order to speed up the
data processing and reduce delay, we briefly summarize the edge computing node model in this paper. Firstly,
considering the properties of privacy, security, trust and resource scheduling, etc., the edge computing is
analyzed. Then, based on these properties, the definition, architecture, and collaboration with cloud-edge-net
of edge computing are discussed. We also introduce the current key technologies used in edge computing,
such as network, virtualization, isolation, deep learning, and access control technologies. Finally, we give a
prospect of the possible application of edge computing in the future.
1 INTRODUCTION
Edge computing is an open platform based on edge
nodes, which integrates network, computing, storage,
application and other core capabilities of distributed
computing. The United States is the birthplace of the
concept of edge computing. In 2003, AKAMAI began
collaborating with IBM on "Edge computing",
providing edge-based services on Web Sphere (IBM &
AKAMAI, 2003). In 2011, Cisco was the first one to
proposed the concept of fog Computing, which extends
the concept of Cloud Computing (BONOMI, 2011).
Compared with Cloud Computing, it is closer to
the place where data is generated. Data, data-related
processing and applications are concentrated in
devices at the edge of the network. From fog
computing to edge computing, mapping along the
edge cloud network hierarchy. It makes possible for a
variety of computing tasks to achieve different levels
of intelligence at different costs and energy budgets
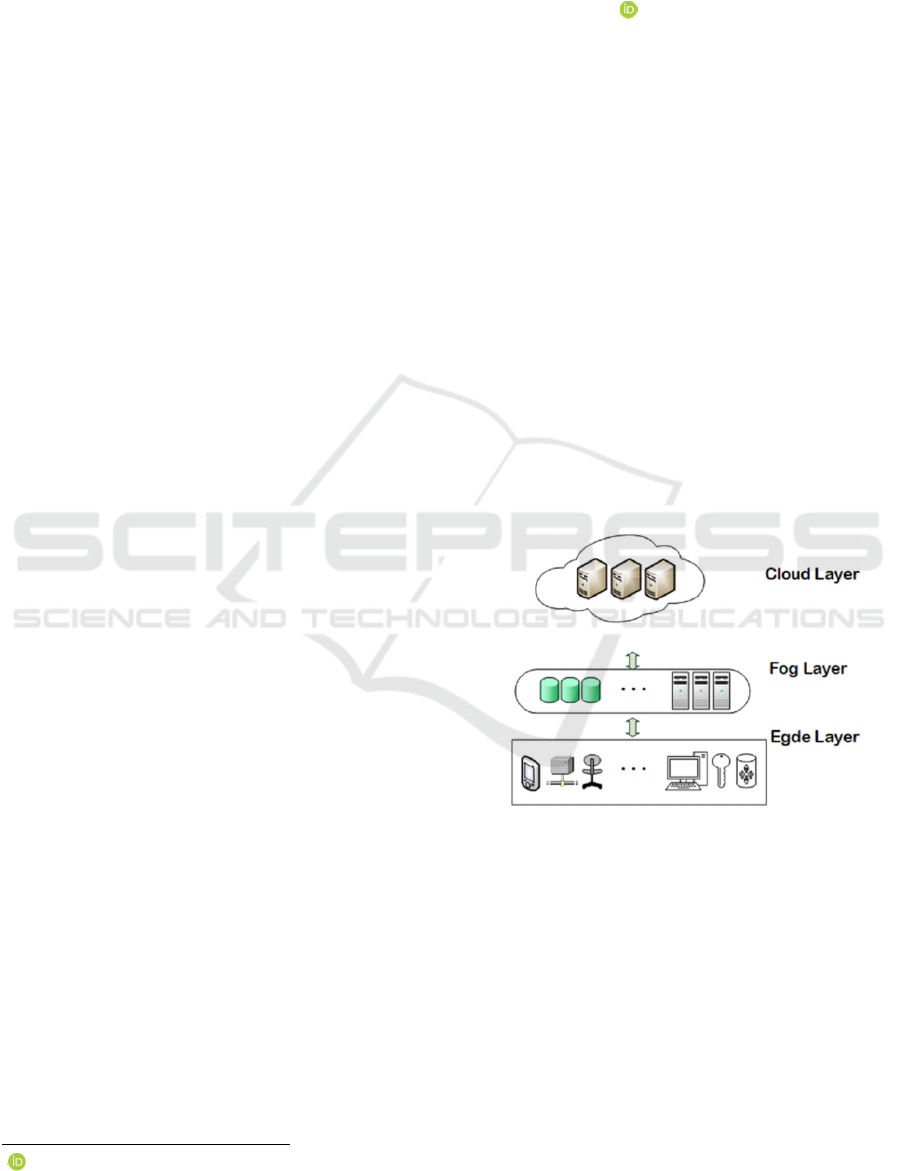
(Martin and Diaz, 2018), as shown Figure 1. In May
2016, a team of professors at Weisong Shi state
university in the United States came up with a formal
definition of edge. Edge computing is a new network
computing mode that performs edge computing.
a
https://orcid.org/0000-0001-6799-7667
Figure 1: A simplified architecture of edge-to-cloud
network with cloud computing.
The downlink data of edge computing represents
cloud service and the uplink represents the
interconnection of everything (Shi and Cao, 2016).
Edge computing refers to the computing and network
resources between the data source and any path to the
cloud computing center.
In November 2018, the Edge Cross Alliance was
established. The alliance was used a two-pronged
approach to address the critical issues involved in
accurately modeling data at the edge. The alliance
Dong, Y., Bai, J. and Chen, X.
A Review of Edge Computing Nodes based on the Internet of Things.
DOI: 10.5220/0009407003130320
In Proceedings of the 5th International Conference on Internet of Things, Big Data and Security (IoTBDS 2020), pages 313-320
ISBN: 978-989-758-426-8
Copyright
c
2020 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
313

also aimed to promote standardization of these data
models to further pursue more precise and simplified
the edge processing methods. They discussed the
edge computing nodes based on the Internet of things
(Boubendir and Guillemin, 2018).
This paper introduces the development history of
edge computing node in section 1. The section 2, 3
introduce the reasons for the generation of edge
computing nodes, and then give an overview from
definition, architecture, and Cloud-Edge-Network
Coordination. And then the key techniques to
promote the development of edge computing are
discussed in the 4
th
section, the 5
th
section is the the
direction of application, the 6
th
is the summary and
outlook.
2 EDGE COMPUTING NODE
GENERATION
In daily life, when users use various applications
on the network, the application will obtain all the
user's data, including the private data. Most of the
data is uploaded to the cloud center for storage. In
the process of data transmission and storage, due to
the openness of the application environment of the
Internet of things, diversity of services, energy
nodes limited and other characteristics, the risk of
user privacy data leakage increases, so the security
problem between nodes remains to be solved.
When the two edge clouds interact, they need to be
accessed through the edge trust node on the edge
cloud. Under the condition of reaching a
consensus, resources are allocated among the edge
clouds. The framework for this interaction can be
seen in Figure 2.
2.1 Privacy, Security and Trust
Saurabh proposed a framework where each sensor
node maintains reputation metrics which both
represent past behavior of other nodes and are used as
an inherent aspect in predicting their future behavior.
He employed a Bayesian formulation and combine
with the beta reputation system, for the algorithm
steps of reputation representation, updates,
integration and trust evolution (Saurabh and
Ganeriwal, 2008). Integrated comprehensive trust
theory, rough set theory, analytic hierarchy process
(AHP) and the combination of weight and grey
correlation analysis, in order to improve user
satisfaction and the success rate of node interaction
(Wang and Wen, 2019).
Figure 2: Trust and resource collaboration between edge
nodes.
Resource efficiency and dependability are the
most basic requirements of the trust model. The
definition of a self-adapted weighted method for trust
aggregation at CH level surpasses the limitations of
the subjective definition of weights in traditional
weighted method. The fuzzy degree of nearness is
used to evaluate the reliability of the recommended
trust values from the third-party nodes (Shao and
Zhou, 2015). Based on service preference to identify
user community effectively, a dynamic cloud service
trust evaluation model based on service-level
agreement (SLA) and privacy awareness is proposed,
which improves the satisfaction of service requesters
and avoids malicious interference (Wang and Wen,
2018). Shahzad provides a study of the issues related
to the data sharing through these smart devices over
service providing cloud. It proposes communication
architecture by introducing an intermediate layer of
data sharing control consisting of privacy agents. It
used to define custom privacy policies for different
personal attributes in different business models
(Shahzad and Iqbal, 2017).
2.2 Resource Allocation
2.2.1 Global Delay
In order to achieve the minimize global delay, a flow
scheduling policy based on link bandwidth
proportional fair allocation was designed by Feng.
The virtual forwarding space (VFS) of flood lighting
is proposed to realize the fair allocation of link
bandwidth and the minimum delay flow scheduling in
the data plane (Feng and Bi, 2014). Considering
dynamic changes in user requirements and limited
available resources in Fog devices. Naha propose
resource allocation and provisioning algorithms by
using resource ranking and provision of resources in
a hybrid and hierarchical fashion. Use the Cloud Sim
toolkit to simulate a real fog environment. The
performance of the proposed algorithms is better
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
314

compared with existing algorithms in terms of overall
data processing time and network delay (Naha and
Garg, 2019). Zenith is a novel model for allocating
computing resources in an edge computing platform
which allows the service providers to establish
resource sharing contracts with edge infrastructure
providers (Xu and Palanisamy, 2017). The latency-
aware scheduling and resource provisioning
algorithm that enables tasks to complete and meet
their latency requirements. A resource allocation
model of edge cloud based on auction mechanism is
proposed (Xu, 2016), and the time-delay requirement
of application is effectively guaranteed by the use of
delay-aware resource scheduling algorithm.
2.2.2 Quality-of-Service
Song presents an effective approach to periodically
distributing incoming tasks in the edge computing
network so that the number of tasks can be processed
in the edge computing network is increased. In order to
satisfied all the accommodated tasks quality-of-service
(QoS) specifications required in the IoT applications
(Song and Yau, 2017). To solve the problem of
resource scheduling in edge applications, under the
principle of not violating the service quality
requirements, a resource scheduling method based on
genetic algorithm is proposed (Skarlat and Nardelli,
2017).
In the context of smart cities, the concept of mobile
edge computing (MEC) is taken as a key factor to
improve the Quality of Service (QoS). Not only does it
enhance the autonomous creation of MEC services,
allowing data to be accessed any-where-anytime, with
the best Quality of Experience (QoE), but it also
reduced latency (Taleb and Dutta, 2017).
2.2.3 Bandwidth Allocation, Offloading
Distributed gradient-push algorithm can solve the
bandwidth allocation problems over WLAN with
directed typologies. Compared with the existing
distributed algorithms, we use weighted running
average bandwidth to replace the current state variables
meanwhile, the convergence performance is improved
and the robustness against noise is enhanced (Shi and
Zhou, 2019). Ascigil proposes a set of practical,
uncoordinated service placement policies. Through a
large number of simulations using synthetic and real
trace data, it has been demonstrated that the
uncoordinated strategy performs better than the
optimal placement solution, satisfying the maximum
amount of user requests (Ascigil and Phan, 2017).
For the power delay trade off of multi-user moving
edge computing system, an online algorithm for
determining local execution and calculating unloading
strategy is presented based on Lyapunov optimization
algorithm (Mao and Zhang, 2016). Lyapunov
optimization-based dynamic computation offloading
algorithm named low-complexity online algorithm,
which jointly decides the offloading decision, the
CPU-cycle frequencies for mobile execution and the
transmit power for computation offloading. A unique
advantage of this algorithm is that the decisions depend
only on the current system state. The implementation
of the algorithm only requires to solve a deterministic
problem in each time slot, for which the optimal
solution can be obtained either in closed form or by
bisection search (Mao and Zhang, 2016).
3 DEFINITION OF EDGE
COMPUTING
3.1 Definition
Edge computing is a new computing model. It can be
seen from the definition of edge computing that edge
computing is not to replace cloud computing but to
supplement cloud computing, providing a better
computing platform for mobile computing and
Internet of things. "Edge" in edge computing refers to
the computing and storage resources on the edge of
the network. The edge of the network here is opposite
to the data center, which is closer to the user both in
terms of geographical distance and network distance.
Professor Satyanarayanan describes edge
computing as: "edge computing is a new computing
model that deploys computing and storage resources
(e.g., cloudlets, micro data centers, or fog nodes) on
the edge of the network closer to the mobile device or
sensor"(Satyanarayanan, 2017). Wayne state
university in the United States WeiSong Shi et al (Shi
and Cao, 2016). The calculation is defined as: "edge
of computing refers to the network edge perform
calculations of a new type of computing model, in
computing the edge on the edge of the downstream
data cloud services, uplink said that everything
connected, and the edge of the edge of computing
refers to from the data source to cloud computing
center path between any of the computing and
network resources."
Edge computing is the technology of using these
resources to provide services to users on the edge of
the network so that applications can process data near
the data source. ISO think edge computing is a main
business processing and data storage in the network
edge node of the distributed computing form (Arndt,
A Review of Edge Computing Nodes based on the Internet of Things
315
2017). However, the Edge Computing Consortium
(ECC) is defined margin calculation is close to the
network edge side of data source, integrating core
ability of network computing storage application
development platform, etc (ECC, 2017).
3.2 Architecture
Resources and information are gathered to the center
by cloud computing, realizing the centralized
computing with complete control over user
information and behavior. Edge computing is a
distributed operation that transfers applications, data
and services from network center nodes to network
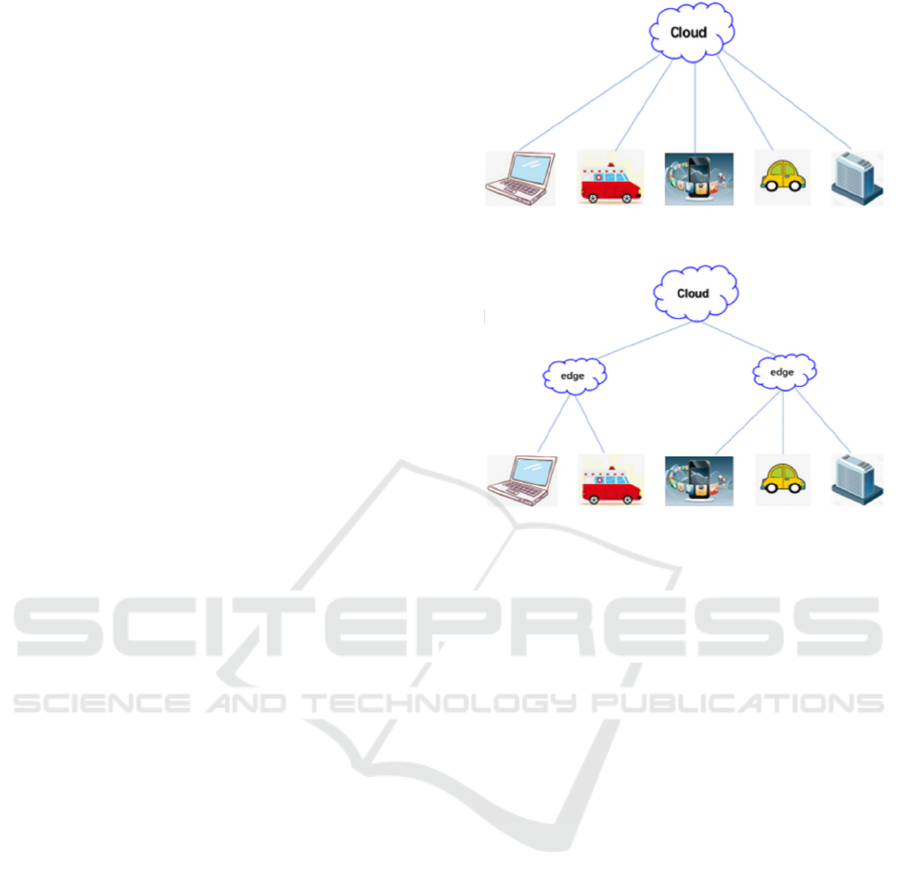
logical edge nodes for processing, you can see the
difference between Figure 3 and 4. Large services
originally handled entirely by cloud center nodes are
decomposed by edge computing, cut into smaller and
more manageable parts and distributed to edge. Based
on the previous work, λ-CoAP architecture, a new
edge computing architecture is proposed. Edge
computing deployments that cover the entire field of
vision, from IOT devices, edge smart gateways to the
cloud infrastructure (Martin and Diaz, 2018).
3.3 Cloud-Edge-Network Coordination
There is force synergy between edge computing and
cloud computing at the center. Force network refers
to the realization of cloud network collaboration,
cloud edge collaboration, and even edge collaboration
between edge computing and cloud computing and
networks, in order to realize the optimization of
resource utilization. On the basis of studying the
demand of edge computing force distribution and
dispatching, a deep fusion of cloud-network-edge
computing force network is proposed. This scheme
can effectively deal with the multi-stage deployment
of computing storage network and even algorithm
resources as well as the flexible scheduling among
nodes (Lei and Liu, 2019).
4 KEY TECHNOLOGY
The rapid development of edge computing is due to
technological advances. Promote the development of
core technologies of edge computing including
network, isolation technology, virtualization
technology, deep learning technology, access control
technology, algorithm execution framework security
and privacy, data processing platform, etc.
Figure 3: Cloud computing.
Figure 4: Edge computing.
4.1 Network
Edge computing pushes the computation closer to the
data source, and even deplores the entire computation
to nodes on the transport path from the data source to
the cloud computing center.
Edge devices generate a large amount of data,
while edge servers provide a large number of
services. Therefore, according to the edge servers and
network conditions, how to dynamically schedule
these data to the appropriate computing service
providers, load balancing will be one of the core
issues in edge computing. The maximal uniform
distribution of the load across closer and simpler
nodes can help managing and providing the big data
and large workloads more easily. Verma proposed an
efficient load balancing algorithm for a Fog-Cloud
based architecture. The ultimate goal is to balance
load through Fog networks and make internet less
Cloud dependent by having data available closer to
the user end (Verma and Yadav, 2016).
Edcs are used for reduce latency and network
congestion by processing data streams and user
requests in real time. The new load balancing
technology implements authentication of the edcs and
finds less heavily loaded edcs for task assignments.
Load balancing techniques enable workload
redistribution between edcs to improve resource
utilization and job response time (Puthal and Obaidat,
2018).
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
316
4.2 Virtualization Technology
Virtualization technology includes memory
virtualization, storage virtualization, hardware
virtualization, software virtualization and other
technologies. It is a process of turning a physical unit
into multiple logical units. It is applicable to multiple
applications to achieve efficient utilization of resources
and efficient management of various resources.
Virtualization technology provides high
availability for critical applications and simplifies
application deployment and migration. It performed
well in terms of cost, time and energy savings (Ding
and Ghansah, 2015). The virtualization technology
can achieve the rational utilization of hardware
resources through virtual software and assigns these
resources into corresponding application software
(Kong 2014). Container is a new virtualization
replaces the traditional virtual machine technology.
Changes have been made in the architecture of
Infrastructure as a Service (Iaas) and Platform as a
Service (Paas) platforms (Wu, 2017).
4.3 Isolation Technology
Isolation technology is a research technology that
supports the robust development of edge computing.
Edge equipment needs effective isolation technology
to ensure the reliability and quality of service.
1) The isolation of computing resources, that is,
the applications shall not interfere with each other;
2) Data isolation, that is, different applications
should have different access rights.
The core idea of Docker is to use the extended
LXC (Linux Container) scheme to achieve a
lightweight virtualization solution. By using kernel
namespace, Docker realizes isolation of container to
ensure the operating environment isolation among
each virtual machine service. The isolation
mechanism of Docker can reduce the memory
overhead and ensure the virtual instance density. (Liu
and Li, 2015).
Containers are constantly gaining ground in the
virtualization landscape as a lightweight and efficient
alternative to hypervisor-based Virtual Machines,
with Docker being the most successful representative.
This strategy allows developers to easily pack
applications into Docker image layers and distribute
them via public registries. Ioannis proposed and
demonstrate a mechanism for secure Docker image
manipulation throughout its life cycle: The creation,
storage and usage of a Docker image is backed by a
data-at-rest mechanism. (Giannakopoulos and
Papazafeiropoulos,2017).
4.4 Deep Learning Technology
Deep learning (DL) is a promising approach for
extracting accurate information from raw sensor data
from IoT devices deployed in complex environments.
Because of its multilayer structure, deep learning is
also appropriate for the edge computing environment
(Li, Ota and Dong, 2018).
DL as the representative technique of artificial
intelligence, it can be integrated into edge computing
frameworks to build intelligent edge for dynamic,
adaptive edge maintenance and management.
Promoting the fusion of edge intelligence and
intelligent edge, Edge Deep Learning (Han and Wang,
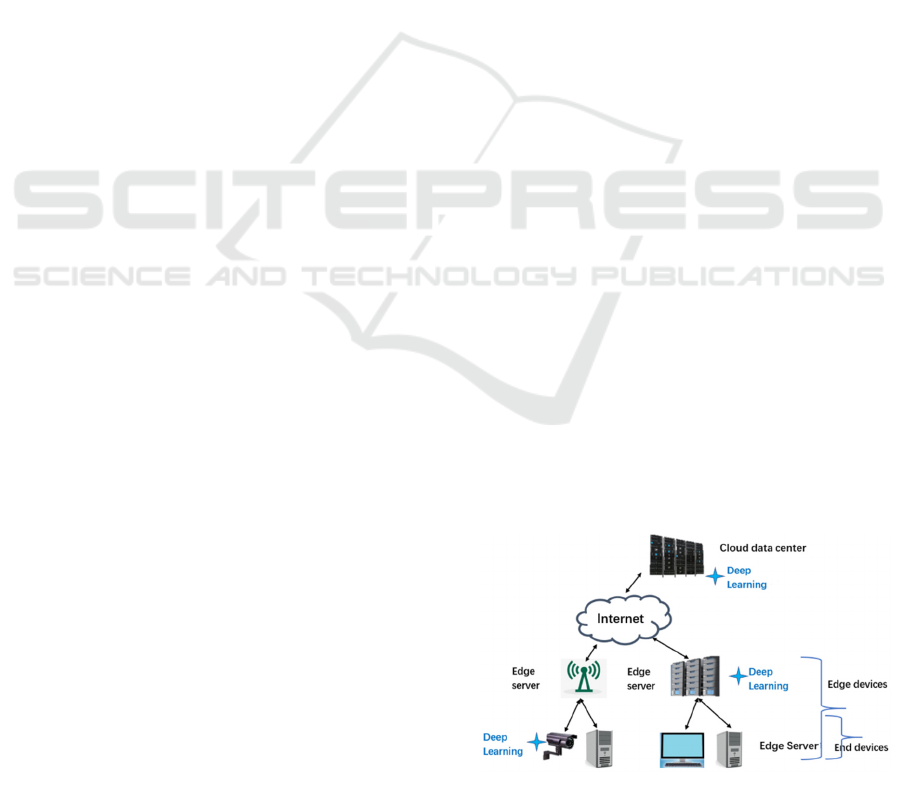
2019). Figure 5 is a frame about combine deep learning
with edge computing. Deep learning technology
require substantial computation resources to run
quickly. Edge computing is a viable way to meet the
high computation and low-latency requirements of
deep learning on edge devices and also provides
additional benefits in terms of privacy, bandwidth
efficiency, and scalability (Chen and Ran, 2019).
4.5 Access Control Technology
Access control technology is based on satisfying
users' demands for maximum enjoyment of resource
sharing, in order to achieve the management of user
access rights, prevent information from being
tampered with or abused by unauthorized users. It is
a reliable tool to ensure system security and protect
user' privacy. In edge computing, access control
becomes more difficult, mainly because in multi-user
access environments, access control functions need to
be provided by edge computing service providers.
Secondly, access control supports remote provision of
user basic information and policy information, and
also supports regular update of access control
information. Finally, access control for highly
distributed and dynamically heterogeneous data is an
important challenge in itself.
Figure 5: Combine deep learning with edge computing.
A Review of Edge Computing Nodes based on the Internet of Things
317

5 DIRECTION OF APPLICATION
5.1 Content Delivery Network
The combination of content distribution network and
edge computing is the future development trend. With
the evolution of CDN technology, the initial content
cache needs to be upgraded to smart edge computing.
The combination of CDN and mobile edge computing
device can fully reuse its nodes and provide edge
computing services. CDN USES global load
technology to direct user access to the nearest
working cache server.
Because of CDN distribution of nodes in the
network edge, service providers can take advantage
of the existing CDN further down to near the user's
network edge node, make each CDN nodes near the
user into edge mobile computing devices, to achieve
operational and support for various applications, in
order to meet the high frequency, the fragmentary
IOT equipment demand of calculation and
transmission. Amazon s AWS Lambda shows how
custom processing can enhance standard content
delivery networks (CDNs) without incurring
additional latency (Klas, 2017). A CDN with the help
of distributed denial of service (DDoS) mitigation can
enhance and maintain the website security from
DDoS attacks (Alrowaily and Lu, 2018).
5.2 5G
As the most important innovation scenario in the 5G
era, edge computing can provide customers with
multiple business guarantees such as low delay and
large bandwidth. According to IDC's data times 2025
report, 50% of data will be analyzed, processed and
stored on the edge of the network by 2025 (Tran and
Hajisami, 2017). At the same time, edge computing is
also considered as an important combination point of
5G, industrial Internet and Internet of things, which
can promote relevant industries to bring about rapid
development. However, with in-depth research and
practice, the concept of edge computing is not limited
to 5G, it has been extended to PON, wifi, 4G, etc.,
that is, multi-access edge computing.
5.3 Industry 4.0
Edge computing can play an important role in the
virtualization and business management of industrial
intelligent manufacturing systems. Firstly, through
the real-time connection and perception of edge
devices, an independent and reconfigurable digital
device model is established to enable the virtual
modeling and relational retrieval of production
resources. Secondly, adaptive allocation of network
resources is realized through SDN technology to
provide effective information transfer means for
reconfigurable devices.
6 CONCLUSIONS
The so-called Internet of everything extends on the X-
axis of time. The largest network is the Internet of
things. The huge scale of the Internet of things
requires fast computing power. If cloud computing is
the coordinator, edge computing is the executor.
Cloud computing is responsible for long-term big
data analysis. Edge computing is the calculation,
processing, optimization and storage of data close to
the edge of the Internet of things. Edge computing
and cloud computing work together and complement
each other. Edge computing is close to the device,
which also contributes to cloud data collection and
supports big data analysis of cloud applications. In
addition, trust is the foundation of secure interaction
between edge computing nodes. Edge compute nodes
control trust relationships and sensitive information
flows in a secure manner. Integrate distributed
computing into edge computing in a centralized cloud
computing architecture to reduce reliance on the
cloud center. Through the core technology of edge
calculation, the calculation efficiency is greatly
improved. Edge computing is still a work in progress.
In the future, the technical standards and
standardization of edge computing can be improved,
and the development of edge computing technology
can also be combined with the new generation of
information technology, so that the research on edge
computing will be more in-depth.
ACKNOWLEDGEMENTS
The research reported herein was supported by the
NSFC of China under Grants Nos. 71571091,
71771112 and 71371092, and by University of
Science and Technology Liaoning Talent Project
Grants No.:601011507-03.
REFERENCES
IBM & Akamai., 2003. Develop edge computing
application [EB].
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
318

Bonomi, F., 2011. Connected vehicles, the internet of
things, and fog computing. The Eighth ACM
International Workshop on Vehicular Inter-Networking
(VANET). ACM.
Martin, Fernandez, C., Diaz, Rodriguez, M., & Rubio
Munoz, B., 2018. An Edge Computing Architecture in
the Internet of Things. 2018 IEEE 21st International
Symposium on Real-Time Distributed Computing
(ISORC). IEEE.
ETSI ISG MEC., 2016. Multi-access edge computing
(MEC) framework and reference architecture.
Shi, W., Cao, J., Zhang, Q., Li, Y., & Xu, L., 2016. Edge
Computing: Vision and Challenges. IEEE Internet of
Things Journal. IEEE.
Boubendir, A., Guillemin, F., Le, Toquin, C., 2018.
Federation of cross-domain edge resources: a brokering
architecture for network slicing. 2018 4th IEEE
Conference on Network Softwarization and Workshops
(NetSoft). IEEE.
Saurabh, Ganeriwal, Laura., 2008. Reputation-based
framework for high integrity sensor networks. ACM
Transactions on Sensor Networks. ACM.
Wang, Y., Wen, J., Wang, X., Tao, B., & Zhou, W., 2019.
A Cloud Service Trust Evaluation Model Based on
Combining Weights and Gray Correlation Analysis.
Security and Communication Networks.
Shao, N., Zhou, Z., Sun, Z., 2015. A Lightweight and
Dependable Trust Model for Clustered Wireless Sensor
Networks. International Conference on Cloud
Computing and Security. SPRINGER.
Wang, Y., Wen, J., Zhou, W., & Luo, F., 2018. A Novel
Dynamic Cloud Service Trust Evaluation Model in
Cloud Computing. 2018 17th IEEE International
Conferences. IEEE.
Shahzad, S., Iqbal, M., Ahmad, N., 2017. Privacy Agents
for IoT Cloud Communication. In Proceedings of the
2nd International Conference on Internet of Things, Big
Data and Security. IEEE.
Feng, T., Bi, J., Wang, K., 2014. Allocation and Scheduling
of Network Resource for Multiple Control Applications
in SDN. 2014 IEEE/IFIP Network Operations and
Management Symposium. IEEE.
Naha, R, K., Garg, S., Chan, A., & Battula, S, K., 2019.
Deadline-based dynamic resource allocation and
provisioning algorithms in Fog-Cloud environment.
Future Generation Computer Systems. ELSEVIER.
Xu, J., Palanisamy, B., Ludwig, H., & Wang, Q., 2017.
Zenith: Utility-Aware Resource Allocation for Edge
Computing. 2017 IEEE International Conference on
Edge Computing. IEEE.
Xu, J., 2016. A Cloud Computing Resource Allocation
Model Based on Combinatorial Double Auction. 2016
3rd International Conference on Information Science
and Control Engineering (ICISCE). IEEE.
Song, Y., Yau, S, S., Yu, R., 2017. An Approach to QoS-
based Task Distribution in Edge Computing Networks
for IoT Applications. 2017 IEEE International
Conference on Edge Computing (EDGE). IEEE.
Skarlat, O., Nardelli, M., Schulte, S., 2017. Optimized loT
service placement in the fog. Service Oriented
Computing and Applications. SPRINGER.
Taleb, T., Dutta, S., Ksentini, A., 2017. Mobile Edge
Computing Potential in Making Cities Smarter. IEEE
Communications Magazine. IEEE.
Zheng, Qing., Shi., Chuan, Zhou., 2019. An Improved
Distributed Gradient-Push Algorithm for Bandwidth
Resource Allocation over Wireless Local Area
Network. Journal of Optimization Theory and
Applications. SPRINGER.
Ascigil, O., Phan, T, K., Tasiopoulos, A, G., 2017. On
uncoordinated service placement in edge-clouds. 2017
IEEE International Conference on Cloud Computing
Technology and Science (CloudCom). IEEE.
Mao, Y., Zhang, J., Song, S, H., 2016. Power-Delay
Tradeoff in Multi-User Mobile-Edge Computing
Systems. Oxford University Press.
Mao, Y., Zhang, J., Letaief, K, B., 2016. Dynamic
Computation Offloading for Mobile-Edge Computing
with Energy Harvesting Devices. IEEE Journal on
Selected Areas in Communications. IEEE.
Satyanarayanan, M., 2017. The Emergence of Edge
Computing. Computer.
Arndt, T., 2017. International Organization for
Standardization. ISO.
Edge Computing Consortium (ECC)., 2017. Alliance
Internet Industrial (AII). Edge computing reference
architecture2.0.
Martin Fernandez, C., Diaz Rodriguez, M., & Rubio
Munoz, B. 2018. An Edge Computing Architecture in
the Internet of Things. 2018 IEEE 21st International
Symposium on Real-Time Distributed Computing
(ISORC). IEEE.
Lei, b., Liu, Z, Y., Wang, X, L., 2019. A new edge
computing scheme based on cloud, network and edge
fusion: Calculate power network. Telecommunications
Science.
Verma, S., Yadav, A, K., Motwani, D., 2016. An efficient
data replication and load balancing technique for
computing environment. International Conference on
Computing for Sustainable Global Development. IEEE.
Puthal., Deepak., Obaidat., Mohammad, S., Nanda,
Priyadarsi., Secure and Sustainable Load Balancing of
Edge Data Centers in Fog Computing. IEEE
Communications Magazine. IEEE.
Ding, W, M., Ghansah, B., & Wu, Y, Y., 2015. Research
on the Virtualization Technology in Cloud Computing
Environment. International Journal of Engineering
Research in Africa. ELSEVIER.
Kong, L, L., 2014. Study of Cloud Computing and
Virtualization Technology. Applied Mechanics and
Materials.
Zhixue, W. U., 2017. Advances on virtualization
technology of cloud computing. Journal of Computer
Applications. ELSEVIER.
Si-Yao, L., Qiang, L. I., Bin, L. I., 2015. Research on
isolation of container based on docker technology.
Computer Engineering & Software.
A Review of Edge Computing Nodes based on the Internet of Things
319

Giannakopoulos, I., Papazafeiropoulos, K., Doka, K.,
Koziris, N., 2017. Isolation in Docker through Layer
Encryption. 2017 IEEE 37th International Conference
on Distributed Computing Systems (ICDCS). IEEE.
Li, H., Ota, K., Dong, M., 2018. Learning IoT in Edge:
Deep Learning for the Internet of Things with Edge
Computing. IEEE Network. IEEE.
Han, Y., Wang, X., Leung, V, C, M., 2019. Convergence of
Edge Computing and Deep Learning: A
Comprehensive Survey.
Chen, J., & Ran, X., 2019. Deep Learning with Edge
Computing: A Review. Proceedings of the IEEE. IEEE.
Klas, G., 2017. Edge Computing and the Role of Cellular
Networks. Computer.
Cloudflflare. What is a cdn? How does a cdn work?
[Online]. Available: https://www.cloudflare.com/
learning/cdn/what-is-a-cdn/
Alrowaily, M., Lu, Z., 2018. Secure Edge Computing in IoT
Systems: Review and Case Studies. 2018 IEEE/ACM
Symposium on Edge Computing (SEC). ACM.
Tran, Tuyen. X., Hajisami, Abolfazl, Pandey, Parul, &
Pompili, Dario., 2017. Collaborative mobile edge
computing in 5G networks: new paradigms, scenarios,
and challenges. IEEE Communications Magazine.
IEEE.
IoTBDS 2020 - 5th International Conference on Internet of Things, Big Data and Security
320
