
Android Run-time Permission Exploitation User Awareness by Means of
Formal Methods
Fausto Fasano
1
, Fabio Martinelli
2
, Francesco Mercaldo
1,2
and Antonella Santone
1
1
Department of Biosciences and Territory, University of Molise, Pesche (IS), Italy
2
Institute for Informatics and Telematics, National Research Council of Italy, Pisa, Italy
Keywords:
Mobile, Malware, Permission, Security, Model Checking, Formal Methods, Android.
Abstract:
Our mobile devices store a lot of sensitive and critical information. Moreover, considering the ability of
smartphones and tables to detect the position and to record audio, it is not absolutely an exaggeration to admit
that potentially our devices can easily spy on us. The ability to perform these crucial tasks must be granted by
the user at the time of their first use by accepting the so-called permissions. The problem is that in Android,
once these permissions are granted, the application can always use them without notifying the user. In this
paper, we propose a methodology, based on formal methods, aimed to detect the exact point in the code (in
term of package, class and method) of an Android application where a permission is invoked at run-time.
Moreover we design a tool able to advise the user whether a permission is invoked, in this way the user can be
informed about the application behaviour.
1 INTRODUCTION AND
RELATED WORK
In last years, mobile malware increased its complex-
ity from the point of view of malicious actions able
to steal more and more sensitive and private infor-
mation. In particular, the Android official market,
due to the official market publication process, it is
the perfect vector to diffuse malware (Mercaldo et al.,
2016c; Mercaldo et al., 2016d). Another motivation
behind the increasing amount of Android malware in
the wild is represented by the easiness of requesting
permissions to sensitive resources such as, for exam-
ple, the camera and the microphone. As a matter
of fact, the Android platform employs the permis-
sion system to restrict application privileges to secure
the sensitive resources of the users. An application
needs to get a users approval for the requested permis-
sions to access the privacy-relevant resources. Thus,
the permission system was designed to protect users
from applications with invasive behaviours, but its ef-
fectiveness highly depends on the users comprehen-
sion of permission approval (Tchakount
´
e, 2014; Mar-
tinelli et al., 2017a; Fasano et al., 2019b). The de-
veloper is responsible for determining appropriately
which permissions an application requires. Accord-
ing to (Kelley et al., 2012; Felt et al., 2012; Tchak-
ount
´
e et al., 2014; Martinelli et al., 2017b), lot of
users do not understand what each permission means
and blindly grant them, allowing the application to ac-
cess sensitive information of the user. Many users,
although an app might request a suspicious permis-
sion among many seemingly legitimate permissions,
still confirm the installation. Most of permissions
defined by Google are coarse-grained. Especially,
the INTERNET permission (Barrera et al., 2010),
the READ PHONE STATE permission (Pearce et al.,
2012), and the WRITE SETTINGS permission (Jeon
et al., 2011) are coarse-grained as they give to an ap-
plication arbitrary access to certain resources. The
INTERNET permission allows an application to send
HTTP(S) requests to all domains, and connect to arbi-
trary destinations and ports (Felt et al., 2010). As a re-
sult, the INTERNET permission provides insufficient
expressiveness to enforce control over the Internet ac-
cesses of the application (Canfora et al., 2016). Be-
cause of the previous problems, researchers have been
involved to determine mechanisms that employs in-
dividual permissions and the combination of permis-
sions to detect and characterise malware (Enck et al.,
2014; Zhou and Jiang, 2012). The Android frame-
work, starting from Android 7, allows the user to ap-
prove a subset of the permissions requested by appli-
804
Fasano, F., Martinelli, F., Mercaldo, F. and Santone, A.
Android Run-time Permission Exploitation User Awareness by Means of Formal Methods.
DOI: 10.5220/0009372308040814
In Proceedings of the 6th International Conference on Information Systems Security and Privacy (ICISSP 2020), pages 804-814
ISBN: 978-989-758-399-5; ISSN: 2184-4356
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

cations
1
(even though some applications do not work
if not all permissions are provided) but this mecha-
nism is not enough to guarantee the security of our in-
formation stored on mobile devices (Chakraborty and
Chattopadhyay, 2020; Foster, 2020).
As such, Enck et al. (Enck et al., 2008) introduce
a policy-based system called Kirin to detect malware
at install time based on undesirable combination of
permissions. Diverse works evaluate the detection of
malware with permissions using machine learning on
Android (Huang et al., 2013). They all realise that a
permission-based mechanism can be used as a quick
filter to identify malicious applications. Zhou and
Jiang (Zhou and Jiang, 2012) characterise Android
applications (both normal and malware applications)
with individual permissions focusing on the number
of occurrences of permissions in those groups. Au-
thors in (Tramontana and Verga, 2019) propose a
method to protect data and resources in Android. ba-
sically developing a method aimed to ask user when a
permission in invoked. The main difference with re-
spect to the proposed work is represented by the adop-
tion of formal verification environment, that demon-
strate their efficacy and robustness in the detection of
malicious behaviour in software and in particular in
Android environment (Canfora et al., 2018).
In this context, the permission to use the device
camera (android.permission.CAMERA) and to record
audio (android.permission.RECORD AUDIO) ex-
ploiting the device microphone are really critical. In
fact, the android.permission.RECORD AUDIO
permission can easily turn the smartphone
into an environmental recorder, while the an-
droid.permission.CAMERA permission is able to
capture pictures and videos. Clearly, these permis-
sions can be used for purposes useful to the user (for
instance, for a voip call) but can be easily exploited
for malicious purposes from malware writers.
Basically, the purpose of a permission is to protect
the privacy of an Android user. Android apps must
request permission to access sensitive user data (such
as contacts and SMS), as well as certain system fea-
tures (such as camera and internet). Depending on
the feature, the system might grant the permission au-
tomatically or might prompt the user to approve the
request
2
.
A central design point of the Android security ar-
chitecture is that no app, by default, has permission
to perform any operations that would adversely im-
pact other apps, the operating system, or the user.
1
https://developer.android.com/training/permissions/
requesting
2
https://developer.android.com/guide/topics/
permissions/overview
This includes reading or writing the user’s private data
(such as contacts or emails), reading or writing an-
other app’s files, performing network access, keeping
the device awake, and so on.
Android basically considers two categories of per-
missions: the normal permissions, i.e., the permission
that the system automatically grants to the mobile app
and the dangerous permissions.
If the app lists dangerous permissions in its man-
ifest (that is, permissions that could potentially af-
fect the user’s privacy or the device’s normal oper-
ation), such as the SEND SMS permission, but also
the android.permission.RECORD AUDIO or the an-
droid.permission.CAMERA, the user at run-time must
explicitly agree to grant those permissions. Once the
user grants the permission, the app is able to invoke it
whenever and wherever in the code.
For this reason even if an app requires a permis-
sion just one time, the permission will be released
from the operating system forever.
Starting from these considerations, in this paper
we propose a method to automatically detect whether
an Android permission is invoked at run-time. The
final aim is to show to the user the permission invo-
cation each time it is requested by the mobile appli-
cation. Android considers several permission as dan-
gerous, in this work we only focus on the permission
requests to access the internet connection, to use the
device camera and to record audio through the device
microphone.
To detect whether a permission is requested we
exploit formal methods, in particular the model
checking technique. We model an Android appli-
cations and with mu-calculus properties we verify
whether a mobile app is asking for the camera and au-
dio recording dangerous permissions by using static
analysis.
The paper proceeds as follows: in the next sec-
tion we provide background notions about the model
checking and mu-calculus logic largely employed in
this paper, in Section 3 the proposed method is de-
scribed, in Section 4 we present a real-world exper-
iment aimed to demonstrate the effectiveness of the
proposed method, in Section 5 a tool to inform the
user when an application is asking a permission at
run-time is introduced and, finally, in last section con-
clusion and future research directions are drawn.
Android Run-time Permission Exploitation User Awareness by Means of Formal Methods
805

2 MODEL CHECKING AND
MU-CALCULUS LOGIC
BACKGROUND
Verification of a software or hardware system involves
checking whether the system in question behaves as
it was designed to behave. Formal methods have
been successfully applied to safety-critical systems.
One reason is the overwhelming evidence that formal
methods do result in safer systems. In this paper, we
show that formal methods are extremely well-suited
to spyware detection. First of all, in this section we
recall some basic concepts.
Model checking is an formal method for determin-
ing if a model of a system satisfies a correctness spec-
ification (Clarke et al., 2001). A model of a system
consists of a labelled transition system (LTS). A spec-
ification or property is a logical formula. A model
checker then accepts two inputs, a LTS and a tempo-
ral formula, and returns true if the system satisfies the
formula and false otherwise.
A labelled transition system comprises some num-
ber of states, with arcs between them labelled by ac-
tivities of the system. A LTS is specified by:
• A set S of states;
• A set L of labels or actions;
• A set of transitions T ⊆ S × L × S.
Transitions are given as triples (start, label,end).
In this paper, to express proprieties of the system
we use the modal mu-calculus (Stirling, 1989) which
is one of the most important logics in model checking.
The syntax of the mu-calculus is the following,
where K ranges over sets of actions (i.e., K ⊆ L) and
Z ranges over variables:
ϕ ::= tt | ff |Z | ϕ ∧ ϕ | ϕ ∨ ϕ | [K]ϕ | hKiϕ | νZ.ϕ | µZ.ϕ
A fixpoint formula may be either µZ.ϕ or νZ.ϕ where
µZ and νZ binds free occurrences of Z in ϕ. An oc-
currence of Z is free if it is not within the scope of a
binder µZ (resp. νZ). A formula is closed if it con-
tains no free variables. µZ.ϕ is the least fixpoint of the
recursive equation Z = ϕ, while νZ.ϕ is the greatest
one. From now on we consider only closed formulae.
Scopes of fixpoint variables, free and bound vari-
ables, can be defined in the mu-calculus in analogy
with variables of first order logic.
The satisfaction of a formula ϕ by a state s of a
transition system is defined as follows:
• Each state satisfies tt and no state satisfies ff;
• A state satisfies ϕ
1
∨ ϕ
2
(ϕ
1
∧ ϕ
2
) if it satisfies ϕ
1
or (and) ϕ
2
. [K] ϕ is satisfied by a state which, for
every performance of an action in K, evolves to a
state obeying ϕ. hKi ϕ is satisfied by a state which
can evolve to a state obeying ϕ by performing an
action in K.
For example, hai ϕ denotes that there is an a-
successor in which ϕ holds, while [a] ϕ denotes that
for all a-successors ϕ holds.
The precise definition of the satisfaction of a
closed formula ϕ by a state s (written s |= ϕ) is given
in Table 1.
A fixed point formula has the form µZ.ϕ (νZ.ϕ)
where µZ (νZ) binds free occurrences of Z in ϕ. An
occurrence of Z is free if it is not within the scope of
a binder µZ (νZ). A formula is closed if it contains
no free variables. µZ.ϕ is the least fix-point of the
recursive equation Z = ϕ, while νZ.ϕ is the greatest
one.
A transition system T satisfies a formula φ, writ-
ten T |= φ, if and only if q |= φ, where q is the initial
state of T .
We will use the following abbreviations:
hα
1
,.. .,α
n
i φ = h{α
1
,.. .,α
n
}i φ
h−i φ = hLi φ
h−Ki φ = hL − Ki φ
[α
1
,.. .,α
n
] φ = [{α
1
,.. .,α
n
}] φ
[−] φ = [L] φ
[−K] φ = [L − K] φ
Some examples of logic properties are now pro-
vided. The simplest formulae are just those of modal
logic:
hαi tt
means that “there exists a transition labelled by the
action α”.
If we use the two different fixpoints, we obtain the
following formulae:
µZ.[α] Z : “all the sequences of α-transitions are finite”.
νY.haiY : “there is an infinite sequence of α-transitions”.
We can then add a predicate p, and obtain the for-
mula:
νY.p ∧ hαiY
saying that “there is an infinite sequence of α-
transitions, and all states in this sequence satisfy p”.
With two fixpoints, we can write fairness formu-
lae, such as:
νY.µX.(p ∧ hαiY ) ∨ hαi X
meaning that “on some α-path there are infinitely
many states where p holds”.
Changing the order of fixpoints we obtain:
ForSE 2020 - 4th International Workshop on FORmal methods for Security Engineering
806

Table 1: Satisfaction of a closed formula by a state.
p 6|= ff
p |= tt
p |= ϕ ∧ ψ iff p |= ϕ and p |= ψ
p |= ϕ ∨ ψ iff p |= ϕ or p |= ψ
p |= [K]
R
ϕ iff ∀p
0
.∀α ∈ K.p
α
−→
K∪R
p
0
implies p
0
|= ϕ
p |= hKi
R
ϕ iff ∃p
0
.∃α ∈ K.p
α
−→
K∪R
p
0
and p
0
|= ϕ
p |= νZ.ϕ iff p |= νZ
n
.ϕ for all n
p |= µZ.ϕ iff p |= µZ
n
.ϕ for some n
where:
• for each n, νZ
n
.ϕ and µZ
n
.ϕ are defined as:
νZ
0
.ϕ = tt µZ
0
.ϕ = ff
νZ
n+1
.ϕ = ϕ[νZ
n
.ϕ/Z] µZ
n+1
.ϕ = ϕ[µZ
n
.ϕ/Z]
where the notation ϕ[ψ/Z] indicates the substitution of ψ for every free occurrence of the variable Z in ϕ.
µX.νY.(p ∧ hαiY ) ∨ hαi X
saying “on some α-path almost always p holds.”
In this paper, we use CAAL (Concurrency Work-
bench, Aalborg Edition) (Andersen et al., 2015) as
formal verification environment. It is one of the most
popular environments for verifying systems. In the
CAAL the verification of temporal logic formulae is
based on model checking (Clarke et al., 2001).
3 THE METHODOLOGY
The proposed method is aimed to detect whether a
sensitive permission is invoked by exploiting model
checking with the aim to alert the user whenever the
permission is invoked at run-time.
In this section, we present the application of a
model checking based approach to detect run-time
permission invocation in Android environment. As
stated in the introduction, we are focused on An-
droid samples with the ability to use the internet
connection, the device camera and microphone to
record audio. We describe mobile applications by
exploiting Milner’s Calculus of Communicating Sys-
tems (CCS) (Milner, 1989) language specification
and express behavioural properties using mu-calculus
branching temporal logic (Stirling, 1989). The
methodology, as explained in previous works (Bat-
tista et al., 2016; Canfora et al., 2018; Cimitile et al.,
2018; Mercaldo et al., 2016a; Fasano et al., 2019a;
Bernardeschi et al., 2019), is based on two main steps.
Figure 1 shows the proposed methodology main
architecture.
The first step generates a CCS specification start-
ing from .class files of the analyzed application writ-
ten in Java Bytecode. Then, we define a Java
Bytecode-to-CCS transformation function. This is
defined for each instruction of the Java Bytecode. It
directly translates the Java Bytecode instructions into
CCS process specifications. The second step aims
to investigate Android application behaviours which
are successively expressed using mu-calculus logic.
We specify the set of properties starting from cur-
rent literature (Zhou and Jiang, 2012; Mercaldo et al.,
2016b) and with the manual inspection of a few sam-
ples. The CCS processes obtained in the first step are
then used to verify the properties. Codes described as
CCS processes are first mapped to labelled transition
systems and then verified with a model checker. In
our approach, we invoke the Concurrency Workbench
of New Century (CWB-NC) (Cleaveland and Sims,
1996) as formal verification environment. When the
result of the CWB-NC model checker is true, it means
that the sample under analysis is malicious, false oth-
erwise. We formulated logic rules from the follow-
ing characterizing behaviours (typical in mobile ap-
plications): (i) the exploitation of an internet connec-
tion, (ii) the request to use the device camera, (iii) the
request to use the device microphone to record au-
dio. The distinctive features of our methodology are:
Android Run-time Permission Exploitation User Awareness by Means of Formal Methods
807

Figure 1: The proposed methodology.
(i) the use of formal methods; (ii) the inspection on
Java Bytecode and not on the source code; (iii) the
use of static analysis; (iv) the capture of malicious
behaviours at a finer granularity. Summing up the
methodology, starting from the Java Bytecode appli-
cation files, we derive CCS processes, which are suc-
cessively used for checking properties expressing the
most common behaviours exhibit by the family sam-
ples. Performing automatic analysis on the Bytecode
instead of the source code has several advantages: (i)
independence of the source programming language;
(ii) identification of malicious payload without de-
compilation even when source code is lacking; (iii)
ease of parsing a lower-level code; (iv) independence
from obfuscation (Canfora et al., 2018; Cimitile et al.,
2018).
In the follow we show a couple of code snippet we
analysed to formulate the temporal logic properties
for the detection of run-time permissions.
Let us the consider the code snippet shown in Fig-
ure 2.
This snippet is belongong to a sample identified by
the da298299c164d2584c4fee96e205bae59e35593b
SHA-1 hash i.e., the WhatsApp Messenger app
3
,
one of the most famous app to send and receive
messages, calls, photos, videos, documents, and
Voice Messages using the 4G/3G/2G/EDGE connec-
tion or Wi-Fi, as available. In detail the snippet
shown in Figure 2 is related to the Java code of the
A1I method of the VoipActivityV2 class belonging to
the com.whatsapp.voipcalling package. In the snip-
pet there are two permission invocations: the first
one is the request for audio recording (i.e., the an-
droid.permission.RECORD AUDIO request) and the
3
https://play.google.com/store/apps/details?id=com.
whatsapp&hl=it
second one is the permission to use the device camera
(i.e., the android.permission.CAMERA request).
With the aim to consider another run-time request
permission, let us consider the code snippet in Figure
3.
The snippet in Figure 3 is re-
lated to a sample identified by the
2f03011c9f7e34ad46d9a26ef47d54b38a4caa49
SHA-1 hash i.e., the Yahoo Weather app
4
, one of the
most widespread app for hourly, 5-day, and 10-day
forecasts with details about wind, pressure, and
chance of precipitation. In detail the snippet in Figure
3 is related to the Java code of the X method of the
bv class. In this snippet, in the 4-th row, there is
the invocation of the android.permission.INTERNET
permission. Both the analised applications were
downloaded from the APKCombo repository
5
.
Starting from the snippets in Figures 2 and 3,
we propose several formulae: the first one (i.e., ψ)
aimed to detect whether there is a request for the an-
droid.permission.RECORD AUDIO permission, the
second one (i.e., χ) aimed to detect whether there
is a request for the android.permission.CAMERA
permission. The third formula, i.e., ϕ is aimed
to verify whether there is a request for the an-
droid.permission.RECORD AUDIO or for the an-
droid.permission.CAMERA permission. The last for-
mula i.e., ζ, is related to the invocation of the an-
droid.permission.INTERNET permission at run-time.
The ψ, χ, ϕ and ζ are satisfied whether at least in
one method of the application under analysis there is
an invocation of the considered permission.
The output of the proposed methodology is the list
4
https://play.google.com/store/apps/details?id=com.
yahoo.mobile.client.android.weather&hl=it
5
https://apkcombo.com/
ForSE 2020 - 4th International Workshop on FORmal methods for Security Engineering
808
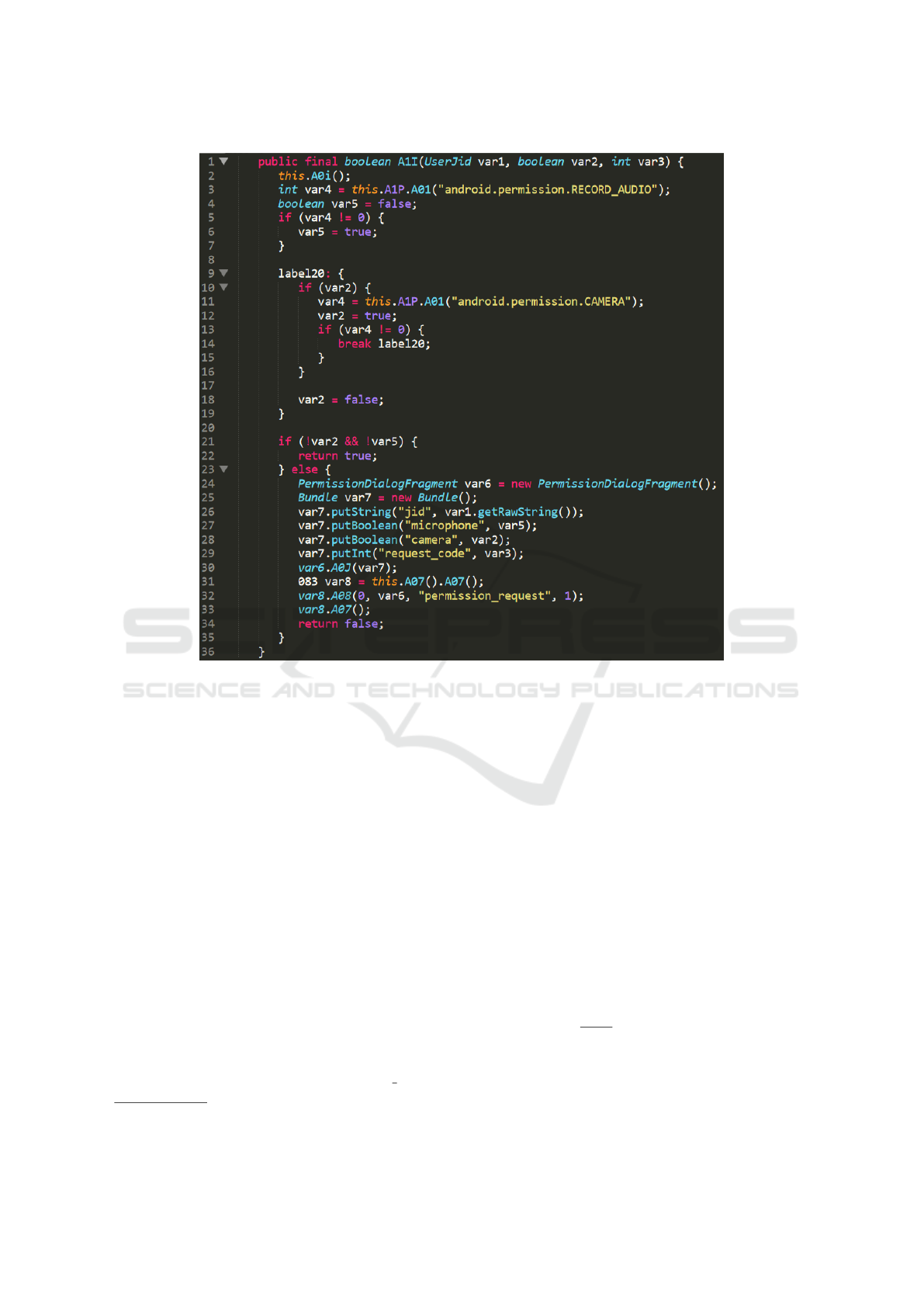
Figure 2: A code snippet belonging to the WhatsApp Messenger application.
of packages, classes and methods where the consid-
ered permission is invoked.
4 EXPERIMENTAL ANALYSIS
In this section, we describe the data-set used in the
experimental evaluation and we present the achieved
results.
4.1 The Data-set
To evaluate the proposed methodology to detect
sensitive permission request we consider a data-
set of real-world Android application obtained
from the Google Play store
6
. To this aim, we
crawled 200 applications from the official An-
droid market belonging to several categories. In
particular, within the data-set, 50 applications re-
quire the android.permission.RECORD AUDIO
6
https://play.google.com/store/apps
permission, 50 applications require the an-
droid.permission.CAMERA permission, 50 ap-
plications require the android.permission.INTERNET
permission at run-time. The remaining 50 applica-
tions do not require these permissions at run-time.
4.2 Performance Evaluation
We consider four metrics in order to evaluate the
results of the classification: Precision, Recall, F-
Measure and Accuracy.
The precision has been computed as the propor-
tion of the examples that truly belong to class X
among all those which were assigned to the class. It
is the ratio of the number of relevant records retrieved
to the total number of irrelevant and relevant records
retrieved:
Precision =
t p
t p+ f p
where tp indicates the number of true positives
and fp indicates the number of false positives.
The recall has been computed as the proportion
Android Run-time Permission Exploitation User Awareness by Means of Formal Methods
809
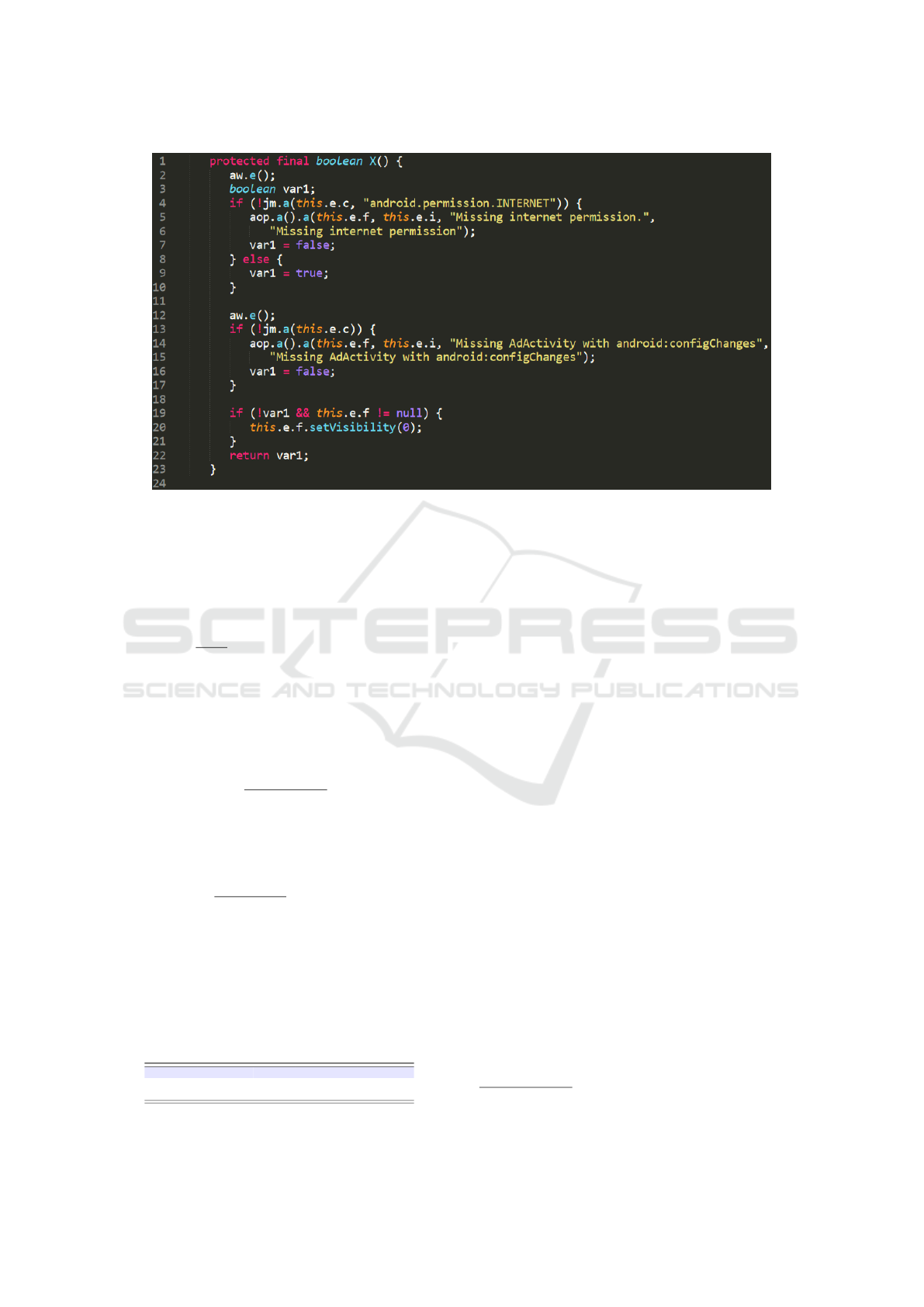
Figure 3: A code snippet belonging to the Yahoo Weather application.
of examples that were assigned to class X, among all
the examples that truly belong to the class, i.e., how
much part of the class was captured. It is the ratio of
the number of relevant records retrieved to the total
number of relevant records:
Recall =
t p
t p+ f n
where tp indicates the number of true positives
and fn indicates the number of false negatives.
The F-Measure is a measure of a test accuracy.
This score can be interpreted as a weighted average
of the precision and recall:
F-Measure = 2 ∗
Precision∗Recall
Precision+Recall
The Accuracy is defined as the ratio of number
of correct predictions to the total number of input
samples:
Accuracy =
t p+tn
t p+tn+ f p+f n
where tp indicates the number of true positives, tn
indicates the number of true negatives, fp indicates the
number of false positives and fn indicates the number
of false negatives.
Table 2 shows the results we obtained for the com-
puted metrics.
Table 2: Classification Results.
Formula Precision Recall F-measure Accuracy
ϕ 1 1 1 1
ζ 1 1 1 1
From the results shown in Table 2 it emerges
that for both the ϕ and the ζ formulae, the proposed
methodology is able to correctly detect and localize
the code snippet where a permission is invoked at run-
time.
5 TOOL DESIGN
In this section we describe the design of the tool we
propose to inform the user about the permission that
the code running on its mobile device is requiring (see
Figure 4).
Starting from the output of the analysis of the pro-
posed method, the idea is to advise - at run-time - the
user, by showing her the permission that the Android
operating system is releasing, as shown in Figures 5
and 6.
Through a reverse engineering process (Fasano
et al., 2019c; Cimitile et al., 2017; Martinelli et al.,
2018) from the Android application the source code
of the application under analysis is obtained.
From the output of the proposed methodology
(shown in Figure 1) the set of the methods with run-
time permission is obtained: in particular from the
proposed methodology we are able to obtain the pack-
age, the class and the method where a permission is
invoked at run-time. In each of these methods a Toast
7
is added. In Android, a Toast is a graphical interface
element able to provide simple feedback about an op-
7
https://developer.android.com/guide/topics/ui/
notifiers/toasts
ForSE 2020 - 4th International Workshop on FORmal methods for Security Engineering
810
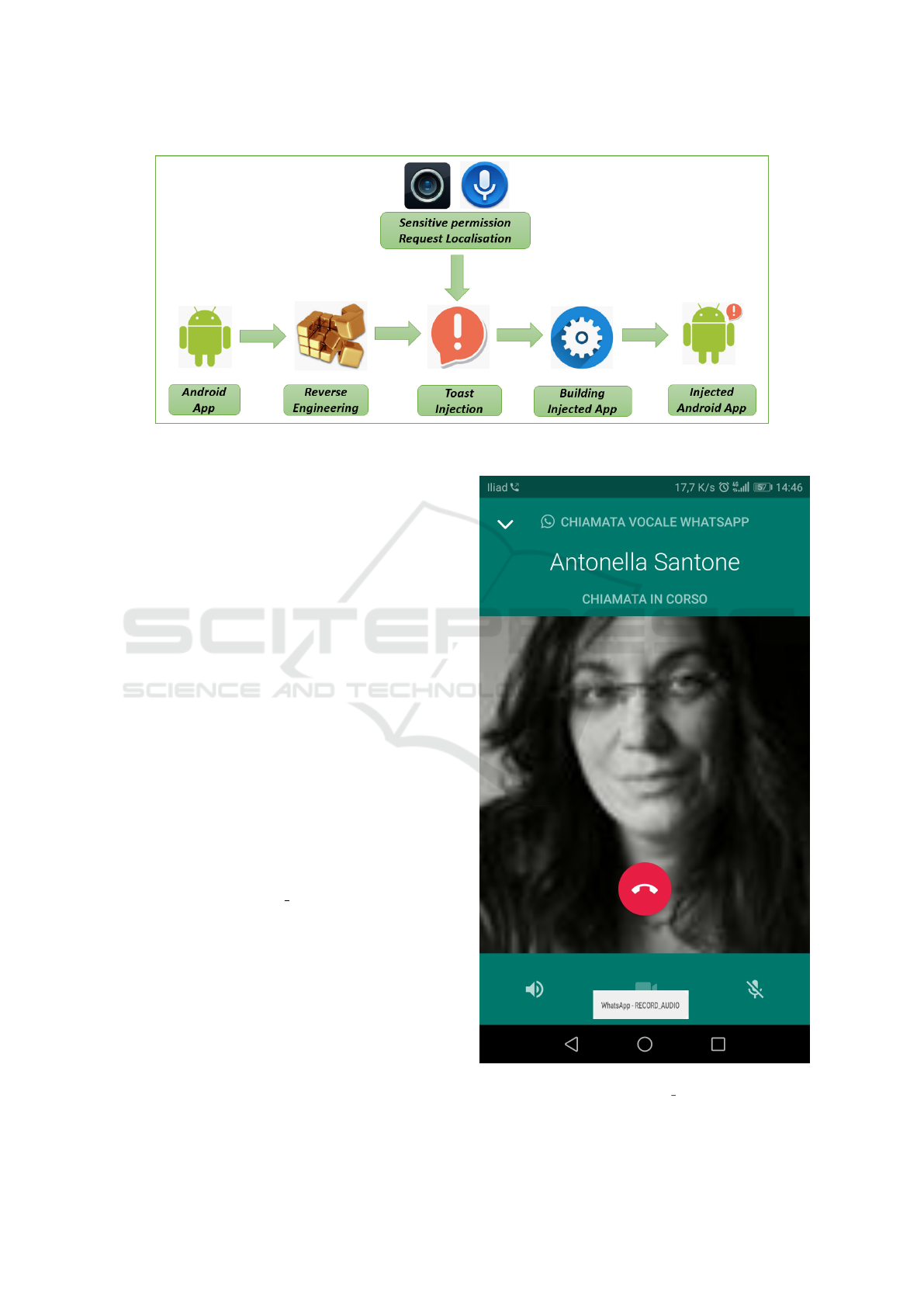
Figure 4: The tool design.
eration in a small popup. It only fills the amount of
space required for the message and the current activ-
ity remains visible and interactive and automatically
disappears after a timeout.
Once the small popups for each method invoking
at run-time a permission are injected, the application
is built with the aim to obtain the app executable. In
this way the user can be advised each time the app is
asking for a permission at run-time.
To show how the designed tool can be helpful to
make aware the user about the permissions requested
by the application, we show two screenshots about
two different applications (i.e, Whatsapp Messenger
and Yahoo Weather) when the Toasts are injected. In
these examples we manually injected the Toast in the
code localised by the proposed methodology, with the
aim to show the usefulness of the designed tool ex-
ploiting the methodology proposed in this work.
Figure 5 shows the Whatsapp Messenger screen
when the user is trying the make a voice call.
From the screenshot in Figure 5 it is pos-
sible to see the injected Android Toast advising
the user that the app is requiring for the an-
droid.permission.RECORD AUDIO permission.
The second screenshot we propose is related to the
Yahoo Weather application and it is shown in Figure
6.
The screenshot in Figure 6 is related to the home
screen of the device, where it is visible to Yahoo
Weather widget. In Android, widgets are miniature
application views that can be embedded in other ap-
plications (for instance the Home screen) and receive
periodic updates. Clearly also widget can ask for run-
time permission, as in this case: in fact when the
user try to update the weather information, the wid-
get is requiring the android.permission.INTERNET as
Figure 5: A screenshot of the WhatsApp application when
the android.permission.RECORD AUDIO permissions is
requested.
Android Run-time Permission Exploitation User Awareness by Means of Formal Methods
811

Figure 6: A screenshot of the Yahoo Weather application
when the android.permission.INTERNET permission is re-
quested.
demonstrated by the message appeared in the Toast.
6 CONCLUSION AND FUTURE
WORK
In this paper, we proposed a static methodology
aimed to detect the usage of run-time permission
in Android environment. We model Android appli-
cations in term of CCS models and, by exploiting
model checking technique, we verify whether a set of
permission in invoked. In this work we focused on
three permissions i.e., android.permission.CAMERA,
android.permission.RECORD AUDIO and an-
droid.permission.INTERNET permissions. We
experiment a data-set composed by 200 applications
downloaded by Google Play, obtaining an accuracy
equal to 1. Moreover we propose a tool, based on the
results obtained by the proposed methodology, aimed
to inform the user at run-time when an application is
asking for permissions.
As future work, first of all we plan to implement
and to release the designed tool in the Android official
market. Moreover, we plan to extend the temporal
logic formula set (Francesco et al., 2014; Ceccarelli
et al., 2014; Cimitile et al., 2018; Canfora et al., 2018;
Santone, 2002; Santone, 2011; Barbuti et al., 2005;
Gradara et al., 2005), with the aim to detect the full
set of permission provided at run-time by the Android
framework.
ACKNOWLEDGMENTS
This work has been partially supported by MIUR -
SecureOpenNets and EU SPARTA and CyberSANE
projects, the Formal Methods for IT Security Lab
8
,
and the MOSAIC Research Center
9
at the University
of Molise.
REFERENCES
Andersen, J. R., Andersen, N., Enevoldsen, S., Hansen,
M. M., Larsen, K. G., Olesen, S. R., Srba, J., and
Wortmann, J. K. (2015). CAAL: concurrency work-
bench, aalborg edition. In Theoretical Aspects of
Computing - ICTAC 2015 - 12th International Col-
loquium Cali, Colombia, October 29-31, 2015, Pro-
ceedings, volume 9399 of Lecture Notes in Computer
Science, pages 573–582. Springer.
Barbuti, R., De Francesco, N., Santone, A., and Vaglini, G.
(2005). Reduced models for efficient ccs verification.
Formal Methods in System Design, 26(3):319–350.
Barrera, D., Kayacik, H. G., Van Oorschot, P. C., and So-
mayaji, A. (2010). A methodology for empirical anal-
ysis of permission-based security models and its ap-
plication to android. In Proceedings of the 17th ACM
conference on Computer and communications secu-
rity, pages 73–84. ACM.
Battista, P., Mercaldo, F., Nardone, V., Santone, A., and
Visaggio, C. A. (2016). Identification of android mal-
ware families with model checking. In ICISSP, pages
542–547.
Bernardeschi, C., Mercaldo, F., Nardone, V., and Santone,
A. (2019). Exploiting model checking for mobile bot-
net detection. Procedia Computer Science, 159:963–
972.
8
https://dipbioter.unimol.it/ricerca/laboratori/metodi-
formali-per-la-sicurezza-informatica/
9
https://dipbioter.unimol.it/ricerca/laboratori/centro-di-
ricerca-mosaic/
ForSE 2020 - 4th International Workshop on FORmal methods for Security Engineering
812

Canfora, G., Martinelli, F., Mercaldo, F., Nardone, V., San-
tone, A., and Visaggio, C. A. (2018). Leila: formal
tool for identifying mobile malicious behaviour. IEEE
Transactions on Software Engineering.
Canfora, G., Medvet, E., Mercaldo, F., and Visaggio, C. A.
(2016). Acquiring and analyzing app metrics for ef-
fective mobile malware detection. In Proceedings of
the 2016 ACM International Workshop on Interna-
tional Workshop on Security and Privacy Analytics.
ACM.
Ceccarelli, M., Cerulo, L., and Santone, A. (2014). De
novo reconstruction of gene regulatory networks from
time series data, an approach based on formal meth-
ods. Methods, 69(3):298–305.
Chakraborty, D. and Chattopadhyay, M. (2020). Assign-
ment tracking on android platform. In Information
and Communication Technology for Sustainable De-
velopment, pages 491–499. Springer.
Cimitile, A., Martinelli, F., Mercaldo, F., Nardone, V.,
and Santone, A. (2017). Formal methods meet mo-
bile code obfuscation identification of code reorder-
ing technique. In 2017 IEEE 26th International Con-
ference on Enabling Technologies: Infrastructure for
Collaborative Enterprises (WETICE), pages 263–268.
IEEE.
Cimitile, A., Mercaldo, F., Nardone, V., Santone, A., and
Visaggio, C. A. (2018). Talos: no more ransomware
victims with formal methods. International Journal of
Information Security, 17(6):719–738.
Clarke, E. M., Grumberg, O., and Peled, D. A. (2001).
Model checking. MIT Press.
Cleaveland, R. and Sims, S. (1996). The NCSU concur-
rency workbench. In Computer Aided Verification, 8th
International Conference, CAV ’96, New Brunswick,
NJ, USA, July 31 - August 3, 1996, Proceedings, pages
394–397.
Enck, W., Gilbert, P., Han, S., Tendulkar, V., Chun, B.-
G., Cox, L. P., Jung, J., McDaniel, P., and Sheth,
A. N. (2014). Taintdroid: an information-flow track-
ing system for realtime privacy monitoring on smart-
phones. ACM Transactions on Computer Systems
(TOCS), 32(2):5.
Enck, W., Ongtang, M., and McDaniel, P. (2008). Mitigat-
ing android software misuse before it happens.
Fasano, F., Martinelli, F., Mercaldo, F., Nardone, V., and
Santone, A. (2019a). Spyware detection using tem-
poral logic. In 5th International Conference on Infor-
mation Systems Security and Privacy, ICISSP 2019,
pages 690–699. SciTePress.
Fasano, F., Martinelli, F., Mercaldo, F., and Santone, A.
(2019b). Energy consumption metrics for mobile de-
vice dynamic malware detection. Procedia Computer
Science, 159:1045–1052.
Fasano, F., Martinelli, F., Mercaldo, F., and Santone, A.
(2019c). Investigating mobile applications quality in
official and third-party marketplaces. In Proceed-
ings of the 14th International Conference on Evalu-
ation of Novel Approaches to Software Engineering,
pages 169–178. SCITEPRESS-Science and Technol-
ogy Publications, Lda.
Felt, A. P., Greenwood, K., and Wagner, D. (2010). The
effectiveness of install-time permission systems for
third-party applications. University of California at
Berkely, Electrical Engineering and Computer Sci-
ences, Technical report.
Felt, A. P., Ha, E., Egelman, S., Haney, A., Chin, E., and
Wagner, D. (2012). Android permissions: User atten-
tion, comprehension, and behavior. In Proceedings of
the eighth symposium on usable privacy and security,
page 3. ACM.
Foster, J. (2020). Who decides what is allowed? user inter-
actions and permissions use on android. ACM SIGAda
Ada Letters, 39(1):71–71.
Francesco, N. d., Lettieri, G., Santone, A., and Vaglini, G.
(2014). Grease: a tool for efficient “nonequivalence”
checking. ACM Transactions on Software Engineer-
ing and Methodology (TOSEM), 23(3):24.
Gradara, S., Santone, A., and Villani, M. L. (2005). Using
heuristic search for finding deadlocks in concurrent
systems. Information and Computation, 202(2):191–
226.
Huang, C.-Y., Tsai, Y.-T., and Hsu, C.-H. (2013). Perfor-
mance evaluation on permission-based detection for
android malware. In Advances in Intelligent Systems
and Applications-Volume 2, pages 111–120. Springer.
Jeon, J., Micinski, K. K., Vaughan, J. A., Reddy, N., Zhu,
Y., Foster, J. S., and Millstein, T. (2011). Dr. android
and mr. hide: Fine-grained security policies on un-
modified android. Technical report.
Kelley, P. G., Consolvo, S., Cranor, L. F., Jung, J., Sadeh,
N., and Wetherall, D. (2012). A conundrum of per-
missions: installing applications on an android smart-
phone. In International conference on financial cryp-
tography and data security, pages 68–79. Springer.
Martinelli, F., Marulli, F., and Mercaldo, F. (2017a). Eval-
uating convolutional neural network for effective mo-
bile malware detection. Procedia computer science,
112:2372–2381.
Martinelli, F., Mercaldo, F., Nardone, V., Santone, A., San-
gaiah, A. K., and Cimitile, A. (2018). Evaluating
model checking for cyber threats code obfuscation
identification. Journal of Parallel and Distributed
Computing, 119:203–218.
Martinelli, F., Mercaldo, F., and Saracino, A. (2017b).
Bridemaid: An hybrid tool for accurate detection of
android malware. In Proceedings of the 2017 ACM on
Asia Conference on Computer and Communications
Security, pages 899–901. ACM.
Mercaldo, F., Nardone, V., and Santone, A. (2016a). Ran-
somware inside out. In Availability, Reliability and
Security (ARES), 2016 11th International Conference
on, pages 628–637. IEEE.
Mercaldo, F., Nardone, V., Santone, A., and Visaggio, C. A.
(2016b). Download malware? no, thanks: how formal
methods can block update attacks. In Proceedings of
the 4th FME Workshop on Formal Methods in Soft-
ware Engineering, FormaliSE@ICSE 2016, Austin,
Texas, USA, May 15, 2016, pages 22–28. ACM.
Mercaldo, F., Nardone, V., Santone, A., and Visaggio,
C. A. (2016c). Ransomware steals your phone. for-
Android Run-time Permission Exploitation User Awareness by Means of Formal Methods
813

mal methods rescue it. In International Conference
on Formal Techniques for Distributed Objects, Com-
ponents, and Systems, pages 212–221. Springer.
Mercaldo, F., Visaggio, C. A., Canfora, G., and Cimitile, A.
(2016d). Mobile malware detection in the real world.
In Proceedings of the 38th International Conference
on Software Engineering Companion, pages 744–746.
ACM.
Milner, R. (1989). Communication and concurrency. PHI
Series in computer science. Prentice Hall.
Pearce, P., Felt, A. P., Nunez, G., and Wagner, D. (2012).
Addroid: Privilege separation for applications and ad-
vertisers in android. In Proceedings of the 7th ACM
Symposium on Information, Computer and Communi-
cations Security, pages 71–72. Acm.
Santone, A. (2002). Automatic verification of concur-
rent systems using a formula-based compositional ap-
proach. Acta Informatica, 38(8):531–564.
Santone, A. (2011). Clone detection through process alge-
bras and java bytecode. In IWSC, pages 73–74. Cite-
seer.
Stirling, C. (1989). An introduction to modal and temporal
logics for ccs. In Concurrency: Theory, Language,
And Architecture, pages 2–20.
Tchakount
´
e, F. (2014). Permission-based malware detec-
tion mechanisms on android: Analysis and perspec-
tives. Journal of Computer Science, 1(2).
Tchakount
´
e, F., Dayang, P., Nlong, J., and Check, N.
(2014). Understanding of the behaviour of android
smartphone users in cameroon: application of the se-
curity. Open J. Inf. Secur. Appl, pages 9–20.
Tramontana, E. and Verga, G. (2019). Mitigating privacy-
related risks for android users. In 2019 IEEE 28th In-
ternational Conference on Enabling Technologies: In-
frastructure for Collaborative Enterprises (WETICE),
pages 243–248. IEEE.
Zhou, Y. and Jiang, X. (2012). Dissecting android mal-
ware: Characterization and evolution. In Proceed-
ings of 33rd IEEE Symposium on Security and Privacy
(Oakland 2012).
ForSE 2020 - 4th International Workshop on FORmal methods for Security Engineering
814
