
New General Secret Sharing Scheme using Hierarchical Threshold
Scheme: Improvement of Information Rates for Specified Participants
Kouya Tochikubo
Department of Mathematical Information Engineering, College of Industrial Technology, Nihon University, Japan
Keywords:
Secret Sharing Scheme, General Access Structure, (k,n)-hierarchical Threshold Scheme, Key Management.
Abstract:
In 2015, a new secret sharing scheme realizing general access structures was proposed (T15). This scheme is
based on authorized subsets and the first scheme that can reduce the number of shares distributed to specified
participants. Reducing the numbers of shares distributed to specified participants is quite useful in secret
sharing schemes. However, this scheme needs to use many secret sharing schemes to obtain shares. In this
paper, we propose a new secret sharing scheme realizing general access structures. The proposed scheme can
reduce the number of secret sharing schemes to obtain shares by using Tassa’s (k,n)-hierarchical threshold
scheme instead of Shamir’s (k, n)-threshold scheme. Thus, the proposed scheme is more efficient than the
scheme A of T15 from the viewpoint of the number of secret sharing schemes to obtain shares.
1 INTRODUCTION
In (k,n)-threshold scheme (Shamir, 1979; Blakley,
1979), every group of k participants can recover the
secret K, but no group of less than k participants can
get any information about the secret from their shares.
The collection of all authorized subsets of partici-
pants is called the access structure. A (k,n)-threshold
scheme can only realize particular access structures
that contain all subsets of k or more participants. Se-
cret sharing schemes realizing more general access
structures than that of a threshold scheme were stud-
ied by numerous authors. Subsequently, Tassa pro-
posed a hierarchical threshold scheme using polyno-
mial derivatives (Tassa, 2007).
On the other hand, Ito, Saito and Nishizeki pro-
posed a multiple assignment secret sharing scheme
for general access structures and showed an explicit
share assignment algorithm for any access struc-
ture (Ito et al., 1987). Their scheme can realize an
arbitrary access structure by assigning one or more
shares to each participant. Benaloh and Leichter
proposed a secret sharing scheme for general ac-
cess structures based on a monotone-circuit (Benaloh
and Leichter, 1990). Secret sharing schemes which
have an explicit assignment algorithm for any access
structure are categorized by two types. One type is
schemes based on unauthorized subsets (Ito et al.,
1987; Tochikubo, 2004; Tochikubo, 2008). Another
type is schemes based on authorized subsets (Be-
naloh and Leichter, 1990; Tochikubo et al., 2005;
Tochikubo, 2013). In this paper, we focus on gen-
eral secret sharing schemes based on authorized sub-
sets. In the implementation of secret sharing schemes
for general access structures, an important issue is the
number of shares distributed to each participant. Ob-
viously, a scheme constructed of small shares is de-
sirable. However, in general, the existing secret shar-
ing schemes for general access structures are imprac-
tical in this respect when the size of the access struc-
ture is very large. Suppose that we want to apply se-
cret sharing schemes to a company. Here, we con-
sider a section which consists of two managers and
20 staff members. A secret can be recovered by a
group of two managers or groups of one manager and
two staff members. In this case, every manager be-
longs to 191 minimal authorized subsets and every
staff member belongs to 38 minimal authorized sub-
sets. We shall realize this access structure by general
secret sharing schemes. Then, each manager has to
hold so many shares. In 2015, a new secret sharing
scheme realizing general access structures was pro-
posed (T15) (Tochikubo, 2015). This scheme is based
on authorized subsets and the first scheme that can re-
duce the number of shares distributed to specified par-
ticipants though this scheme cannot reduce the num-
ber of shares distributed to every participant. There-
fore, reducing the numbers of shares distributed to
specified participants is quite useful in secret sharing
schemes. However, this scheme needs to use many
Tochikubo, K.
New General Secret Sharing Scheme using Hierarchical Threshold Scheme: Improvement of Information Rates for Specified Participants.
DOI: 10.5220/0009103506470654
In Proceedings of the 6th International Conference on Information Systems Security and Privacy (ICISSP 2020), pages 647-654
ISBN: 978-989-758-399-5; ISSN: 2184-4356
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
647

secret sharing schemes to obtain shares.
In this paper, we modify the scheme A of
T15 (Tochikubo, 2015) and propose a new secret
sharing scheme realizing general access structures.
The proposed scheme can reduce the number of
secret sharing schemes to obtain shares by using
Tassa’s (k, n)-hierarchical threshold scheme instead
of Shamir’s (k,n)-threshold scheme. On the other
hand, the number of shares distributed to each partici-
pant is equal to that of the scheme A of T15. Thus, the
proposed scheme is more efficient than the scheme A
of T15.
2 PRELIMINARIES
2.1 Secret Sharing Scheme
Let P = {P
1
,P
2
,·· · ,P
n
} be a set of n participants. Let
D(/∈ P ) denote a dealer who selects a secret and dis-
tributes a share to each participant. Let K and S de-
note a secret set and a share set, respectively. For sets
A and B, we denote a difference set by A − B. The
access structure Γ(⊂ 2
P
) is the family of subsets of
P which contains the sets of participants qualified to
recover the secret. For any authorized subset A ∈ Γ,
any superset of A is also an authorized subset. Hence,
the access structure should satisfy the monotone prop-
erty:
A ∈ Γ,A ⊂ A
0
⊂ P ⇒ A
0
∈ Γ.
Let Γ
0
be a family of the minimal sets in Γ, called the
minimal access structure. Γ
0
is denoted by
Γ
0
= {A ∈ Γ : A
0
6⊂ A for all A
0
∈ Γ − {A}}.
For any access structure Γ, there is a family of sets
¯
Γ = 2
P
− Γ.
¯
Γ contains the sets of participants un-
qualified to recover the secret. The family of maximal
sets in
¯
Γ is denoted by
¯
Γ
1
. That is,
¯
Γ
1
= {B ∈
¯
Γ : B 6⊂ B
0
for all B
0
∈
¯
Γ − {B}}.
In general, the efficiency of a perfect secret shar-
ing scheme is measured by the information rate
ρ (Stinson, 2005) defined as
ρ = min{ρ
i
: 1 ≤ i ≤ n},
ρ
i
=
log|K |
log|S(P
i
)|
where S (P
i
) denotes the set of possible shares that P
i
might receive. Obviously, a high information rate is
desirable. Throughout the paper, p is a large prime,
and let Z
p
be a finite field with p elements. In this
paper, we assume K = S = Z
p
.
2.2 Shamir’s Threshold Scheme
Shamir’s (k,n)-threshold scheme is described as fol-
lows (Shamir, 1979):
1. A dealer D chooses n distinct nonzero elements
of Z
p
, denoted by x
1
,x
2
,·· · ,x
n
. The values x
i
are
public.
2. Suppose D wants to share a secret K ∈ Z
p
, D
chooses k − 1 elements a
1
,a
2
,·· ·a
k−1
from Z
p
in-
dependently with the uniform distribution.
3. D distributes the share s
i
= f (x
i
) to P
i
(1 ≤ i ≤ n),
where
f (x) = K + a
1
x + a
2
x
2
+ ··· + a
k−1
x
k−1
is a polynomial over Z
p
.
It is known that Shamir’s (k,n)-threshold scheme
is perfect and ideal (Stinson, 2005; Karnin et al.,
1983). This implies that every k participants can re-
cover the secret K, but no group of less than k partic-
ipants can get any information about the secret.
The access structure of (k,n)-threshold scheme is
described as follows:
Γ = {A ∈ 2
P
: |A| ≥ k}.
2.3 Tassa’s Hierarchical Threshold
Scheme
Let P be a set of n participants and assume that P
is divided into m+ 1 disjoint subsets U
0
,U
2
,·· · ,U
m
,
i.e.
P =
m
[
i=0
U
i
and U
i
∩ U
j
= φ for all 0 ≤ i < j ≤ m.
Let k = {k
i
}
m
i=0
be a monotonically increasing se-
quence of integers 0 < k
0
< · ·· < k
m
. We set k =
k
m
. Tassa’s (k,n)-hierarchical threshold scheme is de-
scribed as follows (Tassa, 2007):
1. Suppose A dealer D wants to share a secret K ∈
Z
p
, D chooses k − 1 elements a
1
,a
2
,·· ·a
k−1
from
Z
p
independently with the uniform distribution
and defines a polynomial over Z
p
f (x) = K + a
1
x + a
2
x
2
+ ··· + a
k−1
x
k−1
.
2. D identifies each participant P ∈ P with a field
element. For simplicity, the field element that
corresponds to P
r
∈ P will be also denoted by
r (1 ≤ r ≤ n).
ICISSP 2020 - 6th International Conference on Information Systems Security and Privacy
648

3. D distributes the shares to all participants in the
following manner: Each participant of i th level in
the hierarchy P
r
∈ U
i
receives the share f
(k
i−1
)
(r)
where f
(k
i−1
)
(r) denotes the (k
i−1
) th derivative
of f (x) at x = r and k
−1
= 0.
The access structure of Tassa’s (k,n)-hierarchical
threshold scheme is described as follows:
Γ =
(
V ⊂ P :
V ∩
i
[
j=0
U
j
!
≥ k
i
,
∀i ∈ {0,1,. ..,m}
)
.
It is known that Tassa’s (k, n)-hierarchical thresh-
old scheme is perfect and ideal (Tassa, 2007).
Example 1: Let k = (k
0
,k
1
,k
2
) = (1,3,4), P =
{P
1
,P
2
,P
3
,P
4
,P
5
,P
6
} and
U
0
= {P
1
},
U
1
= {P
2
,P
3
,P
4
},
U
2
= {P
5
,P
6
}.
In this case, the access structure Γ and the minimal ac-
cess structure Γ
0
of Tassa’s ((1, 3,4), 6)-hierarchical
threshold scheme are described by
Γ=
(
V ⊂ P :
V ∩
i
[
j=0
U
j
!
≥ k
i
,∀i ∈ {0,1, 2}
)
and
Γ
0
= {{P
1
,P
2
,P
3
,P
4
},{P
1
,P
2
,P
3
,P
5
},
{P
1
,P
2
,P
3
,P
6
},{P
1
,P
2
,P
4
,P
5
},
{P
1
,P
2
,P
4
,P
6
},{P
1
,P
3
,P
4
,P
5
},
{P
1
,P
3
,P
4
,P
6
}},
respectively. Here, we shall realize this access struc-
ture by Tassa’s scheme.
1. D selects a random polynomial
f (x) = K + a
1
x + a
2
x
2
+ a
3
x
3
.
2. D distributes the share s
1
= f (1) to P
1
.
3. D distributes the share s
r
= f
0
(r) to P
r
(2 ≤ r ≤ 4),
where
f
0
(x) = a
1
+ 2a
2
x + 3a
3
x
2
.
4. D distributes the share s
r
= f
(3)
(r) to P
r
(5 ≤ r ≤
6), where
f
(3)
(x) = 6a
3
.
Tassa’s (k,n)-hierarchical threshold scheme can
realize more general access structures than that of
a threshold scheme. If i = 0, then Tassa’s (k, n)-
hierarchical threshold scheme coincides Shamir’s
(k, n)-threshold scheme.
2.4 Secret Sharing Schemes based on
Authorized Subsets
For P = {P
1
,P
2
,·· · ,P
n
}, K ∈ K and Γ, Benaloh and
Leichter’s scheme is described as follows (Benaloh
and Leichter, 1990):
1. Let Γ
0
= {A
1
,A
2
,·· · ,A
m
}. For A
i
∈ Γ
0
, com-
pute |A
i
| shares s
i,1
,s
i,2
,·· · ,s
i,|A
i
|
by using an
(|A
i
|,|A
i
|)-threshold scheme with K as a secret in-
dependently for 1 ≤ i ≤ m.
2. One distinct share from s
i,1
,s
i,2
,·· · ,s
i,|A
i
|
is
assigned to each P ∈ A
i
(1 ≤ i ≤ m).
Example 2: For P = {P
1
,P
2
,P
3
,P
4
,P
5
,P
6
}, consider
the following access structure
Γ
0
= {A
1
,A
2
,·· · ,A
6
}
where
A
1
= {P
1
,P
2
,P
5
,P
6
},
A
2
= {P
2
,P
3
,P
5
,P
6
},
A
3
= {P
2
,P
4
,P
5
,P
6
},
A
4
= {P
3
,P
4
,P
5
,P
6
},
A
5
= {P
1
,P
2
,P
3
,P
4
,P
5
},
A
6
= {P
1
,P
2
,P
3
,P
4
,P
6
}.
We shall realize this access structure by Benaloh and
Leichter’s scheme. In this case, shares are distributed
as follows:
P
1
: s
1,1
,s
5,1
,s
6,1
P
2
: s
1,2
,s
2,1
,s
3,1
,s
5,2
,s
6,2
P
3
: s
2,2
,s
4,1
,s
5,3
,s
6,3
P
4
: s
3,2
,s
4,2
,s
5,4
,s
6,4
P
5
: s
1,3
,s
2,3
,s
3,3
,s
4,3
,s
5,5
P
6
: s
1,4
,s
2,4
,s
3,4
,s
4,4
,s
6,5
where s
i, j
is computed by using Shamir’s
(|A
i
|,|A
i
|)-threshold scheme with K as a secret
(1 ≤ i ≤ 6, 1 ≤ j ≤ |A
i
|).
For P = {P
1
,P
2
,·· · ,P
n
},Q (⊂ P), K ∈ K and
Γ, the scheme A of T15 is described as fol-
lows (Tochikubo, 2015):
1. Let A
0
= {C ⊂ Q : Q ∩ A = C for some A ∈ Γ
0
}
and represent it as A
0
= {C
0
1
,C
0
2
,·· · ,C
0
m
}.
2. For C
0
i
∈ A
0
, let
A
i
= {B ⊂ P − Q : B ∩C
0
i
= φ
and B ∪C
0
i
= A for some A ∈ Γ
0
}
and represent it as A
i
= {C
i1
,C
i2
,·· · ,C
i|A
i
|
}.
New General Secret Sharing Scheme using Hierarchical Threshold Scheme: Improvement of Information Rates for Specified Participants
649

3. For C
0
i
∈ A
0
,
(i) if C
0
i
= φ then S
i
= {w
i
} and w
i
= K,
(ii) if C
0
i
6= φ and A
i
= {φ} then S
i
= {w
0
i
} and w
0
i
=
K,
(iii) if C
0
i
6= φ and A
i
6= {φ} then compute 2 shares
S
i
= {w
i
,w
0
i
} by using Shamir’s (2, 2)-threshold
scheme with K as a secret for 1 ≤ i ≤ m.
4. For C
0
i
∈ A
0
, if C
0
i
= φ then S
1,i
= φ, else compute
|C
0
i
| shares
S
1,i
= {s
0
i,1
,s
0
i,2
,·· · ,s
0
i,|C
0
i
|
}
by using Shamir’s (|C
0
i
|,|C
0
i
|)-threshold scheme
with w
0
i
as a secret for 1 ≤ i ≤ m. One distinct
share in S
1,i
is assigned to each P ∈C
0
i
(1 ≤ i ≤ m).
5. For C
i j
∈ A
i
, if C
i j
= φ then S
2,i, j
= φ, else com-
pute |C
i j
| shares
S
2,i, j
= {s
i, j,1
,s
i, j,2
,·· · ,s
i, j,|C
i j
|
}
by using Shamir’s (|C
i j
|,|C
i j
|)-threshold scheme
with w
i
as a secret for 1 ≤ i ≤ m, 1 ≤ j ≤ |A
i
|.
One distinct share in S
2,i, j
is assigned to each
P ∈ C
i j
(1 ≤ i ≤ m, 1 ≤ j ≤ |A
i
|).
Example 3: Let Q = {P
1
,P
2
}. We shall realize the
access structure of Example 2 by the scheme A of
T15.
• Since Q = {P
1
,P
2
}, A
0
is defined by
A
0
= {C
0
1
,C
0
2
,C
0
3
}
where
C
0
1
= {P
1
,P
2
},
C
0
2
= {P
2
},
C
0
3
= φ.
• A
1
,A
2
and A
3
are defined by
A
1
= {{P
5
,P
6
},{P
3
,P
4
,P
5
},{P
3
,P
4
,P
6
}},
A
2
= {{P
3
,P
5
,P
6
},{P
4
,P
5
,P
6
}},
A
3
= {{P
3
,P
4
,P
5
,P
6
}}.
• For C
0
1
,C
0
2
∈ A
0
, compute 2 shares
S
1
= {w
1
,w
0
1
},
S
2
= {w
2
,w
0
2
}
by using Shamir’s (2,2)-threshold scheme with K
as a secret. Since C
0
3
= φ, we set
S
3
= {w
3
} and w
3
= K.
• For C
0
1
,C
0
2
∈ A
0
, compute |C
0
i
| shares
S
1,1
= {s
0
1,1
,s
0
1,2
},
S
1,2
= {s
0
2,1
}
by using (|C
0
i
|,|C
0
i
|)-threshold scheme with w
0
i
as a
secret independently for 1 ≤ i ≤ 2. Since C
0
3
= φ,
we set
S
1,3
= φ.
• For C
i j
∈ A
i
, compute |C
i j
| shares
S
2,1,1
= {s
1,1,1
,s
1,1,2
},
S
2,1,2
= {s
1,2,1
,s
1,2,2
,s
1,2,3
},
S
2,1,3
= {s
1,3,1
,s
1,3,2
,s
1,3,3
},
S
2,2,1
= {s
2,1,1
,s
2,1,2
,s
2,1,3
},
S
2,2,2
= {s
2,2,1
,s
2,2,2
,s
2,2,3
},
S
2,3,1
= {s
3,1,1
,s
3,1,2
,s
3,1,3
,s
3,1,4
}
by using Shamir’s (|C
i j
|,|C
i j
|)-threshold scheme
with w
i
as a secret independently for 1 ≤ i ≤ 3,1 ≤
j ≤ |A
i
|.
• In this case, shares are distributed as follows:
P
1
: s
0
1,1
P
2
: s
0
1,2
,s
0
2,1
P
3
: s
1,2,1
,s
1,3,1
,s
2,1,1
,s
3,1,1
P
4
: s
1,2,2
,s
1,3,2
,s
2,2,1
,s
3,1,2
P
5
: s
1,1,1
,s
1,2,3
,s
2,1,2
,s
2,2,2
,s
3,1,3
P
6
: s
1,1,2
,s
1,3,3
,s
2,1,3
,s
2,2,3
,s
3,1,4
.
Benaloh and Leichter’s scheme needs shares for
each minimal authorized subset. On the other hand,
the scheme A of T15 can reduce the number of shares
distributed to each participant P ∈ Q (⊂ P ).
3 PROPOSED SCHEME
Here, we propose a new secret sharing scheme re-
alizing general access structures. In the proposed
scheme, we can select a subset of participants Q (⊂
P ) without restrictions. The proposed scheme can
reduce the number of shares distributed to P ∈ Q
by dividing Γ
0
into A
1
,A
2
,·· · ,A
m
according to the
subsets of Q in the same way as the scheme A of
T15. The proposed scheme can reduce the number
of secret sharing schemes to obtain shares by using
Tassa’s (k, n)-hierarchical threshold scheme instead
of Shamir’s (k,n)-threshold scheme. On the other
hand, the number of shares distributed to each par-
ticipant is equal to that of the scheme A of T15.
For P = {P
1
,P
2
,·· · ,P
n
},Q (⊂ P ), K ∈ K and Γ,
the proposed scheme is described as follows:
ICISSP 2020 - 6th International Conference on Information Systems Security and Privacy
650

1. Let A
0
= {C ⊂ Q : Q ∩ A = C for some A ∈ Γ
0
}
and represent it as A
0
= {C
0
1
,C
0
2
,·· · ,C
0
m
}.
2. For C
0
i
∈ A
0
, let
A
i
= {B ⊂ P − Q : B ∩C
0
i
= φ
and B ∪C
0
i
= A for some A ∈ Γ
0
}
and represent it as A
i
= {C
i1
,C
i2
,·· · ,C
i|A
i
|
}.
3. For C
0
i
∈ A
0
,
(i) if C
0
i
= φ then set
S
1,i
= φ,S
2,i
= {s
0
i,1
,s
0
i,2
,·· · ,s
0
i,|A
i
|
}
where s
0
i, j
= K(1 ≤ j ≤ |A
i
|),
(ii) if C
0
i
6= φ and A
i
= {φ} then compute |C
0
i
| shares
S
1,i
= {s
0
i,1
,s
0
i,2
,·· · ,s
0
i,|C
0
i
|
}
by using Shamir’s (|C
0
i
|,|C
0
i
|)-threshold scheme
with K as a secret,
(iii) if C
0
i
6= φ and A
i
6= {φ} then by using Tassa’s
((|C
0
i
|,|C
0
i
| + 1), |C
0
i
| + |A
i
|)-hierarchical thresh-
old scheme with K as a secret, compute |C
0
i
| +
|A
i
| shares
S
1,i
= {s
0
i,|A
i
|+1
,·· · ,s
0
i,|A
i
|+|C
0
i
|
},
S
2,i
= {s
0
i,1
,s
0
i,2
,·· · ,s
0
i,|A
i
|
}
as follows:
s
0
i, j
=
f ( j) (|A
i
| + 1 ≤ j ≤ |A
i
| + |C
0
i
|)
f
(|C
0
i
|)
( j) (1 ≤ j ≤ |A
i
|).
One distinct share in S
1,i
is assigned to each
P ∈ C
0
i
(1 ≤ i ≤ m).
4. For C
i j
∈ A
i
, if C
i j
= φ then S
2,i, j
= φ, else com-
pute |C
i j
| shares
S
2,i, j
= {s
i, j,1
,s
i, j,2
,·· · ,s
i, j,|C
i j
|
}
by using Shamir’s (|C
i j
|,|C
i j
|)-threshold scheme
with s
0
i, j
as a secret for 1 ≤ i ≤ m,1 ≤ j ≤ |A
i
|.
One distinct share in S
2,i, j
is assigned to each
P ∈ C
i j
(1 ≤ i ≤ m, 1 ≤ j ≤ |A
i
|).
Example 4: Let Q = {P
1
,P
2
}. We shall realize
the access structure of Example 2 by the proposed
scheme.
• Since Q = {P
1
,P
2
}, A
0
is defined by A
0
=
{C
0
1
,C
0
2
,C
0
3
} where
C
0
1
= {P
1
,P
2
},
C
0
2
= {P
2
},
C
0
3
= φ.
• A
1
,A
2
and A
3
are defined by
A
1
= {{P
5
,P
6
},{P
3
,P
4
,P
5
},{P
3
,P
4
,P
6
}},
A
2
= {{P
3
,P
5
,P
6
},{P
4
,P
5
,P
6
}},
A
3
= {{P
3
,P
4
,P
5
,P
6
}}.
• For C
0
1
,C
0
2
∈ A
0
, compute |C
0
i
| + |A
i
| shares
S
1,1
= {s
0
1,4
,s
0
1,5
},
S
1,2
= {s
0
1,1
,s
0
1,2
,s
0
1,3
},
S
2,1
= {s
0
2,3
},
S
2,2
= {s
0
2,1
,s
0
2,2
}
by using Tassa’s ((|C
0
i
|,|C
0
i
| + 1),|C
0
i
| + |A
i
|)-
hierarchical threshold scheme with K as a se-
cret (1 ≤ i ≤ 2). Since C
0
3
= φ, we set S
1,3
=
φ,S
2,3
= {s
0
3,1
} where s
0
3,1
= K
• For C
i j
∈ A
i
, compute |C
i j
| shares
S
2,1,1
= {s
1,1,1
,s
1,1,2
},
S
2,1,2
= {s
1,2,1
,s
1,2,2
,s
1,2,3
},
S
2,1,3
= {s
1,3,1
,s
1,3,2
,s
1,3,3
},
S
2,2,1
= {s
2,1,1
,s
2,1,2
,s
2,1,3
},
S
2,2,2
= {s
2,2,1
,s
2,2,2
,s
2,2,3
},
S
2,3,1
= {s
3,1,1
,s
3,1,2
,s
3,1,3
,s
3,1,4
}
by using Shamir’s (|C
i j
|,|C
i j
|)-threshold scheme
with s
0
i, j
as a secret for 1 ≤ i ≤ 3, 1 ≤ j ≤ |A
i
|.
• In this case, shares are distributed as follows:
P
1
: s
0
1,4
P
2
: s
0
1,5
,s
0
2,3
P
3
: s
1,2,1
,s
1,3,1
,s
2,1,1
,s
3,1,1
P
4
: s
1,2,2
,s
1,3,2
,s
2,2,1
,s
3,1,2
P
5
: s
1,1,1
,s
1,2,3
,s
2,1,2
,s
2,2,2
,s
3,1,3
P
6
: s
1,1,2
,s
1,3,3
,s
2,1,3
,s
2,2,3
,s
3,1,4
.
The next theorem shows the proposed scheme is
perfect.
Theorem 1. Let P = {P
1
,P
2
,·· · ,P
n
} be a set of n
participants. For any Q (⊂ P ) and any access struc-
ture Γ(⊂ 2
P
), distribute shares for a secret K by using
the proposed scheme A. Then, for any subset X ⊂ P ,
(a) X ∈ Γ ⇒ H(K|X ) = 0,
(b) X 6∈ Γ ⇒ H(K|X ) = H(K).
Proof: Let X
S
1,i
and X
S
2,i, j
denote the shares in S
1,i
and S
2,i, j
assigned to X, respectively(1 ≤ i ≤ m,1 ≤
j ≤ |A
i
|). At first, we show H(K|X) = 0 for any X ∈
New General Secret Sharing Scheme using Hierarchical Threshold Scheme: Improvement of Information Rates for Specified Participants
651
Γ. From the property of the access structure and the
definition of A
1
,·· · ,A
m
and A
0
, there exists A ∈ Γ
0
such that
C
0
i
∪C
i j
= A ⊂ X .
In this case, we have
|X
S
1,i
| = |C
0
i
| and |X
S
2,i, j
| = |C
i j
|.
Since s
i, j,1
,s
i, j,2
,·· · ,s
i, j,|C
i j
|
are shares computed by
Shamir’s (|C
i j
|,|C
i j
|)-threshold scheme with s
0
i, j
as a
secret, X can recover s
0
i, j
if C
i j
6= φ. From the defini-
tion of S
1,i
, S
2,i
and S
2,i, j
, we immediately obtain
H(K|X)
= H(K|X
S
1,1
,·· · ,X
S
1,m
,X
S
2,1,1
,·· · ,X
S
2,m,|A
m
|
)
≤ H(K|X
S
1,i
,X
S
2,i, j
)
= 0.
Since H(K|X) ≥ 0 is obvious, we have H(K|X) = 0
for any X ∈ Γ.
Next we show H(K|X) = H(K) for any X 6∈ Γ.
From the property of the access structure and the def-
inition of A
i
,·· · ,A
m
and A
0
, for any A
i
∈ Γ
0
, we have
C
0
i
6⊂ X or C
i j
6⊂ X (1 ≤ j ≤ |A
i
|).
This implies
H(K|X
S
1,i
,X
S
2,i, j
) = H(K).
for 1 ≤ i ≤ m,1 ≤ j ≤ |A
i
|. From the definition of S
1,i
,
S
2,i
and S
2,i, j
, we have
H(K|X
S
1,i
,X
S
2,i,1
,·· · ,X
S
2,i,|A
i
|
) = H(K)
for 1 ≤ i ≤ m. This implies
H(X
S
1,i
,X
S
2,i,1
,·· · ,X
S
2,i,|A
i
|
|K)
= H(X
S
1,i
,X
S
2,i,1
,·· · ,X
S
2,i,|A
i
|
). (1)
In order to show H(K|X) = H(K), we expand
H(K|X) as follows:
H(K|X)
= H(K|X
S
1,1
,·· · ,X
S
1,m
,X
S
2,1,1
,·· · ,X
S
2,m,|A
m
|
)
= H(K)
+H(X
S
1,1
,·· · ,X
S
1,m
,X
S
2,1,1
,·· · ,X
S
2,m,|A
m
|
|K)
−H(X
S
1,1
,·· · ,X
S
1,m
,X
S
2,1,1
,·· · ,X
S
2,m,|A
m
|
). (2)
From the chain rule for entropy, we have
H(X
S
1,1
,·· · ,X
S
1,m
,X
S
2,1,1
,·· · ,X
S
2,m,|A
m
|
|K)
=
m
∑
t=1
H(X
S
1,t
,X
S
2,t ,1
,·· · ,X
S
2,t ,|A
t
|
|K, X
S
1,1
,·· ·
··· , X
S
1,t −1
,X
S
2,1,1
,·· · ,X
S
2,t −1,|A
t−1
|
)
(∗)
=
m
∑
t=1
H(X
S
1,t
,X
S
2,t ,1
,·· · ,X
S
2,t ,|A
t
|
|K)
=
m
∑
t=1
H(X
S
1,t
,X
S
2,t ,1
,·· · ,X
S
2,t ,|A
t
|
). (3)
Here, (∗) comes from the fact that X
S
1,1
,·· · ,X
S
1,m
and
X
S
2,1,1
,·· · ,X
S
2,m,|A
m
|
are mutually independent and the
last equality comes from (1). On the other hand, we
have
H(X
S
1,1
,·· · ,X
S
1,m
,X
S
2,1,1
,·· · ,X
S
2,m,|A
m
|
)
=
m
∑
t=1
H(X
S
1,t
,X
S
2,t ,1
,·· · ,X
S
2,t ,|A
t
|
|X
S
1,1
,·· ·
··· , X
S
1,t −1
,X
S
2,1,1
,·· · ,X
S
2,t −1,|A
t−1
|
)
≤
m
∑
t=1
H(X
S
1,t
,X
S
2,t ,1
,·· · ,X
S
2,t ,|A
t
|
). (4)
Substituting (3) and (4) into (2), we obtain H(K|X) ≥
H(K). Since H(K|X) ≤ H(K) is obvious, we have
H(K|X) = H(K).
4 EVALUATION OF THE
EFFICIENCY
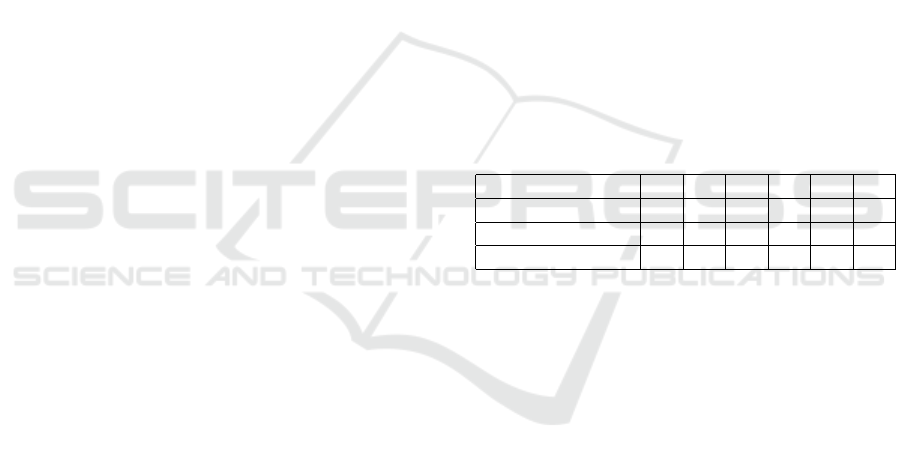
The number of shares distributed to P ∈ P for the ac-
cess structure of Example are described in Table 1.
Table 1: Comparison of the number of shares distributed to
P ∈ P .
P
1
P
2
P
3
P
4
P
5
P
6
Scheme of BL88 3 5 4 4 5 5
Scheme A of T15 1 2 4 4 5 5
Proposed scheme 1 2 4 4 5 5
This result shows that the proposed scheme and
the scheme A of T15 can reduce the numbers of shares
distributed to P ∈ Q .
Let N(P) be the number of shares distributed
to P ∈ P by using the proposed scheme. Similarly,
let N
BL
(P) and N
T 15
A
(P) be the number of shares
distributed to P ∈ P by using Benaloh and Leichter’s
scheme and the scheme A of T15, respectively. The
next theorem shows the number of shares distributed
to each participant is equal to that of the scheme A
of T15 in the proposed scheme and the proposed
scheme is more efficient than Benaloh and Leichter’s
scheme and from the viewpoint of the number of
shares distributed to each participant.
Theorem 2. For any P ∈ P , the number of shares
distributed to P is evaluated as follows:
N(P) =
N
BL
(P) −
m
∑
i=1
|{P} ∩C
0
i
|(|A
i
| − 1) (P ∈ Q )
N
BL
(P) (P /∈ Q ),
N(P) = N
T 15
A
(P) (P ∈ P ).
ICISSP 2020 - 6th International Conference on Information Systems Security and Privacy
652

Proof: From the definition of A
1
,·· · ,A
m
and A
0
,
N(P) and N
T 15
A
(P) are obtained by
N(P) = N
T 15
A
(P) = |{C
0
∈ A
0
: P ∈ C
0
}|
=
m
∑
i=1
|{P} ∩C
0
i
| (5)
for P ∈ Q . On the other hand, N
BL
(P) is obtained by
N
BL
(P) = |{X ∈ Γ
0
: P ∈ X }|. (6)
From the definition of A
1
,·· · ,A
m
and A
0
, we have
{X ∈ Γ
0
: P ∈ X} =
m
[
i=1
{C
0
i
∪C : P ∈ C
0
i
,C ∈ A
i
} (7)
for P ∈ Q . From (6) and (7), we have
N
BL
(P) =
m
∑
i=1
|{C
0
i
∪C : P ∈ C
0
i
,C ∈ A
i
}|
=
m
∑
i=1
|{P} ∩C
0
i
| · |A
i
| (8)
for P ∈ Q .
Similarly, N(P) and N
T 15
A
(P) are obtained by
N(P) = N
T 15
A
(P) =
m
∑
i=1
|{C ∈ A
i
: P ∈ C}| (9)
for P 6∈ Q . From the definition of A
1
,·· · ,A
m
and A
0
,
we have
{X ∈ Γ
0
: P ∈ X } =
m
[
i=1
{C
0
i
∪C : P ∈ C ∈ A
i
} (10)
for P 6∈ Q . From (6) and (10), we have
N
BL
(P) =
m
∑
i=1
|{C
0
i
∪C : P ∈ C ∈ A
i
}|
=
m
∑
i=1
|{C ∈ A
i
: P ∈ C}| (11)
for P 6∈ Q . Theorem 2 is easily obtained by (5), (8),
(9) and (11).
Here, we evaluate the number of secret sharing
schemes to obtain shares. Table 2 shows the number
of secret sharing schemes to obtain shares for Exam-
ple.
This result shows that the proposed scheme can
reduce the number of secret sharing schemes to ob-
tain shares. Actually, we can reduce |A
0
− {φ}| secret
sharing schemes at most.
Let N
0
be the number of secret sharing schemes
to obtain shares in the proposed scheme. Similarly,
let N
0
BL
and N
0
T 15
A
be the number of secret sharing
schemes to obtain shares in Benaloh and Leichter’s
scheme and the scheme A of T15, respectively.
Table 2: Comparison of the number of secret sharing
schemes.
Shamir’s Tassa’s total
schemes schemes
Scheme of BL88 6 0 6
Scheme A of T15 10 0 10
Proposed scheme 6 2 8
The next theorem shows the proposed scheme is
more efficient than the scheme A of T15 from the
viewpoint of the number of secret sharing schemes to
obtain shares.
Theorem 3. The number of secret sharing schemes
to obtain shares is evaluated as follows:
N
0
BL
= |Γ
0
|,
N
0
T 15
A
≤ |Γ
0
| + 2|A
0
− {φ}|,
N
0
≤ |Γ
0
| + |A
0
− {φ}|.
Proof: Benaloh and Leichter’s scheme uses secret
sharing schemes for each minimal authorized subset
A
i
in Γ
0
. Thus, we have
N
0
BL
= |Γ
0
|.
The scheme A of T15 uses secret sharing schemes for
each C
0
i
in A
0
−{φ} to obtain S
i
(1 ≤ i ≤ m), C
0
i
in A
0
−
{φ} to obtain S
1,i
(1 ≤ i ≤ m) and C
i j
in A
i
to obtain
S
2,i, j
(1 ≤ i ≤ m,1 ≤ j ≤ |A
i
|). The proposed scheme
uses secret sharing schemes for each C
0
i
in A
0
− {φ}
to obtain S
1,i
and S
2,i
(1 ≤ i ≤ m) and C
i j
in A
i
− {φ}
to obtain S
2,i, j
(1 ≤ i ≤ m, 1 ≤ j ≤ |A
i
|).
On the other hand, from the definition of
A
1
,·· · ,A
m
and A
0
, we have
m
∑
i=1
|A
i
| ≤ |Γ
0
|.
Thus, we obtain
N
0
T 15
A
≤ |Γ
0
| + 2|A
0
− {φ}|,
N
0
≤ |Γ
0
| + |A
0
− {φ}|.
5 CONCLUSION
We have proposed a new secret sharing scheme real-
izing general access structures. The proposed scheme
can reduce the number of secret sharing schemes
to obtain shares by using Tassa’s (k,n)-hierarchical
threshold scheme instead of Shamir’s (k,n)-threshold
scheme. On the other hand, the number of shares
distributed to each participant is equal to that of the
scheme A of T15.
New General Secret Sharing Scheme using Hierarchical Threshold Scheme: Improvement of Information Rates for Specified Participants
653

ACKNOWLEDGEMENTS
This work was supported by JSPS KAKENHI Grant
Number 18K11303.
REFERENCES
Benaloh, J. and Leichter, J. (1990). Generalized secret
sharing and monotone functions. In Proceedings on
Advances in Cryptology, CRYPTO ’88, pages 27–35,
Berlin, Heidelberg. Springer-Verlag.
Blakley, G. R. (1979). Safeguarding cryptographic keys. In
1979 International Workshop on Managing Require-
ments Knowledge (MARK), pages 313–318.
Ito, M., Saito, A., and Nishizeki, T. (1987). Secret sharing
scheme realizing general access structure. In Proc.
IEEE Globecom’87, pages 99–102.
Karnin, E., Greene, J., and Hellman, M. (1983). On secret
sharing systems. IEEE Transactions on Information
Theory, 29(1):35–41.
Shamir, A. (1979). How to share a secret. Commun. ACM,
22(11):612–613.
Stinson, D. R. (2005). Cryptography: theory and practice.
CRC Press, 3rd edition.
Tassa, T. (2007). Hierarchical threshold secret sharing.
Journal of Cryptology, 20:237–264.
Tochikubo, K. (2004). Efficient secret sharing schemes
realizing general access structures. IEICE Transac-
tions on Fundamentals of Electronics, Communica-
tions and Computer Sciences, E87-A(7):1788–1797.
Tochikubo, K. (2008). Efficient secret sharing schemes
based on unauthorized subsets. IEICE Transac-
tions on Fundamentals of Electronics, Communica-
tions and Computer Sciences, E91-A(10):2860–2867.
Tochikubo, K. (2013). New construction methods of secret
sharing schemes based on authorized subsets. Infor-
mation and Media Technologies, 8(4):978–986.
Tochikubo, K. (2015). New secret sharing schemes realiz-
ing general access structures. Journal of Information
Processing, 23(5):570–578.
Tochikubo, K., Uyematsu., T., and Matsumoto, R. (2005).
Efficient secret sharing schemes based on autho-
rized subsets. IEICE Transactions on Fundamentals
of Electronics, Communications and Computer Sci-
ences, E88-A:322–326.
ICISSP 2020 - 6th International Conference on Information Systems Security and Privacy
654
