
Are the Healthcare Institutions Ready to Comply with Data Traceability
Required by GDPR? A Case Study in a Portuguese Healthcare
Organization
C
´
atia Santos-Pereira
1,2 a
, Alexandre B. Augusto
1
, Jos
´
e Castanheira
3
, Tiago Morais
3
and Ricardo Correia
1,4
b
1
HealthySystems, Porto, Portugal
2
Faculdade de Engenharia da Universidade do Porto, Porto, Portugal
3
Unidade Local de Sa
´
ude de Matosinhos, Porto, Portugal
4
CINTESIS – Centro de Investigac¸
˜
ao em Tecnologias e Servic¸os de Sa
´
ude, Porto, Portugal
Keywords:
Audit-trail, Audit-log, GDPR, Security, Data Privacy, Traceability, Healthcare.
Abstract:
GDPR introduces a new concept: ”Data protection by design and per default” for new software development
however legacy systems will also have to adapt in order to comply. This creates great pressure on health care
institutions, namely hospitals, and software producers to provide data protections and traceability mechanisms
for their current and legacy systems. The aim of this work is to understand the maturity level of a Portuguese
Healthcare Organization in their audit records to comply with GDPR article 30 and 32 since healthcare orga-
nization operate in a daily-basis with personal data. This study was performed with the partnership of a public
Portuguese healthcare organization and were organized into three main phases: (1) data collection of all in-
formation systems that operate with personal data; (2) interviews with IT professionals in order to retrieve the
necessary knowledge for each information system and (3) analysis of the collected data and its conclusions.
This study helped to identify a need inside this organization and to determine a follow-up plan to overpass
this challenge. However it also identified some constrains like financial budget, legacy systems, small team
of IT professionals in the organization and difficulties in establish communication with information system
providers.
1 INTRODUCTION
In 2016, the European Commission proposed to re-
place the Directive (95/46/EC) (Europ
´
een et du Con-
seil, 1995) by the General Data Protection Regulation
(GDPR) (Comission, 2016). The overall intention of
this reform is to mitigate data access and security con-
cerns giving citizens back control over their personal
data, and to simplify the regulatory environment for
business in the digital economy (Skend
ˇ
zi
´
c, 2018)
In order to ensure free secure flow of personal
data, GDPR introduces a new concept: ”Data protec-
tion by design and per default”. This concept is ap-
plied to all products and services aimed or used in the
European market must be designed with data protec-
tion in mind from the earliest stages of development
(Colesky, 2016).
a
https://orcid.org/0000-0001-8425-6342
b
https://orcid.org/0000-0002-3764-5158
In particular the GDPR articles 30 and 32 focus
in the importance of establish record of the activities
and a process to operate over it in order to guaran-
tee data security. Meanwhile the article 30 propose
is to define the necessary information to establish a
complete record for the activities, the article 32 tar-
get the ability to ensure the ongoing confidentiality,
integrity, availability and resilience of processing sys-
tems and services. The article 32 also states that or-
ganization shall define a process for regularly testing,
assessing and evaluating the effectiveness of technical
and organizational measures for ensuring the security
(Comission, 2016), (Haug, 2018). This creates great
pressure on healthcare institutions, namely hospitals,
and software producers to provide auditable traceabil-
ity mechanisms for their current and legacy systems
(Gonc¸alves-Ferreira, 2018).
One way to apply traceability mechanisms is to
implement audit log system. All actors such as infor-
mation systems, processes, and services involved in
Santos-Pereira, C., Augusto, A., Castanheira, J., Morais, T. and Correia, R.
Are the Healthcare Institutions Ready to Comply with Data Traceability Required by GDPR? A Case Study in a Portuguese Healthcare Organization.
DOI: 10.5220/0009000405550562
In Proceedings of the 13th International Joint Conference on Biomedical Engineering Systems and Technologies (BIOSTEC 2020) - Volume 5: HEALTHINF, pages 555-562
ISBN: 978-989-758-398-8; ISSN: 2184-4305
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
555

an auditable event should record an Audit Log. This
will likely result in multiple Audit Log entries that
show whether privacy and security safeguards, such
as access control, are properly functioning across an
enterprise’s system-of-systems (Kong, 2012). Thus,
it is typical to get an auditable event recorded by
both the application in a workflow process and the
servers that support them. For this reason, duplicate
entries are expected, which is helpful because it may
aid in the detection of. For example, fewer than ex-
pected actors being recorded in a multi-actor process
or attributes related to those records being in conflict,
which is an indication of a security problem (Mar-
gulies, 2015).
The content of an Audit Log is intended for use
by security system administrators, security and pri-
vacy information managers, and records management
personnel. This content is not intended to be acces-
sible or used directly by other healthcare users, such
as providers or patients, although reports generated
from the raw data would be useful. An example is a
patient-centric accounting of disclosures or an access
report. Servers that provide support for Audit Log re-
sources would not generally accept update or delete
operations on the resources, as this would compro-
mise the integrity of the audit record. Access to the
Audit Log would typically be limited to security, pri-
vacy, or other system administration purposes (Jaya-
balan, 2017), (Kent and Souppaya, 2006).
Portugal has an extensive information infrastruc-
ture, which plays a central role in supporting health-
care provision, but not all data sources are effectively
connected and some challenges in patient privacy and
the legal basis for connecting patient data remain
(Sim
˜
oes, 2017). Health Information Systems de-
ployed in Hospitals or primary care units were mainly
devoted to support local performed operational tasks
and were implemented without an integrated perspec-
tive, leading with a great heterogeneity and data du-
plication (Pinto, 2016).
Ineffective data management, compliance issues,
and cyber security risks are often linked with not hav-
ing systematic approaches to investments in people,
processes, and technology. Dated technology is ev-
erywhere and connected to everything— not just on
desktop PCs. Many employees at hospitals, health
plans, life sciences companies, and governments lack
awareness of and training to manage financial, oper-
ational, compliance, and cybersecurity risks (Cooper,
2018).
These constitutes a major problem when health
care institutions have to manage a vast amount of ap-
plication, as observed in many public hospitals in Por-
tugal.
Since the date of effect, GDPR takes at least
ninety-one GDPR violations identified by data protec-
tion authorities around Europe, as published by CMS
(CMS, 2019). Since not all fines are made public, this
number cannot be complete. Inside healthcare sec-
tor at least two violations are reported, the fines and
penalties are around 400.000 euros. The first iden-
tified GDPR violation in the healthcare sector hap-
pened in Portugal and was reported by the Portuguese
Data Protection Authority. The investigation in Cen-
tro Hospitalar Barreiro Montijo revealed that the hos-
pital’s staff, psychologists, dietitians and other profes-
sionals had access to patient data through false pro-
files. Portuguese Data Protection Authority identified
that the identity management system appeared defi-
cient – since the hospital had 985 registered doctor
profiles while only having 296 doctors. Moreover,
doctors had unrestricted access to all patient files, re-
gardless of the medical doctor’s specialty. These is-
sues events revealed violation of Article 5 (1) f) and
Article 32 (CNPD, 2018) (Monteiro, 2019). The sec-
ond case was reported by Dutch Supervisory Author-
ity for Data Protection in Haga Hospital. It was de-
tected a violation of Art. 32 GDPR (European Comis-
sion;, 2016), because this Hospital does not imple-
ment a proper internal security of patient records in
place. The investigation followed by Dutch Super-
visory Authority for Data Protection concludes that
dozens of hospital staff had unnecessarily checked the
medical records of a well-known Dutch person (Per-
soonsgegevens, 2019).
The aim of this work is to understand the maturity
level of a Portuguese Healthcare Organization in their
audit records to comply with GDPR article 30 and 32
since healthcare organizations operate in a daily-basis
with sensitive personal data. To achieve this goal it
was selected a Portuguese Healthcare Organization
and with the hospital Information Technology (IT) de-
partment collaboration it was compiled the character-
istics of their information systems with a particularly
focus in the audit-log records of the activities.
2 METHODS
In this section will be presented the methodology used
to performed this study. In particular it will be pre-
sented the study design, the setting and participants.
2.1 Participants
This study was performed with the partnership of a
public Portuguese healthcare organization (Unidade
Sa
´
ude Local) constituted by a Hospital and 18 (eigh-
HEALTHINF 2020 - 13th International Conference on Health Informatics
556
teen) primary care units. The Hospital has capacity
for 342 beds. This organization provides healthcare
services for more than 173.000 citizens. The main ob-
jectives of this organization are: (1) provide primary
care and continuous health care to the county’s pop-
ulation; differentiated healthcare to the population of
the area of influence, and others that address it; (2) en-
sure public health activities and the means necessary
for the exercise of competencies of the health author-
ity in the county; (3) ensure the provision of primary,
differentiated and continuous care, in and integrated
way, embodying a continuum of patient-centered; and
(4) promote the process of research and continuous
education, pre and postgraduate, of sector, providing
for the conclusion of agreements with the competent
authorities.
2.2 Study Design and Setting
The study is organized into 3 (three) main phases,
enumerated below:
1. Data collection of all information systems imple-
mented that lead with personal data;
2. Interview with IT responsible with the objective
of answer the following questions for each infor-
mation system:
• The information system has audit logs?
• The audit logs are accessible by the organiza-
tion?
• The audit logs are structured?
• Which are the content of the audit logs (e.g. ap-
plicational errors, access information)?
3. To analyse the collected information and system-
atize the results.
The interview was performed to the head ot IT de-
partment and his team.
3 RESULTS
In this section it will be present the results of the
study. First it will be presented the characterization
of the Information systems implemented in the orga-
nization, then it was explored the audit logs available
(structure and content), in the last sub-section it will
be presented the audit logs access and use by the or-
ganization studied.
3.1 Information Systems
Characterization
It were identified 64 (sixty-four) information systems
in the organization that treat personal data (including
both patients personal data and collaborators) from 23
(twenty-three) suppliers. The oldest information sys-
tem was implemented in 1997 and since that year this
organization started a dematerialization process until
nowadays.
Fifty seven of all information systems are elec-
tronic medical information systems for the different
departments systems (89%), five information systems
with the purpose of employees management (8%) and
only two information systems are for financial and lo-
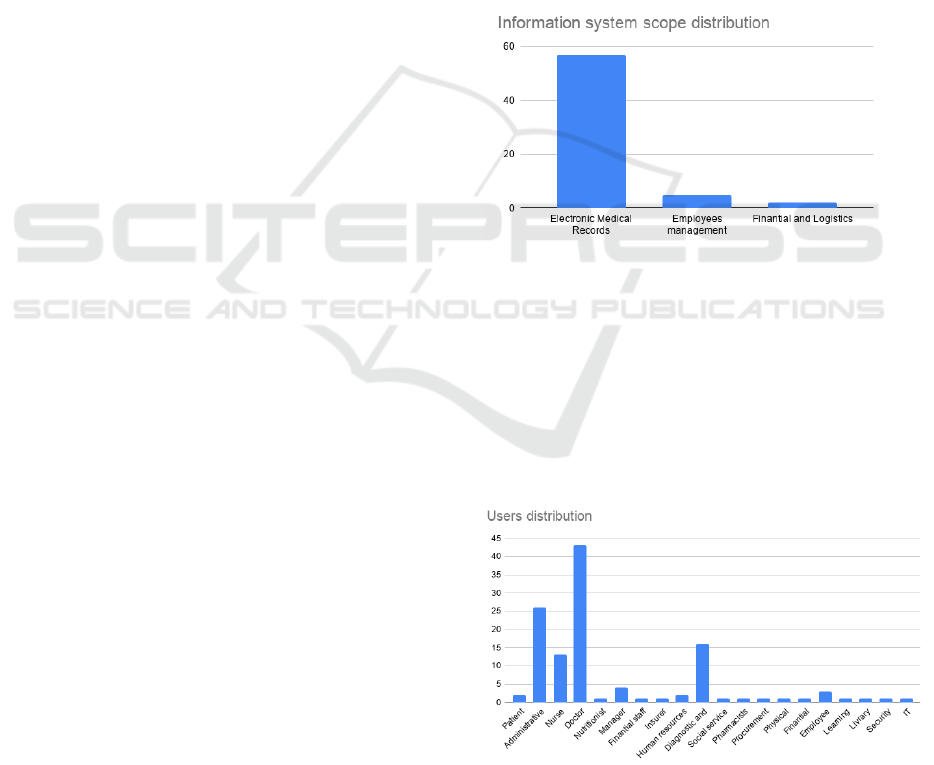
gistic department (3%) as represented in Figure 1.
Figure 1: Information system scope distribution.
Regarding users, the majority of the users are
medical doctors, administrative, nurses and diagnos-
tic and therapeutic technicians. Others users were
identified like IT and financial staff, nutritionist, phar-
macists, social service, Insurer, library users, building
security, formation, infrastructures, procurement, em-
ployee and also patients. This distribution is repre-
sented in Figure 2.
Figure 2: Users distribution.
In terms of data repository the majority of infor-
mation systems are located inside the organization,
Are the Healthcare Institutions Ready to Comply with Data Traceability Required by GDPR? A Case Study in a Portuguese Healthcare
Organization
557
however thirty four percent of the information sys-
tems are located outside namely in ministry of health,
North Regional Health Administration, an external
organization and in the Portuguese Healthcare Reg-
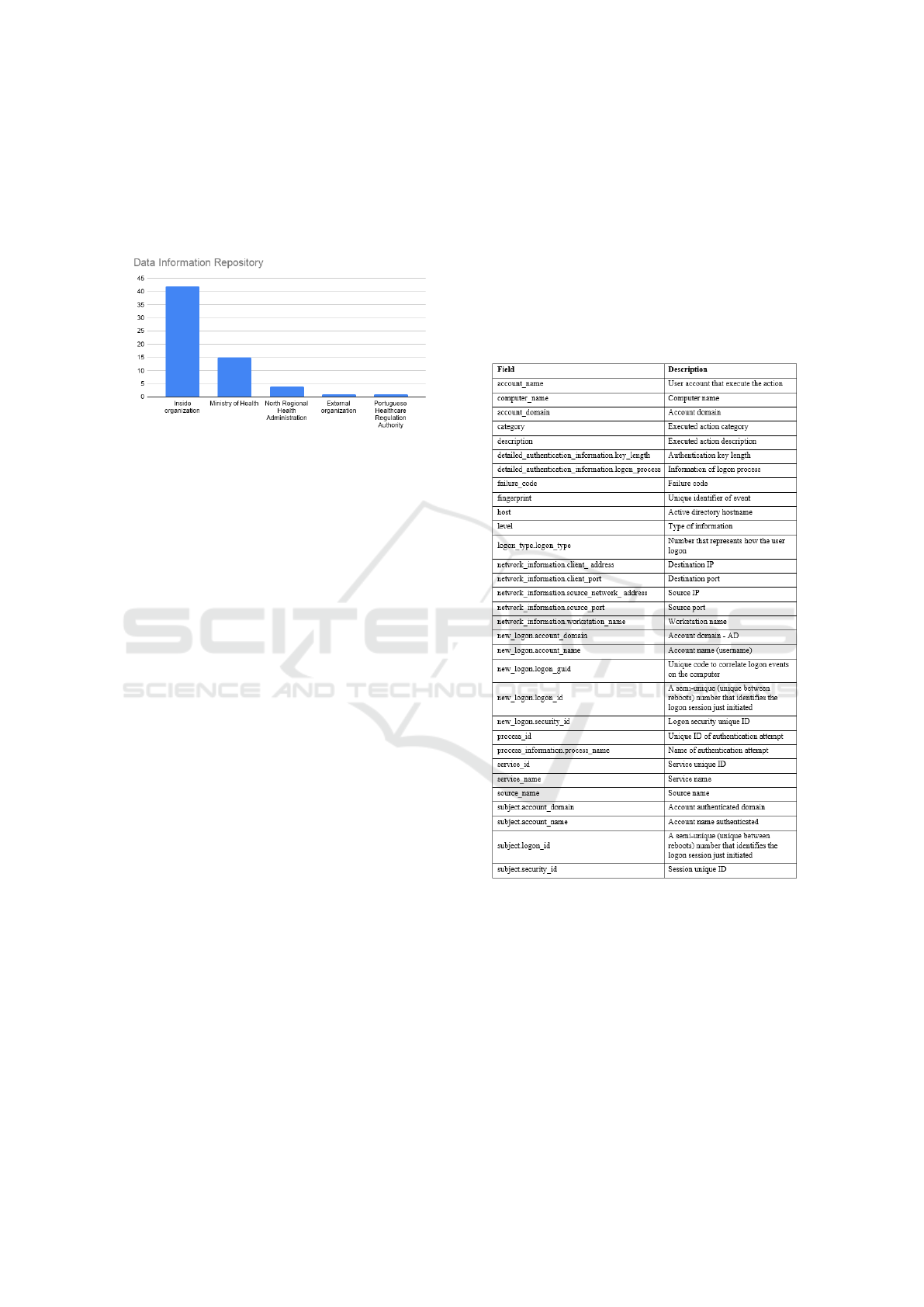
ulation Authority as showed in Figure 3.
Figure 3: Data Information Repository.
3.2 Audit Logs
The results revealed that in the universe of sixty-four
information systems, the organization only has access
to audit logs from three information systems and from
their interoperability platform that record logs from
the communication between systems. The informa-
tion system that provides audit logs are: (1) active di-
rectory; (2) Electronic Health Record, (3) Electronic
medical system for women’s health care and a (4) in-
teroperability platform.
One reason that explains this number is that thirty
four percent of the sixty four information systems
are located outside of the organization namely in the
Portuguese ministry of health, North Regional Health
Administration, an external organization and in the
Portuguese Healthcare Regulation Authority.
In this subsection will be presented the three in-
formation system (active directory, electronic health
record and electronic medical system for women’s
health care) that contains audit logs and the interop-
erability platform which contain all events integrated
between different information systems.
3.2.1 Audit Logs Structure and Content
As mentioned before it will be present the audit logs
structure and content for the three information sys-
tems and the interoperability platform.
• Microsoft - Active Directory (AD)
This system is a directory service developed by
Microsoft, it authenticates and authorizes all users
and computers in a Windows domain type net-
work—assigning and enforcing security policies
for all computers and installing or updating soft-
ware.
The organization studied implemented this tech-
nology to give support for the authentication and
authorization of all collaborators in desktops in-
side the organization. AD allows to extract audit
logs of the users activity, namely authentication
and authorization in desktops but also in informa-
tion systems that are integrated in AD.
This Microsoft tool allows to analyse and export
the logs via Windows Event Viewer. The Figure
4 presents the audit record fields of authentication
process and its descriptions.
Figure 4: Audit log event - active directory.
• Electronic Health Record - Sonho/Sclinico
Sonho/Sclinico is the most used health informa-
tion system used in this organization. This sys-
tem gives support to outpatient, inpatient, operat-
ing room, ambulatory surgery, day hospital, pri-
mary care (outpatient) and primary care (emer-
gency care) (Pav
˜
ao, 2016).
The main end-users are medical doctors, nurses
and nutritionist according to the different modules
available.
HEALTHINF 2020 - 13th International Conference on Health Informatics
558
The IT department of this organization, due to the
relevance of this system, decides to start produc-
ing and collecting audit logs through database ta-
bles access.
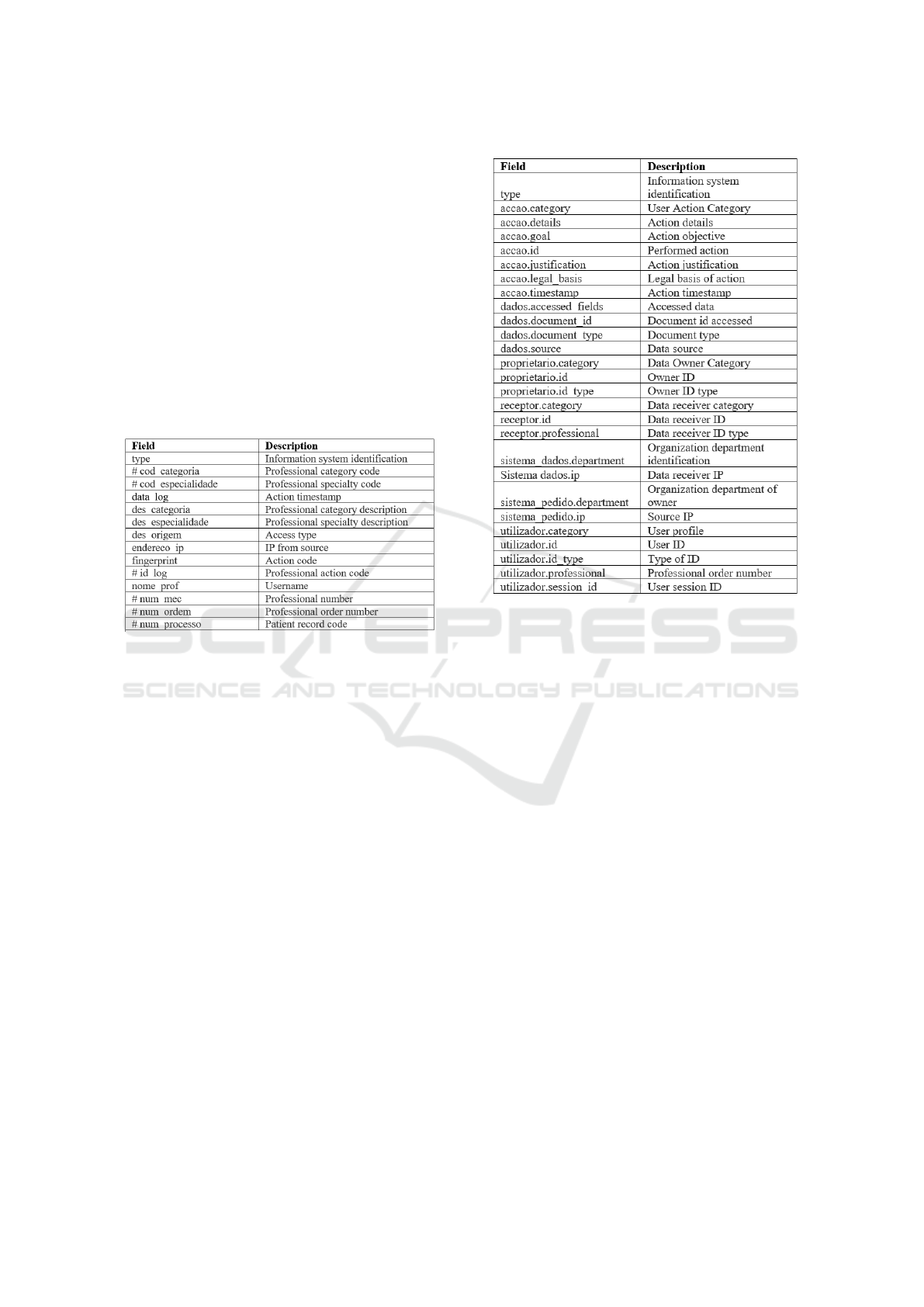
The Figure 5 presents a sample of fields and it de-
scription of the EHR audit log available. In partic-
ular, It includes information about patient (patient
record number), healthcare professional (identi-
fication, category, speciality, name, professional
order number, internal number), characterization
of access (IP, access type, timestamp) and char-
acterization of actions (action code). This audit
log is stored in a database table that was specially
crafted by the Healthcare Organization in order to
keep readable traceability records.
Figure 5: Electronic Health Record log description.
• Departmental Electronic Medical System:
Women’S Health Care
This Electronic Medical Record (EMR) has the
specific goal of meet the need for an obstetric-
specific record and is currently in use in the ob-
stetrical/ gynaecological department. The main
end-users are medical doctors and nurses.
The audit logs provided by this software vendor is
under the GDPR requirements from article 30 by
following the information requirement for a activ-
ity record.
The Figure 6 shows a sample of fields and it de-
scription that compose the audit log from this sys-
tem. This audit log have more fields than the
previous systems, beyond the identification of pa-
tient, healthcare professional and characterization
of access, it also includes a more detailed infor-
mation about what information was accessed and
which actions were performed by the user. In or-
der to access this audit log the organization needs
to access the provider server and retrieve a JSON
format file.
• Interoperability Platform - HS.Helios
The interoperability platform, HS.Helios, has the
Figure 6: Departmental Electronic medical system
(women’s health care) log description.
ability to standardize and exchange health infor-
mation like patient data from different informa-
tions systems. The most common format for data
exchange in healthcare in Portugal is the Health
Level 7 (HL7) version 2, also a newer version
of HL7 known as Fast Healthcare Interoperabil-
ity Resources (FHIR) starts gain some popularity.
More than exchange health information,
HS.Helios, also checks the integrity of ex-
changed messages and monitor the integrations in
real time, allowing the extraction of performance
metrics related to Health Information Systems
integrations of distinct vendors. Furthermore
it is also possible to create audit records of the
exchanged messages. These audit records follows
the Integrating the Healthcare Enterprise (IHE)
Audit Trail and Node Authentication (ATNA)
(IHE, 2019) format that complies with GDPR.
Figure 7 shows the systems that communicate
through this interoperability platform, so it is pos-
sible to extract audit records of each integration
(for example laboratory exams requisitions per-
formed by EMR women’s health care information
systems or laboratory exam requests and results
that came from the emergency department). The
platform also allow to consult these audit records
Are the Healthcare Institutions Ready to Comply with Data Traceability Required by GDPR? A Case Study in a Portuguese Healthcare
Organization
559
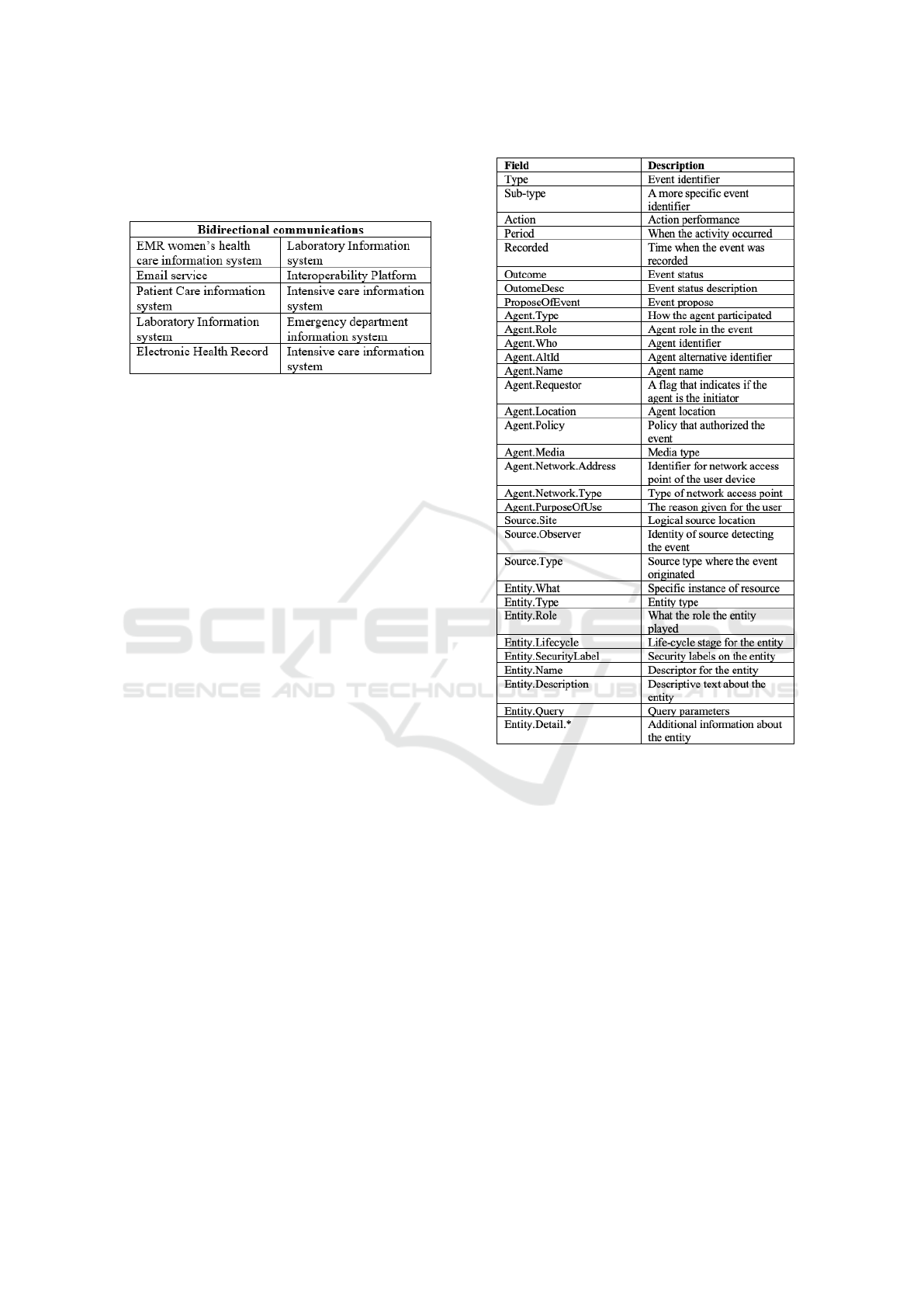
through a web platform allowing the institute to
query over the audit records in a easy and simple
way.
Figure 7: HL7 communications recorded in audit logs.
Figure 8 presents the structure of audit-logs pro-
duced and available in interoperability platform.
This records follows the structure audit event of
the standard HL7 FHIR R4 (HL7.org, 2018) and
is compliant with IHE-ATNA and GDPR estab-
lishing a strong format to produce well detailed
activity record.
3.2.2 Audit Logs Access and Use by
Organization
Concerning the access to audit records, the organiza-
tion mentioned that they rarely access the logs or are
asked to access it. It was also mentioned that very few
professionals outside the IT department know that is
even possible to collect this kind of data, and that if
other professionals knew about that data maybe they
would ask for it.
To access these audit logs the organization needs
to access each systems individually as represented in
Figure 9. The available of these audit logs is compli-
cated (direct access to database tables or third party
systems only used by IT department) and hard to un-
derstand for non-IT professionals, so the secondary
use of data is conditioned.
4 DISCUSSION
After four years of preparation and debate in the
European Union Parliament, the General Data Pro-
tection Regulation (GDPR) came into force in May
2018. Now, more than one year after the most im-
portant shift in data privacy regulation in 20 years ap-
proaches, widespread changes are already being felt
in the healthcare industry, which is facing multiple
challenges to protect sensitive data.
The overall results of this study reveals that the
healthcare organizations are facing a complex chal-
Figure 8: Audit log event - interoperability platform.
lenge. This healthcare organization as many others
even in different sectors in Portugal have a huge num-
ber of legacy information systems to manage. Some
of information system providers already bankrupt and
it is not possible to update the service. These difficul-
ties allied to financial budget constraints constitutes a
hard work to complete. During the study the organi-
zation became more aware of their difficulties, mainly
in the complexity in access the audit logs since many
of systems did not have audit logs available and even
two of three systems (Sonho/Sclinico EHR,Electronic
medical system for women’s health care, MS Active
Director) that have audit logs were not fully compliant
with article 20 of GDPR in their installed versions.
In an universe of sixty four information systems,
at the moment of the study they only could access
three of the information systems and their interoper-
ability platform. As mentioned before twenty two of
HEALTHINF 2020 - 13th International Conference on Health Informatics
560
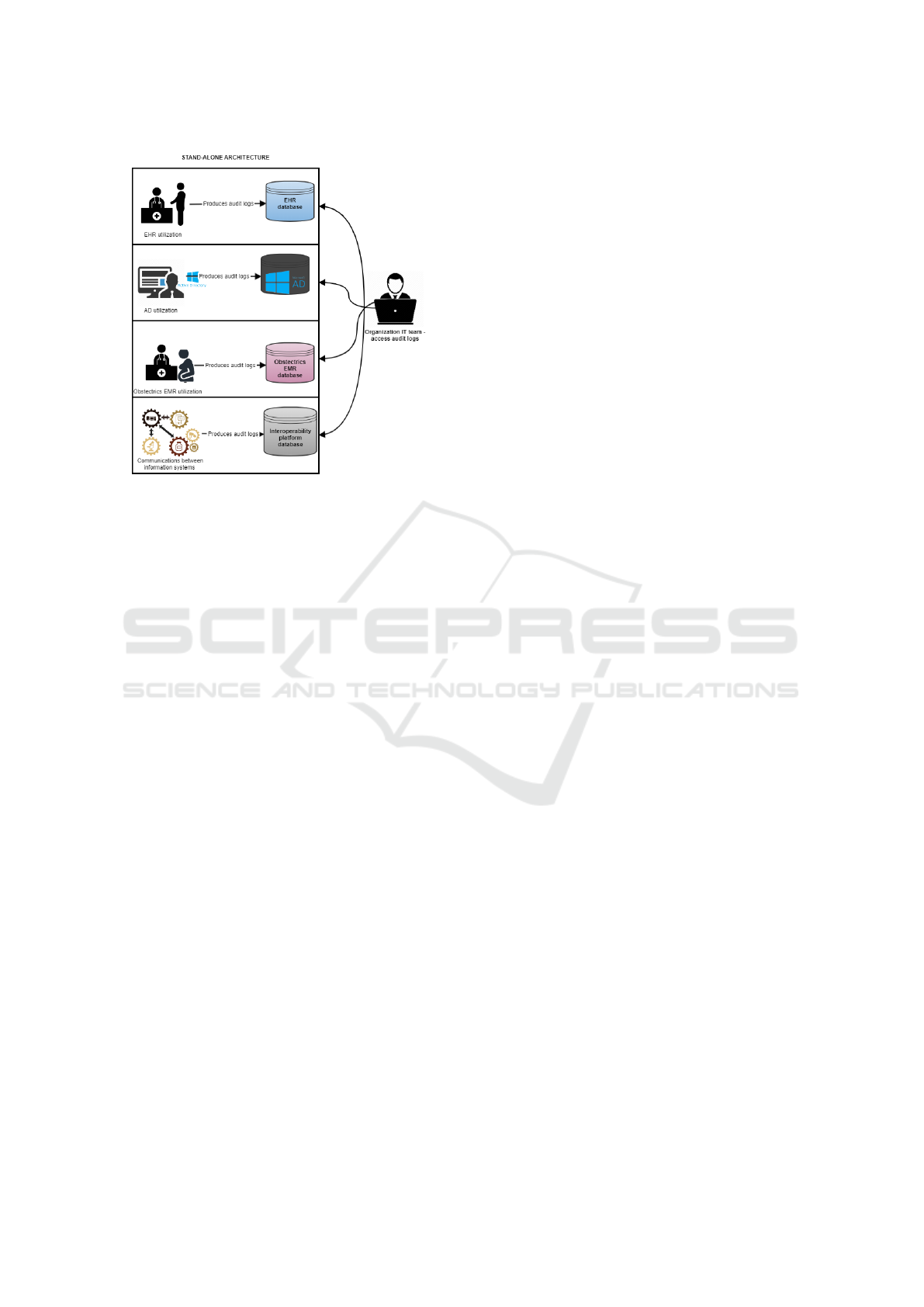
Figure 9: Stand-alone architecture of audit logs recorded.
the sixty four information systems are located outside
of the organization with the responsibility of govern-
mental unities or even external institutions, so for this
systems the challenge is even worse.
Following these results, the organization IT re-
sponsible started communications with all informa-
tion systems providers and the governmental unities
requiring for access the audit logs. In order to fa-
cilitate the communication this organization used as
gold standard for audit log structure and content, the
Portuguese Resolution of the Council of Ministers n.
o
41/2018 - RCM (Presidencia do Conselho de Min-
istros, 2018) which was designed following GDPR
security requirements.
The Portuguese Government considered it is es-
sential to define technical guidelines for the Public
Administration, recommending them to the business
sector, in the area of security architecture for infor-
mation and procedures to be adopted to comply with
GDPR standards. A part of this document is dedicated
to traceability and audit logs.
The organization in study uses this information to
require to providers to facilitate the audit logs with
at least the following fields: (1) who access infor-
mation, (2) from where were accessed (IP and Port),
(3) when accessed, (4) which data were accessed and
(5) which action were performed (create, read, up-
date and delete). Until the moment of this work was
submitted the organization does not had any answer
among providers.
Another important aspect analysed in this study
was the difficult that the organization had to analyse
the available audit logs since they stay in a stand alone
architecture with different ways to access the records
(tables in databases, third party applications, files and
web platform). As a consequence the organization
does not have the means to access the information in
a friendly end-user interface.
The organization also identified that would be in-
teresting cross information from the Active Directory
(authentication) and the information systems, for ex-
ample to create the patient journey or to calculate the
length of sessions and activity in health information
systems. This kind of indicators could help the or-
ganization to identify suspicious cases of usage (like
credentials sharing) and effectively act for the cre-
ation of better security policies. To achieve this goal
the organization will need to implement an audit trail
solution that aggregate the audit logs from every in-
formation systems that leads with personal data and
then work in indicators specification in order to have
a daily basis traceability of events and alarmistic as-
sociated with suspicious cases. By archiving this goal
the organization will comply with the article 32.
In sum, this study helped to identify a need inside
this organization and to determine a follow-up plan
to overpass this challenge. However it also identified
some constrains like financial budget, legacy systems,
small number of IT professionals in the organization
and difficulties in establish communication with sys-
tem providers.
5 CONCLUSION
This study constitutes a small part of the necessary au-
dit work inside the organization. The results showed
how difficult is for a public healthcare organization
to carrying out and implement GDPR requirements.
For one hand they have severe financial constrains
and small team of IT professionals that difficult all
the work and in the other hand due the non-structured
dematerialization they have to lead with legacy infor-
mation systems, that do not follow the standards and
implement a vast amount of old technologies creating
a difficult barrier to overcome. Despite all the effort
observed from the IT professionals of the organiza-
tion there is still a long and complicated path ahead
in order to be complied with GDPR. It is also impor-
tant remember that the articles 30 and 32 are only a
fraction of GDPR. Healthcare organizations should be
readying themselves to ensure their compliance with
the new requirements of the GDPR by taking steps to
understand their existing position.
Identifying a security committee and start carry
out a readiness audit in the organization is a important
step to take in order to provide an overview of compli-
Are the Healthcare Institutions Ready to Comply with Data Traceability Required by GDPR? A Case Study in a Portuguese Healthcare
Organization
561

ance gaps, and then risk rating those gaps against the
likelihood of becoming a GDPR breach. This should
be see as a the start point to define a list of recom-
mendations in order to mitigate the risks of GDPR
non-compliance. This study also identified the het-
erogeneity of the audit logs as constrain since every
information system analysed have a different method
to access their audit logs and even a different format.
In order to access these audit logs it was necessary to
interview different IT professionals (a Database Ad-
ministrator to access the database, System Adminis-
trator to retrieve the file and the AD event viewer and
the integration specialist to access the integration plat-
form). This complexity in accessing the audit logs
showed the importance of having a audit trail platform
to aggregate these audit logs in a common format in
order to access it.
The future work includes a comparison between
audit logs available and the GDPR and Portuguese
Resolution of the Council of Ministers n.
o
41/2018
requirements. After this work it will be need to define
a common format to homogenize and convert the au-
dit logs to a single format in order facilitate to work
with the audit logs in the organization.
ACKNOWLEDGEMENTS
This article is a result of the project Demonstrator
HS.REGISTER (NORTE-01-0247-FEDER-033756),
supported by Competitivity and Internationaliza-
tion Operational Programme (NORTE 2020), un-
der the PORTUGAL 2020 Partnership Agreement,
through the European Regional Development Fund
(ERDF). It was also supported by FCT (Fundac¸
˜
ao de
Ci
ˆ
encia e Tecnologia) through the doctoral fellowship
[SFRH/BDE/105533/2014].
REFERENCES
CMS (2019). GDPR Enforcement Tracker.
CNPD (2018). Deliberac¸
˜
ao N
o
984/2018.
Colesky, M. (2016). Privacy shielding by design — a strate-
gies case for near-compliance. In 2016 IEEE 24th
International Requirements Engineering Conference
Workshops, pages 271–275.
Comission, E. (2016). General Data Protection Regulation.
European Comission.
Cooper, T. (2018). 2018 Global health care outlook: The
evolution of smart health care. Deloitte, pages 1–31.
European Comission; (2016). Art. 32 GDPR Security of
processing.
Europ
´
een et du Conseil, P. (1995). Directive 95/46/CE.
Gonc¸alves-Ferreira, D. e. a. (2018). Hs. register-an audit-
trail tool to respond to the general data protection reg-
ulation (gdpr. Studies in health technology and infor-
matics, 247:81–85.
Haug, C. J. (2018). Turning the Tables — The New Euro-
pean General Data Protection Regulation. New Eng-
land Journal of Medicine, 379(3):207–209.
HL7.org (2018). Audit Event - HL7 FHIR.
IHE (2019). IHE IT Infrastructure Technical Framework
Volume 2a Transactions Part A –. IHE International,
Inc, 2.
Jayabalan, M. (2017). A design of patients data trans-
parency in electronic health records. In 2017 IEEE
ISCE, pages 9–10.
Kent, K. and Souppaya, M. (2006). Guide to Computer
Security Log Management. Nist Special Publication.
Kong, W. (2012). Process improvement for traceability: A
study of human fallibility. In 2012 20th IEEE Inter-
national Requirements Engineering Conference (RE),
pages 31–40.
Margulies, J. (2015). A developer’s guide to audit logging.
IEEE Security Privacy, 13(3):84–86.
Monteiro, A. M. (2019). First GDPR fine in Portugal issued
against hospital for three violations.
Pav
˜
ao, J. (2016). Usability study of sclinico. In 2016 11th
Iberian Conference on Information Systems and Tech-
nologies (CISTI), pages 1–6.
Persoonsgegevens, A. (2019). Haga beboet voor onvol-
doende interne beveiliging pati
¨
entendossiers.
Pinto, E. (2016). Identification and Characterization of
Inter-Organizational Information Flows in the Por-
tuguese National Health Service. Applied clinical in-
formatics, 7(4):1202–1220.
Presidencia do Conselho de Ministros, P. (2018). Resoluc¸
˜
ao
do conselho de ministros n.
o
41/2018.
Sim
˜
oes, J. e. a. (2017). Health System in review -HiT- Por-
tugal. Technical Report 2, European Observatory on
health Systems and Policies.
Skend
ˇ
zi
´
c, A. (2018). General data protection regulation —
protection of personal data in an organisation. In 2018
41st MIPRO, pages 1370–1375.
HEALTHINF 2020 - 13th International Conference on Health Informatics
562
