
User Time Spent between Persuasiveness and Usability of Social
Networking Mobile Applications: Patterns of Influence
Mohammed Bedjaoui, Nadia Elouali and Sidi Mohamed Benslimane
LabRI-SBA Lab., Ecole Superieure en Informatique, Sidi Bel Abbes, Algeria
Keywords: Persuasive Technology, Usability, Users’ Time Spent.
Abstract: Using social media is one of the most common activities for mobile users. Moreover, it is a time-consuming
activity that can lead to addiction. Some gaps in HCI (Human Computer Interaction) ergonomics theory gave
rise to this addiction. These gaps lie in an overexploitation of the usability and/or persuasion criteria that
designers and/or developers use according to their needs when applying influence strategies to affect users’
engagement. Although these strategies are widely applied in online social networks, they are not well
identified and their application levels are still lacking. This paper seeks to establish and validate these
influence strategies. We proposed five (05) patterns of influence in online social networks that have a
significant impact on Users’ Time Spent (UTS) grouping the different usability criteria and persuasion
strategies. Then, we conducted a classification study of those criteria / strategies, using Hybrid Card Sort
method carried out by fifteen (15) eligible experts. Experts were asked to group those criteria / strategies into
a set of patterns based on our predetermined (with the option to create their own patterns). The results analysis
validates our five (05) proposed patterns paving the way to outline their application borderline thereafter.
1 INTRODUCTION
The use of social media such as Facebook, Instagram
and YouTube has become the cornerstone of modern
communication and connection
1
. The average social
media user spends 135 minutes a day online.
Knowing that 60 percent of social media consumption
comes from mobile devices
2
.
A new purpose has emerged, with the great
evolution of social media: to capture the attention of
users and to maximize their engagement. In other
words, maximize the time that users spend with social
media, which can lead to addiction (Kuss and
Griffiths, 2011).
In our paper (Bedjaoui et al., 2018), we presented
our study about the usability and persuasion of the
most used social networking interfaces Facebook and
YouTube according to the UTS (Users' Time Spent).
We conducted heuristic inspection using (Bastien and
Scapin, 1993) usability heuristics and (Némery and
Brangier, 2014) persuasion criteria grid to evaluate
both interfaces. We showed that there are some gaps
in the HCI (Human-Computer Interaction)
1
https://www.psychologytoday.com/us/blog/in-
excess/201805/addicted-social-media
ergonomics theory that gave rise to addictive
interfaces. Some usability criteria (Guidance, Explicit
control, Compatibility) and persuasion criteria
(Personalization, Priming, Commitment,
Ascendency) are overexploited for the purpose of
persuading users to spend as much time as possible.
(The “overexploitation” of persuasive techniques and
ergonomic criteria, turns the techniques that should
serve the user into techniques that manipulate
him/her).
These overexploitation lie in the fact that
designers and/or developers use their judgments to
implement the different usability and persuasion
criteria. In addition, these criteria have no application
borderline. Thus, designers or developers can apply
them according to their needs or interests without
necessarily considering the users objectives (how
they want to spend their time), their relationships
(interpersonal and social choices), their mental and
emotional limits (vulnerabilities, tiredness and ways
in which their minds form habits), etc.
In the present paper, we seek to frame the various
techniques and strategies of influence used by social
media that aim to persuade users to stay online for as
2
https://strikesocial.com/blog/50-social-media-stats-every-
marketer-should-know-in-2018/
Bedjaoui, M., Elouali, N. and Benslimane, S.
User Time Spent between Persuasiveness and Usability of Social Networking Mobile Applications: Patterns of Influence.
DOI: 10.5220/0008976400350044
In Proceedings of the 15th International Joint Conference on Computer Vision, Imaging and Computer Graphics Theory and Applications (VISIGRAPP 2020) - Volume 2: HUCAPP, pages
35-44
ISBN: 978-989-758-402-2; ISSN: 2184-4321
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
35

long as possible and that led to overexploitation of
usability / persuasion criteria, into a set of patterns.
Our purpose is to establish the influence patterns
in order to define their application borderline
thereafter.
At first, we proposed five (05) patterns that
regroup, the different usability criteria and persuasion
strategies (Suggestion Pattern, Reminder Pattern,
Reward Pattern, Interaction Pattern and Social
Influence Pattern). Then and in order to validate our
proposed patterns, we conducted a classification
study of those criteria / strategies, using Hybrid Card
Sort method carried out by fifteen (15) eligible
experts.
The remainder of the paper is organized as
follows. In section 2 we give a background of the
usability and persuasive technology. In section 3, we
discuss related work. We give details on the study
methodology in section 4, and we present the results
and their analyses in section 5. In section 6 we discuss
the application and relationship between these
patterns as well as their influence on UTS. Finally,
section 7 presents some concluding remarks and
outlines topics for future research.
2 THEORETICAL
BACKGROUND
2.1 Usability
The concept of usability aims to develop simple and
effective interactions that take into account users’
reasoning, their workload, their constraints
(environment, position, and task) and strain (fatigue).
Several definitions have been proposed for
usability, the well-known and commonly used was
proposed by (ISO 9241-11, 1998): “The extent to
which a system, product or service can be used by
specified users to achieve specified goals with
effectiveness, efficiency and satisfaction in a
specified context of use”.
Other definitions of usability have been proposed.
They focused on more specific usability criteria, for
example, (Nielsen, 1994) considered “efficiency”,
“ease of learning”, “memorization”, “errors”,
“safety” and “satisfaction”, where (Shneiderman et
al., 2016) emphasized “efficiency” and
“effectiveness”.
Several grids of usability criteria have been
proposed for the evaluation and design of products
and systems. The best known are those of (Bastien
and Scapin, 1993) including several elementary
criteria grouped into eight general principles:
Guidance: All the means implemented to advise,
direct, inform and lead the user during his interactions
(messages, alarms, labels, etc.)
Workload: A set of interface elements that help
reduce user’s perception and memorization load and
increase the dialogue effectiveness.
Explicit Control: Concerns both the system
processing of the explicit actions of users and the
control that users have over the handling of their
actions by the system.
Adaptability: Refers to the ability of a system to
react according to the context, and according to the
needs and preferences of users.
Error management: All the means that aim to avoid
or reduce errors, and to correct them when they occur.
Consistency: Refers to the way in which interface
design choices (codes, denominations, formats,
procedures, etc.) are kept for the same contexts, and
are different for different contexts.
Significance of Codes: Refers to the adequacy
between the object or information displayed or input,
and its referent.
Compatibility: Refers to the agreement that can exist
between the characteristics of the users and the tasks,
on one hand, and the organization of the outputs, the
inputs and the dialogue of a given application, on the
other hand.
2.2 Persuasive Technology
Persuasive design, persuasive interfaces, persuasive
technology and Captology are all denominations,
which, according to the literature refer to the same
phenomenon. All of these terminologies refer to
modifying (or attempting to change) the attitude or
behaviour of users through interfaces and guiding
them to take actions that they would not have done
spontaneously. (Fogg, 2002) has been among the first
contributors in the field of persuasion technology for
which he coined the term “Captology,” an
abbreviation for “Computers As Persuasive
Technology”, which he defines as “design, research,
and analysis of interactive computing products
created for the purpose of changing people’s attitudes
or behaviours”. This concept describes an area in
which technology and persuasion overlap. (As shown
in Figure 1.)
HUCAPP 2020 - 4th International Conference on Human Computer Interaction Theory and Applications
36

Figure 1: Captology.
He introduced the six basic levers of persuasive
technology:
Computer as Persuasive Tools: Presents the
persuasive technologies that aim to bring users to
the expected behaviour or attitude by increasing
their ability to achieve them.
Computers as Persuasive Media:
Conceptualizes persuasive technologies
supported by computers aimed at changing users’
behaviours and/or attitudes through hypothetical
experiences.
Computers as Persuasive Social Actors:
Characterize technologies that use the computer
as a social actor whose goal is to change the
behaviour of its users by exploiting the social
dimension of technologies to influence users. This
is the kind of relationship that occurs when the
device plays the role of a teacher, coach, or expert
(Davis et al., 1998).
Credibility and Computers: Conceptualizes
seven strategies according to the principle that
only credible computing products can influence
and convince users to change their opinions,
attitudes or behaviours.
Credibility and the World Wide Web:
Conceptualizes the strategies defined for use on
websites whose objective is to convince users that
a specific website is the best way to access certain
information or certain content.
Increasing Persuasion through Mobility and
Connectivity: Conceptualizes the strategies
defined for use on mobile devices that persuade
users in the appropriate time and place.
(Oinas-Kukkonen and Harjumaa, 2008) defined
persuasive system as “a computerized software or
information system designed to reinforce, change or
shape attitudes, behaviours or both without using
coercion or deception”. They proposed a framework
called Persuasive Systems Design (PSD) (Oinas-
Kukkonen and Harjumaa, 2009) for the development
and design of persuasive systems, composed into
three distinct phases: (1) understanding key issues
behind the persuasive system, (2) analysing the
persuasion context and (3) designing the system
qualities.
The first phase is concerned with understanding
the key issues behind the persuasive system, where
they define seven postulates that need to be addressed
on designing or evaluating a persuasive system, as
part of understanding the issues that underlie it.
The second phase of Persuasive Systems Design
involves understanding the context of persuasion,
which in itself consists of three aspects: intent, event,
and strategy.
The Intent: Involves understanding (1) who is
persuader, and (2) what type of change is desired
(change of attitude or behaviour).
The Event: Involves analysing (1) the use
context: what is happening around the behaviour
or the habit, (2) the user context: user’s goals and
(3) the technology context, which are the system
goals.
The Strategy: The strategy must be clearly
defined, which consists of understanding: (1) the
Message that will be sent, and (2) the Route (how
it will be sent).
The third phase of persuasive system
development is the design of the system qualities.
Where they define four supports of persuasive
technologies that regroup 28 strategies, essential to
the establishment and maintenance of persuasion:
Primary Task Support: Includes the design
principles that help users to carry out their main
task. Which are reduction, tunneling, tailoring,
personalization, self-monitoring, simulation, and
rehearsal.
Dialogue Support: Includes the design principles
related to the establishment of communication
between human and machine (product). Which
are praise, rewards, reminders, suggestion,
similarity, liking, and social role.
System Support Credibility: Includes the design
principles that describe how to create a more
credible and thus more persuasive system. Which
are social facilitation, social comparison,
normative influence, social learning, cooperation,
competition, and recognition
Social Support: Includes the design principles
that leverages social influence to motivate the
users. Which are social facilitation, social
comparison, normative influence, social learning,
cooperation, competition, and recognition.
User Time Spent between Persuasiveness and Usability of Social Networking Mobile Applications: Patterns of Influence
37

3 RELATED WORKS
We classified existing related work into three
categories:
The first category presents researches that
determine models of persuasion.
The second groups presents the approaches that
determine the patterns of persuasion in online
social networks.
The last groups presents researches that determine
the patterns of social influence, in social networks
and the persuasive systems in general.
The first category presents researches such as
those of (Fogg and Eckles, 2007). They analysed the
persuasiveness of over 50 “Web 2.0” services. Based
on this analysis, they identified a model applied by all
major social networks, called “Behaviour Chain
Model”. It outlines three Phases: “Discovery”,
“Superficial Involvement”, and “True Commitment”.
The first phase, “Discovery”, aims to preconize the
service provided by encouraging users to become
familiar with the site and to visit it. Once users
endorse to the service, they enter the second phase:
“Superficial Involvement”. During this phase, the site
highlights the possibilities of creating content and
exchanging information with other users in order to
motivate them to try the service. The third phase,
“True Commitment”, is characterized by three keys
target behaviours: (1) creating value and content, (2)
involving others, and (3) staying active and loyal. The
model gives important information about the stages
of behaviour change. However, it does not present the
influence strategies that support it.
The second category describes persuasion
patterns. (Iosub et al., 2009) have examined the social
application features of the three main Romanian
Social Networking Sites (SNSs), namely Facebook,
Hi5 and Neogen, on six dimensions corresponding to
the principles of social influence of (Cialdini, 1984) :
Reciprocation, Consistency, Social proof, Liking,
Authority, and Scarcity.
Their purpose was to determine how the
principles of social influence were integrated into the
design of SNS in order to achieve marketing goals, as
well as to determine which principles of social
influence are not currently used in the design of SNS,
and their application could potentially have a relevant
and value-adding effect on SNS competitiveness.
They analysed the three SNS from three
perspectives: social influence principles - marketing
goals, social influence principles - social networking
site and marketing goals - social networking site, and
they showed that social networking sites are mainly
organized according to social principles (reciprocity,
authority, social proof and taste).
In the same context (Adaji and Vassileva, 2016)
sought to identify the persuasion principles of Q&A
social networks. As a case study, they analysed the
StackOverflow network (social network where users
ask and answer questions related to IT). The authors
used the model PSD to analyse the social network
where they identified all persuasive principles present
in the PSD model, with the exception of just four:
tunnelling, rehearsal, reminders and similarity. The
authors conclude that each principle identified in the
social network StackOverflow seeks to promote the
engagement of users on the network.
However, their work was not comprehensive. The
first paper focalized on social design features under
relevant theoretical framework derived from social
psychology where the second paper focused just on
one type of social networks.
The last category presents researches that
emphasize only social influence and its patterns. For
instance, (Weiksner et al., 2008) studied Facebook as
a persuasive technology using a Grounded Theory
approach. They found and named six persuasion
patterns. They classified these patterns into two
categories: Native Patterns, relying on the
functionality provided by Facebook, and Adapted
Patterns, relying on functionality that was designed
for other contexts (e.g., desktop software, web sites,
video games, etc.).
The Native Patterns are composed of:
Provoke and Retaliate: Allow a user to act
towards another user, by exploiting the principle
of reciprocity, the recipient of the gesture has the
social obligation to respond, according to the
norm of reciprocity.
Expression Pattern: Allow users to create
artifacts to express opinions or affiliations, etc., by
exploiting the psychological principle of
ingratiation.
Reveal and Compare: Allow a group of users to
act towards another group of users, by exploiting
the principles of reciprocity, cognitive
dissonance, the need to belong and social
validation.
The Group Exchange: Allow a group of users to
create artifacts collectively following the
principles of impression management,
reciprocity, social validation, and context
variables such as feedback and applause.
The Adapted Patterns are composed of :
Competition: Consists of enhancing competition
between users in order to motivate them to do
particular actions.
HUCAPP 2020 - 4th International Conference on Human Computer Interaction Theory and Applications
38
Deception: Exploits the trust already acquired
from users to persuade them to achieve other
desired goals.
(Oduor et al., 2014) proposed software design
patterns for social influence. They aim to facilitate the
development of effective persuasion systems and to
make a linkage between the intent of designers and
users’ interactions. They proposed four patterns: social
learning and facilitation, competition, cooperation and
recognition. The patterns for social learning and
competition are based on sharing traces, whereas
cooperation and recognition rely on rich exchanges of
support between users.
Nevertheless, those works focused solely on the
social dimension and they did not take into
consideration all the other strategies and influence
processes present in the social network.
To the best of our knowledge, there is no study in
the literature that has extracted all the strategies of
influences into a set of well-defined patterns in an
inclusive way. An approach that presents, explains and
regroups the different strategies of influence used in
the different social networks, considering the different
influence dimensions (social, mental, etc.). In addition,
in our study, we present a direct relationship between
the identified patterns and the usability/persuasion
theory, and thus the criteria that have been
overexploited.
4 STUDY METHODOLOGY
At first we proposed five (05) patterns according to a
classification of usability criteria (the eight (08)
usability criteria for the design and evaluation of HCI
(Bastien and Scapin, 1993)) and persuasion strategies
(of the PSD model proposed by (Oinas-Kukkonen and
Harjumaa, 2009)) that we realized in advance defined
in table (Table. 1).
Table 1: Description of the five (05) proposed patterns.
Pattern
name
Definition Examples
Suggestion
Pattern
The fact of presenting the right information at the
right time gradually and in an allusive way,
compatible with the characteristics of the user, to his
needs, interests, and usage context, with the aim of
capturing his attention, in order to bring him to
engaging actions and to ensure his allegiance.
Providing “Friends Suggestion”,
“Recommended Pages” and “Suggestions of
groups” functions on Facebook.
Providing a set of related videos under the
video selected by the user on YouTube.
Reminder
Pattern
Any messages that interrupt users immediately,
leading them to respond to the delivered messages
asynchronously. It can take various forms, such as an
email, a social notification or an SMS.
Facebook, YouTube, LinkedIn, Twitter or
Instagram notifications.
WhatsApp, Messenger or Snapchat, messaging
system.
Social
influence
Pattern
Any form of influence that emphasizes the social
influence (comparison, competition, reciprocity, etc.)
in order to reinforce the pressure of other members on
the actions of an individual.
Number of views for each video (on YouTube).
Number of likes of each posts (on Facebook).
Number of followers/tweets (On Twitter).
Interaction
Pattern
Any form of incitement or restriction that makes
targeted actions easy and simple while gradually
increasing the cost of the actions requested, or
deterring unwanted actions in order to make them
more difficult than they need to be.
Generally, social media interfaces facilitate tasks that
they want users to perform such as (inviting and
connecting to friends, registering in groups, adding
more pages), by making them simple actions.
Example: (“Invite”, “Like”, “Share” and
“Register” buttons).
And complicate the unwanted actions that they do not
want the user to perform (disable notifications, delete
an account, etc.) for example:
On Facebook, user cannot turn off all
notifications. He can just choose the mode and
the nature of the notifications he receives.
Deleting an account on Snapchat requires
multiple steps as well.
Reward
Pattern
Any form of encouragement of user’s interaction
through forms of rewards that come to reward the user
in the success of his first interactions. It aims to
reinforce his initiatives and maintain his engagement.
News feed with an infinite scroll (Facebook).
Autoplay feature (YouTube) unending videos.
User Time Spent between Persuasiveness and Usability of Social Networking Mobile Applications: Patterns of Influence
39
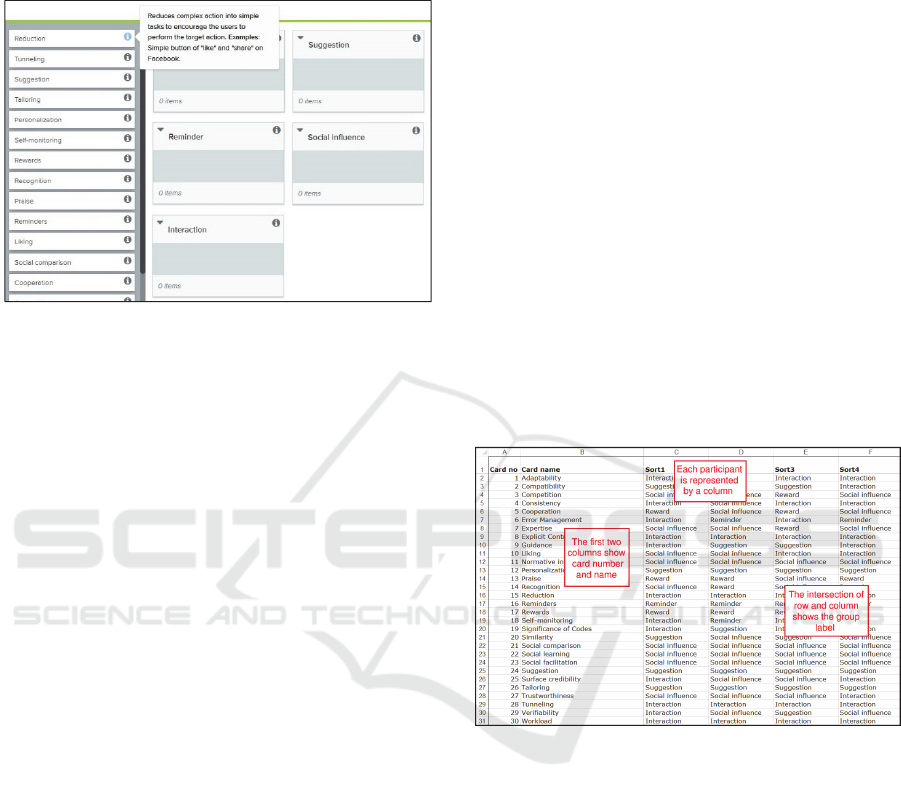
Afterwards and in order to validate these patterns,
we adapted a hybrid card sorting method, implemented
on the web using the OptimalSort tool (Figure 2).
Figure 2: The OptimalSort Card Sorting Interface.
(http://www.optimalworkshop.com/).
We invited fifteen (15) eligible HCI experts to
participate in our study (5 men, 10 women), among
them, 9 are specialized in User
Experience/Ergonomics, 2 in Social
Computing/Human-Computer Interaction, 3 in
Multimodal interaction / Human-Computer
Interaction, and the remaining one in Human-
Computer Interaction and software engineering. Ten
(10) of them have more than ten (10) years of
experience in the field of HCI.
We believe that with the data of 15 experts we will
achieve the desired results since with 15 participants
the results obtained have a correlation of 90% as
affirmed by (Nielsen, 2004).
As cards, we choose the twenty-two (22) strategies
of persuasion of the PSD model proposed by (Oinas-
Kukkonen and Harjumaa, 2009), because it is the only
framework that exists, designed for the development
and design of persuasive systems. We choose also the
eight (08) usability criteria for the design and
evaluation of HCI proposed by (Bastien and Scapin,
1993). The thirty (30) criteria/strategies were presented
with definitions and examples.
Participants were invited to group the eight (08)
usability criteria and the twenty-two (22) strategies of
persuasion into categories. In addition to the
categorization that we proposed, we asked experts to
create their own categories if necessary, by assigning a
meaningful name to each category.
For analysing participants’ data, we adapted both
exploratory and statistical approaches. For the
exploratory one, we used Donna Spencer’s (Spencer,
2009) spreadsheets in order to understand each
expert’s categorizations, to create standardized
categories (which is an essential part of card sorting)
and to generate correlation matrix in order to
summarize the range of classification as well as to
provide information about each card’s placement and
the relationship between cards and participants. While
for the statistical approach, we used Hierarchical
Cluster Analysis (HCA) using complete linkage
method in order to highlight patterns in data.
5 RESULTS AND ANALYSIS
5.1 Standardizing Categories
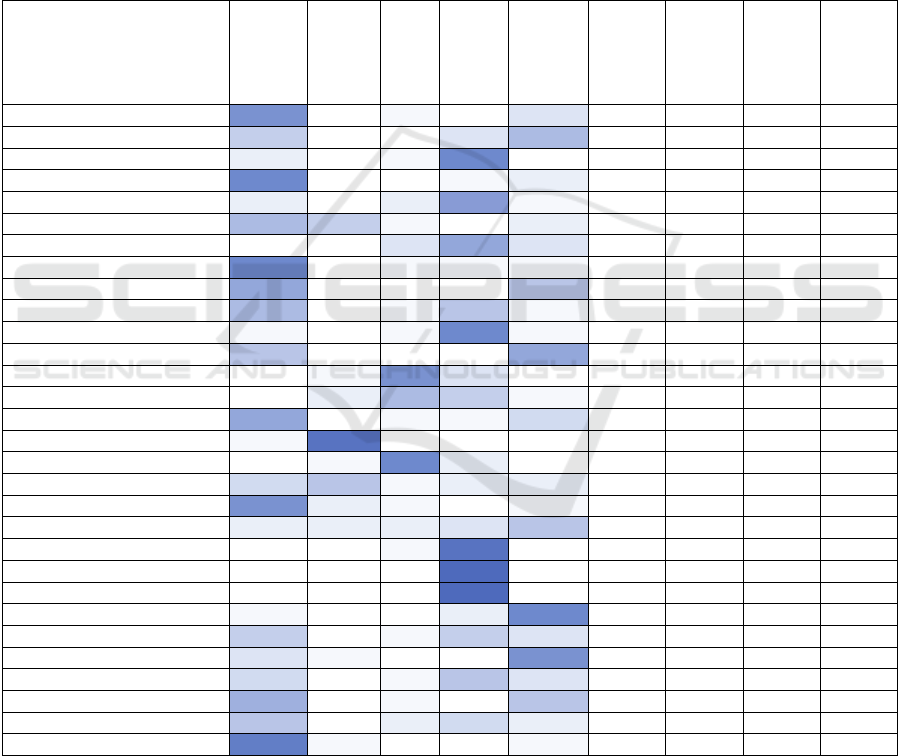
At first, we inserted the data of each participant
extracted, in Donna Spencer’s (Spencer, 2009)
spreadsheet (Figure 3. Shows the generated matrix).
Each row represents a card and each column a
participant. The row and column intersection has the
label for each category. Then, we began standardizing
the labels of categories created by experts in order to
create a set of consistent categories’ labels.
Figure 3: Worksheet with all the raw data.
The experts validated our suggested categories.
They categorized the criteria / strategies using only our
five proposed categories, with the exception of three
experts, who proposed four additional ones. Thus, we
intersected our categories and the additional ones
proposed by experts based on similar words
(terminology of labels), similar ideas and categories
that contains similar cards.
For example, a participant created a category
named “Restriction” that includes the cards (Explicit
Control and Tunneling). However, we found that it was
a subcategory of the “Interaction” category (which
covers the “restriction” and the “incitement”). Another
example, two participants created two categories
named “Customization or Personalization” which
means: “The content customized to the needs of the
HUCAPP 2020 - 4th International Conference on Human Computer Interaction Theory and Applications
40
user” and “Data Influence” which means: “the data that
influences the user in order to attract him”, including
cards (Adaptability, Compatibility, Personalization,
Similarity, Suggestion and Tailoring). However, these
two categories means the same as the “Suggestion”
category, which means, “Offering fitting suggestions
to the user in order to attract and incite him”.
5.2 Cards Placement
After the standardization process, we had an average of
five (05) categories. Table. 2 recaps the standardized
categories, the percentage of each cards’ placement
and the content of each category as well as an insight
of the relationship between cards, categories and
participants. According to this table (correlation matrix
generated by (Spencer, 2009)), we notice that all
categories have at least one card
with high agreement
(75% or more of participants agreed to the placement
of the cards), and 60% cards belong to categories with
medium agreement (50% or more of participants
agreed to the placement of the cards).
Table 2: The correlation matrix created for the hybrid card-sort (as generated by (Spencer, 2009)).
Card name
Interacti
on
Remind
er
Rewar
d
Social
influen
ce
Suggesti
on
Categori
es for
this card
Categori
es with
high
agreeme
nt
Categori
es with
medium
agreeme
nt
Categori
es with
low
agreeme
nt
Adaptability 73% 0% 7% 0% 20% 3 0 1 2
Compatibility 33% 0% 0% 20% 47% 3 0 2 1
Competition 13% 0% 7% 80% 0% 3 1 0 2
Consistency 80% 0% 0% 7% 13% 3 1 0 2
Cooperation 13% 0% 13% 67% 7% 4 0 1 3
Error Management 47% 33% 7% 0% 13% 4 0 2 2
Expertise 0% 0% 20% 60% 20% 3 0 1 2
Explicit Control 80% 0% 7% 7% 7% 4 1 0 3
Guidance 60% 0% 0% 0% 40% 2 0 2 0
Liking 47% 0% 7% 40% 7% 4 0 2 2
Normative influence 7% 0% 7% 80% 7% 4 1 0 3
Personalization 40% 0% 0% 0% 60% 2 0 2 0
Praise 0% 7% 73% 20% 0% 3 0 1 2
Recognition 0% 13% 47% 33% 7% 4 0 2 2
Reduction 60% 0% 7% 7% 27% 4 0 2 2
Reminders 7% 93% 0% 0% 0% 2 1 0 1
Rewards 0% 7% 80% 13% 0% 3 1 0 2
Self-monitoring 27% 40% 7% 13% 13% 5 0 2 3
Significance of Codes 73% 13% 7% 0% 7% 4 0 1 3
Similarity 13% 13% 13% 20% 40% 5 0 1 4
Social comparison 0% 0% 7% 93% 0% 2 1 0 1
Social facilitation 0% 0% 0% 100% 0% 1 1 0 0
Social learning 0% 0% 0% 100% 0% 1 1 0 0
Suggestion 7% 0% 0% 13% 80% 3 1 0 2
Surface credibility 33% 0% 7% 33% 20% 4 0 2 2
Tailoring 20% 7% 0% 0% 73% 3 0 1 2
Trustworthiness 27% 0% 7% 40% 20% 4 0 2 2
Tunneling 53% 0% 7% 0% 40% 3 0 2 1
Verifiability 40% 0% 13% 27% 13% 4 0 2 2
Workload 87% 7% 0% 0% 7% 3 1 0 2
Cards in this category 23 10 20 21 23
Cards with high agreement
(>75%) 3 1 1 5 1
Cards with medium
agreement 13 2 2 7 7
Cards with low agreement
(<25%) 7 7 17 9 15
User Time Spent between Persuasiveness and Usability of Social Networking Mobile Applications: Patterns of Influence
41
Cards in this Category: Refer to the number of
individual cards placed in this category.
Cards with High Agreement: Refer to the
number of individual cards with a correlation of
75% or over (75% of participants or more used
this category for the card).
Cards with Medium Agreement: Refer to the
number of individual cards with a correlation of
25%–50%.
Cards with Low Agreement: Refer to the
number of individual cards with a correlation of
25% or less.
Categories for this Card: Refer to the number of
categories used for this card.
Categories with High Agreement: Refer to the
number of categories with a correlation of 75% or
over (75% of participants or more put this card in
a consistent category).
Categories with Medium Agreement: Refer to
the number of categories with a correlation of
25%–50%.
Categories with Low Agreement: Refer to the
number of categories with a correlation of 25% or
less (participants or fewer used any consistent
category).
Next, we applied an HCA to the global data matrix
of the 15 experts, we were able to identify and label
the clusters on the dendrogram generated by the
HCA. Figure 4 illustrates these results.
5.3 Patterns Extraction
According to the dendrogram (Figure 4), five
consistent patterns are distinguished from the
classification and are cited below:
Suggestion Pattern: This pattern contains four
persuasive strategies from PSD Model:
Suggestion, Personalization, Tailoring and
Similarity and one usability criteria from (Bastien
and Scapin, 1993) ergonomic criteria:
Compatibility.
Reminder Pattern: This pattern contains one
persuasive strategies from PSD Model:
Reminders.
Social influence Pattern: This pattern contains
seven persuasive strategies from PSD Model:
Social comparison, Social facilitation, Social
learning, Expertise, Normative influence,
Competition and Cooperation.
Interaction Pattern: This pattern contains seven
persuasive strategies from PSD Model:
Reduction, Tunneling and to a lesser extent
Verifiability, Liking, Surface credibility and
Trustworthiness, and six usability criteria from
(Bastien and Scapin, 1993) ergonomic criteria:
Workload, Adaptability, Consistency, Explicit
Control, Significance of Codes and Guidance.
Reward Pattern: This pattern contains three
persuasive strategies obtained PSD Model:
Rewards, Recognition and Praise.
Figure 4: Dendrogram generated by the HCA of the hybrid
card-sort.
5.4 Patterns’ Relationships and
Proximity
From Figure 4 we notice that there is a close
relationship between patterns. The pattern
“Interaction” is close to the pattern “Suggestion”, and
both are in turn related to the pattern “Reminders”.
This explains the design of social media that aims to
attract the attention of the user and arouse his interest
to undertake an engaging action, favourable to the
media. On the other hand, the pattern “Social
Influence” is related to the pattern “Rewards”,
HUCAPP 2020 - 4th International Conference on Human Computer Interaction Theory and Applications
42

applied to complete the total commitment of the user
in order to control him.
6 DISCUSSION
In this paper, we identified five influence patterns that
bring together all social media strategies having a
significant impact on user time by applying hybrid
card sorting method. We consider that those patterns
are usually used together gradually since they support
each other (as shown in Figure 5). In fact, the process
of capturing the user is a temporal process that
includes a start, followed by modifications of the user
behaviour towards the media, leading to the objective
sought (maximizing the UTS). Moreover, to bring the
users to this objective, a social network must bring the
user gradually over time, with a succession of phases,
to capture their attention and especially to maintain
their interest and their motivation.
First, the social media must solicit the user to take
the first steps over the social media by offering him
suggestions (proposing close people, adhere to
groups, etc.), by exerting (social) pressure using the
mechanism of normative influence or social
comparison for example, or by reminding him of
actions that he can perform (using instant
notifications for example).
Moreover, to have the prescribed goal and the
behaviour expected from the user, the social network
must prompt him to take action where it is necessary
using simple interactions (for example, buttons that
say click here or subscribe now). On the other hand,
the social network can complicate the unwanted
actions desired by users (for example, disable the user
account, or disable notifications).
Finally, the social media must reward the user for
the success of his first interactions, in order to
reinforce his initiatives and behaviours. Nonetheless,
this process of patterns sequence is our own
conclusion that may need some further research.
All these patterns are useful regarding usability
and persuasion. They guide users, give them some
control, present urgent messages, suggest desired
videos, etc. Nevertheless, these results highlight
important negative points (unlimited suggestions list,
unlimited notifications at any time in the day even if
there is no emergencies, etc.) encouraging users to
use applications more frequently and for greater
duration than they otherwise would.
In addition, patterns such as “Interaction Pattern”
impose an important issue: complicating some
interactions such as reducing notifications or
disabling accounts is not recommended according to
usability criteria. According to (Christian Bastien and
Dominique Scapin, 1993), the usability criterion
“Minimal Actions” consists of reducing the number
of actions necessary to accomplish a goal or a task
(“limiting as much as possible the steps users must go
through”). Thus, complicating some actions calls into
question the interaction pattern and its use in
ergonomics (especially in persuasion).
Figure 5: Relationships between patterns.
To summarize, exploiting all these patterns in
usability and persuasion must be questioned not only
because they have a big effect on the user's time, but
also because their misapplication can conflict with the
ergonomics theory and overexploit its criteria.
7 CONCLUSION
In our paper (Bedjaoui et al., 2018), we showed that
there are some gaps in the HCI ergonomics theory
that gave rise to addictive interfaces. These gaps lie
in the fact that designers and/or developers have to
use their judgments to implement the different
usability and persuasion criteria, principles and rules.
In addition, these criteria have no application
borderline. Thus, designers or developers can apply
them according to their needs or interests without
necessarily considering the users objectives (how
they want to spend their time), their relationships
(interpersonal and social choices), their mental and
emotional limits (vulnerabilities, tiredness and ways
in which their minds form habits), etc.
In this paper, we identified five influences
patterns using hybrid card sorting method. Those
patterns have a significant impact on user time spent
on the media and their misapplication can conflict
with the ergonomics theory.
User Time Spent between Persuasiveness and Usability of Social Networking Mobile Applications: Patterns of Influence
43

Now, we are working on an approach that frame
these influence patterns. We are defining their
application borderlines. For a particular pattern
applied to support particular criteria, we are
identifying rules that make its use more efficient
(from user time viewpoint), keep its advantages and
do not affect the supported criteria. Thus, while
applying a pattern, designers or developers will be
aware of the usage limits and thereby respect them to
benefit from the mechanism advantages while
respecting the users’ time.
We believe that such an approach will allow to
design and build products that motivate the active
participation of the user and respect her/his time.
REFERENCES
Adaji, I., & Vassileva, J. (2016, April). Persuasive patterns
in Q&A social networks. In International Conference
on Persuasive Technology (pp. 189-196). Springer,
Cham.
Bastien, J. C., & Scapin, D. L. (1993). Ergonomic criteria
for the evaluation of human-computer
interfaces (Doctoral dissertation, Inria).
Bedjaoui, M., Elouali, N., & Benslimane, S. M. (2018,
November). User Time Spent Between Persuasiveness
and Usability of Social Networking Mobile
Applications: A Case Study of Facebook and YouTube.
In Proceedings of the 16th International Conference on
Advances in Mobile Computing and Multimedia (pp.
15-24). ACM.
Cialdini, R. B. (1984). The psychology of persuasion. New
York: Quill William Morrow.
Davis, J. W., & Bobick, A. F. (1998, November). Virtual
PAT: a virtual personal aerobics trainer. In Workshop
on Perceptual User Interfaces (pp. 13-18).
Fogg, B. J. (2002). Persuasive technology: using computers
to change what we think and
do. Ubiquity, 2002(December), 5.
Fogg, B. J., & Eckles, D. (2007, April). The behavior chain
for online participation: how successful web services
structure persuasion. In International Conference on
Persuasive Technology (pp. 199-209). Springer, Berlin,
Heidelberg.
International Organization for Standardization. (1998). ISO
9241-11: Ergonomic Requirements for Office Work
with Visual Display Terminals (VDTs): Part 11:
Guidance on Usability.
Iosub, D., Andrei, A. G., & Iacob, A. (2009). Patterns of
social influence in social networking sites–a design
perspective.
Kuss, D. J., & Griffiths, M. D. (2011). Online social
networking and addiction—a review of the
psychological literature. International journal of
environmental research and public health, 8(9), 3528-
3552.
Némery, A., & Brangier, E. (2014). Set of guidelines for
persuasive interfaces: organization and validation of the
criteria. Journal of Usability Studies, 9(3), 105-128.
Nielsen, J. (1994). Usability engineering. Elsevier.
Nielsen, Jakob. Card Sorting: How Many Users to Test.
https://www.nngroup.com/articles/card-sorting-how-
many-users-to-test/ (2004)
Oduor, M., Alahäivälä, T., & Oinas-Kukkonen, H. (2014).
Persuasive software design patterns for social
influence. Personal and ubiquitous computing, 18(7),
1689-1704.
Oinas-Kukkonen, H., & Harjumaa, M. (2008, February).
Towards deeper understanding of persuasion in
software and information systems. In First international
conference on advances in computer-human
interaction (pp. 200-205). IEEE.
Oinas-Kukkonen, H., & Harjumaa, M. (2009). Persuasive
systems design: Key issues, process model, and system
features. Communications of the Association for
Information Systems, 24(1), 28.
Shneiderman, B., Plaisant, C., Cohen, M., Jacobs, S.,
Elmqvist, N., & Diakopoulos, N. (2016). Designing the
user interface: strategies for effective human-computer
interaction. Pearson.
Spencer Donna. Card Sort Analysis Spreadsheet Template.
Retrieved November 2016, from
http://rosenfeldmedia.com/books/card-sorting/ (2009)
Weiksner, G. M., Fogg, B. J., & Liu, X. (2008, June). Six
patterns for persuasion in online social networks.
In International conference on persuasive
technology (pp. 151-163). Springer, Berlin,
Heidelberg.
HUCAPP 2020 - 4th International Conference on Human Computer Interaction Theory and Applications
44
