
A Comparative Performance Evaluation of Distributed Collision-free
MAC Protocols for Underwater Sensor Networks
Faisal Alfouzan, Alireza Shahrabi, Seyed Mohammad Ghoreyshi and Tuleen Boutaleb
School of Computing, Engineering and Built Environment, Glasgow Caledonian University, Glasgow, U.K.
Keywords:
Underwater Sensor Networks (UWSNs), Medium Access Control (MAC), Collision-free MAC Protocols.
Abstract:
The design of Medium Access Control (MAC) protocols for UWSNs poses many challenges because of their
long propagation delay, high mobility, limited bandwidth, and high bit error rate. Due to these unique acoustic
channel characteristics, most contention-based MAC protocols are costly. Thus, collisions and retransmissions
should be efficiently handled at the MAC layer in order to reduce the energy cost and to improve throughput
and fairness across the network. As a consequence, they do not perform as efficiently as their achieved perfor-
mance in terrestrial networks. In this paper, we evaluate the performance of three recently reported distributed
collision-free MAC protocols; namely, ED-MAC, DL-MAC, and GC-MAC under various operational condi-
tions. An extensive simulation study is carried out to compare the performance of these MAC protocols in
terms of packet delivery ratio (PDR), throughput, and energy consumption with different scenarios (narrow
and shallow networks) under varying traffic rates and numbers of nodes. Our study results showed that ED-
MAC reaches the best energy efficiency in a narrow scenario with a light load than DL-MAC and GC-MAC
protocols. While DL-MAC is a suitable choice for both scenarios among others in terms of flexibility. In terms
of reliability and scalability, GC-MAC achieves the best performance in both scenarios than other protocols.
1 INTRODUCTION
Underwater sensor networks (UWSNs) have attracted
a considerable attention to discover and monitor
aquatic environments. This aims to improve ocean
exploration and underwater applications such as envi-
ronmental monitoring, early warning systems, disas-
ter prevention, intrusion detection, military applica-
tions, and exploration of ocean resource (Ghoreyshi
et al., 2017). In UWSNs, a sink is considered on the
water surface, which is applicable to both an acous-
tic modem for underwater communication and a radio
modem for out-of-the-water communications (from
sink to satellite, and from satellite to monitoring cen-
tre) (Ghoreyshi et al., 2016; Alfouzan et al., 2016).
Anchored nodes are located at the bottom of the ocean
in predetermined locations to collect the information.
That information is delivered to the sink using the
relay nodes which are located between the sink and
the anchored nodes at different depth levels. The
anchored and relay nodes utilise acoustic signals to
transmit the data packets (Ghoreyshi et al., 2018a).
Using acoustic signal differently affects the design
of various services in UWSNs (Akyildiz et al., 2005).
Specifically, it has completely changed the design of
Medium Access Control (MAC) protocols compared
to that of terrestrial networks (Hsu et al., 2009). Since
radio wave cannot propagate in the underwater envi-
ronment as efficiently as it achieved in terrestrial net-
works, currently acoustic communication has exten-
sively been studied (Preisig, 2007; Ghoreyshi et al.,
2018b). However, due to the unique characteristics
of its acoustic channels such as slow signal propaga-
tion speed (about 1500m/s in water), limited channel
capacity, and high dynamics of channel quality, MAC
protocol design for underwater acoustic networks face
several challenges. Particularly, the high propaga-
tion delay which significantly affects the MAC design
strategy in UWSNs.
Existing MAC solutions are essentially focused on
TDMA. This is mainly because FDMA is not proper
for UWSNs due to the narrow bandwidth in under-
water acoustic channel as well as the diffuse of lim-
ited band systems to fading and multipath. Moreover,
CDMA is very robust to frequency selective fading
caused by multiple paths. It is therefore unsuitable
for UWSNs due to also its difficulties to address the
near-far problem (Xie and Cui, 2007).
Among them, TDMA is the most promising mul-
tiple access technique for UWSNs. This is mainly
Alfouzan, F., Shahrabi, A., Ghoreyshi, S. and Boutaleb, T.
A Comparative Performance Evaluation of Distributed Collision-free MAC Protocols for Underwater Sensor Networks.
DOI: 10.5220/0007379700850093
In Proceedings of the 8th International Conference on Sensor Networks (SENSORNETS 2019), pages 85-93
ISBN: 978-989-758-355-1
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
85

because it allows the same frequency channel to be
shared by dividing the signal into different time slots.
Furthermore, it is able to maintain reliable transmis-
sion schedules by performing additional updating and
scheduling phases to also remain all sensor nodes syn-
chronised. TDMA also allows sensors, located out
of each others’ transmission ranges, to transmit data
packets simultaneously without collision by using the
concept of spatial reuse (concurrent sending in dif-
ferent neighbourhoods) (Alfouzan et al., 2018a). For
these reasons, TDMA increases channel reuse and
eliminate packet retransmissions, which results in de-
creased energy consumption and increased network
throughput.
Recently, three new TDMA-based distributed
collision-free MAC protocols, ED-MAC (Alfouzan
et al., 2017; Alfouzan et al., 2018a), DL-MAC (Al-
fouzan et al., 2018b), and GC-MAC (Alfouzan et al.,
2018c), have been reported in the literature with var-
ied performance under various operational conditions
and different assumptions. The aim of this paper is
to compare the performance of these protocols under
two different practical scenarios, namely shallow and
narrow scenarios, and to investigate their reliability,
scalability and flexibility under a wide range of ex-
perimental conditions.
The remainder of this paper is organised as fol-
lows. Section 2 describes and classifies the protocols
that we have investigated. Section 3 investigates and
compares the performance evaluation. Section 4 con-
cludes the paper.
2 DESCRIPTION OF THE
PROTOCOLS
This section presents a description of each collision-
free MAC protocol. It is then followed by a classifica-
tion that includes all the requirements and properties
of each, as illustrated in Table 1.
2.1 ED-MAC
An Efficient Depth-based MAC protocol (ED-MAC)
has been proposed in (Alfouzan et al., 2017; Alfouzan
et al., 2018a) with the aim of improving the energy ef-
ficiency, throughput, and fairness. It is a reservation-
based MAC protocol in which a duty cycle mecha-
nism is used by assigning time slots to every indi-
vidual node in the network in a distributed manner.
This is used to reduce the energy consumption by us-
ing a wake-up scheduling scheme; nodes are awake in
some slots to transmit or receive data and are asleep
over the remaining slots.
ED-MAC operates in three phases: initial,
scheduling, and normal operational phase. In the first
phase, all the sensors randomly transmit a number of
small beacons to detect their one-hop neighbouring
nodes. The length of the initial phase is a predefined
fixed value for all sensors.
The primary goal of the scheduling phase is to al-
locate a unique time-slot to every sensor in the net-
work. A timer is utilised at every sensor to prioritise
slot reservation depending on the sensor depth; the
deeper the sensor, the higher priority to reserve a slot.
This timer lets a sensor which is located in a deeper
area to reserve a slot sooner than its above neighbour-
hoods. The value of this timer at each sensor is given
by (Alfouzan et al., 2017; Alfouzan et al., 2018a):
T
sch
=
2M
Depth
M
Depth
+ N
Depth
× T
Delay
− T
Delay
, (1)
where M
Depth
is the depth of the network area and
N
Depth
is a sensor depth in the network. T
Delay
is the
length of the scheduling phase that is a predefined
fixed value, set during the deployment process based
on the application requirements. The value of T
Delay
depends also on the density of the nodes in an under-
water area. This phase is significantly shorter than
that of the normal operational phase.
The third phase, the normal operational phase, is
divided into a number of rounds. Each of them in-
cludes a number of slots. Sensors in each round are
aware of their reserved slots, and other slots that re-
served by their neighbourhoods. Thus, all sensors
can schedule to wake-up either to send their own data
packets during the reserved slots or to receive a data
packet from a neighbouring sensor. They switch to a
sleeping mode in the remaining slots when there is no
data transmission or reception.
2.2 DL-MAC
A Depth-based Layering MAC protocol (DL-MAC)
has been proposed in (Alfouzan et al., 2018b) to
improve energy efficiency, reliability, and flexibility.
This is achieved by dividing the aquatic network area
into a number of horizontal layers to avoid any chance
of vertical collision. A simple clustering approach
for one-hop neighbouring sensors are utilised to also
avoid any possibility of collision between sensors in
the same layer. Therefore, DL-MAC is able to ad-
dress spatial-temporal uncertainty, the near-far effect,
and any hidden/exposed terminal problems.
In DL-MAC, sensors in the network operate in
three phases: updating, scheduling, and operational.
The goal of the updating phase is to gather informa-
tion about one-hop neighbouring nodes. This is per-
formed by exchanging some updating messages. The
SENSORNETS 2019 - 8th International Conference on Sensor Networks
86

length of this phase is a constant value set during the
deployment time for all sensors.
The purpose of the second phase, the schedul-
ing phase, is to assign a time-slot to every individ-
ual sensor in the network to access the medium with
no chance of collision. This is achieved by divid-
ing the network into multi layers, grouped into three
frames, and every frame is also divided into a num-
ber of sub-frames. Each sub-frame consists of a num-
ber of time-slots. A distributed clustering approach is
utilised to allow cluster heads, CHs, selecting unique
sub-frames, which should be different from the adja-
cent clusters. By using a simple clustering approach,
every cluster head is eventually able to assign all its
cluster members, i.e., those are located within a one-
hop neighbourhood, different time slots. Through this
principle, every sensor in the network has a different
time-slot in any two-hop neighbourhood; hence no
collisions can occur. To determine a CH, this model
gives higher priority to a sensor that can cover more
sensors in its 1-hop range at the same layer. This is ap-
plied via a timer-based approach, called degree timer,
which can be given by (Alfouzan et al., 2018b):
T
d
=(d
max
−d
s
)×(T
sch
/d
max
)±λ (2)
where d
s
denotes the sensor degree and d
max
indicates
the maximum node degree in the network topology.
This can be estimated based on the sensor deployment
process, number of sensor nodes, and network dimen-
sions and it can also be known to all nodes during the
deployment time. T
sch
is the scheduling interval time
and λ is a short random time duration to differentiate
the underwater sensor nodes with the same d
s
.
The operational phase is divided into a number of
cycles, each consisting of three frames. Each frame
is composed of k sub-frames. Frames and sub-frames
are used to avoid vertical layers and horizontal clus-
ter interference respectively. Each sub-frame also en-
compasses a number of slots. At each cycle, every
sensor is aware of its frame, sub-frame, and its own
reserved slots, as well as the slots reserved by its
neighbouring sensors. They can therefore be sched-
uled to wake-up either to transmit their own data
packet during the reserved slots or to possibly receive
a data packet from a neighbouring sensor. They are
asleep in the remaining slots when there is no data
transmission or reception.
2.3 GC-MAC
A collision-free Graph Colouring MAC protocol
(GC-MAC) has been proposed in (Alfouzan et al.,
2018c) which aims to achieve better performance
in terms of throughput, energy efficiency, and fair-
ness than other collision-free MAC protocols. GC-
MAC uses the concept of graph colouring to de-
velop a reservation-based contention-free MAC pro-
tocol. This has been achieved by using a distributed
clustering approach for up to two-hop neighbouring
sensors and then to address the hidden and expose
node problems by removing the possible colour con-
flict in two-hop neighbouring graph. Using a TDMA-
like approach, GC-MAC is able to assign a time-slot,
colour, to every individual node in the network in a
distributed manner. Nodes with the same colours can
thus transmit concurrently without collision. Nodes
are awake in some slots to transmit or receive data
packets and asleep over the remaining slots.
GC-MAC includes three phases to operate, which
are initial, scheduling, and operational phase. In the
initial phase, two rounds of beaconing are conducted
to discover two-hop neighbouring sensors. This is
performed by exchanging some beacons between sen-
sors. The length of this phase is set as a constant value
for all sensors during the deployment time.
The primary goal of the scheduling phase is to as-
sign different colours to all nodes which are located
within any two-hop neighbourhood using a simple a
clustering approach. This is achieved by allowing a
cluster head (CH), which is determined as the closest
sensor to a reference point during the first phase, to
assign a different colour for all its one-hop neighbour-
ing (inner) sensors. Afterwards, the outer sensors,
those located outside the cluster, decide about their
own colours individually. By the end of the schedul-
ing phase, every sensor node has a various colour in
any two-hop neighbouring graph and hence no colli-
sion can occur.
The operational phase is divided into a number of
rounds. Each round consists of a number of time-
slots. These time-slots are reserved by assigning a
various colour to each. Nodes with the same colour
can transmit data packets at the same time without any
collision while the hidden and exposed node prob-
lems are properly addressed. In this phase, the sen-
sor nodes wake-up and sleep periodically. In other
words, sensors can schedule to wake-up to send their
own data packets during the reserved slots or to re-
ceive a data packet from a neighbourhood, while they
are asleep in other remaining slots when there is no
data transmission or reception.
2.4 Qualitative Comparison
In this section, we classify each protocol (ED-MAC,
DL-MAC, and GC-MAC) requirements and proper-
ties, and compare them qualitatively.
Table 1 lists all assumptions in which every pro-
A Comparative Performance Evaluation of Distributed Collision-free MAC Protocols for Underwater Sensor Networks
87
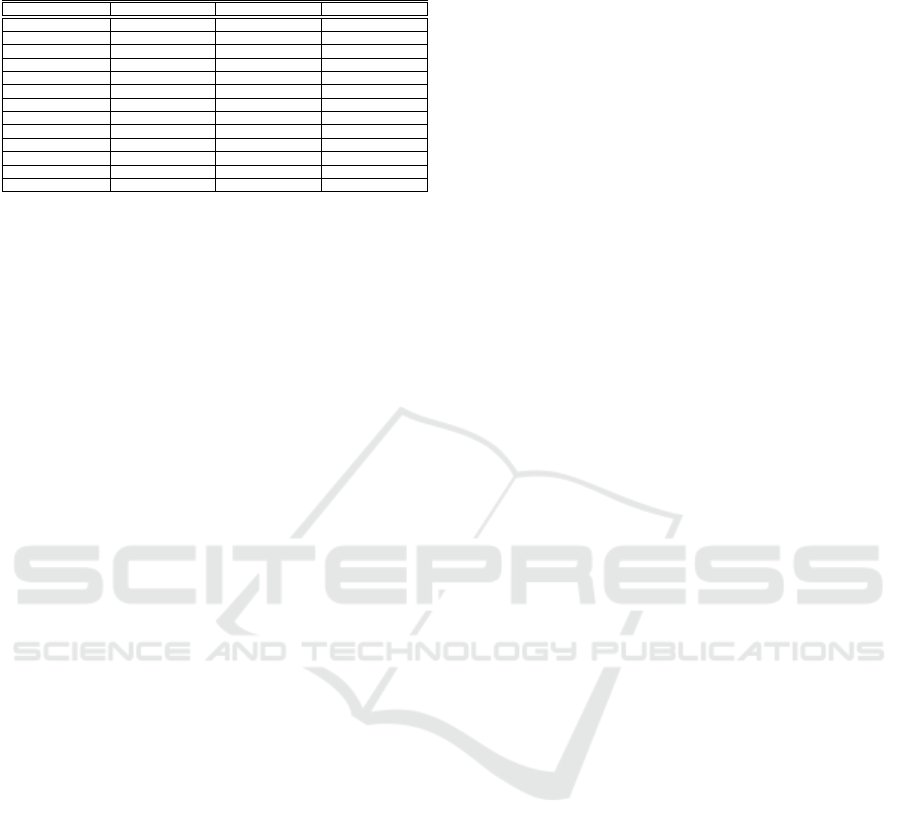
Table 1: Comparisons of the collision-free MAC protocols
for UWSNs.
ED-MAC DL-MAC GC-MAC
Category TDMA-based TDMA-based TDMA-based
Year 2017 2018 2018
Schedule Distributed Distributed Distributed
TDMA status Adaptive slotted Adaptive slotted Adaptive slotted
Network division No Divided to layers Divided to cubes
Clustered No Yes Yes
neighbourhood info One-hop neighbours One-hop neighbours Two-hop neighbours
Priority Depth-based timer Degree timer Node ID
Random time No Yes No
Synchronised Yes Yes Yes
GPS No No Yes
Number of slots 2 × N
max
Equal to d
max
Fixed
Conflict Avoidance No No Yes
tocol is based on. In fact, they are all classified as
a TDMA-based duty-cycle MAC protocols while the
basic information required for their operation are dif-
ferent.
During the deployment process, DL-MAC and
GC-MAC require the network area to be divided into
a number of layers and cubes, respectively, to im-
prove the efficiency of their distributed scheduling.
ED-MAC, however, does not require any network di-
visions. At the same time, its function is not based
on any kind of clustering, whereas this is one of the
requirements of DL-MAC and GC-MAC.
During the first phase, ED-MAC and DL-MAC
require to exchange one-hop neighbouring informa-
tion to be obtained before the scheduling phase. In
their scheduling phases, both protocols set their prior-
ity timers differently. More specifically, ED-MAC’s
timer is used at each node to prioritise slot reserva-
tions depending on the node depth; the deeper the
node, the higher the priority to reserve a slot. Equa-
tion 1 demonstrates how the priority of each sensor
node is calculated. In DL-MAC, the degree timer is
used in each sensor node to start the scheduling phase;
a node with higher d-hop neighbouring nodes, which
can cover more nodes in its 1-hop range at the same
layer, has a higher priority to become a cluster head
(CH) than other nodes. Equation 2 gives the degree
timer of each node in the network, considering a short,
random time duration, λ, to differentiate the sensor
nodes that have the same sensor degree, d
s
.
In the first phase of GC-MAC, however, two-hop
neighbouring information is required to be obtained
before the scheduling phase. The goal of exchanging
the two-hop neighbouring information during the first
phase is to detect the hidden terminal nodes which are
located outside the two-hop neighbouring district of
each other. After creating the neighbouring graph, N
g
,
by each sensor node, the nearest node’s distance to a
reference point, r p, becomes a CH, which is respon-
sible for independently choosing a colour for itself
and different colours for its cluster members (CMs).
Nodes which are located between two adjacent cluster
heads within more than two-hop neighbouring nodes
decide their own colours individually; the lower the
node ID, the higher the priority to select the first avail-
able colour among others.
According to the number of slots, each protocol
has its own algorithm and assumptions which it uses
to divide its operational window differently. In ED-
MAC, for instance, the number of slots is double the
maximum number of nodes in a neighbourhood, N
max
,
in order to exclude the possibility of concurrent data
transmission from a sensor located outside a one-hop
neighbourhood and the node within the neighbour-
hood. Meanwhile, in DL-MAC, the number of slots
is proportional to the maximum node degree found
in the one-hop neighbourhood graphs, d
max
. In GC-
MAC, the number of slots depends on the duration of
the operational phase as well as the slot length, which
is equal to the propagation delay plus a small guard
time to ensure that a packet is entirely received at the
destination before data transmission by another node
can begin.
In addition, GC-MAC the only protocol among
the selection discussed here to introduce the concept
of conflict detection (CD). The primary goal is to de-
tect and resolve any conflicts that may occur between
sensor nodes during the scheduling phase.
3 PERFORMANCE EVALUATION
In this section, we first discuss the simulation scenar-
ios and settings used in our comparison study in the
Aqua-Sim underwater simulation (Xie et al., 2009).
We then define the metrics used in our performance
study. Finally, we compare the design trade-off be-
tween ED-MAC, DL-MAC, and GC-MAC within the
various given scenarios and networks.
3.1 Simulation Scenarios and Settings
We implement our ED-MAC, DL-MAC, and GC-
MAC protocols in Aqua-Sim, which is an NS-2 based
simulator for UWSNs. In our simulations, we con-
sider two scenarios, each of which is evaluated with
reference to two parameters: the traffic rate, and the
number of nodes. In the first scenario, all the under-
water sensor nodes are randomly distributed in a 3D
shallow region of 500m × 500m × 250m. In the sec-
ond scenario, the sensor nodes are randomly deployed
in 3D narrow region of 300m × 300m × 600m. The
following parameters are used in all scenarios, unless
noted otherwise: the traffic rate increases from 0.05
up to 0.5 packets per second. In this set, we randomly
distributed 100 sensor nodes in the given two scenar-
ios. The node density is also increased from 50 to
SENSORNETS 2019 - 8th International Conference on Sensor Networks
88
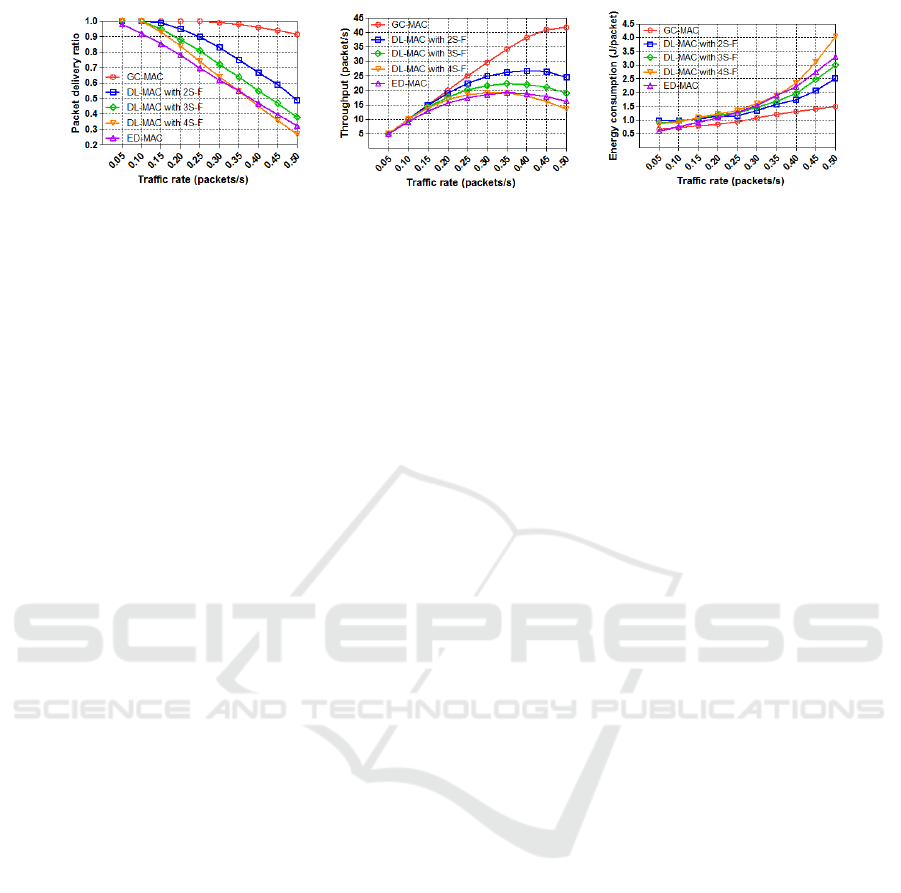
(a) PDR
(b) Throughput
(c) Energy consumption
Figure 1: Shallow region scenario: PDR, Throughput, and Energy consumption vs. Traffic rate.
500 sensor nodes within the same two scenarios. In
this case, the traffic rate is fixed at 0.1 packets per
second. In both scenarios, the power consumption on
transmission mode is 2 Watts, the power consumption
on receive mode is 0.75 Watts, and the power on sleep
mode is 8 mW. The data packet size is set to 1000 bits,
and all other control packets are set at 100 bits. The
channel bit rate (i.e., bandwidth) is set at 10 kbps and
the maximum transmission range is 100 meters.
It should be noted that all the results are averaged
over 20 runs, and that each is obtained with a ran-
domly generated topology in each scenario. The to-
tal simulation time for each run is set to 3600 sec-
onds. In our simulation setup, the length of the first
phase is a predefined fixed value for all sensor nodes,
which is set at each sensor before deployment. Thus,
we consider this phase to be 30 seconds in all three
MAC protocols. The second phase, the scheduling
phase, also uses a predefined constant interval set for
all sensors at the deployment time based on the appli-
cation requirements. Hence, we consider the schedul-
ing phase, T
sch
, to be 90 seconds in these reported
MAC protocols, except GC-MAC which includes the
conflict detection interval, T
cd
added to its scheduling
phase. The T
cd
is set at 30 seconds.
3.2 Performance Metrics
We define the most important metrics in medium ac-
cess control protocols during this comparison study to
evaluate the performance of ED-MAC, DL-MAC, and
GC-MAC protocols as packet delivery ratio (PDR),
throughput, and energy consumption per packet suc-
cessfully received in joules. These metrics are defined
as follows:
The packet delivery ratio, PDR, is defined as the
ratio of the packets successfully received to the to-
tal packets generated in the network. The network
throughput is defined as the number of successful re-
ceived packets divided by the simulation time. The
energy consumption per packet is obtained by divid-
ing the overall energy usage in the network by the
successfully delivered data packets, where the energy
consumption here is measured in joules per packet.
3.3 Simulation Evaluation
In this section, we present the results of the com-
parative performance evaluation of the protocols de-
scribed in Section 2. We first display the simulation
results of the shallow region scenario, before going on
to demonstrate the simulation results of the narrow re-
gion scenario.
3.3.1 Shallow Region Scenario
In this scenario, we first evaluate the PDR, through-
put, and energy consumption under varying traffic
rates in all three MAC protocols, as illustrated in Fig.
(1). In this case, the number of nodes is set to 100
sensor nodes.
Fig. (1a) shows the PDR as a function of data gen-
eration rate. With a low traffic load, the PDR for all
protocols is 100%. When the traffic load further in-
creases, the PDR of ED-MAC and DL-MAC (with
4 and 3 sub-frame configurations) significantly de-
creases. Due to the fact that the scheduling design of
ED-MAC is based on depth criteria, it is more suitable
to a narrow region rather than a shallow one. With a
medium traffic rate (0.25 packets per second), GC-
MAC performs best in terms of packet delivery ratio
by delivering all the data packets. As the traffic rate
further increases, GC-MAC still has the ability to de-
liver most of the packets, followed by DL-MAC with
only 2 sub-frames. This is mainly because GC-MAC
employs the conflict detection mechanism during its
scheduling phase. Regarding the DL-MAC, because
the traffic rate has a reverse relationship with the du-
ration of the operational window, DL-MAC with 2
sub-frames performs better than DL-MAC with 3 and
4 sub-frame conflagrations. DL-MAC with 3 sub-
frames also outperforms DL-MAC with 4 sub-frames.
This is due to the fact that the higher the traffic rate,
the lower the duration of the operational cycle; hence,
no more available slots can be reserved.
A Comparative Performance Evaluation of Distributed Collision-free MAC Protocols for Underwater Sensor Networks
89
(a) PDR
(b) Throughput
(c) Energy consumption
Figure 2: Shallow region scenario: PDR, Throughput, and Energy consumption vs. Number of nodes.
As can be seen in Fig. (1b), the network through-
put of all protocols is proportional to the traffic rate.
When the traffic load increases, the throughput of all
protocols increases correspondingly up to their satu-
ration points. ED-MAC and DL-MAC (with 3 and 4
sub-frames) achieve their maximum capacities sooner
than GC-MAC and DL-MAC do, with 2 sub-frames,
within 0.35 packets per second. DL-MAC with 2
sub-frames and GC-MAC reach their capability re-
garding handling data packets within 0.40 and 0.50
packets per second respectively. We can observe that
GC-MAC outperforms all the other protocols in terms
of throughput with the same traffic rates. This phe-
nomenon is particularly evident in the case of GC-
MAC, because it employs an effective conflict detec-
tion algorithm to avoid collisions, thus considerably
improving network throughput.
Fig. (1c) confirms what we have already seen in
both Fig. (1a) and Fig. (1b). All the protocols are us-
ing a reliable and efficient mechanism for channel ac-
cess and a very limited number of small packets dur-
ing the initial and scheduling phases in order to elim-
inate collisions and achieve high throughput. How-
ever, Fig. (1c) also shows the energy usage per data
packet successfully received. On the one hand, ED-
MAC consumes less energy than any other protocol
during all traffic rates. This is mainly because it has
fewer requirements than the others during the deploy-
ment process as well as the first and second phases,
such as multi layers in DL-MAC and reference points
in GC-MAC. On the other hand, ED-MAC spends a
higher amount of energy per data packet successfully
received than the others, because it delivers a lower
amount of packets than GC-MAC and DL-MAC with
both 2 and 3 sub-frame configurations, as depicted in
Fig. (1a). GC-MAC consumes lower energy in total,
therefore it is the best protocol in terms of energy con-
sumption per packet. It is more interesting to observe
that DL-MAC with 4 sub-frames consumes more en-
ergy per packet at a high traffic rate. This happens
because the higher the traffic rate, the lower the cycle
duration; therefore, there is a short number of slots,
causing high competition between nodes to reserve
those limited slots, and thus greater energy consump-
tion.
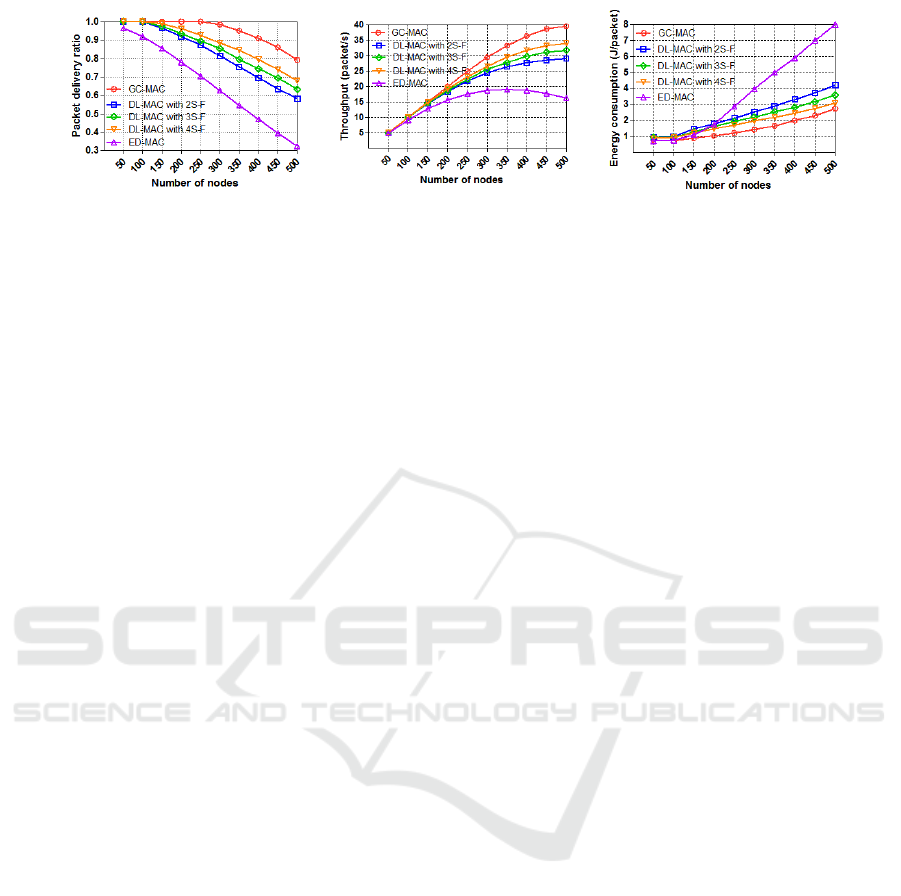
In this scenario, we also evaluate the performance
of all the protocols in terms of PDR, throughput, and
energy consumption under varying number of nodes,
as shown in Fig. (2). This figure illustrates how sparse
and dense sensor nodes in a shallow network can af-
fect the protocols, and examines the scalability and
flexibility among them.
Fig. (2a) illustrates the PDR as a function of num-
ber of nodes. In this figure, GC-MAC clearly outper-
forms all other protocols by handling all data packets
up until 250 nodes. When the node density further in-
creases, the PDR of GC-MAC slightly decreases by
almost 20%. This is because of its efficient schedul-
ing and the conflict detection mechanism that used
during the scheduling phase. However, when the node
density is low, ED-MAC delivers most of the packets
(almost 98%). When the node density is increased,
the PDR of ED-MAC decreases correspondingly to
only deliver 31% with a high dense network. This is
mainly because the ED-MAC policy depends on the
nodes’ depth, i.e., the deeper the node, the higher the
priority to reserve a slot. ED-MAC does not consider
horizontal hidden and exposed nodes located in shal-
lower areas.
It is noteworthy that DL-MAC with higher sub-
frame configurations performs better than DL-MAC
with lower sub-frames. In this figure, DL-MAC with
4 sub-frames outperforms DL-MAC with 2 and 3 sub-
frames. This is because a higher number of sub-
frames implies the ability to handle more nodes. DL-
MAC, with a higher number of sub-frames as a func-
tion of the number of nodes, gives the opposite results
when it is as a function of the traffic rate as depicted in
Fig. (1a). This is because the traffic rate has a reverse
relationship with the duration cycle, as mentioned ear-
lier, while the number of nodes does not, meaning that
when the node density increases, the traffic rate is kept
fixed at 0.1 packets per second.
Changing the node density from 50 to 500 nodes
generates the results shown in Fig. (2b) which shows
that all the throughput of the protocols begin with
SENSORNETS 2019 - 8th International Conference on Sensor Networks
90
(a) PDR
(b) Throughput
(c) Energy consumption
Figure 3: Narrow region scenario: PDR, Throughput, and Energy consumption vs. Traffic rate.
5 packets per second when the node density is low.
As the node density further increases, the through-
put of the protocols rises significantly and eventu-
ally reaches saturation point. In contrast, GC-MAC
has a higher throughput than the others by reaching
nearly 40 packets per second within 500 nodes. DL-
MAC, with three different configurations shows bet-
ter throughput than ED-MAC during all numbers of
nodes. In particular, DL-MAC with 4 sub-frames is
able to handle more data packets than DL-MAC with
2 and 3 sub-frames by almost 21.4% and 6.3% respec-
tively, with a high node density. ED-MAC achieves
almost 20 packets per second within 350 nodes, and
it then degrades as the node density increases. This
is because the ED-MAC’s scheduling policy does not
take the horizontal two-hop neighbourhood into ac-
count. It is therefore not a suitable choice for a shal-
low network.
Fig. (2c) illustrates the relationship between Fig.
(2a) and Fig. (3b). This figure confirms the best
protocol performance in terms of energy consump-
tion. It can clearly be seen that GC-MAC displays
the best performance in terms of energy consump-
tion per data packet over the other protocols during
the whole node density. It is followed by DL-MAC
with 4 sub-frames, which consumes less energy than
DL-MAC with 3 and 2 sub-frame configurations. ED-
MAC, however, spends less energy within 50 and 100
nodes, before increasingly consuming higher energy
per packet up to almost double the others with a high
dense network. This is because, as shown in Fig. (2a),
it delivers fewer packets than the other protocols and
at the same time, it consumes more energy in joules
than the others.
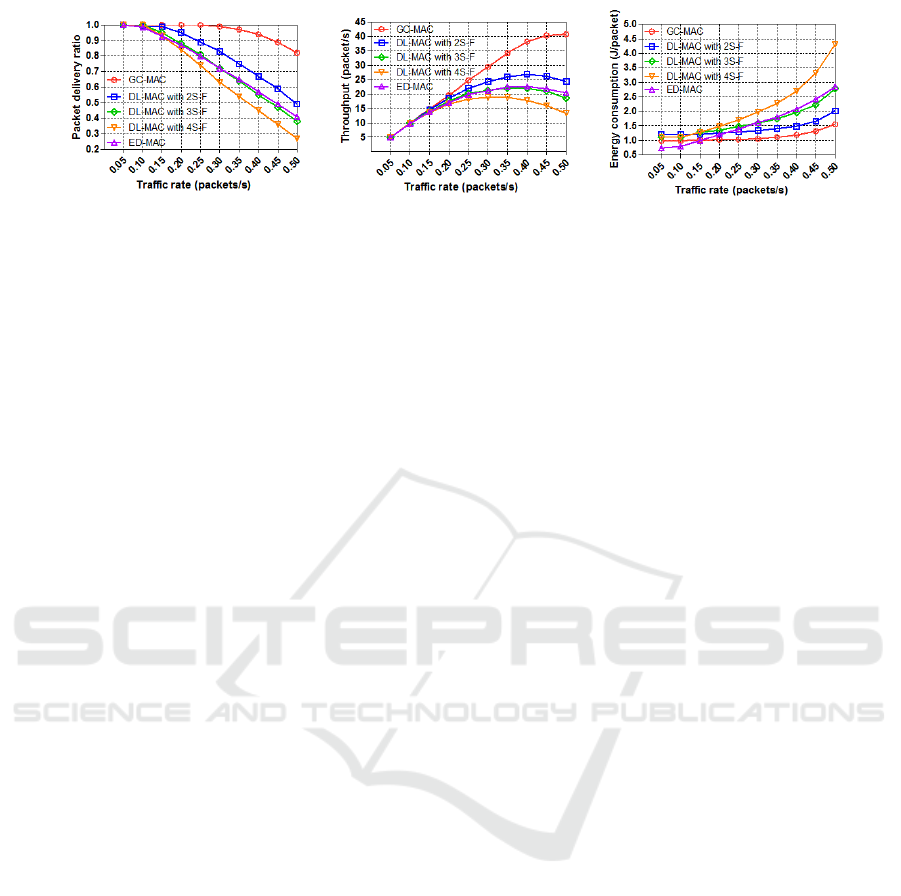
3.3.2 Narrow Region Scenario
In the second scenario, we assess and investigate the
performance of the protocols within a narrow under-
water network in terms of PDR, throughput, and en-
ergy consumption under varying traffic rates, as de-
picted in Fig. (3).
Fig. (3a) shows that the PDR of the three pro-
tocols is proportional to the traffic rate, and that the
PDR of GC-MAC reduces to almost 93% and 80%
corresponding with a traffic rate of 0.4 and 0.5 packets
per second respectively. This is because a higher traf-
fic rate leads to a lower duration of operational round,
resulting in the channel capacity being achieved. Sim-
ilar phenomena are also observed with ED-MAC and
DL-MAC in three different configurations. How-
ever, by carefully considering collision avoidance,
GC-MAC achieves fairly good results for packet de-
livery ratio compared to the others. The result of DL-
MAC with 4 sub-frames is very low with a high traffic
rate because the duration cycle becomes low; there-
fore, nodes are unable to find a free time-slot, i.e.,
a medium channel is divided into three frames, each
frame consists of 4 sub-frames, and each sub-frame
includes a number of slots which is insufficient for
the one-hop neighbouring nodes.
Fig. (3b) presents the network throughput of all
protocols as a function of the traffic rate. The through-
put of the protocols is observed to increase as the
traffic rate increases. This is because the traffic rate
does not exceed the network capacity. Within a traf-
fic rate of (0.3 and 0.4 packets per second), the net-
work congested, resulting in a decreasing throughput
for ED-MAC and DL-MAC with all sub-frame con-
figurations with a growth in traffic rate, except the
GC-MAC trends of 40 packets per second at 0.45 and
0.50 traffic rates. This is mainly because any possi-
bility of collisions is removed by applying the con-
flict detection interval at the end of the scheduling
phase. Therefore, the GC-MAC always achieves the
best throughput compared to ED-MAC and DL-MAC
with different sub-frame configurations.
Fig. (3c) shows the results in terms of energy ef-
ficiency, i.e., the energy consumed per successfully
delivered packet. We can first observe that ED-MAC
is more energy efficient than the others at low traf-
fic rates, because of the lower requirements it faced
during the scheduling phase than other protocols, re-
sulting in a high delivery rate and low energy con-
sumed. It is more interesting to observe that although
GC-MAC consumed more energy than the others at
A Comparative Performance Evaluation of Distributed Collision-free MAC Protocols for Underwater Sensor Networks
91
(a) PDR
(b) Throughput
(c) Energy consumption
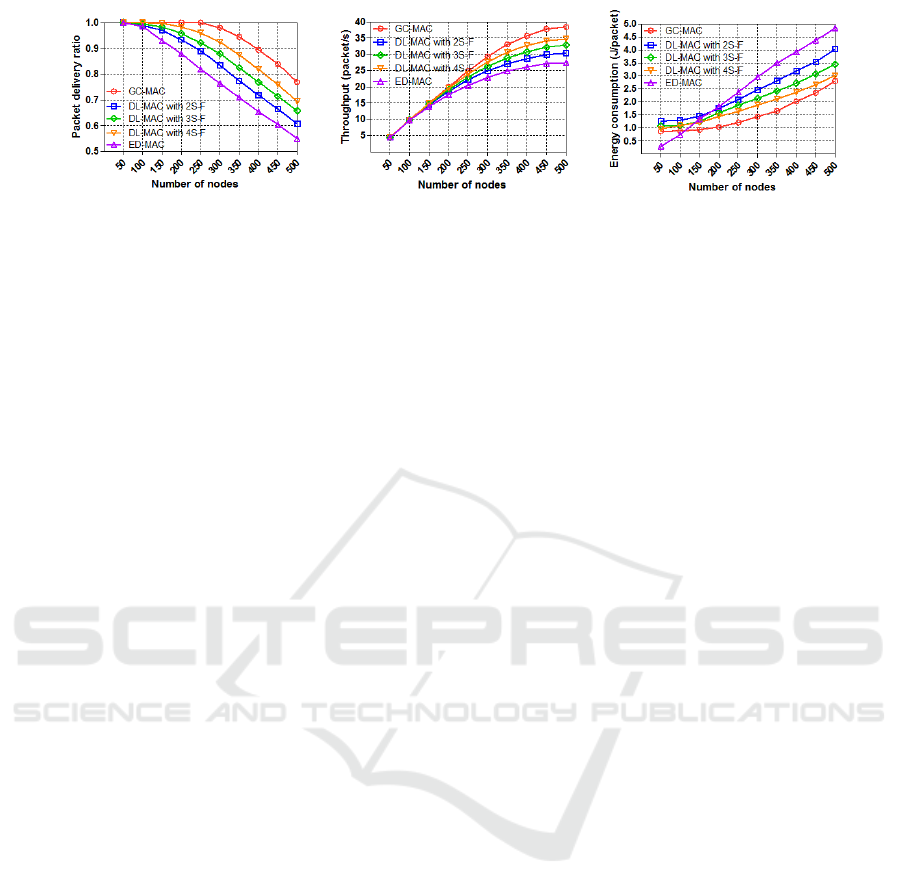
Figure 4: Narrow region scenario: PDR, Throughput, and Energy consumption vs. Number of nodes.
high traffic rates, it can still be considered to have
the best energy efficiency at medium and high traf-
fic rates. This is because its delivery rate outperforms
that of all the other protocols at medium and high traf-
fic rates, as shown previously in Fig. (3a). DL-MAC
with 4 sub-frames, however, is considered inefficient
because it spends double the energy of GC-MAC at
a medium traffic rate. With a high traffic rate, DL-
MAC with 4 sub-frames also consumes nearly three
times more energy than GC-MAC.
This scenario also allows a comparative evaluation
to be carried out of the performance of ED-MAC, DL-
MAC, and GC-MAC in terms of PDR, throughput,
and energy consumption under different sets of node
density, as presented in Fig. (4). This figure shows
how sparse and dense nodes in a narrow network can
affect the performance of the three MAC protocols,
and how scalable and flexible their designs are.
As can be seen in Fig. (4a), the PDR of GC-MAC
remains constant at 100%, as it delivers all the data
packets successfully up to a density of 250 nodes,
then the delivery rate reduces significantly as the node
density further increases. For DL-MAC with three
different sub-frame configurations, the delivery rate
with 2 sub-frames reduces sooner than DL-MAC with
3 and 4 sub-frames. As the node density increases,
the PDR of DL-MAC with 2, 3, and 4 sun-frames is
significantly reduced to deliver approximately 61%,
66%, and 70% data packets respectively in a high
density network (with 500 nodes). This is because a
higher number of sub-frames under a fixed traffic rate
implies an ability to handle more nodes. However, the
PDR of ED-MAC delivers most of the data packets
up to 150 nodes, then it dramatically decreases as the
number of nodes further increases. We can observe
that the delivery rate of ED-MAC is good with an
increased number of nodes, but compared with GC-
MAC and DL-MAC, it has the lowest delivery rate
with all numbers of nodes.
Fig. (4b) presents the results in terms of through-
put. Within 50 and 100 nodes, the network through-
put of all the protocols significantly increases while
achieving 5 and 10 packets per second respectively.
When the number of nodes further increases, the
throughput correspondingly goes up and eventually
reaches the channel threshold. In contrast, GC-MAC
outperforms all the other protocols by handling more
than 35 packets per second with high node density
(within 450 and 500 nodes). Meanwhile, the through-
put of ED-MAC handles lower data packets than the
others. This is because ED-MAC has some limita-
tions during its scheduling phase which do not apply
to GC-MAC and DL-MAC. More specifically, ED-
MAC’s scheduling policy does not take the horizontal
two-hop neighbouring nodes into account, meaning
that a few collisions might occur among them when
the number of nodes increases. DL-MAC is more
scalable and fixable than other protocols in employ-
ing sub-frame configurations. For instance, DL-MAC
with a lower number of sub-frames performs better
than DL-MAC with higher sub-frames in terms of in-
creasing the traffic rate and keeping the node den-
sity fixed. Conversely, when the number of nodes
increases under a fixed traffic rate, DL-MAC with
higher sub-frame configurations performs better than
with lower sub-frames. This is mainly because the
traffic rate has a reverse relationship over the duration
of the operational cycle which, as well as a higher
number of sub-frames, implies the ability to handle
more nodes.
Fig. (4c) illustrates the energy consumption. This
figure shows the best performance in terms of packet
delivery rate along with the energy consumption as-
sociated with sparse and dense nodes. ED-MAC
can be observed to have consumed less energy per
packet than the others with 50 and 100 nodes. As
the node density increases, its energy consumption
rises sharply, reaching just over 4.6 joules per packet
with 500 nodes. However, GC-MAC starts off con-
stant by consuming 1 joule per packet until the num-
ber of nodes exceeds 200 nodes, then its energy con-
sumption increases as the number of nodes increases
too by consuming nearly 2.8 joules per packet with a
high node density. Overall, GC-MAC performs well
from 150 to 500 nodes, followed by DL-MAC with 4
sub-frames. This is because both protocols have more
SENSORNETS 2019 - 8th International Conference on Sensor Networks
92

benefits than the others depending on their scheduling
strategies, as has been explained above.
4 CONCLUSIONS
This paper has presented a comparative performance
evaluation of three collision-free MAC protocols for
channel access in underwater sensor networks. We
have investigated several scenarios that are typical of
the current underwater channel access research. The
first scenario evaluated a shallow network area with
low, medium, and high traffic rates as well as sparse
and dense nodes under a fixed traffic rate. The second
scenario examined the same parameters within a nar-
row network area. These scenarios are mainly used to
study the three protocols’ overall ability, scalability,
and flexibility under sparse and dense sensor nodes as
well as under light to heavy traffic. Our study points
out that every protocol has its own advantages and dis-
advantages, which means that no protocol can fit all
needs in all scenarios.
This study has concluded that ED-MAC achieves
the best performance in a narrow scenario with a light
traffic rate. It is able to handle 99% of the data pack-
ets at a lower energy cost than other protocols. How-
ever, it is not a suitable choice in a shallow scenario
as it does not consider two-hop neighbouring nodes
horizontally. To improve its performance in this re-
gion, more slots are needed to reduce the probabil-
ity of collisions that may occur between nodes lo-
cated horizontally. DL-MAC has the ability to per-
form better than ED-MAC in narrow and shallow re-
gions by scheduling all nodes vertically and horizon-
tally. This is because of its ability to address most
of the MAC problems such as spatial-temporal un-
certainty, the near-far effect, and any hidden/exposed
terminal problems. In terms of flexibility, DL-MAC is
more flexible than other protocols by dividing the net-
work area into frames, and the sensors in each frame
into sub-frames. It is, therefore, suitable for both sce-
narios. While GC-MAC has achieved the best perfor-
mance than others in both narrow and shallow scenar-
ios in terms of reliability and scalability. However, it
has consumed more energy than other MAC protocols
because of the conflict detection interval.
REFERENCES
Akyildiz, I. F., Pompili, D., and Melodia, T. (2005). Under-
water acoustic sensor networks: research challenges.
Ad hoc networks, 3(3):257–279.
Alfouzan, F., Shahrabi, A., Ghoreyshi, S., and Boutaleb,
T. (2018a). An efficient scalable scheduling mac
protocol for underwater sensor networks. Sensors,
18(9):2806.
Alfouzan, F., Shahrabi, A., Ghoreyshi, S. M., and Boutaleb,
T. (2016). Performance comparison of sender-based
and receiver-based scheduling mac protocols for un-
derwater sensor networks. In Network-Based Infor-
mation Systems (NBiS), 2016 19th International Con-
ference on, pages 99–106. IEEE.
Alfouzan, F., Shahrabi, A., Ghoreyshi, S. M., and Boutaleb,
T. (2017). Efficient depth-based scheduling mac pro-
tocol for underwater sensor networks. In Ubiquitous
and Future Networks (ICUFN), 2017 Ninth Interna-
tional Conference on, pages 827–832. IEEE.
Alfouzan, F., Shahrabi, A., Ghoreyshi, S. M., and Boutaleb,
T. (2018b). An energy-conserving depth-based lay-
ering mac protocol for underwater sensor networks.
In 2018 IEEE 88th Vehicular Technology Conference
(VTC), pages 1–6. IEEE.
Alfouzan, F., Shahrabi, A., Ghoreyshi, S. M., and Boutaleb,
T. (2018c). Graph colouring mac protocol for under-
water sensor networks. In 2018 IEEE 32nd Interna-
tional Conference on Advanced Information Network-
ing and Applications (AINA), pages 120–127. IEEE.
Ghoreyshi, S. M., Shahrabi, A., and Boutaleb, T. (2016).
A novel cooperative opportunistic routing scheme for
underwater sensor networks. Sensors, 16(3):297.
Ghoreyshi, S. M., Shahrabi, A., and Boutaleb, T. (2017).
Void-handling techniques for routing protocols in
underwater sensor networks: Survey and chal-
lenges. IEEE Communications Surveys & Tutorials,
19(2):800–827.
Ghoreyshi, S. M., Shahrabi, A., and Boutaleb, T. (2018a).
An efficient auv-aided data collection in underwater
sensor networks. In 2018 IEEE 32nd International
Conference on Advanced Information Networking and
Applications (AINA), pages 281–288. IEEE.
Ghoreyshi, S. M., Shahrabi, A., and Boutaleb, T. (2018b).
A stateless opportunistic routing protocol for under-
water sensor networks. Wireless Communications and
Mobile Computing, 2018.
Hsu, C.-C., Lai, K.-F., Chou, C.-F., and Lin, K.-J. (2009).
St-mac: Spatial-temporal mac scheduling for under-
water sensor networks. In INFOCOM 2009, IEEE,
pages 1827–1835. IEEE.
Preisig, J. (2007). Acoustic propagation considerations for
underwater acoustic communications network devel-
opment. ACM SIGMOBILE Mobile Computing and
Communications Review, 11(4):2–10.
Xie, P. and Cui, J.-H. (2007). R-mac: An energy-efficient
mac protocol for underwater sensor networks. In
2007 International Conference on Wireless Algo-
rithms, Systems and Applications, pages 187–198.
IEEE.
Xie, P., Zhou, Z., Peng, Z., Yan, H., Hu, T., Cui, J.-H., Shi,
Z., Fei, Y., and Zhou, S. (2009). Aqua-sim: An ns-2
based simulator for underwater sensor networks. In
OCEA. 2009, MTS biloxi-marine tec. for our fut.: glo.
and local chall., pages 1–7. IEEE.
A Comparative Performance Evaluation of Distributed Collision-free MAC Protocols for Underwater Sensor Networks
93
