
KYPO Cyber Range: Design and Use Cases
Jan Vykopal
1
, Radek Ošlejšek
2
, Pavel
ˇ
Celeda
1
, Martin Vizváry
1
and Daniel Tovar
ˇ
nák
1
1
Institute of Computer Science, Masaryk University, Brno, Czech Republic
2
Faculty of Informatics, Masaryk University, Brno, Czech Republic
Keywords:
KYPO, Cyber Range, Cyber Attack, System Design, Cloud Computing, Network Virtualization.
Abstract:
The physical and cyber worlds are increasingly intertwined and exposed to cyber attacks. The KYPO cyber
range provides complex cyber systems and networks in a virtualized, fully controlled and monitored environ-
ment. Time-efficient and cost-effective deployment is feasible using cloud resources instead of a dedicated
hardware infrastructure. This paper describes the design decisions made during it’s development. We pre-
pared a set of use cases to evaluate the proposed design decisions and to demonstrate the key features of the
KYPO cyber range. It was especially cyber training sessions and exercises with hundreds of participants which
provided invaluable feedback for KYPO platform development.
1 INTRODUCTION
Operational cyber environments are not suitable for
building a systematic knowledge of new cyber threats
and to train responses to them. Therefore, cyber
ranges or testbeds are usually built to provide a re-
alistic environment suitable for training security and
operations teams. A cyber range provides a place
to practice correct and timely responses to cyber at-
tacks. The learners can practice skills such as network
defence, attack detection and mitigation, penetration
testing, and many others in a realistic environment.
Despite the increasing popularity of cyber exer-
cises (Welch et al., 2002; NATO CCDCOE, 2017),
there is very limited public information about plat-
forms used. Due to the specific use of cyber ranges
(government, military, industry), many technical de-
tails are regarded as sensitive. This paper shall pro-
vide an integrated view of the KYPO cyber range
(KYPO, 2017), which has been in development since
2013. KYPO was made for researching and develop-
ing new security methods, tools and for training se-
curity teams and students. It provides a virtualised
environment for performing complex cyber attacks
against simulated cyber environments.
Apart from the technical aspects, the transdisci-
plinary features of cyber exercises are equally im-
portant. Preparing and carrying out cyber exercise
requires substantial time, effort and financial invest-
ments (Childers et al., 2010). The major workload is
carried out by the organizers, particularly in the exer-
cise preparation phase. The ultimate goal of a cyber
range developers is to minimize this workload and to
support all phases of an exercise’s life cycle. We have
designed and executed a cyber defence exercise to
validate the KYPO cyber range prototype. The tech-
nical part of the exercise relies on the built-in capa-
bilities of KYPO and was used in six runs of a cyber
defence exercise for 50 participants. Several lessons
were learned which provided important guidance for
further KYPO research and development.
This paper is divided into six sections. Section 2
shall provide background information about testbeds
and cyber ranges. Section 3 will describe KYPO’s
architecture design and list the main components of
the proposed architecture. Section 4 shall describe
the user interface and interactions in the KYPO cyber
range. Section 5 will show three selected use cases.
Finally, Section 6 will conclude the paper and outline
future work on KYPO.
2 RELATED WORK
In this section, we introduce generic testbeds which
can be used in cyber security. Then we focus on en-
vironments which have been specially developed for
cyber security training. While some of these evolved
from generic testbeds, others were designed with cy-
ber security in mind. The environments are costly,
but versatile large-scale infrastructures with state of
the art parameters and features as well as
310
Vykopal, J., Oslejsek, R., Celeda, P., Vizvary, M. and Tovarnak, D.
KYPO Cyber Range: Design and Use Cases.
DOI: 10.5220/0006428203100321
In Proceedings of the 12th International Conference on Software Technologies (ICSOFT 2017), pages 310-321
ISBN: 978-989-758-262-2
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

lightweight alternatives with limited scope, function-
ality and resources.
The Australian Department of Defence published
an extensive survey of state of the art cyber ranges
and testbeds (Davis and Magrath, 2013). The survey
lists more than 30 platforms which can be used for
cyber security education worldwide. This number is
based on publicly available, non-classified informa-
tion. Since the development and operation of some
cyber ranges is funded by the military and govern-
ments of various countries, there is likely to be other
classified cyber ranges. To cover recent advances and
innovations, we have done a systematic literature re-
view from 2013 to 2017.
2.1 Generic Testbeds
Emulab/Netbed (White et al., 2002) – this is a clus-
ter testbed providing basic functionality for deploy-
ing virtual appliances, configuring flexible network
topologies and the emulation of various network char-
acteristics. The network topology must be described
in detail by an extension of NS language. Emulab al-
locates computing resources for the specified network
and instantiates it in a dedicated HW infrastructure.
Emulab has been developed since 2000 and there
are currently about 30 of its instances or derivates in
use or under construction worldwide (Emulab, 2017).
It can be considered to be a prototype of an emulation
testbed for research into networking and distributed
systems. It provides accurate repeatable results in ex-
periments with moderate network load (Siaterlis et al.,
2013).
CyberVAN (Cyber Virtual Ad hoc Network, 2017)
– this is a cyber experimentation testbed funded by
the U.S. Army Research Laboratory and developed
by Vencore Labs. CyberVAN enables arbitrary ap-
plications to run on Xen-based virtual machines that
can be interconnected by arbitrary networks topolo-
gies. It employs network simulators such as OPNET,
QualNet, ns-2, or ns-3, so the network traffic of emu-
lated hosts travels through the simulated network. As
a result, this hybrid emulation enables the simulation
of large strategic networks approximating a large ISP
network.
2.2 Cyber Ranges
DETER/DeterLab (Mirkovic et al., 2010) – the DE-
TER project was started in 2004 with the goal of ad-
vancing cyber security research and education. It is
based on Emulab software and has developed new ca-
pabilities, namely i) an integrated experiment man-
agement and control environment SEER (Schwab
et al., 2007) with a set of traffic generators and mon-
itoring tools, ii) the ability to run a small set of risky
experiments in a tightly controlled environment that
maximizes research utility and minimizes risk (Wro-
clawski et al., 2008), and iii) the ability to run large-
scale experiments through a federation (Faber and
Wroclawski, 2009) with other testbeds that run Em-
ulab software, and with facilities that utilize other
classes of control software. Lessons learned through
the first eight years of operating DETER and an out-
line of futher work are summarized in (Benzel, 2011).
DETER operates DeterLab which is an open fa-
cility funded by U.S. sponsors and hosted by the
University of Southern California and University
of California, Berkeley. It provides hundreds of
general-purpose computers and several specialized
hosts (e. g., FPGA-based reconfigurable hardware el-
ements) interconnected by a dynamically reconfig-
urable network. The testbed can be accessed from
any machine that runs a web browser and has an SSH
client. Experimental nodes are accessed through a
single portal node via SSH. Under normal circum-
stances, no traffic is allowed to leave or enter an ex-
periment except via this SSH tunnel.
National Cyber Range (NCR) (NCR, 2017) –
the NCR is a military facility to emulate military
and adversary networks for the purposes of realistic
cyberspace security testing, supporting training and
mission rehearsal exercises (Ferguson et al., 2014).
Its development and operation have been funded by
the U.S. Department of Defense since 2009 and the
target user group are U.S. governmental organiza-
tions. The NCR enables operational networks to be
represented, and interconnected with military com-
mand and control systems, with the ability to restore
to a known checkpoint baseline to repeat the test with
different variables. The NCR is instrumented with
traffic generators and sensors collecting network traf-
fic and data from local and distributed nodes. The
NCR has demonstrated the ability to rapidly configure
a variety of complex network topologies and scale up
to 40,000 nodes including high-fidelity realistic rep-
resentations of public Internet infrastructure.
Michigan Cyber Range (MCR) (MCR, 2017) –
this is an unclassified private cloud operated by Merit,
a non-profit organization governed by Michigan’s
public universities in the USA. The MCR has offered
several services in cyber security education, testing
and research since 2012.
The MCR Secure Sandbox simulates a real-world
networked environment with virtual machines that act
as web servers, mail servers, and other types of hosts.
Users can add preconfigured virtual machines or build
their own virtual machines. Access to the Sandbox is
KYPO Cyber Range: Design and Use Cases
311

provided through a web browser or VMware client
from any location.
Alphaville is MCR’s virtual training environment
specifically designed to test teams’ cyber security
skills. Alphaville consists of information systems
and networks that are found in a typical information
ecosystem. Learners can develop and exercise their
skills in various hands-on formats such as defence and
offense exercises.
SimSpace Cyber Range (Lee Rossey, 2015) – a
U.S. private company runs this cyber range, which
enables the realistic presentation of networks, infras-
tructure, tools and threats. It is offered as a service
hosted in public clouds (Amazon Web Services or
Google), at the SimSpace datacenter, or deployed in
the customer’s infrastructure and premises.
The cyber range provides several types of pre-
configured networks containing from 15 to 280 hosts
which emulate various environments (generic, mili-
tary, financial). It is possible to generate traffic emu-
lating enterprise users with host-based agents and run
attack scenarios automatically by combining various
attacker tasks. All activities can be also monitored
at network and scenario level (network traffic, attack-
ers’ and defenders’ actions, and activities of emulated
users at end hosts). The platform is controlled via
a web portal that also provides access to the results
of an analysis and assessment of monitored activities
within the cyber range.
EDURange (EDURange, 2017) – this is a cloud-
based framework for designing and instantiating in-
teractive cyber security exercises funded by the U.S.
National Science Foundation and developed by Ev-
ergreen State College, Olympia, Washington. EDU-
Range is intended for teaching ethical hacking and
cyber security analysis skills to undergraduate stu-
dents. It is an open-source software with a web fron-
tend based on Ruby and backend deploying virtual
machines and networks hosted at Amazon Web Ser-
vices. The exercises are defined by a YAML-based
Scenario Description Language and can be instanti-
ated by the instructor for a selected group of students.
EDURange supports Linux machines which can be
accessed via SSH. It also has built-in analytics for
host-based actions, namely a history of commands ex-
ecuted by students during the exercise.
2.3 Lightweight Platforms
Avatao (Buttyán et al., 2016; Avatao, 2017) – this is
an e-learning platform offering IT security challenges
which are created by an open community of security
experts and universities. Avatao is developed by an
eponymous spin-off company of CrySyS Lab at Bu-
dapest University of Technology and Economics,
Hungary. It is a cloud-based platform using
lightweight containers (such as Docker) instead of
a full virtualization. This enables it to start a new
challenge in its virtual environment very quickly in
comparison with booting full-fledged emulated hosts.
Learners and teachers access the challenges via web
browser. Hosts and services within the virtual envi-
ronment are accessed by common network tools and
protocols such as Telnet or SSH.
CTF365 (CTF365, 2017) – this is a Romanian
commercial security training platform with a focus
on security professionals, system administrators and
web developers. It is an IaaS where users (organized
in teams) can build their own hosts and mimic the
real Internet. CTF365 provides a web interface for
team management, instantiating virtual machines us-
ing predefined images and providing credential to ac-
cess the machines using VPN and SSH. Each team
has to defend and attack the virtual infrastructure at
the same time. As a defender, a team has to set up
a host which runs common Internet services such as
mail, web, DB in 24/7 mode. As an attacker, the team
has to discover their competitor’s vulnerabilities and
submit them to the scoring system of the CTF365 por-
tal.
Hacking-Lab (Security Competence, 2017) – this
is an online platform for security training and com-
petitions run by a Swiss private company. It pro-
vides more than 300 security challenges and has about
40,000 users. The platform consists of a web por-
tal and a network with vulnerable servers emulated
using virtual machines or Docker containers. Each
team administers a set of vulnerable applications and
has to perform several tasks simultaneously, namely
attack the applications of their competitors, keep their
own applications secure, and up and running, find and
patch vulnerabilities, keep applications up and run-
ning, and solve challenges. A Linux-based live CD is
provided to ease the use of Hacking-Lab. It contains
many hacking tools and is preconfigured for VPN ac-
cess.
iCTF and InCTF iCTF framework (Vigna et al.,
2014) was developed by the University of Califor-
nia, Santa Barbara for hosting their iCTF, the largest
capture the flag competition in the world since 2002.
The goal of this open-source framework is to provide
customizable competitions. The framework creates
several virtual machines running vulnerable programs
that are accessible over the network. The players’ task
is to keep these programs functional at all times and
patch them so other teams cannot take advantage of
the incorporated vulnerabilities. The availability and
functionality of these services is constantly tested by
ICSOFT 2017 - 12th International Conference on Software Technologies
312

a scorebot. Each service contains a flag, a unique
string that the competing teams have to steal so that
they can demonstrate the successful exploitation of a
service. This flag is also updated from time to time by
the scorebot.
InCTF (Raj et al., 2016) is a modification of
iCTF that uses Docker containers instead of vir-
tual machines. This enhances the overall game ex-
perience and simplifies the organization of attack-
defence competitions for a larger number of partici-
pants. However, it is not possible to monitor network
traffic, capture exploits and reverse engineer them to
identify new vulnerabilities used in the competition.
3 KYPO ARCHITECTURE
DESIGN
The KYPO cyber range is designed as a modular dis-
tributed system. In order to achieve high flexibil-
ity, scalability, and cost-effectiveness, the KYPO plat-
form utilizes a cloud environment. Massive virtu-
alization allows us to repeatedly create fully opera-
tional virtualized networks with full-fledged operat-
ing systems and network devices that closely mimic
real world systems. Thanks to its modular architec-
ture, the KYPO is able to run on various cloud com-
puting platforms, e. g., OpenNebula, or OpenStack.
A lot of development effort has been dedicated to
user interactions within KYPO since it is planned to
be offered as Platform as a Service. It is accessed
through web browser in every phase of the life cy-
cle of a virtualized network: from the preparation and
configuration artifacts to the resulting deployment, in-
stantiation and operation. It allows the users to stay
focused on the desired task whilst not being distracted
with effort related to the infrastructure, virtualization,
networking, measurement and other important parts
of cyber research and cyber exercise activities.
3.1 Platform Requirements
At the beginning of the development of the KYPO
platform, many functional and non-functional re-
quirements were defined both by the development
team and the project’s stakeholders. The requirements
were first prioritized using the MSCW method (Must
have, Should have, Could have, and Would like, but
will not have). After the prioritization process, we
identified the must have requirements that were the
most likely to influence the high-level architecture
of the KYPO platform as a whole. The following
selected requirements have strongly influenced our
high-level design choices.
Flexibility – the platform should support the in-
stantiation of arbitrary network topologies, ranging
from single node networks to multiple connected net-
works. For the topology nodes, a wide range of op-
erating systems should be supported (including arbi-
trary software packages). The creation and config-
uration of such topologies should be as dynamic as
possible.
Scalability – the platform should scale well in
terms of the number of topology nodes, processing
power and other available resources of the individual
nodes, network size and bandwidth, the number of
sandboxes (isolated virtualized computer networks),
and the number of users.
Isolation vs. Interoperability – if required, differ-
ent topologies and platform users should be isolated
from the outside world and each other. On the other
hand, integration with (or connection to) external sys-
tems should be achieved with reasonable effort.
Cost-Effectiveness – the platform should support
deployment on commercial off-the-shelf hardware
without the need for a dedicated data center. The op-
erational and maintenance costs should be kept as low
as possible.
Built-In Monitoring – the platform should natively
provide both real-time and post-mortem access to de-
tailed monitoring data. These data should be related
to individual topologies, including flow data and cap-
tured packets from the network links, as well as node
metrics and logs.
Easy Access – users with a wide range of expe-
rience should be able to use the platform. For less
experienced users, web-based access to its core func-
tions should be available, e. g., a web-based terminal.
Expert users, on the other hand, should be able to in-
teract with the platform via advanced means, e. g., us-
ing remote SSH access.
Service-Based Access – since the development ef-
fort and maintenance costs of a similar platform are
non-trivial for a typical security team or a group of
professionals, our goal is to provide transparent ac-
cess to the platform in the form of a service.
Open Source – the platform should reuse suitable
open source projects (if possible) and its release arti-
facts should be distributed under open source licenses.
3.2 High-Level Architecture
It can be seen that many of the requirements were al-
ready created with a cloud computing model in mind.
This naturally influenced the KYPO platform high
level architecture (Figure 1). The platform is com-
posed of five main components – infrastructure man-
agement driver, sandbox management, sandbox data
KYPO Cyber Range: Design and Use Cases
313
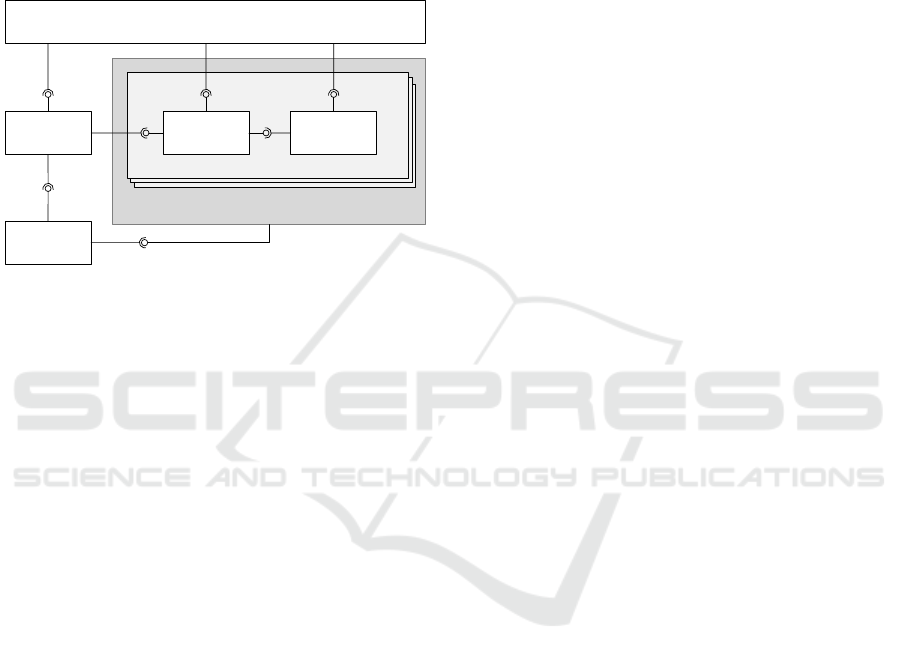
store, monitoring management, and the platform man-
agement portal serving as the main user interaction
point. These components interact together in order
to build and manage sandboxes residing in the un-
derlying cloud computing infrastructure. In the fol-
lowing paragraphs, we will individually describe each
component. Since the user interface (platform man-
agement portal) is very complex it is thoroughly de-
scribed in Section 4.
Computing Infrastructure
Sandbox
Sandbox
Management
Infrastructure
Management
Driver
Sandbox Data
Store
Monitoring
Management
Platform Management Portal
Figure 1: KYPO platform high-level architecture overview.
3.2.1 Infrastructure Management Driver
The infrastructure management driver is used to con-
trol the computing infrastructure. A computing in-
frastructure consists, in general, of housing facilities,
physical machines, network devices, and other hard-
ware and related configuration artifacts. It forms the
raw computing resources such as storage, operating
memory, and processing power. KYPO is designed to
run on public cloud computing infrastructure so that
sandboxes can be built without the need of dedicated
infrastructure.
The infrastructure management driver is the only
component of the architecture which directly access
the low level computing infrastructure. Therefore, the
support of multiple cloud providers is isolated to this
single component. API provided by the driver offers
services which enable the management of virtual ma-
chines and networks in a unified way. At present, the
KYPO runs on OpenNebula cloud and the adaptation
to OpenStack is under development.
3.2.2 Sandbox Management Component
The sandbox management component is used to cre-
ate and control sandboxes in the underlying comput-
ing infrastructure. During the deployment of a sand-
box, it orchestrates the infrastructure via infrastruc-
ture management driver in order to configure virtual
machines and networking.
Advanced networking is one of the most important
features of the KYPO platform. KYPO uses cloud
networking as an overlay infrastructure. The underly-
ing cloud infrastructure uses IEEE 802.1Q, i.e. Vir-
tual LAN tagging, using Q-in-Q tunneling. Q-in-Q
tunneling allows KYPO to configure sandboxes net-
working dynamically. It also does not depend on the
L2 and L3 network addressing of the infrastructure,
using a separate networking configuration. The sand-
box networking allows users to configure their own
L2/L3 addressing scheme in each LAN.
The networking in the sandboxes is done using
one or more Lan Management Nodes (LMN). Each
LAN network is managed by one LMN. LMN is a
standard Debian system with an Open vSwitch (OvS)
multilayer virtual switch (Linux Foundation, 2017).
It combines standard Linux routing and OvS packet
switching. The intra-LAN communication is done on
the L2 layer using OvS as a learning switch. The
inter-LAN communication is forwarded from switch
to standard Linux routing tables.
The notion of KYPO points is used to connect ex-
ternal devices, systems and networks to the KYPO en-
vironment. Since the KYPO platform is cloud-based,
there is a need for the mechanism to be able to connect
systems and devices that do not have a virtualized op-
erating system, i. e. they are hardware-dependent, or
location dependent.
We have developed a device which connects such
systems – based on a Raspberry Pi platform which
automatically connects after its boot via Virtual Pri-
vate Network (VPN) tunnel to the sandbox in KYPO.
This makes the point very easy to use since it has very
small proportions and it can be easily delivered and
connected anywhere. The connection is secured via
the properties of the VPN.
3.2.3 Sandbox Data Store
The sandbox data store manages information related
to the topology of a sandbox and provides its generic
abstraction. Since the KYPO is partially an overlay
environment, it is necessary to bridge the configura-
tion of nodes in the cloud infrastructure and the inner
configuration of virtual machines.
Therefore, modules working with sandbox-related
data, e. g., the platform management portal or the
monitoring management component, do not retrieve
information directly from the cloud but utilize the
sandbox data store instead.
The store contains information about end nodes,
IP addresses, networks, routes, and network proper-
ties during the whole lifetime of the sandbox. They
are updated by the sandbox management component
whenever changes to the sandbox are made. For ex-
ample, when a user deploys a new node or deletes a
ICSOFT 2017 - 12th International Conference on Software Technologies
314

current node.
3.2.4 Monitoring Management Component
The monitoring management component provides
fine-grained control over the configuration of the
built-in monitoring and also provides an API that ex-
poses the acquired monitoring data to external con-
sumers (e. g., platform management portal). All the
necessary information about the sandbox’s topology
is read from the sandbox data store, i. e. information
about existing network links and nodes. Currently,
the platform supports simple network traffic metrics
(e. g., packets, and error octets) and there is also sup-
port for flow-based monitoring and full-packet cap-
ture.
In order to cope with the largely heterogeneous
monitoring data that is inherently generated within
sandboxes and the KYPO platform itself, we use the
normalizer design pattern and the notion of a monitor-
ing bus component implementing this pattern, as de-
scribed in detail by (Tovar
ˇ
nák and Pitner, 2014). The
long-term objective of such a deployment is to render
the monitoring architecture within the platform fully
event-driven. This is motivated by the growing need
for advanced monitoring data corelations both in the
terms of real-time and post-mortem analysis.
During the development of the platform, we en-
countered a problem as to how to differentiate be-
tween the monitoring functionality that should be
built in, and the functionality that should be, concep-
tually, a part of a cyber exercise scenario and the re-
sulting sandbox topology. We have determined that
a reasonable decisive factor is the intended consumer
of the monitoring data and the desired intrusiveness
of the monitoring components on the scenario.
For example, in the case of host-based monitor-
ing, there is a need for various monitoring agents to
be installed and configured on the end-nodes. If the
intended consumer is not part of the scenario, e. g., the
monitoring data are used for the purposes of progress
tracking or scoring in cyber-exercises, the monitoring
agents must be protected from misconfiguration and
other manipulation by the participants. This, how-
ever, breaks the fourth-wall, so to say, since the partic-
ipants need to be informed that such misconfiguration
is prohibited, including network misconfiguration and
so on. This can be sometimes seen as intrusive.
When the intended consumers are the partici-
pants themselves, the monitoring components and
their configuration should be a part of the scenario.
This way it can be misconfigured or stopped alto-
gether. Yet in this case, the monitoring data can be
rendered unusable for external consumers, e. g., for
the purposes of ex-post analysis.
3.2.5 Platform Management Portal
The Platform Management Portal (PM Portal) medi-
ates access to the platform for the end users by pro-
viding them with interactive visual tools. In particu-
lar, the PM Portal is designed to cover the following
types of interactive services.
Management of cyber exercises – the preparation
of cyber exercises is very complex process which re-
quires us to define security scenarios, allocate hard-
ware resources, manage participants, and so on. The
PM Portal supports the automation of these tasks by
introducing a system of user roles and corresponding
interactions.
Collaboration – many security scenarios are based
on mutual collaboration where multiple participants
share a sandbox and jointly solve required tasks or,
on the contrary, compete against each other. The PM
Portal supports multiple flexible collaboration modes
covering a wide range of scenarios.
Access to sandboxes – the PM Portal enables end
users to log into computers allocated in a sandbox
via remote desktop web client as an alternative user-
friendly access point to the portal-independent com-
mand line SSH access.
Interactive visualizations – regardless of whether
a user is analyzing a new malware or is learning new
defence techniques against attackers, it is always cru-
cial to understand and keep track of progress and cur-
rent developments inside the sandbox. The PM Por-
tal, therefore, provides specialized visualization and
interaction techniques which mediate data and events
measured in sandboxes.
4 USER INTERFACE AND
INTERACTIONS
The variability of security issues that the KYPO in-
frastructure is able to emulate places high demands
on the realization of the Platform Management Portal
and its interactive services. While traditional appli-
cations are usually based on clearly defined require-
ments and use cases that delimit software architecture
as well as provided functionality, the design of the PM
Portal has to deal with the dynamic character of its us-
age. This is because the use cases are defined at the
user level as part of security scenarios and then user
interfaces have to also be either definable or at least
highly configurable at the user level.
To assure high accessibility of the services for all
types of end users, the PM Portal is designed as a web
application where users are not bothered by the need
to install anything on their device (not even browser
KYPO Cyber Range: Design and Use Cases
315

plugins or extensions such as Java or Flash).
To deal with the dynamic character of the KYPO’s
use, the PM Portal complies with Java Enterprise Web
Portal standards, as defined in JSR 168 and JSR 286.
Web portals are designed to aggregate and personal-
ize information through application-specific modules,
so-called portlets. Portlets are unified cross-platform
pluggable software components that visually appear
as windows located on a web page. Once developed,
a portlet can usually be reused in many security sce-
narios. Another key feature of enterprise web por-
tals is their support of inter-portlet communication,
synchronization and deployment into web pages and
sites. We utilized these features to create complex
scenario-specific user interfaces as preconfigured web
pages composed of mutually cooperating portlets.
4.1 Role-based Access Control
Preparation of a cyber exercise is very complex
task comprising scenario definition, allocation of re-
sources, user management, and so on. In order to au-
tomatize these processes by means of user interaction,
it is necessary to define user roles with clear access
rules and responsibilities.
Scenarist devises security scenarios with all nec-
essary details including sandbox definition and the de-
sign of web user interfaces for end users engaged in
the scenario. At this level, the interfaces are defined as
generic templates used to generate per-user web pages
in further “scenario execution” phases. Besides the
scenario and UI management, scenarists also autho-
rize selected users to become organizers of exercises
with adequate responsibilities.
An organizer is a well-instructed technically
skilled person authorized by a scenarist to plan and
prepare cyber exercises or experiments of a particular
security scenario. Organizational activities consist of
the allocation of sandboxes in the cloud, adjusting in-
formation pages, configuring a scoring subsystem and
other scenario-specific services, inviting participants,
etc. Organizers also delegate selected participants to
be supervisors of the exercise.
Participants represent end users engaged in a par-
ticular cyber exercise or experiment. They utilize
web UIs prepared by scenarists and perform tasks
prescribed by the security scenario. If the users are
involved in multiple experiments or exercises at the
same time, they have to choose a particular one at the
beginning of the interaction.
We distinguish between ordinary participants and
those having extended supervising privileges. Or-
dinary participants have just one scenario role as-
signed. Scenario roles limit particular participants’
access to particular hosts in the sandbox based sce-
nario definition. For instance, an exercise scenario
defines the roles of an attacker and a defender. The
attacker then has no direct access to the hosts con-
trolled by the defender and vice versa. In contrast,
participants with supervisor privileges have access to
all nodes in the network implicitly. Supervisors also
usually utilize specific web forms and visualizations
that reflect their specific needs. Another difference
can be found in a multi-sandbox collaboration mode.
While ordinary participants have access to only a sin-
gle sandbox, supervisors can access all the sandboxes
allocated for a given exercise.
Authentication of all users is based on federated
identities. Credentials of users attempting to log into
the PM Portal are redirected to a central system for
identity management, which integrates many existing
identity providers and authenticates users against their
external electronic identities. Besides well-known
identity providers (such as Facebook or Google) it is
easy to integrate other external accounts on demand
via a LDAP service. Participants of cyber exercises
can, therefore, use their Google or corporate user-
names and passwords to access the KYPO infrastruc-
ture.
Once authenticated, the authorization of a user is
managed directly in the KYPO infrastructure. The
PM Portal checks the user against his or her as-
signed roles and offers the appropriate web pages and
portlets for further interaction. The more roles the
user has assigned, the broader the user interfaces of
the PM Portal are available.
4.2 Collaboration Modes
The combination of flexible web UIs (supported by
the PM Portal) and the loose coupling of individual
portlets (with sandboxes via remote access) enables
us to simulate various collaboration strategies (Eich-
ler et al., 2015). Three basic collaboration modes are
depicted in Figure 2. The combination of these modes
with other traditional web-browser features (such as
multiple browser tabs opened at the same time or
multi-display views) provide a very flexible solution
covering a wide range of security scenarios.
Individual sandboxes – every participant has their
own private sandbox and web user interface. The web
UI is defined by a scenarist only once in the form of a
template and then the participants have the same set of
interactive tools available. Thanks to its cloud-based
infrastructure, it is easy to allocate many identical
sandboxes for individual users on demand. Neverthe-
less, sandboxes do not depend on each other. There-
fore, participants can complete the same tasks via the
ICSOFT 2017 - 12th International Conference on Software Technologies
316
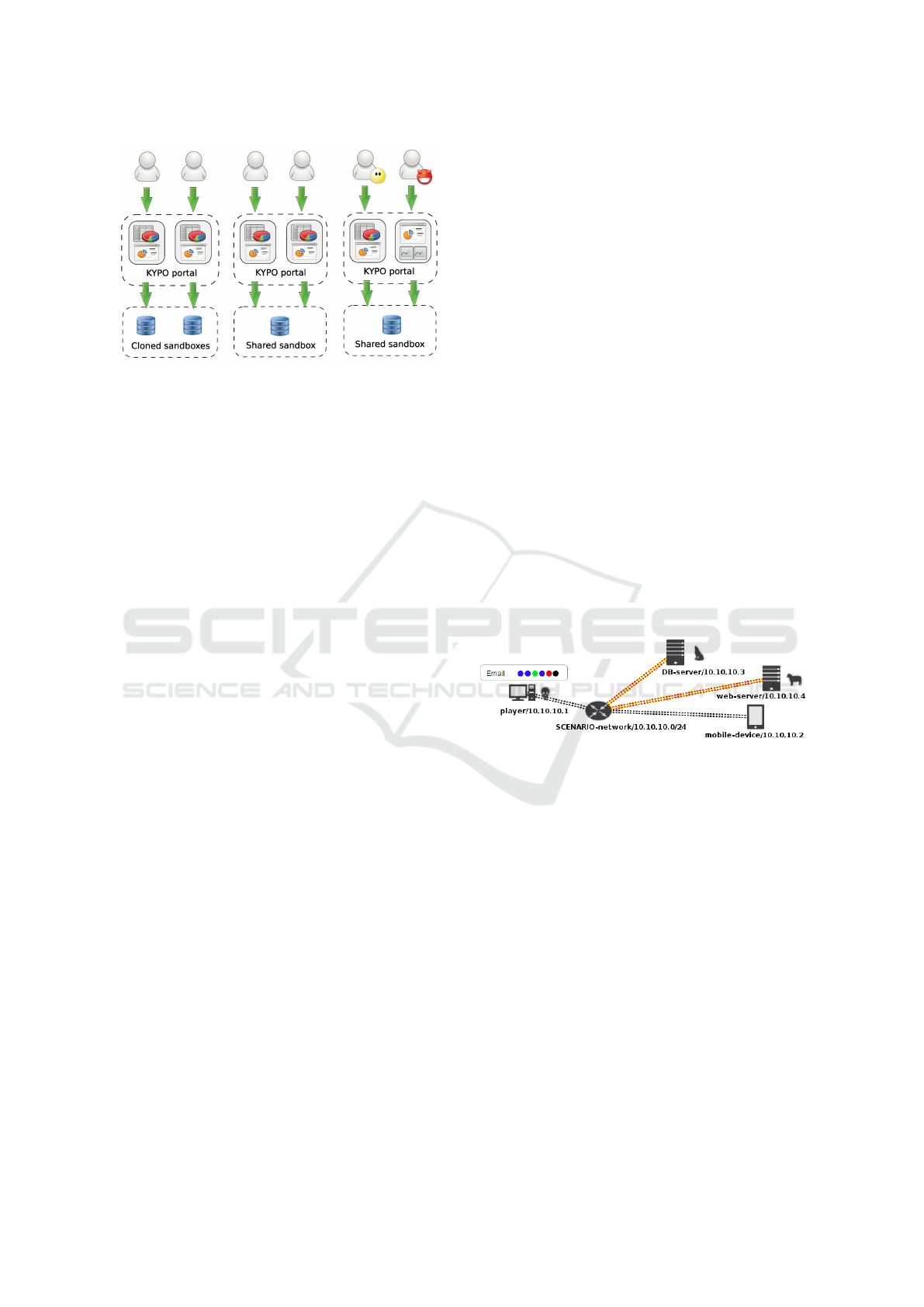
Figure 2: Collaboration modes: individual sandboxes, indi-
vidual views on shared data and role-based collaboration.
same user interface but the state of sandboxes may
differ depending on their activities. This collabora-
tion mode is useful mainly for individual training and
cyber security experiments.
Individual views on shared data – the participants,
each of them sitting at his or her own computer, share
a sandbox and the measured data are shared. Partici-
pants have the same web UI at their disposal but they
use them independently. They can focus on differ-
ent parts of the network, explore different aspects of
the security scenario, return back in time and so on,
but they never affect the views of other participants.
This collaboration mode is useful mainly for collec-
tive learning about security threats or for collaborative
forensic analyses.
Role-based collaboration – in this mixed ap-
proach, participants are divided into teams with pre-
scribed roles, such as attackers or defenders. Teams
have predefined web user interfaces according to their
tasks. Teams can share a sandbox which plays the
role of a battlefield. This collaboration mode is use-
ful for exercises where multiple teams either coop-
erate or compete against each other in a single shared
sandbox. However, this role-based approach extended
with multiple sandboxes enables us to go even further.
For example, we can create multiple defending teams,
each having its own isolated sandbox, and a single at-
tacking team fighting against them simultaneously.
4.3 Web Front-end and Visualization
The web portal technology used for the implementa-
tion of the PM Portal enables us to develop special-
ized interactive user interfaces, which are narrowly
focused on specific goals, but also allow us to com-
bine them easily into complex systems of mutually
synchronized views supporting complex workflows.
There is no space to describe all the developed user
interfaces and interactive visualizations in detail, nor
to discuss their combinations leading to the support of
various security scenarios. Instead, we present only a
few selected portlets that were used most often during
various cyber exercises organized by the KYPO team
so far.
4.3.1 Capture the Flag Games
The PM Portal offers complete support for design-
ing and playing level-based games where users com-
plete cyber security tasks. The administrators’ inter-
face enables the game designer to define the network
topology, individual tasks, hints with penalties, time
limits and other necessary information. There is also
support for sandbox allocation and player enrollment.
The players’ interface guides them through the game
and is usually supplemented with an interactive net-
work topology view.
4.3.2 Network Topology
One key visualization of the PM Portal is a general
topological view, as shown in Figure 3. Versatility
was one of the key requirements for this visualization
since the network topology is present in all scenarios.
Routers, links, computers and servers are represented
in the visualization.
Figure 3: A simple network topology with highlighted
roles, network traffic and incoming emails.
The topology visualization shows multiple dy-
namic data measured in the corresponding sandbox.
The small icons close to the nodes represent logical
roles, e. g., attacker or victim. Unusual traffic on links
is visualized with colors and animations. Nodes can
be accompanied by the visualization of user-defined
events such as incoming emails. Clicking on a node, a
user, if privileged, can access the node’s remote desk-
top via VNC or SPICE client. In this case, a new tab
is opened in the browser with the screen of the remote
host. This visualization is fully interactive, enabling
users to re-organize nodes, collapse, and reveal sub-
networks, zoom in and out, and so on.
4.3.3 Time Manager
Data measured in sandboxes and provided by the
monitoring management component have the form of
KYPO Cyber Range: Design and Use Cases
317

a time series. Therefore, many visualizations used
in the PM Portal have to cope with time-related data
queries in order to show the sandbox’s state either at
a particular point in time or within a given time span.
It would be impractical to deal with time constraints
in every particular portlet independently. Instead, we
developed a Time Manager portlet (Figure 4) which
enable users to visually define time restrictions that
are propagated to other portlets on the page.
Figure 4: A generic timeline management visualization.
4.3.4 Analytic Graphs
KYPO provides several analytically oriented visu-
alizations and interactions. For instance, measured
sandbox data can be transformed into 2D line charts
and radar charts or they can be visualized in 3D, as
shown in Figure 5. These analytic graphs provide
alternative views on multivariate data measured in
the sandbox. To help users to identify anomalies,
the visualizations are fully interactive, support the re-
ordering of axises simply by their direct manipulation
and can switch between two 3D views smoothly by
means of animation so that the user keeps track of the
investigated part of the graph and never loses context.
Figure 5: Interconnected analytic graphs.
4.4 Physical Facility
Although the KYPO cyber range is accessible re-
motely via a web browser, many exercises are orga-
nized in a physical KYPO laboratory. Its hardware
equipment offers a high variability of display tech-
niques as well as a reconfigurability of inputs and out-
puts so that it is possible to support variable collabo-
ration strategies and to distribute relevant information
across several teams and roles.
The room consists of a training area over which a
multimedia control center and a visitors’ gallery are
located, as shown in Figure 6.
Figure 6: The KYPO laboratory is a versatile room. Its
setting can be adjusted to best fit the needs of ongoing exer-
cises.
The training area is equipped with six mobile
audio-video tables, each for 3-4 learners. The ta-
bles integrate all-in-one touch computers providing
access to the KYPO infrastructure. The room is fur-
ther equipped with four mobile FullHD displays and
two UHD/4K displays. These displays can be ei-
ther connected to individual AV tables or used to dis-
play shared information. Nevertheless, the informa-
tion sharing is primarily managed by two wide central
display surfaces; a projection screen and display wall.
The projection screen is 5 meters wide and supports
FullHD 2D or 3D projection from up to 4 sources at
the same time, e. g., the supervisor’s screen and work-
ing spaces of 3 teams. The display wall consists of
a matrix of 5x3 Full HD displays and a multi-touch
frame supporting detection of up to 10 simultaneous
touches (i. e. true multi-touch).
The distribution of content into display outputs is
managed centrally by the coordinator sitting in the
control center. Some basic tasks can be also managed
directly by the supervisor, who has a table located to-
gether with the AV tables in the training area.
5 CYBER RANGE USE CASES
KYPO can be used for various different applications.
During its design and development, we focused on
these three main use cases: i) cyber research, devel-
opment, and testing, ii) digital forensic analysis, and
iii) cyber security education and training. All these
use cases have a similar set of requirements on the
cyber range, but they differ in scenario-specific tools,
the availability of pre-defined content, user interac-
tions and expected knowledge, skills, and effort level
ICSOFT 2017 - 12th International Conference on Software Technologies
318

of the users. However, the concept of sandboxes and
the platform management portal helps us to cope with
this fact, i. e. various types of sandboxes with various
types of tools can be provided, from an empty sand-
box for researchers to a fully populated and config-
ured sandbox for a complex cyber security exercise.
In the following text, we describe the differences of
the three use cases in a detail, and provide references
to research papers employing or benefiting from an
application of the KYPO cyber range.
5.1 Cyber Research and Development
The first use case presented here supports research,
development, and testing new methods or systems for
the detection and mitigation of cyber attacks in net-
work infrastructures of various types.
In this case, KYPO provides a sandbox and
optional monitoring infrastructure for experiments.
Users can provide their own virtual images for hosts
to be instantiated. Alternatively, they can start with
generic virtual hosts available in KYPO which run
common operating systems, services and applications
(e. g., Ubuntu Server, MS Windows Server 2013, De-
bian Server with configured DNS server) and install
applications used in the experiment.
Network traffic and host based statistics can be
monitored and stored within KYPO’s infrastructure,
where they are immediately available for analysis.
Experiments can be evaluated via analytic tools that
researchers deploy into the KYPO infrastructure and
utilize according to their interests. Researchers can
also utilize interactive visualizations of the PM Por-
tal. The network topology visualization (with an indi-
cation of network traffic and event-based activities to-
gether with 2D and 3D analytic graphs) is especially
valuable. The time manager helps to keep track of
real-time developments in the sandbox.
This use case is intended for security researchers
and experienced network administrators because it re-
quires an advanced level of knowledge in network-
ing, host configuration and some knowledge of virtu-
alization technologies. Researchers need to be experi-
enced in order to assemble or adjust their experiment-
specific web UIs, to define their own topologies and
other scenario properties, and to properly design mul-
tiple sandboxes for comparison studies. Regarding
the KYPO user roles, researchers play the role of sce-
narist, organizer and supervisor.
There are several public papers using KYPO
for cyber security research and development rang-
ing from a simulation of a DDoS attack (Jirsík et al.,
2014) through to an evaluation of a network defence
strategy (Medková et al., 2017) and an analysis of
surveillance software (Špa
ˇ
cek et al., 2017).
5.2 Digital Forensic Analysis
The second use case partially builds upon the previous
one and covers basic forensic analysis, which can be
partly automated by tools deployed in the sandbox.
In this use case, the users can deploy virtual images
of unknown or malicious machines in the predefined
sandbox network and run a set of automated dynamic
analyses. The sandbox contains an analytic host that
provides pre-configured tools and an environment for
rudimentary forensic analysis.
This use case supports security incident handlers
and forensic analysts in focusing on the subject mat-
ter and removes the burden of spending their precious
time in the setup of an analytic environment. Since
the digital forensic analysis extends the previous use
case, the required KYPO user roles are also similar.
5.3 Education and Training
The last use case covers a diverse type of edu-
cational hands-on activities, such as security chal-
lenges, competitions, capture the flag games, and at-
tack/defence cyber exercises; all of which closely fol-
low the learning-by-doing principle.
In our experience, the education and training use
case has proven to be the most challenging. On one
hand, the KYPO platform needs to provide many ad-
ditional features, mainly in the terms of user interac-
tions, in order to support both the learners and edu-
cators in their roles. On the other hand, there is a
considerable amount of customized content that must
be created in order to fit a particular educational ac-
tivity, whilst remaining reusable (e. g., virtual hosts,
exercise data stored at hosts).
Some activities, e. g., capture the flag games, are
designed to be held without much direct input from
the teacher. Instead, the assignments for the learn-
ers are implanted into the platform where the game
is deployed, including additional instructions and an
evaluation of the submitted solutions. The learners
typically choose individual tasks or follow the prede-
fined path of the game. Once they find a solution, they
submit the requested data to the game platform which
immediately provides a response whether the solution
is correct or not. If it is, they can proceed further.
In the other cases, it is desirable for the educators
to be able to control the flow of the hands-on activ-
ity based on automatically acquired status informa-
tion about the simulated infrastructure in the sandbox
and also manually trigger tasks for learners, and eval-
uate their actions and reports.
KYPO Cyber Range: Design and Use Cases
319

Whatever the case, it is desirable to put mini-
mal requirements on the learners’ knowledge of the
KYPO infrastructure, virtualization technologies and
other advanced concepts. As a result, the learners can
focus only on the subject of the exercise or training,
such as a penetration testing tutorial or a cyber secu-
rity game.
With regard to KYPO’s user roles, learners fol-
low the scenario roles assigned to them, and interact
with predefined web user interfaces. Instructors have
supervisor privileges to keep track on learners’ activi-
ties and to be able to interfere in their activities if nec-
essary. In contrast, substantial preparation effort and
technical skills are required from scenarists and or-
ganizers who create the content of exercises, allocate
resources and manage the preparation and execution
phase.
This use case motivates further research in active
learning of cyber security. We evaluated the bene-
fits of design enhancements in generic capture the flag
game scheme provided by KYPO platform (Vykopal
and Barták, 2016). Next, we introduced methods of
distributing learners into teams with respect to their
proficiency and the prerequisite skills required by a
cyber exercise (Vykopal and Cegan, 2017).
6 CONCLUSION
Today, KYPO is the largest academic cyber range
in the Czech Republic. The platform is fully cloud-
based and supports multiple use cases (research, edu-
cation and training). We organize national cyber exer-
cises and training sessions to validate proposed cyber
range components and to continually improve them.
We also use KYPO for hands-on security courses to
give students realistic experience in cyber security.
Our current work focuses on research into tools
for more realistic, economical, and time efficient sim-
ulations of real cyber entities. We develop tools to
further automate the preparation and execution of cy-
ber experiments. We connect KYPO to other facilities
(e. g., ICS and LTE networks) to create a more real-
istic cyber-physical environment. We aim to execute
current and sophisticated cyber attacks in the KYPO
infrastructure to provide a research environment for
simulation, detection, and mitigation of cyber threats
against critical infrastructure.
In addition to the technology based contributions,
we would like to contribute to transdisciplinary learn-
ing in cyber security to cope with the ever-evolving
threat landscape. To make a desirable improvement
in the skills of the learners, technical skills must be
complemented by communication, strategy and other
skills for effective attack detection and response.
ACKNOWLEDGEMENTS
This research was supported by the Security Research
Programme of the Czech Republic 2015-2020 (BV
III/1 – VS) granted by the Ministry of the Interior
of the Czech Republic under No. VI20162019014 –
Simulation, detection, and mitigation of cyber threats
endangering critical infrastructure.
Access to the CERIT-SC computing and stor-
age facilities provided by the CERIT-SC Center,
provided under the programme “Projects of Large
Research, Development, and Innovations Infrastruc-
tures” (CERIT Scientific Cloud LM2015085), is
greatly appreciated.
REFERENCES
Avatao (Last accessed on Mar 22, 2017).
https://avatao.com/.
Benzel, T. (2011). The Science of Cyber Security Experi-
mentation: The DETER Project. In Proceedings of the
27th Annual Computer Security Applications Confer-
ence, pages 137–148. ACM.
Buttyán, L., Félegyházi, M., and Pék, G. (2016). Mentoring
talent in IT security–A case study. In 2016 USENIX
Workshop on Advances in Security Education (ASE
16).
Childers, N., Boe, B., Cavallaro, L., Cavedon, L., Cova,
M., Egele, M., and Vigna, G. (2010). Organizing
large scale hacking competitions. In Detection of In-
trusions and Malware, and Vulnerability Assessment,
pages 132–152. Springer.
CTF365 (Last accessed on Mar 22, 2017). Capture The Flag
365. https://ctf365.com/.
Cyber Virtual Ad hoc Network (Last
accessed on Mar 22, 2017).
http://www.appcomsci.com/research/tools/cybervan.
Davis, J. and Magrath, S. (2013). A survey of cyber ranges
and testbeds. Technical report, DTIC Document.
EDURange (Last accessed on Mar 22, 2017).
http://www.edurange.org/.
Eichler, Z., Ošlejšek, R., and Toth, D. (2015). KYPO: A Tool
for Collaborative Study of Cyberattacks in Safe Cloud
Environment, pages 190–199. Springer International
Publishing, Cham.
Emulab (Last accessed on Mar 22,
2017). A list of Emulab Testbeds.
http://wiki.emulab.net/Emulab/wiki/OtherEmulabs.
Faber, T. and Wroclawski, J. (2009). A federated experi-
ment environment for Emulab-based testbeds. In TRI-
DENTCOM, pages 1–10.
ICSOFT 2017 - 12th International Conference on Software Technologies
320

Ferguson, B., Tall, A., and Olsen, D. (2014). National cyber
range overview. In 2014 IEEE Military Communica-
tions Conference, pages 123–128.
Jirsík, T., Husák, M.,
ˇ
Celeda, P., and Eichler, Z. (2014).
Cloud-based security research testbed: A DDoS use
case. In 2014 IEEE Network Operations and Man-
agement Symposium (NOMS).
KYPO (Last accessed on May 16, 2017). https://kypo.cz/.
Lee Rossey (2015). SimSpace Cyber Range. ACSAC 2015
Panel: Cyber Experimentation of the Future (CEF):
Catalyzing a New Generation of Experimental Cyber-
security Research.
Linux Foundation (Last accessed on Mar 22, 2017). Open
vSwitch. http://openvswitch.org/.
MCR (Last accessed on Mar 22, 2017). The Michigan Cy-
ber Range. https://www.merit.edu/cyberrange/.
Medková, J., Husák, M., Vizváry, M., and
ˇ
Celeda, P.
(2017). Honeypot Testbed for Network Defence Strat-
egy Evaluation. In Proceedings of the 2017 IFIP/IEEE
International Symposium on Integrated Network Man-
agement, pages 887–888. IEEE Computer Society.
Mirkovic, J., Benzel, T. V., Faber, T., Braden, R., Wro-
clawski, J. T., and Schwab, S. (2010). The DETER
Project. In 2010 IEEE International Conference on
Technologies for Homeland Security (HST ’10).
NATO CCDCOE (Last accessed on May 16, 2017).
Locked Shields. http://ccdcoe.org/event/cyber-
defence-exercises.html.
NCR (Last accessed on Mar 22, 2017). The Na-
tional Cyber Range. http://www.acq.osd.mil/dte-
trmc/docs/Docs/NCR/2015_NCR
Špa
ˇ
cek, S.,
ˇ
Celeda, P., Drašar, M., and Vizváry, M. (2017).
Analyzing an Off-the-Shelf Surveillance Software:
Hacking Team Case Study. Security and Protection
of Information, (IX).
Raj, A. S., Alangot, B., Prabhu, S., and Achuthan, K.
(2016). Scalable and Lightweight CTF Infrastruc-
tures Using Application Containers. In 2016 USENIX
Workshop on Advances in Security Education (ASE
16), Austin, TX. USENIX Association.
Schwab, S., Wilson, B., Ko, C., and Hussain, A. (2007).
SEER: A security experimentation environment for
DETER. In Proceedings of the DETER Commu-
nity Workshop on Cyber Security Experimentation and
Test on DETER Community Workshop on Cyber Secu-
rity Experimentation and Test 2007. USENIX Associ-
ation.
Security Competence (Last accessed on Mar 22,
2017). Hacking-Lab. http://www.hacking-lab-
ctf.com/technical.html.
Siaterlis, C., Garcia, A. P., and Genge, B. (2013). On the
Use of Emulab Testbeds for Scientifically Rigorous
Experiments. IEEE Communications Surveys Tutori-
als, 15(2):929–942.
Tovar
ˇ
nák, D. and Pitner, T. (2014). Continuous queries
over distributed streams of heterogeneous monitor-
ing data in cloud datacenters. In 2014 9th Interna-
tional Conference on Software Engineering and Ap-
plications (ICSOFT-EA), pages 470–481.
Vigna, G., Borgolte, K., Corbetta, J., Doupe, A., Fratanto-
nio, Y., Invernizzi, L., Kirat, D., and Shoshitaishvili,
Y. (2014). Ten Years of iCTF: The Good, The Bad,
and The Ugly. In 2014 USENIX Summit on Gam-
ing, Games, and Gamification in Security Education
(3GSE 14).
Vykopal, J. and Barták, M. (2016). On the Design of Secu-
rity Games: From Frustrating to Engaging Learning.
In 2016 USENIX Workshop on Advances in Security
Education (ASE 16), Austin, TX. USENIX Associa-
tion.
Vykopal, J. and Cegan, J. (2017). Finding Exercise Equi-
librium: How to Support the Game Balance at the
Very Beginning? In Proceedings of the 2017 ACM
SIGCSE Technical Symposium on Computer Science
Education, SIGCSE ’17, pages 719–719, New York,
NY, USA. ACM.
Welch, D., Ragsdale, D., and Schepens, W. (2002). Training
for information assurance. Computer, 35(4):30–37.
White, B., Lepreau, J., Stoller, L., Ricci, R., Guruprasad, S.,
Newbold, M., Hibler, M., Barb, C., and Joglekar, A.
(2002). An Integrated Experimental Environment for
Distributed Systems and Networks. pages 255–270,
Boston, MA.
Wroclawski, J., Mirkovic, J., Faber, T., and Schwab, S.
(2008). A two-constraint approach to risky cybersecu-
rity experiment management. In Sarnoff Symposium.
Invited paper.
KYPO Cyber Range: Design and Use Cases
321
