
A Probabilistic Baby-step Giant-step Algorithm
Prabhat Kushwaha and Ayan Mahalanobis
∗
IISER Pune, Dr. Homi Bhabha Road, Pashan, Pune 411008, India
Keywords:
Discrete Logarithm Problem, Baby-step Giant-step Algorithm, NIST Curves Over Prime Fields, Parallelized
Collision Search.
Abstract:
In this paper, a new algorithm to solve the discrete logarithm problem is presented which is similar to the usual
baby-step giant-step algorithm. Our algorithm exploits the order of the discrete logarithm in the multiplicative
group of a finite field. Using randomization with parallelized collision search, our algorithm indicates some
weakness in NIST curves over prime fields which are considered to be the most conservative and safest curves
among all NIST curves.
1 INTRODUCTION
It is well-known that computationally hard number
theoretic problems are used as primitives in public-
key cryptography. On that basis, public-key cryptog-
raphy can be divided into two categories. One uses
the hardness of factorizing large integer as the build-
ing blocks to construct public-key protocols and the
other is based on the computational difficulty of solv-
ing the discrete logarithm problem. In this paper, we
are interested in the latter.
Let G be a cyclic group of prime order p and gen-
erated by P which is written additive. Given an el-
ement Q = xP ∈ G, the discrete logarithm problem
(DLP) in G is to compute the integer x. This integer
x is called the discrete logarithm of Q with the base
P. There are generic algorithms such as the baby-step
giant-step algorithm (Hoffstein et al., 2008) which
solves DLP in any group G.
In this paper, we develop and study a different ver-
sion of the baby-step giant-step algorithm. The nov-
elty of our approach comes from the implicit repre-
sentation using F
×
p
as auxiliary group. Our approach
leads to a way to reduce the discrete logarithm prob-
lem to a problem in F
×
p
. The advantage of this ap-
proach is, F
×
p
has many subgroups and one can ex-
ploit the rich and well understood subgroup structure
of F
×
p
. The use of F
×
p
as an auxiliary group was stud-
ied earlier, see (Cheon, 2006; Brown and Gallant,
2004). However we use it in a different context.
In Theorem 1 we develop an algorithm that solves
∗
This research was supported by a SERB and NBHM
grants.
the discrete logarithm problem using implicit repre-
sentation. Two things come out of this theorem:
A If the secret key x belongs to some small subgroup
of F
×
p
, there can be an efficient attack on the DLP.
B If somehow it is known to an attacker that the se-
cret key is in some subgroup H of F
×
p
, that infor-
mation can be used to develop a better attack.
The question remains, what happens if no infor-
mation about the secret x is known. We develop a
probabilistic algorithm (Theorem 2) to expand our at-
tack. To understand this probabilistic attack properly,
we study it on the curve P-256. This is an NIST rec-
ommended curve over a prime field and is considered
secure. Our study, which we present in details in Sec-
tion 3 indicates some weakness in this curve.
2 MAIN WORK
Let G be a cyclic group of prime order p and gen-
erated by P which is written additive. For y ∈ F
p
,
yP ∈ G is called the implicit representation of y ∈
F
p
(with respect to G and P). The following lemma
comes from the idea of implicit representation of a fi-
nite field, proposed by Maurer and Wolf (Maurer and
Wolf, 1999).
Lemma 1. Let a, b be any two integers. Then a = b
(mod p) if and only if aP = bP in G.
Proof. Assume that a = b (mod p), then a = t p + b
for some integer t. Then aP = t pP + bP = bP. Con-
versely, assume that aP = bP, then (a −b)P = 0 in
Kushwaha, P. and Mahalanobis, A.
A Probabilistic Baby-step Giant-step Algorithm.
In Proceedings of the 14th International Joint Conference on e-Business and Telecommunications (ICETE 2017) - Volume 4: SECRYPT, pages 401-406
ISBN: 978-989-758-259-2
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
401

G and this means p|(a −b) which implies that a = b
(mod p).
The usefulness of this lemma is to be able to de-
cide on the equality in F
×
p
by looking at the equality in
G. The following algorithm to solve the discrete loga-
rithm problem uses the order of the discrete logarithm
in the multiplicative group of a finite field. This algo-
rithm is also deterministic but this is different from the
baby-step giant-step (Hoffstein et al., 2008) as it uses
the implicit representation with multiplicative group
of a finite field as auxiliary group.
Theorem 1. Let G be an additive cyclic group gen-
erated by P and order of P is a prime p. Let Q = xP
be another given element of G(x is unknown). For a
given divisor d of p −1, let H be the unique subgroup
of F
×
p
of order d. Then, one can decide whether or
not x belongs to H in O(
√
d) steps. Furthermore, if
x belongs to H, the same algorithm will also find the
discrete logarithm x in O(
√
d) steps where each step
is an exponentiation in the group G.
Proof. Since H is a subgroup of the cyclic group F
×
p
,
we assume that it is generated by some element ζ. If
the generator of H is not given to us, we can com-
pute it using a generator of F
×
and d. The proof
of whether x belongs to H or not follows from the
well-known baby-step giant-step algorithm (Hoff-
stein et al., 2008, Proposition 2.22) to compute the
discrete logarithm.
Let n be the smallest integer greater than
√
d.
Then x ∈H if and only if there exists an integer k with
0 ≤k ≤d such that x = ζ
k
(mod p). Note that any in-
teger k between 0 and d can be written as k = an −b
for unique integers a, b with 0 ≤ a,b ≤ n, by division
algorithm. Therefore, x ∈ H if and only if there exist
two integers a,b with 0 ≤ a, b ≤n such that x = ζ
an−b
(mod p), or equivalently ζ
b
x = ζ
n
a
(mod p). Using
the lemma above, we see that x ∈ H if and only if
there exist two integers a,b with 0 ≤a,b ≤n such that
ζ
b
xP = ζ
n
a
P, equivalently ζ
b
Q = (ζ
n
)
a
P as Q = xP.
Now, we create a list
ζ
b
Q : 0 ≤b ≤n
. Then
we generate elements of the form (ζ
n
)
a
P for each in-
teger a in [0,n] and try to find a collision with the ear-
lier list. When there is a collision, i.e., ζ
b
Q = (ζ
n
)
a
P
for some 0 ≤a, b ≤n, it means that x ∈H. Otherwise,
x /∈ H.
Moreover, if x ∈ H then ζ
b
Q = (ζ
n
)
a
P for some
0 ≤a, b ≤n. So, we use the integers a and b to com-
pute ζ
an−b
(mod p) which is nothing but the discrete
logarithm x. Since the two lists require computation
of at most 2n exponentiations, the worst case time
complexity of the algorithm to check whether or not
x ∈ H, as well as to compute x(if x ∈ H) would be
O(n) ≈ O(
√
d) steps. This completes the proof.
2.1 Comparing Our Work with Usual
Baby-step Giant-step Algorithm
The similarity between Theorem 1 and usual baby-
step giant-step is that both use division algorithm.
However, the main difference between the two lies in
its actual application: division algorithm is applied on
the discrete logarithm x in the usual baby-step giant-
step whereas the division algorithm is used on the
exponent k(of the discrete logarithm x) in Theorem
1. Irrespective of the above difference, Theorem 1
works as a generic deterministic attack on DLP(just
like baby-step giant-step) in the sense that such a sub-
group H always exists. For example, one can always
take H = F
×
p
as the worst-case scenario in Theorem
1, and then the(worst-case) complexity of Theorem 1
is O(
√
p −1) = O(
√
p), same as the usual baby-step
giant-step algorithm.
2.2 Practical Implications of the
Deterministic Attack of Theorem 1
The main practical advantage of the attack presented
in Theorem 1 is that the cost of our attack can be
far less than O(
√
p) if it is known to an attacker that
the discrete logarithm x lies in some proper, relatively
smaller subgroup H of F
×
p
. For example, if x lies in H
with |H| ≈
√
p, then the attack in Theorem 1 solves
the DLP in O(
4
√
p) which is a lot faster than the best-
known generic attacks on DLP.
There is another security issue that above theo-
rem brings to the fore. We take the example of NIST
curves defined over prime fields of different size viz.
P-192, P-224, 256, P-384, P-521 and p denotes the
respective prime order of the curves. Since the above
algorithm depends on d and p −1 factors into small
divisors, the above theorem is applicable to each of
the five NIST curves(NIST, 2000). Although, one can
say that probability of randomly chosen secret x being
inside a particular subgroup of F
×
p
can be very small,
the availability of so many divisors d of p −1 of dif-
ferent sizes itself is not a desirable security feature
from the cryptographic point of view and it is always
a sound security practice to exclude any such proba-
bility, however small. Therefore, as a security neces-
sity, it is highly recommended that p −1 should be
of the form k · p
0
for a very small value of k and some
prime p
0
so that above algorithm does not provide any
faster attack on DLP than the generic attacks.
Remark 1. Even though the above algorithm is
generic in nature, it does have a practical signifi-
cance. Our algorithm applies on all the five prime
order NIST curves (NIST, 2000) viz. P-192, P-224,
SECRYPT 2017 - 14th International Conference on Security and Cryptography
402

P-256, P-384, P-521. Although the probability of a
randomly chosen secret key x being inside a partic-
ular subgroup of F
×
p
can be very small, however, it
is advisable to check, using our algorithm for each
curve, if the secret key x belongs to any of two (large
enough)subgroups whose orders are mentioned in the
appendix A. If it does, we discard the secret key.
2.3 A Probabilistic Version of Baby-step
Giant-step
Suppose that p −1 has large enough(but a lot smaller
than p −1) divisor d and H is the unique subgroup
of F
×
p
of order d. A drawback of the deterministic
algorithm given in Theorem 1 is that it might fail to
solve DLP because the probability of x belonging to
H is very small. One way to increase the probability is
to increase the size of d, if such d exists. Clearly, this
is not a desirable solution because the computational
cost depends on the size of the subgroup.
The above algorithm can be parallelized which
helps us overcome this obstacle by increasing the
probability. We have randomized the above algorithm
where the random inputs will be running on paral-
lel processes or threads. This parallelization along
with collision algorithm (based on birthday para-
dox) (Hoffstein et al., 2008, Theorem 5.38) yields a
randomized probabilistic algorithm which can solve
DLP with a given probability.
Collision Theorem: An urn contains N balls, of
which n balls are red and N −n are blue. One ran-
domly selects a ball from the urn, replaces it in the
urn, randomly selects a second ball, replaces it, and
so on. He does this until he has looked at a total num-
ber of m balls. Then, the probability that he selects at
least one red ball is
Pr(at least one red ball) = 1−
1 −
n
N
m
≥1−e
−mn
N
.
Theorem 2. Let G be an additive cyclic group gener-
ated by P and the order of P is a prime p. Let Q = xP
be another given element of G(x is unknown). For a
given divisor d of p −1, let H be the unique subgroup
of F
×
p
of order d. Then, x can be computed in O(
√
d)
steps with probability at least 1 −e
−dm
p−1
if one has
access to m parallel threads.
Proof. The main idea is to run the algorithm in The-
orem 1 on each of m threads as follows. We ran-
domly selects m elements y
1
,y
2
,..,y
m
in F
×
p
and
compute corresponding m elements Q
1
= y
1
Q =
(y
1
x)P,...,Q
m
= y
m
Q = (y
m
x)P of G. Now, we run
the above algorithm on each of m parallel threads,
with element Q
i
= (y
i
x)P running on i
th
thread. Let
z
i
= y
i
x (mod p) for i = 1, ..,m. If z
i
∈ H for some i,
1 ≤ i ≤ m; then the algorithm on that thread returns
z
i
. Once we have z
i
for some i, we compute z
i
·y
i
−1
(mod p) which is nothing but the discrete logarithm
x.
The collision theorem above tells us about the
probability of at least one z
i
belonging to H for 1 ≤
i ≤ m. In present case, F
×
p
with p −1 elements is
the urn, so N = p −1. The elements of H are red
balls, so n = d. Since we are randomly selecting m
elements y
1
,..,y
m
from F
×
p
, it implies that z
1
,z
2
,..,z
m
also are random elements of F
×
p
. Therefore, proba-
bility that at least one of z
i
would belong to H is at
least 1 −e
−dm
p−1
, by the collision theorem. In other
words, with probability at least 1 −e
−
dm
p−1
, one can
compute z
i
for some i, 1 ≤ i ≤ m if one has access to
m threads. Since the number of steps performed on
each thread before z
i
is computed for some i is at max
2
√
d, we conclude that it takes O(
√
d) steps to com-
pute x with the probability at least 1 −e
−dm
p−1
if m
threads are available. This completes the proof.
Remark 2. It follows from Theorem 2 that if there ex-
ist divisors d of p −1 of suitable sizes, then DLP can
be solved in time much less than the square root of the
group size but with a probability which increases with
the number of threads used. A practical importance of
Theorem 2 lies in the fact that such divisors of p −1
do exist for all NIST curves (NIST, 2000) as well as
most of SEC2 curves (SEC 2(Version 2), 2010). This
gives us precise estimates about the number of group
operations and threads needed to solve DLP with a
given probability. We illustrate this by an example in
the next section.
Remark 3. Note that the probability of solving the
DLP in above theorem is proportional to the product
m ·d. It follows that if we fix a probability, this prod-
uct is constant. Therefore, for a fixed probability of
solving the DLP, there is a trade-off between the num-
ber of steps and number of threads needed in Theorem
2. Increasing one of the two would decrease the other
and vice-a-versa.
3 SECURITY ANALYSIS OF NIST
CURVE P-256
As discussed earlier, our probabilistic algorithm is
applicable to NIST curves. In this section, we will
demonstrate the implication of our algorithm on
NIST curves. We will do that only on the NIST curve
P-256 but similar conclusions hold for other four
A Probabilistic Baby-step Giant-step Algorithm
403
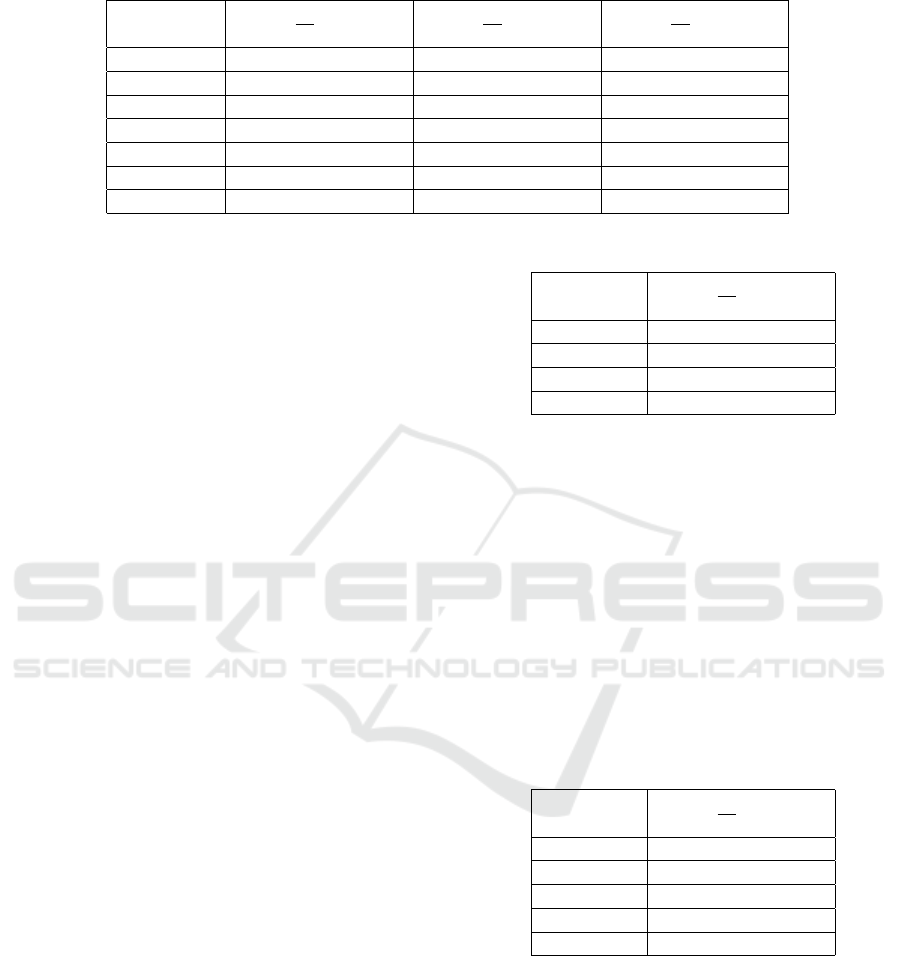
Table 1: Trade-off between d and m for equal probability for curve P-256.
log
2
d
1
= 201.73 log
2
d
2
= 202.73 log
2
d
3
= 203.32
log
2
(
√
d
1
) = 101.86 log
2
(
√
d
2
) = 101.36 log
2
(
√
d
3
) = 101.66
log
2
m = 45 0.00162 0.00324 0.00486
log
2
m = 50 0.05064 0.098711 0.14435
log
2
m = 52 0.18768 0.34013 0.46398
log
2
m = 53 0.34013 0.56458 0.71268
log
2
m = 54 0.56458 0.81040 0.91745
log
2
m = 55 0.81040 0.96405 0.993184
log
2
m = 56 0.96405 0.99871 0.99995
NIST curves over prime field as well, see appendix.
The NIST curve P-256 is defined over the prime field
F
q
and the order of P-256 is a prime p given below.
q = 11579208921035624876269744694940757353
0086143415290314195533631308867097853951
p = 11579208921035624876269744694940757352
9996955224135760342422259061068512044369
p −1 = 2
4
·3 ·71 ·131 ·373 ·3407 ·17449 ·38189·
187019741 ·622491383 ·1002328039319·
2624747550333869278416773953
Since p − 1 factors into many relatively small
integers, we have the following divisors of p −1 of
various sizes.
d
1
= 5344274495032941459639941436409709731
020474123788264129719829 ≈ 2
201.73
.
d
2
= 1068854899006588291927988287281941946
2040948247576528259439658 ≈ 2
202.73
.
d
3
= 1603282348509882437891982430922912919
3061422371364792389159487 ≈ 2
203.32
.
d
4
= 1820794320457723155299328047384788105
3586755339746615889955457403 ≈ 2
213.47
.
d
5
= 2385240559799617333442119742074072418
019864949506806681584164919793 ≈ 2
220.50
.
For above sizes of subgroups and various num-
ber of threads m, the following tables give the prob-
ability to solve DLP. The second column of the Ta-
ble 1 shows the probabilities when the subgroup size
is d
1
≈ 2
201.73
bits. For example, if we have m =
2
54
parallel threads, then our algorithm would solve
DLP in 2
101.86
steps with probability 0.56458 which
is the intersection of the fifth row(corresponding to
m = 2
54
) and the second column(corresponding to
d
1
≈ 2
201.73
). Other entries(probabilities) of the ta-
bles can be understood similarly.
Table 2: Probability for larger d for P-256
log
2
d
4
= 213.47
log
2
(
√
d
4
) = 106.78
log
2
m = 41 0.29234
log
2
m = 42 0.49921
log
2
m = 43 0.74921
log
2
m = 44 0.93710
If we go across a row in the tables, we see the
probabilities getting increased with the size of sub-
group d. If we move along a column, probabilities
increase with the number (m) of parallel threads. Ta-
ble 1 also exhibits the trade-off between d and m for
equal probability. For equal probability, highlighted
diagonally in the second and third column, we see that
increasing the subgroup size by 1-bit(d
1
and d
2
differ
by 1-bit) results in a decrease of 1-bit in the number
of parallel threads m. As an example, to achieve the
probability 0.56458, the subgroup of order d
1
requires
2
54
parallel threads while the subgroup of order d
2
re-
quires 2
53
.
Table 3: Probability for much larger d for P-256
log
2
d
5
= 220.50
log
2
(
√
d
5
) = 110.25
log
2
m = 33 0.16218
log
2
m = 34 0.29805
log
2
m = 35 0.50727
log
2
m = 36 0.75721
log
2
m = 37 0.94106
From Table 3, we can see that DLP on the curve
P-256 can be solved in 2
110.25
(with a significant re-
duction from 2
128
) steps with probability greater than
0.5, while using 2
35
parallel threads. This indicates
a weakness of NIST curve P-256 if one assumes that
2
35
parallel threads are within the reach of modern
distributed computing. Similar conclusions can be
drawn for other NIST curves P-192, P-224, P-384 and
P-521 see appendix.
Moreover, one observes that for most of the curves
in SEC2(Version 2) (SEC 2(Version 2), 2010) which
SECRYPT 2017 - 14th International Conference on Security and Cryptography
404

also include all other ten NIST curves (NIST, 2000)
over binary field, p −1 factors into small divisors.
Therefore, our algorithm for solving DLP on those
curves in SEC2 (SEC 2(Version 2), 2010) can simi-
larly be studied.
4 CONCLUSION
In this paper we presented a novel idea of using the
implicit representation with F
×
p
as an auxiliary group
to solve the discrete logarithm problem in a group G
of prime order p. We modified the most common
generic algorithm, the baby-step giant-step algorithm
to give another deterministic attack on DLP. The prac-
tical significance of our deterministic attack is that it
can be a lot faster than baby-step giant-step in cer-
tain cases. The choice of parameter selection is also
suggested to prevent our faster deterministic attack.
Moreover, we have also presented a probabilistic ver-
sion of baby-step giant-step algorithm and studied it
further for NIST curves over prime fields. This al-
gorithm that we developed brings to the spotlight the
structure of the auxiliary group for the security of the
discrete logarithm problem in G. This aspect is prob-
ably reported for the first time.
REFERENCES
Brown, D. and Gallant, R. (2004). The static Diffie-Hellman
problem. IACR Cryptology ePrint Archive, 2004:306.
Cheon, J. (2006). Security analysis of the strong diffie-
hellman problem. In Eurocrypt 2006, pages 1–11.
Springer.
Galbraith, S. D. and Gebregiyorgis, S. W. (2014). Summa-
tion polynomial algorithms for elliptic curves in char-
acteristic two. In International Conference in Cryp-
tology in India, pages 409–427. Springer.
Gallant, R., Lambert, R., and Vanstone, S. (2000). Improv-
ing the parallelized pollard lambda search on anoma-
lous binary curves. Mathematics of Computation,
69(232):1699–1705.
Hoffstein, J., Pipher, J., Silverman, J. H., and Silverman,
J. H. (2008). An Introduction to Mathematical Cryp-
tography. Springer.
Koblitz, N. and Menezes, A. (2015). A riddle wrapped in an
enigma. IACR Cryptology ePrint Archive, 2015:1018.
Maurer, U. and Wolf, S. (1999). The relationship between
breaking the Diffie–Hellman protocol and computing
discrete logarithms. SIAM Journal on Computing,
28(5):1689–1721.
NIST, F. (2000). 186.2 Digital Signature Standard
(DSS). National Institute of Standards and Technol-
ogy (NIST).
SEC 2(Version 2), S. (2010). : Recommended Elliptic
Curve Domain Parameters. See http://www. secg.org/.
Semaev, I. (2004). Summation polynomials and the discrete
logarithm problem on elliptic curves. IACR Cryptol-
ogy ePrint Archive, 2004:31.
Wiener, M. J. and Zuccherato, R. J. (1998). Faster at-
tacks on elliptic curve cryptosystems. In International
Workshop on Selected Areas in Cryptography, pages
190–200. Springer.
APPENDIX
NIST Curves Over Prime Field
For each of these five NIST curves of order prime p,
two subgroups of F
×
p
with (large enough)orders d
1
, d
2
are given such that d
1
·d
2
= p−1 and gcd(d
1
,d
2
) = 1,
see Remark 1.
P-192
p = 62771017353866807638357894231760590137
67194773182842284081
p −1 = 2
4
·5 ·2389 ·9564682313913860059195669·
3433859179316188682119986911
d
1
= 656279166350909980926771898430320
≈ 2
109.02
d
2
= 9564682313913860059195669 ≈ 2
82.98
P-224
p = 26959946667150639794667015087019625940
457807714424391721682722368061
p −1 = 2
2
·3
6
·5 ·2153 ·5052060625887581870747
0860153287666700917696099933389351507
d
1
= 50520606258875818707470860153287666700
917696099933389351507 ≈ 2
195.01
d
2
= 533642580 ≈ 2
28.99
P-256
p = 11579208921035624876269744694940757352
9996955224135760342422259061068512044369
p −1 = 2
4
·3 ·71 ·131 ·373 ·3407 ·17449 ·38189·
187019741 ·622491383 ·1002328039319·
2624747550333869278416773953
d
1
= 1489153224408067225170753316415649
493584 ≈ 2
130.13
d
2
= 7775700130279284477677638911958252
0177 ≈ 2
125.87
P-384
p = 3940200619639447921227904010014361
3805079739270465446667946905279627659
A Probabilistic Baby-step Giant-step Algorithm
405

3991132635693989563081522949135544336
53942643
p −1 = 2 ·3
2
·7
2
·13·
1124679999981664229965379347·
3055465788140352002733946906144561090
6412496061604078843653919797049292684
80326390471
d
1
= 116779902422724253544491450752845
1248843085599474507893404452814643223
9664131807464380162 ≈ 2
292.55
d
2
= 1124679999981664229965379347
≈ 2
89.86
P-521
p = 686479766013060971498190079908139
321726943530014330540939446345918554
318339765539424505774633321719753296
39963713633211138647686124403803403
72808892707005449
p −1 = 2
3
·7 ·11 ·1283 ·1458105463
·1647781915921980690468599·
361519479488193001021694255910384759
305026570317329238370137171235087892
682166124375593383542689605841850975
9880171943
d
1
= 4166083869350854498586791068944823
62094293135755259682030509895497369427
12923152533496543294196006831576365431
08630210814256821981752 ≈ 2
440.55
d
2
= 1647781915921980690468599 ≈ 2
80.45
SECRYPT 2017 - 14th International Conference on Security and Cryptography
406
