
Distributed Clone Detection in Mobile Sensor Networks
Abu Sayed Chowdhury
1
and Akshaye Dhawan
2
1
School of Electrical Engineering and Computer Science, Washington State University,
P.O. Box 642752, Pullman, WA, U.S.A.
2
Ursinus College, Department of Mathematics and Computer Science, 601 E. Main Street, Collegeville, PA, U.S.A.
Keywords:
Security, Mobile Wireless Sensor Networks, Clone Attacks, Distributed Detection Protocol.
Abstract:
In this paper we present a clone detection technique for mobile wireless sensor networks. Since sensor nodes
can be compromised and cloned by an adversary, it is desirable to have a distributed clone detection algorithm
wherein the nodes in the network themselves identify cloned nodes. Most approaches in the literature have
a deterministic set of witness nodes that check for the presence of cloned nodes for a given ID based by
receiving claim messages that show two or more nodes with the same ID in different locations. We present
a new approach to distributed clone detection called Distributed Detection using Prefix Matching (DDPM).
Our approach is designed to work in a mobile sensor network and is based on using a random number and
a hash function of the claiming nodes ID to generate a key. We then match the prefix of this key to sensor
node IDs in the network to determine a set of inspector nodes that will detect clones for a given round. We
demonstrate a 7-10% improvement in the number of witness nodes as a measure of security while also reducing
the communication overhead.
1 INTRODUCTION
In recent years, mobile sensor networks are be-
ing utilized in several applications including surveil-
lance, habitat monitoring, object tracking, and en-
vironmental information gathering (Akyildiz et al.,
2002; Bonaci et al., 2010; Zhou et al., 2006). Since
sensor nodes are often deployed in remote and harsh
areas, the sensors are vulnerable to capture and com-
promise. Once captured both the data and the code on
a sensor node is potentially available to an adversary.
Attacks can be launched by cloning a captured sensor
node and using the cloned nodes to launch a variety
of insider attacks, injecting false data and conducting
incorrect aggregation. Such attacks have the potential
to severely impact the networks functioning.
Although clone attack detection in static networks
has been explored in the literature, limited work has
been done to tackle this security threat in a mobile
sensor network. It is not straightforward to apply the
clone detection techniques developed for static net-
works to a mobile environment. Some centralized
approaches have been introduced in the literature to
identify clones in mobile sensor networks; however,
they suffer from having a single point of failure and
excessive communication costs. Furthermore, cen-
tralized methods are not appropriate in mobile sensor
network when nodes are scattered in different regions
of the network (Yi et al., 2008). Hence, distributed de-
tection algorithms are crucial to detect cloned nodes
in a mobile network.
In this paper, we present a distributed clone de-
tection strategy called the Distributed Detection Pre-
fix Matching (DDPM) protocol. The key idea of this
technique is to implement a decentralized key based
verification protocol to identify clone nodes. We also
conduct a simulation study comparing DDPM to ex-
isting protocols for both communication overhead and
the level of security provided. We organize the re-
mainder of this paper as follows. We categorize and
illustrate related work in Section 2. Details of DDPM
protocol are described in Section 3. Simulation re-
sults and performance comparison of DDPM with
XED (Yu et al., 2013) are shown in Section 4. Fi-
nally, we conclude the paper and discuss future work
in Section 5.
2 RELATED WORK
In this section, we present a brief survey of the cur-
rent literature on clone detection. We classify clone
detection approaches into two categories. The first
Sayed Chowdhury A. and Dhawan A.
Distributed Clone Detection in Mobile Sensor Networks.
DOI: 10.5220/0006130701350141
In Proceedings of the 6th International Conference on Sensor Networks (SENSORNETS 2017), pages 135-141
ISBN: 421065/17
Copyright
c
2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reser ved
135

category includes centralized algorithms where a cen-
tral base station identifies a cloned node by receiv-
ing reports from the nodes of the sensor network.
The second category includes distributed algorithms
where information is processed by the nodes in the
network cooperatively in order to identify clones in a
distributed manner.
2.1 Centralized Detection
One of the first centralized algorithms for clone de-
tection in the literature was presented in (Eschenauer
and Gligor, 2002). In this paper the authors present a
detection scheme where every sensor node in the net-
work sends a list of its neighboring nodes to the base
station (BS). The BS considers two nodes as clone
nodes if it receives two lists that contain the same
node ID with inconsistent node positions. The ma-
jor drawbacks of this solution is that it suffers from a
single point of failure (the BS) and also has an exces-
sive communication overhead due to many messages
exchanged between nodes and the BS. Additionally,
the nodes closer to the base station are responsible to
forward messages to the BS, thereby consuming more
energy than other nodes and resulting in a shorter life-
time for these nodes.
The authors in (Brooks et al., 2007) introduce a
detection algorithm based on a random key distribu-
tion approach. Here, every sensor node is given a set
of randomly chosen symmetric keys and those keys
are selected from a larger pool of keys. A counting
bloom filter is used by every node for clone detection
and the base station knows the filter of every sensor
node. In order to detect clones, the base station exam-
ines all keys used in the network and if each of these
exceed a certain threshold then that key is considered
as cloned. Finally, a revocation procedure is called to
detect the corresponding cloned nodes.
The SET protocol (Choi et al., 2007) models the
network as a set of non-overlapping regions or clus-
ters. The base station broadcasts a random value
which is used to construct clusters or subsets and se-
lect cluster heads. Cluster heads are referred to as
subset leaders (SLs) and clusters are formed using an
exclusive subset maximal independent set (ESMIS)
algorithm. One or more trees are constructed with
SLs and a bottom-up aggregation is used to aggregate
all nodes. A node is said to be cloned if the corre-
sponding ID is found in two distinct subsets. SET
suffers from a high communication overhead due to a
complex detection scheme.
All of the protocols described above are used in
static sensor networks but they are not suitable for
mobile nodes. (Ho et al., 2009) was the first work
to look at clone detection in mobile networks by pre-
senting a Sequential Probability Ratio Test (SPRT)
based clone detection algorithm. In this scheme, all
nodes report to the Base Station (BS) with a list of
encountered nodes every time they change location.
The BS checks for a cloned node by seeing if it is
present in two different locations with a velocity sur-
passing a certain threshold. This approach could be
error-prone due to mistakes in node speed measure-
ments and SPRT is used to avoid this. However, this
approach still involves a single point failure as well as
rapid energy depletion of nodes near the BS.
2.2 Distributed Detection
Line Selected Multicase (LSM) (Parno et al., 2005)
is the first globally aware distributed algorithm for
clone detection. In LSM, the location of a node is for-
warded with a certain probability to some randomly
chosen destination nodes. Some intermediate nodes
form a claim message path to forward claim mes-
sages from the source to the destination node. All
forwarding nodes examine the signature of the claim,
save it and verify its coherence with other position
claims. A clone is said to be detected when a node in
the intersection of two message paths discovers two
different nodes (with the same ID) with two distinct
claims. LSM suffers from a high memory overhead
and a high communication overhead due to the stor-
ing of many messages and the node-to-node message
passing. Also, it assumes that all nodes are aware of
each others location which may restrict its applicabil-
ity.
In the RED (Randomized, Efficient and Dis-
tributed) (Conti et al., 2011) protocol, the base station
broadcasts a pseudo-random number to every sensor
node periodically. This protocol consists of two steps
for detecting clone nodes. In the first step, a ran-
dom value is shared between nodes and then every
node constructs a digital signature and locally broad-
casts its claim-ID and geographical position to a node
set known as the witness nodes. Witness nodes are
responsible for clone detection. In the second step,
these witness nodes, verify the received signature and
check each claim message for freshness. This enables
clone detection and also prevents stale messages from
being replayed. It is worth noting that this approach
is deterministic i.e., the nodes that will act as inspec-
tors to identify suspicious activities are fixed and that
this strategy is also used for static wireless sensor net-
works.
Zhu et al. (Zhu et al., 2007) presented two
methods Single Deterministic Cell (SDC) and Par-
allel Multiple Probabilistic Cell (P-MPC) where the
SENSORNETS 2017 - 6th International Conference on Sensor Networks
136

network is split into cells and every cell is used to
map nodes. When a node claims, it is routed to the
mapped cell and the claiming message is broadcast to
the mapped cell. The nodes within the mapped cell
then acts as witnesses for the claiming node. The
difference between P-MPC with SDC is that multi-
ple cells can be used to map each node ID; however,
cell mapping is still deterministic since the location
claim is mapped and sent to multiple deterministic
cells with varying probabilities.
The primary version (Yu et al., 2008) of (Yu et al.,
2009) describes the first distributed clone detection
technique for a mobile sensor network. This version
applies a challenge-and-response technique but its de-
tection efficiency is susceptible to colluding clones
and (Yu et al., 2009) provides an approach to detect
the colluding clones. But the drawback of this ap-
proach is that the storage space requirement grows
linearly with the network size. Another limitation is
the scalability of this approach as the network size
grows.
Yu et al. (Yu et al., 2013) proposed two algo-
rithms eXtremely Efficient Detection (XED) and Effi-
cient Distributed Detection (EDD) for mobile sensor
networks to resist clone attacks in a localized fashion.
Every node sends its node ID to the base station using
its one-hop neighbors. The base station then checks
all the IDs it receives for clone detection. However,
they require a double signature scheme which incurs
additional communication costs.
3 DISTRIBUTED DETECTION
USING PREFIX MATCHING
(DDPM)
3.1 Preliminaries
We consider a set of mobile nodes with node IDs
{1, ..., n} in a homogeneous mobile sensor network.
We assume symmetric communication. Time for all
of the sensor nodes is divided into intervals of equal
length and it is not necessary for time to be synchro-
nized across nodes. The sensor nodes use a random
way point (RWP) model (Johnson and Maltz, 1996)
to move wherein a node moves towards a destination
position with a speed ¯v chosen arbitrarily from the in-
terval [ ¯v
min
, ¯v
max
]. A node does not change its position
for a random amount of time when it reaches the des-
tination point. When a node starts a clone detection
round it only moves after this round ends. We as-
sume that every node is aware of its own geographic
position and some neighbors are in close proximity
to a node on every move. We also assume that the
nodes in the mobile sensor network construct an over-
lay network that can be used for routing. We utilize
an identity-based public key system (Liu and Ning,
2008; Malan et al., 2008) to generate and verify signa-
tures. It is not mandatory to have a powerful base sta-
tion (BS) but an initiator should initiate the distributed
detection procedure so that an intruder cannot conduct
a denial-of-service (DoS) threat by insisting that be-
ginning the clone detection procedure would result in
depletion of the cloned nodes energy.
3.2 Threat Model
We consider an adversary model where an intruder
can capture and compromise sensor nodes that are
placed in hostile environment. However, the ad-
versary can compromise only a few nodes to create
clones and will deploy these clones in the network in-
telligently. We must have a minimum of at least one
legitimate node for each cloned node in order for the
proposed scheme to work.
The adversary will always want to hide cloned
nodes from being detected and the detection proce-
dure may be interrupted by the intruder as follows.
Cloned nodes do not wish to participate in the de-
tection procedure or cloned nodes try to fake, drop
or manipulate claim messages that are sent as part
of the detection procedure. Furthermore, it will take
some time for an adversary to capture and compro-
mise some nodes. Nodes excluding the compromised
nodes are considered as legitimate nodes. Sometimes,
an adversary can mislead the clone detection protocol
to consider legitimate nodes as cloned nodes. We re-
fer to this attack as a framing attack.
3.3 Performance Metrics
The metrics that are used to assess DDPM’s perfor-
mance are as follows:
• Security Level: Every clone detection protocol
should detect node replication attacks with a high
probability. If a detection approach is determinis-
tic in a manner that cloned nodes are always de-
tected by witness nodes and every node can act as
a witness with equal probability, then the number
of witness nodes can be used to measure the secu-
rity performance since a large number of witness
nodes can be used to resist a replication attack.
• Communication Overhead: We should minimize
the communication cost to get better performance
in a mobile sensor network because sending more
messages consumes more energy in the sensor
Distributed Clone Detection in Mobile Sensor Networks
137

nodes. For the purpose of this paper, the commu-
nication cost is represented as the average number
of bits transmitted per node per move.
3.4 Reporter-Claimer-Witness Model
We utilize the Reporter-Claimer-Witness model
(Khan et al., 2015) for distributed detection. In this
model, a claimer node broadcasts its location claim
and ID to its neighbors. One or more of these neigh-
bors serve as reporters and map the claim id to witness
nodes. These witness nodes are responsible for clone
detection. When they receive conflicting claims from
cloned nodes, they start a revocation process to let
other nodes know about the presence of cloned nodes.
A key problem that we sought to solve was that of
avoiding having a deterministic set of witness nodes
to verify a claim. If the set of witness nodes is deter-
ministic this creates a significant threat since an ad-
versary can capture and clone these nodes. In order
to solve this problem, we created a prefix matching
scheme that selects the set of witness nodes for each
claim message differently for every detection round.
Every node is assigned a unique 128-bit node ID.
We use a cryptographic hash function of the node IP
address or public key to produce the node ID. For ev-
ery claim message produced by a claiming node, a
key is produced using a 128 bit hash by its neighbor-
ing reporter nodes. This key uses the random num-
ber that was sent by the initiator for clone detection
as well as information from the claiming nodes claim
message. The key idea in prefix matching is to have
the reporter nodes compute a hash for the claim mes-
sage and then search for the node whose node ID is
mathematically nearest to the hash-value. This node
will serve as the witness and check for claims. In
prefix matching, we pick multiple witness nodes by
picking nodes that match the generated key for each
claim message in increasing lengths. This process is
explained in more detail using an example in the next
subsection.
3.5 Details of DDPM
When a new detection round begins, the initiator (usu-
ally the base station) broadcasts an action message
containing a random number, rand.
In DDPM, there are three steps in every round of
clone detection. These are Initialization, Claiming
Neighbors and Processing Claims. We now present
each of these in more detail.
3.5.1 Initialization
In every new round of clone identification, the initia-
tor broadcasts an initialization message to start a de-
tection round. The initialization message is given by:
ini message := < rand,time, signed(k
Priv
Initiator
) >
In the initialization message rand is the random num-
ber generated by the initiator, time is the time stamp
when the initiator generated this message and the
message is signed with k
Priv
Initiator
which is the private
key of the initiator. This message is then broadcast
over the network.
3.5.2 Claiming Neighbors
When a sensor node receives the initialization mes-
sage, it verifies if the message signature is valid or not.
If valid, it extracts the random number rand from the
message. Each node then produces a claim message
with its location and id and sends this to its neighbor-
ing nodes who will serve as reporters. The reporters
will take the claim message and send this to a set of
witness nodes who will verify that the claiming node
is who it claims to be. By doing this, each sensor
node acts as a reporter node for its neighbors. The
claim message is sent through the overlay network
with a probability ρ
c
. ρ
c
can be seen as a means to
control the tradeoff between network traffic and secu-
rity. When ρ
c
= 1, every reporter node will forward
the claim message for its neighbor. For other values
of ρ
c
, the value determines the probability of a re-
porter node forwarding the claim message. For exam-
ple, when ρ
c
= 0.5, there is a probability of 0.5 that a
reporter will forward the claim message, thereby re-
ducing the number of nodes participating in the clone
detection process.
Now let us look into the details of a claim
message. Suppose the reporter is node A and it is
examining the claimer node B. Node A will create the
following claim message :
claim
BA
:= < Id
B
, Loc
B
, Id
A
, Loc
A
, signed(K
Priv
A
) >
In the above claim message Id
B
, Loc
B
, Id
A
, Loc
A
are the ID of node B, the location of node B, the ID
of node A, the location of node A respectively and the
message is signed by the private key of node A given
by K
Priv
A
. The reporter node A then generates a key for
the claiming message using the rand value sent by the
initiator as follows:
key := H(rand, Id
B
)
This key along with the claim message is used in
the next step. It is worth mentioning that for two dif-
ferent cloned nodes having the same ID but existing
at different locations, the claim message produced in
SENSORNETS 2017 - 6th International Conference on Sensor Networks
138

Figure 1: Illustrating verification of claiming message.
this step will vary but the key will be identical since it
is based on the random number used in a given round
of clone detection and the ID of the node.
3.5.3 Processing Claims
Next we present our distributed detection algorithm
that deals with the claim messages generated in the
previous step. Every node in the mobile wireless sen-
sor network contains a table with routing information,
a table with information about its neighboring nodes
and a leaf set. The routing table and leaf set are com-
puted for a given claim message key. In the routing
table, the entries at a given row i point to the nodes
that share the first i characters of their ID’s with the
message key (hence the name prefix matching). Also,
the leaf set contains an equal number of closest nodes
with a larger ID and closest nodes with a smaller ID
than this node.
Our distributed detection algorithm is presented in
Algorithm 1 and it uses and associated clone detec-
tion routing presented in Algorithm 2. R
d
length
indi-
cates a node in the routing table R at row length and
column d. d is the digit of the key at position length.
Each node upon receiving the initialization message
from the initiator generates a claim message and its
associated key as explained in the previous subsec-
tion. To avoid using a deterministic set of witness
nodes to verify this claim, our algorithm uses the key
associated with the claim message to pick a set of
nodes that will serve as witnesses based on matching
the prefix of their ID’s to that of the claim message
key. Since the key is used to pick the set of witness
nodes and the cloned nodes have the same keys, the
witness nodes will be able to detect the presence of
cloned nodes. Furthermore, since a new set of wit-
ness nodes is picked each round based on the random
number used by the initiator, it becomes difficult for
an adversary to guess what nodes will serve as witness
nodes.
An example: Let us now look at an example to bet-
ter understand how the process of using prefix match-
ing to forward claim messages works. Fig. 1 depicts
the process of forwarding claim messages. Suppose
that the source node is sensor A and has an ID of
65a1 f c and it is generating a claim message for a
neighbor B. Also suppose that the key for this claim
message generated for B is d46a1c. Node A
Algorithm 1: Claim management algorithm: claim manage.
for each neighbor B of Id
A
do
claim
BA
:= < Id
B
, Loc
B
, Id
A
, Loc
A
, signed(K
Priv
A
) >;
key:= H(rand, Id
B
);
if key destination is within its leaf set then
forward to the closest node Id of its leaf set;
detect clone(memory, claim
BA
);
else
length:= prefix(key, Id
A
);
if R
d
length
exists then
forward to the node of R
d
length
;
detect clone(memory, claim
BA
);
else
forward to a node whose pre f ix(k ey, id)
≥ length and is numerically closer to the key;
detect clone(memory, claim
BA
);
end if
end if
end for
Algorithm 2: Clone detection algorithm: detect clone.
check the signature of claim
BA
;
if Id
B
has found in the memory then
if Id
B
has found in two distinct Loc then
broadcast revocation procedure;
else
store claim
BA
in memory;
end if
end if
will forward this message to the node which has one
more matching character with the key, i.e., to d13da3
(Since A has 0 digits matching with the message key,
this node d13da3 is incrementing the matching length
to 1). Subsequently the message will be forwarded
to the nodes d4213 f , d462ba and d467c4 respec-
tively since each of these nodes is either improving
the matched length between its id and the message
key by one or is closest to the message key (in the
case of d467c4). All of these nodes are responsible
for clone detection. Note that since this key was gen-
erated using the random number rand sent by the ini-
tiator, each time clone detection is performed, a dif-
ferent set of nodes will be selected to serve as witness
nodes and verify that claim to detect clones.
3.6 Security Issues
3.6.1 Detection Validation
The identity-based cryptographic approach used in
the above algorithms is very useful when the authen-
tication of a trusted identity and claim message are
crucial. Also, this makes it difficult for the adver-
sary to falsify its node ID or to alter the messages
signed by legitimate nodes. Moreover, it will be tough
Distributed Clone Detection in Mobile Sensor Networks
139
for clones to fake their location to the inspector as a
falsely advertised position is far enough deviated from
the transmission range of the witnesses that is suffi-
cient to alert the inspectors.
3.6.2 Witness Protection
When the base station or initiator broadcasts a ran-
dom number, the adversary may try to compromise
witness nodes to defeat detection. Although the in-
truder may try to use the random number to compute
who the witness nodes are and then compromise them
to fail detection, this is unlikely. Since nodes are ran-
domly deployed in the network, it is not possible for
the adversary to capture all of the witness nodes. Ad-
ditionally, for each detection round the witness nodes
are changed so that the intruder cannot postpone clone
detection by capturing some witness nodes.
4 SIMULATION RESULTS AND
ANALYSIS
In this section, we evaluate the performance of our
Distributed Detection using Prefix Matching (DDPM)
strategy via computer simulation and compare it with
eXtremely Efficient Detection (XED) presented in
(Yu et al., 2013).
4.1 Simulation Setup
We implement DDPM using the discrete event net-
work simulator OMNeT++ (OpenSim, 2016). We uti-
lize the random graph model to generate our simula-
tion network. In the simulation, we adjust the sensor
node communication dynamically to maintain an ap-
proximate node degree d. We keep the approximate
node degree d = 15 for our simulations. The claiming
probability, ρ
c
is used as 1.0 for pro-security. This im-
plies that every claim message will be forwarded. We
set the network size N = 1000 nodes. To get precise
results, we consider 8 different network instances, and
for each simulation run of these instances, we perform
10 rounds of detection. A random number rand is
generated for every round and we randomly select the
number of cloned nodes between 2 − 100 by setting
their id the same as that for another node.
4.2 Performance Evaluation
To evaluate DDPM against XED in mobile sensor net-
works, we consider two performance metrics. The
first metric is the average number of witness nodes
and this is used to evaluate the security level. The
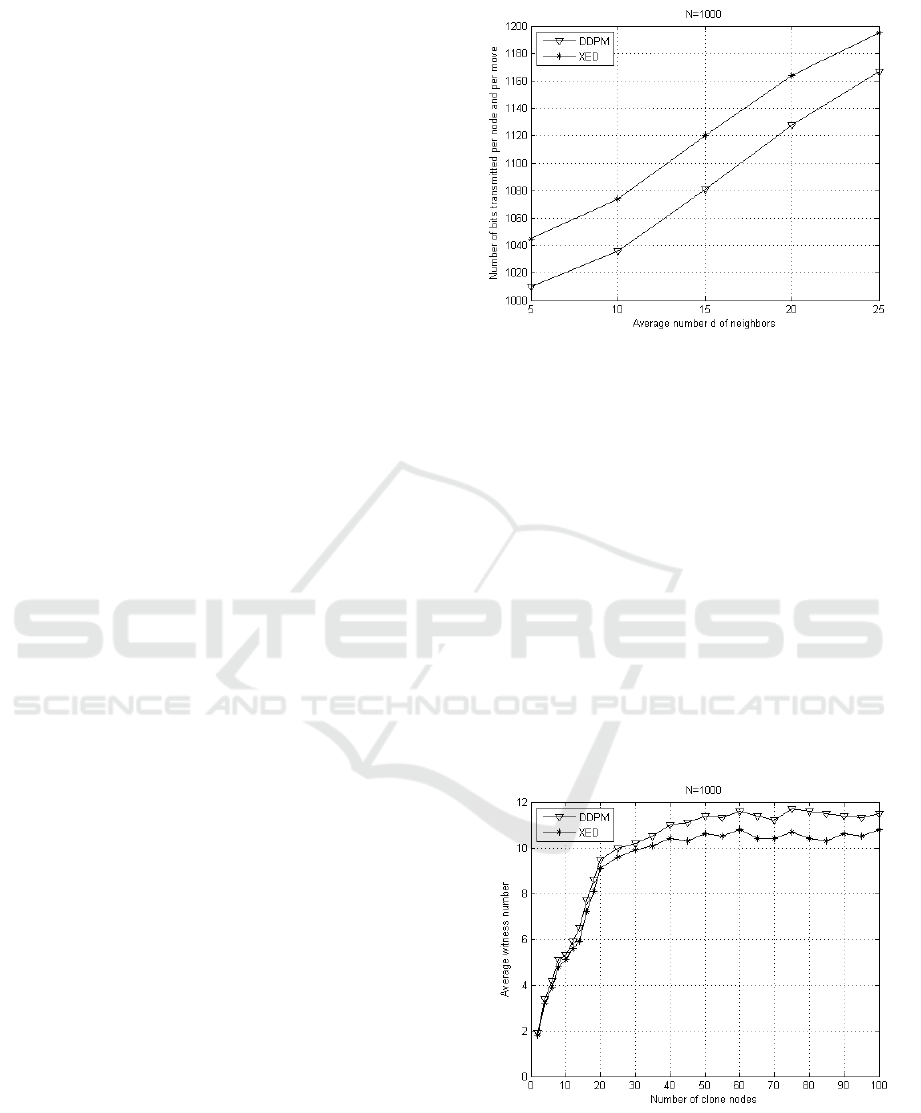
Figure 2: Communication overhead comparison among
DDPM and XED (N = 1000).
second metric is the communication overhead. Both
were explained in Section 3. We vary the number of
cloned nodes randomly between 2 to 100.
Fig. 2 depicts the communication overhead of
DDPM and XED. Nodes change positions accord-
ing to random waypoint model. XED incurs a higher
communication costs because nodes need to exchange
a random number using hash function. In XED when
a node encounters another node, it needs to compute
the hash function again to verify the legitimacy of the
encountered node. On the other hand, DDPM requires
each node to communicate with some intermediate
nodes to check for clones and the hash function is ap-
plied once during the transmission. We see a 4-5%
reduction in the communication overhead for DDPM
when compared to XED.
Figure 3: Security level comparison among DDPM and
XED (N = 1000).
Fig. 3 depicts the simulation results for the secu-
rity level metric. The average number of witnesses in
DDPM is pretty high even if 15% of the sensors ma-
liciously reject claim messages. The performance of
SENSORNETS 2017 - 6th International Conference on Sensor Networks
140

DDPM is compared with extremely efficient detection
(XED). The simulation results indicate that the aver-
age number of witness for the DDPM protocol is 7%-
10% higher than that for XED. The reason for this is
that in XED, only neighbors are responsible to check
whether any node has been cloned or not whereas in
DDPM, the neighbors, the intermediate nodes based
on prefix and the destination node all serve as witness.
Furthermore this set of nodes varies for each round of
detection and is not predetermined. This exhibits the
superiority of the DDPM.
5 CONCLUSION
In this paper, we introduced a distributed approach
for clone detection in mobile sensor networks. We
aimed to solve the problem of avoiding picking a de-
terministic set of nodes that existing approaches suf-
fer from. Our initial simulations show that DDPM can
outperform existing state-of-art approached like XED
with by providing a higher security level. DDPM also
reduces the communication overhead. DDPM is ID-
oblivious as well as area oblivious. For our future
work, we will measure the performance by incorpo-
rating several independent DDPM systems with dif-
ferent random numbers and vary the network density
to check performance in the case of sparse mobile
sensor network.
REFERENCES
Akyildiz, I. F., Su, W., Sankarasubramaniam, Y., and
Cayirci, E. (2002). A survey on sensor networks.
IEEE communications magazine, 40(8):102–114.
Bonaci, T., Bushnell, L., and Poovendran, R. (2010). Node
capture attacks in wireless sensor networks: a system
theoretic approach. In 49th IEEE Conference on De-
cision and Control (CDC), pages 6765–6772. IEEE.
Brooks, R., Govindaraju, P., Pirretti, M., Vijaykrishnan,
N., and Kandemir, M. T. (2007). On the detection
of clones in sensor networks using random key pre-
distribution. IEEE Transactions on Systems, Man,
and Cybernetics, Part C (Applications and Reviews),
37(6):1246–1258.
Choi, H., Zhu, S., and La Porta, T. F. (2007). Set: Detect-
ing node clones in sensor networks. In Security and
Privacy in Communications Networks and the Work-
shops, 2007. SecureComm 2007. Third International
Conference on, pages 341–350. IEEE.
Conti, M., Di Pietro, R., Mancini, L., and Mei, A. (2011).
Distributed detection of clone attacks in wireless sen-
sor networks. IEEE Transactions on Dependable and
secure computing, 8(5):685–698.
Eschenauer, L. and Gligor, V. D. (2002). A key-
management scheme for distributed sensor networks.
In Proceedings of the 9th ACM conference on Com-
puter and communications security, pages 41–47.
ACM.
Ho, J. W., Wright, M., and Das, S. K. (2009). Fast detec-
tion of replica node attacks in mobile sensor networks
using sequential analysis. In INFOCOM 2009, IEEE,
pages 1773–1781. IEEE.
Johnson, D. B. and Maltz, D. A. (1996). Dynamic source
routing in ad hoc wireless networks. In Mobile com-
puting, pages 153–181. Springer.
Khan, W. Z., Aalsalem, M. Y., and Saad, N. (2015). Dis-
tributed clone detection in static wireless sensor net-
works: Random walk with network division. PLoS
One, 10(5).
Liu, A. and Ning, P. (2008). Tinyecc: A configurable library
for elliptic curve cryptography in wireless sensor net-
works. In Information Processing in Sensor Networks,
2008. IPSN’08. International Conference on, pages
245–256. IEEE.
Malan, D. J., Welsh, M., and Smith, M. D. (2008). Im-
plementing public-key infrastructure for sensor net-
works. ACM Transactions on Sensor Networks
(TOSN), 4(4):22.
OpenSim (2016). Omnet++.
Parno, B., Perrig, A., and Gligor, V. (2005). Distributed de-
tection of node replication attacks in sensor networks.
In 2005 IEEE Symposium on Security and Privacy
(S&P’05), pages 49–63. IEEE.
Yi, J., Koo, J., and Cha, H. (2008). A localization technique
for mobile sensor networks using archived anchor in-
formation. In 2008 5th Annual IEEE Communica-
tions Society Conference on Sensor, Mesh and Ad Hoc
Communications and Networks, pages 64–72. IEEE.
Yu, C.-M., Lu, C.-S., and Kuo, S.-Y. (2008). Mobile sensor
network resilient against node replication attacks. In
2008 5th Annual IEEE Communications Society Con-
ference on Sensor, Mesh and Ad Hoc Communications
and Networks, pages 597–599. IEEE.
Yu, C.-M., Lu, C.-S., and Kuo, S.-Y. (2009). Efficient and
distributed detection of node replication attacks in mo-
bile sensor networks. In Vehicular Technology Con-
ference Fall (VTC 2009-Fall), 2009 IEEE 70th, pages
1–5. IEEE.
Yu, C.-M., Tsou, Y.-T., Lu, C.-S., and Kuo, S.-Y. (2013).
Localized algorithms for detection of node replication
attacks in mobile sensor networks. IEEE transactions
on information forensics and security, 8(5):754–768.
Zhou, L., Ni, J., and Ravishankar, C. V. (2006). Supporting
secure communication and data collection in mobile
sensor networks. In INFOCOM.
Zhu, B., Addada, V. G. K., Setia, S., Jajodia, S., and Roy, S.
(2007). Efficient distributed detection of node replica-
tion attacks in sensor networks. In Computer Security
Applications Conference, 2007. ACSAC 2007. Twenty-
Third Annual, pages 257–267. IEEE.
Distributed Clone Detection in Mobile Sensor Networks
141
