
PAbAC: A Privacy Preserving Attribute based Framework for Fine
Grained Access Control in Clouds
Sana Belguith
1,2
, Nesrine Kaaniche
3
, Abderrazak Jemai
4
, Maryline Laurent
3
and Rabah Attia
1,2
1
Tunisia Polytechnic School, Laboratory of Electronic Systems and Communication Network, Tunis, Tunisia
2
Telnet Holding, Telnet Innovation Labs, Tunis, Tunisia
3
SAMOVAR, CNRS, Telecom SudParis, University Paris-Saclay, Paris, France
4
Laboratory LIP2, University of Sciences of Tunis, Tunis, Tunisia
Keywords:
Cloud Storage Systems, Attribute-based Encryption, Attribute-based Signature, Data Confidentiality, Privacy.
Abstract:
Several existing access control solutions mainly focus on preserving confidentiality of stored data from unau-
thorized access and the storage provider. Moreover, to keep sensitive user data confidential against untrusted
servers, existing solutions usually apply cryptographic methods by disclosing data decryption keys only to au-
thorized users. However, these solutions inevitably introduce a heavy computation overhead on the data owner
for key distribution and data management when fine-grained data access control is desired. In addition, access
control policies as well as users’ access patterns are also considered as sensitive information that should be
protected from the cloud. In this paper, we propose PAbAC, a novel privacy preserving Attribute-based frame-
work, that combines attribute-based encryption and attribute-based signature mechanisms for securely sharing
outsourced data via the public cloud. Our proposal is multifold. First, it ensures fine-grained cryptographic ac-
cess control enforced at the data owner’s side, while providing the desired expressiveness of the access control
policies. Second, PAbAC preserves users’ privacy, while hiding any identifying information used to satisfy
the access control. Third, PAbAC is proven to be highly scalable and efficient for sharing outsourced data in
remote servers, at both the client and the cloud provider side.
1 INTRODUCTION
Data security and privacy are major challenges in the
adoption of cloud storage applications, mainly due to
the loss of data control. It is commonly agreed that
data encryption at the client side is a good alterna-
tive to mitigate data secrecy concerns. As such, the
client preserves the decrypting keys out of reach of the
cloud. Although encryption assures the confidential-
ity against curious cloud service providers, the use of
conventional encryption approaches is not sufficient
to support the enforcement of fine-grained access con-
trol policies. That is, data confidentiality preserva-
tion becomes more complicated, considering flexible
data sharing among dynamic groups of users. First,
access control policies should be flexible and distin-
guishable among users with different privileges. Sec-
ond, dynamic groups require efficient sharing of de-
ciphering keys between different authorized users. In
fact, the subscription of a new group member should
not require updating the secret keys of the remaining
users. So that, the complexity of key management is
minimized. Thus, the challenge is to define a com-
prehensive access control mechanism for outsourced
data while both ensuring data confidentiality and pro-
tecting users’ privacy.
For instance, with the involvement of a third-party
cloud provider, a crucial issue is that access patterns
may reveal privacy-sensitive information about users
and potentially leak confidential information about
the content. The confidentiality of outsourced data
and the privacy of users are thus not assured if these
sensitive data are not protected.
In this paper, we propose PAbAC, a novel privacy
preserving Attribute-based framework, that com-
bines Attribute Based Encryption (ABE) and At-
tribute Based Signature (ABS) mechanisms for se-
curely sharing outsourced data via public clouds.
PAbAC introduces a two-level access control model
that combines fine-grained access control which en-
sures a comprehensive granularity for access rules,
and anonymous data access, which allows the stor-
age server to manage access requests with no need to
learn the user identity nor his attributes. The original-
Belguith, S., Kaaniche, N., Jemai, A., Laurent, M. and Attia, R.
PAbAC: A Privacy Preserving Attribute based Framework for Fine Grained Access Control in Clouds.
DOI: 10.5220/0005968201330146
In Proceedings of the 13th International Joint Conference on e-Business and Telecommunications (ICETE 2016) - Volume 4: SECRYPT, pages 133-146
ISBN: 978-989-758-196-0
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
133

ity of PAbAC is multifold. First, PAbAC introduces a
privacy preserving authentication scheme, based on
a novel use of attribute-based signatures.The iden-
tity of the requesting entity client remains protected
against the certifying authorities as well as the cloud
service provider. Moreover, the combination between
attribute based encryption mechanisms and attribute
based signature scheme allows the cloud provider to
control the bandwidth consumption, and then, the sys-
tem’s availability. In fact, the authentication of re-
questing users permits to mitigate Flooding attacks
which exploit the bandwidth under provisioning vul-
nerability (Zunnurhain, 2012). Thus, only authorized
users can download encrypted data.
Second, as a designed decentralised multi-authority
attribute based framework, PAbAC reduces the bottle-
neck of maintaining a central authority for managing
secret parameters. Additionally, it supports issuing a
set of attributes from each attribute authority unlike
other access control schemes which rely on issuing
only one attribute per authority.
Third, the original use of attribute based encryption
and the related attribute based signature guarantees
fine grained access control to outsourced data and
provides an effective key management in sharing sce-
narios. For instance, the PAbAC framework is highly
scalable and offers interesting performances such as
low computation and communication cost, at both the
client and the cloud provider side.
Paper Organisation – The remainder of this work is
as follows: Section 2 presents security considerations
and design goals. Then, Section 3 reviews related
work and introduces attribute based mechanisms. In
Section 4, we describe the system model and review
some preliminaries and cryptographic primitives. Af-
terwards, we detail the framework design and de-
scribe the prototype and its different procedures in
Section 5. In Section 6, rigorous security discussions
are given. Finally, theoretical performances analysis
is provided in Section 7, before concluding in Sec-
tion 8.
2 PROBLEM STATEMENT
Let us consider the following example, where a hospi-
tal supports fine-grained access control on Electronic
Health Records (EHRs) and makes these records
available to hospital employees through a public
cloud. In accordance with regulations such as the
Health Insurance Portability and Accountability Act
(HIPAA) (HIP, ), the hospital policies must specify
which users can access which data item(s). In fact,
a health-care information system based on cloud ser-
vices is required to restrict access of protected medi-
cal records to eligible doctors while a client relation
management system running on a cloud may allow ac-
cess of patients’ information to high-level executives
of the hospital only. In many cases, hospital employ-
ees, mainly doctors, have to share patients’ health in-
formation, in order to properly prescript treatments.
Thus, they usually form dynamic sharing groups with
different granted privileges. Therefore, it is notewor-
thy that data confidentiality preservation is not the
only security concern. It is crucial to support flexible
sharing of encrypted outsourced data among dynamic
group of users, while protecting users’ privacy. In a
real e-health scenario, different medical organisations
can be involved such as hospitals, research laborato-
ries, pharmacies, health ministry as well as doctors
and patients. Let us consider that a doctor shares his
patients’ EHR in a public cloud. On one hand, the
shared data have to be protected from unauthorized
access while ensuring fine grained access control for
different authorized actors. Moreover, the data confi-
dentiality must be preserved against a malicious cloud
service provider. Thus, encryption on the client side
should be applied while supporting flexible sharing of
outsourced data among dynamic group of users.
On the other hand, the private identifying information
of the involved cloud users, such as doctors and pa-
tients, must not be revealed to the remote server. For
instance, the system should not reveal any private in-
formation related to a doctor, such as his professional
card or its speciality, as well as his patients’ data. That
is, the disclosure of such information may be used to
produce targeted advertisement related to the health
condition of the patients, or to run statistical surveys.
Thus, the design of PAbAC is motivated by providing
the support of both robustness and efficiency while
fulfilling the following properties:
• Data Confidentiality – PAbAC has to protect the
secrecy of outsourced and encrypted data contents
against both curious cloud service providers and
malicious users.
• Flexible Access Control – our proposal should
ensure flexible security policies among dynamic
groups of users with different granted privileges,
belonging to different groups.
• Privacy – PAbAC must protect group members’
access patterns privacy, while requesting access to
outsourced data. That is, the cloud server must
be able to grant access with no need to additional
identifying information of the requesting users.
• Low Computation Overhead – on one hand, for
scalability reasons, the amount of computation at
the cloud storage server should be minimized, as
SECRYPT 2016 - International Conference on Security and Cryptography
134

the server may be involved in concurrent interac-
tions. On the other hand, the proposed algorithms
should also have low processing complexity, at the
client side.
• Low Storage Cost – PAbAC should provide ac-
ceptable storage cost at the client side.
3 RELATED WORK
Several research works have been proposed in the lit-
erature in order to securely share data among groups
of users while protecting their privacy (Horv
´
ath,
2015),(Kaaniche et al., 2014),(Wan et al., 2012),(Yu
et al., 2010a), (Raykova et al., 2012), (Di Vimer-
cati et al., 2010b). In order to prevent untrusted
servers from accessing outsourced data, several so-
lutions apply encryption mechanisms at the client
side while disclosing the decryption keys to autho-
rized users only (Benaloh et al., 2009),(Di Vimer-
cati et al., 2010a), (Kaaniche et al., 2013), (Benaloh
et al., 2009), (Di Vimercati et al., 2015). Although
these methods ensure secure data access control, the
key distribution remains a bottleneck. For instance,
it becomes more complicated with the increase of the
number of users. To deal with this concern, Wang
et al. (Wang et al., 2009) propose to deliver the key
management to the remote server while assuming that
this latter is trusted. Moreover, in order to enforce au-
thorization policies, De Vimercati et al. (Di Vimercati
et al., 2007) proposed a novel solution aiming to en-
force the access control to the outsourcing systems.
De Vimercati et al. proposal is based on the appli-
cation of selective encryption as a means to enforce
authorizations while applying hierarchical key assign-
ment schemes.
Recently, Attribute-based Cryptography appears as
a promising technique, designed for ensuring fine
grained access control for outsourced data. This cryp-
tographic mechanism was introduced by Sahai and
Waters in 2005 (Sahai and Waters, 2005).
In the following, we present Attribute based Encryp-
tion mechanisms (ABE) and their application in cloud
environments in Section 3.1. Then, we introduce At-
tribute based Signature schemes (ABS) and review re-
lated work applying ABS for protecting access to out-
sourced data in cloud servers.
3.1 Attribute based Encryption (ABE)
In 2005, Sahai and Waters introduced the concept of
Attribute Based Encryption (ABE), as a new mean for
encrypted access control (Sahai and Waters, 2005).
In ABE, ciphertexts are not necessarily encrypted to
one particular user as in traditional public key cryp-
tography. Instead both users’ private keys and ci-
phertexts are associated with a set of attributes or a
structure over attributes (Bethencourt et al., 2007).
The user is able to decrypt a ciphertext if there is a
match between his private key and the ciphertext. For
instance, Goyal et al. distinguishes two ABE cate-
gories, namely: Key-Policy ABE (KP-ABE) (Goyal
et al., 2006) and Ciphertext-Policy ABE (CP-ABE)
(Bethencourt et al., 2007). Several works rely on ABE
to provide fine grained access control for outsourced
data (Hur and Noh, 2011),(Yu et al., 2010b),(Jahid
et al., 2011). Although these schemes proposed effi-
cient solutions to protect outsourced data, they require
the use of a central trusted authority to manage all
the attributes and issue the related secret keys to users
in the system. Thus, this central authority is able to
achieve a key escrow attack, due to its knowledge of
the users’ private keys.
Wang et al. (Wang et al., 2010) propose a hierarchical
access control mechanism for cloud storage. Their
scheme is based on the Bethencourt et al. CP-ABE
scheme (Bethencourt et al., 2007) and hierarchical
Identity based Encryption (IBE) (Horwitz and Lynn,
2002). This scheme relies on the use of several au-
thorities arranged in a hierarchical way. However, it
still relies on the trusted authority and fails, if the lat-
ter is compromised.
Recently, Lewko and Waters (Lewko and Waters,
2011) proposed a decentralized ABE scheme, where
users could obtain their private keys from different
attribute authorities. Each attribute authority is in
charge for deriving a private key associated to a one
attribute. The proposal (Lewko and Waters, 2011)
did not require a central trusted server, which must
remain active and uncorrupted throughout the life-
time of the system. Based on this decentralized ar-
chitecture, there is no need for absolute trust in a
single designated entity. However, Lewko and Wa-
ters (Lewko and Waters, 2011) assume that each at-
tribute authority is responsible for issuing only one
attribute. Moreover, in order to prevent collusion in
such a setting, this scheme requires that each user
has a unique global identifier (GID), which they must
present to each authority. Unfortunately, due to the
use of GID, the users cannot preserve their privacy
against attribute authorities. In fact, while a user must
present the same GID to each authority, colluding au-
thorities can pool their data and build a complete pro-
file of all of the attributes corresponding to each GID.
However, this might be undesirable, particularly if the
user uses the ABE system in many different settings
and wants to keep information about some of those
settings private. Based on the Lewko and Waters pro-
PAbAC: A Privacy Preserving Attribute based Framework for Fine Grained Access Control in Clouds
135

posal (Lewko and Waters, 2011), Ruj et al. (Ruj
et al., 2011) proposed a distributed sharing scheme
in cloud environments scheme with an attribute revo-
cation extension (DACC). The DACC solution con-
sists of using one or several key distribution centers
responsible for issuing keys to data owners and users
related to their attributes. The data owner encrypts
data under an access structure and stores them in the
cloud. The users, while matching their set of at-
tributes to the access structure, can retrieve the data
from the cloud. We must note that the DACC proposal
also supports revocation of users, without redistribut-
ing keys to all the users of cloud services. In 2015,
Horv
´
a (Horv
´
ath, 2015) proposed a decentralized ABE
scheme for securely sharing data in cloud computing
systems based on the use of the decentralized Lewko
and Waters scheme (Lewko and Waters, 2011). In
order to achieve an efficient revocation scheme, this
proposal relies on the use of an identity based user re-
vocation mechanism to manage access rights for out-
sourced data. This proposed extension supports mul-
tiple independent attribute authorities in which revo-
cation of specific users (e.g. based on users’ identi-
ties) from the system is possible without updates of
attribute public and secret keys.
Most of the mentioned approaches do not propose a
mechanism to authenticate requesting users. More-
over, these schemes are based on the use of Lewko
et al. decentralised ABE scheme (Lewko and Waters,
2011) which requires the use of the users’ global iden-
tifiers GIDs. Thus, the privacy of the user is not pro-
tected against the attribute authorities.
3.2 Attribute based Signature (ABS)
Attribute-Based Signatures (ABS) (Maji et al., 2011)
is a flexible primitive that enables a user to sign a
message with fine grained access control over iden-
tifying information. In ABS, the user possesses a set
of attributes, obtained from a trusted authority. This
latter can sign a message with respect to a predicate
satisfied by his attributes. The signature reveals no
more that the fact that a single user with some set
of attributes satisfying the predicate has attested to
the message. Maji et al. presented a comparison of
ABS with other signature-related-notions (Maji et al.,
2011), such that ring signatures (Rivest et al., 2001)
and group signatures (Chaum and Van Heyst, 1991)
that can be considered as particular categories of at-
tribute based signatures (El Kaafarani et al., 2014a).
In (Maji et al., 2011), Maji et al. also introduced dif-
ferent applications of ABS including attribute-based
messaging (Bobba et al., 2006), trust negotiation
(Frikken et al., 2006) and leaking secrets. Some
constructions of ABS consider multiple authorities
while others only support a single attribute authority.
Okamoto et al. (Okamoto and Takashima, 2013) and
El Kaafarani et al. (El Kaafarani et al., 2014b) have
proposed the first fully decentralized attribute based
signatures schemes. These schemes consist of involv-
ing multiple attribute authorities in the system, with
no reliance on a central authority. The security of at-
tribute based signatures requires users’ privacy and
unforgeability. On one hand, users’ anonymity re-
quires that signatures reveal neither users’ identities
nor the attributes used in the signing algorithm. On
the other hand, unforgeability requires that a user can-
not forge a signature with respect to a signing predi-
cate that the user attributes do not satisfy, even if this
user colludes with other users (Ghadafi, 2015).
Several works rely on the attribute based signature
to ensure the authentication of data owners and fine
grained access control to outsourced data in the cloud.
Indeed, Ruj et al. (Ruj et al., 2012) presented a pri-
vacy preserving authenticated access control scheme
for securing data in clouds based on an attribute based
signature scheme. In the proposed scheme, the cloud
provider verifies the authenticity of the data owner
without knowing the user’s identity before storing in-
formation. To do so, this scheme uses a combina-
tion of the decentralized attribute based encryption
(Lewko and Waters, 2011) and the multi-authority at-
tribute based signature proposed by Maji et al. (Maji
et al., 2011). This proposal relies on the use of a
global identifier GID in order to issue private keys
from attribute authorities to users, thus the attribute
authorities can reveal the user’s identity. Finally, the
proposed authentication scheme is used to authenti-
cate the data owner and there is no way to authenticate
the requesting users. In (Zhao et al., 2011), Zhao et
al. applied the ciphertext-policy attribute based en-
cryption (CP-ABE) proposed by Bethencourt et al.
(Bethencourt et al., 2007) combined with the Maji
et al. (Maji et al., 2011) attribute based signature to
ensure fine grained access control to outsourced data
in the cloud. This proposal does not take interest in
authenticating the requesting users. Moreover, it is
based on a centralized ABE and ABS schemes, thus
it relies on a central trusted authority to issue secret
keys to all the users.
4 PAbAC SYSTEM
In this section, we present our system model in sec-
tion 4.1 and the mathematical background is pre-
sented in section 4.2.
SECRYPT 2016 - International Conference on Security and Cryptography
136
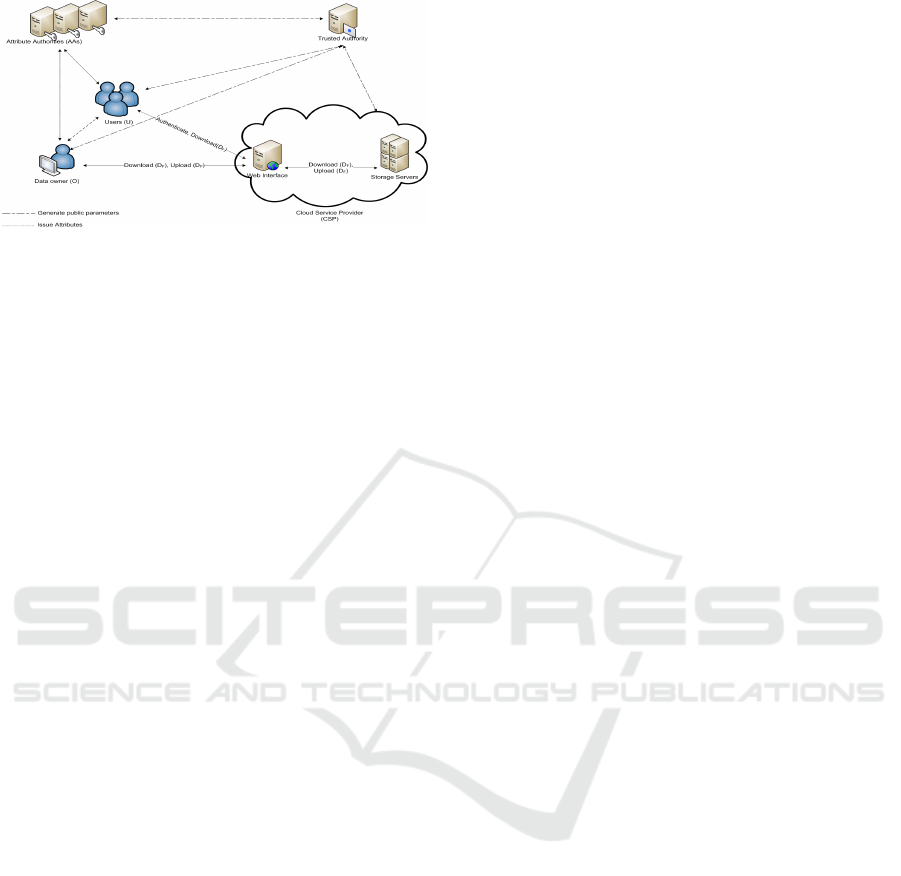
Figure 1: The main architecture entities and their interac-
tion.
4.1 System Model
Figure 1 presents the different entities involved in
PAbAC and defined as follows:
Cloud Service Provider (CSP): the CSP is assumed
to have abundant storage capacity and computation
resources in order to manage data storage service.
The cloud provider consists of data servers and a data
service manager. Data servers are responsible for
storing data outsourced by the data owner while the
data manager is in charge of controlling the accesses
from requesting users to outsourced data and provid-
ing corresponding contents services.
Data Owner (O): the data owner is responsible for
outsourcing data into the remote cloud servers and
granting access privileges to other cloud users, by
specifying an attribute-based access policy for each
data file.
Users (U): a user is a cloud client that may access to
outsourced content by data owners. In a nutshell, if
a user has the set of attributes satisfying the access
structure of the encrypted data file, he then may have
access to data.
Trusted Authority (TA): TA is a trusted third party
in our system which is responsible for generating and
managing public parameters for both used mecha-
nisms: attribute based encryption and attribute based
signature.
Attribute Authority (AA): AA is a party responsi-
ble for deriving a public keys and issuing private keys
to different users that are assigned to their attributes.
The Attribute Authority can be considered as an Iden-
tity Provider. In PAbAC, any trusted party can be-
come an attribute authority and there is no require-
ment for any global coordination other than the cre-
ation of an initial set of common public parameters.
4.2 Mathematical Background
In this section, we first introduce the access structure
in section 4.2.1. Then, in section 4.2.2, we present
the bilinear maps. Finally, we introduce our security
assumptions.
4.2.1 Access Policies
Access policies can be represented by one of the fol-
lowing formats: i) Boolean functions of attributes, ii)
Linear Secret Sharing Scheme (LSSS) matrix, or iii)
Monotone span programs (Lewko and Waters, 2011).
Definition 1. Access Structure
Let {P
1
,··· , P
n
} be a set of parties. A collection
A ⊆ 2
{P
1
,···,P
n
}
is monotone if ∀B,C if B ∈ A and B ⊆ C
then C ∈ A (Lewko and Waters, 2011).
An access structure is a collection A of non-empty
subsets of {P
1
,· ·· , P
n
}, such as A ⊆ 2
{P
1
,···,P
n
}
\
/
0.
We note that any access structure can be converted
into a Boolean function. Boolean functions can
be represented by an access tree, where the leaves
present the attributes while the intermediate and the
root nodes are the logical operators AND (∧) and OR
(∨).
Definition 2. Linear Secret Sharing Schemes (LSSS)
A Linear Secret Sharing Scheme LSSS over a set
of parties P (Lewko and Waters, 2011) is defined as
follows:
1. the shares of each party form a vector over Z
p
.
2. there exists a matrix A with n rows and l columns
called the share-generating matrix for LSSS. ∀i ∈
[1,· ·· , n], the i
th
row of A is labeled by a party ρ(i)
( where ρ is function from {1,·· · , n} to P). When
we consider the column vector ~v = [s,r
2
,· ·· , r
n
],
where s ∈ Z
p
is the secret to be shared, and
r
2
,· ·· , r
n
∈ Z
p
are randomly chosen, then A.~v =
~
λ
is the vector n shares of the secret s according to
LSSS.
In (Beimel, 1996), Beimel presents the algorithm that
converts a boolean function (in the form of access
tree) as a LSSS matrix.
Definition 3. Monotone Span Programs
For a field F and a variable set S = {a
1
,..., a
n
}, a
Monotone Span Program (Karchmer and Wigderson,
1993) is defined by a α × β matrix A along with a
labeling map ρ which associates each row in A with
an element a
i
∈ S. The span program accepts a set
γ if 1 ∈ Span(A
γ
), where (A
γ
) is the sub-matrix of
A containing only rows with labels a
1
∈ γ. In other
words, the span program only accepts the set γ if there
exists a vector s such that s · A
γ
= [1, 0,..., 0].
4.2.2 Bilinear Maps
An admissible symmetric pairing function ˆe from
G
1
× G
1
in G
T
has to be bilinear, non degenerate
PAbAC: A Privacy Preserving Attribute based Framework for Fine Grained Access Control in Clouds
137

and efficiently computable. G
1
and G
T
are two mul-
tiplicative subgroups of a finite field. G
1
and G
T
have
the same order N.
4.2.3 Complexity Assumptions
Our proposal is based on three cryptographic assump-
tions detailed as follows:
Definition 1. Discrete Logarithm Problem (DLP)
Given a generator g of a multiplicative cyclic
group G of order N, and given the public element
y = g
x
∈ G, the problem of finding x is called the Dis-
crete Logarithm Problem.
Definition 2. Computational Diffie Hellman prob-
lem (CDH)
Given a generator g of a multiplicative cyclic
group G of order N, and given two group elements
g
a
∈ G and g
b
∈ G where a, b ∈ Z
N
are two secrets,
the problem of calculating g
ab
from g
a
and g
b
is called
the Computational Diffie Hellman problem.
Definition 3. Decisional Diffie Hellman problem
(DDH)
Given a generator g of a multiplicative cyclic
group G of order N, and given two group elements
g
a
∈ G and g
b
∈ G where a,b ∈ Z
∗
N
are two secrets, the
problem of distinguishing between tuples of the form
(g
a
,g
b
,g
ab
) and (g
a
,g
b
,g
c
) for some random integer
c, is called the Decisional Diffie Hellman problem.
5 PAbAC: PROPOSED SOLUTION
5.1 Motivation
In order to achieve fine grained and privacy preserv-
ing access control to outsourced data in cloud storage,
we combine two latest cryptographic techniques, CP-
ABE and ABS. The choice of attribute based cryptog-
raphy (ABC) is motivated by several reasons. First,
we benefit from an easier key management system,
thanks to the certificate-free feature of ABC. Second,
ABC permits deriving public keys with no need for
previous computation of corresponding private keys.
That is, contrary to traditional public key derivation
schemes, ABC does not require to generate the private
key before the public key. Indeed, users have only to
generate access structure and the related enciphering
key to encrypt data before storage.
CP-ABE is much more appropriate to data outsourc-
ing, since it enables the data owner to generate an ac-
cess tree over selected attributes. Thanks to its flex-
ibility in specifying different access rights for each
individual user, ABE is considered as one of the most
public key primitive which is appropriate for one-to-
many communications. That is, data are encrypted
under a set of attributes so that multiple users who
possess proper keys can decrypt. This potentially
makes encryption and key management more effi-
cient. Moreover, the enciphering entity is not required
to know the access control list.
In order to protect the requesting entity’s privacy,
PAbAC relies on using Attribute based Signature
(ABS). In ABS, messages are signed with respect to
an access structure. Thus, the CSP verifies that the
requesting user having a set of attributes satisfying
the access tree has indeed authenticated the message
without revealing his identity or the set of attributes
used in the signing procedure.
Our PAbAC framework is based on an original use
of the identity based signature scheme presented by
Waters (Waters, 2005) combined with the decen-
tralized Attribute Based Encryption introduced by
Lewko and Waters (Lewko and Waters, 2011) to
achieve an extension of waters’ scheme to a multi-
authority attribute based encryption. This novel en-
cryption scheme presented by PAbAC supports the is-
suance of a set of attribute obtained from the same
authority. Moreover, PAbAC introduces an origi-
nal multi-authority attribute based signature scheme
based on an extension of Waters’ identity based sig-
nature adapted to the multi-authority ABE encryption.
Thus, PAbAC presents lower computation costs espe-
cially at the client side compared with the other access
control schemes. The different notations used in this
paper are listed in Table 1.
Table 1: The different notations used in this paper.
Notation Description
S
U
Set of users’ attributes
S
j
Set of attributes certified by the at-
tribute authority AA
j
Sk
S
j
Secret keys related the set of at-
tributes S
j
obtained from the at-
tribute authority AA
j
AA Attribute Authority
D
F
Data file
O Data Owner
U User
E
D
Encrypted data file
ψ Access policy
5.2 Overview
In PAbAC, there are two main actors: a data owner
(O) and data users (U). The data owner first defines
SECRYPT 2016 - International Conference on Security and Cryptography
138

an access structure ψ that points out who can access
the outsourced data with respect to a set of attributes.
Then, the data file is encrypted under the access struc-
ture ψ, based on an attribute based encryption algo-
rithm. Then, the data owner stores the encrypted data
in the cloud. When a user wants to access the out-
sourced data file, he has first to authenticate with the
cloud. For this purpose, he has to sign a random
message, obtained from the cloud, under the access
structure ψ associated with the outsourced data file.
Afterwards, the cloud verifies the correctness of the
received signature in order to send the requested ele-
ments, namely the encrypted data file.
We suppose that each cloud user has already obtained
the private keys related to his attributes from the cor-
responding attribute authorities. For an e-health use
case, an attribute authority may be the hospital ad-
ministration issuing the affiliation card of each doctor
(i.e the professional card contains a set of attributes
such as the name of the doctor, his affiliation, his se-
rial number, ···).
Based on the required attributes, specified in the ac-
cess structure ψ, the requesting user selects related
private keys in order to decrypt the encrypted data file.
Our PAbAC proposal is defined upon the following
seven algorithms. It involves three procedures on the
basis of two phases. During the first phase, the system
initialisation procedure SYS INIT is executed. The
second phase occurs when the data owner wants to
share data files with other cloud users, based on both
the data storage procedure STORE and the data re-
trieval procedure BACKUP.
The SYS INIT procedure consists of three random-
ized algorithms for the generation of public param-
eters related to the involved attribute authorities re-
ferred to as setup and setup
auth
, and the generation
of users’ private keys denoted by keygen.
The STORE procedure presents the data storage sce-
nario. It consists of the encdata algorithm for the
encryption of data files.
For the data retrieval scenario, the BACKUP procedure
deals with the user’ authentication, namely sign and
verif and the data decryption algorithms referred to
as decdata.
5.3 System Initialisation Procedure
The SYS INIT procedure consists of three random-
ized algorithms, defined as follows:
• setup – this randomized algorithm takes as in-
put the security parameter λ. It outputs the global
public parameters PP defined as follows:
PP = {G
1
,G
T
,N, h, ˆe,u
0
,· ·· , u
n
}
where G and G
1
are two multiplicative groups of
order N, ˆe : G
1
× G
1
→ G
T
is a bilinear map, g,h
are generators of G
1
and {u
0
= g,· ·· , u
n
} are gen-
erators of G
1
randomly chosen such as u
i
= g
r
i
.
• setup
auth
– the setup
auth
algorithm is executed
by an attribute authority AA. The setup
auth
al-
gorithm takes as inputs the public parameters PP
and outputs the pair of private and public keys
(sk
A
, pk
A
), where sk
A
correspond to a random val-
ues α, and the related public key pk
A
is defined as
follows:
pk
A
= { ˆe(g
1
,g
1
)
α
}
• keygen – this algorithm is performed by an at-
tribute authority AA
j
. It takes as input the global
parameters PP, the attribute authority’s secret key
{sk
A
}, a random value t where t ∈ Z
p
and a set
of attributes S
j
= {a
1
,· ·· , a
n
j
}, where n
j
is the
number of attributes of S
j
. It outputs the secret
key sk
S
j
related to the set of attributes S
j
, as de-
picted by Algorithm 1.
Algorithm 1: Keygen procedure.
1: Input: the global parameters PP, the attribute au-
thority’s secret key {sk
A
j
} and a set of attributes
S
j
2: Output: the secret key sk
S
j
related to the set of
attributes S
j
3: K ← g
1
α
· h
t
;
4: L ← g
1
t
;
5: sk
S
j
← {K, L};
6: for all i ∈ [1. .. n
j
] do
7: K
i
← u
i
t
;
8: sk
S
j
← sk
S
j
∪ K
i
;
9: end for
10: return sk
S
j
5.4 Data Storage Procedure
To outsource a data file (D
F
) to the cloud, the data
owner (O) performs the STORE procedure. For this
purpose, he first defines an access policy ψ and ob-
viously selects the attribute needed to satisfy it. We
note that the access policy ψ is described in terms
of a monotonic boolean formula. We represent the
boolean formula as an access tree where the interior
nodes are AND and OR gates, and the leaf nodes cor-
respond to attributes as detailed in Section 4.2.
Thus, the access policy corresponds to the couple
(A,ρ) where A is an n × l access matrix and ρ is the
function that maps the matrix rows to the required at-
tributes. These attributes have to be obtained from a
certified Attribute authority (AA) that is responsible
PAbAC: A Privacy Preserving Attribute based Framework for Fine Grained Access Control in Clouds
139

of issuing the required attributes.
After defining the access structure (A, ρ), the data
owner encrypts the data file D
F
, based on the
encdata algorithm. We note that our encryption al-
gorithm relies on the decentralized Lewko and Wa-
ters ABE scheme (Lewko and Waters, 2011). That is,
we extend the (Lewko and Waters, 2011) proposal to
support deriving a set of private keys related a set of
attributes from each single attribute authority, while
preserving users’ privacy with respect to the involved
attribute authorities.
The STORE procedure consists of the encdata algo-
rithms, defined as follows:
• encdata – the encryption algorithm encdata
is executed by the data owner. It takes as in-
put the attribute authorities’ public keys {pk
A
},
the data file D
F
, the public parameters PP and
the access policy (A,ρ). The encdata algo-
rithm outputs the ciphertext as a tuple E
D
=
(C
0
,C
1,i
,C
2,i
,C
3,i
)
i∈{1,n}
(where i presents a ma-
trix row corresponding to attribute i) defined as
follows:
C
0
= D
F
ˆe(g
1
,g
1
)
s
(1)
C
1,i
= ˆe(g
1
,g
1
)
λ
i
(2)
C
2,i
= g
1
p
i
(3)
C
3,i
= g
1
p
i
g
1
w
i
u
i
p
i
(4)
Where p
i
,s ∈ Z
N
are random values selected by
the data owner, λ
i
=
~
A
i
·~v where ~v ∈ Z
N
l
is a ran-
dom vector with s as its first entry and w
i
=
~
A
i
·
~
τ
such as
~
τ ∈ Z
N
l
is a random vector with 0 as its
first entry.
Figure 2 depicts the storage procedure STORE of the
PAbAC framework.
5.5 Data Backup Procedure
For the data retrieval scenario, the BACKUP proce-
dure starts with the user’ authentication, with respect
to the sign and verif algorithms and is achieved by
the data decryption algorithm referred to as decdata.
The figure 3 presents different interactions between
Figure 2: PAbAC data storage procedure STORE.
Figure 3: PAbAC data backup procedure BACKUP.
the cloud provider and the requesting user for the data
access procedure.
We detail, in Section 5.5.1, the different algo-
rithms for user authentication with the cloud provider
upon requesting access to an outsourced data file E
D
.
Then, we present, in Section 5.5.2, the algorithm
needed for decrypting the outsourced data file.
5.5.1 Anonymous User Authentication
When a user (U) wants to access to the encrypted data
file (E
D
) outsourced by the data owner, the CSP has
to first authenticate the user, with respect to the ac-
cess tree ψ associated with the encrypted data file. So
that, the cloud provider sends a random value m which
consists of the cloud provider identity concatenated
with the current time (i.e. m is assumed to be different
for each authentication session). The requesting user
has then to sign the received value m with respect to
the signing predicate ψ, and sends his signature to the
cloud provider. We note that if the verification fails,
the user cannot access to data and the cloud provider
does not send the encrypted data file. The anonymous
authentication procedure consists of two algorithms,
defined as follows:
• sign – this algorithm takes as input the global
public parameters PP, a random token m, a sign-
ing policy ψ and the set of attributes’ secret keys
{sk
S
j
} that satisfies the signing predicate. It out-
puts a signature σ.
In fact, the user first selects the sub-set of his at-
tributes S
U
that satisfies the signing predicate ψ,
such as: ψ(S
U
) = 1 and signs the received value
m. The user finally sends the signature σ to the
cloud provider who checks the resulting signature.
Thus, the user first converts ψ to its corresponding
monotone span program A which is an n ×l access
matrix, with respect to the row labeling function
ρ : [n] → S
U
. In addition, he computes the vector
~y such as ψ(S
U
) = 1 and ~y ·
~
A = [1,0, ·· · , 0]. In
order to sign the random token m, the data owner
SECRYPT 2016 - International Conference on Security and Cryptography
140

first randomizes his secret key sk
S
j
as follows:
K
0
= Kh
t
0
= g
1
α
h
t+t
0
(5)
L
0
= Lg
1
t
0
= g
1
t+t
0
(6)
K
0
i
= K
i
u
i
t
0
= u
i
t+t
0
,∀i ∈ S
U
(7)
In the sequel, the requesting user’s new pri-
vate key is defined by {sk
0
S
j
} such as {sk
0
S
j
} =
{(K
0
,L
0
,K
0
i
)}.
Then, for each i ∈ [1,n], the signer computes x
i
=
(L
0
)
y
i
and sets z =
∏
n
i=1
((K
0
ρ(i)
)
y
i
. Afterwards, the
signer generates a random r ∈ Z
N
and computes:
σ
1
= zK
0
g
1
mr
(8)
σ
2
= g
1
r
(9)
Finally, the signature for the message m gener-
ated by the user with respect to the signing policy
(A,ρ) is set as follows:
σ = (x
1
,· ·· , x
n
,σ
1
,σ
2
) (10)
• verif – this algorithm is a deterministic algo-
rithm which takes as input an ordered list of at-
tribute authorities’ public keys {pk
A
}, a random
token m, a signature σ and a signing predicate
ψ corresponding to (A,ρ) and outputs accept if
σ is valid on m using the access policy (A,ρ) or
reject otherwise. Afterwards, the CSP com-
putes the vector
~
β = [β
1
= 1, β
2
,· ·· , β
n
], such
that {β
i
}
i∈[2,n]
are randomly chosen and computes
µ
i
=
∑
j=1
l
β
j
A
i, j
. The cloud server accepts the
signature if the following equation holds.
ˆe(g
1
,σ
1
)
?
= pk
A
ˆe(g
1
m
,σ
2
)
n
∏
i=1
ˆe(h
µ
i
u
ρ(i)
,x
i
) (11)
The correctness of the signature algorithm is detailed
in the Section 6.4.
5.5.2 Data Retrieval
The data retrieval procedure consists of decdata al-
gorithm, defined as follows:
• decdata – this algorithm takes as input the user
secret decryption key {sk
S
j
}, the public parame-
ters PP and the ciphertext E
D
and outputs the orig-
inal data file D
F
. If the requesting user has the re-
quired private keys {sk
S
j
} for a subset of rows A
i
of A such that [1,0,··· ,0] is in the span of these
rows, then the user proceeds as follows.
For each matrix row i, the user computes:
C
1,i
. ˆe(L,C
3,i
)
ˆe(LK
i
,C
2,i
)
= ˆe(g
1
,g
1
)
λ
i
ˆe(g
1
t
,g
1
)
w
i
(12)
∏
i
( ˆe(g
1
,g
1
)
λ
i
ˆe(g
1
t
,g
1
)
w
i
)
c
i
= ˆe(g
1
,g
1
)
s
(13)
Where c
i
∈ Z
N
are constants such that
∑
i
c
i
~
A
i
=
[1,0, ·· · , 0].
Then, the data file D
F
can then be obtained as fol-
lows:
D
F
= C
0
/ ˆe(g
1
,g
1
)
s
(14)
The proof of correctness of the decryption algo-
rithm is detailed in the Section 6.4.
6 SECURITY DISCUSSION
In this section, we discuss the resistance of PAbAC
against two adversaries, based on two realistic threat
models, defined hereafter in Section 6.1. We prove
the security of our proposed scheme with respect to
the security requirements introduced in Section 2.
6.1 Threat Model
For designing the most suitable security solutions for
cloud sharing scenarios, we consider two adversaries:
malicious cloud user and honest but curious cloud
server.
Honest but Curious Cloud Server Adversary – this
storage server honestly performs the operations de-
fined by our proposed scheme, but it may actively at-
tempt to gain knowledge of the outsourced sensitive
data, such as access patterns.
Malicious User Adversary – this attacker can be an
unauthorized user. As such, he targets to get access to
the outsourced shared data. The objective of a mali-
cious user is to convince the cloud server that he is a
legitimate cloud user.
6.2 Confidentiality
In our proposed PAbAC scheme, data files are stored
on an encrypted form in cloud servers relying on an
attribute based encryption scheme, in order to ensure
efficient access control. As such, the data confiden-
tiality preservation is tightly related to security of the
used attribute based encryption scheme.
Theorem 1. PAbAC guarantees data confidentiality
of the outsourced data.
Proof. The proposed PAbAC framework is designed
to ensure data confidentiality against both malicious
users and curious cloud provider.
In PAbAC, the data owner is in charge of encrypting
his data before outsourcing them to the cloud stor-
age server. He is also responsible for defining an
PAbAC: A Privacy Preserving Attribute based Framework for Fine Grained Access Control in Clouds
141

access structure that points out who can access the
outsourced data with respect to a set of attributes.
Then, the cloud provider is responsible for sending
data to requesting users after authenticating them, re-
lying on the access policy defined by the data owner.
As such, only the authorized users having the access
structure’s satisfying attributes can generate the deci-
phering keys.
In addition, while considering a curious cloud ser-
vice provider who tries to gain knowledge about out-
sourced data file, this latter cannot access the out-
sourced data. As detailed in Section 5, our encryption
algorithm relies on the Lewko and Waters proposal.
That is, PAbAC inherits the security properties from
(Lewko and Waters, 2011). In addition, data confi-
dentiality preservation against malicious users and a
curious cloud provider is ensured based on the secu-
rity of our proposed access control scheme detailed in
the Section 6.4 and the security level of the applied
encryption scheme (c.f. Lemma 1).
Lemma 1. Unauthorized users cannot decrypt the en-
crypted data.
Proof. The proof of this lemma is equivalent to the
security of the data decryption algorithm. The cor-
rectness of our decryption algorithm is as follows:
A user can decrypt data if and only if it has a match-
ing set of attributes. In fact, access structure ψ (and
hence matrix A) is constructed if and only if there ex-
ists a set of rows A
i
in A, and linear constants c
i
∈ Z
N
such that
∑
i
c
i
A
i
= [1, 0,· ·· , 0].
We note that
C
1,i
ˆe(L,C
3,i
)
ˆe(LK
i
,C
2,i
)
(15)
=
ˆe(g
1
,g
1
)
λ
i
ˆe(g
1
t
,g
1
p
i
) ˆe(g
1
t
,g
1
w
i
) ˆe(g
1
t
,u
i
p
i
)
ˆe(u
i
t
,g
1
p
i
) ˆe(g
1
t
,g
1
p
i
)
(16)
Thus
∏
i
( ˆe(g
1
,g
1
)
λ
i
ˆe(g
1
,g
1
)
tw
i
)
c
i
= ˆe(g
1
,g
1
)
s
(17)
We note that Equation (17) holds because λ
i
=
~
A
i
·~v, w
i
=
~
A
i
·
~
τ, where ~v · [1,0, ·· · , 0] = s and
~
τ ·
[1,0, ·· · , 0] = 0. In the sequel, an authorized user can
obtain the data D
F
as follows:
D
F
= C
0
/ ˆe(g
1
,g
1
)
s
(18)
For an unauthorized user who does not possess the
secret keys related to the set of attributes required for
satisfying the access policy, it is impossible to com-
pute
∑
i
c
i
~
A
i
= [1,0,··· ,0] (Lewko and Waters, 2011).
Thus, ˆe(g
1
,g
1
)
s
cannot be calculated and the adver-
sary cannot recover the data file D
F
.
6.3 Privacy
Based on an attribute based signature scheme, PAbAC
ensures users’ privacy against curious cloud provider.
In our proposed scheme, the requesting data user has
to authenticate with the cloud provider. As such, (U)
has to sign a message received from the cloud service
provider with respect to the access structure defined
by the data owner. The CSP is responsible for verify-
ing the user’s access rights without knowing neither
his identity nor the attributes used to sign the mes-
sage. But, beyond the ABS properties, our PAbAC
scheme ensures the protection of the users identities’
( non traceability property). In fact, the ABE scheme
used does not reveal the encryptor identity neither
the users’ attributes used in the backup phase. The
PAbAC inherits the non traceability property from the
Lewko encryption scheme (Lewko and Waters, 2011).
Theorem 2. PAbAC signature scheme is a privacy
preserving signature.
Proof. The PAbAC signature scheme does not reveal
neither the identity of the signer nor the set of at-
tributes used in the signing. Our signature scheme
requires that the identity of the signer remains anony-
mous. Thus, PAbAC ensures that a signature does not
reveal more information other than what can be al-
ready inferred from the signing predicate itself. The
demonstration of this state is derived from the follow-
ing lemmas.
Lemma 2. PAbAC protects user’s anonymity
Proof. In the authentication procedure, the user has
to sign a random message received from the CSP.
Based on the signature scheme introduced in PAbAC,
the user signs the message using his private keys
which have already been randomized. Thus, the gen-
erated signature does not reveal the attributes used
neither the user’s private keys. Based on the hard-
ness of the Computational Diffie Hellman problem
(CDH), the CSP can not deduce the user’s private
keys related to the used attributes from the signature
σ = (x
1
,· ·· , x
n
,σ
1
,σ
2
) received.
In addition, let us consider a curious cloud provider
adversary that chooses a message m, a signing policy
and two requesting users with two, possibly different,
sets of attributes with the condition that both sets have
to satisfy the signing policy. The adversary gets a sig-
nature by either signer and wins if it correctly guesses
the signer. The curious provider has a negligible ad-
vantage to win the previous game. That is, the PAbAC
signature scheme is based on the randomization of the
signer secret keys.
Lemma 3. PAbAC’s signature scheme is unlinkable
SECRYPT 2016 - International Conference on Security and Cryptography
142

Proof. Let us consider that a curious cloud provider
aims to deduce identifying information about a re-
questing user by running different authentication ses-
sions. In the PAbAC sign algorithm, the user ran-
domises the attributes’ secret keys received from the
attributes authorities as follows:
K
0
= Kh
t
0
(19)
L
0
= Lg
1
t
0
(20)
K
0
i
= K
i
u
i
t
0
∀i ∈ S
U
(21)
Then, in every authentication session, the user gen-
erates a new signature σ = (x
1
,· ·· , x
n
,σ
1
,σ
2
) thanks
to the selected random value t
0
. Moreover, the CSP
sends a random value m which consists of the cloud
provider identity concatenated with the current time
(i.e. m is assumed to be different for each authen-
tication session). As such, while authenticating the
same user based on different authentication sessions,
a curious cloud service provider cannot identify the
requesting user.
6.4 Access Control to Data
PAbAC introduces two-level access control model
that combines the authentication of the requesting
users and the attribute based decryption algorithm. In
the following, we demonstrate that our PAbAC access
control enforcement is resistant against both mali-
cious data users and a curious cloud service provider.
Theorem 3. Authorized users can successfully au-
thenticate and decrypt enciphered data files.
We recall that cloud users have to collect their cer-
tified attributes and the related secret keys from at-
tribute authorities AAs. As such, in PAbAC, only
users, having valid private keys related to their at-
tributes, are able to access data stored in the cloud
while successfully authentication with the cloud
server. This is due to the correctness of our encryp-
tion and signature algorithms and the compliance of
the unforgeability property of the PAbAC signature
scheme inherited from (Waters, 2005).
Lemma 4. Data Decryption Correctness.
Proof. After receiving his attributes’ secret keys
{sk
S
j
}, the authorized user first computes:
C
1,i
ˆe(L,C
3,i
)
ˆe(LK
i
,C
2,i
)
= ( ˆe(g
1
,g
1
)
λ
i
ˆe(g
1
,g
1
)
tw
i
)
c
i
(22)
Then, he computes the constants c
i
∈ Z
N
such that
∑
i
c
i
·
~
A
i
= [1,0,··· ,0]. Then, ˆe(g
1
,g
1
)
s
could be ob-
tained as follows:
∏
i
( ˆe(g
1
,g
1
)
λ
i
ˆe(g
1
,g
1
)
tw
i
)
c
i
(23)
= ˆe(g
1
,g
1
)
∑
i
λ
i
c
i
ˆe(g
1
,g
1
)
∑
i
tw
i
c
i
= ˆe(g
1
,g
1
)
s
(24)
Note that λ
i
=
~
A
i
·~v where ~v = [s, v
2
,· ·· , v
n
] and w
i
=
~
A
i
·
~
τ such as
~
τ = [0,τ
2
,· ·· , τ
n
]. Consequently, we note
that
∑
i
λ
i
c
i
= s and
∑
tw
i
c
i
= 0.
Afterwards, the user can recover the data file D
F
as
follows:
D
F
= C
0
/ ˆe(g
1
,g
1
)
s
Lemma 5. Data signature correctness
Proof. When an authorized user wants to access out-
sourced data, he has to provide a correct signature,
with respect to the access policy defined by the data
owner, that can be verified by the CSP in an anony-
mous way. If σ = (x
1
,· ·· , x
l
,σ
1
,σ
2
) is a valid signa-
ture of the message m for the predicate ψ, then
σ
1
= zK
0
g
m
r (25)
= g
1
mr
h
t+t
0
g
1
α
n
∏
i=1
(u
i
(t+t
0
)
)
y
i
(26)
Thus
ˆe(g
1
,σ
1
) = ˆe(g
1
,g
1
mr
h
t+t
0
g
1
α
n
∏
i=1
(u
i
(t+t
0
)
)
y
i
) (27)
= pk
A
ˆe(g
1
,g
1
r
)
m
ˆe(g
1
,h
t+t
0
)
n
∏
i=1
ˆe(g
1
,u
i
(t+t
0
)
)
y
i
)
(28)
= pk
A
ˆe(g
1
,σ
2
)
m
n
∏
i=1
ˆe(x
i
,h
µ
i
u
i
) (29)
Note that µ
i
=
∑
l
j=1
β
j
A
i, j
, the last equality is obtained
by:
n
∑
i=1
µ
i
y
i
t = t
n
∑
i=1
µ
i
y
i
= t.1 = t (30)
Theorem 4. Unauthorized entities are unable to ac-
cess the outsourced data files
Lemma 6. PAbAC is secure against the collusion at-
tack.
Proof. We recall that the unforgeability property en-
sures that even if requesting users collude and com-
bine their attributes together, they cannot forge a sig-
nature that opens to a signer whose attributes do
not satisfy the access policy. It also covers non-
frameability and ensures that even if requesting users
collude, they cannot frame a user who did not produce
the signature. Similarly, malicious users cannot col-
lude to decipher an encrypted data file if the attributes
of each individual user do not satisfy the access pol-
icy, defined by the data owner.
PAbAC: A Privacy Preserving Attribute based Framework for Fine Grained Access Control in Clouds
143
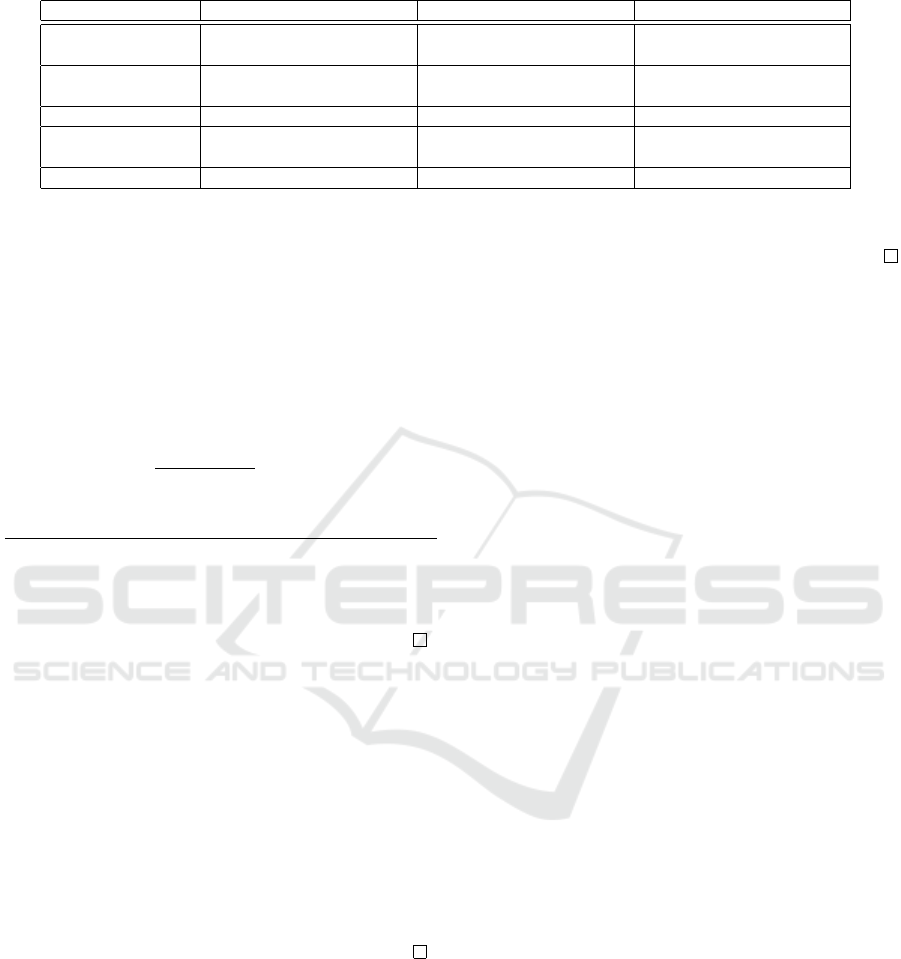
Table 2: Performances Comparison for Different Access Control Mechanisms in Cloud Data Storage Environments.
Scheme Data Owner Comp. CSP Comp. User comp.
(Zhao et al., 2011) E + (2n + 1)E
1
τ
P
(3 + 2n) + (2nl + 1)E
1
(2 + 3n + 2nl)E
1
+ (2n +
1)τ
P
+ (n + 1)E
(Ruj et al., 2012) 3nE
1
+ (2n + 1)E + τ
P
τ
P
(3 + 2n) + (2nl + 1)E
1
(2 + 3n + 2nl)E
1
+ 2nτ
P
+
nE
(Ruj et al., 2011) 3nE
1
+ (2n + 1)E + τ
P
−− 2nτ
P
+ nE
(Ruj et al., 2014) 3nE
1
+ (2n + 1)E + τ
P
τ
P
(3 + 2n) + (2nl + 1)E
1
(2 + 3n + 2nl)E
1
+ 2nτ
P
+
nE
PAbAC (n + 1)E + 4nE
1
+ τ
P
(2 + n)τ
P
+ (n + 1)E
1
2(n + 1)E
1
+ 2nτ
P
+ nE
Let us consider two malicious users U
A
and U
B
hav-
ing each a set of attributes X
A
and X
B
such as X
A
∪ X
B
satisfy the access structure. Suppose that U
A
gets
sk
S
1
= (K
1
,L
1
,K
i
1
) = (g
1
α
·h
t
1
,g
1
t
1
,u
i
1
t
1
) and U
B
gets
sk
S
2
= (K
2
,L
2
,K
i
2
) = (g
1
α
· h
t
2
,g
1
t
2
,u
i
2
t
2
). The users
collude to create a valid set of attributes and derive a
secret key sk
S
1∪2
= sk
S
1
∪ sk
S
2
from the combination
of the two user’s keys. Then, the colluded malicious
users try to decrypt the data as follows:
C
1,i
ˆe(L,C
3,i
)
ˆe(LK
i
,C
2,i
)
= (31)
ˆe(g
1
,g
1
)
λ
i
ˆe(g
1
t
1
+t
2
,g
1
p
i
) ˆe(g
1
t
1
+t
2
,g
1
w
i
) ˆe(g
1
t
1
+t
2
,u
1
p
i
)
ˆe(u
i
1
t
1
u
i
2
t
2
,g
1
p
i
) ˆe(g
1
t
1
+t
2
,g
1
p
i
)
(32)
Afterwards, the equation (12) cannot be resolved as
detailed in (32). Thus, the malicious users can not
recover the original data.
Lemma 7. The CSP is unable to access the encrypted
data files
Proof. The CSP cannot decipher encrypted data be-
cause it does not possess the secret keys {sk
S
j
}, re-
quired for satisfying the access policy defined by the
data owner. Even if the cloud provider colludes with
other unauthorized users, it cannot decrypt data, since
the PAbAC scheme is collusion resistant as detailed
in Section 6.4. Moreover, we suppose that the at-
tribute authorities AAs are not hosted by the CSP.
Thus, even if some attribute authorities are compro-
mised, the CSP cannot decipher data.
Lemma 8. PAbAC is resistant to replay attacks.
Proof. In our proposed PAbAC signature scheme, the
message m, sent by the CSP to the requesting user,
is assumed to be different in each authentication ses-
sion (i.e; m presents the cloud provider’s identity con-
catenated with the current time). In fact, for two
different authentication sessions α and β, the CSP
produces two different messages m
α
and m
β
respec-
tively. Consequently, a malicious user cannot gen-
erate a valid signature if he attempts a replay attack
based on collected data from two different authenti-
cation sessions.
7 PERFORMANCE ANALYSIS
In this section, we present the computation and stor-
age complexities of the PAbAC protocol at both the
client and cloud provider sides. For this purpose,
we are interested by the computations performed at
the data owner side in order to execute the STORE
procedure. Moreover, we will consider the compu-
tation cost related to the execution of the BACKUP
procedure by both the user (U) and the cloud service
provider (CSP).
In the following, we denote by:
• E
1
: exponentiation in G
1
• E : exponentiation in G
T
• τ
P
: computation of a pairing function ˆe
Table 2 details the performance comparison with
most closely related data sharing schemes in cloud
environments.
The STORE procedure consists of performing the
encryption algorithm encdata. During this proce-
dure, the data owner has to encrypt the data file.
As such, he calculates one pairing function ˆe(g
1
,g
1
)
and nE exponentiations in G to compute each of C
1,i
where n is the number of attributes. In addition, the
data owner executes 4n exponentiations in G
1
to cal-
culate C
2,i
and C
3,i
.
The BACKUP procedure is made up three algorithms
verif executed by the CSP and sign and decdata
runned by the data user (U). The user first signs a ran-
dom message in order to authenticate with the cloud.
To sign the message, the user performs 2(n+1) expo-
nentiations in G
1
. Then, this latter executes 2n pairing
to calculate ˆe(L),C
3,i
) and ˆe(K
i
·L,C
2,i
) to decrypt the
data file. In the verification phase, the CSP executes
the verif algorithm. As such, the cloud provider
performs (n +2) pairing functions’ computations and
n + 1 exponentiations in G
1
.
SECRYPT 2016 - International Conference on Security and Cryptography
144

The existent access control schemes (Ruj et al., 2012),
(Ruj et al., 2011), (Ruj et al., 2014) are based on
the Lewko’s decentralized attribute based encryption
scheme (Lewko and Waters, 2011). During the en-
cryption phase, the data owner has to perform one
pairing function ˆe(g
1
,g
1
) and 2n exponentiations in
G
T
to calculate each of C
1,i
. In addition, to calculate
C
2,i
and C
3,i
, the data owner performs 3n in G
1
. In the
data decryption phase, the data user performs n expo-
nentiations in G
T
and 2n pairing functions.
The zhao et al.’s proposal (Zhao et al., 2011) is
based on the use of the CP-ABE scheme proposed
by Bethencourt et al. (Bethencourt et al., 2007).
To encrypt the data file, the data owner performs
(2n + 1) exponentiations in G
1
and one exponentia-
tion in G
T
. The user while decrypting data performs
n + 1 exponentiations in G
T
and 2n + 1 pairing func-
tions. The proposals (Ruj et al., 2012),(Zhao et al.,
2011), (Ruj et al., 2014) are based on the use of the
attribute based signature scheme proposed by (Maji
et al., 2011). In order to sign the message, the user
performs 2 + 3n + 2nl exponentiations in G
1
, where
n is the number of rows of the access matrix A and l
presents the number of columns of A. In the verifi-
cation phase, the CSP has to perform 3 + 2n pairing
function and 2nl + 1 exponentiations in G
1
.
8 CONCLUSIONS
The growing need for secure cloud sharing services
and the attractive properties of the Attribute based
Cryptography lead us to combine them, thus, defining
an innovative solution to the data outsourcing security
and efficiency issues.
In this paper, we design a privacy preserving attribute
based framework for fine grained access control, for
dynamic groups in untrusted cloud storage environ-
ments. Our approach ensures the confidentiality of
outsourced data in public untrusted cloud servers and
defines efficient data sharing in dynamic groups. That
is, flexible access control policies are enforced among
users belonging to separate groups with different priv-
ileges. Our theoretical performances analysis shows
the efficiency of PAbAC in scalable data sharing,
while considering the impact of the cryptographic op-
erations at both the client and the cloud provider side.
ACKNOWLEDGEMENTS
This work is a part of the MOBIDOC project achieved
under the PASRI program, funded by the European
Union and administered by the ANPR.
REFERENCES
Health Insurance Portability and Accountability Act
(HIPAA). https://www.hipaa.com/about/.
Beimel, A. (1996). Secure schemes for secret sharing and
key distribution. PhD thesis, Technion-Israel Institute
of technology, Faculty of computer science.
Benaloh, J., Chase, M., Horvitz, E., and Lauter, K. (2009).
Patient controlled encryption: ensuring privacy of
electronic medical records. In The 2009 ACM work-
shop on Cloud computing security, pages 103–114.
ACM.
Bethencourt, J., Sahai, A., and Waters, B. (2007).
Ciphertext-policy attribute-based encryption. In IEEE
Symposium on Security and Privacy, 2007., pages
321–334.
Bobba, R., Fatemieh, O., Khan, F., Gunter, C., Khurana,
H., et al. (2006). Using attribute-based access con-
trol to enable attribute-based messaging. In The 22nd
Annual Computer Security Applications Conference,
pages 403–413. IEEE.
Chaum, D. and Van Heyst, E. (1991). Group signatures. In
Advances in CryptologyEUROCRYPT91, pages 257–
265. Springer.
Di Vimercati, S. D. C., Foresti, S., Jajodia, S., Paraboschi,
S., Pelosi, G., and Samarati, P. (2010a). Encryption-
based policy enforcement for cloud storage. In Dis-
tributed Computing Systems Workshops (ICDCSW),
2010 IEEE 30th International Conference on, pages
42–51. IEEE.
Di Vimercati, S. D. C., Foresti, S., Jajodia, S., Paraboschi,
S., and Samarati, P. (2007). Over-encryption: man-
agement of access control evolution on outsourced
data. In Proceedings of the 33rd international confer-
ence on Very large data bases, pages 123–134. VLDB
endowment.
Di Vimercati, S. D. C., Foresti, S., Livraga, G., and Sama-
rati, P. (2015). Selective and private access to out-
sourced data centers. In Handbook on Data Centers,
pages 997–1027. Springer.
Di Vimercati, S. D. C. D., Foresti, S., Jajodia, S., Para-
boschi, S., and Samarati, P. (2010b). Encryption poli-
cies for regulating access to outsourced data. ACM
Transactions on Database Systems (TODS), 35(2):12.
El Kaafarani, A., Chen, L., Ghadafi, E., and Davenport,
J. (2014a). Attribute-based signatures with user-
controlled linkability. In Cryptology and Network Se-
curity, pages 256–269. Springer.
El Kaafarani, A., Ghadafi, E., and Khader, D. (2014b).
Decentralized traceable attribute-based signatures. In
Topics in Cryptology–CT-RSA 2014, pages 327–348.
Springer.
Frikken, K. B., Li, J., and Atallah, M. J. (2006). Trust ne-
gotiation with hidden credentials, hidden policies, and
policy cycles. In NDSS. Citeseer.
Ghadafi, E. (2015). Stronger security notions for decen-
tralized traceable attribute-based signatures and more
efficient constructions. In Topics in Cryptology—CT-
RSA 2015, pages 391–409. Springer.
PAbAC: A Privacy Preserving Attribute based Framework for Fine Grained Access Control in Clouds
145

Goyal, V., Pandey, O., Sahai, A., and Waters, B. (2006).
Attribute-based encryption for fine-grained access
control of encrypted data. In The 13th ACM con-
ference on Computer and communications security,
pages 89–98.
Horv
´
ath, M. (2015). Attribute-based encryption optimized
for cloud computing. In SOFSEM 2015: Theory
and Practice of Computer Science, pages 566–577.
Springer.
Horwitz, J. and Lynn, B. (2002). Toward hierarchical
identity-based encryption. In Advances in Cryptolo-
gyEUROCRYPT 2002, pages 466–481. Springer.
Hur, J. and Noh, D. K. (2011). Attribute-based access con-
trol with efficient revocation in data outsourcing sys-
tems. IEEE Transactions on Parallel and Distributed
Systems, 22(7):1214–1221.
Jahid, S., Mittal, P., and Borisov, N. (2011). Easier:
Encryption-based access control in social networks
with efficient revocation. In The 6th ACM Symposium
on Information, Computer and Communications Se-
curity, pages 411–415. ACM.
Kaaniche, N., Boudguiga, A., and Laurent, M. (2013). Id
based cryptography for cloud data storage. In 2013
IEEE Sixth International Conference on Cloud Com-
puting, pages 375–382. IEEE.
Kaaniche, N., Laurent, M., and El Barbori, M. (2014).
Cloudasec: A novel publickey based framework to
handle data sharing security in clouds. In 11th IEEE
International Conference on Security and Cryptogra-
phy(Secrypt).
Karchmer, M. and Wigderson, A. (1993). On span pro-
grams. In Structure in Complexity Theory Conference,
pages 102–111.
Lewko, A. and Waters, B. (2011). Decentralizing attribute-
based encryption. In Advances in Cryptology–
EUROCRYPT 2011, pages 568–588. Springer.
Maji, H. K., Prabhakaran, M., and Rosulek, M. (2011).
Attribute-based signatures. In Topics in Cryptology–
CT-RSA 2011, pages 376–392. Springer.
Okamoto, T. and Takashima, K. (2013). Decen-
tralized attribute-based signatures. In Public-Key
Cryptography–PKC 2013, pages 125–142. Springer.
Raykova, M., Zhao, H., and Bellovin, S. (2012). Privacy
enhanced access control for outsourced data sharing.
In Financial Cryptography and Data Security, volume
7397, pages 223–238.
Rivest, R. L., Shamir, A., and Tauman, Y. (2001). How to
leak a secret. In Advances in CryptologyASIACRYPT
2001, pages 552–565. Springer.
Ruj, S., Nayak, A., and Stojmenovic, I. (2011). Dacc: Dis-
tributed access control in clouds. In IEEE 10th Inter-
national Conference on Trust, Security and Privacy in
Computing and Communications (TrustCom), pages
91–98.
Ruj, S., Stojmenovic, M., and Nayak, A. (2012). Privacy
preserving access control with authentication for se-
curing data in clouds. In The 12th IEEE/ACM Inter-
national Symposium on Cluster, Cloud and Grid Com-
puting (CCGrid), 2012, pages 556–563. IEEE.
Ruj, S., Stojmenovic, M., and Nayak, A. (2014). Decentral-
ized access control with anonymous authentication of
data stored in clouds. IEEE Transactions on Parallel
and Distributed Systems, 25(2):384–394.
Sahai, A. and Waters, B. (2005). Fuzzy identity-based
encryption. In EUROCRYPT 2005, pages 457–473.
Springer.
Wan, Z., Liu, J. E., and Deng, R. H. (2012). Hasbe: a hierar-
chical attribute-based solution for flexible and scalable
access control in cloud computing. IEEE Transactions
on Information Forensics and Security, 7(2):743–754.
Wang, G., Liu, Q., and Wu, J. (2010). Hierarchical attribute-
based encryption for fine-grained access control in
cloud storage services. In The 17th ACM conference
on Computer and communications security, pages
735–737. ACM.
Wang, W., Li, Z., Owens, R., and Bhargava, B. (2009). Se-
cure and efficient access to outsourced data. In The
2009 ACM workshop on Cloud computing security,
pages 55–66. ACM.
Waters, B. (2005). Efficient identity-based encryption with-
out random oracles. In Advances in Cryptology–
EUROCRYPT 2005, pages 114–127. Springer.
Yu, S., Wang, C., Ren, K., and Lou, W. (2010a). Achieving
secure, scalable, and fine-grained data access control
in cloud computing. In INFOCOM IEEE Proceedings
2010, pages 1–9.
Yu, S., Wang, C., Ren, K., and Lou, W. (2010b). Attribute
based data sharing with attribute revocation. In The
5th ACM Symposium on Information, Computer and
Communications Security, pages 261–270.
Zhao, F., Nishide, T., and Sakurai, K. (2011). Realizing
fine-grained and flexible access control to outsourced
data with attribute-based cryptosystems. In Informa-
tion Security Practice and Experience, pages 83–97.
Springer.
Zunnurhain, K. (2012). Fapa: a model to prevent flooding
attacks in clouds. In The 50th Annual Southeast Re-
gional Conference, pages 395–396. ACM.
SECRYPT 2016 - International Conference on Security and Cryptography
146
