
Reducing Transmitted Bits in a Memoryless RFID Anti-collision Protocol
Nikola Cmiljanic, Hugo Landaluce, Asier Perallos and Laura Arjona
DeustoTech-Fundaci
´
on Deusto, Deusto Foundation, Av. Universidades 24, 48007, Bilbao, Spain
Keywords:
RFID, Anti-collision, Tag Identification, Window, Query Tree.
Abstract:
The use of Radio Frequency Identification (RFID) technologies is growing. RFID enables data to be collected
from many objects, for identification and other purposes. One of the main disadvantages in tag identification,
known as the tag collision problem, is becoming significant, since it leads to the increase in the number of
transmitted bits and identification time. The window methodology is created with the aim to manage the
number of transmitted bits by the tags. As a result, tags transmit exclusively the bits defined by the window
instead of sending their full ID value on every response. This paper presents a protocol with a standardized
window. The window size is transmitted as the exponent of power of 2. Simulations show that the proposed
solution with standarized window size reduces the number of bits transmitted by the reader, with respect to
other protocols using the window, which results in a lower number of total bits in the identification process.
1 INTRODUCTION
Radio Frequency Identification (RFID) is very popu-
lar, and it is experiencing a higher growth every day.
RFID is a technology that uses radio waves to auto-
matically identify people or objects. This technology
helps in many fields and provides information about
people, goods and products in transport. As opposed
to barcode, RFID does not require close handling, no
line of sight is required between the reader and the
object to be identified, and tags provide significantly
greater storage capacity. Those are the reasons why
RFID is increasingly present.
The main components of an RFID system are: a
reader and transponders (in advance tags) (Finken-
zeller, 2010). RFID uses radiofrequency waves in or-
der to automatically identify and track tags attached to
objects. The reader is the main component, which is
in charge of managing the identification process and
collecting data from the tags by using an antenna that
broadcasts radio waves. A tag is a small label which is
attached to an object that wants to be identified. The
reader sends out electromagnetic waves that the tag
antenna receives and backscatters with its ID, convert-
ing those waves into digital data.
Tags are categorized into: passive, active, and
semi passive. Passive tags are smaller and do not have
a power supply. They reflect the data received from
the reader to transmit their data. Active tags have an
integrated battery, which is used to provide voltage to
the chip and to transmit a longer distance. Semi pas-
sive tags use a battery only to power on the chip, so
the entire energy, which is received from the reader,
can be used for the transmission of data. Tags are
available in many shapes such as smart cards, coins,
keys, key fobs, clocks, and smart labels. RFID sys-
tems can also be classified according to the working
frequencies of the carrier signals: low frequency (LF)
125kHz-134kHz, high frequency (HF) 13.56Mhz, ul-
tra high frequency (UHF) 860-930 MHz, and super
high frequency (SHF). Depending on the frequency,
tags have various achievable ranges, from a few cm to
8 m (Finkenzeller, 2010).
The process of tag identification comprises a
reader interrogation and a tag response. One of the
main problems in RFID systems happens when multi-
ple tags are interrogated by the reader simultaneously
and they reflect their respective signals back to the
reader at the same time. As a result of this obstruction
there is a failed transmission called collision. These
collisions cause the reader to be unable to identify
tags successfully and rapidly. Thus, RFID obtains
low tag reading performance and a high waste of en-
ergy. To minimize the influence of the tag collision
problem, RFID readers use an anti-collision protocol.
Anti-collision protocols can be divided into three cat-
egories: Aloha-based protocols which are probabilis-
tic, tree-based protocols which are deterministic, and
hybrid protocols (Klair et al., 2010).
Aloha-based protocols (Wang et al., 2009; J. and
T., 2008), come from computer networks and they use
a random access strategy in order to identify tags.
152
Cmiljanic, N., Landaluce, H., Perallos, A. and Arjona, L.
Reducing Transmitted Bits in a Memoryless RFID Anti-collision Protocol.
DOI: 10.5220/0005963201520157
In Proceedings of the 13th International Joint Conference on e-Business and Telecommunications (ICETE 2016) - Volume 6: WINSYS, pages 152-157
ISBN: 978-989-758-196-0
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

They are probabilistic protocols because tags send
data in a randomly selected slot in a frame to reduce
the possibility of collision. Accordingly, it is not guar-
anteed that all the tags will be identified (Wang et al.,
2009). When a collision occurs the tag will be asked
to send its data later with a random time delay.
Tree-based protocols are also known as determin-
istic protocols because all the tags in the interroga-
tion zone will be read within certain time limits (Feng
et al., 2006). A group of collided tags should be sepa-
rated into subsets repeatedly until every tag in the in-
terrogation zone responds correctly. The total amount
of information transmitted between readers and tags
is usually higher than in Aloha based protocols (Klair
et al., 2010). Tree based protocols require tags to have
’sleeping’ capability, as tags are silenced after the pro-
cess of identification.
Hybrid protocols are created to avoid the problems
of Aloha and tree-based protocols (Wu et al., 2013).
Some advantages of hybrid protocols are that they can
achieve a higher slot efficiency than the other types. A
hybrid protocol consists principally of two combined
protocols: one is using randomized divisions in tree-
based algorithms, and another is using tree strategies
after a collision in Aloha-based algorithms.
Tags in the proposed window methodology (Lan-
daluce et al., 2013) can not locate the bit string repre-
senting the window size in the received command. In
this paper, the window standardization is performed.
The window is represented in a fixed size string of 3
bits. When tags receive a command, they can sepa-
rate the part of the reader query from the part of the
window size string.
The rest of the paper is organized as follows.
Section 2 presents the window methodology and de-
scribes three tree based protocols of the state of the
art. In section 3 the proposed Standardized Query
Window tree protocol (SQwT) is presented. Section
4 presents evaluation results and the comparison with
some state of the art protocols. Finally, Section 5 con-
cludes the whole paper.
2 RELATED WORK
Some basic terms are given before presenting the
most related tree based protocols:
• Query is a broadcast command sent by the reader.
This command consists of a prefix (binary string)
that the tags will compare with their ID. If tags’ ID
does do not match the query, the reader command
will be rejected. In case that tags’ ID matches the
query, a response will be transmitted according to
each protocol.
• Slot is the time interval which is intended to or-
ganize the responses from the tags. Three types
of slots can occur depending on the number of tag
responses received at the reader: idle slot, when
(upon reader request) no tag answers; collision
slot, when more than one tag respond to a reader
query, and the reader can not understand the re-
sponse; and success slot, when the reader success-
fully identifies a tag.
• Identification process is the period including all
the reader queries and tags responses. It consists
of a certain number of time slots needed by the
reader to identify the entire set of tags.
Here some of the most important tree based pro-
tocols are presented.
2.1 Query Tree Protocol
The Query Tree protocol (QT) is one of the most sig-
nificant tree based protocols (C. Law and Siu, 2000).
It is called memoryless protocol and it means that a
tag response depends on the current query but not
on the past history of the reader queries. QT tags
have the lowest hardware requirements because they
only compute a prefix-comparison operation between
a query and the tag ID. In each round the reader trans-
mits a query and the tags whose ID matches it, will
respond. In case that more than one tag respond, a
collision occurs and the reader will create two new
queries appending values 1 and 0 to the query. That
is, two new queries will be placed in a Last Imput
First Output stack (LIFO). If there is no answer upon
a query command, the reader knows that there is not
any tag with the required prefix and the query is re-
jected. When a prefix matches a tag’s ID, the tag
transmits the complete ID. By extending the prefixes
until only one tag’s ID matches, the algorithm can
identify the rest of the tags. The identification pro-
cess is completed when the stack is empty. QT tags
transmit the whole ID every time they match a query.
In case more than one tag responds, a collision oc-
curs. Accordingly, all tags that match the query prefix
transmit their full ID and a lot of bits are wasted upon
every collision.
2.2 Smart Tree Traversal Protocol
Smart Tree Traversal protocol (STT) (Pan and Wu,
2011) is created in order to reduce the number of col-
lisions in QT. STT is a tree based protocol with the
ability of self-learning. The reader in this protocol dy-
namically generates queries according to the ability to
recognize tag density and distribution. Depending on
Reducing Transmitted Bits in a Memoryless RFID Anti-collision Protocol
153
the result of the tag response, the reader calculates the
next query:
• Upon a collision, the reader appends x bits of 0’s
on the last transmitted query where x =r+w
col
-1,
r denotes the minimum increase, and w
col
is the
number of consecutive collisions slots.
• When an idle slot occurs, the reader decreases
the query length by the number of bits y, where
y=r+w
emp
-1, by which to decrease the query, and
w
emp
is the number of consecutive idles.
• Upon a success response, the reader visits the sy-
metric node if the query finishes with 0 or it re-
turns one level if it finishes with 1.
On every collision, the full tag response, apart from
the initial query bits, is wasted. In order to alleviate
this issue, the window methodology is presented.
2.3 Query Window Tree Protocol
Instead of transmitting the whole ID value from the
tags, every tag response is limited. The Query win-
dow Tree protocol (QwT) is presented in the literature
(Landaluce et al., 2013). This methodology is applied
to the QT protocol to control the number of transmit-
ted bits by tags. The number of collisions is decreased
by transforming potential collisions into partial suc-
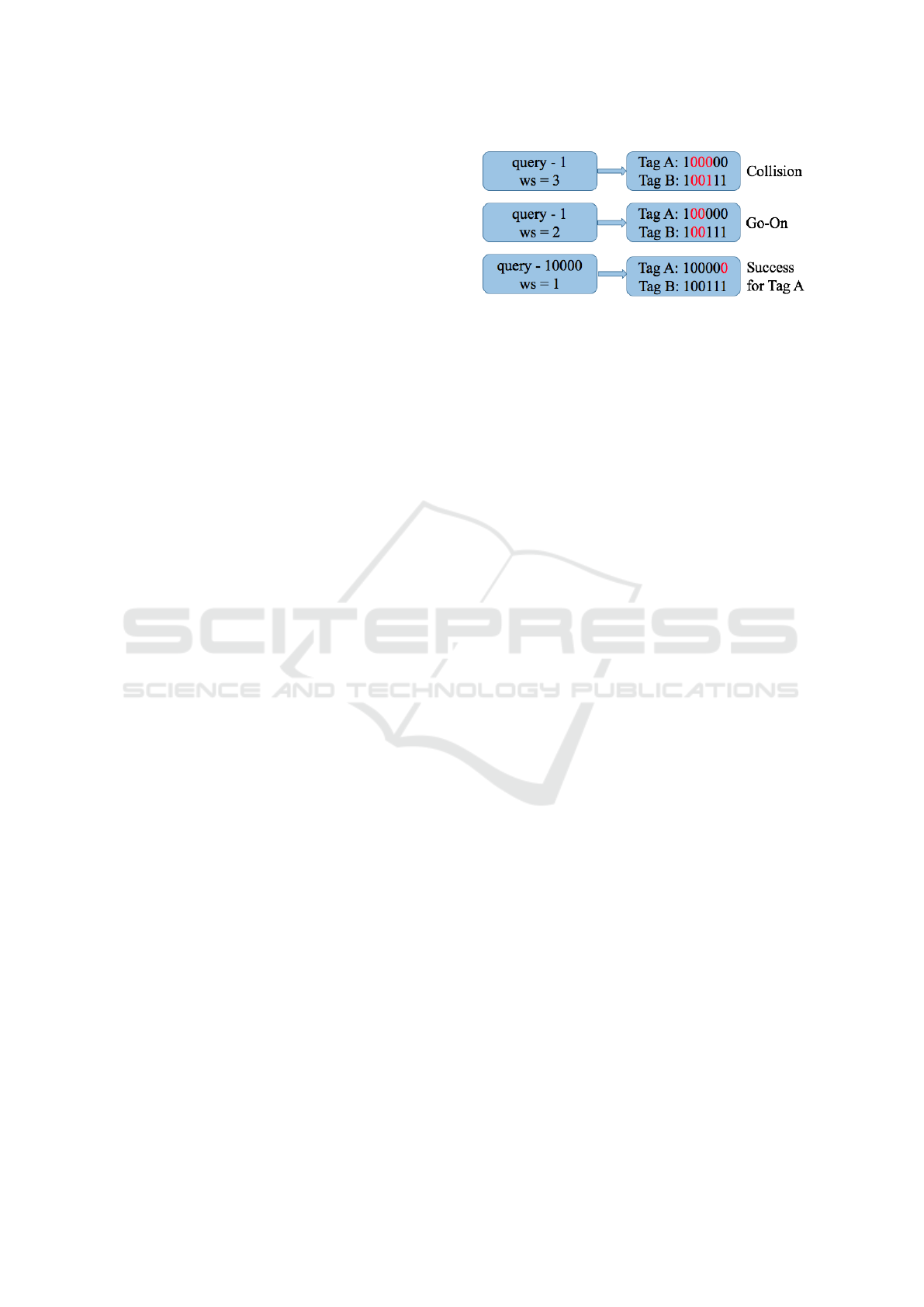
cesses called Go-On slots. The window is a bit-string
transmitted by the tags, instead of their full ID. If tags
match a reader query, they will synchronously trans-
mit the amount of bits of the ID specified by the win-
dow size, ws, instead of their full ID. This is shown
in Fig. 1. QwT uses cyclic redundancy check (CRC)
to differentiate between the type of tags’ responses,
which can be classified into four types:
• Idle slot: when no tag responds upon a reader
query. The reader rejects this query and contin-
ues with the identification process by sending the
next query from the stack.
• Collision slot: when more than one tag responds
the window to the query, but the CRC received
by the reader is not consistent. The reader
creates two new queries: [q
1
, q
2
. . . q
L
, 0] and
[q
1
, q
2
. . . q
L
, 1] where q
i
∈ [0, 1]. The reader trans-
mits the first generated query with unchanged ws
and stores the second one into the stack.
• Go-On slot: when at least one tag responds the
window and the reader can understand it. If the
ID is not complete L+ws<k, where L is the length
of the query and k the length of the tag ID. It is
assumed a Go-On slot and the reader continues to
interrogate tags with an updated query made from
the last received window and the former query.
Figure 1: Window synchronized answer.
• Success slot: when the reader successfully re-
ceives the remaining values of the ID. The reader
collects the complete ID and stores it in a
database. In this slot L+ws=k is met.
Using the proposed QwT, the reader in each interro-
gation round transmits a query of L bits and preselects
ws using the expression (1), where β is an adjustable
parameter (Landaluce et al., 2013).
f (L) = k(1 − e
−βL
), 0 < L ≤ k (1)
When the calculated ws is high, the reader command
needs a high number of bits to represent it. That leads
to a wastage of the reader bits. In order to reduce
the number of the reader bits this paper proposes the
standardization of the window methodology.
3 STANDARDIZED QUERY
WINDOW TREE PROTOCOL
The presented protocol proposes the standardized
window to restrict the number of bits transmitted by
the reader, reducing the total number of transmitted
bits. A decrease of the reader bits is achieved by
reducing the amount of the window size bits in the
reader command. The presented protocol has the abil-
ity to locate the bit string representing the window
size in the received command, differentiating it from
the query by using a fixed size at the end of the reader
command.
SQwT is also a memoryless protocol since the cur-
rent response of each tag only depends on the current
query and ws. Tags that match the reader prefix will
exclusively transmit ws bits.
A heuristic function which computes ws is given
in (1). An adequate value of β is 0.5 for the low-
est Go-On slots rate (Landaluce et al., 2013). After
calculating ws, the reader will choose the first higher
power of 2 value. The obtained value is the number of
bits that matching tags should transmit from the ID.
The reader calculates the number of bits that tags
must respond to a matching query. Instead of sending
WINSYS 2016 - International Conference on Wireless Networks and Mobile Systems
154
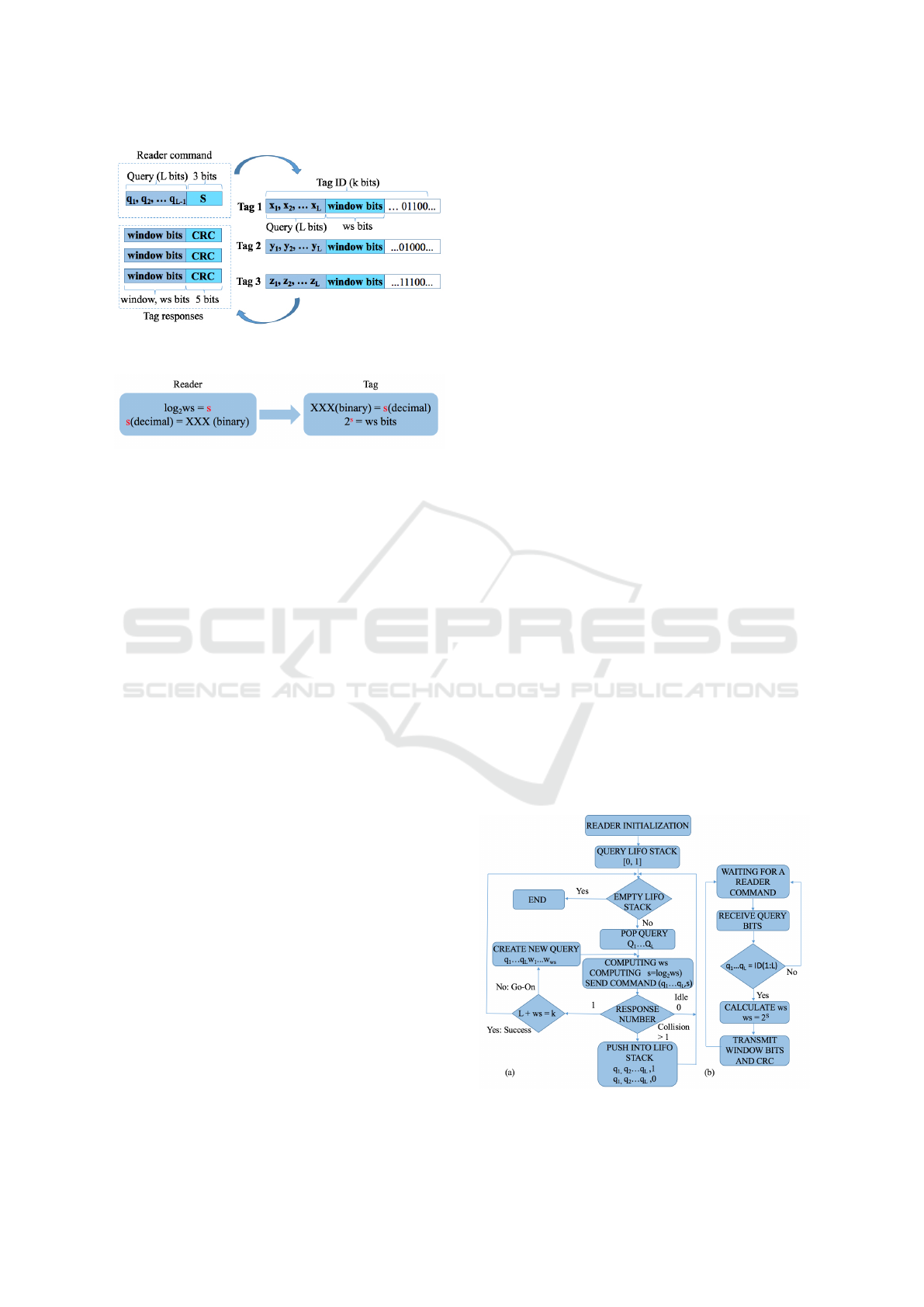
Figure 2: Format of the reader command and tag responses
of the SQwT protocol.
Figure 3: Converting WS between reader and tag.
ws bits, SQwT will transmit a new value s which is
presented in (2).
s = log
2
ws (2)
As shown in Fig.2, the reader interrogates tags with a
query [q
1
, q
2
. . . q
L
] and a fixed string s. All tags will
receive this broadcast message but only tags whose
ID matches the query will calculate s and respond to
the reader request. SQwT gives a constant place of 3
bits included in the reader command. It allows tags
to locate the amount of the window size string in the
received command. The matching tags calculate ws
by using the expression (3) and get the final value.
ws = 2
s
(3)
The process is depicted in Fig.3. E.g., if ws=128,
the reader, first uses (2) with result 7. This is codified
into the binary number 111. The reader transmits this
bit string attached to the predefined query. The ID
length of 128 bits is the most common in RFID (GS1
and EPCglobal, ). For this reason SQwT uses 3 bits in
the reader query for s. For longer IDs, a larger value
of s should be used, and a longer bit string would be
needed.
The reader and tag flow chart of SQwT are given
in Fig 4.(a) and (b). First, the reader initializes by
pushing two queries into a LIFO stack and the reader
pops the last pushed query. For the initial ws calcula-
tion, it uses ws=1. In other rounds, ws should be cal-
culated using (1) and the nearest power of 2 should be
chosen towards ∞. Subsequently, the reader obtains s
with (2) and codifies it with 3 bits. Once s is calcu-
lated, a new reader command including a query and s
will be transmitted to the tags. The reader awaits for
the tags’ answers. Tags receive the reader command
(see Fig. 4.b) and compare the query with their ID.
Matching tags will calculate ws using (3) and will re-
spond the remaining ws bits from bit L w
1
. . . w
ws
, and
a CRC. Depending on the type of response, the reader
will act as follows:
• Upon a collision the reader creates two new
queries: q
1
, q
2
. . . q
L
, 1 and q
1
, q
2
. . . q
L
, 0 and ws
is unchanged.
• For the cases when an empty window is received,
the transmitted query is rejected and another one
query is popped from the stack. The windows size
remains unchanged.
• In case the received CRC is positively checked,
the reader checks the expression L+ws=k, and if
it matches, the tag is successfully identified. A
new query is popped from the stack and textitws
is calculated using (1).
• In case detecting a Go-On (L+ws<k) slot,
the reader produces a new query attaching
w
1
, w
2
. . . w
ws
to the last transmitted query until it
receives the full ID value. The windows size is
calculated using (1).
This procedure sequences repeatedly until it gets the
empty stack.
An example of identification of six tags is depicted
in Fig.5 using QT and the proposed SQwT protocol.
The ID length k used is 8 bits and ws is computed
using exponential heuristic function with β=0.5. The
reader first sends the query (0). Tags A, B, C and D
respond with the whole ID value and a collision oc-
curs using QT protocol. The difference with SQwT
protocol is in the tag response. After matching query
(0) the same tags as in the QT protocol will trans-
mit but just with the first bits, defined by ws value.
The reader can receive a partially successful response
add it adds the bit ’0’ to the previous query forming
Figure 4: Flow chart of the proposed SQwT protocol: (a)
for reader, (b) for tags.
Reducing Transmitted Bits in a Memoryless RFID Anti-collision Protocol
155
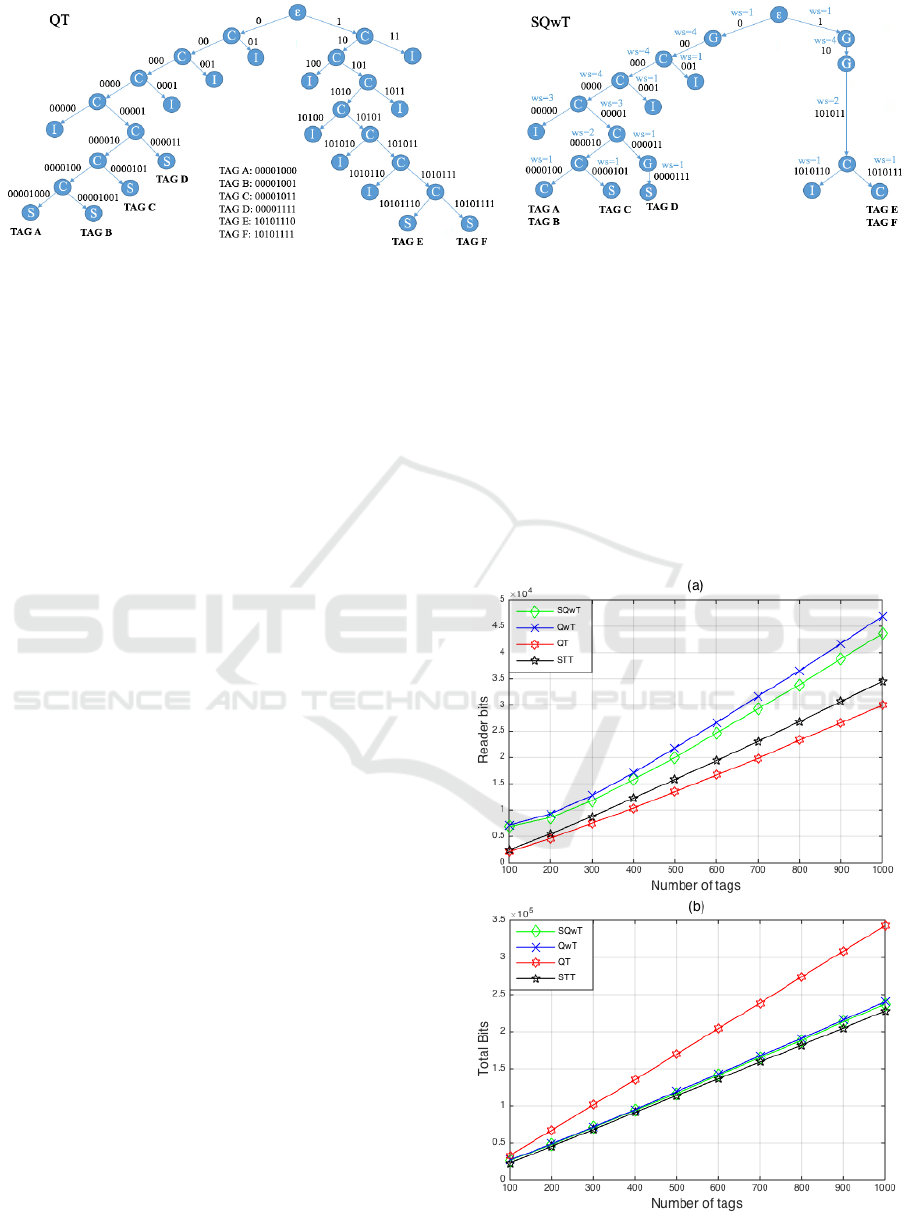
Figure 5: Example of the proposed SQwT and the QT protocol.
a new query (00) and it continues with the identifi-
cation proccess. In this case (1) calculates ws 4 bits.
Again four tags match the query (00) and transmit the
following 4 bits. In this round, the reader can not
understand the responses and collision occurs. The
following part of tree is the same in both protocols
because 3 collided slots will occur. Every time a col-
lision occurs the reader pushes into the stack two new
queries: [q
1
, q
2
. . . q
L
, 0] and [q
1
, q
2
. . . q
L
, 1]. The left
subtree under the 0 branch of both protocols is the
same untill transmitting query 0000100. QT proto-
col needs to make one more interrogation round be-
cause tags respond the whole ID values as opposed
to SQwT which transmits just the last bits, and tags
A and B can be identified. After this success slot,
the reader pops the next query and can identify Tag
C. The reader pops out a new query from the stack
(000011), resulting in the identification of tag D. QT
protocol needs two more slots in order to identify the
same number of tags. The right part of the tree is sig-
nificantly reduced in the SQwT protocol. After trans-
mitting the first query ’1’ from the right side of the
tree, two Go-On slots will occur. Afterwards, SQwT
pops the next query (101011) and detects a collision.
The last query created during the last collision results
in the identification of the remaining two tags: Tag
E and Tag F. Eventually, when the comparison of QT
and SQwT is analyzed, results show a lower number
of transmitted bits per tag, and a decrease of the num-
ber of collisions.
4 EXPERIMENTATION
This section presents the evaluation of the simulation
results of the presented SQwT with QT (C. Law and
Siu, 2000), QwT (Landaluce et al., 2013) and STT
(Pan and Wu, 2011). The simulations are executed
using MatLab R2014. The number of tags has been
varied from 100 to 1000. Simulations are averaged
over 100 times for accuracy in the results, and the
IDs are randomly generated for every iteration with
a length of 128 bits. CRC is assumed 5 bits. Table
1 shows the calculation of the number of transmitted
bits for the protocols used in the simulation.
Simulated results in Fig.6.a present the reader bits
used in the identification process. Presented results
show evidence of decreased reader bits for the pro-
posed SQwT protocol in the comparison with win-
dow based protocol, especially in dense tag environ-
ments. SQwT outperformed QwT in reader bits and
consumes total bits similar to STT. The total number
Figure 6: Performance of the SQwT: (a) reader bits, (b) total
bits.
WINSYS 2016 - International Conference on Wireless Networks and Mobile Systems
156

Table 1: Calculation of transmitted bits used in simulation.
Protocol Reader command Tag response
SQwT L + 3 ws +CRC
QwT L + blog
2
wsc + 1 ws +CRC
QT L k
STT L k − L
of bits transmitted between the reader and the tags
is shown in Fig.6.b. It is calculated as the number
of transmitted bits by the reader plus the number of
tag bits received on the reader side. Results indi-
cate that SQwT significantly outperformed QT in total
bits with the influence of the window methodology.
The results indicate that SQwT is a dexterity proto-
col, which using a standardized window, reduces the
number of transmitted reader bits used in the identifi-
cation process.
5 CONCLUSIONS AND FUTURE
WORK
A novel SQwT protocol for reducing the number of
reader bits is presented here. The standardized win-
dow methodology is proposed and the window size
is represented as a fixed string of 3 bits. The basic
approach is the tag ability to locate the bit string rep-
resenting the window size in the received command,
differentiating it from the query. It is achieved by giv-
ing a constant place of 3 bits included in the reader
command. Simulated results proved the dexterity of
SQwT and outperformed other window based solu-
tion since the number of transmitted reader bits are
significantly reduced. Future work will look at the
possibility of implementing SQwT to be adapted to
different ID distributions.
ACKNOWLEDGEMENTS
This work has been supported by the Spanish Min-
istry of Economy and Competitiveness under the iL-
ogisTICs project (TEC2013-45585-C2-2-R) and the
Basque Government under the UBITRACE project
(PC2013-71A)
REFERENCES
C. Law, K. L. and Siu, K. (2000). Efficient memoryless
protocol for tag identification. In Proceedings of the
4th International Workshop on Discrete Algorithms
and Methods for Mobile Computing and Communica-
tions,.
Feng, B., Li, J.-T., Guo, J.-B., and Ding, Z.-H. (2006). Id-
binary tree stack anticollision algorithm for RFID. In
11th IEEE Symposium on Computers and Communi-
cations, 2006. ISCC ’06. Proceedings., pages 207–
212.
Finkenzeller, K. (2010). RFID Handbook. Wiley.
GS1 and EPCglobal. ”GS1 EPC Tag Data Standard 1.6”
GS1, EPCglobal, Sept. 2011.
J., E. and T., L. (2008). Crc-16-based collision resolution
in EPCglobal Class1 Generation2 RFID systems. In
Proceedings of the International Conference on Wire-
less Information Networks and Systems, pages 61–65.
Klair, D., Chin, K.-W., and Raad, R. (2010). A survey and
tutorial of RFID anti-collision protocols. Communi-
cations Surveys Tutorials, IEEE, 12(3):400–421.
Landaluce, H., Perallos, A., and Zuazola, I. (2013). A fast
RFID identification protocol with low tag complexity.
IEEE Communications Letters, 17(9):1704–1706.
Pan, L. and Wu, H. (2011). Smart trend-traversal protocol
for RFID tag arbitration. IEEE Transactions on Wire-
less Communications, 10(11):3565–3569.
Wang, C., Daneshmand, M., Sohraby, K., and Li, B. (2009).
Performance analysis of RFID Generation-2 proto-
col. IEEE Transactions on Wireless Communications,
8(5):2592–2601.
Wu, H., Zeng, Y., Feng, J., and Gu, Y. (2013). Binary
tree slotted aloha for passive RFID tag anticollision.
IEEE Transactions on Parallel and Distributed Sys-
tems, 24(1):19–31.
Reducing Transmitted Bits in a Memoryless RFID Anti-collision Protocol
157
