
Analysis of Performance of the Routing Protocols Ad Hoc using
Random Waypoint Mobility Model Applied to an Urban Environment
Liliana Enciso, Pablo Quezada, José Fernandez, Byron Figueroa and Veronica Espinoza
Universidad Tecnica Particular de Loja, San Cayetano Alto, 1101608, Loja, Ecuador
Keywords: Ad-Hoc, AODV, DYMO, DSDV, DSR, MANET, NS2, OLSR, TraceGraph, ZRP.
Abstract: Mobile ad-Hoc Network (MANET) is a group of mobile nodes interconnected and dynamic. A routing
protocol is used to find the routes between the mobile nodes and facilitate the communication within the
network. The aim of the protocols is to establish a correct and efficient route between a pair of mobile nodes,
also it needs to be discovered and kept with a minimum consumption of bandwidth. This research work shows
the performance assessment of six routing protocols: Destination Sequenced Distance-Vector (DSDV),
Optimized Link State Routing (OLSR), Dynamic Source Routing Protocol (DSR), Ad Hoc On-Demand
Distance Vector (AODV), Zone Routing Protocol (ZRP), Dynamic MANET On-Demand (DYMO). The
evaluation was defined scenarios with 50, 90, 130, 170, 210 and 250 nodes and parameters such as: numbers
of generated packages , broadcast packages, delay of node to node. The simulations and visualization from
the results were executed in the network simulator NS2 version 2.34 and TraceGraph.
1 INTRODUCTION
Nowadays, the computer networks are within the
reach of all because of the Internet, it has generated
different types of networks within which are the
mobile networks Ad- Hoc o MANET (Mobile Ad-
Hoc Networks), which do not require a previous
infrastructure, it allows that two or more user have
mobile terminals that can make a network at any time
(Sangwan et al., 2013), (Anwar., 2008), (Sathish.,
2011).
A MANET network is a group of mobile nodes
that can communicate to each other through of
wireless, the nodes as are mobiles can move by a free
space, giving rise to different topologies in all
moment (Sangwan, Duhan and Dahiya, 2013),. It is
a dynamic topology due to outages in links, and to the
appearance of new links. This type of links has some
inconvenient than a conventional link does not show.
The topology of this type of links can change quickly
and unpredictably. Furthermore, it is possible to
occur variations in the nodes and links capabilities
such as: frequent errors in the transmission and lack
of safety due to the own features of the devices which
are part of this type of networks as restriction of
bandwidth and energy (by the use of batteries)
(Anwar et al., 2008). Finally, it is necessary to
emphasize that one of the main inconvenient of the
MANET network, is its security due to the different
features of this type of network, as wireless or the lack
of infrastructure that can control and handle the
network, which is susceptible to suffer attacks. For
this type of network, there are protocols of specific
routing because the existing ones for fixed networks
are no the adequate for them.
2 ROUTING PROTOCOL
The routing protocol are classified according their
features, the way more known is based in as a mobile
node process the information of control; for that
reason, there are two main types: the proactive
protocols which are basically an adaptation of the
vector distance protocols and link status of the wired
networks, and reactive protocols also called low
demand which were developed mainly for the
MANET networks. There are other type of protocols
which are called hybrids which keep a proactive
philosophy in local field and reactive at more global
level) (Vermani et al., 2012).
2.1 Proactive Protocols
The proactive protocols or the based in tables are
208
Enciso, L., Quezada, P., Fernandez, J., Figueroa, B. and Espinoza, V.
Analysis of Performance of the Routing Protocols Ad Hoc using Random Waypoint Mobility Model Applied to an Urban Environment.
In Proceedings of the 12th International Conference on Web Information Systems and Technologies (WEBIST 2016) - Volume 1, pages 208-213
ISBN: 978-989-758-186-1
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

those which keep the information about how to reach
at all destinations of the network (nodes) (Vermani,
Sharma and Yadav, 2012). This information is stored
in tables which are updated periodically when there
are modifications in the topology of the network
(Kumar and Kumar, 2012). The difference among the
protocols of this type is the way in the table are
updated, the quantity of tables used, the information
of each table and the way to find information. The
protocols more important in this type are:
DSDV (Destination Sequenced Distance-Vector)
It is a unicast proactive protocol adapted from the RIP
traditional, its main aim is to avoid the loops
problems in the update of the routing tables. For that
reason, it adds a new field in the tables, the sequence
number that allows distinguish between an old table
and a new one (Vermani, Sharma and Yadav, 2012),
(Jain, Gaur and Upadhyay, 2014). DSDV applies an
algorithm based in the distance vector, this means that
keep the tables with all its accessible destinations
together with the following leap, the metric and a
number of sequence of the input in the generated table
by the destination node. The tables are sent with
diffusion messages on a regular basis or when there is
a significant difference of the network topology. A
route is considered better than other if it has a
sequence number major or in case of a tie, if the
distance at the destination is minor. When a B node
detects that the route to certain destination D is lost,
overflow the networks with an updated of that input
in which is incremented the sequence number in one
and the distance is marked as infinite (Jain, Gaur and
Upadhyay, 2014). When an A node receive this
message, it incorporates to its table the updated of the
input into D through B always that there was not an
input better to reach D. To achieve certain
consistency in the routing table of each node by
changing the network topology, the updates must be
frequents and quick enough and therefore each node
can have a realistic vision of the network at a specific
time (Jain, Gaur and Upadhyay, 2014).
OLSR (Optimized Link State Routing)
This protocol is an optimizing algorithm of state of
adapted classic link to the requirements of a LAN
wireless. The key concept that is used in the protocol
is the MultiPoint Relays (MPR) (Ashish, Singh and
Kumar, 2010). MPR are nodes which send messages
into forward during the overflow process. This
technique substantively decrease the overload of
messages in comparison with a mechanism of classic
overflow, where each node retransmits every message
when is receipted the first copy of the message
(Kumar and Kumar, 2012). In OLSR, the information
of state link is generated only by the chosen nodes as
MPR (Ashish, Singh and Kumar, 2010). For that
reason, a second optimization is obtained decreasing
the minimum number of control messages
overflowed in the network. As third optimization, a
MPR node can opt only inform links between each
other and their selectors MPR. Therefore, as it is
contrary to the state algorithm of classic link, partial
information of state of link is distributed in the
network. This information is used to the calculus of
the route. OLSR offers optima routes (in terms of
number of leaps). The protocol is particularly
adequate to big and dense networks (Jain, Gaur and
Upadhyay, 2014).
2.2 Reactive Protocols
The routing reactive protocols are those that form the
routes on-demand that means in the moment that a
root node needs to send a message into a destination
node are created the routes from the origin to their
destination. With this type of protocols is optimized
the use of resources of bandwidth and the use of
battery and it is penalized the latency in finding the
route (Kumar and Kumar, 2012).
DSR (Dynamic Source Routing Protocol)
The reactive protocol DSR (Dynamic Source Routing
Protocol) is a protocol created especially for Ad-Hoc
networks, it only sends information when is
necessary, saving network energy, releasing
bandwidth and saving battery. Furthermore, DSR
incorporates a mechanism to avoid the creation of
loops. It is compatible with IPv6 (Kumar and Kumar,
2012). As counterpart, there is the initial latency at
discover a route, and it is a protocol based on the
source, the package header has increasing while it is
moving by the nodes; as a consequence, valuable
bandwidth is lost. This protocol can be structured in
two mechanics: of route discovery and the
maintenance of it. The first make the search of the
route and has the RREQ (Route Request) packages to
look for the route if it is not available in the routing
table and RREP (Route Reply) which answers at
RREQ on the discovery of a route. The second
mechanism has the RRER (Route Error), which show
a falling route and the ACK, which periodically make
the maintenance of the route (Ashish, Singh and
Kumar, 2010).
AODV (Ad Hoc On-Demand Distance Vector)
This protocol allows the dynamic routing multi-hop
among mobile nodes which take part in the setting
and maintenance of Ad-Hoc network (Jain, Gaur and
Upadhyay, 2014), (Kumar and Kumar, 2012). AODV
Analysis of Performance of the Routing Protocols Ad Hoc using Random Waypoint Mobility Model Applied to an Urban Environment
209

allows to the mobile nodes obtain quickly routes for
new destinations without require those routes be kept
in absence of active communication (Sangwan,
Duhan and Dahiya, 2013). Therefore, it makes
possible that the mobile nodes respond before the loss
of link and changes in the topology in a quick and
efficient way, invalidating the routes which use the
loss link in the affected nodes (Anwar, Azad, Rahman
and Moshee, 2008). The AODV operation creates a
free routing of hoops which avoid the problem of the
“account into infinity” from Bellman-Ford algorithm,
and offer a quick convergence before changes in the
network topology Ad-Hoc (Roberts, Rajeev and
Jaiswal, 2013).
An Ad-Hoc network (Mobile Ad-hoc Network o
MANET) is a group of nodes or host which
communicate between them through wireless links
without the necessity of an infrastructure of fixed
network. Each node works as router and it is routing
the different packages among the different terminals,
without the necessity of a direct reach between the
source and the destination. This type of network is
autonomous between terminals which can move
freely) (Vermani, Sharma and Yadav, 2012), (Enciso
and Mengual, 2014). The nodes use routing tables to
organize the leaps among the intermediate nodes so
they can send the packages. These routing tables must
be updated with frequency because the network is
mobile and changes of position are constant (Enciso
and Mengual, 2014).
DYMO (Dynamic MANET On-demand)
The routing protocol DYMO is designed for Ad-Hoc
mobile networks. It can be adapted at the changes of
the network topology and establish route unicast
between the destination node and the root node
(Kumar and Kumar, 2012). The basic operations of
the protocol DYMO are the discovery and
management of routes. During the discovery of route,
the root node begins with the diffusion of the route
request (RREQ) in the whole network to find the
destination node. During this diffusion process, each
intermediate node registers the route at root node.
When the destination node receives the RREQ, it
gives an answer of (RREP) unicast route into the
protocol of routing DYMO (Roberts, Rajeev and
Jaiswal, 2013), (Sivakumar and Kumar, 2009),
(Enciso and Mengual, 2014). The origin is designed
for Ad-Hoc mobile networks. It can adapted to the
changes of the network topology and establish unicast
route between the destination node and the root node.
The basic operations of DYMO protocol are the
discovery of routes and management of routes.
During the discovery of route, the root node begins
with the diffusion of the Route Request (RREQ) in
the whole network to find the destination node
(Sivakumar and Kumar, 2009).
2.3 Hybrids Protocols
ZRP (Zone Routing Protocol)
It is a hybrid routing protocol because it combines the
best properties of the proactive and reactive
protocols. ZRP is based in separation of the network
in zones. It differentiates a close or neighborhood
zone compose by the nodes that are at maximum of N
leaps and the rest of the network. In ZRP are used
two components for the routing (Sathish, Thangavel
and Boopathi, 2011). In the close zone is used the
component Intra Zone Routing Protocol (IARP)
which acts as a proactive protocol, keeping the routes
of the nodes which are to N leaps or less, being N
variable. The mechanism used to discover the
neighbour nodes is the regular exchange of messages
HELLO (Anwar, Azad, Rahman and Moshee, 2008),
(Sathish, Thangavel and Boopathi, 2011). For the
global routing into the nodes out of the interior or
close zone, ZRP has the Interzone component
Routing Protocol (IERP), which is as a reactive
protocol. When is necessary the route into a new
node, using the IERP is asking this route with the
mechanism Bordercast Resolution Protocol (BRP)
(Anwar, Azad, Rahman and Moshee, 2008). This
mechanism functions sending messages of
requirement of route to the nodes which belong to the
interior zone and which are in the border, which
means the maximum number of leaps to be
considered of the interior zone. If one of these border
nodes knows the route, it will send a message
indicating the node which begins the petition (Kumar
and Kumar, 2012). If this is not the case, the petition
will be forwarded by the whole network until it
arrives into a node which knows a route into the
destination. Then the answer will be sent back into
the origin, keeping the intermediate nodes
consequently the message passes to use as a route into
the desired destination. As, It was mentioned before,
the ratio (leaps number) of the interior zone is
adjustable according to the network necessities. As
extreme cases, if this ratio is small as minimum one,
ZRP will behave as protocol merely reactive.
Conversely, if the ratio is infinite, the behaviour will
be proactive (Kumar and Kumar, 2012), (Sivakumar
and Kumar, 2009).
3 SIMULATION ENVIRONMENT
The general aim of this research is to assess and
WEBIST 2016 - 12th International Conference on Web Information Systems and Technologies
210
analyse the performance of six existing routing
protocols, which are: AODV, DSR, DYMO, DSDV,
OLSR and ZRP on an Ad-hoc mobile network
environment (MANET), which made different
simulations in the network among 50, 90, 130, 170,
210, 250 nodes (customers) on a specific area. In the
Table 1, shows the variables and parameters for the
network simulation.
Table 1: Variables and parameters for the simulation.
Variable Values
Set val (chan) Channel/WirelessChannel
Set val (prop) Propagation
Set val (netif) Phy/WirelessPhy
Set val (mac) Mac/80211
Set val (ifq) Queue/DropTail/PriQueue
Set val (ll) LL
Set val (ant) Antenna/ OmniAntenna
Set val (ifqlen) 100
Set val (nn) 50,90,130,170,210, 250
Set val (rp) AODV, DSR, DYMO
Set val (rp) DSDV, OLSR, ZRP
Set val (y) 1912.54
Set val (stop) 150
3.1 Selection of the Area for the
Simulation
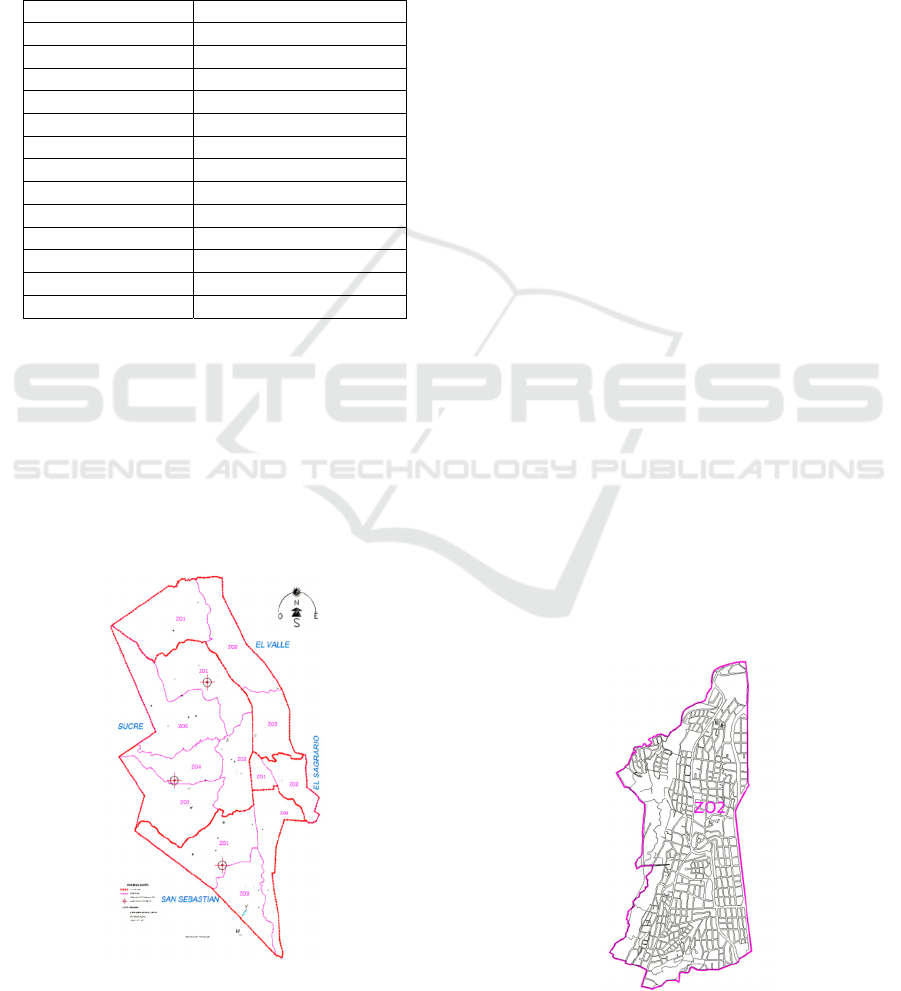
The area of the Loja city is divided by zones
according to the municipal regulations, the Fig. 1.
shows the total of urban area, the parishes and the
zones which take part of the urban perimeter. For the
present research was selected the zone 2,
denominated Z02 according to the map of the Fig. 2.
Figure 1: Map of the urban area selected for the simulation.
The selected zone has an area of 3657800.2365 and
perimeter of 10446.5313 m. This zone was selected
because it is placed in the downtown where is
concentrated most of the population. For the purposes
of the simulation, during the creation of the scenarios
was considered this area within a square, of equal side
to the square root of 3657800.2365 m2, with it was
obtained a square of equal side of 1912.5376 m; this
values will be used as parameter of x and y required by
NS-2.34 to determine the study area.
As additional date the selected street names are
the following: at north from the Turunuma avenue to
brazil street at south, by the east from the Gran
Colombia avenue to the Shushuguayco avenue in the
west.
3.2 Model of Mobility
In this research was simulated a network with mobile
nodes; for that reason, it is necessary to indicate a
pattern of mobility which will follow the same, the
election of the model of mobility will be essential
because it will have a significance impact in the
network features. There are some models of mobility
and in this research will be used the random
destination model Random Waypoint Model (RWP),
due to the NS2 has directly implemented in its
libraries. In general, it includes pauses between
changes of address and/or speed, a mobile node
begins in a place and period of time determined, that
means a pause, when the time expired, the mobile
node selects a random destination and speed
uniformly distributed, after the mobile node travels
into a new destination with the selected speed. When
the mobile node arrives, it makes a pause in a specific
period of time before beginning again. In the Table
2, is shown the configuration of the mobility
parameters for the simulation.
Figure 2: Selected zone for the simulation.
Analysis of Performance of the Routing Protocols Ad Hoc using Random Waypoint Mobility Model Applied to an Urban Environment
211
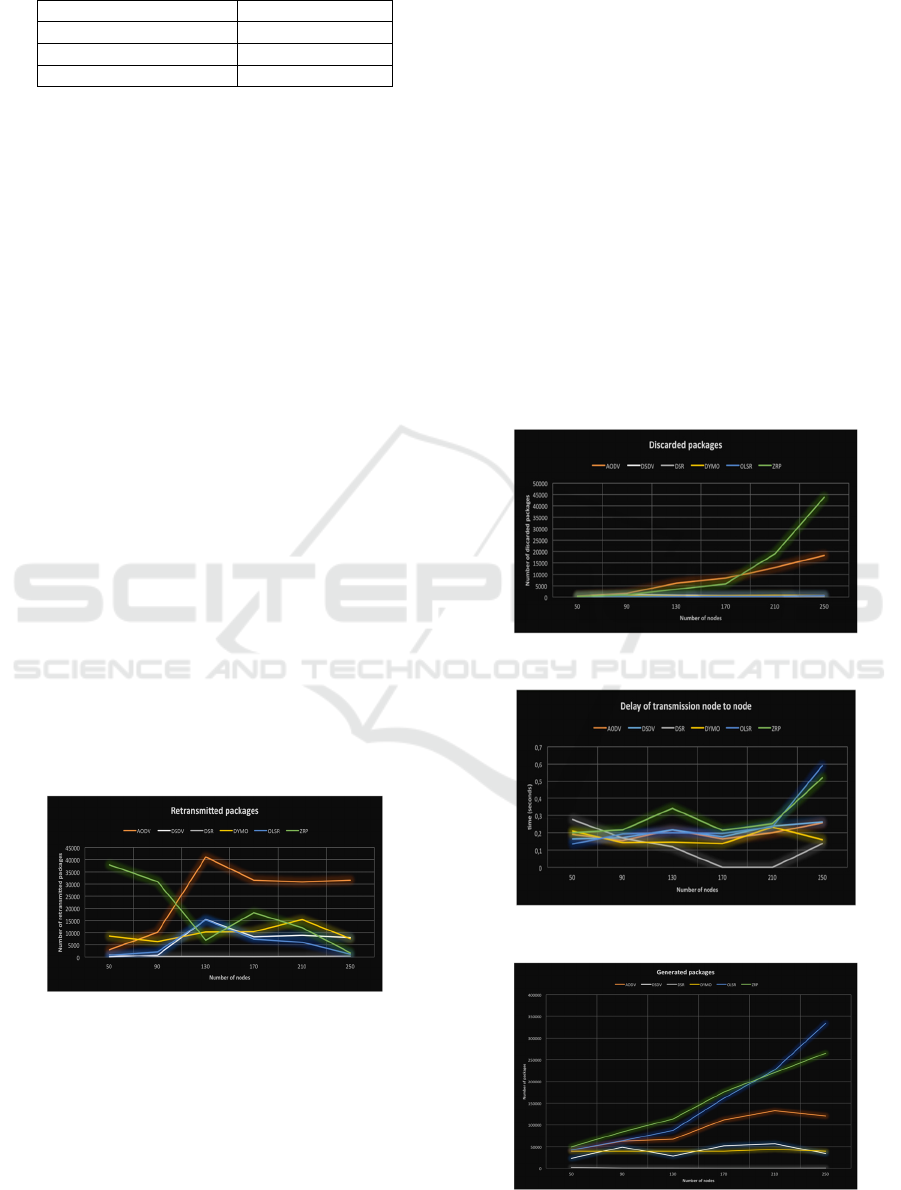
Table 2: Configuration of the mobility parameters.
Parameter Value
Min. speed 0 m/s
Max. speed 10 m/s
Pause time
0 seg
3.3 Tools
Network Simulator Version 2 (NS2) - It is a
simulator of discrete events available for Linux and
Windows (it is not recommendable the Windows
version). NS2 was initially created for fixed networks
and after was incorporated to the wireless model by
the Monarch group (Mobile Networking
Architectures). This simulation tool is very powerful
because it has two programing languages, C++ and
otcl, which interact to obtain a best performance.
TraceGraph - It is a free tool to draw and specially
to analyse the generated traces (*.tr) by the network
simulator NS2 version 2.34
4 METRICS FOR THE ANALYSIS
OF THE ROUTING
PROTOCOLS
Retransmitted Packages - The Fig. 3 represents the
amount of retransmitted packages during the
simulation, for the following number of simulated
nodes 50, 90, 130, 170, 210 and 250 nodes. It is
possible to observe that the best performance of
retransmitted packages is given by the AODV
protocol. However, this metric is not enough to
determine the effectiveness of a protocol in particular.
Figure 3: Retransmitted packages.
Discarded Packages - The Fig. 4, represents the
amount of discarded nodes by every one of the
protocols for the amount of generated nodes during
the simulation. Up to 90 simulated nodes, all the
analysed protocols generate standard maximum of
discarded packages, but while it is increasing the
number of simulated nodes, the number of discarded
packages is increasing. The AODV and ZRP
protocols are which produce mayor number of
discarded packages during the simulation time.
Delay of Transmission Node to Node - The Fig. 5
represents the delay that there is in the transmission
between the nodes of every one of the protocols. For
smaller quantities or similar to 90 nodes, the delay of
programing of all protocols the behaviour is similar.
However, at increasing the number of nodes,
programming time is increased. The reactive
protocol DYMO is the best performance at increase
of simulated nodes.
(1)
Where: P
Rec -
Received packages, P
Gen -
Genera-ted
packages, P
Desc –
Discarded packages y P
Retrans –
Retransmited packages. The equation “(1)”, is part of
the analysis to determine the quality of service in the
reception of valid packages during the transmission.
Figure 4: Discarded Packages.
Figure 5: Delay of transmission Node to Node.
Figure 6: Generated packages.
P
Rec
=P
Ge n
− P
Desc
+P
Retrans
WEBIST 2016 - 12th International Conference on Web Information Systems and Technologies
212

Packages Generated by Protocol - The Figure 6.,
shows the number of packages that every one of the
protocols has generated for the communication. The
hybrid protocols as ZRP and Proactive as OLSR are
the largest quantity of packages generated during the
simulation time.
5 CONCLUSION
This research, it was applied in an urban scenario in
case of emergency, where is required that a protocol
will be able to transmit the highest quantity of nodes of
the network in the less time possible; in consequence,
the best protocol of routing of the Ad Hoc networks is
DYMO because permit less quantity of retransmitted
packages, less number of packages of retransmitted
packages, less number of discarded packages, and the
less time of transmission node to node.
REFERENCES
Anwar, F., Md. Azad, S., Md. Rahman, A. and Moshee
Uddin, M., 2008. Performance Analysis of Ad hoc
Routing Protocols in Mobile WiMAX Environment,
IAENG International journal of Computer Science.
Ashish K. M, Singh, D., and Kumar, A., 2010. Performance
Comparison of DSR, OLSR and FSR Routing Protocols
in MANET Using Random Waypoint Mobility Model,
International Journal of Information and Electronics
Engineering.
Enciso Quispe, L. and Mengual Galan, L., 2014. Behavior
of Ad Hoc routing protocols, analyzed for emergency
and rescue scenarios, on a real urban area, Elsevier.
Jain, J., Gaur, N., Upadhyay, V., 2014. Comparison and
Analysis of AD-Hoc Routing Protocols (Proactive,
Reactive and Hybrid), International Journal of Applied
Engineering Research.
Kumar, S. and Kumar, J. 2012. Comparative Performance
Analysis of Routing Protocols in MANET using
Varying Pause Time, International Journal of
Computer Applications.
Roberts, A., Rajeev P. and Jaiswal, A.K. 2013. WSN
Performance Parameters of AODV, DYMO, OLSR and
IERP in RWP Mobility Model through Qualnet,
International Journal of Computer Applications.
Sangwan, R., Duhan, M. and Dahiya, S., 2013. Energy
Consumption Analysis of Ad hoc Routing Protocols for
Diferent Energy Models in MANET, IOSR Journal of
Electronics and Communication Engineering (IOSR-
JECE)
Sathish, S., Thangavel, K. and Boopathi, S., 2011.
Comparative Analysis of DSR, FSR and ZRP Routing
Protocols in MANET, IACSIT.
Sivakumar, N., Kumar, S., 2009. Comparison of DYMO
protocol with respect to various quantitative
performance metrics. International Journal of Science,
Engineering and Technology Research (IJSETR).
Vermani, B., Sharma, N., Yadav, B., 2012. Performance
Comparison of Wireless Mobile Ad-Hoc Networks on
the basis of Various Simulation Parameters,
International Journal of Latest trebds in Engineering
and technology.
Analysis of Performance of the Routing Protocols Ad Hoc using Random Waypoint Mobility Model Applied to an Urban Environment
213
