
ROBUST VIDEO WATERMARKING BASED ON 3D-DWT
USING PATCHWORK METHOD
Yadoallah Zamanidoost, Satar Mirza kuchaki
Department of Electrical Engineering, Iran University Science & Technology, Tehran, Iran
Zhinoos Razavi Hesabi, Antonio Navarro
Department of Electrical Engineering, Aveiro University, Aveiro, Portugal
Institute of Telecommunications, University Campuse, Aveiro, Portugal
Keywords: Video watermarking, Human vision system, Patchwork algorithm, 3D-DWT.
Abstract: The digital watermarks have recently been recognized as a solution for protecting the copyright of the
digital multimedia. In this paper, a new method for video watermarking with high transparency based on
3D-DWT is proposed. This algorithm is implemented on the basis of Human Vision System (HVS). By
using the patchwork methods in Discrete Wavelet Transform (DWT) domain, this algorithm is robust
against different attacks such as frame dropping, frame swapping, frame averaging, median filtering and
MPEG-2 video encoding. The experimental results show that the embedded watermark is robust and
invisible. The watermark was successfully extracted from the video after various attacks.
1 INTRODUCTION
In recent decade, information watermarking in
digital environment has attracted much interest
because of its ability in covering different aims.
Considering the high volume of video products in
recent years, special attention is focused on this type
of technology. Information watermarking is
embedment of a hidden message within another
signal. This signals named cover signal can be text,
digital image, audio or video file. Watermarking
follows different aims such as authentication,
reserving right of author, copy right and control of
data spreading, amongst others.
Three challenges exist in the field of
watermarking. In this process, data embedding must
be done in such a manner that watermarked signal
keeps its transparency. On the other hand, the signal
including hidden information may be exposed under
different processes such as filtering, geometric
transformation, adding noise, etc and after these
transformations, hidden message can be extractable.
This significant feature is called watermarking
system robustness.
With regard to application of watermarking in
video signals, high robustness in related algorithms
is a primary necessity. Another important challenge
in these systems is capacity. Capacity is by
definition the amount of information that can be put
on host signal while preserving its transparency and
robustness.
Many algorithms have been proposed for video
watermarking. First and foremost algorithm is
Hartung method (Harung, Girod, 1998). This
method is based on spread spectrum algorithms and
is executable on uncompressed and compressed
video signals. In addition to this method, various
algorithms have been considered to do watermarking
on uncompressed and compressed video signals like
data embedding in 3D-DCT domain (park, Lee, and
Moon, 2006) and 3D-DWT (Angiang, Jing, 2007)
for uncompressed video. There are other patterns in
which watermarking algorithms related to still
images are used and motion characteristics of video
have been used as parameters to modify presented
designs.
Patchwork algorithm was used for the first time
in image watermarking implemented on the basis of
comparison of two groups average, variance or other
signal properties (Yeo, Kim, 2003). This method has
been used in different transformation fields such as
DCT and DWT. (Kii, Onishi, Ozawa, 1999),
109
Zamanidoost Y., Mirza Kuchaki S., Razavi Hesabi Z. and Navarro A..
ROBUST VIDEO WATERMARKING BASED ON 3D-DWT USING PATCHWORK METHOD .
DOI: 10.5220/0003312001090113
In Proceedings of the International Conference on Imaging Theory and Applications and International Conference on Information Visualization Theory
and Applications (IMAGAPP-2011), pages 109-113
ISBN: 978-989-8425-46-1
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)
(2 1) (2 1) (2 1)
1
( , , ) ( ) ( ) ( )[ ( , , )*cos( )cos( )cos( )]
22
LLL
xU yV zW
FUVW CUCV CW f xyz
LLL
X
YZ
(1)
(OSluciak, Vargic, 2004). Patchwork algorithm in
audio watermarking shows a relatively high
performance leading to the high attack resistance
(Khademi, Akhaee, Ahadi, Amindavar, 2009). In
this paper, the patchwork algorithm is used for video
watermarking based on the 3D-DWT domain
(Anqiang, Jing, 2007).
2 WATERMARK EMBEDDING
PROCESS
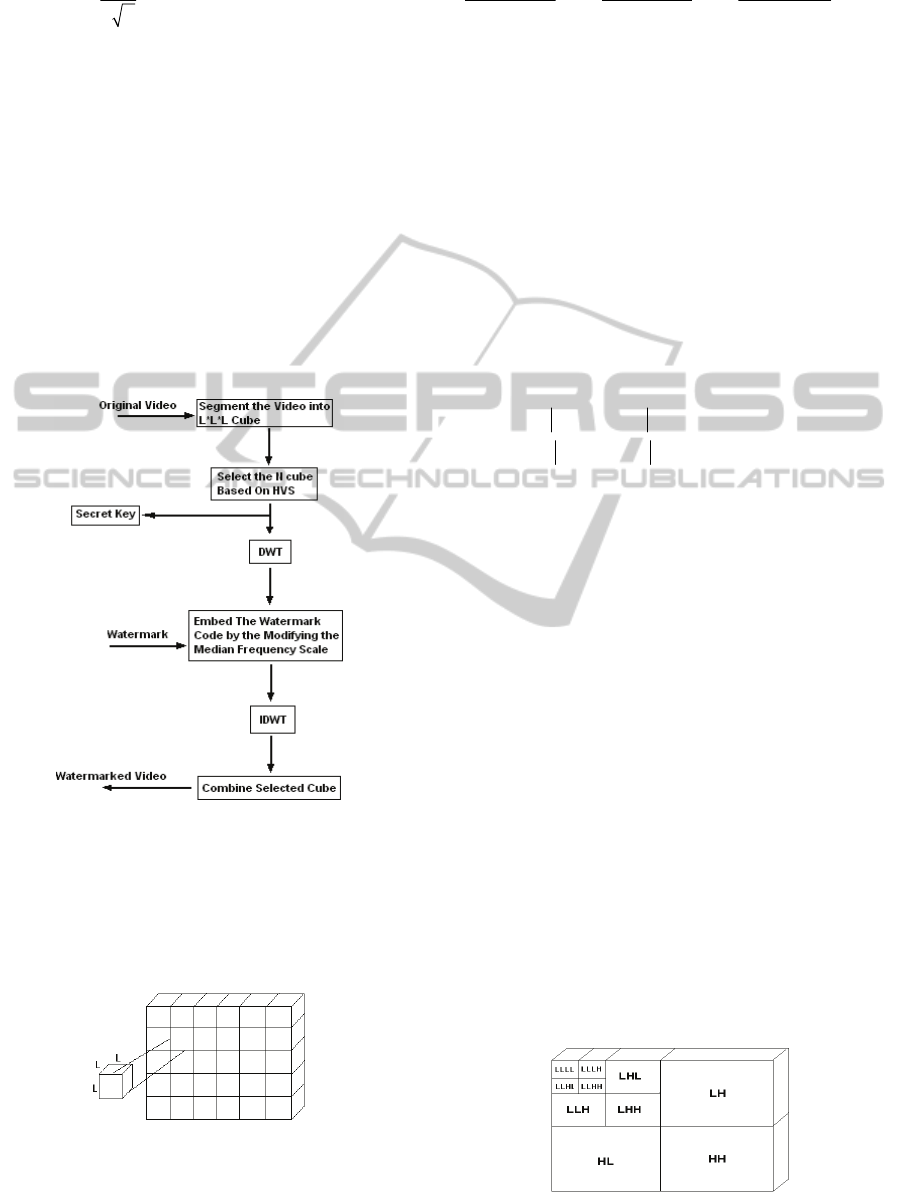
Fig. 1 shows a block diagram of the watermark
embedding process in an original video signal.
Figure 1: Embedding watermark process.
2.1 Selecting of N Cube based on HVS
First, the input video signal is divided into cubes of
L*L*L. Then, according to HVS, N cubes are
chosen (Fig. 2).
Figure 2: Dividing video signal to cubes of L*L*L.
This choosing criterion is used as a secret key to
increase algorithm security. The best position for
hiding watermark in video signal is where human
eye is less sensitive. Human eye has two
fundamental weak points:
1) Human eyes can not see details on the fast
moving object
2) Human eyes are not sensitive to the distortion in
the complex or high connectivity texture region
These two features can be extracted from the video
signal by 3D-DCT transformation according to
equation (1):
where C(U),C(V),C(W) are constants. After
applying equation 1 on cubes of L*L*L, the amount
of texture and objects movement are obtained by
equation 2.
LLLKLLWVUFEE
LLKWVUFEE
KNM
KNT
***,),,(
)1*(1,),,(
,
,
(2)
N is the cube number and k is pixel number inside
that cube. According to equation (2), E
T
is texture
amount and E
M
is amount of object movement inside
the cube. A change in E
T
and E
M
results in a change
in the Secret key and also an increase in these
parameters causes the transparency to improve and
the capacity to decrease and vice versa.
2.2 3D-DWT Transformation
of Selected Cubes
There are two main methods for 3D-DWT
Transformation:
1) 2D-DWT transform other each frame of cube,
then 1D-DWT transform from each pixel row
(
Huang-yu, Ying, cheng-ke, 2004).
2) 1D-DWT transform from each pixel row of cube,
then 2D-DWT transform other each frame of cube.
In the present study, the first method has been
applied. Each frame was transformed into a 2D-
DWT with 3 levels and Haar filter. Then each pixel
row was transformed to a 1D-DWT with 3 levels
using Haar transform (Fig 3).
Figure 3: 3D-DWT with 3 levels and Haar filter.
IMAGAPP 2011 - International Conference on Imaging Theory and Applications
110
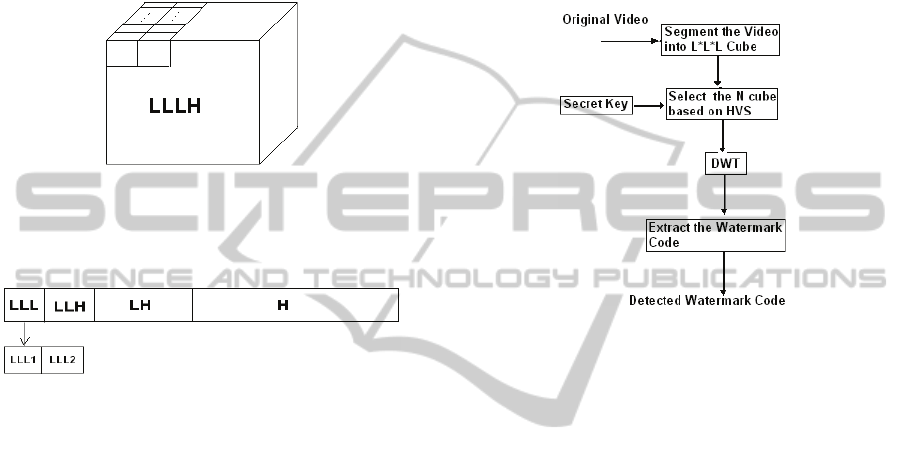
2.3 Watermark Embedding
by Patchwork Method
In this step, watermark is embedded to LLLH and
LLHL windows forming median frequency. By
embedding watermark in this window, watermarked
signal becomes robust to averaging and median
filtering attacks. First, adjacent row pairs are chosen
and variance of each of them is determined (Fig. 4).
Figure 4: Median frequency window.
As seen in Fig. 5, for watermarking LLL1 and
LLL2 are used.
Figure 5: LLL1 and LLL2 from LLL window.
Watermarking is explained by the following
algorithm:
If m == 0
LLL1=(LLL1+LLL2)/2+TH;
LLL2=(LLL1+LLL2)/2-TH;
Else
LLL1=(LLL1+LLL2)/2-TH;
LLL2=(LLL1+LLL2)/2+TH;
End
M is the watermark bit and TH is the threshold limit
of algorithm, by increasing TH, transparency of
video signal decreases while resistance against
frame dropping and frame swapping attack
increases. On the other hand decreasing TH
increases the PSNR of the video signal and
decreases the signal resistance against
aforementioned attacks.
2.4 Formation of Video Watermarked
After embedding watermark, video signal is
reconstructed. To do this, first, each pixel row was
transformed to a 1D-IDWT with 3 levels and Haar
filter, and then each frame was transformed to a 2D-
IDWT with 3 levels and Haar filter. At the end, all
cubes are combined together to form the
watermarked video.
3 WATERMARK EXTRACTING
PROCESS
Fig. 6 shows block diagram of watermark extracting
from watermarked video.
Figure 6: Watermark extracting process.
As seen in Fig. 6, first the watermarked video
signal is divided into cubes of L*L*L. Then, N
cubes are chosen according to secret key formed in
watermark embedding step. Afterwards, each cube is
transformed by a 3D-DWT with 3 levels and Haar
filter as mentioned in section 2.2. Adjacent pairs of
pixel rows of two LLLH and LLHL windows are
compared from variance point of view. The row with
higher variance is chosen. According to the
following algorithm, watermark is extracted by
comparison of LLL1 and LLL2.
If LLL1 >= LLL2
m = 0;
Else
m = 1;
End
4 EXPERIMENTAL RESULTS
In this experience 16*16*16 cubes are used and
amount of TH (embedding watermark threshold) is
40. The video sequences used in the experiments
include foreman and Stefan. The size of each frame
is 352x288. It is necessary to mention that to stand
up against MPEG-2 encoding attack; each class
includes I-Frames (Simitopoulos, Tsaftaris and
ROBUST VIDEO WATERMARKING BASED ON 3D-DWT USING PATCHWORK METHOD
111

Boulgouris, 2002). The embedded watermark
signature is a binary image (size 60x20 pixels),
shown in Fig.8 (a).
(a) Original video frame
PSNR=41.65 PSNR=40.87
(b) Watermarked video frame
Figure 7: Original and watermarked video frame.
An original frame from each video is shown in
Fig.7 (a). The corresponding watermarked frame for
each is shown in Fig.7 (b). Figure 8.(b) and (c)
shows the watermark image after extracting from
foreman and Stefan sequences.
(a) Original image (b) NC=0.9965 (c) NC=0.9945
Figure 8: Original watermark and extracted watermark.
PSNR (peak signal to noise ration) is one
commonly objective in perceptual quality measure.
PSNR is defined as:
)/255(10log10
2
MSEPSNR
(3)
In this equation, mean squared error (MSE) is
formulated as:
1
0
2
1
0
),(),(
1
M
i
N
j
w
jiXjiX
NM
MSE
(4)
Where, X's are the coefficients of the original video
and
w
X
's are the coefficients of the watermarked
video. M and N stand for the height and width of the
image, respectively.
In order to evaluate the performance of the
watermarking algorithm objectively, BER (Bit Error
Rate) and NC (Normalized Cross-Correlation
Function) are introduced.
1
0
0
1
1
M
i
i
i
i
i
ww
ww
M
BER
(5)
1
0
1
0
2
1
0
1
0
2
1
0
1
0
1212
12
),(),(
),(),(
),(
M
i
M
j
s
M
i
M
j
M
i
M
j
s
s
jiwjiw
jiwjiw
WWNC
(6)
In equation (5),
w is the extracted watermark, and
w is the original watermark. In equation (6),
),( jiw denotes the original watermark image, and
),( jiw
s
denotes the extracted watermark image.
Without any attack, the experimental results are
shown in Table.1. The extracted watermark
signature is obviously similar to the original
watermark.
In order to test the robustness of this
watermarking scheme, a set of attack experiments
were performed.
4.1 Median Filtering Attack
The system performance against 3*3 median
filtering is shown in Table.1.
4.2 Frame Averaging Attack
Frame averaging is another significant attack to the
video watermark. In this experiment, we use the
average of current frame and its too nearest
neighbours to replace the current frame which are
formulated as:
1,...,3,2
3
),(),(),(
),(
11
'
nk
yxfyxfyxf
yxf
kkk
k
(7)
Experimental results are shown in Table 1.
4.3 Lossy Compression
The MPEG lossy compression is one of the most
basic attacks to video watermark. Table 1 shows the
results after MPEG-2 Lossy compression.
Table 1: Performance in term of the Normalized
Correlation (NC) of the detect watermark.
Foreman Stefan
No Attack 0.9965 0.9945
Median Filtering 0.9632 0.9576
Averaging 0.9557 0.9527
MPEG2 0.9288 0.9189
IMAGAPP 2011 - International Conference on Imaging Theory and Applications
112
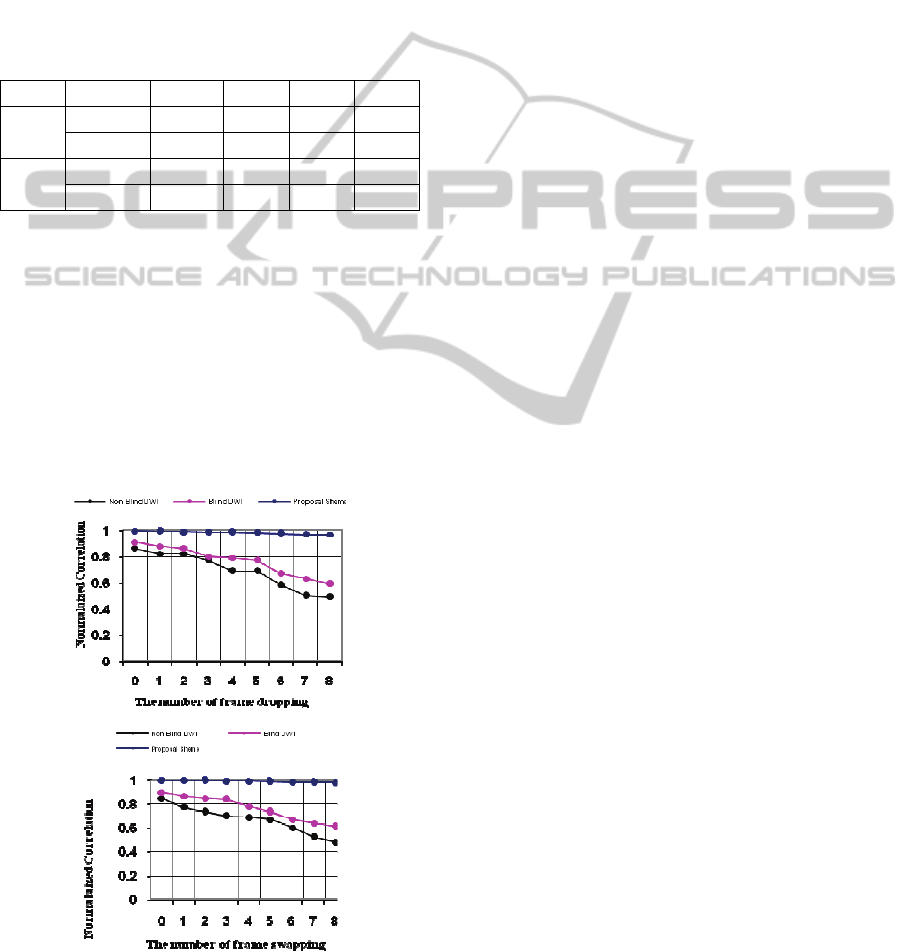
4.4 Frame Dropping
and Frame Swapping Attack
Frame dropping and swapping are very simple and
common attacks because of data redundancy. To
investigate the robustness of the proposed method
against these kinds of attacks, extraction of the
watermark after dropping and swapping different
rates of frames in the video clips was performed.
Experimental results are shown in Table.2.
Table 2: Results after frame dropping and frame Swapping
attack.
1/32 1/16 1/8 1/4
forman
Dropping 0.9878 0.9745 0.9588 0.9398
Swapping 0.9912 0.9813 0.9732 0.9532
Stefan
Dropping 0.9897 0.9867 0.9689 0.9478
Swapping 0.9932 0.9889 0.9773 0.9529
According to the above experimental results, the
watermarking scheme is robust against a variety of
common video processing attacks such as median
filtering; frame averaging, frame dropping, frame
swapping and MPEG2 lossy compression. The
extracted watermark is highly similar to the original
watermark.
This method is compared with non-blind method
(X. Niu, shenghe Sun, 2000) and blind method (A.
Essaouabi, E. Ibnelhaj, 2009) for Stefan sequences.
Figure 9.(a) and (b)
(a) The effect of the frame dropping
(b) The effect of the frame swapping
Figure 9: comparison of Blind, Non Blind and proposal
watermarking scheme for Stefan scene.
5 CONCLUSIONS
This paper presented semi-blind video watermarking
based on wavelet transform. By using the secret key
in embedding algorithm, this algorithm has high
security. Image that is used as a watermark is a
binary image. Procedure of this method includes
video processing, video embedding and video
detection that are described in details. This method
is a powerful method against attacks such as frame
averaging, frame swapping, frame dropping, median
filtering and MPEG2 lossy compression.
REFERENCES
F. Harung, B. Girod, 1998. watermarking of
uncompressed and compressed video signal
processing, 66 (3) pp. 283-301.
H. Park, S. H. Lee, and Y. S. Moon, 2006. Adaptive video
watermarking utilizing video characteristics in 3D-
DCT domain. lecture notes in computer science, pp.
397-406.
L. Angiang, L. Jing, 2007. A novel scheme for robust
video watermark in the 3D-DWT domain. first
international symposium on data, pp. 514-516.
Z. Huang-yu, L. Ying, W. Cheng-ke, 2004. A Blind
spatial-temporal algorithm based on 3D wavelet for
video watermarking. international conference on
multimedia and Expo (ICME) ,pp 1727-1730.
K. Yeo, H. J Kim, 2003. Generalized Patchwork
algorithm for image watermarking. international
conference on multimedia system, pp 261-265.
H. Kii, J. Onishi, S. Ozawa, 1999. The Digital
Watermarking method by using both patchwork and
DCT. IEEE international conference on multimedia
system ,pp 895-899.
OSluciak, R. Vargic, 2004. An Audio Watermarking
method based on wavelet patchwork algorithm. IEEE
international conference on multimedia.
N. Khademi, M. A. Akhaee, S. M. Ahadi, H.
Amindavar,August 2009. Robust Multiplicative
Patchwork method for audio watermarking," IEEE
Transaction on audio, speech and language processing,
Vol 17, NO.6,pp 1133-1141.
L. Anqiang, L. Jing, 2007. A Novel Scheme for robust
video watermarking in 3D-DWT Domain. First
International symposium on data, privacy and E-
Commerce IEEE ,pp 514-516.
A. Essaouabi, E. Ibnelhaj, 2009. A 3D wavelet-Based
method for digital video watermarking. IEEE
international conference on multimedia, pp 429-434.
D. Simitopoulos, S. Tsaftaris and N. Boulgouris, Aug.
2002.compressed-domain video watermarking of
MPEG stream. in proc. IEEE int. conf. on multimedia
and Expo, pp. 569-572.
ROBUST VIDEO WATERMARKING BASED ON 3D-DWT USING PATCHWORK METHOD
113
