
CELLULAR AUTOMATA BASED KEY AGREEMENT
Debdeep Mukhopadhyay
Department of Computer Science and Engineering
Indian Institute of Technology, Kharagpur, India
Dipanwita RoyChowdhury
Department of Computer Science and Engineering
Indian Institute of Technology, Kharagpur, India
Keywords:
Cellular Automata, Key Agreement, Random Oracles, one-way function.
Abstract:
This paper proposes a new key agreement protocol using Cellular Automata (CA). The primitives on which the
protocol is based has been developed using specially designed CA structures. The paper aims at developing a
key agreement technique which is not based on the Diffie-Hellman problem. The removal of exponentiations
makes the protocol fast and have a linear time complexity. The protocol has been found to resist known forms
of attacks. Indeed the initial review promises the development of a key agreement protocol which meets nicely
the conflicting ends of security and efficiency.
1 INTRODUCTION
Authentication and key establishment are fundamen-
tal building blocks for securing electronic commu-
nication. Cryptographic algorithms, for encryption
and decryption cannot perform their specified func-
tions unless secure keys have been established. Key
establishment (A.Menezes and Vanstone, 1996) is
a process or protocol whereby a shared secret be-
comes available to two or more parties, for subse-
quent cryptographic use. Key agreement mechanism
is a key establishment technique in which a shared
secret is derived by two or more parties as a func-
tion of information contributed by or associated with
each of these (ideally) such that no party can predeter-
mine the resulting value. Since the seminal paper of
Diffie and Hellman (W.Diffie and M.Hellman, 1976)
in 1976, several solutions have been proposed for key
agreement whose security lies on the Diffie-Hellman
problem (either computational or decisional) in finite
groups. However modular exponentiation is an ex-
pensive operation. Despite the increase in availabil-
ity of computational resources considerable demand
exists in the development of protocols that can be
implemented on devices with limited computational
power. Applications of such type being mobile hand-
sets, handheld devices, embedded hardware and smart
cards.
In this paper we propose a Cellular Automata (CA)
based key agreement protocol. Cellular Automaton
has a regular, cascadable and modular structure thus
giving scope to efficient implementation(Chaudhuri
et al., 1997). The paper shows a CA based technique
to implement a k-bit to k-bit trapdoor permutation f
which is used to build an encryption function which
is secured under the Random Oracle (RO) model (Mi-
hir Bellare and Phillip Rogaway, 1994). The en-
cryption function is used in combination with a spe-
cially designed Cellular Automaton called Two Pre-
decessor Single Attractor Cellular Automata (TPSA-
CA) to derive a common secret key K
AB
. Comple-
mented Cellular Automaton has been characterized
in (Mukhopadhyay and RoyChowdhury, 2004). This
characterization has been extended in the present pa-
per where the complemented CA has been used to de-
velop a technique to vary the key at a very fast rate.
As a matter of general principle it is not possible
to establish an authenticated session key without ex-
isting secure channel already being available. In fact
this statement has been stated formally and proved to
be correct(Boyd, 1993). The proposed protocol also
assumes the existence of an offline server which pro-
vides certified long term keys to the principals. It
may be noted that these long term keys are used to
encrypt random bit strings and are also used only in
the key-establishment phase. But the resultant of the
agreement protocol is a session-key which is used to
encrypt files of fixed formats (like bmp files or jpeg
files). Also they are used for bulk encryption and
so are more amenable to cryptanalysis. Thus they
262
Mukhopadhyay D. and RoyChowdhury D. (2005).
CELLULAR AUTOMATA BASED KEY AGREEMENT.
In Proceedings of the Second International Conference on e-Business and Telecommunication Networks, pages 262-267
DOI: 10.5220/0001412402620267
Copyright
c
SciTePress

are required to be altered frequently(Boyd and Math-
uria, 2003). The complemented CA rules and the one
way function provide a way to vary the key frequently
which is presented in the paper. The proposed proto-
col has been shown to be secured in the face of known
attacks. The removal of the exponentiation opera-
tion leads to huge computational savings. Keys can
be guaranteed to be random even if one of the inputs
become known - a property lacking in D-H based pro-
tocols(Boyd and Mathuria, 2003).
The outline of the paper is as follows: Section 2 de-
velops the CA based primitives for the key agreement
protocol. Section 3 proposes the key agreement proto-
col using the CA based primitives. Section 4 discusses
the security of the scheme and the work is concluded
in section 5.
2 CA BASED PRIMITIVES FOR
THE KEY AGREEMENT
PROTOCOL
Key agreement protocols require the strength of their
underlying primitives. The basic components (prim-
itives) on which the present agreement protocol de-
pends are enumerated below:
1. A CA based Encryption function
2. A CA based Agreement function which uses the
information contributed by the two principles
3. A CA based function for varying the session key at
a very fast rate
In the following subsections the cryptographic primi-
tives are explained.
2.1 CA based encryption function
In (Mihir Bellare and Phillip Rogaway, 1994) Bellare
and Rogaway have proved that under the Random Or-
acle (RO) model the following encryption is semanti-
cally secured.
E
G,H
(x)=f(x + G(r)||r + H(x + G(r))
Here, + indicates the bitwise exor operation and || in-
dicates the string concatenation. The message to be
encrypted is a k bit binary sequence and r is a ran-
dom k bit number. In the above expression H and G
are random oracles and f is a trapdoor permutation.
In the RO model it is assumed that H and G are func-
tions truly returning random values each time, except
that it always return the same output when the input
is same. They are a k bits → k bits pseudo-random
permutations. In our construction f is chosen as a CA
based one-way permutation which operates on 2k bits
and produces a 2k bits output. The functions H and
G are realised using CA based structures which are
known to be excellent pseudo-random number gener-
ators(Chaudhuri et al., 1997; Hortensius et al., 1989).
Security is based on the reasoning that if an adver-
sary A can break the encryption scheme with some
success probability, then there is an algorithm M
which can invert the underlying trapdoor permuta-
tion f with comparable probability and time. So, first
we outline the CA based one way function, which is
based on simple rules, thus leading to efficient imple-
mentations.
2.1.1 One Way function based on Simple Rules
A function f is one-way if
1. It is polynomial time computable
2. It is hard to invert i,e no polynomial time algorithm
can find any pre-image of f(x).
Let the input of the one way function be X =
{x
n−1
,x
n−2
,...,x
0
} and the output is Y =
{y
n−1
,y
n−2
,...,y
0
}.
We define a state transition by the following func-
tion:
y
n
= x
n+1
+(x
n
x
n−1
)
Here, the bar symbol indicates the bitwise comple-
ment,
indicates the bitwise or operator and + indi-
cates the bitwise exor operator. The cellular automa-
ton has a zero boundary condition, i,e x
−1
= x
n
=0.
Thus the output Y can be easily constructed from X
but the inverse is hard. A mapping x → φ(x) is called
invertible if φ(x)=φ(y) iff x = y. According to that
definition the present function is not invertible.
However, the function (state transition) can be eas-
ily inverted if the value of x
0
is known. Thus depend-
ing on x
0
there can be two values (pre-images) of Y .
If such a transformation is used 2 times any output
state can have 2
2
pre-images with equal probability
if the last bits of the transformation are random to
an adversary. Thus if the transformation is repeated
n number of times there can be 2
n
pre-images with
equal probability. Inorder to decrypt we have a key r
(which is a long term key in our algorithm). The bits
of r are exored to the 0
th
bit slices of all the stages of
the transformation. The information is sent as a part
of the encrypted message. The part of the message is
called the trap-pad (denoted by P ). The application
of the above transition one time is denoted by N (X)
and for n times by N
n
(X). Thus we construct the
one-way function with the trapdoor as follows:
Y = N
n
(X)=N
n
(x
n−1
,x
n−2
,...,x
0
)
The 0
th
bit slices at all the stages of the transfor-
mation are stored in an n bit register. Thus P =
([N(X)]
0
+ r
0
, [N
2
(X)]
0
+ r
1
,...,[N
n−1
(X)]
0
+
r
n−1
). Thus the one way permutation is denoted by
{P, Y } = {P, N
n
(X)}
CELLULAR AUTOMATA BASED KEY AGREEMENT
263

Thus any principal (party) with a valid long term
key (r) can easily decrypt the sequence and obtain X
while for an adversary all the pre-images are equally
probable.
2.2 Two Predecessor Single
Attractor Cellular Automata
(TPSA-CA) Based Function
TPSA CA are a special class of non-group CA in
which the state transition graph forms a single in-
verted binary routed tree at all zero state. The CA
has been characterized in (Chaudhuri et al., 1997) and
has been used in the current protocol to develop an
efficient technique to agree on the key for the first
time. These CA are characterized by the fact that
every reachable state in the state transition graph has
exactly two predecessors. The only cyclic state is the
all zero state (for a non-complemented TPSA CA),
which is an attractor (or graveyard). Corresponding
to a TPSA CA M
1
and a state S, there exists a com-
plemented CA M
2
with state S as an attractor. If the
characteristic matrix M
1
be indicated by T
p
and it is
required to build a complemented TPSA CA such that
S is the graveyard (attractor) then the characteristic
matrix of the complemented CA, T
c
is related to T
p
by
T
c
(X)=T
p
(X)+(I + T
p
)Z
where X is the seed to the CA.
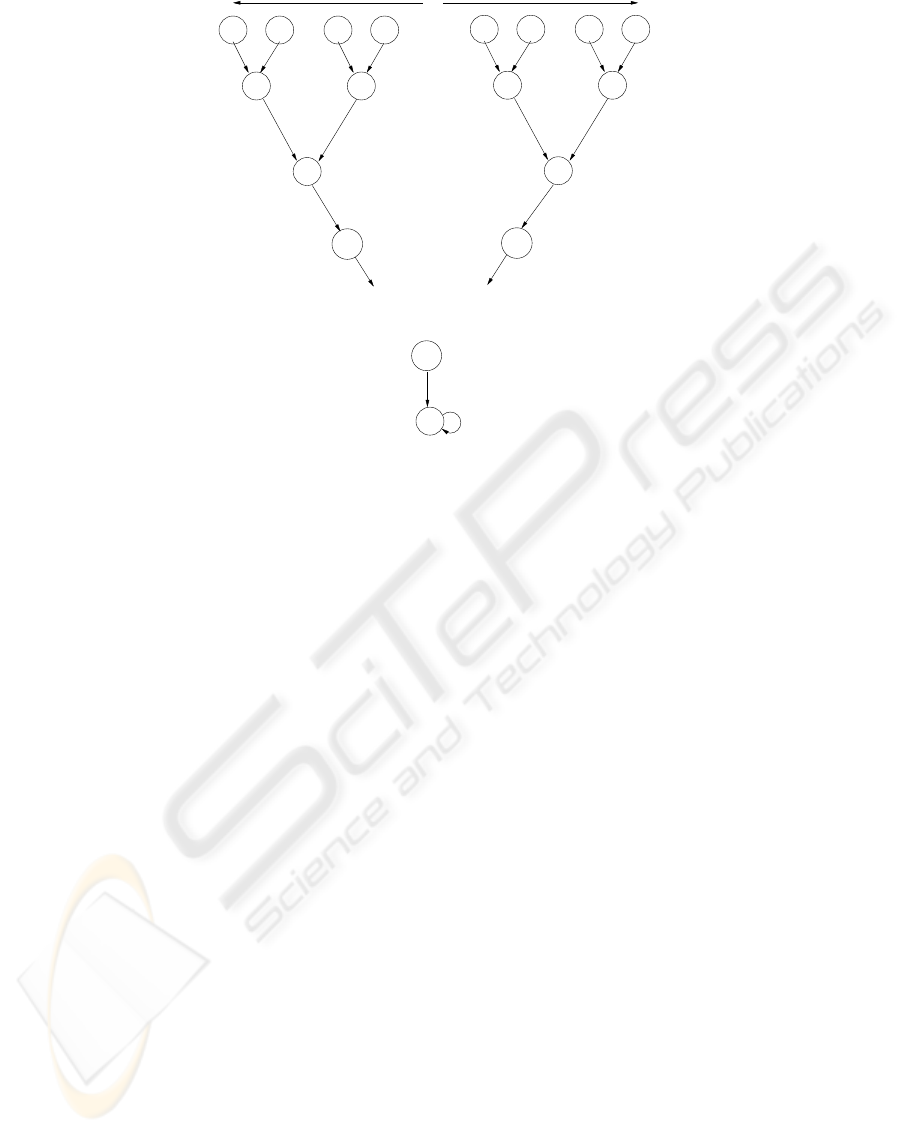
2.2.1 How TPSA CA provides key freshness?
The state transition graph of an n bit TPSA Cellular
Automaton is shown in figure 1. Given two inputs
A and B the path between the points are noted. The
path between A and B, with both ends included give a
list of indices that forms a set. For a given TPSA CA
we have a unique path between A and B. However
the path depends on the graveyard state, which can
be changed as already mentioned. The elements of
the path is used to return the modulo-2 sum of the se-
lected numbers which form elements of the list. Since
the state transition depends on the graveyard state and
all the states can be made the graveyard, all the paths
and final sum are possible for a given pair of A and
B. It may be noted that for an n bit TPSA Cellu-
lar Automaton the path between A and B has atmost
2n elements i,e twice the depth of the inverted binary
tree. So, the computation of the output sum can take
place in linear time (O(n)).
The final sum of the path is the agreed key K
AB
which is the output of the contributions of the two
parties, say N
A
and N
B
. Mathematically, K
AB
=
TPSA(N
A
,N
B
), where TPSA is the TPSA CA
based function explained. Since the transition char-
acteristic T of the TPSA CA is not invertible (note
the graph) if the final path sum and one of the inputs
say N
A
is known then it is not possible to calculate
the other element N
B
without exhaustive search. This
prevents a principal B to calculate the value of N
B
so
that he can force the value of N
A
and N
B
to output
an old key (old sum). Such type of function provides
key-freshness to the key.
2.3 CA based function for varying
the key
In this subsection we provide the properties of a spe-
cial type of complemented Cellular Automaton which
is used to vary the key at a fast rate.
One of the rules of Cellular Automata (
T ) is rule
153, (Chaudhuri et al., 1997). The present section
characterizes the CA with rule 153. It is known that if
a cellular automaton with rule 153 is fed with an ini-
tial seed of X, then the cellular automaton produces
an output
T (X)=T (X)+IF, where I is a unit ma-
trix and F is all one vector. Hence, we have X,
T (X)
and
T
2
(X) members of the same cycle. Physically,
an n-cell uniform CA having rule 153 evolves with
equal number of cyclic states. The CA has some re-
markable properties. The CA evolves equal lengths
and the length for an n-cell CA grows linearly with
the number of cells.
The following theorem characterizes a CA based
on the rule
T .
Theorem 1
(Mukhopadhyay and RoyChowdhury,
2004) The length of cycle for an n-cell CA, having
rule
T
,is
l =
2
logn+1
,
n
≥
2
(1)
2.3.1 Generalisation of 153 CA
The above characterization for the Cellular Automa-
ton is for rule 153. Similarly, it may be proved that
the same characterization holds for generalised Cel-
lular Automata with characteristic matrix, T
g
where
T
g
= A.(T ).A
−1
. In order to relate the state spaces of
the generalised CA, we define two rules:
R1(X)=X +
T
g
(X)+T
2
g
(X)
and, R2(X)=X +
T
g
(X)+T
3
g
(X)
It may be proved that for a and b randomly cho-
sen indices,
T
a
g
R1R2(T
b
g
(X)) = T
b
g
R2R1(T
a
g
(X)).
Every element, X of a cyclic subspace when mapped
by the rule R1 (or R2) gives another cycle. The rules
or the properties of the CA are used to migrate from
one cyclic subspace generated by T
g
to another. The
inter-relations promise the development of CA-based
algorithms used to develop an agreement property,
which is illustrated in figure 2.
ICETE 2005 - SECURITY AND RELIABILITY IN INFORMATION SYSTEMS AND NETWORKS
264
.............
.
.
.
.
.
.
A
B
2
n/2
Attractor (Graveyard)
Figure 1: The state transition graph of a TPSA CA
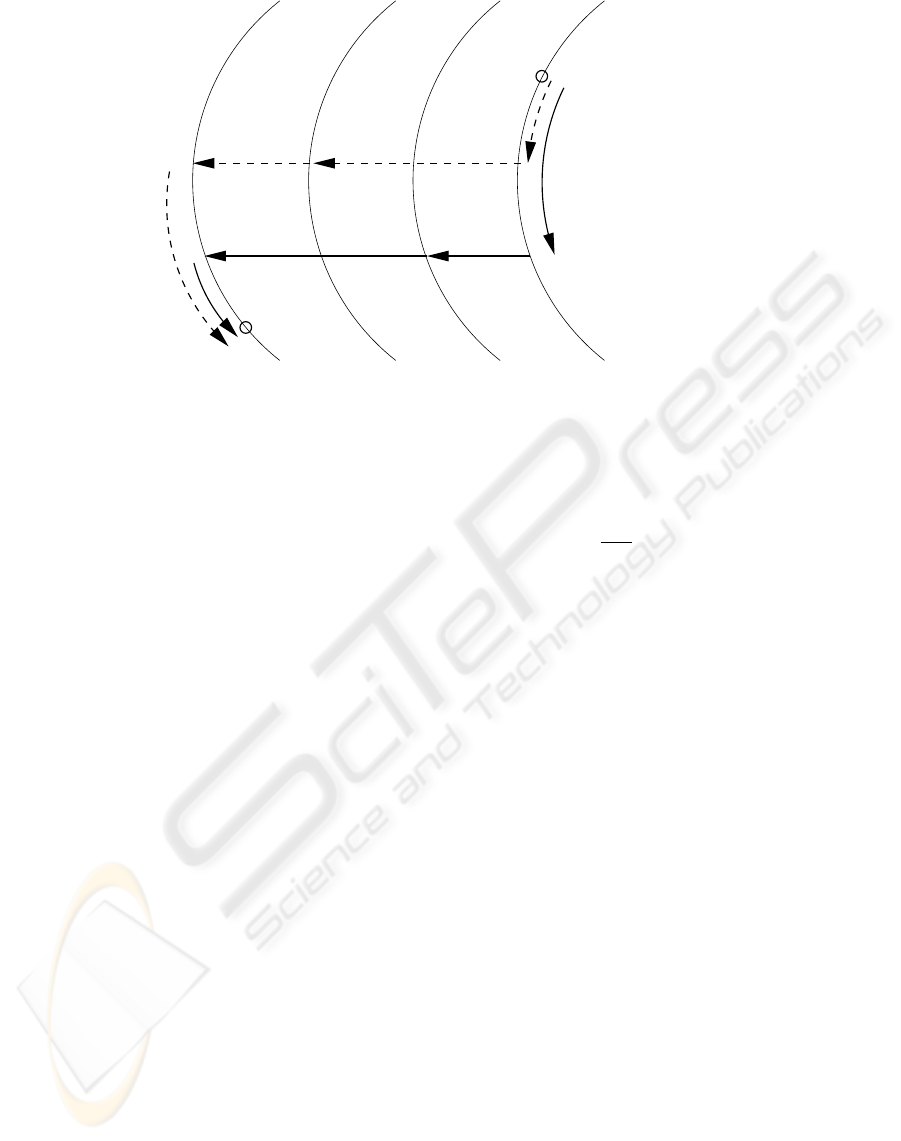
2.3.2 Regeneneration of session keys
Key freshness is important, that is the key should
change frequently. Thus less data is encrypted by the
same key, so that the eavesdropper has lesser proba-
bility of success. Further the amount of damage done
due to the revelation of a key is reduced if the key is
frequently changed.
The class of the group CA characterized with the
matrix T
g
exhibit an interesting agreement property.
Figure 2 shows the state space cycles. P1 is an ini-
tial point of agreement of two parties. After the ini-
tial agreement both takes up different paths (as shown
by the dashed and the solid lines). It is certain from
the above results both the paths converge again at P2
which is the second point of collision or agreement.
This property promises the development of an effi-
cient agreement protocol using Cellular Automata.
3 ESSENTIALS OF THE
PROTOCOL
The Cellular Automata based key agreement protocol
is presented in this section. The two parties A and B
exchange messages to derive a final key K
AB
.
Message 1: A → B , E
B
(A, N
A
,Z)
Message 2: A ← B , E
A
(B,N
B
),x
B
Message 3: A → B , x
A
The terms used in the protocol are explained next.
• Principal A uses the CA based encryption scheme
(proposed in section 2.1) to encrypt the identifier A
i,e E
A
, the nonce N
A
and the secret graveyard state
Z on which the state transition graph of the TPSA
CA is dependent. The encrypted text has a trappad
P which in combination with B’s long term key is
used by B to decrypt the ciphertext and obtain the
secret graveyard (explained in section 2.1.1).
• B then sends his contribution N
B
to A using the
CA based encryption function (i,e E
B
). Mean-
while, B computes the shared key K
AB
by using
the TPSA CA based on the secret graveyard state.
The values of N
A
and N
B
are as outlined in sec-
tion 2.2. B also generates a random number r
B
and
computes a value x
B
= R2[T
r
B
g
(K
AB
+f(K
AB
)],
where f is the CA based one way function and T
g
is
the generalised Cellular Automaton characterized
in section 2.3.2. B then sends back x
B
to A who
also uses the values of N
A
,N
B
and Z to compute
the value of K
AB
.
• A also generates a random number r
A
and calcu-
lates x
A
= R2[T
r
A
g
(K
AB
+ f (K
AB
)]. The value
of x
A
is then sent to B.
Using the following theorem (agreement property)
both A and B can continnue to generate new keys at
a very fast rate.
Theorem 2 A
computes
K
1
from the knowledge of
x
B
(the public information),
r
A
(the private informa-
tion) and the initially agreed key
K
AB
.
B
computes
K
2
from the knowledge of
x
A
(the public informa-
tion),
r
B
(the private information) and the initially
agreed key
K
AB
. Then
K
1
=
K
2
, thus they both agree
on a new derived key.
CELLULAR AUTOMATA BASED KEY AGREEMENT
265
a
b
b
a
R1
R1R2
R2
P1 (Agreement
1)
P2 (Agreement 2)
Figure 2: Agreement Property of the State Spaces
Proof: The proof follows directly from the char-
acterization presented in the previous section. A cal-
culates K
1
= T
r
A
g
[R1{R2[T
r
B
g
(K
AB
+ f (K
AB
))}]
and B computes K
2
= T
r
B
g
[R2{R1[T
r
A
g
(K
AB
+
f(K
AB
))}]. From the property of the generalised au-
tomata, K
1
= K
2
. Thus they both agree on a new key.
4 SECURITY ASPECTS OF THE
PROTOCOL
The key agreement protocol’s security is dependent
on the security of CA based encryption and the
pseudo-randomness of the CA based functions x
A
and x
B
(generated using T
g
).
The CA based encryption is secured under the Ran-
dom Oracle method (Mihir Bellare and Phillip Rog-
away, 1994). The security of the encryption is based
on the security of the underlying CA based one way
function. For an adversry who does not have the se-
cret information (long-term key) all the elements can
be preimages of the output f (x) with equal probabil-
ity.
A TPSA CA based function is used to derive the
agreed key K
AB
. Since the graveyard state Z is kept
secret from the adversary this function helps in de-
riving the key with freshness property (explained in
subsection 2.2).
Finally the pseudo-randomness of x
A
and x
B
has
been verified using standard tests for randomness. In
figure 3 the results of the avalanche analysis has been
presented. The Avalanche Test is based upon the fact
that a 1-bit change in the plain text should produce a
radical change in the ciphered text (Stallings, 2003).
A pair of input sequences have been taken and the
function is applied upon both of them. The number of
bit-differences in the output sequence are noted. The
mean of the distribution should be n/2 and the stan-
dard deviation,
√
npq, where n is the block-size and
p=q=1/2 (binomial probability). The key-agreement
protocol has been simulated on large number of data
and derived keys have been observed pairwise. The
results have been found to comply with the expected.
The randomness of the values x
A
and x
B
can also
be proved if it is assumed that r
A
and r
B
are ran-
dom. The randomness of the values are further en-
hanced by the use of the CA based one way func-
tion which is a slight variant of rule 30 CA (which
is known to be a powerful random sequence genera-
tor (Wolfram, 1983). Also the generalisation of the
153 CA shows how the randomness can be varied by
constructing various T
g
’s where the characterization
and agreement properties are still valid. It has been
checked that the protocol prevents known attacks like
replay attacks, known key attacks and triangle attacks.
5 CONCLUSION
The paper proposes a Cellular Automata based key
agreement protocol. The protocol is based on CA
based primitives which have been developed in the
paper. The security of the key agreement protocol
is based on the security of a CA based encryption
scheme which is secured under the Random Oracle
Method. Since the protocol does not have any expo-
nentiation operation and is based on simple rules the
technique can be used to generate session keys at a
very fast rate. It has been checked that the protocol
prevents known attacks like replay attacks, known key
ICETE 2005 - SECURITY AND RELIABILITY IN INFORMATION SYSTEMS AND NETWORKS
266
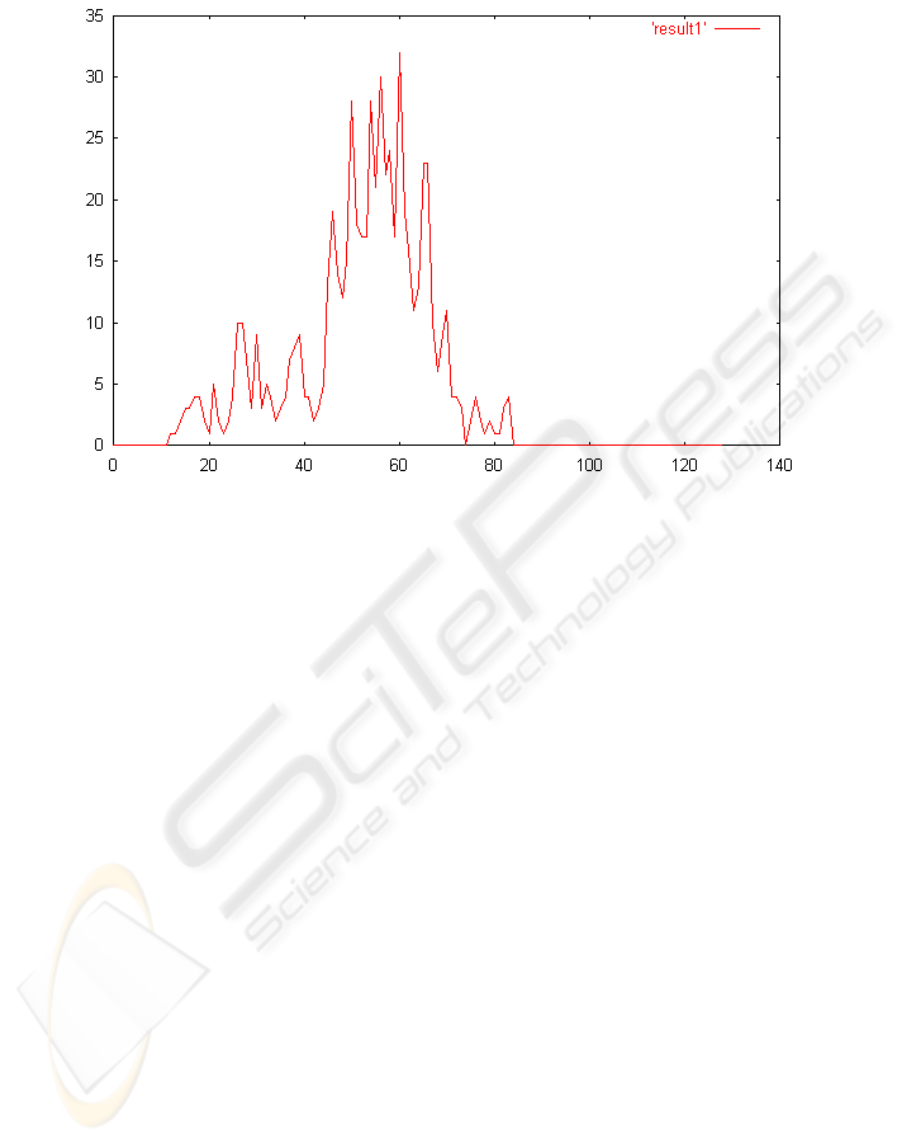
Figure 3: Avalancle Test Results
attacks and triangle attacks. However the history of
agreement protocols obviates the necessity of formal
proofs of such protocols and is currently underway.
REFERENCES
A.Menezes, P. V. O. and Vanstone, S. (1996). Handbook
of Applied Cryptography, chapter 12, pages 489–541.
CRC Press.
Boyd, C. (1993). Hidden assumptions in cryptographic pro-
tocols. IEEE Journal of Selected Areas in Communi-
cations, 11(5):694–701.
Boyd, C. and Mathuria, A. (2003). Protocols for Authenti-
cation and Key Establishment, chapter 5, pages 138–
199. Springer.
Chaudhuri, P. P., Chowdhury, D., Nandi, S., and Chattopad-
hyay, S. (1997). Additive Cellular Automata Theory
and its Application, volume 1, chapter 4. IEEE Com-
puter Society Press.
Hortensius, P. D. et al. (1989). Cellular automata based
pseudo-random number generators for built-in self-
test. 8(8):842–859.
Mihir Bellare and Phillip Rogaway (1994). Optimal Assy-
metric Encryption-How to Encrypt with RSA. In Ad-
vances in Cryptology-Eurocrypt 1994. Lecture Notes
in Computer Science, Vol. 950, Springer Verlag.
Mukhopadhyay, D. and RoyChowdhury, D. (2004). Char-
acterization of a class of complemented group cellular
automata. In In the Proceedings of ACRI 2004, LNCS
3305. University of Amsterdam, Science Park Ams-
terdam, The Netherlands.
Stallings, W. (2003). Cryptography and Network Security.
Prentice Hall.
W.Diffie and M.Hellman (1976). New Directions in Cryp-
tography. In IEEE Transactions on Information The-
ory (22), pages 644–654. IEEE.
Wolfram, S. (1983). Statistical mechanics of cellular au-
tomata. Rev. Mod. Phys., 55(3):601–644.
CELLULAR AUTOMATA BASED KEY AGREEMENT
267
