
Efficient Heuristic Safety Analysis of Core-based Security Policies
Peter Amthor
Ilmenau University of Technology, Germany
Keywords:
Security Engineering, Security Policies, Access Control Systems, Access Control Models, Safety, Heuristic
Analysis, SELinux.
Abstract:
Being of paramount importance for the correctness of a security policy, the property of safety has received
decades of attention in the field of model-based security engineering. To analyze the safety of a security model,
heuristic approaches are used to avoid restrictions of the model calculus while accepting semi-decidability of
this property. Within this field, this paper addresses three open problems concerning the DEPSEARCH heuristic
safety analysis framework: Inefficient state-space exploration, static verification of unsafety-unsatisfiability,
and parameter dependency analysis. We describe these problems on a formal basis, specify solution proposals,
and implement these in the current, model-independent f DS framework. A practical evaluation based on
SELinux is performed to study effectiveness and future optimization of the framework.
1 INTRODUCTION
While security requirements of IT systems have be-
come of paramount importance, the tasks of rigor-
ous specification, verification, and implementation
of security properties have received increasing atten-
tion (Sandhu, 1988; Kleiner and Newcomb, 2007;
Stoller et al., 2011; Ranise et al., 2014; Shahen et al.,
2015). The problems of systems security specification
and implementation have found a solution in policy-
controlled systems: Here, a security policy is a pre-
cise and unambiguous definition of rules, e. g. related
to isolation, access control, or information flow con-
trol mechanisms, which forms the backbone for re-
liable and correct enforcement of these rules. Conse-
quently, solving the problem of verification inevitably
requires to formally analyze precisely that backbone
(a security model) for properties such as policy con-
sistency, information flow leaks, or potential prolifer-
ation of privileges.
Considering the importance of such security prop-
erties, the fundamental safety undecidability result
has been relevant since its first presentation in (Har-
rison et al., 1976). The seminal HRU model for
dynamic access control systems is introduced there,
along with the safety property describing potential
proliferation (also known as leakage) of privileges.
Informally, a snapshot of an access control system
is considered safe with respect so some privilege if
and only if no future modification to that snapshot is
able to allow an access using the privilege in question,
which was not allowed in the initial snapshot.
Given its critical nature, the proof of undecid-
ability of this problem in (Harrison et al., 1976) led
to massive efforts in reducing a model’s complexity
and thus expressive power in a least-obstructive way
(Sandhu, 1988; Sandhu, 1992; Stoller et al., 2011;
Ferrara et al., 2013; Ranise et al., 2014; Shahen et al.,
2015). Most related work in this area features models
decidable with respect to a restricted flavor of HRU
safety which, being constructed with a specific appli-
cation domain in mind, completely satisfies the se-
mantic needs of that domain’s policies. However,
since all these models significantly differ in their se-
mantics, analysis algorithms derived for them are usu-
ally not applicable to other policy domains, which in
turn need to be built from scratch. Because of the
huge semantic gap between an informal policy and
the formalized model, this is an error-prone process.
Our current work aims at overcoming this prob-
lem. Instead of restricting a model’s expressive
power to achieve a decidable flavor of safety, our
approach accepts the impossibility of confirming a
safe model. We instead try to confirm the critical
case of safety violation in unrestricted HRU models
(which is possible due to the actual semi-decidable
nature of the problem). This is done in an approx-
imative, heuristics-based approach resulting in the
DEPSEARCH (DS) algorithm (Amthor et al., 2013).
To apply this approach to a broader range of models,
384
Amthor, P.
Efficient Heuristic Safety Analysis of Core-based Security Policies.
DOI: 10.5220/0006477103840392
In Proceedings of the 14th International Joint Conference on e-Business and Telecommunications (ICETE 2017) - Volume 4: SECRYPT, pages 384-392
ISBN: 978-989-758-259-2
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

we have merged it with two generalized modeling pat-
terns (core-based modeling (K
¨
uhnhauser and P
¨
olck,
2011; P
¨
olck, 2014) and entity labeling (Amthor,
2015; Amthor, 2016)). The resulting f DS framework
allows to tailor heuristic safety analysis to a multitude
of policy semantics beyond traditional HRU (Amthor,
2017).
However, despite promising first results, our
safety analysis algorithms still expose weaknesses
with respect to both heuristic effectivity and effi-
ciency. Based on our previous work and some criti-
cal observations made there, the goal of this paper is
to take the next step towards practice by presenting
f DS++, an optimized framework for safety analysis
based on DEPSEARCH. In details, we have identified
and solved the following weaknesses:
1. Inefficient heuristic for state-space exploration,
leading to a significant portion of ineffective
heuristic steps;
2. Negligence of static model properties influencing
unsafety-satisfiability, which effectively allows to
identify known-safe policies and to avoid heuris-
tic analysis where unnecessary;
3. Lack of support for parameter assignment algo-
rithms (which contribute to an efficient state space
traversal) based on static dependency analysis.
We have specified these improvements and imple-
mented the resulting algorithms tailored to SELX, an
access control model for the SELinux operating sys-
tem (Amthor, 2015) (Section. 4). As a preliminary
proof-of-concept validation that complements ongo-
ing experimentation, we outline an exemplary anal-
ysis of an excerpt of the SELinux reference policy
(Section 5). Our results hint at a feasibility of the
generalized safety analysis approach in practice and
indicate the direction of ongoing and future work in
that field.
2 DYNAMIC SECURITY MODELS
The goal of this section is to introduce the core-based
modeling pattern by P
¨
olck (K
¨
uhnhauser and P
¨
olck,
2011; P
¨
olck, 2014) as a formal environment to de-
scribe our safety analysis approach. Here and for the
rest of this paper, we will use the following conven-
tions for formal notation:
|= is a binary relation between variable assign-
ments and formulas in second-order logic, where I |=
φ iff I is an assignment of unbound variables to values
that satisfies φ. In an unambiguous context, we will
write
h
x
0
,...,x
n
i
|= φ for any assignment of variables
x
i
in φ that satisfies φ. A logical formula assigned to
a variable is delimited by [[ ]]. We will mark fixed
values referenced from outside the formula by under-
lining, e.g. a fixed x in an expression φ = [[ y = x ]].
B is the set of Boolean values > (true) and ⊥ (false).
In a directed graph
h
V,E
i
, E
in
v
denotes the set of in-
coming edges of a node v, while E
out
v
denotes its set
of outgoing edges.
The Model Core. To provide a uniform formal ba-
sis for safety definition and dynamic model analy-
sis, we use a generalization of the deterministic au-
tomaton introduced in HRU models. This automaton
serves as an abstract pattern used to define specialized
policies in a formally uniform calculus.
A core-based access control model is defined as
an automaton, the model core:
h
Q,Σ,δ,λ,q
0
, EXT
i
where Q is a set of protection states, Σ is a set of in-
puts, δ : Q × Σ → Q is the state transition function,
λ : Q × Σ → B is the output function, q
0
∈ Q is the
initial protection state, and EXT is an arbitrary tuple
of static model extensions.
The model core is tailored to a domain-specific se-
curity policy by defining Q (a system’s dynamic pro-
tection state) and EXT (static portion of the policy).
To describe protection state dynamics for a particu-
lar policy, the state transition function δ is defined via
pre- and post-conditions of any possible state transi-
tion. This is done by comparing each input of the
automaton with two formulas in second-order logic,
PRE and POST. We then define δ by formally spec-
ifying the conditions that each pair of states q and q
0
has to satisfy w.r.t. an input σ ∈ Σ for a state transition
from q to q
0
to occur:
δ(q,σ) =
q
0
,
h
q,σ
i
|= PRE ∧
h
q
0
,σ
i
|= POST
q, otherwise.
Because an access control system is fundamentally
deterministic, POST requires that q
0
equals q where
not redefined. In practice, PRE and POST are di-
vided into commands that match particular interface
calls of the modeled system: For any command
cmd ∈ Σ
C
, PRE(cmd) denotes the partial, command-
specific pre-condition of cmd and POST(cmd) its
post-condition. The AC system’s interface is then
modeled by Σ = Σ
C
× Σ
Y
, where Σ
C
is a set of
command identifiers and Σ
Y
contains sequences
of possible values (actual command parameters)
for variables in PRE and POST. Corresponding to
Σ
Y
, Σ
X
is a set of formal command parameters,
i. e. variable names used in PRE and POST. An
engineering-friendly, conventional notation of δ
is then based on partial definitions for each input
command: We call the set of such partial definitions
Efficient Heuristic Safety Analysis of Core-based Security Policies
385

∆ = {
h
cmd,x
cmd
,PRE(cmd),POST(cmd)
i
|cmd ∈
Σ
C
;x
cmd
∈ Σ
X
;PRE(cmd),POST(cmd) ∈ B} a
model’s state transition scheme, a specification of the
behavior of δ.
In the core-based pattern, a HRU model is defined
as
h
Q,Σ,δ,λ,q
0
,
h
R
ii
, with a protection state defined
as q =
S
q
,O
q
,acm
q
∈ Q. We call R the set of ac-
cess rights, S
q
the subjects set, O
q
the objects set, and
acm
q
: S
q
×O
q
→ 2
R
the access control matrix of state
q, the latter defining authorization rules in form of
Lampson’s ACM (Lampson, 1971). The notation of
a simple example command delegateRead of an HRU
model’s state transition scheme is shown in Fig. 1.
I delegateRead(s
1
,s
2
,o) ::=
PRE: read right ∈ acm
q
(s
1
,o) ;
POST: acm
q
0
(s
2
,o) = acm
q
(s
2
,o) ∪{read right}
Figure 1: Exemplary command definition for a core-
based HRU model: delegateRead with parameters
h
s
1
,s
2
,o
i
models delegation of read right regarding o by s
1
to
s
2
. PRE(delegateRead) requires that s
1
possesses this
right for a state transition by this command to occur,
POST(delegateRead) requires s
2
to do so afterwards.
3 SAFETY ANALYSIS
In this section, we discuss the basic idea of heuris-
tic safety analysis. We will outline our most analysis
strategy, DEPSEARCH, along with the algorithm for
HRU safety analysis. This will be the foundation for
a subsequent discussion of algorithmic optimizations.
We start by defining the notion of privilege prolifera-
tion introduced by HRU safety:
As formalized for the HRU model, the safety
of a system fundamentally addresses such questions:
Given a protection state of an HRU model, is it pos-
sible that some subject ever obtains a specific right
with respect to some object? If this may happen,
such a model state is considered unsafe with respect
to that right. An intuitive definition of this question,
(r)-simple-safety, has been presented by Tripunitara
and Li (Tripunitara and Li, 2013):
Definition 1. Given a core-based HRU model
h
Q,Σ,δ,λ,q
0
,
h
R
ii
, a state q =
S
q
,O
q
,acm
q
∈ Q is
(r)-simple-unsafe with respect to a right r ∈ R iff
∃q
0
=
S
q
0
,O
q
0
,acm
q
0
∈ {δ
∗
(q,a)|a ∈ Σ
∗
}:
∃s ∈ S
q
0
,∃o ∈ O
q
0
: r ∈ acm
q
0
(s,o)
∧
s /∈ S
q
∨ o /∈ O
q
∨ r /∈ acm
q
(s,o)
where δ
∗
: Q ×Σ
∗
→ Q is the transitive state transition
function defined as δ
∗
(q,σ ◦ b) = δ
∗
(δ(q,σ),b) and
δ
∗
(q,ε) = q for any σ ∈ Σ ∪ {ε},b ∈ Σ
∗
.
As per this definition, safety always relates to both
a specific model state q to analyze (in practice, this is
a momentary configuration of the system in question)
and a specific access right r whose proliferation we
are interested in. We call this r, being the source of
an HRU model’s authentication mechanics, a safety
analysis target.
Heuristic State-Space Exploration. In order to
handle the undecidability of HRU safety, we choose
to trade accuracy for tractability: using a heuristic,
unsafe model states may be found (given such exist),
while termination of the algorithm cannot be guaran-
teed. The idea of heuristic safety analysis thus lever-
ages the semi-decidability of the problem. On the
plus side, valuable hints on model correctness are ob-
tained if unsafe states are found and policy engineers
are pointed to input sequences that lead to such states.
The strategy behind heuristic safety analysis al-
gorithms is to find an input sequence that, starting at
q, enters r into a matrix cell of some follow-up state
q
target
. When this happens, q is proven to be unsafe
with respect to r; as long as no such target state is
found, the search continues. A successful heuristic
must therefore maximize the probability of an input
to contribute to a path from q to q
target
.
The DEPSEARCH Approach. We developed DS
based on the insight that in the most difficult case,
right leakages in a model appear only after specific
state transition sequences where each command ex-
ecuted depends exactly on the execution of its pre-
decessor. From this observation we derived the idea
of a two-phases algorithm: First, a static analysis of
inter-command dependencies is performed; a subse-
quent, dynamic analysis consists of state space explo-
ration by simulating the automaton’s behavior. We
will discuss these phases on an informal basis, for an
in-depth discussion and evaluation of DS for HRU see
(Amthor et al., 2013; Amthor et al., 2014).
During the first phase, a static analysis of the
HRU state transition scheme is performed. It yields a
graph-based description of inter-command dependen-
cies, constituted by entering (as a part of POST) and
requiring (part of PRE) the same right in two differ-
ent commands. As a result of the static analysis, these
dependencies are modeled by a command dependency
graph (CDG)
h
V,E
i
where nodes c
1
,c
2
∈ V represent
commands, and an edge
h
c
1
,c
2
i
denotes that a post-
condition of c
1
matches at least one pre-condition of
c
2
. An example of a CDG is depicted in Fig. 2.
The CDG is assembled in a way that all paths from
vertices without incoming edges to vertices without
outgoing edges indicate input sequences for reaching
SECRYPT 2017 - 14th International Conference on Security and Cryptography
386

q
target
from q. To achieve this, two virtual commands
c
q
and c
target
are generated: c
q
is the source of all
paths in the CDG, since it represents the state q to
analyze in terms of a command specification added to
∆. It is generated by encoding acm
q
in POST(c
q
). In
a similar manner, c
target
is the sink of all paths in the
CDG, which represents all possible states q
target
by
checking the presence of the target right in any matrix
cell in PRE(c
target
).
In the second, dynamic analysis phase, the CDG
is used to guide dynamic state transitions by generat-
ing input sequences to the automaton. The commands
involved in each sequence are chosen according to
different paths from c
q
and c
target
, which in turn de-
termine the direction of state space exploration. Paths
in the CDG are generated based on a simple ant al-
gorithm: with each edge traversed to generate an in-
put sequence, the algorithm increases an edge weight
“scent” which has repellent effect for the next itera-
tion of the CDG traversal, thus effectively leading to
a full path coverage and potentially maximal chances
for actually generating a right leakage.
DS successively generates input sequences by
traversing the CDG on every possible path and in
turn parameterizing the emerging sequence of com-
mands with values from Σ
Y
. Each effected state tran-
sition is simulated by the algorithm, and once a CDG
path is completed, the unsafety-criteria (cf. Def. 1) is
checked.
4 f DS IMPROVEMENTS
Three major problems affecting both efficiency and
effectivity of the original DS have become evident
during its usage:
Efficient State-Space Exploration: DS uses an ant
algorithm for CDG path generation, which ultimately
determines efficiency and effectivity of state-space
exploration. As a closer look on more complex state
transition schemes reveals, its partially randomized
strategy is not optimal, possibly resulting in high rates
of unsatisfiable simulation paths for such CDGs.
Static Satisfiability Analysis: A mere dependency
analysis does not exploit particular static properties
of a state transition scheme leading to leakage-free
policies, which we call unsafety-unsatisfiable (i. e.
provable safe). An intuitive example indicating an
unsafety-unsatisfiable state transition scheme is the
existence of cycles in the CDG.
Parameter Dependency Analysis: The assignment
of state-specific values to parameters in the state tran-
sition scheme is a highly policy-specific task. How-
ever, since the inference of command sequences from
mutual execution dependency as one portion of the
automaton’s input proved a successful idea, we expect
significant improvements during the dynamic analysis
phase by restricting the domain of possible parameter
values in a similar manner.
The original DS was restricted to HRU models. In
(Amthor, 2017), we generalized the approach to f DS,
which can be tailored to a wide range of core-based
models using generic interfaces. We have shown this
principle based on the SELinux model SELX. How-
ever, since f DS does not yet address the above effi-
ciency problems, we will discuss them more detailed
in the following and present solution proposals.
4.1 Efficient State-space Exploration
In f DS, state space exploration is driven by input se-
quences generated by the heuristic. These sequences
are controlled by the CDG, which is successively tra-
versed with the goal of maximum path diversity in
mind; however, this strategy disregards the influence
of path ordering. In a worst-case dependency situa-
tion, where each command requires execution of all
predecessors (i. e., each incoming edge of each CDG
node stands for a different dependency), this may lead
to the traversal algorithm not generating a minimal se-
quence of paths, but preferring redundant or unsatisfi-
able paths over necessary ones. The reason for this is
the initially equal chance for all in-edges of c
target
to
be chosen; the algorithm does not state any determin-
istic criteria for preferring one of them.
Consider the example in Fig. 2. Based on the par-
ticular order of choosing between equally-weighted
edges, the minimal number of paths needed to exe-
cute c
6
varies from 2 to 5 (unsatisfiable commands in
parentheses):
optimal: c
q
→ c
1
→ c
2
→ c
4
→ (c
6
→ c
t
)
c
q
→ c
1
→ c
3
→ c
5
→ c
6
→ c
t
worst case: c
q
→ c
1
→ (c
4
→ c
6
→ c
t
)
c
q
→ c
1
→ (c
6
→ c
t
)
c
q
→ c
1
→ (c
5
→ c
6
→ c
t
)
c
q
→ c
1
→ c
2
→ c
4
→ (c
6
→ c
t
)
c
q
→ c
1
→ c
3
→ c
5
→ c
6
→ c
t
In order to prioritize such paths more likely to
be executed, nodes with low in-degree in the CDG
should be traversed before such with higher in-degree.
This leads to paths whose dependencies can be satis-
fied early on, and which thus produce more successful
state transitions.
Solution. Our modified algorithms for path genera-
tion (Alg. 1) and CDG assembly (Alg. 2) adapt edge
weights (“scents”) according to the above idea:
Efficient Heuristic Safety Analysis of Core-based Security Policies
387

Algorithm 1: f DS++::CDGPathGeneration
Input:
h
V,E
i
. . . CDG as generated by Alg. 2
d,
ˆ
d . . . edge weighting/increment
function of
h
V,E
i
c
q
. . . CDG source node
Output: path . . . path in the CDG
d . . . modified edge weights
function lowestScent(in E
v
⊆ E)
e
min
← E
v
.someMember;
minw ← d(e
min
);
for e
v
∈ E
v
do
if minw > d(e
v
) then
e
min
← e
v
;
minw ← d(e
min
);
return e
min
;
v ← c
q
, path ← v;
repeat
h
u,v, i
i
← lowestScent(E
out
v
);
path ← path ◦ v;
(1) d(
h
u,v, i
i
) ← d(
h
u,v, i
i
) +
ˆ
d(
h
u,v, i
i
);
until E
out
v
=
/
0;
return path, d;
Algorithm 2: f DS++::CDGAssembly
Input: ∆ . . . model’s state transition scheme
Output:
h
V,E
i
. . . command dependency
graph
d,
ˆ
d : E → N . . . edge
weighting/increment function
c
q
. . . CDG source node
procedure predecessors(in v ∈ V )
(3) (c) P ← buildPredSet(∆,v);
for
h
c,i
i
∈ P do
if c /∈ V then
V ← V ∪ {c};
predecessors(c);
E ← E ∪ {
h
c,v, i
i
};
(1) d(
h
c,v, i
i
) ← |P|;
(2)
ˆ
d(
h
c,v, i
i
) ← |P|;
(d) c
q
← createCDGSource(q);
(e) c
target
← createCDGSink(target);
∆ ← ∆ ∪ {c
q
};
V ← {c
target
};
E ←
/
0;
predecessors(c
target
);
return
h
V,E
i
,d,
ˆ
d,c
q
;
c1 c3
cq
c2
c4 c5
c6
c
target
Figure 2: A CDG to illustrate the path generation problem.
The edge weighting function d is initialized on
CDG assembly, where the cardinality of each node’s
set of predecessors determines the weight of all its
incoming edges (see Alg. 2, line (1)). During path
generation, edge weights serve as “scents” as usual,
while an additional increment function
ˆ
d is used to
modify them when passing an edge (Alg. 1, line (1)).
Setting an edge increment to the respective edge’s ini-
tial weight during CDG assembly (Alg. 2, line (2))
ensures that the intended traversal frequency is main-
tained for the rest of the dynamic analysis.
In order to satisfy as many dependencies as possi-
ble as early as possible, it is advantageous for Alg. 1
to traverse the CDG in direction of its edges, starting
at c
q
(instead of in reverse, starting with c
target
).
4.2 Static Satisfiability Analysis
For policies with a leakage-free state transition
scheme, safety might be statically inferred from
reachability properties of the CDG (e. g. indicating
cyclic dependencies); however, the current definition
of the CDG does not allow this: Semantics of an edge
h
c
1
,c
2
i
only denote that “c
1
establishes at least one
condition necessary for executing c
2
” (cf. (Amthor
et al., 2013)) – but not how many and which particular
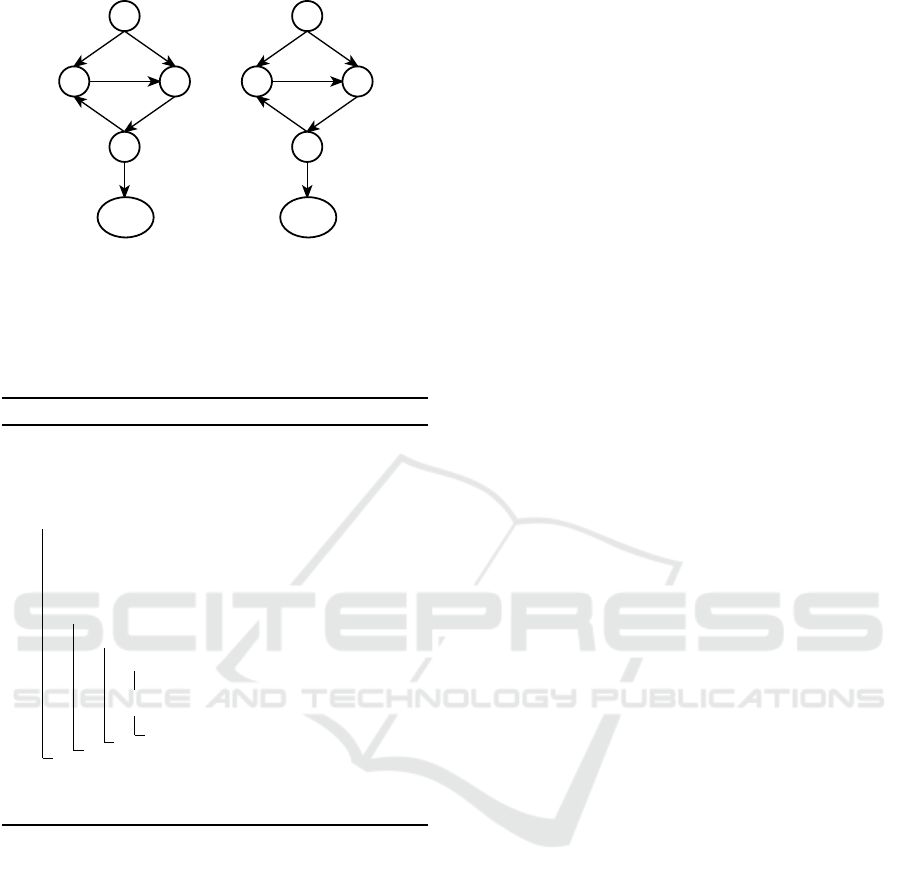
conditions. Fig. 3(b) shows an HRU-based example
of such a graph, with the specific rights that establish
the respective dependency added to each edge.
As indicated above, unsatisfiable dependencies
can be statically identified by refining edge semantics
in the CDG. For this we use an edge-colored multi-
graph
h
V,E
i
,E = V ×V × N, where
h
u,v, i
i
∈ E ⇔ u
establishes a precondition of v whose color is i. In
HRU for example, 1 ≤ i ≤ |R| would cover all possible
precondition colors (matching HRU rights). In SELX,
assuming (t)-safety (Amthor, 2017), colors 1 ≤ i ≤ |T |
match SELinux types.
We will now define potential satisfiability of a
CDG as a goal of static satisfiability analysis: Using
this definition, a costly, heuristic state-space explo-
ration can be avoided for such state transition schemes
SECRYPT 2017 - 14th International Conference on Security and Cryptography
388
c3
cq
r1r4
r1
r2r4, r5
rt
c1
c2
c
target
(a) potentially satis-
fiable
c3
cq
r1r4
r3
r2r4, r5
rt
c1
c2
c
target
(b) unsatisfiable
Figure 3: Fine-grained edges semantics for CDG satisfiabil-
ity analysis: In case (a), conditions of c
1
may be satisfied by
c
q
, while in case (b), c
1...3
all depend on each other’s prior
execution in a cycle.
Algorithm 3: f DS++::unsatisfiable
Input: CDG =
h
V,E
i
Output: > if CDG is unsatisfiable; ⊥ if CDG
is potentially satisfiable
function isPSat(in v ∈ V )
if v = c
q
then return > ;
if v ∈ H then return ⊥ ;
H ← H ∪ {v};
for
h
u,v, i
i
∈ E
in
v
do
for
h
u
0
,v, j
i
∈ E
in
v
do
if i = j then
return isPSat(u) ∨ isPSat(u
0
)
else
return isPSat(u) ∧ isPSat(u
0
)
H ←
/
0;
return ¬ isPSat(c
target
);
which do not allow for c
target
to be reachable under
any dynamic conditions.
Definition 2. Potential Satisfiability of a CDG:
1. A CDG node v is potentially satisfiable iff ∀u,u
0
∈
V,{
h
u,v, i
i
,
h
u
0
,v, j
i
} ⊆ E
in
v
:
i = j ⇒ u is potentially satisfiable
∨ u
0
is potentially satisfiable
i 6= j ⇒ u is potentially satisfiable
∧ u
0
is potentially satisfiable.
2. c
q
is potentially satisfiable.
3. A CDG is potentially satisfiable iff c
target
is poten-
tially satisfiable.
Solution. To implement our extended CDG defini-
tion, we had to modify CDG assembly: the func-
tion buildPredSet (Alg. 2, line (3)) now returns a set
of command-color-pairs, allowed to include multiple
pairs for the same predecessor command. For a core-
based model with variables set Var, it is defined as
buildPredSet
SELX
(∆,c
succ
) = {
c
pred
∈ ∆,i ∈ N
|
∃x
i
∈ Var : PRE(c
succ
) and POST(c
pred
) depend on
the assignment of x
i
}
where Var is defined as the set of variables in the state
transition scheme, which are used as formal parame-
ters of some command. It holds Σ
X
= Var
∗
.
As per CDG construction, there is a path from
each node to c
target
. This implies we can check the
conditions in Def. 2 in a backwards-depth-first search,
starting from c
target
. Based on this strategy, our static
satisfiability analysis is implemented in Alg. 3 and
called right before the dynamic analysis phase in
Alg. 5, line (1).
4.3 Parameter Dependency Analysis
In order to assist a model-specific parameter selec-
tion heuristic, domains of possible values for parame-
ter variables should be as small as possible. This can
also be achieved by a more fine-grained static depen-
dency analysis: Parameter selection can be mapped
to a constraint satisfaction problem (CSP), and thus
tackled by a CSP solver algorithm. If we take a basic
arc consistency algorithm such as AC-3 (Mackworth,
1977), an additional data structure is needed to repre-
sent variables, domains, and constraints of the CSP:
the parameter constraints network (PCN).
The PCN is defined as an undirected,
bipartite, and node-labeled graph PCN =
h
V ∪ Cons,E ⊆ V × Cons,DOM
i
where V ⊆ Var
is a set of variables, Cons is a set of constraints
(logical formulas), and DOM = {dom
k
: Var
k
→
2
Val
k
|1 ≤ k ≤ K} is a set of domain-labeling func-
tions for each variable. Here, Val is the set of all
possible values that could be assigned to a parameter,
corresponding to Var. It also constitutes Σ
Y
= Val
∗
in a core-base model; for HRU e. g. Val = S ∪ O, for
SELX Val = E ∪ C ∪ P ∪ U ∪ R ∪ T . K denotes the
number of value domains, which is derived from the
number of basic sets for values: for HRU it holds
K = 2, for SELX K = 6.
Solution. The PCN is assembled by subdividing
edges in the CDG, als specified in Alg. 4. We initial-
ize our PCN with empty sets, and iteratively extend it
by transforming each edge
h
c
1
,c
2
,i
i
in the CDG into
a number of constraint nodes (line (1)): one for each
precondition in c
2
that matches CDG edge color i.
Each such constraint is a disjunctive formula includ-
ing one clause for each potentially i-satisfying state
Efficient Heuristic Safety Analysis of Core-based Security Policies
389

Algorithm 4: f DS++::PCNAssembly
Input: CDG =
h
V
CDG
,E
CDG
i
Output: PCN =
h
V ∪ Cons,E, DOM
i
V ←
/
0, Cons ←
/
0, E ←
/
0,DOM ←
/
0;
(6) for 1 ≤ k ≤ K do
(1) for
h
c
1
,c
2
,i
i
∈ E
CDG
do
P
k
src
← {x ∈ Var
k
|
POST(c
1
) depends on x and i};
P
k
sink
← {x ∈ Var
k
|
PRE(c
2
) depends on x and i};
for x ∈ P
k
sink
do
if x /∈ V then
dom
k
(x) ← Val
k
;
(3) V ← V ∪ {x};
exp ← [[⊥]];
for x
0
∈ P
k
src
do
(2) exp ← [[exp ∨ (x = x
0
)]];
(4) E ← E ∪ {
h
x
0
,exp
i
};
(5) E ← E ∪ {
h
x,exp
i
};
Cons ← Cons ∪ {exp};
DOM ← DOM ∪ {dom
k
};
return
h
V ∪ Cons,E, DOM
i
;
manipulation in POST(c
1
), which is iteratively as-
sembled in line (2). We then add all variables in these
formulas as nodes to the PCN (line (3)), each con-
nected with the previously created constraint nodes
(lines (4), (5)) according to arc consistency semantics.
To clearly separate and thus minimize the different
domains of variables, the whole process is repeated
for each domain (line (6)).
During dynamic analysis, right before a command
sequence is attempted to be executed, we run the CSP
solver on the PCN, yielding a (possibly pruned) do-
main for each variable x which in turn modifies the
initial PCN for the next iteration. We then select
an assignment for each variable based on a policy-
specific heuristic. We have abstracted this policy-
specific parameter assignment heuristic, which is as-
sumed to call a CSP solver as a subroutine, through
the interface assignParams (Alg. 5, line (2)).
4.4 f DS++ Heuristic
In Alg. 5, we have specified the improved f DS++ al-
gorithm, using Algs. 2, 3, 4, and 1. Arabic labels
in the algorithms denote references throughout this
chapter, while latin labels indicate abstract interfaces
that must be implemented based on the particular
core-based/EL model to analyze: assignParams (a)
implements a parameter assignment heuristic, which
is based on a momentary state, a command sequence
Algorithm 5: f DS++
Input: δ . . . model’s state transition function
∆ . . . model’s state transition scheme,
specifying δ
q
0
. . . model state to be analyzed
target . . . leakage target
Output: seq . . . states sequence leaking target
q ← q
0
, seq ← ε;
CDG,d,
ˆ
d,c
q
← CDGAssembly(∆,q,target);
if unsatisfiable(CDG) then
return seq;
else
seq ← q;
PCN ← PCNAssembly(CDG);
repeat
h
path,d
i
←
CDGPathGeneration(CDG,d,
ˆ
d,c
q
);
(2) (a)
h
assignment, PCN
i
←
assignParams(q,path, PCN);
while c ← path.nextNode do
q
0
← δ(q,c,assignment(c));
seq ← seq ◦ q
0
;
q ← q
0
;
until(b) isLeaked(q
0
,q
0
,target);
return seq;
to be executed, and a PCN defining domains of pos-
sible values for each variable used as a parameter
in the input command sequence. It returns an as-
signment function for these parameters and a mod-
ified PCN with updated (and thus minimized) do-
mains. isLeaked (b) implements a safety definition
(e. g. Def. 1), which is evaluated to a boolean value
based on some initial state, some reached state to
check for a leakage, and target. buildPredSet (b)
checks model-specific dependencies in ∆ to return the
set of predecessor nodes, along with their respective
dependency color, based on some given node in the
CDG. createCDGSource (d) creates a definition of c
q
based on q
0
. createCDGSink (e) creates a definition
of c
target
based on target.
(Amthor, 2017) shows how to implement these in-
terfaces based on the example of SELX.
5 ONGOING EVALUATION
This section describes ongoing and future work re-
garding an experimental evaluation of f DS++. Us-
ing SELX-implementations of the interfaces listed in
Sec. 4.4, we have implemented Alg. 5 and performed
an exemplary (t)-safety analysis of an SELinux policy
excerpt as a first proof-of-concept application.
SECRYPT 2017 - 14th International Conference on Security and Cryptography
390

One major prerequisite for applying the heuristic
is model instantiation. Here, we have reused existing
tools and methods for extracting both an initial state
space and static policy rules. These methods are de-
scribed in detail in (Amthor, 2016) and include (1) a
file system crawler that extracts protection state infor-
mation from a file system of a virtual machine snap-
shot, (2) a policy scanner, which parses the SELinux
policy specification language and produces a SELX
model implementation, (3) a simulation runtime envi-
ronment (WorSE, cf. (Amthor et al., 2014)) that im-
plements the automaton’s state transition scheme.
We specified our state transition scheme using
SELX basic commands, as described in (Amthor,
2016), which led to a expectable, trivial CDG consist-
ing solely of create and relabel. Composing these ba-
sic commands and taking into account other than only
type-dependencies leads to a more complex graph.
Note that in this specific analysis scenario, inter-
command dependencies are solely type variables –
leading to a runtime-specific CDG, whose dynamic
reanalysis has not been subject of our heuristic yet (as
already pointed out in Sec. 4.2).
Moreover, focusing on rather complex policy se-
mantics as in SELinux emphasizes the impact of mul-
tiple dependency classes: in SELX these are, for ex-
ample, type-, role-, class-, or user-dependency, all
of which must be represented in the CDG. For the
sake of clearly implementing and presenting the al-
gorithmic concepts, we have so far opted for a one-
dimensional solution, taking into account solely type-
dependencies. Since our approach is approximative,
this delivers valid results, yet open to further opti-
mization in terms of fine-grained policy semantics.
Both problems, dynamic CDGs and complex de-
pendencies, indicate the direction of our future re-
search in heuristic safety analysis. The immediate
next step, an experimental, comparative evaluation
of the improvements of f DS++ in terms of heuristic
steps count and heuristic runtime, is subject ongoing
work regarding practical systems analyses.
6 CONCLUSIONS
In this paper, we have presented solutions to three
open problems with heuristic safety analysis: First,
we identified an efficiency-enhanced path generation
scheme for state-space exploration, which prefers
such commands with less dependencies required to be
executed, and derived an edge-weighting scheme for
its implementation. Second, we defined the unsafety-
unsatisfiability property of a state transition scheme
in terms of command reachability (which also means
potential executability). We then specified an algo-
rithm for a static analysis that may identify policies
satisfying this property as safe, eliminating the need
for a heuristic simulation in such cases. Third, a
static support algorithm for model-specific parame-
ter assignment heuristics was described. The idea is
basically identical to that of inter-command depen-
dencies, which is implemented leveraging a constraint
satisfaction problem solver (an arc consistency algo-
rithm was proposed for this).
As a proof of concept, we have presented practi-
cal insights given by an analysis of an SELinux se-
curity policy based on SELX, which pave the way for
current and future research focusing multiple depen-
dency classes in complex policies and dynamic com-
mand dependency graphs.
REFERENCES
Amthor, P. (2015). A Uniform Modeling Pattern for Oper-
ating Systems Access Control Policies with an Appli-
cation to SELinux. In Proc. 12th Int. Conf. on Security
and Cryptography, SECRYPT 2015, pp. 88–99.
Amthor, P. (2016). E-Business and Telecommunications:
12th Int. Joint Conf., ICETE 2015, Colmar, France,
July 20–22, 2015, Revised Selected Papers, chapter
The Entity Labeling Pattern for Modeling Operating
Systems Access Control, pp. 270–292. Springer.
Amthor, P. (2017). Towards a Uniform Framework for
Dynamic Analysis of Access Control Models. In
Proc. 10th International Symposium on Foundations
& Practice of Security, FPS 2017. (under review)
Amthor, P., K
¨
uhnhauser, W. E., and P
¨
olck, A. (2013).
Heuristic Safety Analysis of Access Control Mod-
els. In Proc. 18th ACM Symposium on Access Control
Models and Technologies, SACMAT ’13, pp. 137–
148. ACM.
Amthor, P., K
¨
uhnhauser, W. E., and P
¨
olck, A. (2014).
WorSE: A Workbench for Model-based Security En-
gineering. Computers & Security, 42(0):40–55.
Ferrara, A. L., Madhusudan, P., and Parlato, G. (2013). Pol-
icy Analysis for Self-administrated Role-Based Ac-
cess Control. In Piterman, N. and Smolka, S. A., ed-
itors, Tools and Algorithms for the Construction and
Analysis of Systems, vol. 7795 of LNCS, pp. 432–447.
Springer.
Harrison, M. A., Ruzzo, W. L., and Ullman, J. D. (1976).
Protection in Operating Systems. Communications of
the ACM, 19(8):461–471.
Kleiner, E. and Newcomb, T. (2007). On the Decidabil-
ity of the Safety Problem for Access Control Poli-
cies. Electronic Notes in Theoretical Computer Sci-
ence (ENTCS), 185:107–120.
K
¨
uhnhauser, W. E. and P
¨
olck, A. (2011). Towards Access
Control Model Engineering. In Proc. 7th Int. Conf. on
Information Systems Security, ICISS’11, pp. 379–382.
Efficient Heuristic Safety Analysis of Core-based Security Policies
391

Lampson, B. W. (1971). Protection. In 5th Ann. Princeton
Conf. on Information Sciences and Systems, pp. 437–
443. Reprinted Jan, 1974: Protection. In Operating
Systems Review, 8(1), pp. 18–24.
Mackworth, A. K. (1977). Consistency in Networks of Re-
lations. Artificial Intelligence, 8(1):99–118.
P
¨
olck, A. (2014). Small TCBs of Policy-controlled Operat-
ing Systems. Universit
¨
atsverlag Ilmenau.
Ranise, S., Truong, A., and Armando, A. (2014). Scalable
and precise automated analysis of administrative tem-
poral role-based access control. In Proc. 19th ACM
Symposium on Access Control Models and Technolo-
gies, SACMAT ’14, pp. 103–114. ACM.
Sandhu, R. (1988). The Schematic Protection Model:
Its Definition and Analysis for Acyclic Attenuating
Schemes. Journal of the ACM, 35(2):404–432.
Sandhu, R. S. (1992). The Typed Access Matrix Model. In
Proc. 1992 IEEE Symposium on Security and Privacy,
SP ’92, pp. 122–136. IEEE.
Shahen, J., Niu, J., and Tripunitara, M. (2015). Mohawk+T:
Efficient Analysis of Administrative Temporal Role-
Based Access Control (ATRBAC) Policies. In Proc.
20th ACM Symposium on Access Control Models and
Technologies, SACMAT ’15, pp. 15–26. ACM.
Stoller, S. D., Yang, P., Gofman, M., and Ramakrishnan,
C. R. (2011). Symbolic Reachability Analysis for Pa-
rameterized Administrative Role Based Access Con-
trol. Computers & Security, 30(2-3):148–164.
Tripunitara, M. V. and Li, N. (2013). The Foundational
Work of Harrison-Ruzzo-Ullman Revisited. IEEE
Trans. Dependable Secur. Comput., 10(1):28–39.
SECRYPT 2017 - 14th International Conference on Security and Cryptography
392
