
Hypergraph-based Access Control using Formal Language
Expressions – H GAC
Alexander Lawall
Institute for Information Systems at Hof University, Alfons-Goppel-Platz 1, 95028 Hof, Germany
Keywords:
Access Control, Attribute-based Access Control, Language Expressions, Organizational Model, Identity
Management.
Abstract:
In all organizations, access assignments are essential in order to ensure data privacy, permission levels and
the correct assignment of tasks. Traditionally, such assignments are based on total enumeration, with the
consequence that constant effort has to be put into maintaining the assignments. This problem still persists
when using abstraction layers, such as group and role concepts, e.g. Access Control Matrix and Role-Based
Access Control. Role and group memberships are statically defined and members have to be added and
removed constantly. This paper describes a novel approach – Hypergraph-Based Access Control H GAC
– to assign human and automatic subjects to access rights in a declarative manner. The approach is based
on an organizational (meta-) model and a declarative language. The language is used to express queries
and formulate predicates. Queries define sets of subjects based on their properties and their position in the
organizational model. They also contain additional information that causes organizational relations to be active
or inactive depending on predicates. In H GAC, the subjects that have a specific permission are determined
by such a query. The query itself is not defined statically but created by traversing a hypergraph path. This
allows a structured aggregation of permissions on resources. Consequently, multiple resources can share parts
of their queries.
1 INTRODUCTION
Nowadays, companies have to deal with permanent
change. Subjects (e.g. human actors, machines, print-
ers, etc.) join, leave or move within the organiza-
tion. The rearrangement of whole departments is also
common. Therefore, the flexibility of the organiza-
tional structure is essential to react to such changes,
cf. (Vahs, 2007). Otherwise, the organization risks to
lose their partners, e.g. deliverers and customers, and
elimination from the market, cf. (Krcmar, 2010).
The organizational structure is currently shaped
by work in project teams, global teams, networks
and global teams in networks (cf. (Krcmar, 2010)).
(Lawall et al., 2014b) formalizes a metamodel for
modeling arbitrary organization structures that pro-
vides the required flexibility and complexity.
Access assignments have to be appropriate to poli-
cies that are declared in the company, cf. (Ferrari,
2010, p. 4). Consequently, the validity of rela-
tions has to be restricted to realize these policies, cf.
(Lawall et al., 2014d). This is fulfilled by different
types of predicates assigned to the relations.
Language expressions restrict the validity based
on context information, parameters handed from ap-
plication systems and / or attributes of subjects re-
spectively resources in a company (cf. (Lawall et al.,
2014a)). Figure 3 shows an example of a restricted
relation based on parameters. The restricted relation
with the language expression damage > "1500" is
traversed if the parameter handed from the application
system corresponding to “damage” fulfills the predi-
cate.
A hyperedge in the organizational model – also
called hyper-relation – restricts a relation by role.
This means that a relation in the organizational model
is only traversed if an entity acts in the appropriate
role, cf. (Lawall et al., 2014d) and (Lawall et al.,
2014a). Figure 3 depicts a hyperedge between two
subjects and a role. The relation is traversed if the
origin subject acts in the role in that the hyperedge
ends in.
This contribution compares approaches for defin-
ing access assignments and establishes the novel
H GAC. The conjunction of three components
– organizational model, declarative language and
267
Lawall A..
Hypergraph-based Access Control Using Formal Language Expressions - HGAC.
DOI: 10.5220/0005484602670278
In Proceedings of 4th International Conference on Data Management Technologies and Applications (DATA-2015), pages 267-278
ISBN: 978-989-758-103-8
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

hypergraph-based access control – are a powerful
mechanism to declare access assignments that are sta-
ble over time and fit the organizational circumstances
and policies.
The formulated language expression (query) is
used to define the access assignments in application
systems. It defines policies of the company. Policies
do not change often, and neither does the expression.
Consequently, all application systems create no main-
tenance effort concerning access assignments after the
initial definition of the expressions. Every time a sub-
ject joins, leaves or moves within the company, only
logically centralized organizational model, cf. section
6, has to be changed. The application systems are not
affected.
Knorr describes in (Knorr, 2000) an approach to
assign access rights by workflows that are modeled
with petri nets. If a subject is assigned to a task in
a process, the subject automatically gets the rights to
objects needed to execute the task. The definition of
responsible subjects is done by role-based access con-
trol (RBAC). The approach is only valid in workflows.
All other application systems are excluded
1
.
Outline
In order to demonstrate widespread key issues, sec-
tions 2.1 and 2.2 describe the access control matrix
and the role-based access control.
Chapter 3 then introduces the novel approach
called hypergraph-based access control. After the
definition of hypergraphs an example of an organi-
zational model is described (section 3.1). Section 3.2
defines the formal specification of H GAC which is
explained by example in section 3.3.
The subsequent chapter 4 illustrates the proposed
declarative language with syntax (section 4.1) and se-
mantics (section 4.2). The language is used to declare
the subjects that are assigned to access rights.
The paper concludes with a case study (chapter 5)
and the overall conclusion of the contribution (chapter
6).
2 ACCESS CONTROL
For the definition of access rights exist different ap-
proaches. The following sections describe the access
control matrix (ACM) and the wide-spread role-based
access control (RBAC).
1
The approach is only suited for process-oriented organiza-
tional structures. The functional and divisional perspective is omit-
ted.
The basic model of access control consists gener-
ally of a tuple, cf. (Benantar, 2006, pp. 22) and (Fer-
rari, 2010, p. 6). It consists of sets S, R and O. The
set S includes all subjects substantiated by enumera-
tion and represents users and processes. The access
rights R , e.g. read, write for files and execute for
processes, are the operations on concrete objects of
the set O. The elements of O - files, processes, tables,
devices, and so on - are the objects on which subjects
have access rights.
“There is usually a direct relationship between
the cost of administration and the number of
associations that must be managed in order
to administer an access control policy: The
larger the number of associations, the costlier
and more error-prone access control adminis-
tration.” (Ferraiolo et al., 2003, p. 19)
A concrete access right Z is defined as Z = (s, r, o)
with s ∈ S , r ∈ R and o ∈ O. In general, there are two
variations to define access rights. All subjects have
all access rights on all objects except rights that are
explicitly revoked with tuples Z. Another concept is
that no subject has any access rights on any object
until the access right is explicitly defined. The second
case is the most used approach
2
.
2.1 Access Control Matrix – ACM
The basic idea of the access control matrix was intro-
duced in (Graham and Denning, 1972). The formal-
ization of (Saunders et al., 2001) and (Seufert, 2002)
is used to describe the access control matrix (ACM).
The configuration of a concrete access control ma-
trix is defined with ACM = (S, R , O, (R
t
)
s∈S,o∈O
)
3
.
The access control matrix (R
t
)
s∈S,o∈O
consists of el-
ements R
t
⊆ R , where subjects s ∈ S are represented
as rows and objects o ∈ O are represented as columns.
An entry R
t
in the matrix is the access right R
t
of sub-
ject s to object o (see figure 1).
A configuration in an application system (e.g.
workflow management systems, internet portals,
database management systems, enterprise resource
planning systems) with processes and files is given
with:
• S = {u1, u2, p1} is the set of users u1, u2 and pro-
cess p1
• R = {read, write, execute} is the set of rights for
processes (execute) and files (read, write)
• O = { f 1, f 2, f 3, p1, p2, p3} is the set of objects
with files and processes
2
This case is used in the remaining paper.
3
t indicates the point of time of a configuration in a system.
DATA2015-4thInternationalConferenceonDataManagementTechnologiesandApplications
268
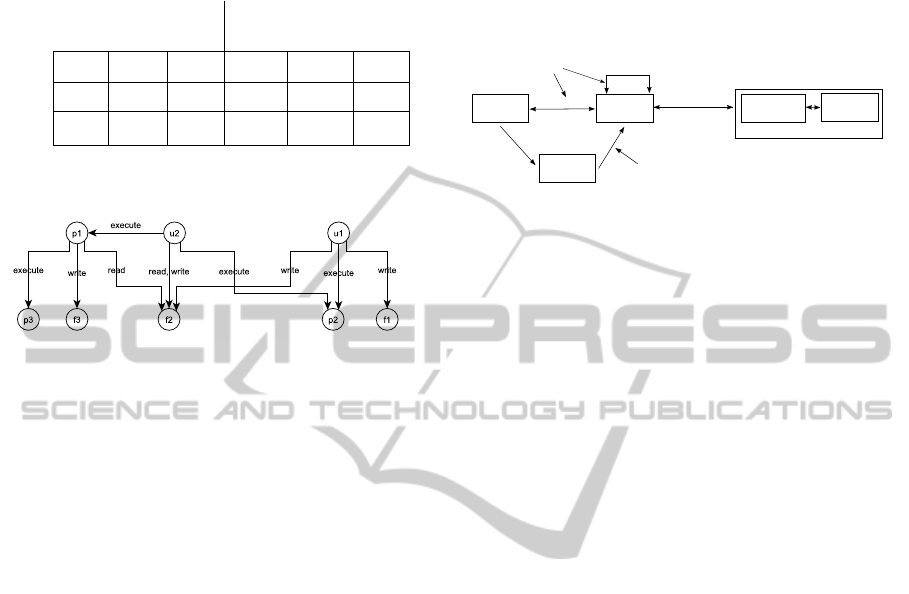
• (R
t
)
s∈S,o∈O
is represented as figure 1a respec-
tively figure 1b
{execute}
objects
subjects
processes
files
f1 f2 f3 p1 p2 p3
u1
u2
p1
{write}
{read} {write}
{execute}
{read,
write}
{execute} {execute}
{write}
(a) Configuration of an Access Control Matrix (cf. (Seufert,
2002))
(b) Access Control Matrix as graph
Figure 1: Representations of an Access Control Matrix.
Discussion
The static definition of subjects assigned with access
rights on objects is a problem regarding the continu-
ous change in companies. Especially human subjects
joining, moving or leaving companies are of interest
concerning access rights and policies. Subjects are
not limited to persons. Also automatic subjects like
machines, computers and agents (cf. (Lawall et al.,
2013b)) are involved. Software and hardware are sim-
ilarly fluctuating in companies. The combination of
the different application systems K and applications
A makes the validity of access rights / policies at a
specific point in time error-prone. A consistent state
across all application systems is almost impossible.
Another aspect is the high maintenance effort re-
sulting from continuous changes. The administrators,
the responsible users or both are challenged by this
effort.
The approximated maintenance effort in ACM for
subject s ∈ S joining j(s), moving m(s) or leaving l(s)
is:
ACM
j(s),m(s)
=
∑
k∈K
∑
a∈A
|O
s,k,a
| · |R
k,a
| (1)
ACM
l(s)
=
∑
k∈K
∑
a∈A
|O
s,k,a
| (2)
The determination of all subjects that are assigned to
access right r on an object o is another problem. All
subjects of a company have to be resolved from the
involved column o. Each entry in the access control
matrix has to be compared with the right r to decide if
the subject is assigned to the right. In the worst case
|
S
|
·
|
R
|
comparisons per object are needed.
2.2 Role-Based Access Control – RBAC
Sessions
Subjects Roles
Access
Rights
Objects
Permissions
Dynamic Separation of Duty
Static Separation
of Duty
Subject
Assignment
Permission
Assignment
Role Hierarchy
Figure 2: Role-based Access Control adapted by (Ferraiolo
et al., 1999).
Instead of assigning subjects individually to objects
with their concrete access rights like in section 2.1
– the access control matrix – subjects are associated
with one or more roles (User Assignment, UA). A
role is associated with a corresponding set of access
rights to objects (Permission Assignment, PA). A sub-
ject’s access to objects is based on the access rights
of the roles to which the subject is assigned, cf. (Fer-
raiolo et al., 2001), (Liu et al., 2006), (Sandhu, 1992),
(Sandhu, 1998) and (Sandhu et al., 1996).
Administrators for identity management tasks have to
manage the access rights to an ideally small number
of role definitions, rather than many individual user
permissions, cf. (Williamson et al., 2009).
There are more RBAC implementations extend-
ing the mentioned core RBAC. In (Chen, 2011) and
(Chen and Zhang, 2011), the extensions of RBAC in-
clude role hierarchies, constraints and the combina-
tion of role hierarchies and constraints (cf. fig. 2).
Role hierarchies are used to inherit access rights. For
example, a head of a department is superior to his
clerk and has also same access rights to all objects
which the clerk is assigned to.
The constraint extension restricts the Subject Assign-
ment and the assignment in role hierarchies with
Static Separation of Duty in RBAC with constraints.
Dynamic Separation of Duty restricts the active roles
of a subject in a session, cf. figure 2.
Discussion
The main factor for using RBAC compared to the ac-
cess control matrix is to reduce management costs. If
access rights are assigned to a subject’s role, the main-
tenance effort for managing individual access rights
is eliminated, cf. (Ferraiolo et al., 2003, p. 19). This
means that as a subject moves into or out of a job
function within an organization, access to the asso-
ciated roles is granted and automatically rescinded.
Hypergraph-basedAccessControlUsingFormalLanguageExpressions-HGAC
269

The administration effort is decreased because the re-
assignment of subjects to roles compared to the as-
signment of subjects to access rights has less work
load. If there are more roles than subjects needed, the
effort is higher.
The problem remains that the new role subject as-
signment has to be done in all application systems K
and applications A. Another aspect is that the User
Assignment is static with regards to access rights. The
access rights in a company for objects (e.g. processes,
files,...) are often based on context-
4
, attribute-
5
and /
or parameter-
6
values. This is difficult with the RBAC
approach. For each characteristic policy, a separate
role is needed. Technical roles (roles in applications)
are no longer job functions as intended in RBAC, cf.
(Ferraiolo et al., 2003, p. 10). Thus, the organiza-
tional job functions are not congruent to the roles in
RBAC. An permanent effort in maintaining the map-
ping between job functions and roles is essential to
ensure consistent policies / access rights. Thus a con-
sistent access right assignment spread over all appli-
cation systems with fluctuating subjects is hardly pos-
sible. The approximated maintenance effort in RBAC
for subject s ∈ S joining j(s), moving m(s) or leaving
l(s) is:
RBAC
j(s),m(s),l(s)
=
∑
k∈K
∑
a∈A
|Role
s,k,a
| (3)
The permission definition based on RBAC is more
stable over time than using the access control matrix
in the application systems respectively applications.
Because the assignment of a role to permissions re-
mains the same, the Subject Assignment changes.
Using RBAC, the determination of all subjects as-
signed to access right r on an object o is the follow-
ing: Subjects are assigned to their roles by UA and
permissions are assigned to roles by PA. In order to
determine all assigned subjects, all roles with the right
r on o need to be found by evaluating PA. In a sec-
ond step, all subjects assigned to these roles have to
be resolved by evaluating UA.
3 HYPERGRAPH-BASED ACCESS
CONTROL – H GAC
The formal specification of a hypergraph defined by
(Gallo et al., 1993) will be redefined for the access
4
The context in which a subject acts (e.g. “purchase” in a work-
flow).
5
Access rights are assigned using attributes of e.g. a subject
(like “Hiring Year” > 2).
6
Access rights defined by parameters passed from an appli-
cation system. If for example the “damage” in an insurance case
amounts to 200000, only subjects fulfilling this are responsible.
DB-Agent
structural
Role
Subject
Omitted parts of the graph
Organizational-
unit
Entity-type
Relation-type
deputy
House Damages
Clerk
role-dependent
damage > "1500"
Head
u
1
u
2
u
3
p
1
QM-Officer
Figure 3: Excerpt of an Organizational Model of an Insur-
ance Company.
control with H GAC.
A hypergraph as defined by (Gallo et al., 1993)
is a graph G
hyp
= (V, E) with the set of nodes
V =
{
v
1
, v
2
, ..., v
n
}
and the set of hyperedges E =
{
E
1
, E
2
, ..., E
m
}
. A directed hyperedge E
i
= (S, Z)
consists of arbitrary non-empty sets of start nodes
S ⊆ V and target nodes Z ⊆ V .
H GAC redefines the introduced hypergraph def-
inition by relations on relations (cf. section 3.2). It
uses language expressions to declare subjects (cf. sec-
tion 4).
3.1 Organizational Model
Structural Relations
Figure 3 shows an example model of an insurance
company
7
. The model consists of the department
House Damages, the subjects u
1
, u
2
, u
3
(human sub-
jects) and p
1
(automatic subjects) with their func-
tional units Head, Clerk and DB-Agent. The subject
u
1
is also working as QM-Officer a position within
another department.
Organizational Relations
Beside the structural relations, the company’s model
contains further relations – organizational relations
8
(e.g. deputy, supervisor and reporting relations) that
interconnect entities. In this example, the Head u
1
has a deputy u
2
if u
1
acts as Head of the department
House Damages
9
. If u
1
acts as QM-Officer, then u
2
is
not a possible deputy.
In case the DB-Agent p
1
is unavailable, a
constrained deputy relation to u
3
is evaluated at
7
The metamodel is described in (Lawall et al., 2014b).
8
In (Lawall et al., 2012), (Lawall et al., 2013a) and (Lawall
et al., 2013b), the complete metamodel and formal language in-
cluding, i.a. constraints, are specified.
9
It is possible to restrict any and all organizational relations to
be role-dependent.
DATA2015-4thInternationalConferenceonDataManagementTechnologiesandApplications
270

first. If the parameter-based
10
predicate (damage >
"1500") of the relation is fulfilled, it transfers all ac-
cess rights of p
1
to u
3
. In this scenario, the subject u
3
is a Clerk responsible for expensive insurance cases.
If u
3
and p
1
are simultaneously unavailable, the gen-
eral deputy relation between DB-Agent and Clerk is
evaluated. The result set consists of subject u
2
which
is then the deputy. u
3
is not an element of this set
because of unavailability. This algorithm represents a
prioritization mechanism.
Another variant to restrict the validity of relations
are context-sensitive constraints (not included in the
example). A constraint assigned to a deputy relation
of a subject is fulfilled if the context is identical to the
context provided by an application system.
3.2 Formal Specification
The start node is substituted in the formal specifica-
tion as α := Permission.
The access control hypergraph G
Perm
= (V, E) is
defined as:
• The set of nodes V =
{
α, o
1
, ..., o
l
}
with o
g
∈ O ∧
g = 1, ..., l
– The node α is the reference node of all access
right definitions.
– O the set of objects which are assigned to
rights.
• The set of edges E = {r
h
j
| r
h
j
∈ ξ
j
∧ h = 1, ..., d}
consists of ternary relations r
h
j
( j : relation-types for rights, d : number of rela-
tions per relation-type)
– R : set of relation-types of rights
– ξ
j
∈ R : set of relations of a specific relation-
type of a right
– ∀r
h
j
(r
h
j
∈ ξ
j
): r
h
j
⊆ (
{
α
}
∪ ξ
j
)×(O ∪ ξ
j
)×L:
11
∗ The element
{
α
}
∪ξ
j
of the tuple declares the
start of an edge in G
Perm
. α ∈ V is the first start
node of every relation of a relation-type j of
an hyperedge. Afterwards, arbitrary relations
r
b
j
∈ ξ
j
with b = 1, ...,
ξ
j
− 1 can be the start
of an edge of the same relation-type j.
∗ O ∪ ξ
j
defines the end of an edge in the graph.
This can be a concrete object o ∈ (O ⊂ V ) or
a set of relations of a relation-type ξ
j
.
10
If a value is handed from an application system to the orga-
nizational model via the formal language, the expression is called
parameter-based.
11
The relation r
1
j
includes always the “Permission” (α) node.
∗ A language expression L is a valid element
of language L(G)
12
. The empty word ε is in-
cluded in the language L(G) as well.
– f
L
: r
h
j
→ L extracts the language expression L
assigned to the hyper-relation r
h
j
.
• The subjects S result from evaluating the lan-
guage expressions L on the model.
– L ⇒
∗
S
part
⊆ S defines the result set S
part
of
the language expression L. The symbol ⇒
∗
indicates the resulting subjects of the language
expression L by traversing the organizational
model. The traversal algorithms are formal-
ized in (Lawall et al., 2014a) and (Lawall et al.,
2014c).
– S
path
=
e
S
p=1
S
part
with e equals the path length,
defines the set of all subjects assigned to access
right j on the path P
o∈O
j
. This path starts in α
and ends in o ∈ O. All language expressions
L of the relations r
h
j
on P
o∈O
j
are concatenated
with OR
13
. The resulting expression is evaluated
on the model to get the subjects S
path
.
The set of all subjects assigned to an access right
j for an object o ∈ O can be evaluated differently. It
is possible to compare all paths of a right j related to
the object o.
Starting the traversal in object o is more efficient
because an unnecessary evaluation of paths contain-
ing O \ o is excluded. The direction of the concatena-
tion of the language expressions is in “reverse” order.
The reverse and forward concatenation of language
expressions results in identical subjects.
3.3 Definition of Access Rights
An example (cf. fig. 4) configuration of the hyper-
graph G
Perm
= (V, E) is:
• O = { f 1, f 2, f 3, p1, p2, p3}: the set of objects
containing files and processes
• V =
{
α, f 1, f 2, f 3, p1, p2, p3
}
• E = {r
1
read
, r
1
write
, r
2
write
, r
3
write
, r
4
write
, r
5
write
,
r
1
exec
, r
2
exec
, r
3
exec
, r
4
exec
, r
5
exec
}
– R =
R EAD, W R IT E, EX EC UT E
– ξ
read
=
r
1
read
– ξ
write
=
r
1
write
, r
2
write
, r
3
write
, r
4
write
, r
5
write
– ξ
exec
=
r
1
exec
, r
2
exec
, r
3
exec
, r
4
exec
, r
5
exec
12
The syntax and semantic of the language is defined in (Lawall
et al., 2013a).
13
The empty word ε is excluded from this concatenation.
Hypergraph-basedAccessControlUsingFormalLanguageExpressions-HGAC
271
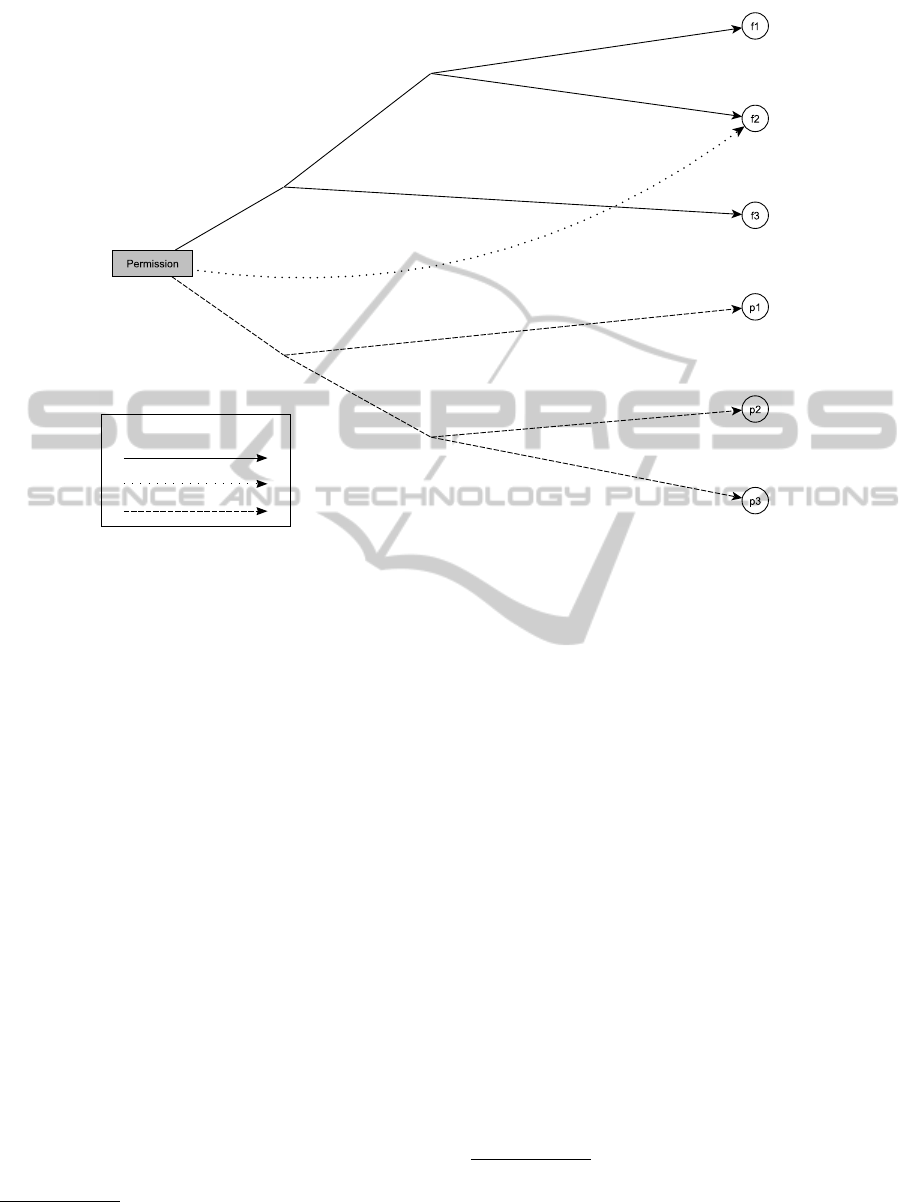
Head(House Damages)
DB-Agent(House Damages) WITH damage = <value>
DB-Agent(House Damages)
"u
2
" OR DB-Agent(House Damages)
Clerk(House Damages).ATT.HiringYear > "5"
DB-Agent(House Damages)
Head(House Damages) OR
Clerk(House Damages).ATT.ProcessFlag = true
Relation-type
Write
Read
Execute
Figure 4: Access Rights defined by using a Hypergraph and Formal Expressions.
– r
1
read
= ({α}, { f 2}, "u2" OR DB-Agent
(House Damages))
– r
1
write
=
{α}, {r
2
write
, r
3
write
}, ε
– r
2
write
= ({r
1
write
}, { f 3}, DB-Agent(House
Damages))
– r
3
write
= ({r
1
write
}, {r
4
write
, r
5
write
},Head(House
Damages))
– r
4
write
= ({r
3
write
}, { f 2}, DB-Agent(House
Damages) WITH damage = "2000")
– r
5
write
=
{r
3
write
}, { f 1}, ε
– r
1
exec
=
{α}, {r
2
exec
, r
3
exec
}, ε
– r
2
exec
= ({r
1
exec
}, {p1}, Clerk(House
Damages).ATT.HiringYear > "5")
– r
3
exec
=
{r
1
exec
}, {r
4
exec
, r
5
exec
}, ε
– r
4
exec
= ({r
3
exec
}, {p2},Head(House
Damages) OR Clerk(House
Damages).ATT.Processflag = "true")
– r
5
exec
= ({r
3
exec
}, {p3},DB-Agent(House
Damages))
• The set of subjects S = {u
1
, u
2
, u
3
, p
1
} (human
and automatic)
14
(cf. fig. 3):
– f
L
r
1
read
= "u2" OR DB-Agent(House
Damages) ⇒
∗
S
part
=
{
u
2
, p
1
}
14
The following results can be different in cases of absence of
subjects depending on deputy relations.
– f
L
r
2
write
= f
L
r
5
exec
= DB-Agent(House
Damages) ⇒
∗
S
part
=
{
p
1
}
– f
L
r
3
write
= Head(House Damages)
⇒
∗
S
part
=
{
u
1
}
– f
L
r
4
write
= DB-Agent(House Damages)
WITH damage = "2000" ⇒
∗
S
part
=
{
p
1
}
– f
L
r
2
exec
= Clerk(House
Damages).ATT.HiringYear > "5"
⇒
∗
S
part
=
{
u
2
}
15
– f
L
r
4
exec
= Head(House Damages) OR
Clerk(House Damages).ATT.Processflag
= "true" ⇒
∗
S
part
=
{
u
1
, u
3
}
16
– f
L
r
1
write
= f
L
r
5
write
= f
L
r
1
exec
=
f
L
r
3
exec
= ε ⇒
∗
S
part
=
/
0
• The set of all subjects assigned to access rights on
an object o ∈ O:
– Access right W R I T E to an object f 1 is as-
signed to subject u
1
:
∗ Path P
f 1
W R I T E
=
r
5
write
, r
3
write
, r
1
write
∗ S
path
=
/
0 ∪
{
u
1
}
∪
/
0 =
{
u
1
}
– Access right W R IT E to an object f 2 is
assigned to subjects u
1
, p
1
and access right
15
u
3
is not included in the resulting set of subjects because the
attribute-based predicate is not fulfilled.
16
u
3
is included in the resulting set of subjects because the value
of his attribute fulfills the attribute-based predicate.
DATA2015-4thInternationalConferenceonDataManagementTechnologiesandApplications
272

R EAD to u
2
, p
1
:
W R IT E:
∗ Path P
f 2
W R I T E
=
r
4
write
, r
3
write
, r
1
write
∗ S
path
=
{
p
1
}
∪
{
u
1
}
∪
/
0 =
{
u
1
, p
1
}
R EAD:
∗ Path P
f 2
R EAD
=
r
1
read
∗ S
path
=
{
u
2
, p
1
}
– Access right W R I T E to an object f 3 is as-
signed to subject p
1
:
∗ Path P
f 3
W R I T E
=
r
2
write
, r
1
write
∗ S
path
=
{
p
1
}
∪
/
0 =
{
p
1
}
– Access right EX EC UT E to an object p1 is
assigned to subject u
2
:
∗ Path P
p1
EX EC UT E
=
r
2
exec
, r
1
exec
∗ S
path
=
{
u
2
}
∪
/
0 =
{
u
2
}
– Access right EX EC UT E to an object p2 is
assigned to subjects u
1
, u
3
:
∗ Path P
p2
EX EC UT E
=
r
4
exec
, r
3
exec
, r
1
exec
∗ S
path
=
{
u
1
, u
3
}
∪
/
0 ∪
/
0 =
{
u
1
, u
3
}
– Access right EX EC UT E to an object p3 is
assigned to subject p
1
:
∗ Path P
p3
EX EC UT E
=
r
5
exec
, r
3
exec
, r
1
exec
∗ S
path
=
{
p
1
}
∪
/
0 ∪
/
0 =
{
p
1
}
The definition of a specific access right using
(hyper-) relations and language expressions in con-
junction with the organizational model simplifies the
maintenance if the company’s organization changes.
This is established by the logically centralized organi-
zational model and the language expressions that are
stored in the hypergraph.
The maintenance effort for applying company
policies decreases with H GAC . In the example, the
path
P
f 2
W R I T E
=
r
4
write
, r
3
write
, r
1
write
defines the ac-
cess right W R I T E assigned to object f 2. The
subjects resulting from the language expression
DB-Agent(House Damages) WITH damage =
"2000" assigned to the relation r
4
write
is exclusively
valid for object f 2.
The relation r
3
write
with the language expression
Head(House Damages) is valid for the objects f 1
and f 2. The expression does not have to be stored
twice. Thus, H GAC provides a mechanism to avoid
redundancies.
Access rights for new objects in application sys-
tems can be integrated at any point of the access right
hypergraph. The user can reuse previously defined re-
lations and assigned expressions. The user connects
the new relation to the hypergraph. If needed, he as-
signs a new language expression to get the appropriate
set of subjects that have access to the new object.
For example, a user adds an object f 4 (e.g. fi-
nancial report for the department House Damages)
to an application system. The policy for this object
implies that the Head and Clerks of the department
House Damages can access it, but not the DB-Agent.
Therefore, the user instantiates a relation of the type
W R IT E and assigns the expression Clerk(House
Damages). This new relation r
6
write
= ({r
3
write
}, { f 4},
Clerk(House Damages)) originates in r
3
write
17
and
ends in object f 4. Thus, the policy is defined by
reusing existing parts. This avoids redundancies.
For clarification, all redundant expressions (e.g.
DB-Agent (House Damages)) shown in figure 4 are
“redundantly” written to simplify reading. Such re-
curring expressions can be stored in macros, so that
changes in the macro affect all (hyper-) relations that
store this macro. Macros avoid redundancies in the
definition of access rights respectively policies with
H GAC.
4 DECLARATIVE LANGUAGE
The domain-specific language L(G) is defined by the
context-free grammar G = (N, Σ, P, S
G
) with the set
of non-terminals N, the alphabet Σ with N ∩ Σ =
/
0,
the production rules P and the start symbol S
G
with
S
G
∈ N (cf. (Fowler, 2010)). Each production rule
has the format l → r with l ∈ N and r ∈ (N ∪ Σ)
∗
.
4.1 Syntax
Non-terminals that expand only to one specific
sequence of terminals (keywords) are represented as
e.g. ‘NOT’, ‘WITH’.
The grammar G
1
for defining queries is a tuple of:
• The set of non-terminals N
1
=
{start, query, actor, f units, f unit, oude f , ounits,
ounit, relationTokens, withParams,
contextDe f inition, attConstraints, kcv, parameter,
kvp, id, string}
• The alphabet of terminals Σ
1
=
{‘a’,‘b’,...,‘z’,‘A’,‘B’,...,‘Z’,‘
¨
a’,‘
¨
u’,‘
¨
o’,‘
¨
A’,‘
¨
U’,‘
¨
O’,
‘0’,‘1’,...,‘9’,‘
’,‘-’,‘(’,‘)’,‘,’,‘.’,‘*’,‘=’,‘<’,‘>’}
18
• The set of production rules P
1
19
17
r
3
write
includes Head(House Damages).
18
The terminals derived from the non-terminal string are also
included.
19
Meaning of meta-symbols: ? means 0 or 1 and * means
0 to ∞ occurrences.
Hypergraph-basedAccessControlUsingFormalLanguageExpressions-HGAC
273

start → query | query logic query | ε
query → actor|actor ‘AS’ f units
query → query ‘NOT’ query
query → query ‘FALLBACKTO’ query
query → query ‘WITH’ withParams
query → f units ‘(’oude f ‘)’
query → relationTokens ‘(’query‘)’
query → ‘(’query logic query‘)’
query → ‘(’query‘).’attConstraints
actor → ‘*’ |id|string
f units → f unit| ‘(’ f unit logic f unit‘)’
f unit → ‘*’ |id|string
oude f → ounit|ounits logic ounits
ounits → ounit| ‘(’ounits logic ounits‘)’
ounit → ‘*’ |id|string|ounit ‘SUBS’
relationTokens → (‘ALL’ | ‘ANY’)? id
(‘OF’|‘TO’)
withParams → contextDe f inition|parameter|
withParams ‘,’ withParams
contextDe f inition → ‘CONTEXT=’ context (‘,’
context)∗
attConstraints → ‘ATT.’ kcv
kcv → id comp string| ‘(’kcv logic kcv‘)’
parameter → kvp (‘,’ kvp)∗
kvp → id ‘=’ string
logic → ‘AND’ | ‘OR’
comp → (‘=’ | ‘<=’ | ‘>=’ | ‘<’ | ‘>’ | ‘!=’)
id → ([‘a’-‘z’,‘A’-‘Z’] | ‘ ’ | ‘
¨
A’ | ‘
¨
a’ | ‘
¨
U’ | ‘
¨
u’ |
‘
¨
O’ | ‘
¨
o’) ([‘a’-‘z’,‘A’-‘Z’] | ‘
¨
A’ | ‘
¨
a’ | ‘
¨
U’ | ‘
¨
u’ |
‘
¨
O’ | ‘
¨
o’ |[0 − 9]| ‘ ’ | ‘-’)
∗
string → ‘"’ id ‘"’
• The set of start symbols S
G
1
= {start}
The grammar G
2
for defining predicates on rela-
tions is a tuple of:
• The set of non-terminals N
2
=
{internal, relPred, parameteratt, context,
parameter, attribute, kcv, logic, id}
• The alphabet of terminals Σ
2
= Σ
1
• The set of production rules P
2
20
internal → relPred| relPred logic relPred|ε
relPred → context|parameteratt|
‘(’relPred‘)’ | ‘(’relPred logic relPred‘)’
parameteratt → parameter|attribute|
‘(’parameteratt logic parameteratt‘)’
context → id| ‘(’context logic context‘)’
20
Production rules for non-terminals kcv, logic and id
correspond to those in P
1
.
parameter → kcv|
‘(’parameter logic parameter‘)’
attribute → ‘ATT.’ kcv|
‘(’attribute logic attribute‘)’
• The set of start symbols S
G
2
= {internal}
The grammar G is the result of the union of gram-
mars G
1
and G
2
21
. This equals G = {N
1
∪N
2
, Σ
1
, P
1
∪
P
2
∪ {s
G
→ start | internal}, {s
G
}} A language ex-
pression L is syntactically correct if L is derivable
starting from the set of start symbols of the language:
L(G) =
L ∈ Σ
∗
| S
G
∗
G
L
. The bottom-up ap-
proach for the syntactical evaluation is also possible.
4.2 Semantics
Language expressions are formulated within or out-
side of the organizational model. Within means that
the expression is inside of an organizational model
and represents a predicate assigned to a relation. The
grammar for the definition of predicates is G
2
.
The syntax for queries is defined by the grammar
G
1
. They are the outside perspective. Application
systems pass language expressions to the organiza-
tional model (via organizational server, cf. section
6, fig. 6). The expression is then evaluated on the
organizational model which yields subjects.
The semantics of the domain-specific language
L(G) is described informally for brevity. The seman-
tics of queries that are formulated to get the appropri-
ate set of subjects is the following
22
– L(G
1
):
• Based on Structural Relations are queries de-
scribing a concrete subject, e.g. “u1”, subjects
having a specific role in a specific organizational-
unit e.g. Clerk(House Damages), or subjects
having a specific role in any organizational-unit
e.g. Clerk(*).
• Separation of Duty is expressed by the NOT-
clause mostly used in workflow management
systems, e.g. SUPERVISOR OF(<initiator>)
NOT <initiator>, to prevent the initiator of a
process from approving his own request for pur-
chase.
• Prioritization defines primary candidates and an
alternative to fall back to. If the set of primary
candidates is empty, the second query is evalu-
ated, e.g. Clerk(House Damages) FALLBACKTO
Head(House Damages).
21
Union of context-free grammars according to (Hoff-
mann, 2011).
22
Composite access rights can be defined by the concate-
nation of queries with logical AND and OR.
DATA2015-4thInternationalConferenceonDataManagementTechnologiesandApplications
274

• Parameter Passing is done using WITH. Applica-
tion systems pass parameters to the organizational
model, e.g. DB-Agent(House Damages) WITH
damage = "1000".
• Acting Role describes the role in which a subject
acts. This is used to decide if role-dependent re-
lations are valid, e.g. the deputy relation between
u1 and u2. This deputyship is only valid if u1 acts
as Head (cf. section 3.1). There are different pos-
sibilities to formulate such queries. The implicit
enumeration of roles e.g. Head(House Damages)
specifies the role Head. The explicit variant to
pass a role to the organizational model when di-
rectly naming a subject is possible with e.g. u1
AS Head.
• Subjects restricted by Attributes are subjects
that fulfill the attribute constraints. The expres-
sion Clerk(House Damages).ATT.HiringYear
> "2" describes the subjects that have been on the
job for more than two years.
• Based on organizational Relations that are
deputyship, supervision and reporting dependen-
cies. This can also be used for audits. If, for
example, all possible deputies have to be listed,
the expression ANY DEPUTY OF(p1) can be used.
The possible subjects are u2 and u3, stemming
from the predicated and not predicated deputy re-
lations from p1 and DB-Agent. ANY ignores pred-
icates (e.g. damage > "1500" or role-dependent
predicates). ALL indicates that the relation is to be
followed transitively.
The semantic of predicates on relations that are
used to declare organizational circumstances are
23
–
L(G
2
):
• General Validity means that if no predicate is as-
signed to a relation (ε) it is always valid, e.g. the
deputy relation between the roles DB-Agent and
Clerk.
• Based on the Current Context the Subject is
supposed to Act in, specific relations can be valid
or invalid. This has consequences for organiza-
tional regulations, e.g. u2 can only be u1’s deputy,
if u1 acts as Head, not if he acts as QM-Officer.
Another context can be a “purchase”. A predi-
cate is e.g. purchase.damage > "1500". The
deputyship between p1 and u3 is dependent on the
context “purchase”.
• Based on Attributes of the Subjects, subjects
can be filtered from the result set. Relations on
23
Predicates can be based on a combination of context,
attributes and parameters.
the path do not change their validity by this mech-
anism.
• Based on Parameters from application systems,
the relations may be valid or invalid. This directly
influences the traversal of relations within the or-
ganizational model.
Discussion
The novel approach H GAC reduces the maintenance
effort to zero. If subjects join, move or leave the com-
pany, no changes have to be done concerning access
right assignment. The access rights are immediately
and automatically consistent.
On the one hand, this is enabled by the organiza-
tional (meta-) model of the company’s circumstances,
cf. section 3.1, and on the other hand by the declar-
ative language, cf. chapter 4. The policies are for-
mulated in language expressions that describe the re-
quirements for access.
The expressions declare queries for policies / ac-
cess rights in application systems. They are based on
organizational structures (entities and relations) and
consider properties of subjects (attributes).
Additionally, the language is used to define pred-
icates. They are used for policies that are formulated
on relations in the organizational model. The con-
junction of queries and predicates is a powerful tool
for defining policies.
Characteristic technical roles, as needed in RBAC,
to define the needed policies / access rights are obso-
lete. Policies are described by language expressions
and structured using hyperedges in H GAC . Thus,
changes – property changes (e.g. name, hiring year,
salary, etc.) and relation changes (e.g. join, move,
leave, new supervisor or deputy relation, etc.) – con-
cerning subjects do not affect the access right and pol-
icy definitions.
If, for example, a subject s ∈ S joins j(s), moves
m(s) or leaves l(s) the company, the effort
24
in
H GAC maintaining access rights in the application
systems is:
H GAC
j(s),m(s),l(s)
= 0 (4)
The only maintenance effort is in the organizational
model, cf. section 5.
Structuring access rights is limited in ACM and
RBAC approaches. The access rights can be struc-
tured hierarchically, e.g. for directory rights and con-
tained directories and files. This is an object-centered
view. The objects are generally structured. H GAC
favors an operator-centered view. The operators (i.a.
24
The effort is identical for relation changes, e.g. adding
a supervisor relation in the organizational model.
Hypergraph-basedAccessControlUsingFormalLanguageExpressions-HGAC
275

Table 1: Access Rights on Object “Project X” by Role.
Rights R Role Subjects in Role
f , m, e, l, r, w Role
A
16
f , m, e, l, r, w Role
B
13
f , m, e, l, r, w Role
C
42
f , m, e, l, r, w Role
D
4
e, l, r Role
E
13
Table 2: Access Rights on Object “International” by Role.
Rights R Role Subjects in Role
f , m, e, l, r, w Role
A
16
e, l, r Role
F
193
e, l, r Role
G
150
f , m, e, l, r, w Role
H
64
e, l, r Role
I
3983
e, l, r Role
J
172
e, l, r Role
K
305
e, l, r Role
L
178
e, l, r Role
M
65
m, e, l, r, w AD − HOC 5
read, write) are structured and the subjects are de-
clared by the language expressions. This makes it
easy to find all subjects that have a specific access
right to a specific object.
5 CASE STUDY
In order to validate and compare the approach, a case
study was conducted. Two objects with access rights
assigned using RBAC were evaluated. These objects
are directories on a file server:
• “Project X” (cf. table 1) is an arbitrarily selected
directory of a research project.
• “International” (cf. table 2) is a directory contain-
ing resources for academic international affairs.
Tables 1 and 2 show the permissions that are
assigned to different roles for the objects. They
also list the number of subjects that are as-
signed to the individual roles. The set R =
{ f ull access, modi f y, execute, list, read, write} de-
fines the access rights that can be assigned.
For brevity, they are denoted in the tables as
{ f , m, e, l, r, w} correspondingly.
As can be seen from the amount of subjects, an
ACM approach would not be practical with almost
4000 subjects, even for such a small number of ob-
jects
25
.
A detailed look at the subject assignments re-
vealed a number of inconsistencies:
25
subjects * objects * access rights ≈ 4000 · 2 · 6
• Subjects occur multiple times in different roles.
• Subjects are assigned to roles that have more
rights than the subject should have. A student as-
sistant had the role of a researcher.
• The ad-hoc role AD − HOC is a technical role
specific to the object “International”. It is not
used anywhere else and contains a reference to a
subject that does no longer exist in the directory
server.
• There exist a number of pseudo-subjects, such as
test accounts that allow system administrators to
impersonate members of specific roles.
• Technical roles (subjects with the same rights) and
organizational roles (subjects with the same job
position) are mixed arbitrarily.
This list of discrepancies illustrates how error-
prone the maintenance of join, move and leave op-
erations is in RBAC. For each operation, all affected
role assignments have to be maintained. In H GAC ,
these operations have to be performed once in the or-
ganizational model.
Figure 5 shows the hypergraph in H GAC that is
equivalent to the representation in RBAC. For clarity,
the different sets of rights {e, l, r}, { f , m, e, l, r, w} and
{m, e, l, r, w} are represented as one relation-type each
in the depiction. The actual hypergraph contains a
relation-type per access right.
The key of the representation of an RBAC model
in H GAC is the formulation of the roles as language
expressions:
• Role
A
represents the IT-administrators of the Uni-
versity: Admin(University)
• Role
B
, Role
C
and Role
D
are technical roles
for members of the Research Department:
Member(Research Department)
• Role
E
are employees of the IT-Infrastructure de-
partment: Member(IT-Infrastructure)
• Role
F
and Role
G
encompass lecturers of the uni-
versity: Lecturer(*).
• Role
H
are employees of the Datacenter depart-
ment: Member(Datacenter).
• Role
I
Role
J
and Role
K
represent different types of
students, e.g. external and internal students. As
they appear together, they can be represented as
Student(*).
• Role
L
represents all administrative employees of
the university, *(Administration).
• Role
M
are research assistants of the Uni-
versity, as can be described as Research
Assistant(University).
DATA2015-4thInternationalConferenceonDataManagementTechnologiesandApplications
276
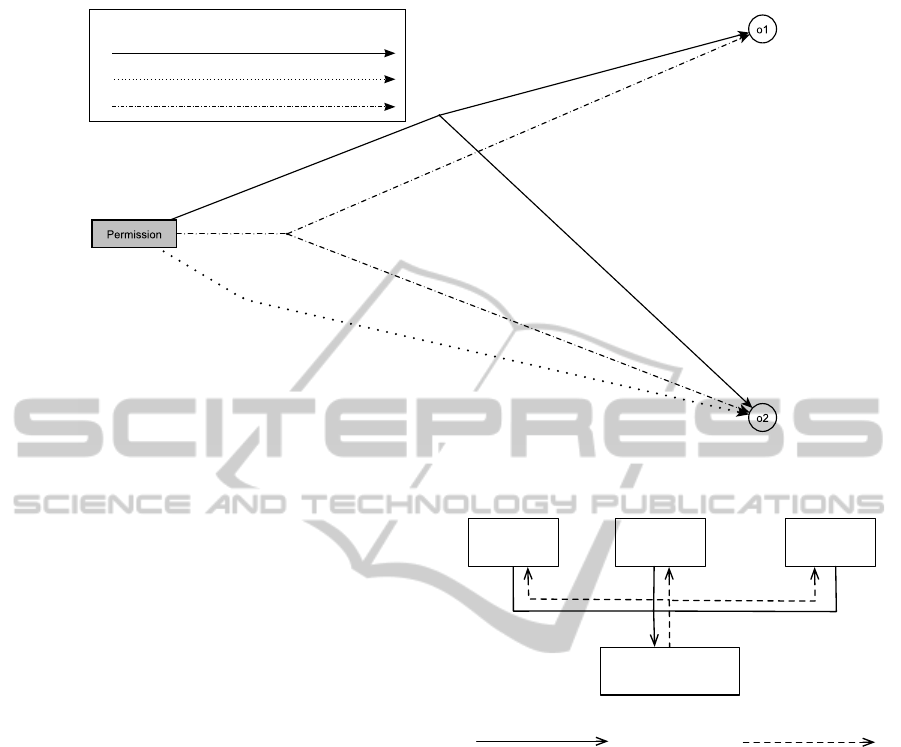
Relation-type
Execute, List, Read
Modify, Execute, List, Read, Write
Full Access, Modify, Execute, List, Read, Write
Admin(University)
Member(Research Department)
Member(Datacenter)
Member(IT-Infrastructure)
Lecturer(*) OR Student(*) OR Research Assistant(University)
OR *(Administration)
*(International Office)
Figure 5: Access Rights of the Case Study in H GAC.
• The special role AD − HOC contains all employ-
ees of the International Office of the university.
The expression *(International Office) de-
scribes them.
6 CONCLUSION
The approaches ACM and RBAC require extensive
maintenance effort (cf. equations (1), (2) and (3))
to accommodate fluctuating subjects in the company.
This effort is erased in H GAC (cf. equation (4)).
The language expressions declaring policies / access
rights are more stable over time than total enumera-
tion used by ACM and RBAC. Access rights are de-
fined in H GAC in a descriptive manner. The descrip-
tion can be based on organizational structures (i.a.
departments, job functions, supervisor relations) and
properties (i.a. name, hiring year, salary). In addi-
tion, parameters from application systems or different
contexts can be decisive. The contexts are defined by
the nature of necessary tasks or of common resources.
The organizational model includes the definition of
responsible subjects for the administration of the or-
ganizational model itself. This decreases the work-
load of administrators and distributes the work to the
subjects that maintain the organizational model.
The subject that joins, moves or leaves the com-
pany causes maintenance effort in all application sys-
tems respectively applications which is prone to error.
As a consequence, the definition of consistent access
rights that conform to reality is facilitated.
System 1 System 2 System n...
Organization
Server
Query Result
Figure 6: Organizational Server connected with Application
Systems adapted from (Lawall et al., 2014b).
The concept of H GAC in conjunction with an or-
ganizational server solves the afore-mentioned prob-
lems (cf. figure 6). The systems hand the language
expressions (query) to the organizational server hold-
ing the organizational model of the company. The
expressions are evaluated on the model and the set
of authorized subjects are handed back to the system
(result). All connected systems are immediately in
synchronization with organizational facts if the new
organizational conditions are modeled in the organi-
zational server. This makes access rights consistent
over various application systems.
The focus for future research is the extension of
the language to overcome problems resulting from re-
naming organizational entities. A macro-like mecha-
nism will be examined to have a single point of main-
tenance for expressions. Macros remedy the redun-
dant storage of identical expressions. They are refer-
Hypergraph-basedAccessControlUsingFormalLanguageExpressions-HGAC
277

ences to expressions. Only expressions referenced by
macros have to be changed.
REFERENCES
Benantar, M. (2006). Access Control Systems: Secu-
rity, Identity Management and Trust Models. Access
Control Systems: Security, Identity Management and
Trust Models. Springer.
Chen, L. (2011). Analyzing and Developing Role-Based Ac-
cess Control Models. PhD thesis, University of Lon-
don.
Chen, Y. and Zhang, L. (2011). Research on role-based
dynamic access control. In Proceedings of the 2011
iConference, iConference ’11, pages 657–660, New
York, NY, USA. ACM.
Ferraiolo, D., Kuhn, D., and Chandramouli, R. (2003).
Role-based Access Control. Artech House computer
security series. Artech House.
Ferraiolo, D. F., Barkley, J. F., and Kuhn, D. R. (1999). A
role-based access control model and reference imple-
mentation within a corporate intranet. ACM Trans. Inf.
Syst. Secur., 2:34–64.
Ferraiolo, D. F., Sandhu, R., Gavrila, S., Kuhn, D. R., and
Chandramouli, R. (2001). Proposed NIST standard
for role-based access control. ACM Transactions on
Information and System Security, 4:224–274.
Ferrari, E. (2010). Access Control in Data Management
Systems. Synthesis lectures on data management.
Morgan & Claypool.
Fowler, M. (2010). Domain-Specific Languages. Addison-
Wesley Professional.
Gallo, G., Longo, G., Pallottino, S., and Nguyen, S. (1993).
Directed Hypergraphs and Applications. Discrete
Appl. Math., 42(2-3):177–201.
Graham, G. S. and Denning, P. J. (1972). Protection: Prin-
ciples and Practice. In Proceedings of the May 16-18,
1972, Spring Joint Computer Conference, AFIPS ’72
(Spring), pages 417–429, New York, NY, USA. ACM.
Hoffmann, D. W. (2011). Theoretische Informatik.
M
¨
unchen: Carl Hanser, M
¨
unchen, 2. edition.
Knorr, K. (2000). Dynamic access control through Petri net
workflows. In Computer Security Applications, 2000.
ACSAC ’00. 16th Annual Conference, pages 159–167.
Krcmar, H. (2010). Informationsmanagement. Springer,
Berlin; Heidelberg.
Lawall, A., Schaller, T., and Reichelt, D. (2012). An
Approach towards Subject-Oriented Access Control.
In S-BPM ONE 2012, pages 33–42, Heidelberg.
Springer-Verlag.
Lawall, A., Schaller, T., and Reichelt, D. (2013a). Integra-
tion of Dynamic Role Resolution within the S-BPM
Approach. In S-BPM ONE 2013, pages 21–33, Hei-
delberg. Springer.
Lawall, A., Schaller, T., and Reichelt, D. (2013b). Who
Does What – Comparison of Approaches for the Def-
inition of Agents in Workflows. In Web Intelligence
(WI) and Intelligent Agent Technologies (IAT), 2013
IEEE/WIC/ACM International Joint Conferences on,
volume 3, pages 74–77.
Lawall, A., Schaller, T., and Reichelt, D. (2014a). Cross-
Organizational and Context-Sensitive Modeling of
Organizational Dependencies in C-ORG. In S-BPM
ONE (Scientific Research), pages 89–109, Heidelberg.
Springer-Verlag.
Lawall, A., Schaller, T., and Reichelt, D. (2014b). Enter-
prise Architecture: A Formalism for Modeling Orga-
nizational Structures in Information Systems. In Bar-
jis, J. and Pergl, R., editors, Enterprise and Organiza-
tional Modeling and Simulation, volume 191 of Lec-
ture Notes in Business Information Processing, pages
77–95. Springer Berlin Heidelberg.
Lawall, A., Schaller, T., and Reichelt, D. (2014c). Local-
Global Agent Failover Based on Organizational Mod-
els. In Web Intelligence (WI) and Intelligent Agent
Technologies (IAT), 2014 IEEE/WIC/ACM Interna-
tional Joint Conferences on, volume 3, pages 420–
427.
Lawall, A., Schaller, T., and Reichelt, D. (2014d). Re-
stricted Relations between Organizations for Cross-
Organizational Processes. In Business Informatics
(CBI), 2014 IEEE 16th Conference on, pages 74–80,
Geneva.
Liu, Y. A., Wang, C., Gorbovitski, M., Rothamel, T.,
Cheng, Y., Zhao, Y., and Zhang, J. (2006). Core
Role-based Access Control: Efficient Implementa-
tions by Transformations. In Proceedings of the 2006
ACM SIGPLAN Symposium on Partial Evaluation and
Semantics-based Program Manipulation, PEPM ’06,
pages 112–120, New York, NY, USA. ACM.
Sandhu, R. S. (1992). The Typed Access Matrix Model.
In Proceedings of the 1992 IEEE Symposium on Secu-
rity and Privacy, SP ’92, pages 122–136, Washington,
DC, USA. IEEE Computer Society.
Sandhu, R. S. (1998). Role-Based Access Control. Ad-
vances in Computers, 46:237–286.
Sandhu, R. S., Coyne, E. J., Feinstein, H. L., and Youman,
C. E. (1996). Role-Based Access Control Models.
Computer, 29(2):38–47.
Saunders, G., Hitchens, M., and Varadharajan, V. (2001).
Role-based Access Control and the Access Control
Matrix. SIGOPS Oper. Syst. Rev., 35(4):6–20.
Seufert, S. E. (2002). Die Zugriffskontrolle. PhD thesis,
Bamberg, Univ., Diss., 2002.
Vahs, D. (2007). Organisation: Einf
¨
uhrung in die Organi-
sationstheorie und -praxis. Sch
¨
affer-Poeschel.
Williamson, G., Sharoni, I., Yip, D., and Spaulding, K.
(2009). Identity Management: A Primer. Mc Press
Series. MC Press Online.
DATA2015-4thInternationalConferenceonDataManagementTechnologiesandApplications
278
