
The Analytical Approach to Information Value Management
Diego Abbo
School of Systems Engineering, University of Reading, Reading, U.K.
Keywords: Accounting Approach to Information Value.
Abstract: Increased computer interconnectivity is offering organizations of all types unprecedented opportunities to
improve operations, cutting costs, and sharing information. The success of many of these efforts depends, in
part, of an organization ability to protect the data and systems, and mainly of the value of the used infor-
mation.
The achievement is to identify the value of both the Information and the Information Infrastructure in order
not to spend a penny more of the value of what it should be protected and to define the appropriate infor-
mation business budget.
In general terms we can assume that the cyber dimension is a global set of information systems where it
should be discerned two different accounts: the first is the snapshot of the patrimonial value of the infor-
mation and the in use relative infrastructure. The second considers, in a given timeframe, the information
income statement that means the cyber wealth produced.
1 INTRODUCTION
A “defined ICT architecture” can range in dimen-
sions from a single INTERNET connected PC or a
business INTRANET to the network realm of the
civil service of a government or of the international
governmental organizations:
Increased computer interconnectivity and the social
acceptance of Internet are offering organizations of
all types unprecedented opportunities to improve
operations by reducing paper processing, cutting
costs, and sharing information.
Furthermore the growing of interdependency of
the complex integrated information systems will
continue and accelerate and more technologies are
integrated to deliver rich services. Today there is no
way to model, understand, monitor and manage the
risks presented by the growth of these systems.
Risk is defined as a feasible detrimental outcome
of an activity or action subject to hazards. The risk
is a word that admirably serves the forensic needs of
new global culture and its calculation is deeply en-
trenched in science and manufacturing and as a
theoretical base for decision making.
Generally speaking risks are generally classified
as “speculative” (the difference between loss or
gain, for example, the risk in gambling) and “pure
risk”, a loss or no loss situation, to which insurance
generally applies.
The actual state of art has its milestone in the so
called Probabilistic Risk Assessment -PRA-. The
PRA has emerged as increasingly popular analysis
tool especially during last decade. PRA is a system-
atic and comprehensive methodology to evaluate
risks associated with every life- cycle aspect of a
complex engineered technological entity from con-
cept definition, through design, construction, and
operation, and up to removal from service.
In PRA risk is characterized: the magnitude (or
severity) of the adverse consequence(s) that can
potentially result from the given activity or action,
and the likelihood of occurrence of the given ad-
verse consequence(s). If the measure of conse-
quence severity is the number of people that can be
potentially injured or killed, risk assessment be-
comes a powerful analytical too assess safety per-
formances.
The risk is associated to a negative event and to
the fact that for any negative event, normally, we
have pure damages (the costs of the pure loss) resili-
ence damages (the costs of reset) and consequential
damages (can be the loss of image, business activity
or a step of the threat to pursue other more harmful
aims)
549
Abbo D..
The Analytical Approach to Information Value Management.
DOI: 10.5220/0004616405490554
In Proceedings of the 15th International Conference on Enterprise Information Systems (IVM-2013), pages 549-554
ISBN: 978-989-8565-60-0
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

However if we consider the speculative risk it
should be considered also the “positive consequenc-
es” in accordance with the concept widely accepted
in the business world of no risk no return. Individual
investors managing their investments must be care-
ful when it comes to the amount of risk that they
take on. If they take on too much risk, perhaps by
making aggressive investments, the losses could
exceed their risk tolerance, or to be uncertain for
comfort. On the other hand, if they failed to take on
enough risk, by making conservative investments,
they may earn returns that are stable, but inadequate
for achieving the investor’s financial objectives.
Risk management is not only about reducing down-
side potential or the probability of pain, but also
about increasing upside opportunity or the prospects
for gain.
In both cases the point of attack for any specula-
tion and/or consideration is the value of the assets.
Value is a word whose meaning is different for
different people. This is old as civilization. In the
year 365 B.C. Aristotle had mentioned about seven
type of values. They are: religious, political, social,
aesthetic, ethical, economic, judicial. The economic
value of goods, the only one that can be measured in
terms of objective monetary units, presents two
sides according to Aristotle. The one is the value
that Aristotle called “natural” and it is exploited
through the final consumption. The other “non natu-
ral” is realized by exchanging goods with each oth-
er, using it so you do not to meet the direct needs,
but indirectly for other. In essence, Aristotle has a
clear distinction between use value and exchange
value, he shall notify heterogeneity and, just like the
classic two thousand years later folds on money and
on the market price as the best approximation to an
ideal criterion of commutative justice.
Aristotle, in fact, acknowledges that the goods
are the product of human labor, but as the jobs are
different from each other qualitatively and quantita-
tively, the reference to the labor-time necessary to
produce a commodity is not an adequate measure of
exchange value, is the currency that we must there-
fore rely on. An information system is an engineered
capital good that produces specific services in a
defined organizational context, a delivery system.
In general terms we can assume that the infor-
mation is moving, in a delivering system, from a
point of production to a point of utilization, and a
delivering system can be considered a multiple pro-
gressive segments of points of departure and points
of arrivals for the information in accordance with
the logical atomism.
-- Logical atomism is a philosophical belief that
originated in the early 20th century with the devel-
opment of analytic philosophy. The theory holds that
the world consists of ultimate logical "facts" (or
"atoms") that cannot be broken down any further.--
The information is produced (processed) in one
physical site, stored in the same or in another site
and communicate through a physical meaning to the
site of utilization. All the three entities (production,
communication and utilization) exploit instrumental
items as facilities that are hosting pertinent devices,
hardware, software, operation systems, applicative
programs, files, physical meaning of communication
(internal and external network) and are linked to the
human factors as operational management policy,
training, working activities and the end purpose of
the delivered information.
This paper is organized in two main conceptual
sections. The first one defines a set of models and
pertinent indicators capable of creating qualitative
standards of the value of information in an engi-
neered capital good.
-- The model represents a set of equation and/or
other mathematical relations with the capacity of
apprehending the characteristics of the contingency
situation and subsequently to describe, to estimate
and to control the working out.--
The second aspects analyses the Aristotle’s values
that can affected the information management in the
whole cyber dimension.
Particularly the economic value is accounted in a
static and dynamic way: the first represents the
snapshot of the information and the in use relative
infrastructure balance sheet. The second considers,
in a given timeframe, the information profit and
loss statement that means the cyber services pro-
duced.
2 INFORMATION VALUE
AND PERTINENT MODELS
AND/OR PROFILES
2.1 A.I.M.S. (ABBO’s Information
Models for Security)
A system is a collection of interacting components,
policies and procedures that are integrated and orga-
nized to react to an input and produce a predictable
output and have a feedback. Everything is not a part
of the system is called the surroundings
ICEIS2013-15thInternationalConferenceonEnterpriseInformationSystems
550
(Rogers, 2006). The components themselves and
the relationships among them determine how the
system works. A complex system is defined as a
diverse system of sub- systems working together
toward a common goal.
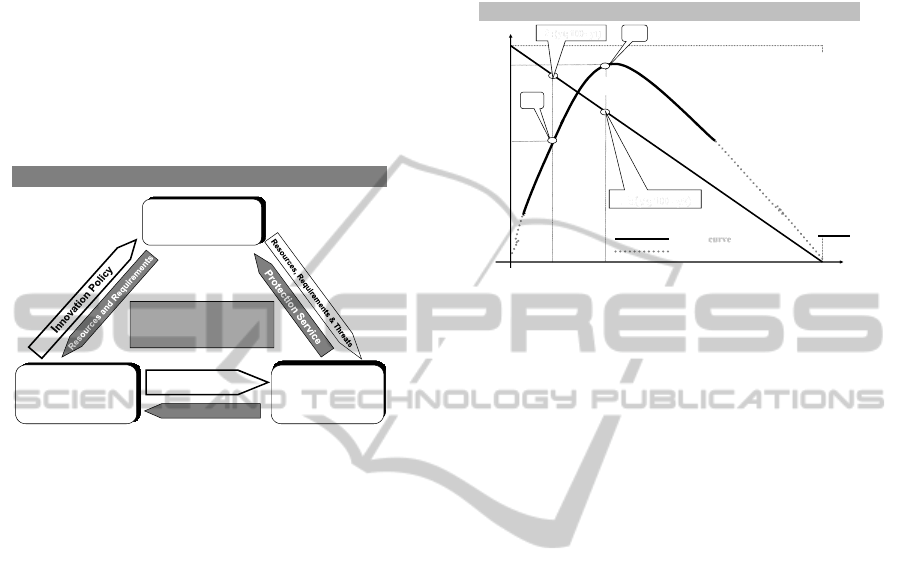
The three entity model or the ICT Security Com-
pany’s System is the core model of A.I.M.S. (Abbo
Information Models for Security) family (Abbo
2012 p 126). It is made of three sub – systems like
three entities in a close market how it is illustrated in
Figure 1 (Abbo, Sun, Feb 2009 pp 195 – 200).
ICT SECURITY COMPANY’s SYSTEM
INFORMATION
MISSION
ICT SECURITY
MISSION
Resources, Requirements
&Threats
Protection Service
COMPANY’S
MISSION
BUSINESS FLOW
(FACTs; ACTs; RI; DI;)
in a given timing
Figure 1: The three missions are the entities of a close
market where Company and Information are the two
customers of Security Services.
The three entity model is strictly linked to the defini-
tions of real cost and functional cost of the re-
sources. The real cost is the prize of a resource in
the external market and is clearly represented in the
balance sheet of the Company’s mission. The func-
tional cost is the percentage of each single resource
that we should invest for the defensive measures of
the resource for its operational survival.
The focal point is that considering each single
resource in terms of 100 percent functional units we
can share it in three complementary slots.
If we put on graphics the percent of each rele-
vant resource that is dedicated respectively to the
Information mission and to the ICT security mission
we have the ISO-line of balanced budget (Figure
2).The value of security performance is represented
by the ordinate of each point in the realistic curve
that is a percentage value. The difference between
one hundred and the value of security performance
represents both the value of “threat performance”
and the “quantitative risk analysis” for any model
that has same premises and surrounding conditions.
By an analytical point of view that means to draw
the curve y = SP(x): the functional cost is fixed but
the correspondence with the value of Security Per-
formance Curve is variable that should be conquered
on the field. While functional cost and security per-
formance rates are variables that should be consid-
ered in the strategic planning, the dynamic confron-
tation is related to the operational planning.
100%
100%
CURVE OF SECURITY PERFORMANCE
R1
100-Y1
O
R2
100-Y2
A:(y
1
;
100
-y
1
)
B:(y
2
;
100
-y
2
)
P1
y = SP(x)
P2
Non realistic curve
Realistic curve
Represents, for each Asset,
the ratio between the quantity
of no compromising data and
the total number of data
treated by the information
mission in the same
amount of time.
E.g. referred to
the point R1 the
value in the
curve of SP
equals:
P1
100
Figure 2: The curve is the representation of the ratio be-
tween security performance and functional cost of security
mission.
The calculation of functional cost should be some-
thing of relatively easily to individuate and its ac-
ceptance as an analytical tool addresses any possible
scenario represented by all the families of security
performances in every IS security context. In addi-
tion any change in the security architecture of an
existing or projected IS system should take always
into consideration both the functional cost and the
rate of security performance.
The combination of the functional costs is effi-
cient only in the area represented by the integral of
the realistic curve.
In the consideration of the inter-relation between
Company Mission and Information Mission, in
terms of percentage of dedicated resources, it is
possible to create the Iso-line of balanced budget for
e-government.
As for security management if we put on
graphics the percent of each relevant resource that is
dedicated respectively to the Company mission and
to Information mission we have the ISO-line of
balanced budget for e-government.
As for the graphic for security performance (pre-
vious Figure 2) the resources should be inclusive of
all the assets, instrumental tools and human factors.
Now if we consider two ICT architecture the first
with a minor rate of resources dedicated to Infor-
mation Mission and the second with an increased
rate of resources we have an increased performance
of the second architecture. The advantage is meas-
ured in percentage of time reduction (gain of time)
that the second architecture achieves compared with
the first one. The curve that is called e-government
TheAnalyticalApproachtoInformationValueManagement
551

performance (Figure 3) is mathematically represent-
ed by the formula:
y = e-G(x) = I/T
Where I represents the quantity of information that
is delivering in a defined amount of time T.
Anyway the curve is theoretical because we
should take into consideration the underperformance
of the second architecture and the security issues
due to the threat successful attack to our information
business flows. So the real curve is:
y = e-G(x) = (I/T- Tp
%/T)
where Tp%/T stays for the Threat performance in a
defined time T.
A similar curve can be also build –up consider-
ing the competitive advantage that comes from the
migration from a older technology and/or architec-
ture to new ones.
CURVE OF e-GOVERNMENT PERFORMANCE
100%
100%100-Y1
O
100-Y2
y = e-GT(x) =
I – Tp
%
T
R2
A:(y
1
;
100
-y
1
)
y = e-G(x) =
I
T
R1
B:(y
2
;
100
-y
2
)
P1
P2
Real curve
Theoretical curve
e-GOVERNMENT
PERFORMANCE
Represents, for any increasing
percentage rate of digitalization,
the percentage of timing reduction
of the Business flows along the
information physical dimension
(Communication, Storage and
Processing)
Threat performance
Figure 3: The curve is the representation of the ratio be-
tween the Information Performance and its running time.
The advantage of this analytical approach is that we
have a scalar quantity that is a time that represents a
measurable scale for compare two different architec-
tures. That means that it is possible to make histori-
cal and future comparisons between increasing tech-
nologies.
The three entity model, on its applicative imple-
mentation to a given architecture, is able to deter-
mine the reduction of the value of information man-
agement due to losses The losses are dependent
from threat performance in its widest sense that
range from a human willingness to a human care-
lessness to an “act of GOD”. In order to determine
the value of information management it is necessary
an integration of other models that are considering
the pure risks and the speculative risks.
Generally
speaking Risks are generally classified as “specula-
tive” (the difference between loss or gain, for exam-
ple, the risk in gambling) and “pure risk”, a loss or
no loss situation, to which insurance generally ap-
plies (Broder p.630).
2.2 The Accounting Model
Value may be expressed in accordance with the
accounting rules that means the release of the infor-
mation balance sheet and the information income
statement.
A balance sheet summarizes an organization or
individual's assets, equity and liabilities at a specific
point in time. We have two forms of balance sheet.
They are the report form and the account form. Indi-
viduals and small businesses tend to have simple
balance sheets. Larger businesses tend to have more
complex balance sheets, and these are presented in
the organization's annual report. Large businesses
also may prepare balance sheets for segments of
their businesses. A balance sheet is often presented
alongside one for a different point in time (typically
the previous year) for comparison.
An income statement (US English) or profit and
loss account (UK English) is one of the financial
statements of a company and shows the company's
revenues and expenses during a particular period. It
indicates how the revenues (money received from
the sale of products and services before expenses are
taken out, also known as the "top line") are trans-
formed into the net income (the result after all reve-
nues and expenses have been accounted for, also
known as "net profit" or the "bottom line"). It dis-
plays the revenues recognized for a specific period,
and the cost and expenses charged against these
revenues, including write-offs (e.g., depreciation
and amortization of various assets) and taxes. The
purpose of the income statement is to show manag-
ers and investors whether the company made or lost
money during the period being reported.
The application of the income statement to the
cyber dimension represents a “snapshot” of the
Information while the income statement represents
the flow of Information or better the flow of “infor-
mation traffic” in a defined period of time.
The build-up of both those documents for the
cyber dimension can be representative both of the
value of Information, in the broadest sense of the
word, and of the losses due security breaches.
Balance sheet and income statement are referred
to an unitary period of time normally one year or
one semester. For the information value purposes
ICEIS2013-15thInternationalConferenceonEnterpriseInformationSystems
552

the unitary period of time should be the same of the
business information flow (B.I.F.) life-cycle.
The quantity of information is normally encapsulat-
ed in business information flows (B.I.F.s) that we
can defined as a summation of Acts, Facts, Request-
ed Information and Delivered Information in a given
timing:
Acts, Facts, RI, DI
∆T
The facts consist on the potential productivity of the
infrastructural architecture and the acts all the hu-
man and automatic actions connected with the archi-
tecture.
All those assets are component of the “chain of
value” of the company to fulfill its mission and it’s
possible to measure them like an income account in
a fiscal period.
The B.I.F. exist because has an unitary mission
(Figure 4). If the mission of the B.I.F. cannot be
fulfilled the B.I.F. should be not existing in the ac-
counting scale and should be considered aborted or
spoiled.
THE B.I.F. AS UNITARY ACCOUNTING PERIOD
INFORMATION
PROCESSING
PREVIOUS
INFORMATION
STORED
REQUESTED
NEW INFORMATION
INTRODUCED
DURING B.I.F.
OPERATION
INFORMATION
COMMUNICATED
TO THE END USER
B.I.F. LIFETIME CYCLE
The B.I.F. is an holistic unitary entity focusing a specific
information management aim
The quantity of B.I.F.s in a fiscal period represents the
management value of the information in that specific architecture
Figure 4: The unitary B.I.F. scheme.
In the global architecture accounting the quantity of
B.I.F.s represents the management of information
value. In other words the estimation of the value
information of any single B.I.F. can account the
global value of information management.
3 INFORMATION VALUE
METRICS
The point of attack for any speculation and/or con-
sideration for the rate of impact is the capacity of
accounting the value of the assets that in the cyber
world is represented by the information infrastruc-
ture, the information and the “information traffic”.
The “information traffic” can be defined as the
number of B.I.F.s that are carried out by an individ-
uated operational information architecture in a given
standardized period of time.
The value of “information traffic” can be related to
value engineering (VE).
In today’s economic environment, VE lays stress on
economic values (Kumar, 2009 p. 38).
The constituents of economic value are: esteem
value, exchange value, use value, cost value:
It requires some explanation in order to understand
its relevance towards value engineering.
Exchange value is that value in the product, process,
service or system which can help to trade with some
other things. More the exchange value, more will it
be lucrative for the customer.
Esteem value can be defined as that part of the
product, process, service or system which will force
the person to own them. In today’s global economic
situation, it becomes the responsibility for the manu-
facturer or service providers to inculcate these val-
ues. Esteem values are the want and the desire of the
customers.
Use value of the product, process, service or system
is that value for which the things has been created.
Everything is being created to fulfil certain purpose.
It should include the need of the customer.
Cost value is the cost of the product, process or
service or the system. It is to be borne in mind that
this cost is not only the acquisition cost but it is the
total cost which in the parlance of finance is known
as Life cycle cost (LCC) or cradle to grave cost.
As we have mentioned before value may be ex-
pressed in accordance with the accounting rules that
should be adapted to means the release of the infor-
mation balance sheet and the information income
statement.
In an accounting perspective value may be ex-
pressed mathematically. The elements of the math-
ematical expression are performance (or function)
and cost (Kumar, 2009 p. 39)
It can be stated as:
Performance (or function)
Value =
Cost
In the information value management the unitary
performance should be seen as the ratio between the
speed of an unitary B.I.F. and its own cost.
TheAnalyticalApproachtoInformationValueManagement
553

The global performance is done, in a fiscal period,
by the total number of B.I.F.s divided by the total
cost where the total cost is the summation of the cost
of B.I.F.s and the cost of the ones aborted or
spoiled.
Such accounting solution is linked the information
management value not only to the cost value but
also to esteem, use and exchange values.
Aristotle and the contextualization of the infor-
mation management in all the measurable issue of
social sciences.
4 CONCLUSIONS
Value has different meaning for different people.
The cyber dimension is producing a service and the
subsequent issue is to estimate the value of that
service. An information system is an engineered
capital good that produces specific services in a
defined organizational context, a delivery system
with a chain of value.
The estimation of information management value
should considers two different accounts: the first is
the snapshot of the patrimonial value of the infor-
mation and the in use relative infrastructure. The
second considers, in a given timeframe, the infor-
mation income statement that means the cyber
wealth produced or more specifically the “infor-
mation traffic”.
A proper way to identify the value in the cyber
dimension is to develop the capacity to map, moni-
tor and manage the B.I.F.s with standardized proce-
dures.
In such information value engineering frame it
is possible to estimate all the values mentioned by
Aristotle: religious, political, social, aesthetic, ethi-
cal, economic, judicial.
The impact of the implementation of such ac-
counting solution and/or model represents the full
integration of the seven type of values mentioned by
Aristotle.
REFERENCES
Abbo Diego – Sun Lily. “Security Analysis of Information
Systems” IADIS International Conference - e-Society
Proceedings Vol II – Edited by Piet Kommers and
Pedro Isaìas Barcellona – spain (Feb - 2009)
Abbo Diego “Information Security Management Account-
ing”, Emerging Informatics - Innovative Concepts and
Applications, Shah Jahan Miah (Ed.), ISBN: 978-953-
51-0514-5, InTech, URL: http://www.
intechopen.com/books/emerging-informatics-innova
tive-concepts-and-applications/information-security-
management-accounting- (2012).
Broder, J. F. Encyclopaedia of Security Management –
Techniques and Technology, Butterworth-Heinemann,
Burlington MA, U.S.A. (1993).
Kumar Mukhopadhyaya Anil “Value Engineering Mas-
termind”. Published by Vivek Mehra for SAGE Pub-
blication India Pvt Ltd, ISBN 978-81-321-0062-1
(2009).
Rogers B. B. Engineering Principles for Security Mana-
gers – The Hanbook of Security Edited by Martin Gill
– Palgrave Macmillan, London, U.K. (2006).
ICEIS2013-15thInternationalConferenceonEnterpriseInformationSystems
554
