
Secure Alert Tracking in Supply Chain
Mehdi Khalfaoui
1
, Refik Molva
2
and Laurent Gomez
1
1
SAP Labs France, Mougins 06254, France
2
Eurecom , Biot 06410, France
Keywords:
Supply Chain, Wireless Sensor Networks, Privacy Preserving, Homomorphic Encryption, Alerts Detection.
Abstract:
Risk management practices, techniques and tools with respect to companies’ supply chains have begun to
receive more attention recently, as the need to improve supply chain performances has increased in order to
keep the balance between financial considerations and those of the customer interests. With the multiplication
of intermediate actors, a single threat at one point might compromise the safety of the all actors involved in
the supply chain process. Therefore, there is a clear need for product tracking in order to trace anomalies
for mitigation of potential threats in the future. Traditional approaches rely on operator-assisted verification
procedures that mainly suffer from the lack of global coverage. In this paper, we propose an automated process
to securely trace the supply chain actors that interact with the product, as well as the operations that were
performed, and the alerts that got raised. The core component of this process is wireless sensor nodes attached
to the product. Empowered with sensing capabilities, wireless sensor nodes are meant to raise alert in case of
detection of an anomaly. Our solution allows for tracing the path taken by a product and the recording of the
alerts that got raised, while preserving the actors’ privacy. The solution combines a polynomial path encoding
technique, together with additive homomorphic encryption to ensure the correctness of the path taken by a
product, and to preserve the privacy of the actors, respectively.
1 INTRODUCTION
Supply chain management (SCM) involves multiple
actors and processes. Those supply chain actors, of-
ten, have different roles and responsibilities. Identifi-
cation of each actor’s role and responsibility at supply
chain setup is mandatory requirement for making the
different actors fully accountable about their actions.
Accountability is defined as the requirement or duty
to provide an account or justification for one’s actions
to whomever is answerable (Swift, 2001). In other
words, each one of the actors involved in the activ-
ity is accountable, explains or justifies actions to the
authorities, whenever they demand.
Accountability calls for tracing the different
anomalies and accidents in the supply chain, and to
link them to the actors who is interacting with the
product at the moment when the anomaly occurs. An
anomaly tracking mechanism can help enhancing ac-
countability in supply chains. However, supply chain
is multi-actors environment, which raises security and
privacy challenges. Actors aim at tracking the anoma-
lies in the supply chain, which implies the tracking of
the involved actors, and the operations performed on
the product, yet they are reluctant to leak information
about their internal processes. Hence, preserving the
privacy of supply chain actors in this multi-partner en-
vironment has to be taken into account.
In that context, product safety and supply chain
actors are a mandatory requirement in today’s supply
chains. However, managing all the supply chain pro-
cesses, to have a trace of all the anomalies all along
the supply chain, can be difficult task thanks to the
complexity of the actors’ networks.
The purpose of this paper is to introduce an
anomaly tracking solution using wireless sensor net-
works. This mechanism allows the traceability of the
operations performed on the product, the actors that
interact with the latter, and the anomalies that were
detected by sensors. At each anomaly detection, sen-
sor raises an alert. Moreover, the mechanism pre-
serves the privacy of the involved actors, by allowing
to only authorized entities the ability of tracing. To
this effect, sensors are used as secure storage device
to store a mark that represents the product path. More
precisely, each product type will be attached to a spe-
cific sensor. At each new interaction with an actor,
the sensor’s memory is updated to add the current ac-
tivity identity. The set of identities collected by the
sensor identifies the path trace that the product went
219
Khalfaoui M., Molva R. and Gomez L..
Secure Alert Tracking in Supply Chain.
DOI: 10.5220/0004532102190229
In Proceedings of the 10th International Conference on Security and Cryptography (SECRYPT-2013), pages 219-229
ISBN: 978-989-8565-73-0
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

through. Moreover, if the sensor detects an anomaly
such as raising temperature, it will add it directly to
the path. At the end of the supply chain, a verifier ex-
tracts the trace and verifies its validity, and what the
exact alerts that got generated. The verifier is often
a supply chain manager that wants to have a global
overview of its supply chain in order to mitigate any
potential threats.
In order to preserve actors’ privacy, actors’ identi-
ties have to be kept secret. Encryption is a straightfor-
ward solution preventing eavesdroppers from steal-
ing identities and impersonatingany legitimate supply
chain actor. However, any technical solution that ad-
dresses secure and privacy preserving product track-
ing should take into account the limitations of sen-
sor nodes. These are constrained devices in terms
of computation power, memory, and energy. Due to
the limited memory featured by sensors, straightfor-
ward storage of the collected encrypted steps’ identi-
ties cannot be afforded. Thus, a compression mecha-
nism to reduce the size of the path traces is a manda-
tory requirement in order to overcome the memory
limitation of sensors. Also, the scarce energy re-
sources of sensor nodes, make the implementation of
complex functions such as public key encryption al-
gorithms difficult (Gennaro et al., 1997). Therefore,
our solution places all the complex computations on
the supply chain actor’s system in order to suit the
scarcity of the computational resources.
The main features of the suggested tracking
scheme are as follows:
• It allows the supply chain manager to verify the
legitimacy of the path taken by a product. More
precisely, it allows the supply chain manager to
verify which set of actors, a product has visited.
• It tracks all the anomalies that got raised by the
sensor nodes along the supply chain. For each
anomaly, our solution links it to the correspond-
ing supply chain actor.
• It guarantees the privacy of products and there-
with actors in the supply chain. Only the supply
chain manager is able to verify the path taken by
a product.
Moreover the scheme is suitable for low capacity
sensors. It only requires a few Kbytes storage. The
protocol execution for each supply chain step requires
only two modular multiplication.
1.1 Scenario: Importation of Chemicals
from China to Europe
Figure 1 illustrates typical supply chain example from
RESCUEIT project (Gomez et al., 2011). Aerosols
are imported from a Chinese harbour toward the har-
bour of Le Havre, in France. Shipped goods are
household and gardening chemicals: Garlon brush
cluttering 350 ml, DECAP four express 500 ml
and Ronstar 2kg. These products are meant to be
shipped by boat from a Chinese harbour. When re-
ceived at the Le Havre harbour, the merchandise is
checked by customs against REACH (Williams et al.,
2009)regulations. REACH is the European Commu-
nity Regulation on chemicals and their safe use (EC
1907/2006) (Williams et al., 2009). It deals with the
registration, evaluation, authorization and restriction
of chemical substances. The aim of REACH is to
provide an additional layer of protection for humans
and the environment through the better and earlier
identification of the intrinsic properties of chemical
substances. To that extend, REACH introduces spe-
cific constraints on chemicals along the supply chain.
They include the flash point, incompatibilities be-
tween products, and humidity conditions for chemi-
cals. At the Le Havre harbour, french customs with
the support of a Approved Economic Operator pro-
ceed to a merchandise integrity check. After a check
of administrative document describing the content of
the cargo, customs verify the quantity and quality of
the goods received. Once quality checks have been
performed at Le Havre harbour, and customs have
verified that the merchandise is compliant with safety
regulations, products are shipped by pickup trucks to-
ward the warehouse located close to Savigny le Tem-
ple. This warehouse belonging to K+N (Khune and
Nagel, 2013) is classified SEVESO II. This classifi-
cation defines a set of safety management systems,
emergency and land-use planning. In addition, it re-
inforces provisions on inspections to be carried out
by classified sites. In this case specific safety mea-
sures are implemented on site, such as storage rules
(e.g. limited quantity of chemical stored at the same
place). Finally, household and gardening products are
distributed by retailers (e.g. supermarket) such as the
Casino group (Casino, 2013).
In case of anomalies along the supply chain such
as temperature raising, the impact on population
safety, and on the environment can be disastrous. For
instance, an explosion might take place at the ship-
ment process, which depending on its intensity, fire
can have more or less serious impact on individual
health (e.g., slightly burning to death). Therefore,
anomalies detection mechanism should be in place to
mitigate potential accidents.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
220
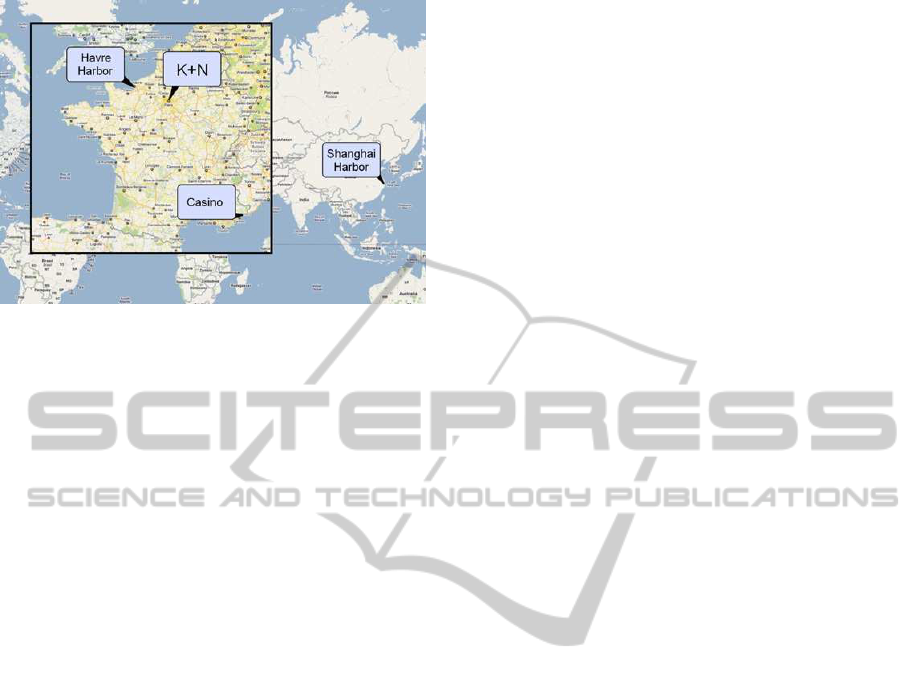
Figure 1: Import of Chemical Substance from outside of
EU.
2 RELATED WORK
Anomalies detection in supply chains has been around
as an active topic in research for many years. How-
ever, managing those anomalies and transiting it to
the right people has not been so deeply investigated
by research institutions. Often, supply chain actors
don’t disclose the detection of an anomaly, or they
simply ignore it for economical reasons (Trejo-Pech
et al., 2009). Therefore, any mitigation plan by the
supply chain manager is not complete since no com-
munication about potential threats was made. Wire-
less sensor networks with their sensing capabilities al-
low the detection of anomalies related to the physical
environment in real time. Accordingly, they are good
candidate to raise alerts if an anomaly occurs.
The usage of wireless sensor networks in supply
chains started with the need of real time product mon-
itoring. Many projects (Szewczyk et al., 2004; Bia-
gioni and Bridges, 2002; Werner-Allen et al., 2005;
Burrell et al., 2004; Gibbons et al., 2003) use wireless
sensor networks capabilities of sensing the physical
parameters of the environment and detecting at early
stage any potential threat. Nevertheless, those project
often neglect the multi-actors aspect of today’s supply
chains, and the need of supply chain actors to protect
their sensitive data, such as storage time, cost, their
clients, or even their suppliers. For instance Gomez
et al. (Gomez et al., 2012) suggested a mechanism
to delegate anomalies detection to sensor nodes. The
mechanisms is based on bytecode representation of
alerts to deal with the limited memory issues. How-
ever, the solution doesn’t take into account the privacy
of the involved supply chain, neither the threat of fake
alerts injection.
Cryptographic mechanisms preserving privacy of
supply chain actors are suggested by many re-
searchers. Khalfaoui et al. (Khalfaoui et al., 2012)
proposed a mechanism based on AND-ACC colli-
sion and paillier cryptosystem in order to trace the
steps and the activities that a product went through,
while preserving the privacy of the actors that inter-
acted with the product. Only the supply chain man-
ager, which is the verifier can trace the product path.
Elkhiyaouiet al. (Blass et al., 2011) proposed an cryp-
tographic mechanism on RFIDs to deal with simi-
lar tracing problem. Nevertheless, there is no ap-
proach that comprehensively addresses the problem
of anomaly detection in supply chains using sensors
and in a privacy-preserving manner.
3 BACKGROUND
A supply chain in this paper simply denotes a set of
sites that a product goes through. These sites perform
a specific activity involving the product such as pack-
aging, shipment, or storage. The main concern taken
into account by our solution is the privacy of the part-
ners in the supply chain against the other business
partners. Only, an authorized actor is able to recog-
nize the sites that a product visited, and the activity
that were performed. Formally, a supply chain is rep-
resented by a digraph G = (V,E) whereby each vertex
v represents one step in the supply chain. A step v in
the supply chain is uniquely associated with an entity.
Each directed edge e, which links vertex v
i
to ver-
tex v
j
, express that v
j
is a possible next step to step
v
i
in the supply chain. This simply means that ac-
cording to the organization of the supply chain, a
product might proceed to step v
j
after the comple-
tion of step v
i
. Whenever a product in the supply
chain proceeds to step v
i
, the entity interacts first with
the sensor. This latter may detect a potential threat.
Whenever the case, S added an alert alert
k
the path
trace. A path P is defined as finite sequence of steps
P = (v
0
,alert
0
),...,(v
l
,alert
l
), where l is the length
of the path P. A Path P is deemed valid if it is part
of a legitimate supply chain networks. The proposed
solution involves the following entities:
• Sensors S
i
: Each sensor is attached to a prod-
uct in the supply chain. A sensor S
i
features a
re-writeable memory that stores the trace T
(S
i
, j)
.
T
(S
i
, j)
represents the trace of the path that the sen-
sor took in the supply chain until site j. Sensors
can also compute a cryptographic function f to
authenticate the partners’ systems in the supply
chain.
• Issuer I : the issuer I attaches S
i
to a product and
writes into S
i
an initial trace T
(S
i
,0)
.
SecureAlertTrackinginSupplyChain
221

• Manager M: M wants to identify the sequence
of steps that S went through and the sequence of
alerts that S raised it all along the product path. M
therefore, reads the current trace T
(S,M)
of S, and
decides whether S visited legitimate sequence of
steps or not. Then, M extracts the different alerts.
We assume that M knows which paths in the sup-
ply chain are valid or not. In other words, M has
a database DB
valid
of valid path traces.
• Actors Ac
i
: supply chain actor is partner that be-
long to the supply chain, and may or may not
interact with the product. Each actor is allowed
to perform a set of supply chain activities on the
product. Without loss of generality, we assume
that each supply chain actor’s system Ac
i
. Ac
i
uses
some function f
Ac
i
to generate T
(S,step
j+1
)
from
T
(S,step
j
)
, i.e., f
Ac
i
(s
(S
i
, j)
) = T
(S, j+1)
.
• Alert alert
i
: an alert
i
is raised when an anomaly
is detected by S, such as increasing in temperature
or pressure above a defined threshold.
• Step step
i
: supply chain step step
i
step is an ac-
tivity that has been performed by a supply chain
actor. step
i
represents the i
th
activity performed
on the product.
Thus, an AlertSec system is:
• a Supply Chain G = (V,A)
• a Sensor S
• a set of possible traces T
• a set of different steps Steps
• a set of different alerts Alerts
• a supply chain manager M
• a set of valid paths P
4 PROTOCOL DESCRIPTION
4.1 Approach
In our scheme, the path trace combines the sequence
of the supply chain steps visited by S, and the alerts
that are generated during the product transition. The
main concept is to represent different paths in the
supply chain using different polynomials. More pre-
cisely, at the end of a supply chain’s valid path P
valid
,
a path’s trace is the evaluation of specific polynomial
at a fixed value x
0
. Therefore, a path in the supply
chain is represented by polynomial P(x
0
) that consists
of digest of the path.
However, the polynomial based path representa-
tion is vulnerable to prevent path cloning, i.e., copy-
ing the path of a valid sensor into a fake one to be
injected into the supply chain. To tackle this prob-
lem, sensors will store P(x
0
) multiplied by a keyed-
HMAC of their unique IDs. Keyed-HMAC serves the
following purpose: It proves that sensors are issued
by a legitimate authority and prevents an adversary
from injecting its own sensors. A path’s trace, there-
fore, consists of three elements that are: a unique ID,
HMAC
k
(ID) and HMAC
k
(ID)*P(x
0
). Our scheme
can be structured into four parts:
• Issuer I writes an initial trace into a sensor S.
• Supply chain actors successively compute the
evaluation of a polynomial to achieve the evalu-
ation of the final polynomial P(x
0
) at the end of
a valid path. Each actor visited by sensor updates
a new trace by applying specific arithmetic opera-
tions.
• sensor S raises alert and add it to the path trace.
• M extracts the trace from S, and checks if it is
valid one or not.
4.2 Preliminaries
4.2.1 Path Encoding Technique
The polynomial path encoding is used in (Blass et al.,
2011). It is based on techniques for software fault de-
tection. Noubir et al. (Noubir et al., 1998) propose to
encode a software’s state machine using polynomials
such that the exact sequence of states visited during
run-time generates a unique ”mark”. Therewith, run-
time faults can be detected. By considering the step
instead of state machine, the path encoding used by
Noubir et al. (Noubir et al., 1998) can be applied in
our case.
For each step step
i
in the supply chain, step
i
is
associated with a unique random identifier step
i
∈ F
q
, where q is a large prime.
As mentioned above, a path in the sup-
ply chain is represented as a polynomial ∈ F
q
.
The polynomial corresponding to a path P =
−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−→
(step
0
,alert
0
)(step
1
,alert
1
).. . (step
l
,alert
l
) is de-
fined in Equation (1). All operations are in F
q
.
Q
P
(x) =
l
∑
i=0
c
i
∗ x
l−i
(1)
where c
i
corresponds to the identity of either a step
j
or alert
l
.
To have a more compact representation of
paths, a path P is represented as the evaluation
SECRYPT2013-InternationalConferenceonSecurityandCryptography
222

of Q
P
at x
0
, where x
0
is a generator of F
∗
q
. We
denote φ(P ) = Q
P
(x
0
). The desired property of
anti-collision, .i.e ∀P 6= P ′,Pr(φ(P ) = φ(P ′)) =
1
q
(Noubir et al., 1998), ensures the uniqueness of the
path mark with high probability.
4.3 Paillier Cryptosystem
The following is description to the Paillier cryptosys-
tem (Paillier, 1999) that we use in order to achieve
both privacy and security of our mechanism:
Key Generation. Let k be the security parameter.
Choose uniformly and at random two k-bit primes p
and q, set N = pq, and set λ(N) = lcm(p − 1,q − 1).
Choose a random base g ∈ Z
∗
N
.
Encryption. To encrypt message m ∈ Z
N
, one
chooses a random value r ∈ Z
∗
N
and computes the ci-
phertext as
c = E (m,r) = g
m
r
N
modN
2
(2)
Decryption. When receiving a ciphertext c, check
that c < N
2
. If yes, retrieve the message m as
m = D(c) =
L(c
λ(N)
modN
2
)
L(g
λ(N)
modN
2
)
modN (3)
Where ∀u ∈ {u < N
2
/u ≡ 1modN}L(u) =
u−1
N
Additive Homomorphic Property. Paillier cryp-
tosystem has the property to be additively homomor-
phic:
E (m
1
,r
1
) ∗ E (m
2
,r
2
) = E(m
1
+ m
2
,r
1
r
2
) (4)
This property allows the execution of arithmetic op-
erations on encrypted data. Therefore, it supports the
evaluation of the polynomial mark at each step of the
supply chain without decryption.
Self Blinding. Paillier cryptosystem has the prop-
erty to be Self-Blinding, i.e the property by which
any ciphertext can randomly be changed into an-
other without affecting the plaintext. This property
is achieved as follows:
∀r ∈ Z
N
D(E(m,r)) = m (5)
Therefore, the decryption of any message m is in-
dependent of the value of r.
4.4 Detailed Protocol Description
Our protocol consists of several phases, which we de-
scribes as follows:
• Initialization. This phase is responsible for ini-
tializing the supply chain actors and the wireless
sensor nodes.
• Authentication. This phase is responsible for veri-
fying the legitimacy of the actors that interact with
sensors.
• Collection. This phase is responsible for col-
lecting the actors’ identities, and alerts to have a
unique path trace.
• Verification. This phase is responsible for verify-
ing the correctness of the path trace and the ex-
traction of the different alerts.
4.4.1 Initialization
In this phase, we assume that every actor in the sup-
ply chain has the required resources to perform the
following actions:
• I generates randomly a list of steps identifiers for
each actor. I distributes each step’s identity to the
corresponding actor.
• I generates a Paillier public key pk
M
and private
key sk
M
. Then I sends E
M
(step
i
) to its actor in
secure way.
• M shares with the supply chain actors a Rabin’s
private key (p
R
,q
R
). Rabin cryptosystem (Ra-
bin, 1979) is used to achieve authentication of the
supply chain actors. Rabin encryption is single
square modular encryption, which makes it feasi-
ble for low capacity devices such as sensor nodes.
Rabin’s public key N
R
= p
R
q
R
is stored in the sen-
sor to perform the authentication process.
• M generates the identifiers list S
list
of sensors. For
the sake of simplicity, we assimilate a sensor S
i
and its identifier ID
i
. I stores in each sensor S
i
,
the Paillier encryption of its ID
i
, the Paillier en-
cryption of HMAC
k
(S
i
), where HMAC
k
is keyed
hash function (Bellare et al., 1996), and k is its
secret key.
• M generates the identifiers list alert
list
of alerts.
M stores in each sensor S
i
, the Paillier encryption
of the all alerts needed, and the Paillier encryp-
tion of HMAC
k
(S
i
), where HMAC
k
is keyed hash
function (Bellare et al., 1996), and k is its secret
key.
At the completion of this phase, each sensor is ini-
tialized with the value of the initial trace, that is,
E(HMAC
k
(S
i
)).
SecureAlertTrackinginSupplyChain
223

4.4.2 Trace Update
In this phase, the sensor S and the actor’s system in-
teract in the supply chain by executing the follow-
ing actions: We assume that the sensor S has visited
the steps step
0
, ..., step
l
. When, S visits the actor’s
system step
l+1
, it is already stored the trace P
l
=
−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−→
(step
1
,alert
1
)(step
2
,alert
2
)...(step
l
,alert
3
) that en-
codes the path from the sites that belong to the
steps step
1
,step
2
,.. . ,step
l
, and raised the alerts
alert
1
,alert
2
,.. . ,alert
3
. Therefore, the current state
of the sensor is E(P
l
), which corresponds to the path
trace after interacting with the l steps.
4.4.3 Authentication
S chooses a random value r ∈ F
N
R
and sends
Rabin(r) = r
2
modN
R
to A, while storing the hash(r)
and hash(N
R
− r). A decrypts Rabin(r) using its pub-
lic key. The decryption gives exactly four solutions,
r, N
R
− r, t, N
R
−t. As the actor does not know which
is the real solution, he chooses to send back to S two
hash values. The values are chosen in such a way that
their sum is not null modN
R
. For example A chooses
to send hash(r), and hash(N
R
− t). Therefore, S con-
siders the authentication as successful, if one of the
received value matched one of the stored value. Then,
S can start trace collection procedure.
4.4.4 Collection
After the authentication phase, S starts the collection
phase. S sends its current state s(S, l) to the actor’s
system A
l+1
. For the sake of simplicity, we assume
there is no alert has been raised at this point of time.
Therefore, actor
l+1
updates the sensor’s state as fol-
lows:
s(S,l + 1) = s(S, l)
x
0
∗ E
M
(c
l+1
) (6)
= s(S,l)
x
0
∗ g
c
l+1
r
N
modN
2
(7)
Assuming that our products has to interact with n sup-
ply chain partner, the final sensor’s state is:
T(S,n) = T(S,n− 1)
x
0
∗ g
step
n
r
N
1
modN
2
= T(S,0) ∗ g
∑
n
i=1
step
i
x
0
n−i
r
N
2
modN
2
= g
HMAC
k
(S)x
n
0
+
∑
n
i=1
step
i
x
0
n−i
r
N
3
modN
2
= E
M
(HMAC
k
(S)x
0
n
+
n
∑
i=1
step
i
x
0
n−i
)
(8)
where r
1
,r
2
, andr
3
are in F
N
R
. (9)
4.4.5 Alert Injection
Now Let’s assume that an alert step
m
is raised just
after the step
k
. S updates its internal trace to take into
account the current alert. As the last step is step
k
, the
current state of S is s(S,k). S adds the alert to the trace
as follows:
T(S,k, alert
i
) = T(S, k)
x
0
∗ g
alert
i
∗x
d
0
r
N
1
modN
2
,where r
1
∈ F
N
= E
M
(HMAC
k
(S)x
0
n
+
k
∑
j=1
step
j
∗ x
0
n− j
+ alert
i
∗ x
d
0
)
(10)
(11)
(12)
4.4.6 Path Verification
In this phase, the supply chain manager M checks if
the path recorded in the sensor is a valid one. M ex-
tracts the final trace from the sensor T(S,n), and de-
crypts it, so he can extract the path trace φ(P ).
φ(P ) = D
TTP
(T(S, n)) =
n
∑
i=1
a
i
x
i
= HMAC(S)x
m
0
+
m
∑
i=1
step
i
x
0
m−i
+ (13)
n
∑
i=d+p
alert
i−d
x
0
d+p−i
(14)
Using successive division operations, M extracts
the coefficients a
0
,a
1
,... ,a
n
of the polynomial φ(P ).
Then, M computes HMAC
k
(S) and compare it with
a
m
. If a
m
= HMAC
k
(S), M accepts the sensor. Other-
wise, M rejects S.
4.4.7 Alert Detection
Finally, M checks if the step identifiers step
1
, step
2
,
..., step
m
belongs to the list of valid steps’ identi-
fiers, and the path trace φ(P )modx
d
0
proofs that the
sequence of the steps is valid. if one of the identifiers,
or the sequence is not valid, M rejects the sensor, and
declares the product as not compliant. M retrieves the
alerts alert
0
, alert
1
, ..., alert
l
as follows:
alert
i
= a
d+p−i
(15)
alert
i
is detected at step (m + d) − (d + p − i)
which is step
m−p+i
.
5 SECURITY ANALYSIS
In this section we prove the security of AlertSec sys-
tem. The proof was inspired from (Ouafi and Vaude-
nay, 2009). Let’s A an adversary that has the purpose
of forging a valid path.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
224

5.1 A is not a Legitimate Actor
if A authenticates successfully itself to S, she breaks
the Rabin scheme security by definition. Therefore,
only the legitimate supply actors can try to update the
path trace maliciously.
if A took a blank sensor and try to inject a valid
trace on it (from scratch), we use the security of
keyed-HMAC to proof the infeasibility of this case.
Security of keyed-HMAC. For our proof sketch,
we are using the property indistinguishability of
keyed hash function.
Indistinguishability Property Let O
distinguish
be an
oracle that when A provides it with a message m,
O
distinguish
returns with the same probability a ran-
dom number, or HMAC
k
(m). A cannot guess with
no-negligibleprobability if the returned value is a ran-
dom number, or HMAC
k
(m).
Lemma. Producing a new valid trace contradicts
the indistinguishiability property of HMAC
k
.
Proof (Sketch). From A , we can build an adversary A
′
that uses A to break the indistinguishability property
of keyed-HMAC. we provide A , with a sensor S and
its s
id
. A produces a new valid trace E (T
m
) that corre-
sponds to the sensor s
id
. A provides s
id
to O
distinguish
.
O
distinguish
returns value H to be tested. A decrypts
E (T
m
). She gets T
m
, and computes T
m
mod H. If
T
m
mod H = 0, H is the HMAC
k
(s
i
d), otherwise H is
a random number.
5.2 A is a Legitimate Actor
If A is legitimate actor, the authentication process will
succeed, and S accepts the received value from A .
In this case, the decisional composite residuosity as-
sumption to prove the security of our protocol against
forgery by a legitimate actor.
The Decisional Composite Residuosity Assump-
tion (DCRA). The DCRA states that given a com-
posite n and an integer z, it is hard to decide whether z
is a n-residue mod n
2
or not. In other words, whether
there exists y such that z = y
n
mod n
2
. This assump-
tion is mainly used to proof the semantic security of
Paillier cryptosystem (Paillier, 1999).
Cryptographic protocol is semantically secure if its
indistinguishability against chosen plaintext attacks
(IND-CPA) holds.
SPT is Semantically Secure if and only if DCRA
and the Indistinguishibilty of keyed-HMAC Hold.
Proof. The main idea of this proof is to build an at-
tacker A ′ from A whose advantage ε to forge a valid
path, that is able to break DCRA. As shown in the
previous Lemma, A cannot provide a new valid path
trace from scratch. Now, Let’s assume that A can up-
date a valid path trace that she got from the learning
phase to a new valid path trace. For the sake of sim-
plicity, we consider that the AlertSec system has only
one valid path.
Let O
DCRA
be an oracle that, when it is queried
with a parameter n, it flips a coin b ∈ 0, 1. If b =
1 it takes a y ∈ Z and returns y
n
mod n
2
otherwise, it
returns a random number C.
A ′ creates AlertSec system with a valid path,
(step
0
, ..., step
m
). Then, she generates the AND-
ACC identifier corresponds to each step.
Let E (T
m−1
) be the encrypted path trace until the
step
m−1
. First, A
′
sends a query to O
DCRA
with N
(Paillier modular) as parameter, and gets a challenge
C. A
′
computes E (T
m−1
)*C mod N
2
, and writes the
result in a sensor S.
If in the challenge phase, A is able to update the trace
to a valid path trace E(T
m
), then E (T
m−1
). C mod
N
2
is a valid ciphertext of T
m−1
(i.e E (T
m−1
). C mod
N
2
is re-encryption to E (T
m−1
) ). Therefore, C is N-
residue mod N
2
, and A
′
breaks the DCRA assump-
tion, with advantage of 1/2*ε, since she is wrong half
of the time because of oracle’s coin flip.
Table 1 illustrates the messages exchanged between
the involved entities during the challenge game.
6 PRIVACY ANALYSIS
In this section we prove the privacy requirement of
step unlinkability of AlertSec system. Step unlinka-
bility is defined as preventing an adversary A from
telling that two different sensors interacted with a
common step.
Theorem. AlertSec provides step unlinkability un-
der DCRA.
Proof. Assume there is an adversary A whose advan-
tage ε to break the step unlinkability experiment is
non-negligible. We now construct a new adversary
A
′
that executes A and breaks the semantic security
of Paillier.
Let O
DCRA
be an oracle that, when it is queried
with a parameter n, it flips a coin b ∈ 0, 1. If b =
SecureAlertTrackinginSupplyChain
225

Table 1: Forgery challenge game.
O
DCRA
A
′
A
receive N ←− send N
pick C −→ receive C
compute E (T
m−1
).Cmod N
2
−→ receive E(T
m−1
).Cmod N
2
receive E (T
m
) ←− update trace E (T
m
)
receive 1 or 0 ←− if E (T
m
) is valid, send 1 else send 0
1 it takes a y ∈ Z and returns y
n
mod n
2
otherwise, it
returns a random number C.
A ′ creates AlertSec system with multiple valid
paths. Then, She generates the AND-ACC identifiers
correspond to each step. First, A
′
sends a query to
O
DCRA
with N (Paillier modular) as parameter, and
gets a challengeC. Then, A
′
builds two traces for two
different path, with one step in common. Let E (T
m
)
the path trace for the path (step
0
, . .., step
m
), and
E (T
′
m
) the path trace for the path (step
′
0
, ..., step
′
m
)
with step
i
and step
′
i
are the common step. However,
the identifier is E (v
i
) for step
i
and E (v
i
)*C mod N
2
for step
′
i
. A
′
provides the two traces to A
′
in the
challenge phase.
If in the challenge phase, A is able to decide if
both traces has a common step with an advantage
ε, then E (v
i
). C mod N
2
is a valid ciphertext of v
i
). Therefore, C is N-residue mod N
2
, and A
′
breaks
DCRA, with advantage of 1/2*ε, since She is wrong
the half of the time because of oracle’s coin flip.
Table 2 illustrates the messages exchanged during the
challenge game.
7 PERFORMANCE ANALYSIS
This section is allotted to present the analytical perfor-
mance evaluation of the proposed scheme. We only
evaluate the performances related to the sensor itself.
The performance evaluation criteria of the sensor, are
the storage cost, the computation cost and the com-
munication cost.
7.1 Storage Cost
The storage cost is computed as the number of bytes
that the sensor node has to store. Generally, this stor-
age cost is introduced by the storage of different pa-
rameters and keys necessary to the function of the
our scheme. The proposed privacy preserving prod-
uct tracking scheme does not require much memory
overhead.
• Initialization phase: in this phase, the sensor has
to store Rabin’s public key of size sizeof(N
R
),
the path trace initialization sizeof(E (T)), a sen-
sor ID of size sizeo f(S
id
), and k4 encrypted
alerts of sizeo f(E(T)) each. Therefore, the to-
tal storage needed by S at this phase is (k + 1) ∗
sizeof (E (T)), + sizeof(S
id
) + sizeof(N
R
).
• Collection phase: In this phase, S has to gener-
ate random number to start the authentication with
the actor’s system. The generated nonce has a
size of sizeof(N
R
). Hash value of the generated
nonce of size sizeof(hash) has to be stored as
well. Therefore, the the total storage needed by
S at this phase is sizeof(N
R
) + sizeof(hash). The
update path process does not increase the size of
the path trace, thus, no more memory capacity is
required.
• Verification phase: In this phase, no storage by the
sensor is required.
The total storage cost needed by S in our scheme is
(k+1)∗sizeof(E(T)), + sizeof(S
id
) + 2∗sizeof(N
R
)
+ sizeof(hash).
7.2 Energy Cost
7.2.1 Computation Cost
The computation cost can be measured in terms of
time, use of CPU or energy dissipation. In fact, these
parameters are related and each one can be deduced
from the other. For instance, the energy dissipa-
tion can be deduced from the time as follows: En-
ergy=Power*Time, where Power represents the CPU
power when it is in its active state and Time represents
the computing time. In the present analysis, the term
SECRYPT2013-InternationalConferenceonSecurityandCryptography
226

Table 2: Step unlinkability challenge game.
O
DCRA
A
′
A
receive N ←− send N
pick C −→ receive C
compute E(T
m
) and E (T
′
m
) −→ receive E (T
m
) and E (T
′
m
)
receive 1 or 0 ←− check if E (T
m
) and E (T
′
m
) have a common step
receive 1 or 0 ←− if 1 is received, send 1 otherwise send 0
cost is used in its general form without specifying the
unit. The computation cost of our scheme during each
phase can be computed as the sum of the computa-
tion cost of the main operations executed during this
phase.
• Initialization phase: in this phase, the main opera-
tions are performed by the supply chain manager
M himself. Therefore, No computation required
by the sensor S in this phase.
• Collection phase: in this phase, S generates a ran-
dom number, then S has to encrypt it using rabin
scheme (i.e. single modular square). S computes
a hash in order to check the validity of the actor’s
response. Then, S updates its trace by adding alert
to it, which has a cost of single modular multipli-
cation. In total, S consumes c(rabin) + c(rand) +
c(hash) +c(modularmultiplication) for each in-
teraction with a single (step,alert) at maximum.
Indeed, if there is no alert detected, no modular
multiplication is required.
• Verification phase: In this phase, S has to authen-
ticate the supply chain manager M, which is simi-
lar to authenticate a supply chain actor. therefore,
S consumes in this phase, c(rabin) + c(rand) +
c(hash).
The total computation cost needed by S in our
scheme is (c(rabin) + crand + c
hash
)*(l + 1) +
+c(modularmultiplication)*m, where m is the num-
ber of steps in the supply chain.
7.2.2 Communication Cost
The main factor of the communication cost is the en-
ergy dissipation. The communication cost is com-
puted using the same approach as TKH (Son et al.,
2010). Actually, the communication cost in terms
of energy dissipation is computed as the size of
sent/received messages multiplied by the energy dis-
sipated for the sent/receive of one bit. We denote e
r
the energy consumed by S, when it receives one bit,
and e
s
when S sends one bit.
• Initialization phase: In this phase, S does not
send any messages, however, it receives the ini-
tialization parameters. therefore, S consumes
(sizeof(N
R
)+ sizeof(S
id
)+sizeof(E (T)))*e
r
.
• Collection phase: In this phase, S sends encrypted
rabin value, which has the same size as the rabin’s
public key, then S receivesa hashed value. Then, S
receives the encrypted step’s identity from the ac-
tor’s site. Therefore, S consumes (sizeof(N
R
))*e
s
+
(sizeof(hash) +sizeof(E (T)))* e
r
for each interac-
tion with a single step.
• Verification phase: In this phase, S exchanged the
same messages with the supply chain manager as
it performs with a supply chain actor’s site, ex-
cept of the received updated path trace. There-
fore, S consumes (sizeof(N
R
)+ sizeof(E (T)))*e
s
+
(sizeof(hash))* e
r
The total communication cost needed by
S in our scheme is (sizeof(N
R
)+ sizeof(hash)*
(l + 1) + sizeof(S
id
)+sizeof(E (T))*l + 1)*e
r
+(sizeof(N
R
)*(l + 1)+ sizeof(E (T)))*e
s
where l is
the number of the supply chain actors that interact
with the product.
It is worth to mention that the storage cost, com-
putation cost, and the communication cost can have a
different result depending on the size of the security
keys, and the algorithms that the supply chain man-
ager may choose.
In this paper, a Rabin’s public key has a size
of 1024 bits. The hash function used is SHA1,
which has an output size of 160 bits. Paillier en-
cryption has an output’s size of 2048 bits. For
sensor identity, a size of 160 bits is chosen. Ra-
bin’s encryption is a single modular square which
requires roughly 100µJ using ATmel128 micropro-
cessor (http://www.atmel.com/Images/doc2467.pdf, )
based on the result of Gaubatz et al. (Gaubatz et al.,
2005). In our scheme, we use the TinyRNG (Francil-
lon and Castelluccia, 2007) to generate random num-
bers. TiyRNG consumes around 58µJ at each ran-
SecureAlertTrackinginSupplyChain
227
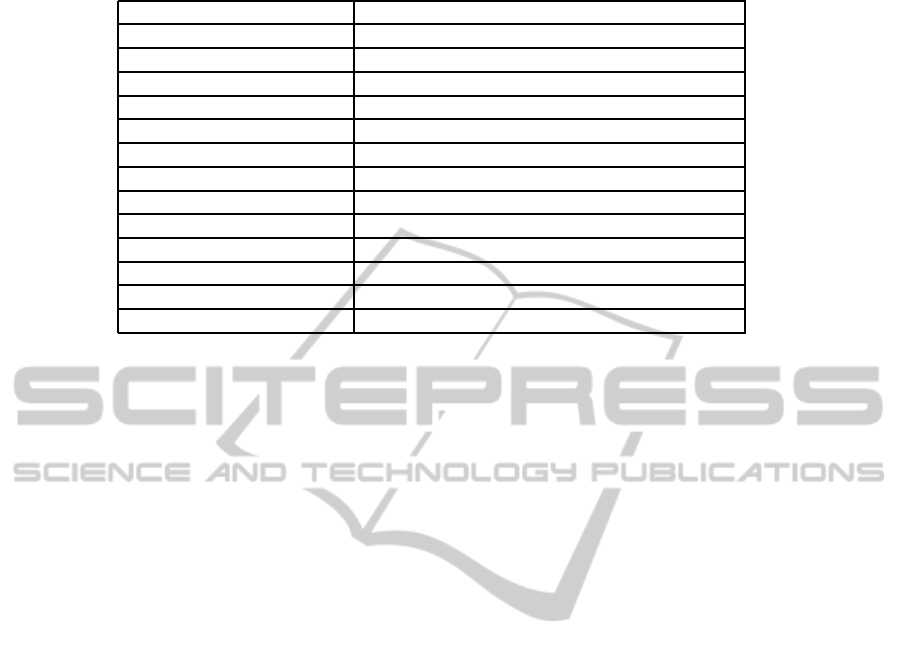
Table 3: Performance analysis of AlertSec.
Parameter value
sizeof(S
id
) 160 bits
sizeof(N
R
) 1024 bits
sizeof(hash) 160 bits
sizeof(E (T)) 2048 bits
c(rabin) 100µJ
c(modularmultiplication) 100µJ
c(rand) 58µJ
c(hash) 1µJ
e
r
0,209µJ
e
s
0.226µJ
The storage cost 20714 bits for 8 alerts
the computation cost 161, 59mJ for 100 steps and 10 detected alerts
the communication cost 12,34mJ for supply chain with 100 steps
dom number generation. Hash function consumes
roughly 1µJ (Hempstead et al., 2008). The commu-
nication cost are set to e
s
=0.209µJ and e
r
=0.226µJ
from the characteristics of the CC2420 transceiver
used in the Xbows MICA-Z and Telos B sensor
nodes (http://www.xbow.com/, ).
Table 3 shows that our protocol is imple-
mentable using today’s sensors such as Cross-
bow motes (http://www.xbow.com/, ) and phidgets
(http://www.phidgets.com/, ). It only requires sen-
sors to store mainly the Rabin public key, which is
1024 bits, and the encrypted state, which is 2048 bits.
Through the different steps of the supply chain, the
amount of memory needed does not increase.
8 CONCLUSIONS
In this paper, we presented a protocol to secure the
tracking of products and alerts in supply chain. Our
main idea is to encode the path of the products us-
ing polynomial path encoding. Partners in the supply
chain update the path trace successively, such that the
path has unique identifier. Whenever a sensor detect a
potential threat, it updates its internal trace by adding
the specific alert. Our protocol’s security and privacy
proprieties relies on the semantic security of Paillier
and the security of keyed-HMAC. It requires only one
modular multiplication in each step, and only 3Kb of
storage, which ensures its feasibility in available sen-
sors in the market.
In our supply chain scenario, we assume that we have
a global supply chain manager. There is no notion
of multiple managers. However in real world, that is
might not be true. Supply chain can have a quality,
security, and recall manger. Delivering the right in-
formation to the right manager is an issue, especially
in big scale supply chains. However, this is left to
future work
REFERENCES
Bellare, M., Canetti, R., and Krawczyk, H. (1996).
Keying hash functions for message authentication.
In Advances in CryptologyCRYPTO96, pages 1–15.
Springer.
Biagioni, E. and Bridges, K. (2002). The application
of remote sensor technology to assist the recovery
of rare and endangered species. International Jour-
nal of High Performance Computing Applications,
16(3):315–324.
Blass, E., Elkhiyaoui, K., and Molva, R. (2011). Tracker
: security and privacy for rfid-based supply chains.
In NDSS’11, 18th Annual Network and Distributed
System Security Symposium, 6-9 February 2011, San
Diego, California, USA, ISBN 1-891562-32-0.
Burrell, J., Brooke, T., and Beckwith, R. (2004). Vineyard
computing: Sensor networks in agricultural produc-
tion. Pervasive Computing, IEEE, 3(1):38–45.
Casino (2013). Casino group.
Francillon, A. and Castelluccia, C. (2007). Tinyrng: A cryp-
tographic random number generator for wireless sen-
sors network nodes. In Modeling and Optimization
in Mobile, Ad Hoc and Wireless Networks and Work-
shops, 2007. WiOpt 2007. 5th International Sympo-
sium on, pages 1–7. IEEE.
Gaubatz, G., Kaps, J., and Sunar, B. (2005). Public key
cryptography in sensor networksrevisited. Security in
Ad-hoc and Sensor Networks, pages 2–18.
Gennaro, R., Krawczyk, H., and Rabin, T. (1997). RSA-
based undeniable signatures. Advances in Cryptolo-
gyCRYPTO’97, pages 132–149.
Gibbons, P., Karp, B., Ke, Y., Nath, S., and Seshan, S.
(2003). Irisnet: An architecture for a worldwide sen-
sor web. Pervasive Computing, IEEE, 2(4):22–33.
Gomez, L., Gaci, O., Deutsch, J., and El-Khoury, E. (2012).
Sensor based risk assessment for the supply of dan-
gerous products. In SENSORCOMM 2012, The Sixth
SECRYPT2013-InternationalConferenceonSecurityandCryptography
228

International Conference on Sensor Technologies and
Applications, pages 342–348.
Gomez, L., Khalfaoui, M., El-Khoury, E., Ulmer, C.,
Deutsch, J., Chettouh, O., Gaci, O., Mathieu, H., El-
Moustaine, E., Laurent, M., et al. (2011). Rescueit:
securisation de la chaine logistique orientee service
depuis le monde des objets jusqua lunivers informa-
tique. In Workshop Interdisciplinaire sur la Securite
Globale.
Hempstead, M., Lyons, M., Brooks, D., and Wei, G. (2008).
Survey of hardware systems for wireless sensor net-
works. Journal of Low Power Electronics, pages 11–
20.
http://www.atmel.com/Images/doc2467.pdf. Last access:
01/06/2012.
http://www.phidgets.com/. Last access: 12/06/2011.
http://www.xbow.com/. Last access: 01/06/2012.
Khalfaoui, M., Molva, R., and Gomez, L. (2012). Secure
product tracking in supply chain. In INSCRYPT 2012,
8th International Conference on Information Security
and Cryptology, 28-30 November 2012, Pekin, China,
Pekin, CHINA.
Khune and Nagel (2013). Khune and nagel group.
Noubir, G., Vijayananda, K., and Nussbaumer, H. (1998).
Signature-based method for run-time fault detection
in communication protocols . Computer Communica-
tions, pages 405–421.
Ouafi, K. and Vaudenay, S. (2009). Pathchecker: An RFID
Application for Tracing Products in Supply-Chains. In
International Conference on RFID Security. Citeseer.
Paillier, P. (1999). Public-key cryptosystems based
on composite degree residuosity classes. In Ad-
vances in Cryptology, EUROCRYPT99, pages 223–
238. Springer.
Rabin, M. (1979). Digitalized signatures and public-key
functions as intractable as factorization.
Son, J.-H., Lee, J.-S., and Seo, S.-W. (2010). Topological
key hierarchy for energy-efficient group key manage-
ment in wireless sensor networks. Wirel. Pers. Com-
mun., 52(2):359–382.
Swift, T. (2001). Trust, reputation and corporate account-
ability to stakeholders. Business Ethics: A European
Review, 10(1):16–26.
Szewczyk, R., Osterweil, E., Polastre, J., Hamilton, M.,
Mainwaring, A., and Estrin, D. (2004). Habitat mon-
itoring with sensor networks. Communications of the
ACM, 47(6):34–40.
Trejo-Pech, C. J., Weldon, R. N., House, L. A., and Gun-
derson, M. A. (2009). The accrual anomaly finan-
cial problem in the food supply chain. Agribusiness,
25(4):520–533.
Werner-Allen, G., Johnson, J., Ruiz, M., Lees, J., and
Welsh, M. (2005). Monitoring volcanic eruptions with
a wireless sensor network. In Wireless Sensor Net-
works, 2005. Proceeedings of the Second European
Workshop on, pages 108–120. IEEE.
Williams, E. S., Panko, J., and Paustenbach, D. J. (2009).
The european union’s reach regulation: a review of its
history and requirements. Critical reviews in toxicol-
ogy, 39(7):553–575.
SecureAlertTrackinginSupplyChain
229
