
FORMALIZING END-TO-END CONTEXT-AWARE TRUST
RELATIONSHIPS IN COLLABORATIVE ACTIVITIES
Ioanna Dionysiou
Department of Computer Science, School of Sciences, University of Nicosia, Nicosia, Cyprus
Dave Bakken, Carl Hauser
Department of Computer Science, School of Electrical Engineering and Computer Science
Washington State University, Pullman, WA, U.S.A.
Deborah Frincke
CyberSecurity Group, Pacific Northwest National Laboratory, Richland, WA, U.S.A.
Keywords:
Trust relation, dynamic trust, composable trust, activity-oriented trust.
Abstract:
The diversity of the kinds of interactions between principals in distributed computing systems, including
critical infrastructures, has expanded rapidly in recent years. However, such applications and their users
are vulnerable with respect to both the diversity of the principals providing these services or data and the
interactions between them. This paper introduces formalisms for a new trust model that addresses these
limitations. The novelty of the new model is its ability to specify and reason about trust dynamically and when
composed beyond pairwise relationships for a specific interaction. An intuitive and practical way is presented
to manage end-to-end trust assessment for a particular activity, where multiple trust relationships are examined
in order to derive the overall trust for the activity.
1 INTRODUCTION
Distributed computing has evolved greatly in the last
decade or so. Interactions between entities used to
be mainly client-server or database oriented. Recent
years have seen a great increase in the kind and num-
ber of entities interacting, the patterns in which they
interact, and the kinds of distributed services support-
ing these interactions. This ubiquitous use of dis-
tributed applications provides increased convenience,
safety, and enjoyment for society. However, such ap-
plications and their users are vulnerable with respect
to both the diversity of the principals providing these
services or data and the interactions between them.
Consider the North American electric power grid,
for instance, with nearly 3500 utility organizations
(Force, 2004). These individually owned utility sys-
tems have been connected together to form intercon-
nected power grids, which must be operated in a coor-
dinated manner. There are many points of interactions
among a variety of participants and a local change can
have immediate impact everywhere. In order to detect
disturbances that could escalate into cascading out-
ages and take corrective actions, real-time informa-
tion about the grid dynamics must be obtained to en-
hance the wide-area system observability, efficiency,
and reliability. Power utilities are reluctant to disclose
information in order to protect themselves financially
and legally. Sharing of data might jeopardize their
business due to their inability to quantify the risk re-
garding interactions with other grid participants. For
example, unrestricted access to a utility’s data that are
market-sensitive indicators could give a competitor an
unfair advantage in adjusting its own contracts and
prices. Similarly, a utility could distribute inaccurate
data to mislead the other market participants.
The “no sharing” policy could be relaxed un-
der normal operating conditions if the risk of shar-
ing were systematically contained (Dionysiou et al.,
2007). In order to do that, private, public and national
entities must collaborate in a way that sensitive infor-
mation is shared without compromising it. This col-
laborative environment is nontrivial to establish and
operate because its participants do not have the nec-
546
Dionysiou I., Bakken D., Hauser C. and Frincke D. (2008).
FORMALIZING END-TO-END CONTEXT-AWARE TRUST RELATIONSHIPS IN COLLABORATIVE ACTIVITIES.
In Proceedings of the International Conference on Security and Cryptography, pages 546-553
DOI: 10.5220/0001926905460553
Copyright
c
SciTePress

essary knowledge and tools to assess the quality of
the received data and the risk of compromising that
data. Trust management is a service that, when used
properly, has the potential to enable the entities that
operate within critical infrastructures to share confi-
dential, proprietary, and business sensitive informa-
tion with reliable partners.
In this paper, we introduce a conceptual trust
model that allows entities to reason about the fol-
lowing issues: how to specify and adapt the degree
of trust that they place in an entity (dynamic trust)
and how much trust to place in data they receive that
comes through nontrivial chains of processing or ser-
vices without using traditional transitivity (compos-
able trust). To be more specific, the paper presents
the following contributions:
• A notation for specifying trust relationships that
are tied not only to a narrow context but to a
broader activity
• An intuitive and practical way to manage end-
to-end trust assessment for a particular activity,
where multiple trust relationships are examined in
order to derive trust for the activity, including ex-
plicit consideration of expectations and their vio-
lations in analyzing end-to-end trust
The remainder of the paper is organized as fol-
lows. Section 2 discusses trust among collaborators
for a specific activity. Section 3 presents our con-
ceptual trust model, with emphasis on the trust on-
tology involved in deriving end-to-end trust assess-
ments. Related work is discussed in Section 4 and
Section 5 concludes.
2 ACTIVITY-ORIENTED TRUST
RELATIONSHIPS
Creating a universally acceptable set of rules and
mechanisms to specify trust is a difficult process be-
cause of the variety in trust interpretations. Re-
searchers have defined trust concepts for many per-
spectives, with the result that trust definitions overlap
or contradict each other (Presti et al., 2003). Never-
theless, trust is an abstraction of individual beliefs that
an entity has for specific situations and interactions.
An entity’s beliefs are not static but they change as
time progresses and new information is processed into
knowledge. Trust must evolve in a consistent manner
so that it still abstracts the entity’s beliefs accurately.
In this way, an entity continuously makes informed
decisions based on its current beliefs.
In a typical trust setting, there is a trustor and
a trustee. A trustor is the entity that makes a trust
ACTIVITY
Context
1
Trustee
1
Trustee
k
...
Context
N
Trustee
1
Trustee
m
......
Figure 1: Context-Aware Activity.
assessment for an entity, which is the trustee. The
scope of the trust relationship between a trustor and
a trustee is narrowed to a specific action called a
context. A trust relationship may be one-to-many
to cover a group of trustees, which are trusted simi-
larly within the same context (Grandison and Sloman,
2000). Such approach cannot encompass the com-
plexity of trust in an activity that involves different
contexts and trustees. An activity is an interaction
that involves multiple trustees that may assume dif-
ferent roles (Figure 1); in other words, the successful
outcome of an activity requires the collaboration of
trustees performing specific functions, which are not
necessarily the same.
Consider Figure 2. In this setting, there is a data
stream d between entity P and entity C. It could ap-
pear that entity C may assess the risk of using data
d by making a trust assessment regarding entity P’s
ability to produce reliable data d. However, this is
not sufficient. The presence of intermediate entities
S
1
and S
2
that forward this data to C affect the qual-
ity of received data d. As a result, trustor C has to
make trust assessments for all interacting trustees that
collaboratively execute a task and combine them in
order to derive an end-to-end trust assessment about
the quality of the data stream. Thus, if C were to make
a trust assessment concerning the activity of the infor-
mation flow between P and itself, then the following
trust relationships had to be examined:
• relationship τ(C, P,...)
1
between P and C regard-
ing P’s ability to produce data d
• relationship τ(C, S
1
, ...) between S
1
and C regard-
ing S
1
’s ability to forward data d
• relationship τ(C, S
2
, ...) between S
2
and C regard-
ing S
2
’s ability to forward data d
3 TRUST MODEL ONTOLOGY
The theory of sets and relations is used to represent
trust between trustors and trustees (Dionysiou, 2006).
This section formally defines trust between trustors
1
For simplicity reasons, we omit for now the remaining
trust attributes
FORMALIZING END-TO-END CONTEXT-AWARE TRUST RELATIONSHIPS IN COLLABORATIVE ACTIVITIES
547

trustee
P
trustor
C
trustee
S
1
data d
interaction id
1
data d
interaction id
1
trustee
S
2
data d
interaction id
1
information flow
trust relationship
τ(C,S
2
,...)
τ(C,P,...)
τ(C,S
1
,...)
Figure 2: Trust Relationships in an Activity.
and trustees as a relation τ and examines the rela-
tion’s attributes, properties, and operations. The nota-
tion τ(γ, δ, c, λ, ι, ε, id, s) represents a trust relationship
between two entities and it is interpreted as “trustor γ,
based on γ’s trusting attitude, believes that the extent
to which trustee δ will act as expected for context c
during time interval ι is λ, and this belief is subject to
the satisfaction of expectation set ε. This relationship
is valid for a specific interaction id and its status is
indicated by s.”
3.1 Trust Relation Attributes
The attributes of the trust relation τ are trustor γ,
trustee δ, context c, levels λ, time interval ι, expecta-
tion set ε, interaction identifier id, and status s. These
are explained below.
3.1.1 Trustors and Trustees
The first two attributes γ, δ of the trust relation τ rep-
resent the trustor and trustee respectively. These are
entities with unique identifiers.
3.1.2 Context
The scope of the trust relationship is narrowed to a
specific function called context. Without loss of gen-
erality, context c is portrayed as an action performed
on data. In this case, action could be producing, for-
warding, and consuming data. Data is classified based
on its type, which includes sensitive data, public data,
recommendation data, etc. Given that A is the set
of actions performed on data and DT the set of data
types, then context c = (A, D) with D ⊂ DT .
3.1.3 Trust Levels
Trust is subjective because a trustor’s requirements
are not met by trustees at the same degree or a
trustor’s expectations for trustees varies. There is a
number of ways to denote how much an entity is wor-
thy of trust. Trust values (Abdul-Rahman and Hailes,
1997), degrees (Abdul-Rahman and Hailes, 2000) and
levels (Grandison and Sloman, 2000) are all used by
the trustor to categorize trustees based on their per-
ceived trustworthiness.
Our model adopts the term trust level. Trust levels
are closely related to two important concepts: trust-
fulness of the trustor and trustworthiness of the trustee
(Buskens, 2002). Trustfulness is defined as the extent
to which the trustor is willing to take the risk of trust
being abused by the trustee. On the other hand, trust-
worthiness is the extent to which the trustee honors
trust, if trust is placed. The trustfulness of the trustor
varies and it depends on the trustor’s willingness to
trust. In our model, the trustfulness of the trustor is a
synonym of trusting attitude.
Trust levels λ is an ordered pair (λ
im
, λ
t
) with
λ
im
∈ Λ
im
, λ
t
∈ Λ
t
, and its coordinates represent trust-
ing attitude and trustworthiness extent respectively.
Λ
im
is the set of values for trusting attitude whereas
Λ
t
is the set of values for trustworthiness extent.
3.1.4 Time Interval
A trust relation consists of trust relationships that are
valid for a period of time. The temporal database
interpretation of time is chosen for modeling time.
In temporal databases, time domain T is consid-
ered to be an ordered sequence of points t
i
in some
application-dependent granularity (Elmasri and Na-
vathe, 2000). The granularity of time does not affect
the logic of the trust relation if it is consistent through-
out the model.
There are two types of intervals: expected inter-
val and actual interval. The expected interval ι=(t
s
,t
e
)
indicates the anchored time duration in which a trust
relationship is predicted to be valid. The actual inter-
val is the one that the trust relationship was observed
to be valid in the real world. The latter is not part
of the relation, but it’s recorded as experience upon
termination of trust relationship.
3.1.5 Expectations
An expectation is defined as a requirement and its
allowed values that a trustor has for a particular in-
teraction with a trustee. An expectation is a tuple
(π, o, ν
o
, ν
a
, ev) , where π is a trust requirement, o is a
standard relational operator, ν
o
is the observed or ac-
tual value for the requirement, ν
a
is the allowed value
for that requirement and ev represents the evaluation
criteria for the specific requirement. The observed
value ν
o
is the aggregated value of multiple observa-
tions (also called evidence) over time. ev contains the
aggregation algorithm that is used to derive the actual
value.
The first expectation attribute is the trust require-
ment π. Trust requirements are grouped in behavioral
SECRYPT 2008 - International Conference on Security and Cryptography
548
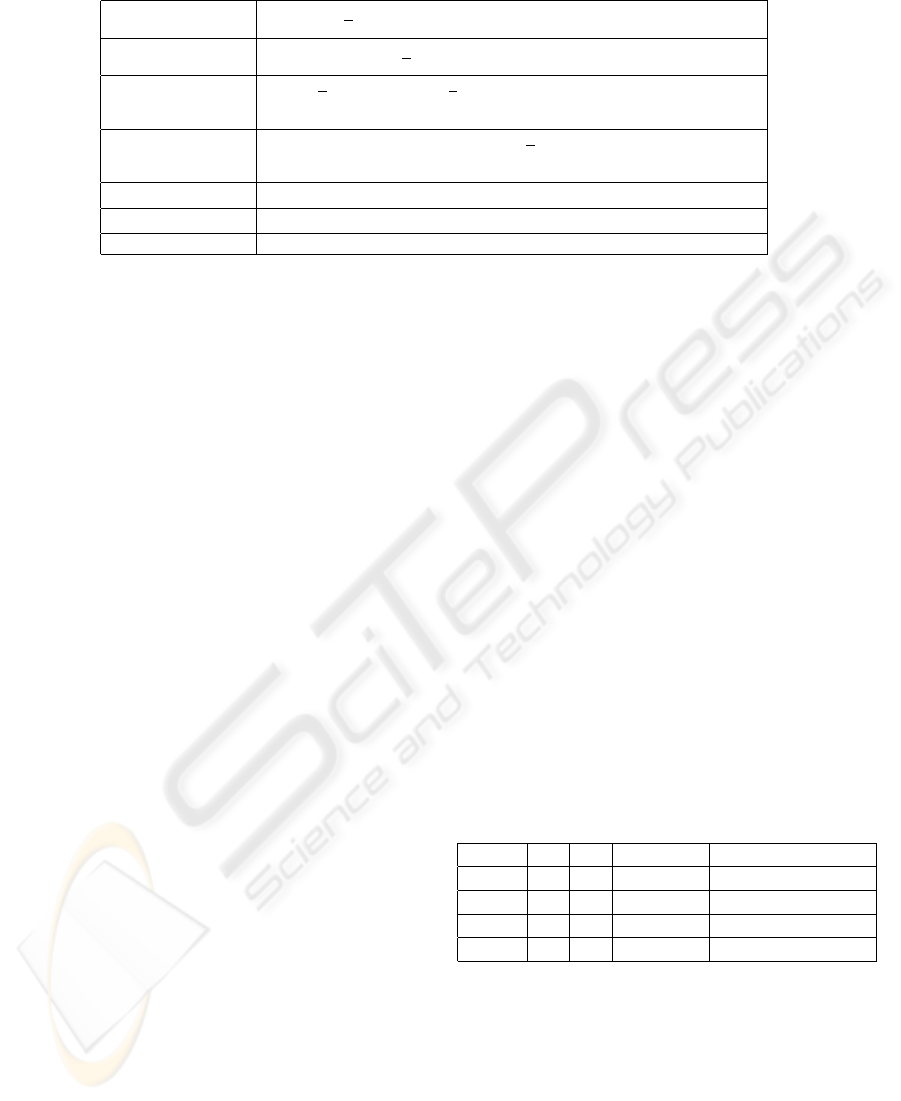
Table 1: Aggregation Algorithms for Single Evidence Type.
Average v
j
all
=
1
n
∑
n
i=1
(v
j
i
), where n is the number of external sources
Weighted Average v
j
all
=
1
n
∑
n
i=1
f (τ
i
, v
j
i
), where f is a function
Weighted Average v
j
all
=
u
x
∑
x
i=1
f (τ
i
, v
j
i
) +
v
z
∑
z
i=1
f (τ
i
, v
j
i
), where x + z = n, u + v = 1
Combination
Majority v
j
all
is the value that more than
n
2
external sources agree on
(allow for a δ deviation)
m-out-of-n v
j
all
is the value that at least m out of n external sources agree on
Plurality v
j
all
is the value that most external sources agree on
User-defined Any customized aggregation method such as median value, etc
(β), security (σ), and QoS (φ) categories. Trust re-
quirement π ∈ Π, with Π = Π
β
∪ Π
σ
∪ Π
φ
.
The second expectation attribute is the equality or
inequality operator o. Operator o takes values from
the set O that consists of the relational operators =,
<, 6, >, >, and 6=.
The third and fourth attributes are the observed
and allowed values respectively. Value ν ∈ V , with
set V consisting of values that are assigned to require-
ments. Set V is defined as ∪V
i
, with V
i
be the set of
values that requirement π
i
takes. Without loss of gen-
erality, assume that every V
i
is totally ordered by 6
and all operators o ∈ O are defined for all ν ∈ V .
Finally, the fifth attribute ev represents the eval-
uation parameters for the particular requirement.
At time t, a requirement can only have one ac-
tual value, which is the result of aggregating
many observed values. An element ev is a tu-
ple (covering,triggering, aggregation) that describes
the covering method, triggering rule and aggregation
scheme for π. The covering attribute provides the
conditions under which an expectation is considered
valid and the remaining two characterize the “when”
and “how” the observed value is updated.
Incoming evidence must be evaluated in the con-
text of existing trust relationships. When triggering
conditions are activated, the evidence is aggregated.
Aggregating evidence can be seen as a voting mecha-
nism where instances of evidence types are combined
by a voting scheme into a single output. Aggrega-
tion algorithms can be triggered either at predefined
intervals or when a number of instances arrive at the
evaluator. The aggregated result is an observed value
for a trust requirement. It is important to note that an
observed value is not necessarily related directly to a
single evidence type. A user could specify functions
that map multiple evidence types to trust requirement
values.
There is a spectrum of aggregation algorithms that
could target the aggregation of evidence from multi-
ple instances of a single evidence type and evidence
from different evidence types. The aggregation al-
gorithms that could be supported include average,
weighted average, majority, m-out-of-n, plurality, and
any user-defined aggregation. Consider v
j
all
to be the
aggregated observed value for entity j, v
j
i
to be evi-
dence value by external source i for entity j, and τ
i
to
be the trust relationship between the evaluating trustor
k and external entity i. The aggregation algorithms
that trustor k can use to derive a single observed value
for j are shown in Table 1.
The covering techniques mentioned in this paper
are strict and relaxed, where in the former case the
observed value satisfies the allowed value under oper-
ation o and in the latter case a deviation d is allowed.
The expectation semantics dictate that an expectation
is valid if and only if the relationship between ob-
served value ν
o
and allowed value ν
a
under operation
o and covering method covering is also valid. Other-
wise, a violation occurs. Table 2 illustrates examples
of valid expectations and violations.
Table 2: Valid Expectations and Violations.
Op. o ν
o
ν
a
Covering Valid or Violation
= 3 5 strict violation
= 5 3 d=2 valid
6 6 5 strict violation
6 6 5 d=4 valid
An expectation set ε describes the requirements
that a trustor has for a trustee. Expectation set ε is the
subset of the cartesian product Π × O ×V ×V × EV .
Each member of the expectation set is an expec-
tation as defined above. There is a unique tuple
(π, o, ν
o
, ν
a
, ev) ∈ ε that corresponds to any given π.
By itself an expectation set is not interesting un-
less operations are performed on its elements. How-
ever, prior to defining these operations we must
first define the primitive comparison relationships be-
FORMALIZING END-TO-END CONTEXT-AWARE TRUST RELATIONSHIPS IN COLLABORATIVE ACTIVITIES
549

tween its elements. The relationships between ex-
pectation tuples determine the relationships between
expectation sets. These binary relationships include
the standard equality (=) and less than or equal (6)
relationships as well as the redefinition of not equal
6=. In addition, a new relationship called relaxed
equal is defined. Based on the binary relationships,
expectation sets when compared fall in one of the
four categories: strictly-equal, relaxed-equal, cov-
ered/covering and unrelated (Dionysiou, 2006).
Starting with the relationships between expec-
tation tuples, the equality relationship is presented
first. Two expectation tuples are equal if their
respective trust properties π
1
, π
2
, observed values
ν
o
1
, ν
o
2
, allowed values ν
a
1
, ν
a
2
, and covering meth-
ods covering
1
, covering
2
are the same. The triggering
and aggregation methods do not need to be the same
since they don’t affect the semantics of the expecta-
tion tuples. Those attributes merely affect the when
and how the observed value changes.
Equal Expectations (=). Expectation
(π
1
, o
1
, ν
o
1
, ν
a
1
, ev
1
) is equal with expectation
(π
2
, o
2
, ν
o
2
, ν
a
2
, ev
2
) if and only if π
1
= π
2
∧ o
1
=
o
2
∧ ν
o
1
= ν
o
2
∧ ν
a
1
= ν
a
2
∧ covering
1
∈ ev
1
=
covering
2
∈ ev
2
.
The relaxed equal relationship is a new relation-
ship that relates two expectations that refer to the
same property mapped to different values.
Relaxed Equal Expectations (≈). An expectation
(π
1
, o
1
, ν
o
1
, ν
a
1
, ev
1
) is relaxed equal with another ex-
pectation (π
2
, o
2
, ν
o
2
, ν
a
2
, ev
2
) if and only if (π
1
=
π
2
∧ o
1
= o
2
∧ ν
o
1
6= ν
o
2
∧ ν
a
1
6= ν
a
2
∧ covering
1
=
covering
2
) or (π
1
= π
2
∧ o
1
= o
2
∧ ν
o
1
6= ν
o
2
∧ ν
a
1
=
ν
a
2
∧ covering
1
= covering
2
).
Two expectation sets are strictly equal if they
contain the same elements. Expectation sets
ε
1
= {(cooperation, =, 1, 1, ev), (reliability, >
, 0.98, 0.97, ev2)} and ε
2
= {(cooperation, =
, 1, 1, ev), (reliability, >, 0.98, 0.97, ev2)} are strictly
equal.
Strictly Equal Expectation Sets. Expectation set ε
1
is
strictly equal to expectation set ε
2
if and only if ε
1
is
an improper set of ε
2
, under the equality definition.
The relaxed equal comparison is a general-
ization of the strictly equal comparison between
two expectation sets. Consider expectation sets
ε
1
= {(cooperation, >, 3, 1, ev), (reliability, >
, 0.98, 0.97, ev2)} and ε
2
= {(cooperation, >
, 2, 1, ev), (reliability, >, 0.98, 0.97, ev2)}. These two
sets don’t have the same elements, but they both
contain values for the same properties: cooperation
and reliability. These two sets are called relaxed
equal.
Relaxed Equal Expectation Sets. Expectation set ε
1
is relaxed-equal to expectation set ε
2
if and only if for
all tuples i=(π
1
, o
1
, ν
o
1
, ν
a
1
, ev
1
) ∈ ε
1
there is tuple j
= (π
2
, o
2
, ν
o
2
, ν
a
2
, ev
2
) ∈ ε
2
such as |ε
1
| = |ε
2
| and
(i ≈ j or i = j).
In order to address the issue of trust composabil-
ity, one must provide answer to queries like “What
is the expectation set for a path that starts from X
and terminates at Y?” . Merging is an operation that
accomplishes that by applying a function f
π
on the
values of a property. The function f
π
essentially ag-
gregates the observed and allowed values into single
values respectively; average, maximum, minimum,
weighted average are all candidate f
π
.
Merging of Expectation Sets. Consider expectation
sets ε
1
and ε
2
. The merging of the two expectation
sets results in a new expectation set ε
merge
that is con-
structed as follows:
1. Initialize ε
merge
=
/
0
2. If ε
1
= ε
2
, then ε
merge
← ε
merge
∪ ε
1
.
3. if ε
1
≈ ε
2
, then ∀i:(π
1
, o
1
, ν
o
1
, ν
a
1
, ev
1
)
∈ ε
1
, j:(π
2
, o
2
, ν
o
2
, ν
a
2
, ev
2
) ∈ ε
2
such that i ≈ j and ε
merge
← ε
merge
∪
{((π
1
, o
1
, f
π
(ν
o1
, ν
o2
), f
π
(ν
a1
, ν
a2
), ev
1
) )}.
3.1.6 Interaction id
Another trust relation attribute is the interaction iden-
tifier id. There is a unique identifier for each activity,
the interaction id. There are at least two trust relation-
ships for any activity.
3.1.7 Status
The last attribute is the status of a trust relationship.
Status s ∈ S = {OK, WARNING, ALERT}.
3.2 Trust Relation Properties and
Operations
The next step in formalizing trust is the definition of
its properties. The standard properties of any n-ary
relation (reflexive, irreflexive, symmetric, antisym-
metric, transitive, and equivalence) do not hold due
to non-absolute characteristics of trust relationships.
Thus, new properties must be investigated.
One of the characteristics of trust relation τ is
its dynamic nature, meaning that τ(γ, δ, c, λ, ι, ε, id, s)
which is valid in time t
1
may become invalid in t
2
,
with t
2
> t
1
, and vice versa. Another characteristic of
trust is its composable nature, meaning that existing
trust relationships can be aggregated to derive an end-
to-end trust assessment for a particular activity at time
t. Thus, operations are categorized in two groups: the
SECRYPT 2008 - International Conference on Security and Cryptography
550

ones that affect and change the current state of the
trust relation and the ones that use the existing state
of the trust relation to make trust assessments.
3.2.1 Operations Changing Trust Relation State
Trust relation τ is affected by time, arrival of new ev-
idence, and violation of expectations, to just name a
few. There are other events that change the trust rela-
tion state such as the change of trusting attitude level,
but these are not described here.
Expiration of Valid Time. A trust relationship
(γ, δ, c, λ, ι, ε, id, s) does not hold in relation τ if its
valid interval time expires. Thus, a trust relationship
τ(γ, δ, c, λ, ι, ε, id, s) is not valid in τ if the current time
t > t
e
, t
e
∈ ι.
Arrival of New Evidence. Suppose that new evi-
dence is available for a particular trustee and context.
The new value will be applied to the appropriate trust
requirement according to the trustee evaluation infor-
mation for the trust requirement. Suppose that new
evidence arrives at trustor γ for trustee δ regarding
context c. The new evidence includes the trust re-
quirement π
r
and the recommended value ν
r
. All trust
relationships (γ, δ, c, λ
i
, ι
i
, ε
i
, id
i
, s
i
) are updated to re-
flect the application of the new evidence on ν.
Expectation Violation. Whenever new evidence
arrives, the observed value changes according to the
aggregation scheme for the specific requirement. An
update in the observed value may lead into expecta-
tion violation. In this case, the respective trust re-
lationship’s status is set to ALERT. The relationship
does not necessarily become false in τ; according to
policies it might be the case that a trustor wants to
monitor the relationship before terminating it. How-
ever, all other trust relationships that are associated
with the alerted relationship’s interaction identifier
have their status set to WARNING. In a case that
an expectation (π, o, ν
o
, ν
a
, ev) ∈ ε is not valid for
τ(γ, δ, c, λ, ι, ε, id, s) , the respective relationship’s sta-
tus s becomes ALERT and all tuples associated with
the same interaction identifier id have their status set
to WARNING. However, a relationship’s status is re-
stored whenever the violation gets corrected during
the monitoring interval. In this case, the ALERT
gets replaced by OK, and all WARNING are replaced
with OK. Note that if there are multiple violations for
a specific interaction, then WARNING(s) remain as
they are until all ALERT(s) become OK.
3.2.2 Operations using Trust Relation State
The current state of the trust relation can be used to
make nontrivial trust assessments for activity-specific
relationships with the same context and with different
contexts; the later gives the end-to-end trust assess-
ment for the particular activity.
Let’s consider first the aggregate trust assess-
ment for context c in interaction id. In particu-
lar, consider tuples (γ
1
, δ
1
, c
1
, λ
1
, ι
1
, ε
1
, id
1
, s
1
) and
(γ
1
, δ
2
, c
1
, λ
1
, ι
2
, ε
2
, id
1
, s
1
) in τ. Trustor γ
1
may syn-
thesize the two tuples to derive an aggregated trust
assessment for context c during interval ι
i
(the inter-
section of ι
1
and ι
2
) by applying expectation set oper-
ations on the expectation sets ε
1
and ε
2
to derive the
aggregated expectation set ε
i
. Expectation set ε
i
has
to be checked against the various trust level specifica-
tions in order to assign the trustworthiness level λ
i
for
the new tuple (γ
1
, δ
1,2
, c
i
, λ
i
, ι
i
, ε
i
, id
1
, s
1
) .
Next, consider the end-to-end trust assessment
for interaction id. Suppose there are aggregated
trust assessments for contexts c
1
and c
2
, which
are the only contexts belonging to interaction id
1
:
these are tuples (γ
1
, δ
1
, c
1
, λ
1
, ι
1
, ε
1
, id
1
, s
1
) and
(γ
1
, δ
2
, c
2
, λ
1
, ι
2
, ε
2
, id
1
, s
1
) . Trustor γ
1
may compose
the two tuples to derive an end-to-end trust assess-
ment for interaction id
1
during interval ι
i
(the inter-
section of ι
1
and ι
2
) by applying expectation set oper-
ations on the expectation sets ε
1
and ε
2
to derive the
aggregated expectation set ε
i
. Expectation set ε
i
has
to be checked against the various level specifications
in order to assign the trustworthiness level λ
i
for the
new tuple (γ
1
, δ
1,2
, c
1,2
, λ
i
, ι
i
, ε
i
, id
1
, s
1
) .
We will demonstrate the two operations above
with an illustrative example. Assume that Figure 3
is a graph for trust relation τ of the network depicted
in Figure 2. A node represents either a trustor or a
trustee. Nodes are connected by directed edges that
start at a trustor node and end at a trustee node. Each
edge carries the tuple that describes the relationships
between the two connecting nodes. An edge may
carry multiple tuples. Suppose that trustor C would
like to derive the end-to-end trust assessment regard-
ing the information flow for data d. Then, as ex-
plained in section 2, the following trust relationships
must be considered:
• relationship between P and C regarding P’s ability
to produce data d: τ(γ
C
, δ
P
, c
2
, λ
1
, ι
3
, ε
3
, id
1
, s
OK
)
• relationship between S
1
and C regard-
ing S
1
’s ability to forward data d:
τ(γ
C
, δ
S1
, c
1
, λ
1
, ι
1
, ε
1
, id
1
, s
OK
)
• relationship between S
2
and C regard-
ing S
2
’s ability to forward data d:
τ(γ
C
, δ
S2
, c
1
, λ
1
, ι
2
, ε
2
, id
1
, s
OK
)
FORMALIZING END-TO-END CONTEXT-AWARE TRUST RELATIONSHIPS IN COLLABORATIVE ACTIVITIES
551

PC
S
1
S
2
τ(C,S
1
,c
1
,λ
1
,ι
1
,ε
1
, id
1
, s
1
)
τ(C,S
2
,c
1
,λ
1
,ι
2
,ε
2
, id
1
, s
1
)
τ(C,P,c
2
,λ
1
,ι
3
,ε
3
, id
1
, s
1
)
c
1
= (forward,{sensitive,recommendation})
c
2
= (generate,{sensitive})
λ
1
= (normal, partial)
ι
1
= [1,10] , ι
2
= [1,15] , ι
3
= [1,8]
s
1
= OK
ε
1
= {(authentication, =, certificate,certificate, ev
1
), (reliability, >=, 0.97, 0.95, ev
2
)}
ε
2
= {(authentication, =, certificate,certificate, ev
1
), (reliability, >=, 0.95, 0.95, ev
2
)}
ε
3
= {(authentication, =, certificate,certificate, ev
1
), (reliability, >=, 0.90, 0.80, ev
2
)}
Figure 3: Trust Relation Graph.
First, the trust aggregation for the same context c
1
will take place for trustees S1 and S2. The result will
be τ(γ
C
, δ
S1,S2
, c
1
, λ
1
, ι
k
, ε
k
, id
1
, s
OK
) , with i
k
=(1,10)
and ε
k
={(authentication, =, certificate,certificate,
ev1), (reliability, >, average(0.95,0.97), aver-
age(0.95,0.95), ev2)}. Then, the end-to-end trust
assessment will take place between the new trust
relationship τ(γ
C
, δ
S1,S2
, c
1
, λ
1
, ι
k
, ε
k
, id
1
, s
OK
) and
τ(γ
C
, δ
P
, c
2
, λ
1
, ι
3
, ε
3
, id
1
, s
OK
) . In this case,
τ(γ
C
, δ
P,S1,S2
, c
1,2
, λ
1
, ι
m
, ε
m
, id
1
, s
OK
) , with i
m
=(1,8)
and ε
m
={(authentication, =, certificate,certificate,
ev1), (reliability, >, average(0.90,0.96), aver-
age(0.80,0.95), ev2)}.
4 RELATED WORK
In recent years, researchers have investigated various
definitions of trust, modeling trust and its manage-
ment (Vacca, 2004; Winslett et al., 2002; Herzberg
et al., 2000; Group, 2004; Grandison, 2001; Blaze
et al., 1996; Chu et al., 1997; Blaze et al., 1998; Zim-
mermann, 1995; Marsh, 1994; Josang, 1997; Josang
et al., 2006; Abdul-Rahman and Hailes, 2000). Start-
ing with one of the early and widely known trust mod-
els, the PGP trust model (Zimmermann, 1995) creates
an informal web of trust which is used for authentica-
tion purposes. A recent survey of contemporary trust
management systems is compiled by Grandison and
Sloman (Grandison and Sloman, 2000), who point out
the limitations of those solutions as they mostly ad-
dress access control issues rather than the more gen-
eral analysis of trust. KeyNote (Blaze et al., 1998)
and PolicyMaker (Blaze et al., 1996), for instance, are
primarily concerned with security issues (authentica-
tion and access control). A solution to more general
trust relationships is proposed by SULTAN (Grandi-
son and Sloman, 2000), a trust management model
that uses a logic-oriented language to specify trust. In
addition to the practical approaches to trust, there are
formal trust models that describe more general trust
factors. The Marsh (Marsh, 1994) logic-based frame-
work uses formal representation to capture the seman-
tics of the social paradigms of trust whereas Josang’s
subjective logic (Josang, 1997; Josang et al., 2006) is
another formal model that uses beliefs as the basis for
trust.
Unlike other approaches, our model derives end-
to-end trust assessments without using transitive in-
direct trust explicitly in the derivations. The seman-
tics of indirect trust are captured in the form of fine-
grained recommendations that are considered to be an
evidence type; the weight of this evidence on the over-
all trust assessment, like any other evidence type, is
based on the trustor-recommender existing trust rela-
tionship. In this case, the trust relationship context
could be ”recommending” whereas the activity iden-
tifier could be the interaction identifier of the partic-
ular recommendation information flow. In addition,
our model extends the traditional concept of trust con-
ditions into more expressive expectations, which in-
clude not only expected values for particular prop-
erties but also covering, aggregating, and triggering
mechanisms that manipulate the observed value.
5 CONCLUSIONS
This paper presents a new trust paradigm and asso-
ciated formalisms, devised to support dynamic and
composable trust suitable for collaborative activities.
Dynamic and composable trust is essential for topolo-
gies where interactions are dynamic and they almost
always involve the collaboration of multiple entities
to disseminate data from its source to its destination.
In this setting, dynamic trust enables the specifica-
tion and management of trust relationships to change
over the operational lifecycle of the activity as rele-
vant conditions that affect trust change. Composable
trust allows end-to-end trust assessment for the entire
activity, where multiple trust relationships are exam-
ined in order to derive trust for the activity. We also
presented an intuitive and practical way to manage
end-to-end trust assessment for a particular activity,
including explicit consideration of expectations and
their violations.
REFERENCES
Abdul-Rahman, A. and Hailes, S. (1997). A distributed
trust model. In Proceedings of the ACM New Secu-
rity Paradigms Workshop, pages 48–60.
Abdul-Rahman, A. and Hailes, S. (2000). Supporting trust
in virtual communities. In Proceedings of the 33th
Hawaii International Conference on System Sciences
(HICSS), pages 1769–1777, Maui, Hawaii.
SECRYPT 2008 - International Conference on Security and Cryptography
552

Blaze, M., Feigenbaum, J., and Keromytis, A. D. (1998).
Keynote: Trust management for public key infrastruc-
tures. In Proceedings of the 6th International Work-
shop on Security Protocols, Cambridge, UK.
Blaze, M., Feigenbaum, J., and Lacy, J. (1996). Decentral-
ized trust management. In SP ’96: Proceedings of the
1996 IEEE Symposium on Security and Privacy, page
164, Washington, DC, USA. IEEE Computer Society.
Buskens, V. W. (2002). Social Networks and Trust, vol-
ume 30 of Theory and Decision Library. Series C,
Game Theory, Mathematical Programming, and Op-
erations Research. Boston, London Kluwer Academic
Publishers.
Chu, Y.-H., Feigenbaum, J., LaMacchia, B., Resnick, P.,
and Strauss, M. (1997). Referee: trust management
for web applications. Comput. Netw. ISDN Syst., 29(8-
13):953–964.
DHS (2006). Protected critical infrastructure information
(pcii) program. www.dhs.gov.
Dionysiou, I. (2006). Dynamic and Composable Trust
for Indirect Interactions, Ph.D. Dissertation. De-
partment of Electrical Engineering and Computer Sci-
ence, Washington State University.
Dionysiou, I., Frincke, D., Bakken, D., and Hauser, C.
(2007). An approach to trust management chal-
lenges for critical infrastructures. In Proceedings of
the 2nd International Workshop on Critical Informa-
tion Infrastructures Security (CRITIS07), to appear in
Lecture Notes in Computer Science Series, Springer
Berlin, 2007, Malaga, Spain.
Elmasri, R. and Navathe, S. (2000). Fundamentals of
Database Systems. Addison-Wesley Longman, Inc.
Force, U. C. P. S. O. T. (2004). Final report
on the August 14, 2003 Blackout in the United
States and Canada: Causes and Recommendations.
https://reports.energy.gov/BlackoutFinal-Web.pdf.
Grandison, T. (2001). Trust specification and analysis
for internet applications. Technical report, Ph.D.
Thesis, Imperial College of Science Technology and
Medicine, Department of Computing, London.
Grandison, T. and Sloman, M. (2000). A survey of trust in
internet applications. IEEE Communications Surveys
and Tutorials, 3(4):2–16.
Group, T. C. (2004). TCG Specification Architecture
Overview. TCG.
Herzberg, A., Mass, Y., Michaeli, J., Ravid, Y., and Naor,
D. (2000). Access control meets public key infras-
tructure, or: Assigning roles to strangers. In SP ’00:
Proceedings of the 2000 IEEE Symposium on Security
and Privacy, page 2, Washington, DC, USA. IEEE
Computer Society.
Josang, A. (1997). Prospectives of modeling trust in in-
formation security. In Proceedings of the 2nd Aus-
tralasian Conference on Information Security and Pri-
vacy, Sydney, Australia.
Josang, A., Gray, E., and Kinateder, M. (2006). Simplifi-
cation and analysis of transitive trust networks. Web
Intelligence and Agent Systems, 4(2):139 – 161.
Marsh, S. (1994). Formalizing Trust as a Computational
Concept. Department of Computer Science, Univer-
sity of Sterling.
Presti, S. L., Cusack, M., Booth, C., Allsopp, D., Kirton,
M., Exon, N., Beautement, P., Butler, M., Leuschel,
M., and Turner, P. (2003). Trust issues in pervasive
environments, deliverable wp2-01. Technical report,
University of Southampton and QinetiQ.
Vacca, J. (2004). Public Key Infrastructure: Building
Trusted Applications and Web Services. AUERBACH.
Winslett, M., Yu, T., Seamons, K., Hess, A., Jacobson, J.,
Jarvis, R., Smith, B., and Yu, L. (2002). The trust-
builder architecture for trust negotiation. IEEE Inter-
net Computing, 6(6):30 – 37.
Zimmermann, P. R. (1995). The official PGP User’s Guide.
MIT Press.
FORMALIZING END-TO-END CONTEXT-AWARE TRUST RELATIONSHIPS IN COLLABORATIVE ACTIVITIES
553
