
AN INVESTIGATION INTO THE REQUIREMENTS
for an e-Learning System
Yaen Y. Sofer, Steve B. McIntosh
School of Computer Science, Cardiff University, Queen's Buildings,
Newport Road, Cardiff, UK
Keywords: Learning environment, Distance learning, e-Learning, Web-based Technology, SSM, CPTM, Requirements,
Activities, Persona, Viewpoints, Business model.
Abstract: The learning environment where students of the same age group learn together instructed by a teacher, was
developed over the years and is known today as the traditional classroom. This traditional classroom may be
changed by using the latest Web-based technology to replace and/or support the learning process. These
new learning environments are accessible using the Internet as the main communication medium and by
other remote means such as CD-ROM, and video. Many aspects of the current use of these new
technologies reflect an approach to teaching and learning reminiscent of the “programmed learning” training
material of the 1970s. This paper uses Soft Systems Methodology (SSM) to construct a Consensus Primary
Task Model (CPTM) to analyse the requirements for a distance or e-learning system. In conducting the
analysis, we investigate the alternative methods proposed for the construction of a CPTM.
1 INTRODUCTION
Since the early days of education, people have
searched for appropriate ways to spread and share
their knowledge with their peers. In the 18
th
and 19
th
centuries, Jewish pupils used to study in small
basements instructed by the community Rabbi. This
study environment used to be called the ‘Heder’
(‘The Room’). The pupils used to study the Bible
and gained reading and writing skills.
According to Dr. Katz, Director of the School of
Education at Bar-Ilan University, The study of the
evolution of communication technology has
considerably influenced the development of distance
learning. Katz (Katz, 2001) categorises the stages of
the development of distance learning as three
generations: First generation: utilising traditional
printed material and communications via mail and
telephone. Second generation: audio recordings,
radio and television broadcasts. Both first and
second generation Distance Learning delivery
systems were designed primarily to produce and
distribute learning materials as efficiently as the
technology of the day permitted without any
attention being focused on the lack of interactive
communication between students and teachers.
Third generation: includes interactive video,
email, and world wide web (www) technologies,
learning activities via these Distance Learning
systems has been redefined to include teacher-
student interaction. Interactive video-conferencing
or interaction by way of on-line Internet-based
instructional and learning packages offer one-to-
many tuition in which teachers and students are able
to communicate synchronously thereby solving
instructional and learning problems in real time.
This may transport the student to a new cognitive
environment which motivates and stimulates the
student (Katz, 1998, 2000, 2001).
This evolution of the learning environment and
methods has arisen in response to technology. We
are unconvinced that the development has taken
place in a systematic way, through an analysis of the
requirements of the basis of the needs of various
stakeholders in the learning system. In general,
requirements elicitation is a complex and difficult
task, and there is evidence (see for example the
British Computer Society survey “IT Projects: Sink
or Swim”, January 2000) that failure to get the
requirements right is clearly associated with the
failure of IS/IT projects. In this context, failure may
include lack of user acceptance.
233
Y. Sofer Y. and B. McIntosh S. (2004).
AN INVESTIGATION INTO THE REQUIREMENTS - for an e-Learning System.
In Proceedings of the Sixth International Conference on Enterprise Information Systems, pages 233-237
DOI: 10.5220/0002604202330237
Copyright
c
SciTePress

A number of stakeholders, with different
viewpoints, can be identified in considering learning
systems. Their views may be surmised, and having
been identified will impact the perception of purpose
of the system to be designed. For example:
The “learner” has some motivation to learn, but
may be assumed to wish to do so at minimum cost in
time and effort.
The instructor may seek to transfer knowledge in
the most effective and efficient way.
The employer may wish to reduce costs by
delivering learning remotely, avoiding travel costs
and loss of production.
The infrastructure owner may wish to minimise
communications overhead.
The material owner may wish to protect
intellectual property rights.
Because the various stakeholders have different
views of the purpose of the system, requirements
elicitation implies the need to consider an
appropriate methodology. A methodology according
to Dr. Brian Wilson is a description of how to think
about the process of analysis prior to doing it. The
methodology can be described as a set of guidelines
which simulate the intellectual process of analysis
(Wilson, 2001).
The question of which methodology to choose is
itself problematic. It must reflect characteristics of
the problem, scope and compass of the methodology
and the skills and knowledge of the analyst, among
other considerations A valid first question to ask is,
is the situation considered as a ‘soft’ or a ‘hard’
problem? Wilson indicates that the design of a piece
of a software to meet a given specification is a
‘hard’ problem whereas the specification of
information requirements to meet business needs is a
‘soft’ problem particularly if the needs as specified
by potential users. He states that the assumption
upon which Soft Systems Methodology (SSM) is
based is that:
Whatever the nature of the organisations,
assume that the individuals within it are pursuing
purposeful activity.
Individuals may well be pursuing different
purposes, but they are not acting randomly. This
means that providing we can identify their purposes
and accommodate them, we should be able to
alleviate the problem of competing viewpoints.
2 THE ARGUMENT
According to Dr. Owston (Owston, 2000) the growth
of Web-based courses over the last several years has
been extraordinary. Despite the widespread adoption
of this new technology by educational institutions, it
seems that we know very little about Web-supported
pedagogy. Owston (Owston, 1997) cautions that
before embracing the innovation of this new
technology we need to be able to answer three
questions:
(1) Does the Web increase access to learning?
(2) Can the Web promote improved learning?
(3) Can increased access and improved learning
be attained without increasing the costs of
education?
Owston indicates that unless we have evidence
of satisfying these criteria we may be doomed to
promoting just another educational bandwagon
(Owston, 2000).
On the question of access, Owston suggests that
each of us may have a different interpretation of
what ‘access to learning’ means, although most will
agree that it means making education more
attainable for more people. Owston suggested that
this implies an increase in the availability of
educational opportunities for those unable to attend
formal classes (i.e. school, university, corporate
training etc) because of cultural, economic, or social
barriers. According to Owston, Web-based
educational methods can break down these barriers.
Owston suggests, however, that although the
Web breaks down the long-standing physical and
temporal barriers of access to education, it can create
new kinds of barriers for students. These include
shortages of computer hardware, malfunctions of
hardware, skills difficulties and bandwidth
problems.
Owston suggests that there are promising
indications that the Web is a viable means to
increase access to education. Evidence on how it can
promote improved learning is not as readily
available. In fact, there is debate in the instructional
design literature about whether there are any unique
attributes of media that can promote improved
learning (Clark, 1983, 1994; Kozma, 1991, 1994).
Owston suggests that the issue becomes further
complicated when the Web is used as a ‘tool for
learning’, as opposed to a medium for delivering
pre-determined content, which requires the users to
gain the skills needed to use the tool; this may cause
new barriers as mentioned above.
With regard to the cost of education, Owston
suggests that there are three main areas of cost for a
Web based course:
(1) Hardware and software - includes the Internet
connection itself and all necessary computer
hardware and Web related software required for
delivering as a course.
(2) Course development - includes planning the
course content and suitable pedagogy for developing
the Web resources associated with the course.
ICEIS 2004 - HUMAN-COMPUTER INTERACTION
234
(3) On-going course support – includes posting
new materials and removing dated materials,
verifying the validity of the links, improving the
layout and design, adding functionality and uses of
new technology.
Based on these assumptions, we can define a
purpose for a Web-based learning environment,
offering efficient, effective learning and reducing the
cost of education. Using an appropriate
methodology, we can derive system requirements.
3 SELECTING SSM AS THE
METHODOLOGY
The terms ‘hard’ and ‘soft’ are used frequently in
explanations of the Soft Systems approach, but first
we need to make clear the distinction between the
two. The terms are essentially comparative ones and
are used to distinguish between methods of
examination that address clearly defined problems
(techniques) and others that are used when the
problem is not clear at the outset. Here a preliminary
investigation is required to identify and select the
problem to be solved. The latter type of examination
applies to situations that are regarded as
unstructured or soft, inevitably involving people
working as individuals or groups towards some
organisational or other goal (Patching, 1990). This is
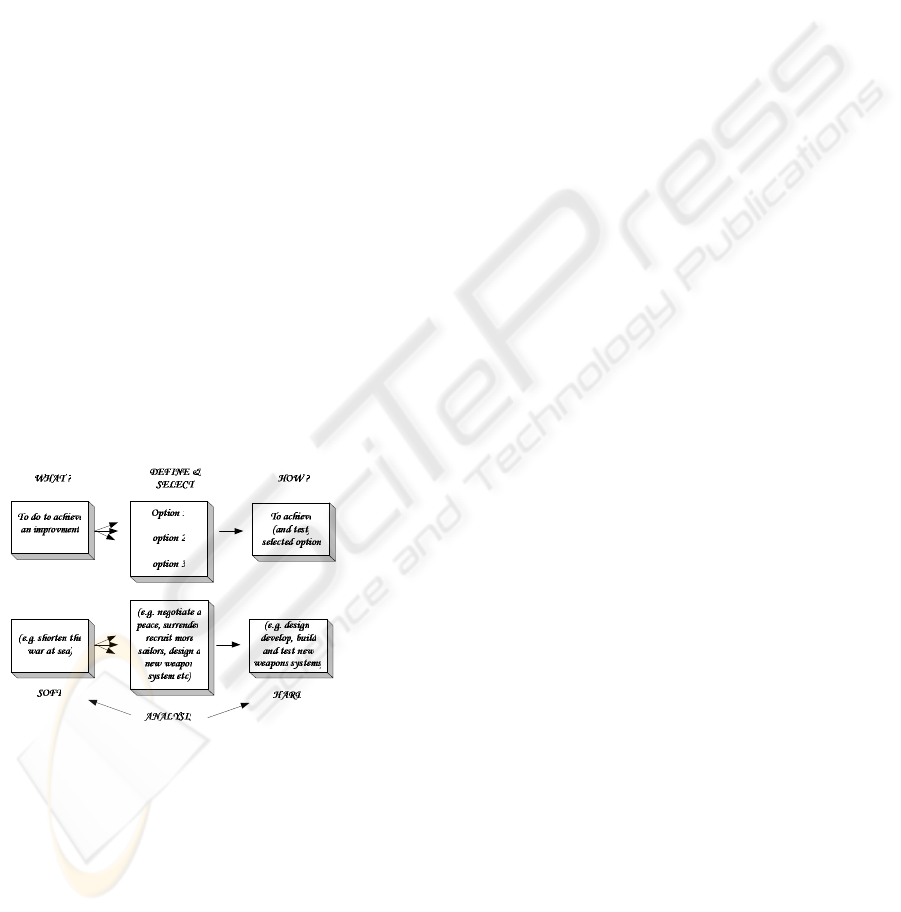
illustrated in Figure 1.
Figure 1: The Soft/Hard Division (Checkland and Scholes,
1999)
Checkland (Checkland, 1999) describes the use
of SSM in relation to ‘problem-solving’. He argues
that ‘Real-world problems’ are more of a case of
‘perceptions of problems’, this means that any
problem can be perceived differently by different
individuals or groups. Furthermore, Checkland states
that: “a fixed element in every problem situation will
be the existence of the role of ‘problem owner’,
occupied by those who perceive the problem. A
second fixed element will be the role, of the would-
be problem solver, the occupants of which wish to
tackle the perceived problem(s).”
SSM is concerned with defining what problem(s)
needs to be solved, clarifying the problems that exist
as a prerequisite for defining the options for
improvement. These raise the questions that the
designed system should give an answer to.
4 ROOT DEFINITION
According to both Checkland and Wilson, the Root
Definition (RD) is a way of trying to capture the
sense (root) of the purpose to be served. Like
differential equations, RDs do not exist in reality but
represent a precise framing of the system’s purpose,
achieved with the participation of available
stakeholders. The equivalent in real-world
terminology might be business objectives, mission
statement, specifications etc.
The next stage is to define the area of concern
more precisely (i.e. to synthesise the ‘Root
Definition’ (Checkland, 1999)). That will lead us
towards a well defined statement about the area of
concern, its activities and components. This may
represent a minimum that can be agreed in terms of
the domain of the real activity. It will offer people
who have an interest in the system the opportunity to
see what they are agreeing on and what has been left
out. As suggested by Checkland, the Root Definition
used as a statement of purpose in SSM can be
validated in terms of the mnemonic “CATWOE”
(Checkland and Scholes, 1999). This is illustrated
below.
According to the assumptions identified earlier,
we can define a Root Definition representing one
view of a learning system:
“A client owned system to provide appropriate
training to trainees by using the Internet as the main
communications medium and learning environment,
to provide an effective and efficient training solution
to allow trainees to take a course anywhere at any
time in order to reduce the training costs, while
maintaining the privacy of the system and complying
with training policy and directives, and while
learning from the operation of the total system”.
Customer: Not stated (payer of training costs)
Actor: Trainees
Transformation: Untrained trainees Æ
appropriately trained trainees
Weltanschauung: Using the Internet as the main
communication medium to deliver effective and
efficient training will reduce the training costs
AN INVESTIGATION INTO THE REQUIREMENTS FOR AN E-LEARNING SYSTEM
235

Owner: Client
Environment: Internet; training policy and
procedures
Using this RD allows us to develop a model of
the activities that the system must logically do, if it
is to be the system described in the RD. The words
in the RD allow us to make an initial assessment of
the likely subsystems in the overall model, with a
view to facilitating the development of a full model
at a relevant level of detail. The following candidate
subsystems:
• Provide effective and efficient training
• Assess training (needed to assure effectiveness)
• Comply with the client’s training policy and
procedures
• Assess the cost of training (necessary in order to
reduce costs)
• Maintain privacy
• Maintain knowledge base
• Monitor and control the system’s performance
(required by systems theory)
5 GUIDANCE AND METHODS OF
CONSTRUCTING THE
SYSTEM’S CPTM
The Consensus Primary Task Model (CPTM)
reflects an accommodation of stakeholders’
viewpoints. Each viewpoint may give rise to
different ideas on the transformation carried out by
the system, and different “Weltanschauungen”
1
, or
beliefs that underlay the purpose of the system.
The four methods for the construction of the
CPTM are:
A. mission-statement: this is the most defensible
method since the starting point is a ‘definition of
purpose’ arrived at by personnel in the situation
itself. The drawback of this method is that it uses
only one RD. As we saw from our root definition
earlier, even this suggests seven subsystems models
to consider. Using this method for construction will
not result in a model offering sufficient detail, which
will lead us to a CPTM model of limited utility.
B. W-decomposition: this is the most difficult
method to be used since the combination of the
resultant W-dependent models has to be based upon
a well-specified non-contentious RD and model.
1
Weltanschauung – German word, described by
Checkland and Wilson as world-view or viewpoints of
the system.
C. Wider-system Extraction: this method is
relatively easy to use once a wider-system model has
been derived. In our case we offer an
economic/effective online training system delivered
remotely using the Internet Technology. Our main
aim is to reduce the training costs on the one hand
and on the other hand to offer an efficient and
effective training process. To use the Wider-system
Extraction method of construction we should
examine the system Ws. In our case these are the
other methods of training (i.e. learning from books
and etc.); as this is not our main purpose we will not
use this method.
D. Enterprise Model Assembly: this is the
method most widely used by Dr Wilson in his
consulting and has proved the most acceptable from
the client ‘buy-in’ point of view. Of course, the
client must have some initial appreciation of the
status and purpose of the models being generated so
that acceptance can be pursued. The method, apart
from being based upon a very simple generic model
of any enterprise, is an appropriate method, given
widely differing Ws. With a little practice, it is a
relatively easy method, but relies on the ability to
construct a logically defensible conceptual model
from a set of RDs (Wilson, 2001).
Wilson argues that in a model of an enterprise
there will be a set of activities which represents its
core purpose, T–Core Transformation. There will be
other activities which facilitate, or support, this
process-S–Support. Since the enterprise is bound by
the limitations of its environment
2
, other activities
must exist which link its activities to the
environment -L–Linking, providing opportunities to
use the Internet Technology and other remote
methods. Finally in a managed enterprise there will
activities of planning, monitoring and control to
enable it to survive in a changing environment –
P,M,C–Planning, Monitoring and Controlling (in
this case, making sure that the online training
solution is effective and efficient) (Wilson, 2001).
6 CONCLUSIONS
The main purpose of modelling a system using this
approach is to derive as wide a range as possible of
the system’s functional and non-functional
2
In a “Human Activity System (HAS)”, the assignment of
a boundary is a subjective matter. Wherever the
boundary is considered to be, an “open” system
exchanges information with its environment.
ICEIS 2004 - HUMAN-COMPUTER INTERACTION
236

requirements, reflecting the differing views of
relevant stakeholders.
The list of activities and their logical
relationships derived from the system’s CPTM allow
us to investigate the system’s functional and non-
functional requirements. Choosing the appropriate
way of constructing the CPTM has an impact on the
utility of the resulting model, because of the
different assumptions underlying the approach.
Analysing the activities represented in the CPTM,
will give us the basis of the list of functions that the
system will be required to support, and should meet
the expectations of the stakeholders considered in
the analysis.
7 FURTHER WORK
In this research paper we have used Dr. Wilson’s
Enterprise Model in order to construct the system’s
CPTM. A number of unfinished questions were
raised during that process and require further
investigation and work. While the CPTM addresses
“what” the system has to achieve, it remains an open
question “how” to carry out each activity. This
question raises concerns about the non-functional
requirements, which are to some extent ignored in
the approach we have used.
One of our main concerns was the importance of
the system’s End-user. For consideration is what the
End-user seeks in the system. One of the proposed
solutions can be the use Cooper’s idea of the
Persona (Cooper, 1999) to describe the system’s
user. The Persona is an elastic imaginary user that
has identity (i.e. name) and will be addressed by
name (i.e. David) and not as ‘User’. As David is
determined by his set of characteristics we will be
able to know what David seeks in the system and
build a solution dedicated to David and his
colleagues. This will be approached by building a
Business Model that will indicate:
The need for the proposed solution (market)
The market sector for which the solution will be
aimed at (David and his colleagues).
The second question relates to information
analysis. The CPTM provides a list of the necessary
system activities, which we regard as functional
requirements. Analysing those requirements will
give us a list of Software based Functions that the
system needs to support, which will lead to ‘Data
Requirements’ which can be divided into:
Performance data (i.e. how do we know how
well we are doing each activity)
Operational data (i.e. what information do we
need in order to carry out the activity)
In terms of the development of an on-line
learning system, we believe that our approach will
lead us to a defensible set of functional
requirements. We propose to carry out the necessary
further analysis and implement the design arrived at.
With respect to our consideration of the candidate
approaches to the development of a CPTM, we need
to justify our confidence in the enterprise assembly
approach by constructing the CPTM using
alternatives, and determining whether there is any
substantive difference in the resulting models.
REFERENCES
Checkland, P., 1999, Systems Thinking, Systems Practice,
Includes 30-year retrospective, John Wiley and Sons,
Chichester, A5-A57,4-11,16,18,78,94,164,225-
227,314,199, 203.
Checkland, P., Scholes, J., 1999, Soft systems methodology
in action, John Wiley and Sons, Chichester 35,163.
Clark, R. E., 1983. Reconsidering research on learning
from media, Review of Educational Research, 53(4),
445-459.
Clark, R. E., 1994, Media will never influence learning,
Educational Technology Research and Development,
42(2) ,21-29.
Cooper, A., 1999, The inmates are running the Asylum,
why High-Tech Products Drive us Crazy and How to
Restore the Sanity, SAMS, 121-152.
Katz, Y. J., Yablon, Y. B., & Sagee, R., 2001, In:
Sponberg,H.,Lustigova, Z., & Zelenda, S. (Eds.),
Charles University, Prauge. 114-117.
Katz., Y. J., 2000, The comparative suitability of three
ICT distance learning methodologies for college level,
Educational Media International, 37 (1), 25-30.
Katz., Y. J., 1998, The relationship between distance
learning methods and satisfaction and achievement of
college students, In G. Davies (Ed.) Teleteaching '98:
distance learning, training and education, Austrian
Computer Society (OCG) and IFIP, 569-578.
Kozma, R. B., 1991. Learning with media, Review of
Educational Research, 61(2), 179-212.
Kozma, R. B., 1994. Will media influence learning?
Reframing the debate, Educational Technology
Research and Development, 42(2), 7-19.
Owston, R. D., 1997. The World Wide Web: A technology
to enhance teaching and learning?, Educational
Researcher, 26(2), 27-33.
Owston, R. D., 2000. Evaluating Web-based learning
environments: Strategies and insight,
CyberPsychology and Behavior, 3(1), 79-87.
Patching, D., 1990. Practical soft systems analysis,
Pitman, London, 40-53.
Wilson, B., 1990, Systems: Concepts, Methodologies and
Applications, John Wiley and Sons, Chichester.
Wilson, B., 2001. Soft System Methodology: Conceptual
Model Building and its Contribution, John Wiley and
Sons, Chichester, 73-75, 111-122, 133.
AN INVESTIGATION INTO THE REQUIREMENTS FOR AN E-LEARNING SYSTEM
237
