
An Agent-based Simulation of Extremist Network Formation through
Radical Behavior Diffusion
Carlos Sureda Gutierrez, Benoit Gaudout and Frederic Amblard
University of Toulouse, 2 Rue du Doyen-Gabriel-Marty, 31042 Toulouse, France
Keywords: Network Formation, Cultural Transfer, Social Simulation, Radicalization, Terrorism, Agents.
Abstract: Understanding how terrorist networks are created and how individuals turn into extremism and then into
terrorism is a current subject of interest and a cross-domain research problem since it involves scholars from
political sciences, sociology, physics and computer scientists among others. In this paper, an agent-based
approach is used to simulate the process of radicalization and creation of a terrorist network, and the link
between both processes. Each citizen has several attributes allowing the model to take into account
heterogeneous profiles of individual. Furthermore, we model the social transfer that takes place during the
interaction of individuals in order to understand how cultural ideas are transmitted. This paper also provides
a non-exhaustive but detailed survey of the state of the art on the agent-based terrorist networks modelling.
1 INTRODUCTION
We have seen in the last years an increase of news
related to terrorism issues, and it is nowadays
considered as one of the main global issues. This is
the case of France in particular, where the fight
against the terrorism is the second main
preoccupation of the population (Lévy, et al., 2016),
specially after the terrorist attacks suffered recently.
Nevertheless, extremism principles and its
corresponding practice implementation – terrorism –
have existed long before in another form and with
others goals. For example, in the late 20
th
century
some regional terrorist groups as Euskadi Ta
Askatasuna (ETA) in Spain or Irish Republican
Army (IRA) in Ireland had the main attention of
regional media.
Terrorist Networks (TN) works can be studied
according to several points of views, methodologies
and goals, doing its classification very complex, and
could even lead to a publication on this subject. A
first look can be taken by type of approach:
quantitative vs. qualitative, even if some authors
support a combined approach (Crossley, 2010).
Quantitative studies try to find a model that explains
the system withouth taking into account the
purposeful action of actors. On another side, the
qualitative approach focuses on the context in which
the relationships are created within the network and
the different types of links. Qualitative studes
(Taylor, 2010) try to explain how the particular
situation of actors at every moment drives the
structure of networks (Hidalgo, 2016). The focus can
also be made on the diffusion of behaviors within a
network, as (Deffuant, et al., 2002) (Holme and
Newman, 2006). Likewise, there are some
contributions on terrorist behavior modelling
(Taylor, 2010).
Most of the work done on TN takes the network
as a macro macro object where the structure cannot
emerge from heterogeneous egos, hence the utility
of an agent-based approach. Agent-based simulation
models make possible to analyse the macroscopic
effects of the heterogeneous agents’ interactions.
There are some papers in the literature that deal with
TN using an agent-based simulation approach.
Among them, different topics that can be analysed:
radicalization (MacKerrow, 2003) (North, et al.,
2004), recruitment (Berry, et al., 2004) (Li, et al.,
2015), operational tasks and roles (O'Neil, 2012) (Li,
et al., 2015), knowledge acquisition (Moon and
Carley, 2007), counter-terrorism (Keller, et al.,
2010) (Ilachinski, 2012).
Nevertheless, none of papers described above
focuses on the simulation of TN formation process
as a subject of study, combining at the same time the
diffusion of radicalism, heterogeneous behaviours
and micro-macro mechanisms modifying the form of
the network. The model presented in this paper deals
236
Sureda C., Gaudou B. and Amblard F.
An Agent-based Simulation of Extremist Network Formation through Radical Behavior Diffusion.
DOI: 10.5220/0006198602360243
In Proceedings of the 9th International Conference on Agents and Artificial Intelligence (ICAART 2017), pages 236-243
ISBN: 978-989-758-219-6
Copyright
c
2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

with these issues. Moreover, cultural transfers and
meeting mechanisms are introduced.
This paper is organized as follows: in section 2
we discuss in detail about agent-based simulation
approaches and propose a set of key aspects when
modelling TN; in section 3 our model is presented
and compared to other papers through these key
aspects; then in section 4 show some results. Finally,
section 5 concludes the paper.
2 AGENT-BASED SIMULATIONS
OF TERRORIST NETWORKS
Since the complexity and variety of agent-based
models of TN, we propose in the next paragraph a
detail of central questions and common aspects that
are studied in the state of the art and discuss about
them. The papers analysed here have been selected
in order to match all the specifications of our
research: and agent-based simulation, the notion of
social network and modelling of terrorism.
Each paper focuses more often in a central
question that represents the main idea (ex. Counter-
terrorism) responding at the same time to some other
aspects that can often be common to other papers
(ex. How are the links created?). These aspects have
been chosen in order to fit with the actual interest in
this paper, that is the network formation.
Thus, the following main questions and common
aspects have been identified.
2.1 Main Questions
2.1.1 Counter Terrorism
One of the most important questions addressed in
TN studies is the development, analyse and
simulation of counter-terrorism strategies.
(Raczynski, 2004) introduces the infiltration of
counter-terrorist agents within the TN, together with
the possibility of some terrorist agents collaborating
with anti-terrorist structures. Therefore, terrorist
agents can be neutralized leading to the destruction
of terror structures. (Ilachinski, 2012) developed an
exhaustive framework taking into account different
dynamics, and it focuses on the co-evolution of both
terrorist and counter-TN, using some measures as
entropy, vulnerability or cohesion. Moreover,
counter-terrorist agents can detect, infiltrate and
capture terrorist agents and/or links. (Tsvetovat and
Carley, 2004) simulates the behaviour of the terrorist
structure under attacks aiming to destabilize the
network. In order to do it, the anti-terrorism agents
have two goals: to learn the structure, tasks and
knowledge distribution of terrorists and to remove
and isolate terrorist agents. Regarding the first goal,
there are 3 ways of intercepting information spread
through the TN (random, snowball and socially
intelligent traffic analysis). Once the counter-
terrorist agents have enough information about the
TN, they can attack a random point, the one with the
highest degree centrality or cognitive load. (Genkin
and Gutfraind, 2011) studies different profiles (lone
and trapped wolfs, wolf and trapped wolf packs) and
scenarios of radicalization through isolation,
clustering and mean cell size measures. Occlusion
and encapsulation mechanisms are explained from a
SNA point of view and presented as counter-
terrorism strategies. (Keller, et al., 2010) analyses 4
counter-terrorism strategies and their corresponding
response from terrorist agents: leader-focused,
grassroots, geographic and random. Terrorist agents
modify their parameters in order to protect
themselves from these attacks. For example, they
increase the cost of creating new links in the case of
a leader-focused anti-terrorist strategy, since having
too many links is problematic. The same strategy is
adopted by terrorist agents in (O'Neil, 2012), where
highly exposed terrorist agents are killed or captured
et each simulation step. Each terrorist agent has a
secrecy attribute, that reflects the agent’s ability to
remain unexposed. Regarding (Li, et al., 2015), the
counter-terrorism aspect is taken into account by
allowing the network to be recovered after an attack.
The TN can be perturbed by eliminating either a
leader or a regular member of a terrorist cell, and the
reconstruction process is explained.
2.1.2 Behaviour Diffusion
Modelling the terrorist’s behaviour and its diffusion
is another approach used for studying TN formation.
Behaviour and opinion are two related concepts that
can raise some confusions. In this paper, an agent
behaviour and opinion is equivalent, and is
completely defined through its characteristic vectors
of characteristics (cf. paragraph 3.2).
(MacKerrow, 2003) focus in social bargaining
process that allows a bottom-up approach for belief
spreading. He also introduces the grievance toward a
social group using socio-economic and cultural-
penetration metrics, and the notions of social welfare
and social capital, as well as a social pressure.
(Berry, et al., 2004) developed a whole framework
to model behaviour diffusion. Agents’
disgruntlement evolves according to its personal
network, society attitude, mosques they are member
An Agent-based Simulation of Extremist Network Formation through Radical Behavior Diffusion
237

of and finally the clique behaviour, that is the
behaviour of agents surrounding it. Disgruntlement
changes following a linear reinforcement and/or
linear attraction. (Genkin and Gutfraind, 2011)
model the pressurability on an agent, that measures
how fast an individual changes his opinions
according to his friends’ ones, an essential notion in
order to model how a moderate agent becomes a
radical one.
2.1.3 Operations, Tasks and Roles
An important part of TN studies is focusing about
the objective of their members. Some papers take
into account the organization of a terrorist attack by
modelling different roles, tasks or necessary
operations in order to perform a mission.
(O'Neil, 2012) and (Li, et al., 2015) develop a
whole framework dedicated to operations, roles and
tasks, with hierarchical structures and leader
selection process. (Ilachinski, 2012) developed a
model of TN as a complex adaptive system, with
very complex roles, missions and dynamics.
(Raczynski, 2004) uses a probability of terrorist
attack based on the size of the TN as well as the
number of existing terrorist-supporting structures.
(Tsvetovat and Carley, 2004) model different tasks
and its assignation to agents through a meta-matrix.
Concerning (Moon and Carley, 2007), the objective
of individuals is knowledge acquisition (a pre-
condition to a terrorist attack).
2.1.4 Recruitment
In order to become a terrorist, a radical agent in
(Berry, et al., 2004) has to belong to a radical clique
and to be contacted by a “bridge” agent, that is an
agent who allows to interact with a terrorist
organization. A similar idea is used by (MacKerrow,
2003), where an agent has to be radicalized before
contacting a terrorist organization. Moreover
(MacKerrow, 2003) proposes a parameter of “self-
motivation toward terrorism” that allow some agents
to require more or less active recruitment. (Li, et al.,
2015) introduces a recruitment cell that
communicates with other cells in order to know
about human resources needs. They define also the
processes of recruitment and a parameter of
recruitment cost. (O'Neil, 2012) take also into
account a recruiter role and proposes a mechanism
of replacement of a leader.
2.2 Common Aspects
In order to answer the previous questions, we have
identified some more general aspects tackled by
authors. These aspects are not the main issue of
respective papers but they are however necessary to
answer some central questions. The first three (Link
creation, Structure and process relation and
Topology) correspond to network formation related
issues, and the last two (Multilayer and In/Out data)
are more methodological.
2.2.1 Link Creation
This is the most important step in a simulation
model of network formation.
(Berry, et al., 2004) calculates the weight of a
relationship between two agents, based on the
disgruntlement level of agents and their personal
traits. A link is created from a certain threshold.
(MacKerrow, 2003) uses a social bargaining
between agents since they seek to get into a leader’s
network, that is someone with a lot of relationships,
so creating a link has a “social cost”. (Raczynski,
2004) creates a link when agents are spatially close,
and this is more likely when they are in cities, an
abstract agent of his model. (North, et al., 2004)
focus on the inference from incomplete network
data, together with some social network rules and
detailed documentation about interactions between
agents. (Ilachinski, 2012) link dynamics is based in
one hand on the theory of communication of (Monge
and Contractor, 2003), that is social reward and
mission gain, and in the other hand in an equation
calculating the perceived risk of creating a link.
Furthermore, agents have some motivations to create
or erase links, as acquiring mission-required
resources or the perceived risk of discovery.
(Tsvetovat and Carley, 2004) and (Moon and Carley,
2007) give a detailed equation to select the best
candidate to create a link to and also a probability of
interaction based on differences between agents’
attributes, social distance and spatial proximity.
(Genkin and Gutfraind, 2011) follows the “never
swap a good friend” rule. This is based on
homophily, magnets (the equivalent of social spots
in this paper), degree budget (maximum of
connections by agent), transitivity and an attrition
parameter measuring the migration rate of radicals
among different communities. (Keller, et al., 2010)
applies the preferential attachment principle.
(O'Neil, 2012) shows a formula calculating the
weight of links, based on agents’ roles and locations.
Moreover, there is a mechanism controlling the
macro behaviour of the network, depending on the
success of terrorist operations. (Li, et al., 2015)
specifies some scenarios where a link can be created.
ICAART 2017 - 9th International Conference on Agents and Artificial Intelligence
238

For example, when an agent transfers a resource
from a cell to another, links created by terrorist
recruitment cells when they capture new terrorist,
and the designation of a new leader.
2.2.2 Structure and Process Relation
Some authors explain how network’s structure and
agents’ behaviours interact, independently of link
creation process.
For example, in (O'Neil, 2012) the network
structure changes according to the issue of
operations. In (Li, et al., 2015), the network is re-
structured after the counter-terrorism attacks.
(Genkin and Gutfraind, 2011) identifies radical
profiles as well as counter-terrorism strategies using
SNA measures and the position of agents in the
network. Agents in (Moon and Carley, 2007) change
its behaviour and goal according to its position in the
space, since they seek for knowledge and resources
distributed over the geographical space. (Berry, et
al., 2004) models an inter-relation between cliques
and agents’ behaviours, that is these two entities
influence each other at the same time. Finally, the
structure of the network in (Ilachinski, 2012)
depends on roles, operations and the battlefield
context.
2.2.3 Network’s Topology
Regarding the structure of the obtained networks in
analysed papers, it is difficult to stablish a consensus
about the actual topology of TN.
(MacKerrow, 2003) (Berry, et al., 2004)
(Tsvetovat and Carley, 2004) (Genkin and
Gutfraind, 2011) (Li, et al., 2015)obtain
cellular/clique based networks. (Raczynski, 2004)
obtain a tree structure. (Moon and Carley, 2007)
follows a spatial structure. (Keller, et al., 2010) uses
a preferential attachment rule so he obtains a scale-
free network. Finally, (North, et al., 2004)
(Ilachinski, 2012) (O'Neil, 2012) allow their model
to create any kind of topology, depending on
parameters or existing prior data.
2.2.4 Multilayer Networks
As discussed before, qualitative approaches are
interested in the type and motivation of relationship
between individuals, and multilayer structures are
the natural way of taking into account these details.
Furthermore, there are more and more mathematical
formalizations of multilayer networks (De
Domenico, et al., 2013).
Regarding terrorist multilayer networks,
(MacKerrow, 2003) defines kinship, religious,
organizational and friendship layer. (Berry, et al.,
2004) observes the following layers according to the
weight or strength of the link between individuals, in
ascending order by strength: world, mosque,
acquaintance, strong bonds and clique. (Ilachinski,
2012) proposes a more complex layer division, with
3 different layers oriented to a counter-terrorism
strategy: genotype (primitive agent behaviour),
phenotype I (emergent agent behaviour) and
phenotype II (emergent squad and force behaviour).
Moreover, agents in his framework perform actions
in two different spaces: physical and information
one. Finally, (Tsvetovat and Carley, 2004) and
(Moon and Carley, 2007) uses a meta-matrix
approach allowing to take into account agents,
knowledges, resources, locations and tasks.
2.2.5 In/out Data
(Berry, et al., 2004)does not precise any input data,
however a similar paper (Berry, et al., 2003)
discusses about using available data from urban
street gangs as an analogy of terrorist groups.
(MacKerrow, 2003) uses census data, interviews and
GIS data in his model in order to initialize attributes
like ethnography, income, religion, educational
degree, etc. Likewise, the allegiance vector is built
from qualitative data. (North, et al., 2004) generates
a TN from a sample of a given network. (Moon and
Carley, 2007) describes the input data set as the
result of an automatic process of analysis of
unclassified documents like newspaper articles or
intelligence reports using AutoMap text analysis
tool. Regarding spatial information, they hand coded
corresponding latitudes and longitudes. (O'Neil,
2012) extracts information from JJATT database
(doitapps.jjay.cuny.edu/jjatt/) in order to define
agent’s roles. Moreover, since his model mimics real
world networks, the Jemaah Islamiyah network from
JJATT was used as initial network. (Keller, et al.,
2010) models counter-terrorism strategies based on
empirical ones. (Ilachinski, 2012) doesn’t put any
data in his model but the topology and dynamic of
his model have been developed following
operational and ground knowledge. (Genkin and
Gutfraind, 2011) does not use any real data as input
of the model, however the results are partially
validated by empirical data and radical profiles are
based on empirical cases of home-grown self-starter
terrorism. This data comes from some available
datasets as Lexis-Nexis, TRC or START among
others. NetWatch package, presented in (Tsvetovat
and Carley, 2005) and (Tsvetovat and Carley, 2004),
An Agent-based Simulation of Extremist Network Formation through Radical Behavior Diffusion
239

generates synthetic TN based on real network data.
As case of study, they show the generative model of
the September 11th hijackers dataset collected by
(Krebs, 2001). Real data is also used to describe the
terrorist attack strategies, that is sequences of tasks,
resource management, etc.
Table 1 sums up the precedents paragraphs.
3 MODEL DESCRIPTION
The model described below is a GAMA
implementation based on (Berry, et al., 2004).
GAMA is a modelling and simulation platform
(Grignard, et al., 2013) that allows modellers and
experts in numerous domains (ecology, social
sciences, etc.) to build complex models without
strong computer sciences skills, thanks to high-level
modelling language, supporting the integration of
multiple level of agency and realistic environments.
Nevertheless, even if some aspects as social spot
stickiness or social similarity (cf. next paragraphs)
are common to (Berry, et al., 2004), the main goal of
this paper is to show a mechanism of network
formation and not only the recruitment of terrorist
through clique detection. Moreover, this paper
focuses on cultural vector or social transfer and
meeting mechanisms.
3.1 Entities
3.1.1 Social Spots
Social spots represent places where behaviour
diffusion takes place. During the simulation, agents
can attend a social spot. In order to choose a social
spot, a stickiness (Berry, et al., 2004) percentage is
computed. This value depends on agent personality
and social spot ideology. A social spot ideology is
defined from its members’ zeal and cultural vector,
and from its own cultural vector. This last value can
represent the personality of the social spot leader, or
some trait well known about the social spot. For
example, one can have a certain a priori about a
social place independently of the existence of a
leader.
3.1.2 Agents
An agent’s personality is defined by fixed attributes
like age, sex, religion, etc. and a cultural vector
similar to the allegiance vector presented by
(MacKerrow, 2003) that describes cultural traits,
that is the opinion about some specific
organizations, countries, etc. Moreover, an agent has
a value of zeal, which is defined as a measure of
agent’s political violence (Genkin and Gutfraind,
2011). Zeal value allows to make a difference
between an extremist passive agent and an active
one. An agent with a very high zeal value is ready to
becomes a terrorist. This is similar to the
disgruntlement value described by (Berry, et al.,
2004). Zeal evolves every time two agents meet, in
function of their current zeal values. For example, if
both agents are radicals, they mutually increase their
zeal.
“Society” is a special kind of agent based on
(Berry, et al., 2004) that influences agents at each
simulation step. This influence has an impact in the
agent’s cultural vector depending on its social
pressure sensibility value. Society agent allows us to
model the macro mechanism taking place in the
network formation process.
3.2 Dynamics
The dynamic of the model is fully described by 3
processes: dynamic related to the social network that
is the formation of links, the attending to a social
spot and the social transfer between agents. These
dynamics are computed sequentially (discrete event
simulation) Every dynamic influences the other,
since for example an agent will create a link with
other agent depending on a score taking into account
if they are in the same social spot and the similarity
between their cultural vectors.
3.2.1 Link Creation
The model allows agents to meet in different ways.
First, they can do random meetings with a certain
probability (Tsvetovat and Carley, 2005). Otherwise,
there are two meeting or dynamic mechanisms:
a. According to the social similarity
Here, a social similarity measure is used to
decide whether two random agents are able to create
(or remove if below a threshold) a link between
them within the social network. Social similarity is
based on the similarity equation presented in (Berry,
et al., 2004) and network measures like shared
friends, homophily and degrees.
b. According to agent’s opinion
The model presented in (Holme and Newman,
2006) is used to compute the dynamics of opinions.
At each simulation step, an agent has two
possibilities: Either to switch one of his links by
another one (that is remove one link and create
another one) that allow it to connect with an agent
ICAART 2017 - 9th International Conference on Agents and Artificial Intelligence
240

having the same opinion or to replace his own
opinion by the opinion of one of its neighbours,
keeping the same link.
3.2.2 Attending a Social Spot
An agent can belong to a social spot if a “stickiness”
score is high enough to attend it. This score is based
on (Berry, et al., 2004) with a modification allowing
to take into account both fixed characteristic and
cultural vectors.
3.2.3 Social Transfer
The social transfer mechanisms allow agents to
communicate and exchange their cultural values,
what will have an impact in the other dynamics
(creating links and attending a social spot).
The current version of the model described here
uses Axelrod model for the dissemination of culture
(Axelrod, 1997), which allows to change one value
of the cultural vector at each interaction.
4 RESULTS
The following results show how a network is formed
through a radicalization process depending on the
social meeting mechanism used. The red dots
represent radical people and the white ones are
neutral people. For theses simulations, we have
initialized a population of 20 agents, 17 of which are
neutrals and 3 radicals. This size corresponds to a
neighbourhood scale simulation, where opinions can
diverge, be homogenized, evolve, etc. We think this
is a good trade-off between a large-scale simulation
as a region or inter-countries simulation
(MacKerrow, 2003) or a more restricted simulation
within a small group of 5-10 participants as many
sociological works.
Cultural and fixed vectors and zeal values are
initialized randomly between [-1,1], and social
pressure sensibility is minimal in the case of radical
agents, that is they are totally convinced in their
cause and can’t be neutralized. In this simulation,
there is a radical social spot and a neutral one, so its
cultural vectors correspond to its ideologies.
Moreover, the society agent influences some random
agents at each simulation step. This influence
changes some values of cultural vector in order to
radicalize the agent.
As explained above, there are two mechanisms
for agents to meet. The first one, based on a social
similarity metric, generates a network with two main
components: a clique of neutral people and another
one of radicals Figure 1.
This is an expected result since the model is
based on Berry’s (Berry, et al., 2004) which aims to
show the clique based structure of a TN. More
interesting is the evolution of the structure through
the simulation. One can observe that on t=75 there
are two communities of neutral people. This is due
to the existence of two different social spots, but
there is a homogenization process over the
simulation that bring together all neutral people in
one single clique. Concerning radical people, there is
a one person who was radicalized between t=0 and
t=75. Nevertheless, radicals don’t create a network
as quickly as neutrals. This can be explained with
the zeal parameter. Actually, one can be radical
because of different raisons, but the probability of
creating a link between two radicals is higher when
the zeal level is similar, that is when they are ready
to become an actual terrorist, meaning ready to
perform a terror act. There are also some contacts
between radical and non-radical people, but they
become increasingly rare.
Figure 2 corresponds to the network formation
process using Axelrod combined with (Holme and
Newman, 2006). The obtained structure is
completely different compared to the previous one.
People are more dynamic and choose their contacts
giving more importance to the opinion. Opinions
change in a more dynamic way, and the result is a
population with more radicals. Some people keep
their opinion and remain isolated from the main
component, that was not possible with the previous
model. This can be explained because social spots
have less impact on people behaviour, since people
are less devoted to the behaviour supported by social
spots and more on people’s one.
5 CONCLUSIONS
This paper describes a model of terrorism network
construction, with mechanisms allowing the
diffusion of cultural values, social meetings and
radicalization. We showed how the diffusion of
radical behaviour is related to the formation of the
network and vice-versa.
Axelrod model is used for the cultural transfer
between agents. However, other models of social
transfer as (Schleussner, et al., n.d.) (MacKerrow,
2003) (Deffuant, et al., 2002) are being developed
and adapted to our model in order to compare the
resulting networks.
Some important questions in terrorism as
An Agent-based Simulation of Extremist Network Formation through Radical Behavior Diffusion
241

operations, tasks and roles could be added to our
model as separated modules. Similarly, we could
study the multilayer structure of the society,
allowing us to discover more details about the
radicalization process.
Finally, the model is easily adaptable to others
multi-agent platforms or high-level computer
languages
REFERENCES
Axelrod, R., 1997. The dissemination of culture a model
with local convergence and global polarization..
Journal of conflict resolution, 41(2), pp. 203-226.
Berry, N. et al., 2003. Computational social dynamic
modeling of group recruitment, s.l.: Sandia National
Laboratories.
Berry, N. et al., 2004. Emergent clique formation in
terrorist recruitment. s.l., s.n.
Crossley, N., 2010. The social world of the network.
Combining qualitative and quantitative elements in
social network analysis. Sociologica, 4(1), pp. 0-0.
De Domenico, M. et al., 2013. Mathematical formulation
of multilayer networks. Physical Review X, 3(4), p.
041022.
Deffuant, G., Amblard, F., Weisbuch, G. & Faure, T.,
2002. How can extremism prevail? A study based on
the relative agreement interaction model. Journal of
artificial societies and social simulation, 5(4).
Genkin, M. & Gutfraind, A., 2011. How do terrorist cells
self-assemble: Insights from an agent-based model of
radicalization, s.l.: SSRN 1031521.
Grignard, A. et al., 2013. GAMA 1.6: Advancing the art of
complex agent-based modeling and simulation. s.l.,
Springer Berlin Heidelberg, pp. 117-131.
Hidalgo, C. A., 2016. Disconnected, fragmented, or
united? a trans-disciplinary review of network science.
Applied Network Science, 1(1), p. 1.
Holme, P. & Newman, M. E., 2006. Nonequilibrium phase
transition in the coevolution of networks and opinions.
Physical Review, 74(5), p. 056108.
Ilachinski, A., 2012. Modeling insurgent and terrorist
networks as self-organised complex adaptive systems.
International Journal of Parallel, Emergent and
Distributed Systems, 27(1), pp. 45-77.
Keller, J. P., Desouza, K. C. & Lin, Y., 2010. Dismantling
terrorist networks: Evaluating strategic options using
agent-based modeling. Technological Forecasting and
Social Change, 77(7), pp. 1014-1036.
Krebs, V. E., 2001. Mapping networks of terrorist cells.
Connections, 24(3), pp. 43-52.
Lévy, J.-D., Desreumaux, M. & Bartoli, P.-H., 2016.
Baromètre annuel: Bilan de l'année écoulée 2015 et
perspectives pour l'année future 2016, s.l.: Harris
Interactive.
Li, B., Sun, D., Zhu, R. & Li, Z., 2015. Agent Based
Modeling on Organizational Dynamics of Terrorist
Network. Discrete Dynamics in Nature and Society.
MacKerrow, E. P., 2003. Understanding why-dissecting
radical Islamist terrorism with agent-based simulation.
Los Alamos Science, Volume 28, pp. 184-191.
Monge, P. R. & Contractor, N. S., 2003. Theories of
communication networks. s.l.:Oxford University Press.
Moon, I. C. & Carley, K. M., 2007. Modeling and
simulating terrorist networks in social and geospatial
dimensions. IEEE Intelligent Systems, 22(5), pp. 40-
49.
North, M. J., Macal, C. M. & Vos, J. R., 2004. Terrorist
Simulation with NetBreaker. Ann Arbor, Michigan,
s.n.
O'Neil, P., 2012. Dynamic, covert network simulation. s.l.,
Springer Berlin Heidelberg, pp. 239-247.
Raczynski, S., 2004. Simulation of the dynamic
interactions between terror and anti-terror
organizational structures. Journal of Artificial
Societies and Social Simulation, 7(2).
Schleussner, C. F., Donges, J. F., Engemann, D. A. &
Levermann, A., n.d. Clustered marginalization of
minorities during social transitions induced by co-
evolution of behaviour and network structure.
Taylor, M., 2010. Is terrorism a group phenomenon?.
Aggression and Violent Behavior, 15(2), pp. 121-129.
Tsvetovat, M. & Carley, K. M., 2004. Modeling complex
socio-technical systems using multi-agent simulation
methods. KI, 18(2), pp. 23-28.
Tsvetovat, M. & Carley, K. M., 2005. Generation of
realistic social network datasets for testing of analysis
and simulation tools, s.l.: SSRN 2729296.
ICAART 2017 - 9th International Conference on Agents and Artificial Intelligence
242
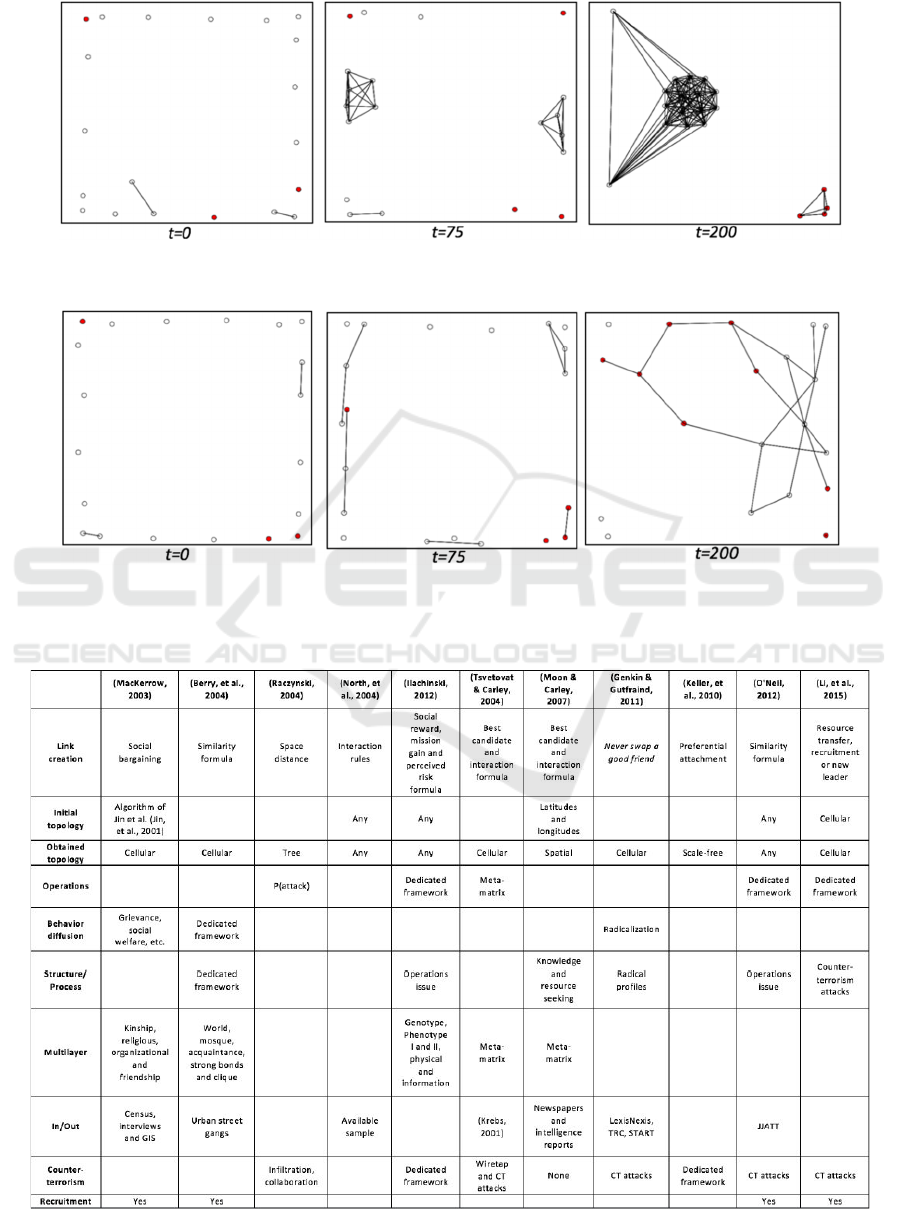
APPENDIX
Figure 1: Network formation using Axelrod model of social transfer combined with social similarity based mechanism of
meetings.
Figure 2: Network formation using Axelrod model of social transfer combined with Holme’s model (Holme and Newman,
2006) of opinion diffusion.
Table 1: Detail of key features by paper.
An Agent-based Simulation of Extremist Network Formation through Radical Behavior Diffusion
243
