
Multi-Agent Approach for Evacuation Support System
Shohei Taga
1
, Tomohumi Matsuzawa
2
, Munehiro Takimoto
2
and Yasushi Kambayashi
1
1
Department of Computer and Information Engineering, Nippon Institute of Technology,
4-1 Gakuendai, Miyashiro-machi, Minamisaitama-gun, Saitama 345-8510, Japan
2
Department of Information Sciences, Tokyo University of Science, 2641 Yamazaki, Noda 278-8510, Japan
Keywords: Multi Agent, Mobile Agent, Ant Colony Optimization, Mobile Ad Hoc Network, Contingency Plan, Risk
Management.
Abstract: We propose a system that supports evacuation after a large-scale disaster. When a large-scale disaster
occurs, collecting information by using portable devices is difficult, because communication base stations
collapse and traffic congestion occurs. Evacuees are at a loss where they should go for safe places in lack of
information. In order to overcome these problems, we have proposed and evaluated a multi-agent system
that is built on MANET. Our aim is to let the users share information on MANET, and provide safe routes
to the destination by using collected information. In the previous paper, we proposed and implemented the
main functions of the proposed system, and performed feasibility study of the multi-agent system by using
simple simulator. In this paper, we report the revised system and investigate the relationships between the
number of the users and diffusivity of information, and the number of the generated mobile agents by using
newly constructed simulator. In the experiments for evaluation, we simulated a realistic situation by using
real map data and we took stochastic change of the situation into consideration, because the situation must
be getting worse by time elapses.
1 INTRODUCTION
When a large-scale disaster, such as big earthquakes
occurs, a large-scale fire occurs, buildings collapse,
and roads break. In addition, the public transports
may paralyze and large-scale traffic congestion may
occur. As a result, a number of evacuees may
inundate the damaged towns. Furthermore, people
starts to use the communication devices, such as
smartphones, to collect information about the service
status of public transport and safety information of
family and friends. As a result, communication base
stations may become too congested as well as
destroyed. The users of communication services
cannot depend on the traditional communication
infrastructure, because of the collapse of the base
stations and extreme congestion.
When the Great East Japan Earthquake occurred
in 2011, we experienced shaking of magnitude 5
even in Tokyo. Tokyo
is more than 300km south from
the seismic centre. About 5.15 million people could
not confirm the safety of their family members due
to communication network congestion. A cascading
communication failure prevented people from
contacting their families and friends. People had to
go back home using unfamiliar roads on foot. In
such situations, where the buildings may be on fire
and bridges may collapse, it is very dangerous to
walk on the roads without navigating information.
Some companies have already developed support
applications that address large-scale disasters. An
example is the "Disaster return home support map"
that Mapple-on, Inc. offers. (Mapple ON Co., Ltd.,
2016). This application installs the map data to the
users’ portable device in advance. Even if a
large-scale disaster cut off the Internet, people can
use the map information off-line. This application
provides the minimum necessary information to cope
with large-scale disasters such as alternating roads
and emergency shelter. This application also
provides the route guidance function to the
destination of each user. However, the system lacks
of a function to collect the environmental
information that dynamically changes, such as fires
or buildings collapsing after the disaster. Therefore,
a situation may happen such that the system suggests
a safe route that is actually damaged and impassable,
and of course dangerous. Thus, we need a means to
provide alternative routes to the destination for each
user by collecting environmental information about
the dynamically changing post disaster situation.
220
Taga S., Matsuzawa T., Takimoto M. and Kambayashi Y.
Multi-Agent Approach for Evacuation Support System.
DOI: 10.5220/0006194202200227
In Proceedings of the 9th International Conference on Agents and Artificial Intelligence (ICAART 2017), pages 220-227
ISBN: 978-989-758-219-6
Copyright
c
2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

We proposed a system that supports pedestrians
returning home after a large-scale disaster (Taga et
al., 2016). The system was intended to provide an
appropriate route to the destination for each user. We
designed the system that can collects information
even when a communication failure occurs, and
generate routes dynamically based on the collected
information. In the previous paper, we proposed and
evaluated the main functions of the system, and
performed a feasibility study of the multi-agent
system by using simple simulator. In the
experiments, we observed that the communication
load to the agent system is unrealistically high. For
that reason, we have simplified the agent system. In
this paper, we report the revised system and
investigate the relationships between the number of
the users and diffusivity of information, and the
number of the generated mobile agents by using
newly constructed simulator. In the experiments for
evaluation, we have simulated realistic situation by
using real map data and taking stochastic change of
the situation into the consideration, because the
situation must be getting worse by time elapses.
It is preferable to build a mobile ad hoc network
(MANET) by direct communication between
portable devices to cope with the post disaster
circumstance. Since the network uses portable
devices as relays, communication can continue
without the intervention of the base station. Since
MANET is a network constructed by using only
portable devices, it is more prone to disconnection of
the communication networks than the station-base
communication system. Furthermore, the proposed
system is supposed to be used by evacuees after
large scale disasters, therefore the users of the
system as communication nodes are always moving,
this problem requires even more serious
consideration on routing.
In order to mitigate the above problem, we have
adopted mobile agents in our proposed system.
Mobile agents are software agents that hold not only
data but also computing capability when moving.
Thus, mobile agents can continue processing state
before moving on the destination so that they can
decide autonomously and intelligently to where it
should move without the assistance of routers. The
communication is established only at the moment the
mobile agents to move. Therefore, it should be
useful in the communication based on an unstable
MANET environment.
The structure of the balance of this paper is as
follows. The second section describes the
background and discusses the related works. The
third section describes the multi-agent system that is
the basis of our proposed system. In order to
demonstrate the feasibility of our system, we have
constructed a simulator for this system and have
conducted numerical experiments. We report the
results and discuss the future works in the fourth and
fifth sections. Finally, we conclude our discussion in
the sixth section.
2 BACKGROUND
Asakura et al. investigated the calculation of the
evacuation routes after a large-scale disaster. They
have proposed a method that uses Ant Colony
Optimization (ACO), and have shown it is useful in
a simulator. (Asakura et al., 2013).
Alejandro Avilés et al. investigated how to
support people escaping to the emergency exit from
the building (Aviles et al., 2014). In their study, they
assumed some of evacuees use portable device based
guidance system like in our study. They have also
adopted MANET and the ACO in order to derive
escape routes.
ACO is an optimization technique that mimics
the foraging behavior of ants. Ants go back and forth
between the feeding grounds and nest in order to
bring food from feeding areas to nests. At that time,
ants put down volatile chemical substance called
pheromone to the routes they went. Other ants that
are back and forth feeding grounds and nest follow
the pheromone and replenish drop the pheromone.
By these actions, the long paths to the feeding
grounds lose their pheromone by evaporation before
the pheromone replenished. On the other hand, other
ants strengthen shorter path pheromone before
evaporation. As the result, ants derive the optimum
route to feeding area. We call methods that are using
this characteristic ACO. (Dorigo et al., 1996).
In Avilés’s study, an evacuee who succeeded to
escape generates a mobile agent called Goal Agent
(GA) from his or her portable device. Generated GA
repeats the move to the portable devices of other
evacuees, to record the number of times of the
movement of its own to the destination portable
device. Further, an evacuee who is seeking safe exits
generates the other kind of mobile agents called
Routing Agent (RA) from his or her portable devices.
Generated RA repeatedly migrates to the portable
devices in the other evacuees, collects the number of
times of the movement of GA that is recorded in the
destination device. The system uses the number of
movements of the GA as pheromone of ACO to
guide evacuees to the safe route. They proposed a
method of providing the evacuees the trajectory of
Multi-Agent Approach for Evacuation Support System
221
the movement of the smallest number of movements
of GA that should be the optimal escape route.
There is a network technique called Delay
Tolerant Network (DTN). DTN is a technique that
was designed for adapting difficult circumstances to
maintain the network communication, such as nodes
constructing the network are scarce and always
moving. When a source node cannot communicate
with the destination node to which it wants to send
data, the node keeps storing the data to transmit.
When the target node is approaching, it then
transmits the previously accumulated data. When
sending data to a distant node, the system treats the
nodes between them as relays and achieves the data
transmission like a bucket brigade. Thus, if
temporarily communication is established
intermittently, it is possible to communicate between
arbitrary nodes. This feature is similar to that of
mobile agents.
Nishiyama et al. investigated communication
network that combines the DTN and the MANET by
using only smartphones (Nishiyama et al., 2016).
They constructed a communication network with
multi-hop connections between the smart phones by
Wi-Fi. As a feature, it utilizes the switching network
techniques with different characteristics of MANET
and DTN in accordance to the communication
conditions autonomously. When the system finds
many nodes, it uses MANET, and it found
communication is difficult, it switches to use DTN.
Thus, the reduction of the communication load and
power saving is achieved. Moreover, by utilizing the
drones in addition to smartphones, additional
scalability can be expected. Our study is also using a
network technique combined with MANET and
DTN by the mobile agents.
Nishiyama et al. focused only on constructing
communication network, while our research focuses
the dynamic routing using mobile agents. For both
MANET and DTN, the communication network
among the portable devices that people have is
constantly changing. In addition, all the evacuees
who use the system are not necessarily looking to the
same destination. They should be able to set the
destination for their own. Mobile agent perceives its
environment, and it can autonomously change the
behavior. Taking advantage of these features, we are
implementing a system that is capable of responding
flexibly to a wide variety, such as user requests and
network environment changes.
The proposed system has two main features; one
is to build a network consisting of only portable
devices by wireless communication. The other one is
the sharing and spread information by the
multi-agent system in the network. We assume
MANET as the communication network. Imaginary
situation in which the proposed system is used
would be a scene where the congestion of the
portable device communication occurs. Therefore,
we can assume that there are many users, and
constructing MANET would be no problem.
However, in our proposed system, a mobile agent
has certain destination and the direction is limited. If
a mobile agent cannot find a destination node in its
limited direction, the mobile agent has to wait. Such
a case needs DTN. Therefore, the network that we
are proposing has both the features of MANET and
DTN. We describe the multi-agent system in detail in
the next section.
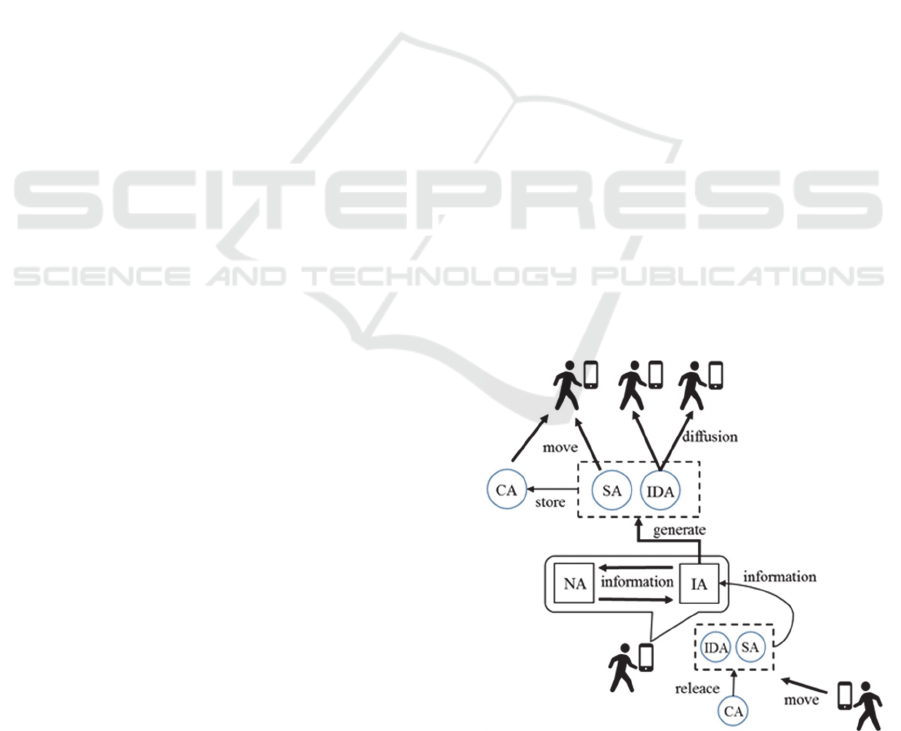
3 AGENT SYSTEM
The proposed system is a multi-agent system. A
multi-agent system is a system implemented by
multiple agents that operate cooperatively. In the
agent system, there are two types of agents. One is
static agents that reside on the users’ portable
devices: they are the information agent (IA) and the
node management agent (NA). The other is mobile
agents that move among the users’ smartphones:
they are the information diffusion agent (IDA), the
safety information agent (SA) and the container
agent (CA). The user generates mobile agents as
needed, and mobile agents convey messages while
moving between portable devices. Static agents are
resident in portable devices and process the data
gathered by mobile agents as well as provide user
interface. They also have responsibility to generate
mobile agents. Figure 1 shows the relations between
these agents.
Figure 1: Multi-agents system.
ICAART 2017 - 9th International Conference on Agents and Artificial Intelligence
222
3.1 Information Agent (IA)
IA is a static agent. Its roles are providing the user
interface, generating mobile agents, and deriving the
evacuation routes on the map for each user.
First, we describe the user interface. IA displays
the derived route on the map with useful information
such as impassable points and first aid stations.
When the user finds an impassable point or a first aid
station, he or she presses the corresponding diffusion
button on the screen so that IA creates an IDA to
diffuse the newly discovered information. IA
updates the information on the map as IDAs, which
are created by other users, arrive and give IA new
information.
Second, we describe the generation of mobile
agents. When the generation condition of each
mobile agent is satisfied, IA generates the mobile
agent. When IA generates the mobile agent, it passes
necessary information to the mobile agent, and
dispatches it to one of the portable devices nearby.
When the mobile agent generated by another
portable device arrives, IA receives the information
and passes it to NA.
Third, we describe the route derivation. IA
derives the route to the destination by using the
collected information. While the default destination
is set to the home, the system switches the
destination to the rest area after certain time has
elapsed since system startup, in order to give the user
a break. The user can choose whether the switching
occurs and duration time for switching. IA derives
the return route by Dijkstra algorithm, and then
displays it in the map on the interface screen
(Dijkstra, 1959). If IA receives information of an
impassable point on the current route, it re-derives a
new route that avoids that point. IA also re-derives
the route when the user changes the destination so
that IA provides the latest and secure route.
3.2 Node Management Agent (NA)
NA is a static agent that keeps the collected
information and passes the information to IA on
request. The stored information includes GPS
information representing the current location, the
current destination, the impassable locations, the first
aid stations and the location of the rest areas along
with the time they are stored and the IDs of the IDAs
that convey the information. When redundant
information is delivered, NA deletes the old
information by referring to the time information. In
addition, after a certain time from the store, the old
information is deleted.
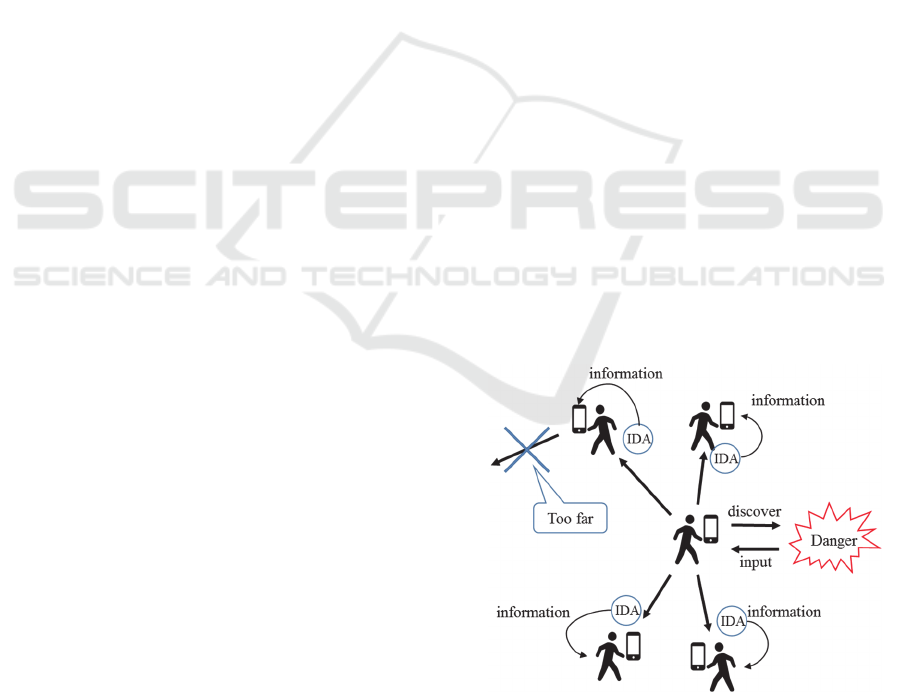
3.3 Information Diffusion Agent (IDA)
IDA is a mobile agent that diffuses useful
information such as impassable points on roads and
bridges, resting places and the first aid stations that
the user finds. IDAs collectively implement the
information sharing among the users.
When the user presses one of the diffusion
buttons on the interface screen, IA produces an IDA.
The IDA has the information about what the user
finds the location and the time. Then, the IDA clones
itself to the number of portable devices that are
linked to the originating smartphone. One copy
moves each of the neighbor portable devices. IDA
has a unique ID and all the IDs of the duplicated
IDAs are the same. Upon arrival, IDA passes its
information and its ID to the IA of the portable
devices it arrives to and it clones itself again to all
connected portable devices. If its ID is already stored,
the IDA self-destructs without doing anything. By
doing so, IDA prevents dispersing redundant
information. In addition, each IDA disappears after a
certain number of movements.
IDAs collectively implement the pheromone in
ACO. IDA determines the value of its information
according to the distance between the point of origin
and the current position, the number of movements it
performed, the elapsed time from it was generated.
In other words, IDA reduces the value of its
information as the number of movements, the
elapsed time, the distance between the point of
origin and current position increases. When the
information value gets to be below a certain
threshold, the IDA gets to be useless and
self-destructs (Figure 2).
Figure 2: Information diffusion agent.
Multi-Agent Approach for Evacuation Support System
223
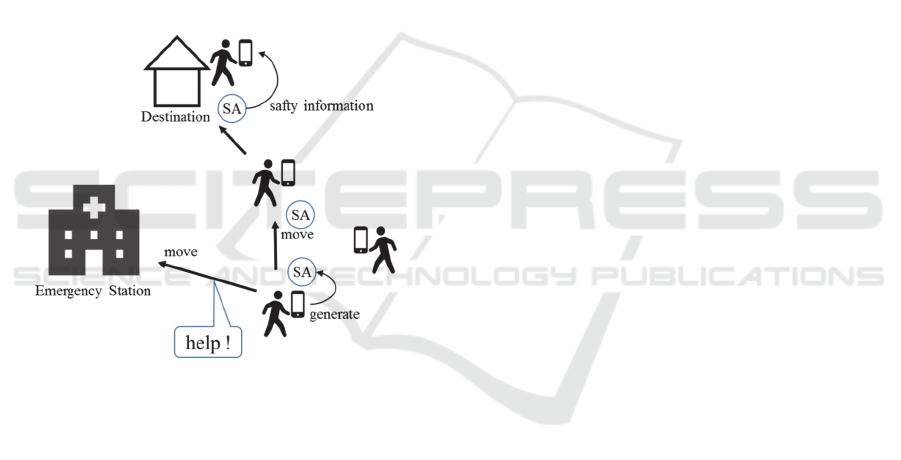
3.4 Safety Information Agent (SA)
SA is a mobile agent that transmits the safety
information. Safety information is not related to the
evacuation. However, safety information of family
members and friends is what people want to know.
SA conveys information such as user’s name,
date of birth, current position, and state (fine or
injured). IA generates SA, and passes the input
information described above. IA generates SA at
predetermined time intervals. Generated SA moves
to the portable devices that are in the direction of the
location registered in advance (such as a home or
office) until it reaches to the destination. If SA
cannot reach to the destination for a long time, SA
self-destructs. When the user cannot move for
reasons such as injury, he or she needs to ask for
help. Such a time, SA moved to the nearest
emergency station, such as police or rescue stations
(Figure 3).
Figure 3: Safety information agent.
3.5 Container Agent (CA)
CA is another mobile agent, which bundle multiple
mobile agents with the same destination together. In
the preliminary experiments, we found the
communication load for mobile agents was too high.
Especially in a large city, it is large enough to
overload the communication capacity. This may
cause problems in unstable communication networks
such as MANET and DTN. The mobile agent may
not be able to move due to network congestion and
battery consumption.
In order to mitigate this problem, we take
advantages of the idea of the container agent system
proposed by (Kambayashi et al., 2016). When IA
finds multiple mobile agents with the same
destination, it create a CA that bundles the mobile
agents move to the same device in one batch and
conveys at once. This method enables multiple
mobile agents to be transferred at once. Once the
transfer completes, CA will be discarded and the
mobile agents included in it will be unbundled into
independent mobile agents.
4 EXPERIMENTS
We have designed and implemented a simulator in
order to evaluate the proposed system. Figure 4
shows the simulator. This shows the situation of a
post disaster city. This is the map of a part of Tokyo,
where the first author lives. We assume the
communication failure has occurred in the city.
4.1 Experimental Conditions
Elements displayed on the simulator are: 1) area map
of the simulated field, 2) the users (circle icon) who
use the proposed system, 3) the communication links
between portable devices owned by the users, 4) the
danger zone that the user cannot passes (x marked),
5) the destinations of the users (areas of “G” icon ).
When the simulation starts, the users are placed
on the field in random positions. The destination for
each user is also randomly selected from safe places.
In Figure 4, there are four safe places as destinations.
When the simulation starts, the entire user begins to
move in unison to their destinations. Each user aims
the destination in the shortest route, because the
system suggests the shortest path. The route search
to the destination uses Dijkstra method.
When a user comes close to the danger zone
while he or she is moving, the user stops moving and
generates IDA. The IDA has the position
information of the danger zone in contact. The IDA
duplicates itself and moves to the portable devices
that are linked by MANET to the portable device
that has created IDA. Then IDA passes information
to IA on the destination portable device, and diffuses
again. This action repeats as long as IDA is in range
from the discovered danger zone within 120m. After
the user generates IDA, the user can turn back the
way he or she has come. Then, IA takes the
discovered danger zone in consideration and
recalculates the route to the destination.
When IA on a user’s portable device obtains the
information of danger zone by arriving IDA
generated by other user, the IA recalculates the route
to the destination that avoids the danger zone. As
time elapses, the number of danger zones increases
as well as existing danger zones spreading by a
predetermined time interval. When a user is caught
ICAART 2017 - 9th International Conference on Agents and Artificial Intelligence
224
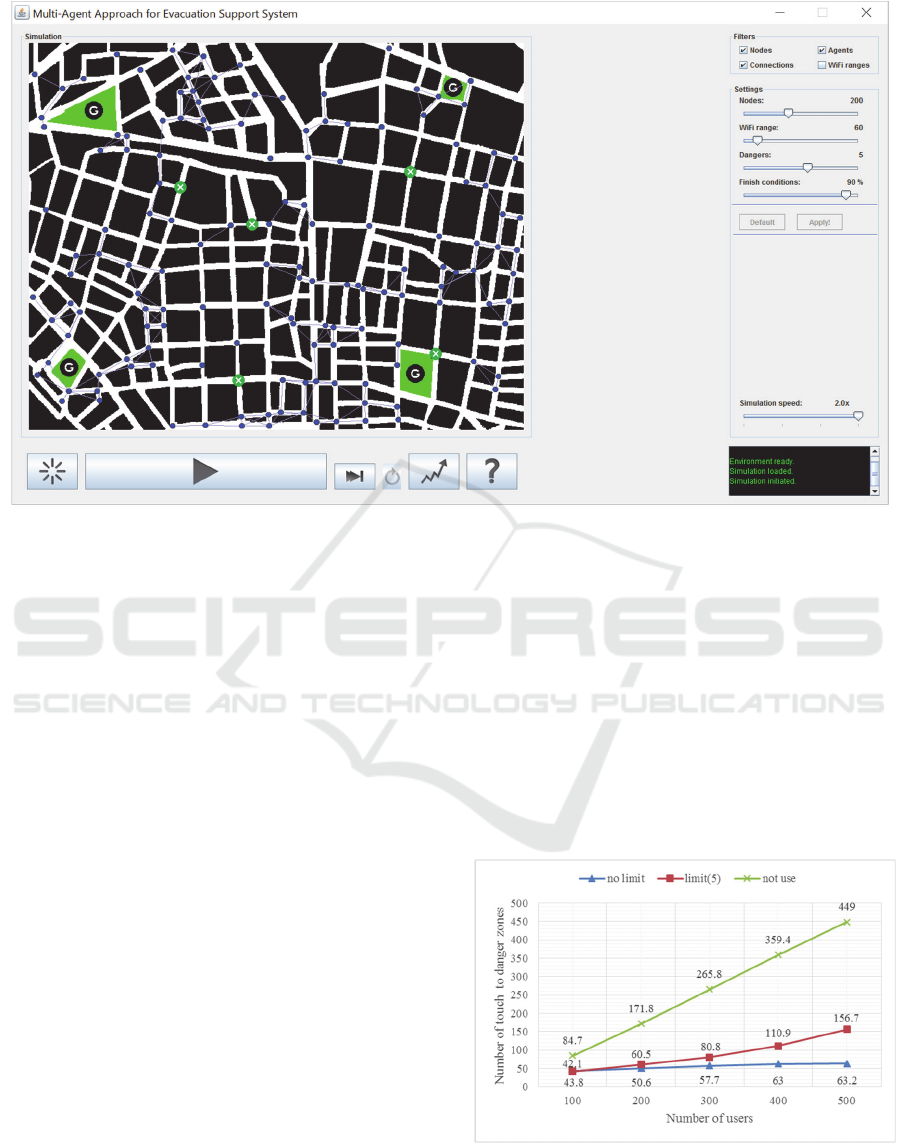
Figure 4: The simulator.
by danger zones and he or she finds no way to go out,
the user dies. If a user dies or arrives to the
destination, the user stops moving. Simulator
terminated when a certain percentage number of
users has arrived at the destination.
In this simulator,
“one round” expresses the unit length the user moves
and process agents. The number of rounds is
recorded and be treated as elapsed time of the
simulation. We recorded the following data: (a) The
maximum number of mobile agents that reside on
one of the portable device, (b) the number of times
that the users touched to the danger zones, and (c)
elapses time to complete the evacuation. We have
conducted experiments with the number of users 100,
200, 300, 400 and 500. For each case, we have
performed ten times and recorded the average
numbers for three data above. We have performed
experiments three cases for (b) and (c). The case 1 is
the case where each portable device can have
unlimited number of mobile agents, the case 2 is the
case where each portable device can have up to five
mobile agents, and the case 3 is the case no user uses
the system. Map used in the simulation is Arakawa,
Tokyo where the first author lives. The simulation
field is
900m * 1200m, and the
communication range
is set to
40m. That
is the distance that most Japanese
Wi-Fi devices can reach in general. Each simulation
ends when
90 % of users reach to their destination.
4.2 Experimental Results
The experimental results are as follows. The
maximum number of mobile agents was proportional to
number of users
.
Figure 5 shows the number of times that the
users touched to the danger zones. The graphs
display the three cases of the maximum number of
residing mobile agents: no limit, five, and zero.
Naturally, the more mobile agents can move and
reside on portable devices, the less the number of
times that the users touched to the danger zones.
Figure 5: The number of times that the users touched to the
danger zones.
Multi-Agent Approach for Evacuation Support System
225
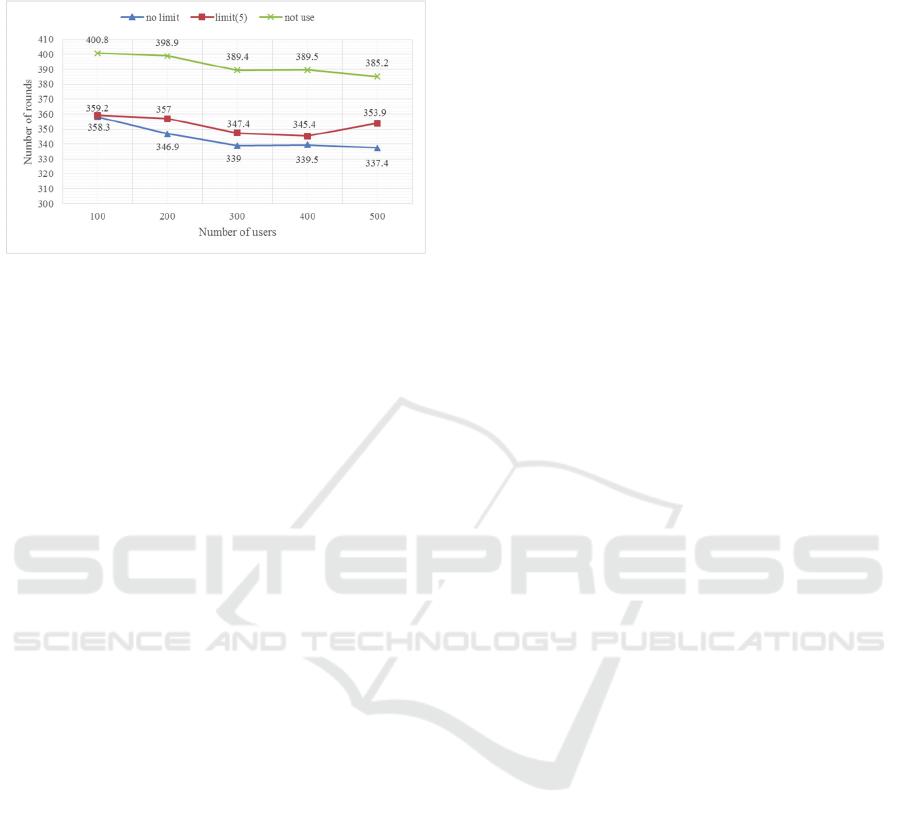
Figure 6 shows the duration time to complete the
evacuation for each of three cases.
Figure 6: Elapses time evacuation to complete.
4.3 Observations
First, let us consider the maximum number of mobile
agents that resides on each portable device. The
number of agents is a little more than proportional to
the number of the users. When the number of users
is 100, the number of mobile agents on one portable
device is at most ten. When the number of users is
500, however, the number of agents on one portable
device becomes more than 70. Those mobile agents
are coming in and going out on each portable device.
Kambayashi et al. investigated how long it took one
mobile agent to move between portable devices by
using IEE802.11. (Kambayashi et al., 2016).
According to their study, it takes about 1.6 seconds
for one mobile agent to move between two portable
devices. Even though their study did not use as many
mobile agents as our study, the result suggests it
would take more than several tens of seconds for
movements of 70 mobile agents. In such a case, such
process would cause battery consumption and
congestion by mobile agents.
Next, let us consider the number of times that
users touched the danger zones. We observed that
using our system drastically decreases the number of
touches to the danger zones as shown in Figure 5. In
the case of 100 users, our system decreases the
number of touches to danger zones by almost 50%.
In the case of 500 users, the effect is further dramatic.
In the case of no limit on the maximum number of
mobile agents, the number of touches to danger
zones decreased to about 1/7 as compared with those
of not using the proposed system. This result
suggests that, the more the participants in the
network constructed by the proposed system, the less
people face to the dangers due to improved
information propagation.
As described above, however, if there were 500
users, there would be too many mobile agents. Too
many mobile agents effectively paralyze the
multi-agent system due to congestion. Therefore, we
consider the case of the limited number of mobile
agents and the case of not-limited number of mobile
agents. The maximum number of mobile agents in
the case of not-limited number is about seventy. The
maximum number of mobile agents in the case of
limited number of agents is five. Even though we
limit the number of mobile agents that can reside on
one portable device to five, we can decrease the
number of times the users touch to the danger zones
drastically. When people do not use the system,
almost all the participants touch to the danger zones.
On the other hand, people use the system with
restricted portable devices, i.e. the number of mobile
agents is up to five, touch to the danger zone only
one third times.
Finally, let us consider the duration time to
complete the evacuation. Whether the number of
mobile agents is limited or not limited does not
affect very much, while whether using the system or
not affects very much. Figure 6 clearly show the
effectiveness of our system. People using the system
can move to their safe places much quicker than
people not using the system can.
5 DISCUSSIONS
As shown in Figure 5, the more the participants in
the MANET, the better the performance of the
proposed system. However, increasing number of
mobile agents leads to various problems. In order to
cope with these problems, we have limited the
number of mobile agents that can reside on one
portable device in the experiment (b). Our results
suggest that even though limiting the number of
mobile agents decreases the performance of the
proposed system, the effect is not fatal. Limiting the
number of mobile agents can help to construct a
system that is more realistic. In this study, we only
experimented with the maximum number of the
agents five, but it is necessary to propose a
theoretical basis for such restrictions.
As an example, we are reconsidering the way to
dispatch IDAs. This agent performs the role of
diffusing the discovered information to other users.
It is not necessary to move IDA to a user who is
closer to the discovered information than those who
discover the information. Because, this user can find
the discovered information before IDA arrives to this
user. This problem requires further consideration.
Due to the nature of the proposed system, false
information might be diffused. In fact, when the
Great East Japan Earthquake of 2011 occurred, there
were problems with false information diffused
ICAART 2017 - 9th International Conference on Agents and Artificial Intelligence
226

through social networking service. In time of a
large-scale disaster, information is of high
importance. In addition, many people become
disoriented and can be deceived easily by the false
information. Therefore, it is necessary to take
precautions against this.
One of the ways to address this problem may
take advantages of ACO. The characteristic of the
pheromone in ACO applies to diffused information.
For example, the system can treat old information as
less important than new information. Then it
becomes possible to select and discard information.
It is not clear, however, how to set the pheromone
values. Goto et al. have studied a route search using
ACO. They have used two types of pheromones.
One pheromone calculates the escape route. Another
pheromone deletes the pheromone, which exists in
the danger zone. From these pheromones, the system
calculates routes to avoid the danger zone. (Goto et
al., 2016).
6 SUMMARY
In this paper, we proposed a system that supports
evacuation at the time of large-scale disasters. In
order to cope with communication failure due to
damage and congestion of the communication base
station, we proposed to build a MANET via
communication between portable devices, and to
collect information by a multi-agent system. We
have implemented a simulator that evaluates how
much the proposed system can save evacuees at the
time of large-scale disasters. On the simulator, we
have performed many experiments and recorded
three data: (a) The maximum number of mobile
agents that reside on one of the portable device, (b)
the number of times that the users touched to the
danger zones, and (c) elapses time to complete the
evacuation. We have found that the more people join
the MANET, the better the information spreads,
though having too many mobile agents also leads to
problems.
In addition to the problem with over-proliferation
of the mobile agents, the current system also suffers
from the problem with diffusing false information.
There is certainly needs to improve the simulator for
a more realistic simulation. For example, Goto et al.
created a simulator based on the real tsunami data of
Rikuzentakada after the Great East Japan Earthquake
occurred in 2011 (Goto et al., 2016). Ushiyama et al.
reproduce the details of this tsunami phenomenon
from various recorded data and testimony (Ushiyama
et al., 2012). We are planning to use this data.
ACKNOWLEDGEMENTS
This work is supported in part by Japan Society for
Promotion of Science (JSPS), with the basic research
program (C) (No. 25330089 and 26350456),
Grant-in-Aid for Scientific Research.
REFERENCES
Aviles, A. M., Takimoto, M., Kambayashi, Y., 2014.
Distributed evacuation route planning using mobile
agents. Transaction on Computational. Collective
Intelligence XVII, LNCS 8790, pp.128-144.
Taga, S., Matsuzawa, T., Takimoto, M., and Kambayashi,
Y., 2016. Multi-Agent Approach for Return Route
Support System Simulation. Proceeding of the Eighth
International Conference on Agents and Artificial
Intelligence, vol. 1, pp.269-274.
Mapple ON Co., Ltd., 2016. Disaster return home support
map. http://mapple-on.jp/products/kitaku.
Nishiyama, H., Ito, M., Kato, N., 2014.
Relay-by-Smartphone: Realizing Multi-Hop
Device-to-Device Communications. IEEE
Communications Magazine, vol. 52, no. 4, pp. 56-65,
Apr.
Goto, H., Ohta, A., Matsuzawa, T., Takimoto, M.,
Kambayashi, Y., and Takeda, M., 2016. A Guidance
System for Wide-area Complex Disaster Evacuation
Based on Ant Colony Optimization. Proceeding of the
Eighth International Conference on Agents and
Artificial Intelligence, pp.262-268.
Kambayashi, Y., Nishiyama, T., Matsuzawa, T., and
Takimoto, M., 2016. An Implementation of an Ad hoc
Mobile Multi-Agent System for a Safety Information,
Proceeding of the Thirty-sixth International
Conference on Information Systems Architecture and
Technology, AICS vol. 430, pp.201-213.
Ushiyama, M., and Yokomaku, S., 2012. Estimation of
situation in Rikuzentakata city just before tsunami
attack based on time stamp data. Japan Society for
natural disaster science, Vol. 31, No. 1, pp. 47-58.
Asakura, K., Fukaya, K., and Watanabe, T., 2013.
Construction of navigational maps for evacuees in
disaster areas based on ant colony systems.
International Journal of Knowledge and Web
Intelligence, Vol. 4, pp. 300-313.
Dijkstra, E. W., 1959. A Note on Two Problems in
Connexion with Graphs. Numerische Mathematik,
vol.1, pp. 269-271.
Dorigo, M., Maniezzo, V., Colorni, A., 1996. Ant system:
Optimization by a colony of cooperating agents, IEEE
Transaction on System, Vol. 26, No. 1, pp.29-41.
Multi-Agent Approach for Evacuation Support System
227
