
Outsourcing Scheme of ABE Encryption Secure against Malicious
Adversary
Go Ohtake
1
, Reihaneh Safavi-Naini
2
and Liang Feng Zhang
3
1
Science & Technology Research Laboratories, Japan Broadcasting Corporation, Tokyo, Japan
2
Department of Computer Science, University of Calgary, Calgary, Canada
3
School of Information Science and Technology, ShanghaiTech University, Shanghai, China
ohtake.g-fw@nhk.or.jp, rei@ucalgary.ca, zhanglf@shanghaitech.edu.cn
Keywords:
Outsourcing Scheme, Attribute-based Encryption, Malicious Adversary, Random Oracle Model.
Abstract:
Integrated broadcast-broadband services allow viewers to simultaneously receive broadcast content over the
airwaves and additional information related to the content over the Internet. This integration provides oppor-
tunities for new services to be tailored and offered to individual viewers. Viewing histories provide a rich
variety of data for service providers to learn the preferences of individual viewers and fine-tune their offerings.
Each person’s viewing history, however, is privacy-sensitive data and may reveal information that the viewer
does not want revealed. In this paper, we propose a system that allows viewers to specify a policy that they
would like to be applied to their viewing history, when shared with service providers, by using attribute-based
encryption (ABE). A ciphertext is associated with a policy, and it can be decrypted only by service providers
who conform to the policy. To reduce the computations of the user terminal, we develop a system with prov-
able security that allows the encryption to be outsourced to a cloud server, without the need to trust the cloud
server. Although our solution is described for integrated broadcast-broadband services, the architecture and
results could also be used for sharing viewing histories of services such as Netflix. We implemented our
scheme and showed that it significantly reduces the computation cost of a user terminal.
1 INTRODUCTION
1.1 Background
Integrated broadcast-broadband services (Baba et al.,
2012; Ohmata et al., 2013; Ohmata et al., 2015;
NHK, ; ETSI, ; BBC, ; KBS, ) allow viewers to
view content through broadcast and, simultaneously,
additional content through the Internet. The addi-
tional content can be used to personalize broadcasts
and provides opportunities for electronic commerce.
For example, in a link navigation service (Ohmata
et al., 2015), a service provider provides program-
related keywords for goods, locations, and shops as
the television program progresses. These keywords
are linked to services that the viewers can access by
clicking on the word shown on the screen on their
mobile devices. To make the personalization of the
broadcast and services effective, viewers must share
their viewing preferences with the service provider.
Viewing histories are a rich source of data for ser-
vice providers to learn about viewers’ interests. Their
data, however, could reveal sensitive personal infor-
mation about a viewer and so must be handled with
care. Ideally, viewers want to share their viewing his-
tories with service providers that pass certain crite-
ria, including being trustworthy or having a high rat-
ing based on customer reviews. This, of course, can
be achieved by encrypting a history using the pub-
lic keys of the desired service providers, or by es-
tablishing a secure connection using a protocol such
as TLS with those providers, and sending the data to
them one-by-one. Although these solutions allow the
viewer to fully control sharing of their viewing his-
tory, they have two major drawbacks. Firstly, they are
not scalable: they are computationally expensive and
require the viewer to encrypt the data, or establish a
secure connection, for each provider independently,
and this must be done at regular intervals in order to
provide an up-to-date viewing history. Secondly, their
use is limited to the service providers that the viewer
knows, and unless the viewer does not make an effort
to identify new service providers, the pool of services
that will receive the data will be limited, meaning
that the viewer may never learn about new services
that emerge. An ideal solution for sharing viewing
Ohtake, G., Safavi-Naini, R. and Zhang, L.
Outsourcing Scheme of ABE Encryption Secure against Malicious Adversary.
DOI: 10.5220/0006129600710082
In Proceedings of the 3rd International Conference on Information Systems Security and Privacy (ICISSP 2017), pages 71-82
ISBN: 978-989-758-209-7
Copyright
c
2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
71

history would allow the viewer to produce a single
encrypted copy of their viewing history, and specify
an access policy that will be enforced on the service
providers. It is also important to ensure that the com-
putation of the user terminal is minimized. This is im-
portant not only because user terminals, such as tele-
vision sets, cannot be expected to be equipped with
powerful cryptoprocessors, but also because the com-
putation must be performed at regular intervalsas new
viewing histories are generated. The terminal compu-
tations can be reduced by outsourcing them to cloud
servers. This, however, raises the issue of trust. Out-
sourcing computations on the original data would al-
low a cloud server to learn the viewing history. More-
over, one must ensure that the requested computation
has been performed correctly.
1.2 Our Contributions
In this paper, we propose a secure outsourcing system
of attribute-based encryption (ABE) that (i) allows
sharing of viewer’s data according to a viewer-defined
policy, (ii) reduces the viewer-side computation to a
single encryption using ElGamal encryption, and (iii)
ensures privacy of content and correctness of compu-
tation against a malicious cloud server. We use ABE
to enable viewers to encrypt their own viewing history
and specify the attributes of the service providers who
can access the data. ABE provides an elegant means
of expressing and enforcing access control policies.
In a ciphertext-policy ABE, a service provider has a
set of attributes that is verified by a trusted author-
ity who issues the corresponding private key to them.
A ciphertext can be generated by any viewer using
the public key of the system. The ciphertext is at-
tached to a policy that is expressed by a Boolean for-
mula. A service provider whose attribute set satisfies
this policy can use the decryption algorithm and their
private key to recover the data. Encryption in ABE,
however, is costly, and the computation cost grows
linearly with the number of attributes. We design an
outsourcingscheme that reduces the viewer-sidecom-
putation to a single ElGamal encryption. This encryp-
tion protects the viewer’s data against any attack from
a cloud server. This ciphertext is then converted by
the cloud server into an ABE ciphertext according to
a policy that is provided by the viewer. We do not as-
sume a trusted cloud server and design the outsourc-
ing system that protects viewers against its potential
misbehavior. We consider colluding attacks where the
cloud server and service providers whose attributes do
not satisfy the viewer’s policy would like to make the
viewing history readable to themselves.
We consider five different entities: a registration
authority (RA), a key generation center (KGC), view-
ers, a cloud server, and service providers (See Fig-
ure 1). Viewers are registered with the RA and re-
ceive an ID (identification) and credentials that they
can use when contacting the cloud server. This is to
ensure that the data provided to the cloud server are
valid and the system is not abused. Service providers
are registered with the KGC and receive private keys
associated with their verified attributes. The cloud
server is not assumed to be honest. Each viewer’s
data must be protected for the sake of privacy. Also,
the computation delegated to the cloud server must
be verifiable. These requirements are captured in se-
curity and unforgeability, ensuring that (i) the view-
ers’ personal information remains private in the sys-
tem and only accessible to the service providers who
have the required attributes, and (ii) the computation
of the cloud server is verifiable by the viewers and the
service providers. We use game-based definitions to
model these requirements and devise an outsourcing
scheme of ABE encryption that ensures these proper-
ties. We give formal proofs of security for these prop-
erties, assuming access to a random oracle by the par-
ticipants. Our scheme is based on the “large universe”
ABE scheme of Waters (See Appendix A in (Waters,
2008)) that supports an unlimited number of attributes
and has constant-size public parameters for any pol-
icy that can be described by a Linear Secret Sharing
Scheme (LSSS) matrix. We implement the encryp-
tion algorithms of our scheme and the ABE scheme of
Waters (Waters, 2008) on a user terminal and measure
the processing times. The experimental results show
that our scheme reduces the encryption cost of a user
terminal to about one third that of the ABE scheme of
Waters (Waters, 2008), without assuming a trustwor-
thy server.
Outsourcing Encryption. The encryption algo-
rithm of an ABE scheme has a substantially higher
computation cost than that of conventional public key
encryption schemes such as RSA or ElGamal en-
cryption. Therefore, a user terminal with a low-
performance CPU, such as a television set or a mobile
device, must bear a comparatively large computation
cost when encrypting a viewing history. This prob-
lem has motivated a number of recent studies on out-
sourcing schemes for the computation (Hohenberger
and Waters, 2014; Li et al., 2012; Zhou and Huang,
2011). In all these schemes, a large part of encryption
process is outsourced to a cloud server. The schemes,
however, assume that the cloud server is either hon-
est and, while following the protocol, there is no col-
lusion with other entities, or it is honest-but-curious
and, while following the protocol, may collude with
ICISSP 2017 - 3rd International Conference on Information Systems Security and Privacy
72

other entities to learn the private information of the
users. Our work is the first to consider security against
a malicious cloud server who does not follow the pro-
tocol and may collude with other entities. This is a re-
alistic model for outsourcing the viewing history en-
cryption when viewers cannot rely on a trustworthy
cloud server.
Towards Attribute-based Sharing of Viewing His-
tories. Outsourcing the ABE ciphertext computa-
tion to a cloud server is an attractive solution in
many application scenarios. Our scenario considers
the resource-limited clients of integrated broadcast-
broadband services, and content distribution services
such as Netflix or Spotify have similar requirements.
Here, the users’ viewing histories are known by the
service provider: in fact, they would be the basis of
any recommendation system run by it. Moreover,
users may be willing to share this data with third-party
service providers for the purpose of receiving differ-
ent services. For example, having a lot of movies for
children in one’s viewing history would suggest the
viewer has an interest in toys, and in such case, rel-
evant information can be provided directly by a third
party or through the service provider. This sharing
of information must meet the terms and conditions
specified by the user that are encoded as a set of at-
tributes that the third party must satisfy. The incentive
for the service provider (e.g. Netflix) to outsource the
encryption is the number of subscribers and the re-
quired update frequency of the viewing history. Once
the service provider receives the user’s consent and
conditions, it uses the system proposed in this paper
to minimize their computation.
1.3 Related Work
Sahai and Waters (Sahai and Waters, 2005) proposed
the first ABE scheme as an extension of identity-
based encryption (IBE). ABE schemes are attractive
because they allow access control of content in real-
istic situations. ABE schemes can be classified into
(i) key-policy ABE (KP-ABE) (e.g. (Goyal et al.,
2006; Ostrovsky et al., 2007; Rouselakis and Waters,
2013; Attrapadung, 2014; Gay et al., 2015; Attra-
padung et al., 2016)), and (ii) ciphertext-policy ABE
(CP-ABE) (e.g. (Bethencourt et al., 2007; Cheung
and Newport, 2007; Katz et al., 2008; Nishide et al.,
2008; Waters, 2008; Emura et al., 2009; Lewko et al.,
2010; Okamoto and Takashima, 2010; Ohtake et al.,
2013; Rouselakis and Waters, 2013; Attrapadung and
Yamada, 2015; Attrapadung et al., 2016)). In KP-
ABE, a ciphertext is associated with a set of attributes,
and a private key is associated with a policy. In CP-
ABE, a private key is associated with a set of at-
tributes, and a ciphertext is associated with a policy.
A ciphertext can be decrypted by a user whose at-
tributes satisfy the policy that is attached to the ci-
phertext. In this paper, we consider CP-ABE. Out-
sourcing of ABE was first considered in (Green et al.,
2011), which proposed ABE decryption outsourcing
with the goal of minimizing the users’ decryption
cost and assumed honest-but-curious cloud servers.
In (Zhou and Huang, 2011), an outsourcing scheme
for ABE encryption and decryption was proposed,
also assuming honest-but-curious cloud servers. An
outsourcing scheme for ABE encryption based on
the scheme of (Zhou and Huang, 2011) and using a
MapReduce cloud was proposed in (Li et al., 2012).
In this scheme, distributed processing is performed
by a number of cloud servers wherein at least one of
them is assumed to be honest. The scheme in (Ho-
henberger and Waters, 2014) is an online/offline ABE
scheme in which the encryption algorithm is divided
into two parts: online encryption, which is performed
by a user terminal, and offline encryption, which is
performed by an honest cloud server. An outsourc-
ing scheme for ABE key generation and decryption in
which the outsourced computation results are check-
able was proposed in (Li et al., 2014); this scheme as-
sumes honest-but-curious cloud servers. To the best
of our knowledge, ours is the first outsourcing scheme
of ABE encryption for when the cloud server is poten-
tially malicious.
2 PRELIMINARIES
Secret sharing schemes are proposed independently
by (Shamir, 1979) and (Blakley,1979). A more recent
survey of the area can be found in (Beimel, 1996).
2.1 Access Structures
Definition 1 (Access Structure). Let P =
{P
1
,P
2
,...,P
n
} be a set of parties. A collection of
subsets of P , A ⊆ 2
{P
1
,P
2
,...,P
n
}
, is a monotone access
structure if ∀B,C: if B ∈ A and B ⊆ C then C ∈ A. A
set A in A is called an authorized set, and a set A not
in A is called an unauthorized set.
In ABE, the role of the parties is taken by the at-
tributes: the private key is a secret that is divided into
shares, with each share assigned to an attribute. The
access structure A includes the subset of attributes
that can reconstruct the key and decrypt the cipher-
text. We only consider monotone access structures.
Outsourcing Scheme of ABE Encryption Secure against Malicious Adversary
73

2.2 Linear Secret Sharing Schemes
Definition 2 (Linear Secret Sharing Schemes
(LSSS)). A secret-sharing scheme Π over a set of par-
ties P is called linear (over Z
p
) if,
1. The shares of the parties form a vector over Z
p
.
2. There exists a matrix M with ℓ rows and n columns
called the share-generating matrix for Π and a
function ρ which maps each row of the matrix to
an associated party. That is, for i = 1, ...,ℓ, the
value ρ(i) is the party associated with row i. Sup-
pose we have a column vector ~v = (s, r
2
,..., r
n
),
where s ∈ Z
p
is the secret to be shared, and
r
2
,..., r
n
∈ Z
p
are randomly chosen, then M~v is
the vector of ℓ shares of the secret s according to
Π. The share (M~v)
i
belongs to party ρ(i).
It is shown in (Beimel, 1996) that every LSSS
having the above definition enjoys the linear recon-
struction property, defined as follows: Suppose that
Π is a LSSS for the access structure A. Let S ∈ A
be any authorized set, and let I ⊂ {1, 2,...,ℓ} be de-
fined as I = {i : ρ(i) ∈ S}. Then, there exist constants
{w
i
∈ Z
p
}
i∈I
such that, if {λ
i
} are valid shares of any
secret s according to Π, then
∑
i∈I
w
i
λ
i
= s. Further-
more, it is shown in (Beimel, 1996) that these con-
stants {w
i
} can be found in time polynomial in the
size of the share-generating matrix M. Like any se-
cret sharing scheme, it has the property that for any
unauthorized set S /∈ A, the secret s should be infor-
mation theoretically hidden from the parties in S.
2.3 Bilinear Maps
Let G and G
T
be two multiplicative cyclic groups
of prime order p. Let g be a generator of G and
e : G × G → G
T
be a bilinear map that has the fol-
lowing properties:
1. Bilinearity: e(u
a
,v
b
) = e(u, v)
ab
for all u,v ∈ G
and a,b ∈ Z
p
.
2. Non-degeneracy: e(g,g) 6= 1.
We say that G is a bilinear group if the group oper-
ation in G and the bilinear map e : G × G → G
T
are
both efficiently computable. Notice that the map e is
symmetric, since e(g
a
,g
b
) = e(g,g)
ab
= e(g
b
,g
a
).
2.4 Decisional Parallel Bilinear
Diffie-Hellman Exponent
Assumption
The decisional q-parallel Bilinear Diffie-Hellman Ex-
ponent (BDHE) problem (Waters, 2008) is defined as
follows. Choose a group G of prime order p accord-
ing to the security parameter. Let a,s, b
1
,..., b
q
∈ Z
p
be chosen at random and g be a generator of G. If an
adversary is given~y =
g,g
s
,g
a
,..., g
(a
q
)
,g
(a
q+2
)
,..., g
(a
2q
)
∀
1≤ j≤q
g
s·b
j
,g
a/b
j
,..., g
(a
q
/b
j
)
,g
(a
q+2
/b
j
)
,..., g
(a
2q
/b
j
)
∀
1≤ j,k≤q,k6= j
g
a·s·b
k
/b
j
,..., g
(a
q
·s·b
k
/b
j
)
,
it must remain hard to distinguish e(g,g)
a
q+1
s
∈ G
T
from a random element in G
T
.
An algorithm B that outputs z ∈ {0,1}
has advantage ε in solving the deci-
sional q-parallel BDHE problem in G if
Pr
h
B(~y,T = e(g,g)
a
q+1
s
) = 0
i
− Pr[B(~y,T = R) = 0]
≥ ε.
Definition 3. We say that the decisional q-parallel
BDHE assumption holds if no polynomial time algo-
rithm has a non-negligible advantage in solving the
decisional q-parallel BDHE problem.
3 DEFINITIONS
3.1 Model
The model of outsourcing ABE encryption is defined
as follows.
Definition 4. The outsourcing scheme of ABE encryp-
tion is a tuple consisting of the following algorithms:
Setup(λ) → (PK, MSK). This algorithm takes as in-
put a security parameter λ. It outputs the public
parameter PK and the master key MSK.
KeyGen(PK,MSK,S) → SK. This algorithm takes
as input PK, MSK, and a set of attributes S. It
outputs a private key SK associated with S.
Encrypt
u
(PK, A, M ) → (CT
′
, π). This algorithm
takes as input PK, an access structure A, and a
message M . It outputs an intermediate ciphertext
CT
′
and a proof π.
Encrypt
c
(PK, A, CT
′
) → CT. This algorithm takes
as input PK, A, and CT
′
. It outputs a ciphertext
CT.
Decrypt(CT,π,SK,PK) → M / ⊥. This algorithm
takes as input CT, π, SK, and PK. It outputs M if
π is a valid proof of CT and S satisfies A. Other-
wise, it outputs the error message ⊥.
Figure 1 shows a model of an outsourcing
scheme of ABE encryption for integrated broadcast-
broadband services. There are five different entities:
ICISSP 2017 - 3rd International Conference on Information Systems Security and Privacy
74
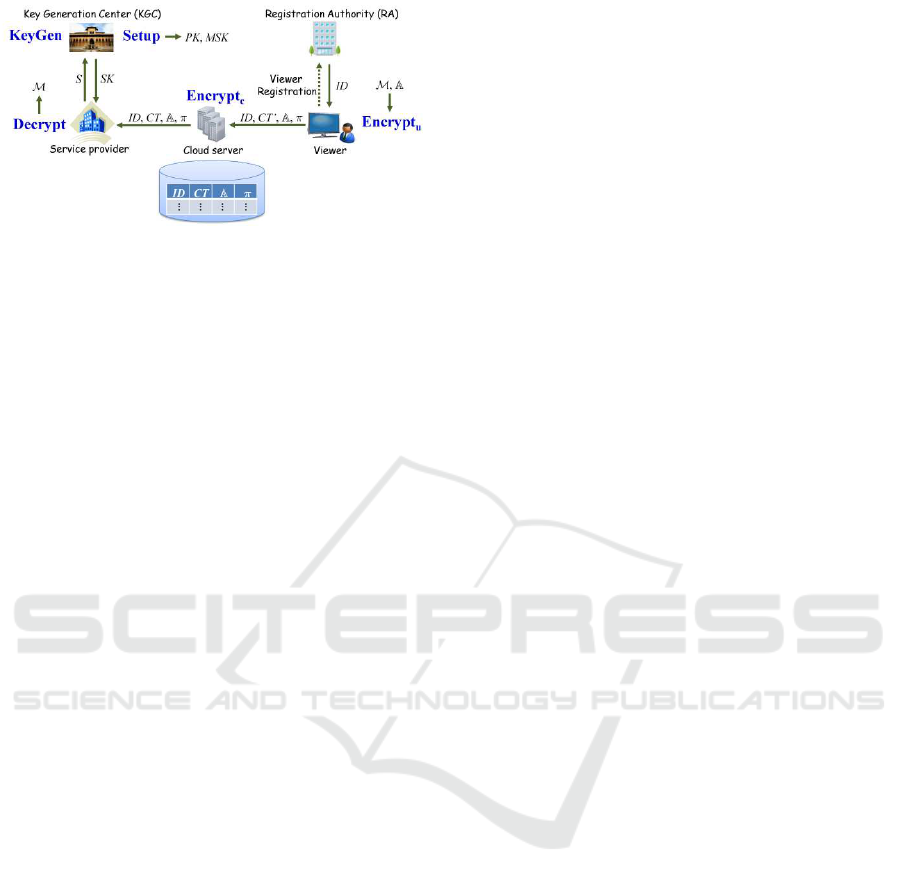
Figure 1: Model outsourcing scheme of ABE encryption for
integrated broadcast-broadband service.
a registration authority (RA), a key generation center
(KGC), viewers, a cloud server, and service providers.
The RA registers viewers of broadcast services. A
registered viewer is given identity information ID that
allows a third party to verify their identity, possibly
through interacting with the RA. The KGC sets up the
access control system by running the Setup and Key-
Gen algorithms for the ABE system, and after verify-
ing the service providers’ attributes S, provides them
with private keys SK associated with S. A registered
viewer uses Encrypt
u
to encrypt their viewing his-
tory M that will be an ElGamal ciphertext sent to the
cloud server. This first level of encryption ensures the
privacy of the viewer information in the cloud server.
The viewer provides to the cloud server a policy that
they would like to enforce. The cloud server uses
Encrypt
c
to convert the received ElGamal ciphertext
into an ABE ciphertext that enforces the viewer’s pol-
icy for the service providers, making it accessible
to all service providers who possess the required at-
tributes. Service providers who have received their
private keys of the ABE system and whose attributes
satisfy the viewer’s policy can use Decrypt to access
the viewing history of the viewer.
In the following, we focus on the access control
part of the system and assume that the cloud server
verifies the identity of the viewers who provide their
viewing history, by using ID and an identity service
that uses the RA registration process. This ensures
that the viewing history is provided by valid view-
ers. Otherwise, viewing histories may be provided
by fake viewers, resulting in unreliable data for ser-
vice providers (resulting in, e.g., incorrect viewing
statistics). Note that this does not pose a threat to
the privacy of the viewer, as their viewing history is
stored in encrypted form. The system works as fol-
lows: First, a viewer creates an intermediate cipher-
text CT
′
of M with an access structure A to specify
a condition for a service provider who can decrypt
the viewing history. The viewer transmits ID, CT
′
,
A, and a proof π to the cloud server. The cloud server
transformsCT
′
into a ciphertextCT, and then it stores
(ID,CT, A,π) for each viewer in a public database. A
service provider downloads the tuple of (ID,CT, A,π)
for a specified viewer and verifies its correctness by
using π. Note that the viewer can verify the correct-
ness of (ID,CT,A,π) stored in the public database.
The service provider can decrypt CT and obtain a
viewing history M iff the tuple is correct and the ser-
vice provider has a set of attributes S satisfying A.
3.2 Security Model
The following is our trust assumptions and secu-
rity requirements for the outsourcing ABE encryp-
tion system. We assume that the viewers are honest
and follow the protocol. (We exclude malicious view-
ers by using identity verification at the cloud server.)
The cloud server is not trusted and may deviate from
the protocol. This assumption accounts for the pos-
sibility that a cloud server may collude with service
providers who do not satisfy the viewer’s policy and
enable them to bypass the viewer’s access policy. Ser-
vice providers follow the protocol, but may collude
together, and possibly with the cloud server, to by-
pass the viewer’s access policy and access his or her
viewing history. Our basic security requirements are
as follows:
1. A collusion of service providers,who individually
do not satisfy the access policy of a viewer, and a
cloud server cannot obtain any information about
the viewing history of the viewer.
2. A cloud server cannot modify a ciphertext that is
decrypted into a differentviewing history from the
original one.
Note that the cloud server in Requirement 2 would
have no incentive for making an attack. In this case,
the attack would interfere with a service, though it
might be performed by the cloud server.
Fulfilling the above requirements would realize
a secure integrated broadcast-broadband service. In
Figure 1, a viewer transmits an intermediate cipher-
text CT
′
to the cloud server for outsourcing part of
the encryption process. CT
′
includes the viewing his-
tory of the viewer, so the cloud server might try to get
it (Requirement 1). Then, a cloud server convertsCT
′
into a ciphertext CT, but it might be “incorrect” (Re-
quirement 2). Also, as is the case with conventional
ABE schemes, the viewing history might be obtained
from CT as a result of the service providers colluding
(Requirement 1). In light of the above requirements,
we define two kinds of security for an outsourcing
scheme of ABE encryption: security and unforgeabil-
ity.
Let Π = (Setup, KeyGen, Encrypt
u
, Encrypt
c
,
Decrypt) be an outsourcing scheme of ABE encryp-
Outsourcing Scheme of ABE Encryption Secure against Malicious Adversary
75

tion. The definition of security includes attacks made
by a cloud server that colludes with service providers.
The goal of the attacker is to learn the plaintext that
they are not supposed to learn. Formally, we use the
following experiment to define security against an ad-
versary A.
Outsourcing of ABE Encryption Experiment
O-ABE-Exp
ind
A,Π
(λ):
Init. The adversary gives a challenge access struc-
ture A
∗
to the challenger.
Setup. The challenger runs the Setup algorithm and
gives the public parameter PK to the adversary.
Phase 1. The challenger initializes an empty table
T, an empty set D, and an integer counter j = 0.
Proceeding adaptively, the adversary can repeat-
edly make any of the following queries:
• Create(S): The challenger sets j := j + 1. It
runs the KeyGen algorithm on S to obtain the
private key SK and stores in table T the entry
(j, S, SK). Then it returns SK to the adversary.
• Corrupt(i): If the i
th
entry in table T exists, the
challenger obtains the entry (i, S, SK) and sets
D := D∪ {S}. Then it returns SK to the adver-
sary. If no such entry exists, it returns ⊥.
Challenge. The adversary submits two messages
M
0
and M
1
. The challenger flips a random coin
b ∈ {0,1}. It runs the algorithm Encrypt
u
(PK,
A
∗
, M
b
) to obtain (CT
′
, π
∗
). The challenger re-
turns (CT
′
, π
∗
) to the adversary.
Phase 2. Phase 1 is repeated with the restrictions
that the adversary cannot trivially obtain a private
key for the challenge ciphertext (CT
∗
, π
∗
) derived
from (CT
′
, π
∗
). That is, the adversary cannot
make a Corrupt query that would result in a set
of attributes S such that f(S,A
∗
) = 1 being added
to D.
Guess. The adversary outputs a guess b
′
of b. The
output of the experiment is 1 iff b = b
′
.
Definition 5 (Security). An outsourcing scheme of
ABE encryption Π is secure if for all probabilistic
polynomial-time adversaries A , there exists a negli-
gible function negl such that:
Pr[O−ABE−Exp
ind
A,Π
(λ) = 1] ≤
1
2
+ negl(λ).
The above definition includes an attack in which
the cloud server receives an intermediate-ciphertext
(CT
′
, π) from a viewer and creates a ciphertext (CT
∗
,
π
∗
), where π
∗
6= π and CT
∗
can be decrypted into the
original message by colluding with service providers
whose attributes do not satisfy the policy.
Remark 1. The above security implies the security of
conventional ABE schemes. This is because an adver-
sary can obtain a challenge ciphertext CT
∗
from CT
′
in the Challenge phase of the security game by using
the Encrypt
c
algorithm.
Next, we define the unforgeability of our outsourc-
ing scheme. This security definition includes attacks
made by a cloud server. The goal of the attacker is to
modify a ciphertext so that it is decrypted to a differ-
ent plaintext from the original one. We use the follow-
ing experiment to define unforgeability with respect
to an adversary A.
Outsourcing of ABE Encryption Experiment
O-ABE-Exp
unf
A,Π
(λ):
Init. The adversary gives a challenge access struc-
ture A
∗
to the challenger.
Setup. The challenger runs the Setup algorithm and
gives the public parameter PK to the adversary.
Query. The challenger initializes an empty table T,
an empty set D, and an integer counter j = 0. Pro-
ceeding adaptively, the adversary can repeatedly
make any of the following queries:
• Create(S): The challenger sets j := j + 1. It
runs the KeyGen algorithm on S to obtain the
private key SK and stores in table T the entry
(j, S, SK). Then it returns SK to the adversary.
• Corrupt(i): If the i
th
entry exists in table T, the
challenger obtains the entry (i, S, SK) and sets
D := D ∪ {S}. It then returns SK to the adver-
sary. If no such entry exists, it returns ⊥.
Challenge. The adversary submits a challenge mes-
sage M
∗
. The challenger runs the algorithm
Encrypt
u
(PK, A
∗
, M
∗
) to obtain (CT
′
, π
∗
). The
challenger returns (CT
′
, π
∗
) to the adversary.
Output. The adversary outputs (CT
∗
, π
∗
). The out-
put of the experiment is 1 if Decrypt(CT
∗
, π
∗
, SK,
PK) /∈ {⊥, M
∗
}.
Definition 6 (Unforgeability). An outsourcing
scheme of ABE encryption Π is unforgeable if for all
probabilistic polynomial-time adversaries A, there
exists a negligible function negl such that:
Pr[O−ABE−Exp
unf
A,Π
(λ) = 1] ≤ negl(λ).
Remark 2. In the Output phase, we assume that the
adversary outputs a proof π
∗
which is the same as
the proof received in the Challenge phase. This is
because the adversary can easily create (CT
∗
, π
∗∗
)
ICISSP 2017 - 3rd International Conference on Information Systems Security and Privacy
76

satisfying π
∗∗
6= π
∗
and Decrypt(CT
∗
, π
∗∗
, SK, PK)
/∈ {⊥, M
∗
} by choosing M
∗∗
6= M
∗
and running the
Encrypt
u
and Encrypt
c
algorithms.
4 PROPOSED SCHEME
We propose an outsourcing scheme for Waters’ “large
universe” ABE scheme (See Appendix A in (Waters,
2008)), where the number of attributes is unlimited,
while the public parameter size is constant. Waters’
scheme provides flexibility for the service provider to
add new attributes and efficiency for storage of the
public key. A policy is expressed as a monotonic
Boolean formula that can be mapped into the share-
generating matrix of a LSSS that is used in the ABE
system.
4.1 Outsourcing Scheme of ABE
Encryption
As described in Section 3.2, we assume that the cloud
server is malicious and may not follow the protocol.
Our scheme masks the secret in a column vector of a
LSSS using random numbers. This prevents the cloud
server from learning about the secret from the masked
vector, given the intermediate ciphertext. It also uses
the hash of randomness technique to verify the cor-
rectness of the ciphertext.
Our scheme has the following five algorithms:
Setup(). The setup algorithm chooses a bilinear
group G of prime order p, a bilinear map e : G ×
G → G
T
, a generator g of G , and hash functions
H : {0,1}
∗
→ G, H
′
: { 0,1}
∗
× G
T
× G
T
× {0, 1}
∗
→
{0,1}
∗
and H
′′
: {0,1}
∗
→ {0,1}
∗
. In addition, it
chooses random numbers α,a ∈ Z
p
. The algorithm
outputs the public parameter,
PK = {g,e(g,g)
α
,g
a
,H(·),H
′
(·,·, ·,·), H
′′
(·)},
and the master key MSK = g
α
.
KeyGen(MSK, S). The key generation algorithm
takes as input MSK and a set of attributes S. The algo-
rithm first chooses a random value t ∈ Z
p
. It creates
K = g
α
g
at
, L = g
t
, K
x
= H(x)
t
(∀x ∈ S).
The algorithm outputs a private key,
SK = {K,L,K
x
(∀x ∈ S)}.
Encrypt
u
(PK,ID, (M,ρ),M ). The algorithm takes
as input PK, a viewer’s identity ID, a LSSS access
structure (M, ρ), and a message M . We assume that
each element of the access matrix M is either 0 or 1.
The function ρ associates rows of M with attributes.
In this construction, we limit ρ to be an injective func-
tion; i.e., an attribute is associated with at most one
row of M.
Let M be an ℓ × n access matrix. The algorithm
randomly chooses s, y
2
, ..., y
n
, β
1
, β
2
, ..., β
n
∈ Z
p
and
sets a column vector~v = (s+β
1
,y
2
+β
2
,..., y
n
+β
n
) ∈
Z
n
p
. It then calculates
C = M · e(g,g)
αs
, C
′
= g
s
,
π = H
′
(ID,C, e(g,g)
αs
,H
′′
(pos
M
)).
Here, po s
M
is a string showing all of the elements in
the access matrix M that are 1. For example, if the
matrix M is
M =
0 1
1 1
1 0
,
then pos
M
is as follows:
p os
M
= {(1,2),(2,1),(2, 2),(3,1)}.
For 1 ≤ i ≤ ℓ, let J
i
be a set J
i
= { j : M
ij
= 1(1 ≤ j ≤
n)}. The algorithm calculates
E
i
= g
a
∑
j∈J
i
β
j
and outputs an intermediate ciphertext,
CT
′
= {C,C
′
,(E
i
)
1≤i≤ℓ
,~v,(M,ρ)},
and a proof π.
The algorithm takes as input PK and CT
′
. For
1 ≤ i ≤ ℓ, the algorithm calculates λ
i
= M
i
~v, where
M
i
is the row vector corresponding to the ith row
of M. The algorithm also chooses random numbers
r
1
,..., r
ℓ
∈ Z
p
, and calculates
C
i
=
g
aλ
i
H(ρ(i))
−r
i
E
i
, D
i
= g
r
i
(1 ≤ i ≤ ℓ)
and outputs a ciphertext,
CT = {C,C
′
,(C
i
,D
i
)
1≤i≤ℓ
,(M,ρ)}.
Decrypt(CT,π,SK,PK, ID). The decryption algo-
rithm takes as input CT, π, SK, PK, and ID. Sup-
pose that S satisfies the access structure, and let I ⊂
{1,2,..., ℓ} be defined as I = {i : ρ(i) ∈ S}. Moreover,
let {w
i
∈ Z
p
}
i∈I
be a set of constants such that if {λ
i
}
are valid shares of any secret s according to M, then
∑
i∈I
w
i
λ
i
= s. The algorithm computes
e(C
′
,K)/(
∏
i∈I
(e(C
i
,L)e(D
i
,K
ρ(i)
))
w
i
) = e(g,g)
αs
.
If π 6= H
′
(ID,C, e(g,g)
αs
,H
′′
(pos
M
)), the algorithm
outputs ⊥. This will happen in two cases: (1) CT was
Outsourcing Scheme of ABE Encryption Secure against Malicious Adversary
77

modified; (2) SK does not satisfy the policy in CT.
Hence, ⊥ will appear whenever (1) or (2) happens.
Otherwise, it outputs the message,
M = C/e(g,g)
αs
.
Remark 3 . Our scheme is secure even if the
cloud server is malicious because (i) the vector ~v =
(s,y
2
,..., y
n
) that is used to create the shares of s is
masked from an adversary by using random numbers
(β
1
,β
2
,..., β
n
), and (ii) to verify the correctness of
the Encrypt
c
algorithm, a proof π is added to the ci-
phertext. The formal security proof is shown in Sec-
tion 4.2.
Remark 4. The proof π is like a message authenti-
cation code (MAC), since it uses a hash function H
′
and a shared key e(g,g)
αs
. A viewer can verify the
correctness of a tuple of (ID, CT, A, π) stored in the
cloud server if the viewer keeps the random number s
that is generated in the Encrypt
u
algorithm. Namely,
even if a malicious cloud server creates another tuple
of (ID, CT
∗
, A
∗
, π
∗
) from scratch and stores it in a
public database, the viewer can detect the attack (al-
though this requires the viewer to check the status of
the database periodically).
Another solution to prevent the above attack is
using a digital signature scheme, but it might put a
heavy load on a user terminal equipped with only
a low-performance CPU. That’s why we use a hash
function to verify the correctness of the ciphertext.
Remark 5. The hash function H
′
with four in-
put values can be implemented by a secure hash
function, and using the concatenation of all inputs:
H
′
(ID||C||e(g,g)
αs
||H
′′
(pos
M
)).
4.2 Security Proof
Here, we prove that our scheme has the security and
unforgeability properties defined in Section 3.2. The
proof of security are based on (Waters, 2008).
Theorem 1. Our scheme is selectively secure un-
der the decisional q-parallel BDHE assumption in the
random oracle model.
Proof. Suppose we have an adversary A with non-
negligible advantage ε = Adv
A
in the selective secu-
rity game against our construction. Moreover, sup-
pose it chooses a challenge matrix M
∗
where both di-
mensions are at most q. Below, we show how to build
a simulator B that solves the decisional q-parallel
BDHE problem.
Init. The simulator B takes as input a q-parallel
BDHE challenge (~y,T). B runs the adversary
A, which gives B the challenge access structure
(M
∗
,ρ
∗
). Here, M
∗
is ℓ
∗
× n
∗
matrix and ℓ
∗
,n
∗
≤ q.
Setup. B chooses a random value α
′
∈ Z
p
and
implicitly sets α = α
′
+ a
q+1
by letting e(g,g)
α
=
e(g
a
,g
a
q
)e(g,g)
α
′
. B sends hg,e(g,g)
α
,g
a
i to A.
Phase 1. B initializes empty tables T
1
, T
2
, T
3
, T
4
,
an empty set D, and an integer j = 0. It answers the
adversary’s queries as follows:
• Random Oracle Hash H(x): If there is an entry
(x,h) in T
1
, return h. Otherwise, begin by choos-
ing a random value z
x
. If there is some index i
such that ρ
∗
(i) = x, calculate
h = g
z
x
g
aM
∗
i,1
/b
i
· g
a
2
M
∗
i,2
/b
i
·· ·g
a
n
∗
M
∗
i,n
∗
/b
i
.
Record (x,h) in T
1
and return h. Note that if there
is no index i such that ρ
∗
(i) = x, then H(x) = g
z
x
.
Note that the responses from the oracle are dis-
tributed randomly because of the value of g
z
x
.
• Random Oracle Hash H
′
(ID,
¯
C,
¯
K,
¯
V): If there is
an entry (ID,
¯
C,
¯
K,
¯
V,h
′
) in T
2
, return h
′
. Other-
wise, choose a random value h
′
∈ {0,1}
∗
, record
(ID,
¯
C,
¯
K,
¯
V, h
′
) in T
2
and return h
′
.
• Random Oracle Hash H
′′
(P): If there is an entry
(P,h
′′
) in T
3
, return h
′′
. Otherwise, choose a ran-
dom value h
′′
∈ {0,1}
∗
, record (P,h
′′
) in T
3
and
return h
′′
.
• Create(S): Set j := j+1. Suppose S does not sat-
isfy (M
∗
, ρ
∗
). Choose a random value r ∈ Z
p
.
Find a column vector ~w = (w
1
,..., w
n
∗
) ∈ Z
n
∗
p
such
that w
1
= −1 and M
∗
i
~w = 0 for all i where ρ
∗
(i) ∈
S. Set
L = g
r
n
∗
∏
i=1
(g
a
q+1−i
)
w
i
= g
t
by implicitly defining t = r + w
1
a
q
+ w
2
a
q−1
+
·· · + w
n
∗
a
q+1−n
∗
. Compute K as
K = g
α
′
g
ar
n
∗
∏
i=2
(g
a
q+2−i
)
w
i
.
Next, we calculate K
x
(∀x ∈ S). If x ∈ S for which
there is no i such that ρ
∗
(i) = x, simply let K
x
=
L
z
x
. Otherwise, create
K
x
= L
z
x
n
∗
∏
j=1
g
(a
j
/b
i
)r
n
∗
∏
k=1,k6= j
(g
a
q+1+ j− k
/b
i
)
w
k
!
M
∗
i, j
.
ICISSP 2017 - 3rd International Conference on Information Systems Security and Privacy
78

Finally, set SK = hK, L,K
x
(∀x ∈ S)i, store
( j,S,SK) in T
4
, and return SK to A .
• Corrupt(i): A cannot ask to corrupt any key cor-
responding to the challenge structure (M
∗
,ρ
∗
). If
the ith entry exists in table T
4
, B obtains the entry
(i,S,SK) and sets D := D ∪ {S} . It returns SK to
A. It returns ⊥ if no such entry exists.
Challenge. A submits a message pair (M
0
,M
1
) to
B. B flips a random coin β ∈ {0,1} and sets
C = M
β
T · e(g
s
,g
α
′
), C
′
= g
s
.
It then chooses random values β
1
,..., β
n
∗
,β
′
1
,..., β
′
n
∗
∈
Z
p
. B sets
E
i
= g
a(β
1
M
i,1
+···+β
n
∗
M
i,n
∗
)
for i = 1,..., ℓ
∗
and
~v = (β
′
1
,..., β
′
n
∗
).
B sets CT
′
= hC,C
′
,(E
i
)
1≤i≤ℓ
∗
,~v,(M
∗
,ρ
∗
)i. It also
sets
¯
C = C,
¯
K =
¯
C/M
β
, and
¯
V = H
′′
(pos
M
∗
) by us-
ing the random oracle hash H
′′
. Then, if the entry
(
¯
C,
¯
K,
¯
V,h
′
) exists in T
2
, B sets π
∗
= h
′
. Otherwise, B
chooses a random value h
′
∈ {0,1}
∗
and sets π
∗
= h
′
.
Finally, B returns CT
′
and π
∗
to A.
Phase 2. B continues to answer queries as in Phase
1.
Guess. A outputs a guess β
′
of β. If β
′
= β, B out-
puts 0 to indicate that T = e(g,g)
a
q+1
s
. Otherwise, it
outputs 1 to indicate that T is a random group element
in G
T
.
When T = e(g,g)
a
q+1
s
, B gives a perfect simula-
tion, and we have
Pr
h
B(~y,T = e(g,g)
a
q+1
s
) = 0
i
=
1
2
+ Adv
A
.
On the other hand, when T is a random group element
in G
T
, the message M
β
is completely hidden from A,
and we have
Pr[B (~y,T = R) = 0] =
1
2
.
Therefore, B can solve the decisional q-parallel
BDHE problem with non-negligible advantage.
Theorem 2. Our scheme is selectively unforgeable if
the hash function H
′
is collision-resistant in the ran-
dom oracle model.
Proof. Let A be an adversary who breaks our scheme
in the selective unforgeability game and B be a simu-
lator that solves the decisional q-parallel DBHE prob-
lem. As described in Section 3.2, A wins if their out-
put (CT
∗
, π
∗
) satisfies Decrypt(CT
∗
,π
∗
,SK,PK) /∈
{⊥,M
∗
}.
Init. Same as Init in the proof of Theorem 1.
Setup. Same as Setup in the proof of Theorem 1.
Query. Same as Phase 1 in the proof of Theorem 1.
Challenge. A gives a challenge message M
∗
to the
simulator B. B then calculates an intermediate ci-
phertext,
CT
′
= {C,C
′
,(E
i
)
1≤i≤ℓ
∗
,~v,(M
∗
,ρ
∗
)},
and a proof π
∗
by using the Encrypt
u
algorithm. B
returns (CT
′
,π
∗
) to A.
Output. A outputs (CT
∗
,π
∗
). B outputs 1 if
(CT
∗
,π
∗
) satisfies Decrypt(CT
∗
,π
∗
,SK,PK) /∈ {⊥
,M
∗
}. Otherwise, it outputs 0.
Let CT = {C, C
′
, (C
i
,D
i
)
1≤i≤ℓ
∗
, (M
∗
,ρ
∗
)} be a
well-formed ciphertext that is obtained from CT
′
and
can be decrypted into M
∗
. Also, let CT
∗
= {
˜
C,
˜
C
′
,
(
˜
C
i
,
˜
D
i
)
1≤i≤ℓ
∗
, (
˜
M
∗
,
˜
ρ
∗
)} be the ciphertext forged by
A. Remember that C = M
∗
·
¯
K (
¯
K = e(g,g)
αs
) and
¯
K depends on C
′
, C
i
, and D
i
. Therefore, there are
only two cases in which A wins: one case is that the
hash function H
′
has a collision and
˜
C is not well-
formed, and the other case is that H
′
has a collision
and either
˜
C
′
,
˜
C
i
, or
˜
D
i
is not well-formed . That is,
the probability that A wins is as follows:
Pr[O−ABE−Exp
unf
A,Π
(λ) = 1]
= Pr
(π
∗
= H
′
(ID,
˜
C,
¯
K,H
′′
(pos
M
∗
))) ∧ (
˜
C 6= C)
+Pr
(π
∗
= H
′
(ID,C,
˜
K,H
′′
(pos
M
∗
))) ∧ ((
˜
C
′
6= C
′
)
∨ (
˜
C
i
6= C
i
)
1≤∃i≤ℓ
∗
∨ (
˜
D
i
6= D
i
)
1≤∃i≤ℓ
∗
)
.
If H
′
is collision-resistant, the above probability is
negligible. Therefore, our scheme is selectively un-
forgeable.
5 PERFORMANCE
5.1 Comparison with Conventional
Schemes
Table 1 compares the encryption costs of our scheme
and the ABE scheme of Waters (Waters, 2008). In
this table, M
G
and M
G
T
denote the cost of one mod-
ular exponentiation in G and G
T
, respectively, and ℓ
denotes the number of attributes in the policy and also
the number of rows of the LSSS matrix. Our scheme
outsources 2ℓ modular exponentiations in G from the
Outsourcing Scheme of ABE Encryption Secure against Malicious Adversary
79
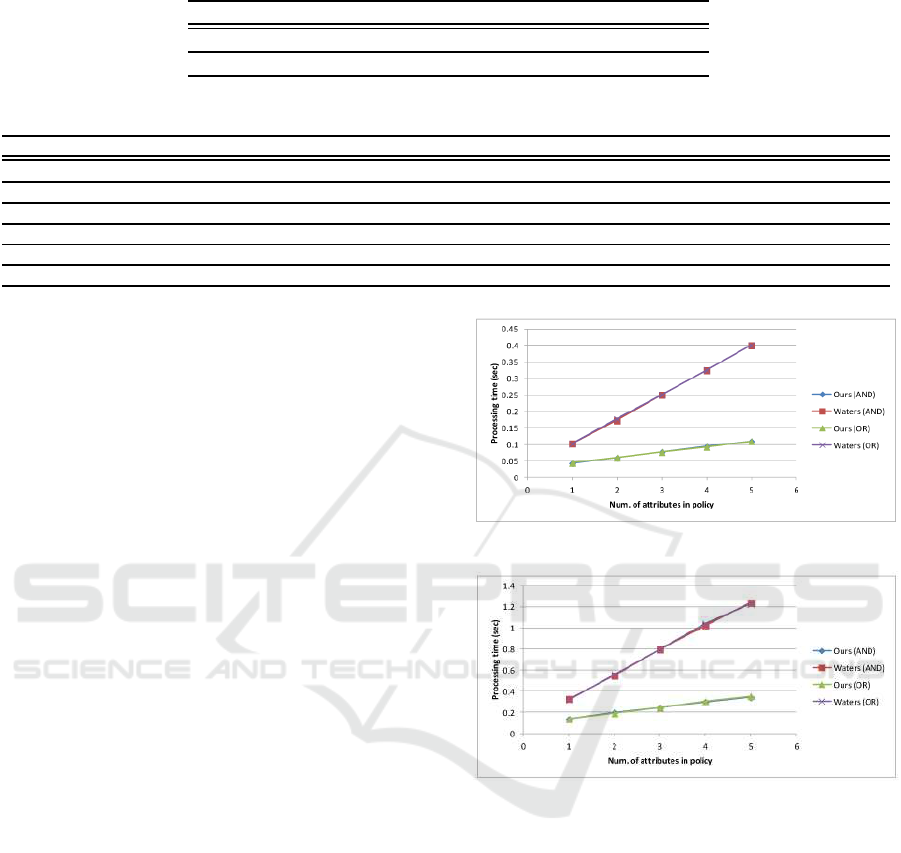
Table 1: Comparison of our scheme and conventional ABE scheme.
[Waters08] Our scheme
Enc. cost for user (3ℓ + 1)M
G
+ M
G
T
(ℓ + 1)M
G
+ M
G
T
Enc. cost for cloud - (3ℓ)M
G
Table 2: Comparison of our scheme and conventional outsourcing schemes of ABE.
[ZH11] [LJLC12] [HW14] Our scheme
Enc. cost for user 3M
G
+ M
G
T
3M
G
+ M
G
T
2S
Z
p
+ P
Z
p
(ℓ +1)M
G
+ M
G
T
Enc. cost for cloud (2m)M
G
(2m)M
G
(5ℓ +1)M
G
+ M
G
T
(3ℓ)M
G
Cloud server honest-but-curious honest-but-curious honest malicious
Security assumption - - q−1 decisional q-parallel BDHE
Security model generic group generic group standard random oracle
Distributed processing no yes no no
original Waters’ scheme to a cloud server, resulting
in a smaller cost for a user terminal. This will be a
particularly significant saving when the number of at-
tributes in the policy, ℓ, is large.
Table 2 compares the encryption cost of our
scheme with that of the ABE outsourcing schemes in
(Zhou and Huang, 2011; Li et al., 2012; Hohenberger
and Waters, 2014). In this table, S
Z
p
and P
Z
p
denote
the cost of one subtraction and one multiplication in
Z
p
, respectively, and m denotes the number of leaf
nodes in a tree representation of the policy statement.
Note that the schemes in (Zhou and Huang, 2011; Li
et al., 2012; Hohenberger and Waters, 2014) have a
lower cost for a user terminal (for ℓ > 2) but their se-
curity is against an honest or honest-but-curious cloud
server, while our scheme provides security against a
malicious cloud server. We may consider multiple
cloud servers and distributed processing in a setting
such as (Li et al., 2012). The security model however
needs to consider malicious cloud servers.
5.2 Implementation Evaluation
We implemented the encryption algorithm of our
scheme and that of Waters’ scheme (Waters, 2008) on
a PC and a tablet computer, representing a user termi-
nal (See Table 3 for details).
We considered a viewing history consisting of 64
records and five possible attributes for the service
provider. The viewing history is encrypted using AES
and a temporary key. This key is then encrypted with
the ABE. We measured the processing time of the en-
cryption algorithm run on a user terminal as the aver-
age of 100 trials. In Figure 2 and 3, the horizontal axis
denotes the number of attributes in the policy and the
vertical axis denotes the processing time (seconds).
For simplicity, we used a ciphertext policy consist-
ing of only AND-gates, or only OR-gates. The cost
of our scheme and Waters’ scheme is labeled accord-
Figure 2: Experimental results (using PC).
Figure 3: Experimental results (using tablet).
ingly for each case. It can be seen that our scheme
costs much less than Waters’ scheme. In particular,
for five attributes, our scheme on a tablet computer
takes 0.4 seconds, while Waters’ scheme takes 1.2
seconds. Note that the processing time only depends
on the number of attributes in the policy and is inde-
pendent of the actual policy statement.
Remark 6. We only measured the client-side encryp-
tion time. However, the measurements of the decryp-
tion time for a service provider, the encryption time
for a cloud server, and the communication cost be-
tween a sender and a receiver do not make sense be-
cause a service provider and a cloud server would
normally have a high-performance CPU and the pro-
tocol is not interactive.
ICISSP 2017 - 3rd International Conference on Information Systems Security and Privacy
80

Table 3: Specifications of user terminal.
PC tablet
CPU Intel Core i7-4790 (3.60GHz) Apple A8X
Memory 8GB -
OS CentOS 7.2 iOS 9.2
Browser Firefox 38.3.0 Firefox 1.4
Programming language JavaScript JavaScript
5.3 Discussion
Our experimental results in Section 5.2 show that our
scheme significantly reduces the encryption cost of a
user terminal. The CPUs in television sets are less
powerful than those in PCs or tablet computers, and
reducing costs is a very important consideration. We
considered an attribute set size of five. A larger set
of attributes would allow for a more flexible access
control policy. The number of attributes in a policy
can easily grow. For example, in a “5-level user rat-
ing” for an attribute of a service provider, “user rating
≥ 3” is represented as
“user rating= 3” OR “user rating= 4”
OR “user rating= 5”
As noted earlier, our scheme has 2ℓ fewer modular ex-
ponentiations compared with Waters’ scheme. Hence,
it can significantly reduce the encryption cost of the
user terminal.
6 CONCLUSIONS
We considered outsourcing of ABE encryption to a
malicious cloud server. We examined the security re-
quirements, formalized the security model, and con-
structed a scheme with provable security based on
Waters’ ABE scheme. We comparedimplementations
of our scheme and Waters’ original scheme. Our se-
curity proof is in the random oracle model. Construct-
ing an outsourcing scheme of ABE encryption that is
secure without a random oracle remains an open prob-
lem. Our approach can be further refined by breaking
the viewing history into smaller portions and labeling
them according to the type of program. Encryption
can be selectively performed on each portion, each
with possibly a different policy, for relevant groups of
service providers, thereby giving viewers finer con-
trol over their viewing history. For example, the user
could allow his or her viewing history of food pro-
grams to be shared with service providers that have
the label “food”. Constructing an outsourcing scheme
for ABE encryption that allows a viewer to specify
more than one policy for accessing their viewing his-
tory is another open problem.
ACKNOWLEDGEMENTS
Reihaneh Safavi-Naini’s research is supported in
part by Albetra Innovates Technology Futures in
the Province of Alberta, Canada. Liang Feng
Zhang’s research is supported by National Nat-
ural Science Foundation of China (Grant No.
61602304) and Shanghai Pujiang Talent Program
(No. 16PJ1406500).
REFERENCES
Attrapadung, N. (2014). Dual system encryption via doubly
selective security: Framework, fully-secure functional
encryption for regular languages, and more. In Proc.
of Eurocrypt’14, pages 557–577.
Attrapadung, N., Hanaoka, G., Ogawa, K., Ohtake, G.,
Watanabe, H., and Yamada, S. (2016). Attribute-based
encryption for range attributes. In Proc. of SCN’16,
pages 42–61.
Attrapadung, N. and Yamada, S. (2015). Duality in abe:
Converting attribute based encryption for dual predi-
cate and dual policy via computational encodings. In
Proc. of CT-RSA’15, pages 87–105.
Baba, A., Matsumura, K., Mitsuya, S., Takechi, M., Fuji-
sawa, H., Hamada, H., Sunasaki, S., and Katoh, H.
(2012). Seamless, synchronous, and supportive: Wel-
come to hybridcast: An advanced hybrid broadcast
and broadband system. IEEE Consumer Electronics
Magazine, 1(2):43–52.
BBC. YouView: Extraordinary TV for everyone. http://
www.youview.com/.
Beimel, A. (1996). Secure Schemes for Secret Sharing and
Key Distribution. PhD thesis, Israel Institute of Tech-
nology.
Bethencourt, J., Sahai, A., and Waters, B. (2007).
Ciphertext-policy attribute-based encryption. In Proc.
of IEEE Symposium on Security and Privacy 2007,
pages 321–334.
Blakley, G. R. (1979). Safeguarding cryptographic keys. In
Proc. of AFIPS National Computer Conference, vol-
ume 48, pages 313–317.
Outsourcing Scheme of ABE Encryption Secure against Malicious Adversary
81

Cheung, L. and Newport, C. (2007). Provably secure ci-
phertext policy abe. In Proc. of ACM Conference on
Computer and Communications Security 2007, pages
456–465.
Emura, K., Miyaji, A., Nomura, A., Omote, K., and Soshi,
M. (2009). A ciphertext-policy attribute-based en-
cryption scheme with constant ciphertext length. In
Proc. of ISPEC’09, pages 13–23.
ETSI. TS 102 796: Hybrid Broadcast Broadband TV;
V1.3.1.
Gay, R., Meaux, P., and Wee, H. (2015). Predicate encryp-
tion for multi-dimensional range queries from lattices.
In Proc. of PKC’15, pages 752–776.
Goyal, V., Pandey, O., Sahai, A., and Waters, B. (2006).
Attribute-based encryption for fine-grained access
control of encrypted data. In Proc. of ACM Con-
ference on Computer and Communications Security
2006, pages 89–98.
Green, M., Hohenberger, S., and Waters, B. (2011). Out-
sourcing the decryption of abe ciphertexts. In Proc. of
USENIX Security Symposium 2011.
Hohenberger, S. and Waters, B. (2014). Online/offline
attribute-based encryption. In Proc. of PKC’14, pages
293–310.
Katz, J., Sahai, A., and Waters, B. (2008). Predicate encryp-
tion supporting disjunctions, polynomial equations,
and inner products. In Proc. of Eurocrypt’08, pages
146–162.
KBS. icon (in Korean). http://icon.kbs.co.kr/site/main/
main.php.
Lewko, A., Okamoto, T., Sahai, A., Takashima, K., and
Waters, B. (2010). Fully secure functional encryp-
tion: Attribute-based encryption and (hierarchical) in-
ner product encryption. In Proc. of Eurocrypt’10,
pages 62–91.
Li, J., Huang, X., Li, J., Chen, X., and Xiang, Y. (2014).
Securely outsourcing attribute-based encryption with
checkability. IEEE Trans. Parallel and Distributed
Systems, 25(8):2201–2210.
Li, J., Jia, C., Li, J., and Chen, X. (2012). Outsourcing
encryption of attribute-based encryption with mapre-
duce. In Proc. of ICICS’12, pages 191–201.
NHK. Hybridcast (in Japanese). http://www.nhk.or.jp/
hybridcast/online/.
Nishide, T., Yoneyama, K., and Ohta, K. (2008). Attribute-
based encryption with partially hidden encryptor-
specified access structures. In Proc. of ACNS’08,
pages 111–129.
Ohmata, H., Endo, H., Baba, A., Matsumura, K., Sunasaki,
S., and Kai, K. (2015). System architecture for cross-
channel application services on hybridcast. In Proc.
of IEEE International Conference on Consumer Elec-
tronics 2015 (ICCE 2015), pages 108–109.
Ohmata, H., Takechi, M., Mitsuya, S., Otsuki, K., Baba, A.,
Matsumura, K., Majima, K., and Sunasaki, S. (2013).
Hybridcast: A new media experience by integration
of broadcasting and broadband. In Proc. of the ITU
Kaleidoscope Academic Conference 2013.
Ohtake, G., Hironaka, Y., Kai, K., Endo, Y., Hanaoka,
G., Watanabe, H., Yamada, S., Kasamatsu, K., Ya-
makawa, T., and Imai, H. (2013). Partially wildcarded
attribute-based encryption and its efficient construc-
tion. In Proc. of SECRYPT’13, pages 339–346.
Okamoto, T. and Takashima, K. (2010). Fully secure func-
tional encryption with general relations from the deci-
sional linear assumption. In Proc. of Crypto’10, pages
191–208.
Ostrovsky, R., Sahai, A., and Waters, B. (2007). Attribute-
based encryption with non-monotonic access struc-
tures. In Proc. of ACM Conference on Computer and
Communications Security 2007, pages 195–203.
Rouselakis, Y. and Waters, B. (2013). Practical con-
structions and new proof methods for large universe
attribute-based encryption. In Proc. of ACMCCS’13,
pages 463–474.
Sahai, A. and Waters, B. (2005). Fuzzy identity-based en-
cryption. In Proc. of Eurocrypt’05, pages 457–473.
Shamir, A. (1979). How to share a secret. Communications
of the ACM, 22:612–613.
Waters, B. (2008). Ciphertext-policy attribute-based en-
cryption: An expressive, efficient, and provably se-
cure realization. In eprint 2008/290.
Zhou, Z. and Huang, D. (2011). Efficient and secure data
storage operations for mobile cloud computing. In
eprint 2011/185.
ICISSP 2017 - 3rd International Conference on Information Systems Security and Privacy
82
