
IEEE C37.118-2 Synchrophasor Communication Framework
Overview, Cyber Vulnerabilities Analysis and Performance Evaluation
Rafiullah Khan, Kieran McLaughlin, David Laverty and Sakir Sezer
Queen’s University Belfast, Belfast, U.K.
Keywords:
Smart Grid, Synchrophasor, Cyber Security, Vulnerability, IEEE C37.118.
Abstract:
Synchrophasors have become an important part of the modern power system and numerous applications have
been developed covering wide-area monitoring, protection and control. Most applications demand continuous
transmission of synchrophasor data across large geographical areas and require an efficient communication
framework. IEEE C37.118-2 evolved as one of the most successful synchrophasor communication standards
and is widely adopted. However, it lacks a predefined security mechanism and is highly vulnerable to cyber
attacks. This paper analyzes different types of cyber attacks on IEEE C37.118-2 communication system and
evaluates their possible impact on any developed synchrophasor application. Further, the paper also recom-
mends an efficent security mechanism that can provide strong protection against cyber attacks. Although,
IEEE C37.118-2 has been widely adopted, there is no clear understanding of the requirements and limitations.
To this aim, the paper also presents detailed performance evaluation of IEEE C37.118-2 implementations
which could help determine required resources and network characteristics before designing any synchropha-
sor application.
1 INTRODUCTION
Synchrophasors are the measurements of electrical
quantities across different parts of the power system
synchronized using a common precise time source.
For higher accuracy and utilizing a universal time
source, synchrophasors are normally time-stamped
using Global Positioning System (GPS) time. With
the development of synchrophasor technology, nu-
merous applications have been proposed. Today, syn-
chrophasor technology is being used in Wide-Area
Monitoring System (WAMS), Wide-Area Protection
and Control System (WAPCS), islanding detection,
determining stability margins, system dynamics vi-
sualization and recording, enhancing operator situa-
tional awareness, etc (Schweitzer et al., 2008).
The aim of synchrophasor technology is to rep-
resent power system condition/status in real time.
This requires transmission of synchrophasor measure-
ments across large geographical areas in real-time
with very low latency. Using IP based communica-
tion is feasible where it utilizes already available high
speed infrastructure. To transmit synchrophasor mea-
surements over an IP network, a suitable communi-
cation framework is required. The IEEE C37.118-2
standard evolved as one of the most successful and
widely adopted communication framework for syn-
chrophasor applications. The IEEE C37.118-2 stan-
dard specifies messaging format but does not put any
restriction on the choice of communication medium
or transport protocol. Further, IEEE C37.118-2 stan-
dard does not addressed security features. The syn-
chrophasor measurements are transmitted over inse-
cure IP network which make IEEE C37.118-2 com-
munication highly vulnerable to cyber attacks (Stew-
art et al., 2011).
This paper describes the IEEE C37.118-2 stan-
dard in details highlighting its main features and ca-
pabilities. It also explores how vulnerabilities can
be exploited to launch different types of attacks on
IEEE C37.118-2 communication system. In partic-
ular, reconnaissance, authentication/access, man-in-
the-middle, replay/reflection and denial of service at-
tacks are explored. These attacks alone or in com-
bination may severely impact the synchrophasor ap-
plications. They may leave different components of
the synchrophasor system not being able to commu-
nicate with each other or unintentionally performing
wrong decisions. For most critical synchrophasor ap-
plications, cyber attacks could potentially cause se-
vere damage to the physical equipment. Therefore, it
is vital to effectively analyze and mitigate cyber vul-
nerabilities in the synchrophasor system. Most often,
attackers try to exploit communication framework to
Khan, R., McLaughlin, K., Laverty, D. and Sezer, S.
IEEE C37.118-2 Synchrophasor Communication Framework - Overview, Cyber Vulnerabilities Analysis and Performance Evaluation.
DOI: 10.5220/0005745001670178
In Proceedings of the 2nd International Conference on Information Systems Security and Privacy (ICISSP 2016), pages 167-178
ISBN: 978-989-758-167-0
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
167

launch attacks. To protect IEEE C37.118-2 commu-
nication framework against attacks, this paper recom-
mends an effective security mechanism where secu-
rity policy and keying material periodically change.
Such refreshment of security credentials prevent at-
tacker never being able to discover a valid secret key.
Even if an attacker somehow discovers secret key
through analyzing captured packets, it will no longer
remain valid. In short, the main contributions of this
paper include:
1. Analysis of vulnerabilities in IEEE C37.118-2
standard through different cyber attacks and their
impact on the synchrophasor application.
2. Recommendation of an efficient security mecha-
nism integrated in IEEE C37.118-2 standard and
evaluation of its effectiveness.
3. Detailed performance evaluation of IEEE
C37.118-2 standard to analyze requirements and
limitations in a practical environment.
The rest of the paper is organized as follows: Sec-
tion 2 addresses related work. Section 3 describes a
generic synchrophasor system and its basic building
blocks. Section 4 describes IEEE C37.118-2 stan-
dard, different types of defined messages, and com-
munication modes and protocols. Section 5 analyzes
cyber vulnerabilities in IEEE C37.118-2 standard and
recommends a suitable security mechanism by ad-
dressing its unique features. Section 6 presents de-
tailed performance evaluation of IEEE C37.118-2 im-
plementations. Finally, Section 7 concludes the paper.
2 RELATED WORK
Synchrophasor technology got increasing popularity
since its development. Its applications quickly pro-
gressed from simple data visualization and archiv-
ing or postmortem analysis to several real-time pro-
tection, monitoring and control applications. This
is due to the capability of synchrophasors represent-
ing power system condition in real time and taking
prompt control actions. The authors in (Schweitzer
et al., 2008) described several advanced real-time syn-
chrophasor applications developed over time. Sev-
eral efforts were put to develop a suitable communi-
cation standard for synchrophasors. IEEE C37.118-2
evolved probably as the first most successful commu-
nication standard. It was originally based on IEEE
1344 standard and its evolution is explained in (Mar-
tin et al., 2008). The authors have also highlighted
key differences between old and new versions and
introduced several applications for IEEE C37.118-2
standard.
Since, most synchrophasor applications involve
transmission of data across large geographic areas us-
ing non-reliable and insecure IP network, analysis of
potential cyber vulnerabilities and threats drawn more
and more research attention (Allgood et al., 2011).
It is worth to mention that IEEE C37.118-2 standard
does not include any security feature and making ap-
plications highly vulnerable to cyber attacks. Al-
though cyber security research in general is not new,
still implementation of experimental tools or strate-
gies to effectively mitigate vulnerabilities for syn-
chrophasor system is quite limited.
Authors in (Stewart et al., 2011) presented best
practice techniques (such as firewall, Virtual Private
Network (VPN)) and verified by experiments to over-
come cyber vulnerabilities. Their main focus was to
ensure information security between substation and
control center. However, security within the substa-
tion LAN or within the control center LAN has negli-
gible considerations. Authors in (Morris et al., 2011)
evaluated the resilience of Phasor Measurement Units
(PMUs) against denial of service attacks using IEEE
C37.118. They flooded PMU with ARP request pack-
ets, IPv4 packets and PPPoE packets and monitored
its unresponsiveness. Further, the authors evaluated
resilience against malformed packets through proto-
col mutation tests. Several other efforts also tried to
protect synchrophasor network against cyber attacks
(Sikdar and Chow, 2011).
Along with information security, several research
efforts also focused on ensuring PMU and Phasor
Data Concentrator (PDC) security (D’Antonio et al.,
2011). A further work analyzing PMUs vulnerabili-
ties using IEEE C37.118 protocol was performed by
(Coppolino et al., 2014). Synchrophasor applications
require high time synchronization which is normally
achieved through GPS. GPS spoofing may leave se-
vere impact on any synchrophasor application. This
is analyzed by authors in (Shepard et al., 2012) that
GPS spoofing can cause intentional tripping of power
generators and may even cause physical damage to
equipment. A further work analyzing detection of
GPS spoofing attacks is presented in (Yu et al., 2014).
In short, cyber vulnerabilities analysis is a hot re-
search topic and numerous research articles are avail-
able in literature. There are also number of avail-
able surveys analyzing cyber threats relevant to smart
grid in general, PMU network, and/or synchrophasor
applications (Boyer and McBride, 2009), (Baumeis-
ter, 2010), (Yan et al., 2012), (Zargar et al., 2013),
(Beasley et al., 2014).
Most of the research in literature addresses cy-
ber vulnerabilities for power system in general with
few have little focus on synchrophasors network. No
ICISSP 2016 - 2nd International Conference on Information Systems Security and Privacy
168
much work is available on analyzing cyber vulnera-
bilities in IEEE C37.118-2 communication standard.
This paper analyzes cyber vulnerabilities in IEEE
C37.118-2 standard and evaluates possible impact on
the synchrophasor application. Further, this paper
also recommends a security mechanism to be used
with IEEE C37.118-2 standard to achieve protec-
tion against different cyber attacks. Although IEEE
C37.118-2 standard is being widely used, its require-
ments and limitations in practical environment have
never been addressed. To this aim, this paper also
presents detailed performance evaluation of IEEE
C37.118-2 standard.
3 OVERVIEW OF
SYNCHROPHASOR
MEASUREMENT SYSTEM
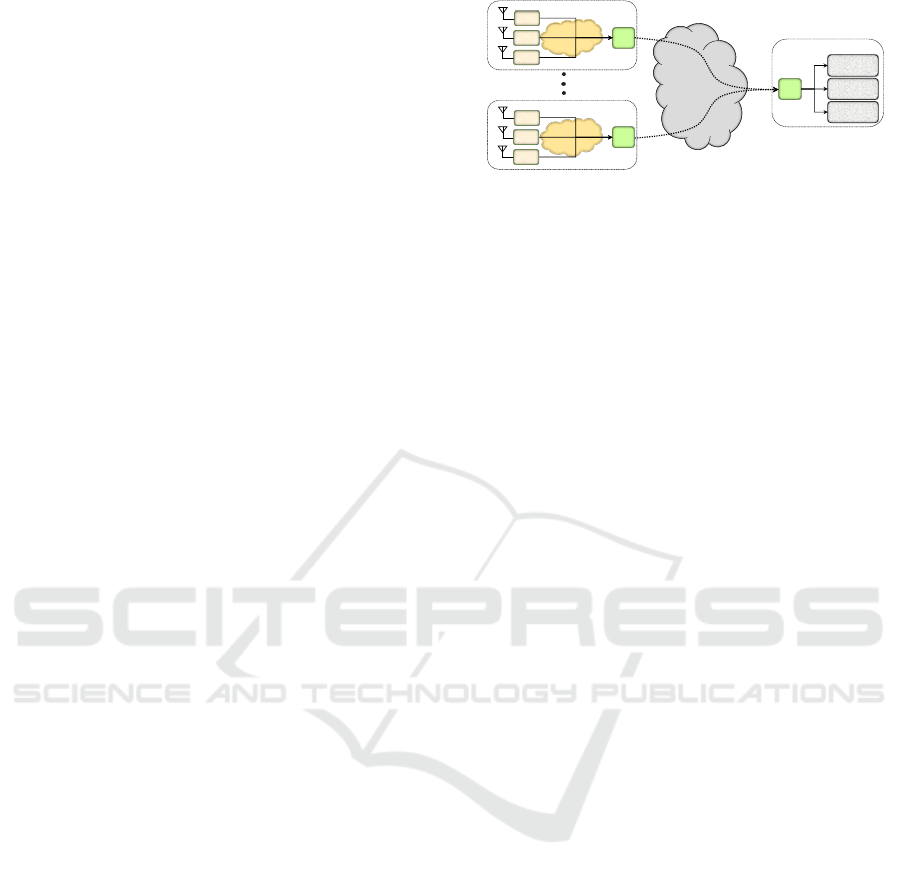
A synchrophasor system consists of several basic
building blocks including GPS receivers, PMUs,
PDCs, communication network and equipment and
visualization, monitoring or control software as
shown in Fig. 1. A PMU is the device that performs
measurements of synchrophasor data which represent
electrical quantities for current/voltage waveform at a
given time instant. The measurements performed by
PMU are normally time stamped to a common and
highly precise time source often GPS. Thus, PMU
devices are normally equipped with a GPS antenna.
The PMU can be a standalone device with dedicated
functionality or it may co-exist on a multi-functional
device. There are two possible modes of operations
of PMU; commanded and spontaneous. In com-
manded mode, PMU establishes bi-directional com-
munication with its peer (local or remote PDC or ap-
plication). The peer can send commands to PMU to
control its operations (e.g., stop/start or control syn-
chrophasors transmission). The communication be-
tween PMU and its peer is normally private unicast in
commanded mode. In spontaneous mode, PMU oper-
ations cannot be controlled by its peer. The commu-
nication is uni-directional (from PMU to its peer) and
PMU is not able to receive any commands. The com-
munication between PMU and its peers is normally
multicast in spontaneous mode of operation.
Another important element in a synchrophasor
system is PDC. PDC is a device which receives syn-
chrophasor data from more than 1 PMU and aggre-
gates and transmits as one output stream. A PDC may
be receiving data from multiple PMUs (i.e., substa-
tion PDC in Fig. 1) or multiple PDCs (i.e., Control
Center PDC in Fig. 1).
Substation 1
LAN
PDC
GPS Antenna
Substation N
LAN
PDC
GPS Antenna
Control Center
Monitoring /
Visualization
PDC
Control
Software
Archive
Network /
Internet
PMU
PMU
PMU
PMU
PMU
PMU
Figure 1: Generic synchrophasor communication system.
As illustrated in Fig. 1, the control center may be
receiving data from more than one substation and han-
dover to respective application. The application may
be designed for simply archiving data, performing vi-
sualization/monitoring or performing protection and
control functionalities. It can be observed in Fig. 1
that the synchrophasor data could be directly provided
by PMUs to respective application without needing
any PDC. However, such approach will result in a
lot of network traffic overhead (analyzed in Section
6) and ambiguity for control application in interpret-
ing data from each PMU. Thus, the substation PDC
makes the transmission much more efficient by send-
ing out only one stream of data instead of multiple
streams.
As depicted in Fig. 1, synchrophasor measure-
ments are transmitted in real-time over insecure pub-
lic Internet. Thus, a suitable communication proto-
col is required that can ensure security as well as low
transmission latency. IEEE C37.118-2 is most wide
used communication framework for synchrophasor
applications. Although it lacks security features and
is vulnerable to cyber attacks. Section 4 analyzes im-
portance of security and presents a suitable security
mechanism for IEEE C37.118-2 standard.
4 IEEE C37.118-2
COMMUNICATION STANDARD
Synchrophasor applications demand real-time trans-
mission of messages with very low latency. This sec-
tion briefly addresses the IEEE C37.118-2 standard,
which evolved as one of the most suitable and well
tested standard for the transmission of synchrophasor
measurements. IEEE C37.118-2 standard effectively
addresses synchrophasor requirements, presents suit-
able format and structure for messages and ensures to
keep communication overhead to the minimum possi-
ble level.
IEEE C37.118-2 Synchrophasor Communication Framework - Overview, Cyber Vulnerabilities Analysis and Performance Evaluation
169

4.1 Overview
With the development of synchrophasor technology
and its need for transmission over wide area net-
works, IEEE established a working group to develop
a suitable communication standard. The working
group developed IEEE 1344 in 1995, the first standard
for transmission of synchrophasor measurements in
real-time. IEEE 1344 addresses data formats, struc-
tures and time synchronization of data from multiple
sources. However, it does not address measurement
accuracy, support for transmission hierarchy, hard-
ware and software requirements, process for calcu-
lating synchrophasors, security mechanism and trans-
port protocol. These considerations are left to the
users based on their needs and application require-
ments.
In 2005, IEEE 1344 was replaced by an improved
IEEE C37.118 standard which overcomes the limita-
tions of the previous standard and focuses on the re-
quirements for future power systems. The most obvi-
ous improvements include the introduction of meth-
ods for evaluating measurement performance, ac-
counting measurements from multiple PMUs and a
more complete messaging system. It introduced To-
tal Vector Error (TVE) criterion to check if the mea-
surements are compliant with the standard. It mainly
shifted focus from the measurement method to the
measurement results. Thus, any algorithm or tech-
nique can be used as long as it produces acceptable
results.
The IEEE C37.118 standard was limited to ad-
dress accuracy requirements only for steady state
conditions. Over time, the IEEE realized the need
to address requirements for synchrophasor measure-
ments also under dynamic conditions. Further, IEEE
C37.118 standard combined synchrophasor measure-
ment and communication functions. To overcome
the shortcomings and fix some minor errors, IEEE
C37.118 split into two parts in 2011, IEEE C37.118-
1 and IEEE C37.118-2. IEEE C37.118-1 addresses
requirements for synchrophasor measurements under
dynamic conditions which makes it very suitable for
most of the applications where the phasor measure-
ments could be severely affected by system noise and
disturbances. Whereas, IEEE C37.118-2 addresses
only the communication framework and requirements
for transmission of synchrophasors. It is worth men-
tioning that IEEE C37.118-2 is an extended standard
with some new features but provides full backward
compatibility with original IEEE C37.118. Further, it
also does not put any restriction on the choice of com-
munication protocol, communication medium and the
mode of communication.
SYNC
SOC
CHK
2 Bytes
2 Bytes
2 Bytes 4 Bytes 4 Bytes
Depending on Data Size
2 Bytes
MSB
LSB
IDCODE
FRAMESIZE
FRACSEC
DATA 1 DATA 2
DATA N
Figure 2: IEEE C37.118-2 standard message format.
4.2 Message Format and Types
IEEE C37.118-2 specified a standard format for dif-
ferent types of the messages as depicted in Fig. 2.
Each message begins with identification and synchro-
nization word (SYNC), followed by FRAMESIZE
(total Bytes inside message), IDCODE (ID of the
synchrophasor data source), SOC (Second Of Cen-
tury count since epoch midnight 01.01.1970), FRAC-
SEC (FRACtion of SECond and time quality), DATA
(Depends on message type) and CHK (Cyclic Re-
dundancy Check (CRC)). The content and structure
of DATA field is different for different types of
messages. IEEE C37.118-2 standard described four
types of messages: data, configuration, command and
header. Header message carries descriptive informa-
tion in human readable format while all other types
of messages are in machine readable format. Com-
mand messages are sent by the control application to
data source (e.g., PMU, PDC) as instructions/orders
while data, configuration and header are sent by the
data source.
4.2.1 Data Message
Data messages are sent by the data source which
include real-time measurements of synchrophasors.
The sending device can be a PMU (containing single
block of data) or PDC (containing multiple blocks of
data). Each block of data contains a complete struc-
ture according to IEEE C37.118-2 (phasors in polar
or rectangular format, analog and digital values, fre-
quency deviation, rate of change of frequency etc). In
the case of a PDC, data from multiple PMUs is cor-
related to a particular time stamp and transmitted in a
single message.
4.2.2 Configuration Message
Configuration messages contain information and pro-
cessing parameters (calibration factors, meta data,
data types, etc) for a synchrophasor data stream. It ba-
sically provides necessary information to the receiver
on how to decode data messages. IEEE C37.118-2
standard identified three types of configuration mes-
sages: CFG-1, CFG-2 and CFG-3. CFG-1 and CFG-
2 were also present in the first IEEE C37.118 stan-
dard published in 2005. CFG-1 represents data source
(PMU, PDC) capabilities and the data it will be re-
porting. CFG-2 represents measurements currently
ICISSP 2016 - 2nd International Conference on Information Systems Security and Privacy
170

being transmitted in data messages. CFG-3 is similar
to CFG-1 and CFG-2 but includes added information
and flexible framing.
4.2.3 Header Message
Header messages carry human readable descriptive
information about the data source, scaling algorithms,
filtering etc. It does not have a special format for
the DATA field (in Fig. 2) but carries information in
ASCII format.
4.2.4 Command Message
Command messages are orders received by a data
source device. These orders include but are not lim-
ited to: start and stop transmission of data messages,
send header message, send CFG-1, CFG-2 or CFG-3
configuration message etc.
Data Source Controller
Command: Send Configurations
Configuration: CFG-2
Command: Start Data Transmission
Data: Synchrophasors
Command: Stop Data Transmission
Figure 3: Generic IEEE C37.118-2 communication sce-
nario for data source operating in commanded mode.
Fig. 3 depicts a generic communication scenario
when the data source operates in commanded mode.
For simplicity header message is not shown which
may be requested by control application/controller
using command message. Upon receiving request,
data source sends a header message to the con-
troller. When a data source operates in spontaneous
mode (cannot receive commands), then communica-
tion should only contain data and configuration mes-
sages. A data source will ensure to send configuration
messages whenever necessary to enable the receiver
to correctly decode data messages.
4.3 Communication Modes and
Protocols
IEEE C37.118-2 only specifies different types of mes-
sages and their structure, format and content. It does
not put any restriction on communication mode or
choice of transport protocol. Most industrial imple-
mentations targeted either RS232 serial or IP based
network communication depending on the applica-
tion. The possible communication modes include:
client-server/unicast (one device sends data which is
received by one other device), multicast (one device
sends data which is received by a group of device) and
broadcast (one device sends data which is received by
all available device in the network). The freedom on
the choice of transport protocol leads to several com-
bination: (i) TCP for all types of messages, (ii) UDP
for all types of messages, and (iii) data messages on
UDP while all other messages on TCP. Each combi-
nation will have its own pros and cons which we will
try to analyze in Section 6.
5 SECURITY ANALYSIS &
RECOMMENDATIONS
IEEE C37.118-2 does not specify any kind of cryp-
tographic signature. Thus, packets are vulnerable to
spoofing, being modified in the network during trans-
mission or being transmitted by un-authorized peers.
This section first analyzes how vulnerabilities in IEEE
C37.118-2 based communication system could be ex-
ploited in the form of different possible attacks. To
overcome the vulnerabilities, a security mechanism
based on Group Domain of Interpretation (GDOI) is
recommended that could be efficiently integrated in
IEEE C37.118-2 communication systems (Weis et al.,
2011). Finally, this section also analyzes the effec-
tiveness of the recommended security system.
5.1 Cyber Vulnerabilities Analysis
Cyber vulnerabilities in IEEE C37.118-2 could be ex-
ploited by unauthorized entities/attackers to extract,
modify or insert messages in the network. With the
knowledge of vulnerabilities, different types of at-
tacks could be launched which may impair the com-
munication and cause physical damage to the syn-
chrophasor system. The attacks described here are
based on the generic synchrophasor system depicted
in Fig. 1.
5.1.1 Reconnaissance Attack
In a reconnaissance attack, an adversary first tries to
discover vulnerabilities in the network which could be
exploited for the actual attack. It is the unauthorized
learning process of the network devices or commu-
nication system to discover available services, open
ports, identify network stack daemons or the operat-
ing system, etc. Reconnaissance itself is not normally
a harmful action but provides necessary information
IEEE C37.118-2 Synchrophasor Communication Framework - Overview, Cyber Vulnerabilities Analysis and Performance Evaluation
171

for the adversary to plan and launch more severe at-
tacks such as Denial of Service (DoS) attack, access
attack etc.
Reconnaissance attack could be launched either
on the physical device or on the communication net-
work. The main focus here is the communication
network. Through eavesdropping on network traf-
fic of IEEE C37.118-2, attackers could learn about
the substation name, names and locations of differ-
ent physical components (e.g., PMU, breakers) and
configurations of the device sending packets. Such
information is normally carried by IEEE C37.118-
2 configuration messages. The attacker may be in-
terested in controlling the PMU operations (or the
whole substation depending on synchrophasor ap-
plication) through eavesdropping on command mes-
sages. Eavesdropping on data messages will enable
an attacker to know the current physical state of the
substation. The level of risk through eavesdropping
on header messages might be low or high depend-
ing on the synchrophasor application. In short, eaves-
dropping on different types of IEEE C37.118-2 mes-
sages can enable an attacker to launch high impact
attacks on the substation.
5.1.2 Authentication/Access Attack
Authentication is an access control mechanism which
ensures that only authorized users can get access to a
system or resources. It is the process in which cre-
dentials provided by the client devices are checked
and compared to the information on file/database and
access is granted only if the credentials match. Unau-
thorized access to a device or information is some-
times also referred to as access attack.
IEEE C37.118-2 does not specify any form of au-
thentication between communicating devices. Thus,
it is possible that the control application or the
PDC interprets messages being received from genuine
PMUs but it may not be the case. The messages may
be received from non-intended PMUs or from attack-
ers through packet injection or replay attacks.
Not only on the network traffic, access attacks
may also take place on the physical device e.g.,
PMU/PDC or control center. Once attacker has con-
trol on the physical device, he can easily alter packets
being transmitted or injects packets on its own.
5.1.3 Man In The Middle Attack
In a Man In The Middle (MITM) attack, the at-
tacker impersonates two communicating devices and
makes them believe that they are directly communi-
cating with each other. Instead, the attacker lies in
the middle and is able to intercept each and every
packet exchanged between the two communicating
devices. The MITM attack may also involve connec-
tion/session hijacking. The attacker capabilities in a
successful MITM attack include hijacking packets, al-
tering or dropping them and injecting new packets.
The MITM attack can target any message type
in an IEEE C37.118-2 synchrophasor communication
system. However, its impact could be much more se-
vere on command, configuration and data messages
compared to header messages. Targeting configu-
ration messages will enable an attacker to severely
disrupt the synchrophasor application. The attacker
can easily leave a receiver (applications at the con-
trol center) unable to decode/understand data mes-
sages. This makes attack on configuration messages
the most attractive choice for an attacker. Command
messages control the whole communication and an
attacker may intentionally disrupt or start/stop the
transmission of data messages. Attacks on data mes-
sages may alter/modify the synchrophasor measure-
ments and make the receiver believe that the data is
genuine. This will leave receiver unintentionally per-
forming decisions based on incorrect data. The im-
pact of MITM attack on header messages is applica-
tion dependent.
5.1.4 Replay or Reflection Attack
Replay attacks rely on MITM attack to record com-
munication between two devices and replay it to hide
real system information. The replay packets might
lead to incorrect decisions by the receiving device.
Further, this attack does not require detailed knowl-
edge of the underlying system. The impact of replay
attacks on different types of IEEE C37.118-2 mes-
sages is similar to a MITM attack. Replaying data
messages may cause the receiver to carry out incorrect
actions. If configurations change, replaying old con-
figuration messages could prevent the receiver from
decoding upcoming data messages.
5.1.5 Denial of Service Attack
The DoS attack is different from previous attacks as it
does not require unauthorized access to network traf-
fic or the communicating devices but simply attempts
to disrupt or block communication between the com-
municating devices. The DoS attacks overwhelm
the target device with high data rate bulk packets so
that it becomes irresponsive due to lack of available
resources (bandwidth, CPU, memory etc) or buffer
overflow. Referring to Fig. 1, the DoS attack can be
on the communication link between PMUs and sub-
station PDC, substation PDC and control center PDC
or control center PDC and the control applications.
ICISSP 2016 - 2nd International Conference on Information Systems Security and Privacy
172

Group Controller / Key Server (GCKS)
Group Member Group Member Group Member
Internet
Phase 1
Phase 2
Phase 3
Figure 4: Generic GDOI-based communication scenario.
The most feasible choice for most of the attackers will
be targeting communication link between substation
PDC and control center PDC. This will lead to loss of
substations visibility for the control center.
Normally, DoS attacks will prevent all types of
IEEE C37.118-2 messages being processed by the re-
ceiver. However, if the DoS attack is weak, it may
result in less number of messages being lost at the
receiver. Depending on the type of message (that is
lost), the impact of DoS attack could be different.
Loss of configuration message will leave receiver un-
able to decode upcoming data messages. Loss of few
data messages will make difficult for the receiver to
take decisions due to not having enough information
about the synchrophasor system dynamics. Loss of
command message will prevent receiver from control-
ling data source. While the impact of DoS attack on
header message is application dependent.
5.2 Enabling Security based on GDOI
To secure the IEEE C37.118-2 based communica-
tion system against attacks, its inherent vulnerabilities
should be addressed. Further, a mechanism should
be introduced that can make attacker activities visi-
ble to the user. To this aim, this paper suggests the
use of GDOI to ensure secure communication of syn-
chrophasors using IEEE C37.118-2. GDOI is a group
key management protocol published by Cisco Sys-
tems & MIT (Weis et al., 2011). Since publication,
GDOI is getting increasing popularity. It has already
been adopted in IEC 61850-90-5, a real time commu-
nication system for the smart grid applications. GDOI
ensures that the communication remains highly se-
cure by constantly changing group Security Associ-
ations (SAs).
The generic GDOI-based communication sce-
nario is depicted in Fig. 4. The GDOI group
key management model consists of two types of de-
vices: Group Controller/Key Server (GCKS) and
Group Member (GM). GCKS is responsible to main-
tain group security policy and generation of keys. As
shown in Fig. 4, the GDOI mechanism consists of
three phases:
• Phase 1: The group members authenticate and
register with the GCKS in order to get IPsec SAs
which are necessary to secure communication be-
tween the group members. The registration phase
is secured through encryption using Pairwise key.
It is possible that GCKS manages more than one
group and each group has different SAs. To re-
quest security policies and keys, group members
need to provide group ID to GCKS. After the
group ID is verified, GCKS sends group security
policy to the group member. The group member
checks if it can handle the policy and acknowl-
edges to the GCKS in order to download the Key
Encryption Key (KEK). The KEK is used to en-
crypt the message in which GCKS provides Traf-
fic Encryption Key (TEK) to the group member.
• Phase 2: The group member uses TEK as an
IPsec SA to encrypt messages it exchanges with
other group members. In synchrophasor applica-
tions, TEK will be used to encrypt different types
of IEEE C37.118-2 messages.
• Phase 3: Remember, GCKS assigns both KEK
and TEK keys with certain validity period. The
keys should be refreshed periodically and pro-
vided to group members before the expiry of pre-
vious keys to enable uninterrupted secure commu-
nication between group members. This keys up-
date mechanism can be unicast to a single group
member or multicast to all group members. Mul-
ticast update messages have no delivery acknowl-
edgment and are transmitted multiple times to ac-
count for any packet loss.
The GDOI protocol is based on Internet Se-
curity Association and Key Management Proto-
col (ISAKMP) to protect the group members au-
thentication and registration in Phase 1. All the
group members and GCKS must have the same
ISAKMP policy acquired via an out of band method.
The ISAKMP policy should be strong enough as
the whole GDOI mechanism security depends on
it. Two new ISAKMP exchanges are defined
in GDOI: GROUPKEY-PULL and GROUPKEY-
PUSH. GROUPKEY-PULL exchange is used in
Phase 1 as explained above. GROUPKEY-PULL ex-
change allows group members to request group pol-
icy and keying material (KEK, TEK) from GCKS.
GROUPKEY-PUSH exchange is Phase 3 in which
GCKS distributes the updated group policy and key-
ing material to all authorized group members before
the expiry of the previous keying material.
It is important that GCKS is explicitly a trusted
entity by all group members. If no authentication is
IEEE C37.118-2 Synchrophasor Communication Framework - Overview, Cyber Vulnerabilities Analysis and Performance Evaluation
173

performed, MITM attack between GCKS and group
member could be possible for a rogue GDOI partici-
pant. It is also important that GCKS explicitly authen-
ticates/authorizes each group member before sending
them group policy and keying material. The GCKS
should implement a method for authenticating mem-
bers (e.g., by maintaining an up to date authorization
list).
5.3 Benefits of GDOI based Security
All the different types of attacks described in Sec-
tion 5.1 could be mitigated if the devices and IEEE
C37.118-2 communication are appropriately secured.
As explained before, the reconnaissance attack could
either take place on the network devices or the com-
munication network. The main focus here is only on
the communication network. If IEEE C37.118-2 mes-
sages are encrypted, eavesdropping on network traf-
fic would not benefit the attacker. Although IEEE
C37.118-2 does not include authentication, still the
authentication or access attacks could be prevented. It
is due to the fact that unauthorized users could not ac-
quire security policy and keying material from GCKS.
Without having valid TEK, devices are not be able to
communicate. Similarly to eavesdropping on network
traffic, MITM attack could be easily prevented due to
encrypted messages.
The replay attacks replay the recorded communi-
cation between two devices. These attacks could also
be prevented due to periodic security policy and key-
ing material refreshment mechanism used in GDOI.
The replayed messages might be based on old key-
ing material which is no longer valid. This obviously
depends on the validity period of keys assigned by
GCKS. A shorter key validity period could effectively
prevent IEEE C37.118-2 based communication from
replay attacks. The DoS attacks overwhelm the target
device with high traffic. The impact of DoS attacks
can be mitigated to a degree if the receiver simply
discard messages without processing them. This is
only possible if the receive knows that messages are
received from unauthorized device. The GDOI mech-
anism prevents any unauthorized device being able to
communication with authorized devices.
Thus, different types of attacks could be prevented
as long as key distribution mechanism is not com-
promised. GDOI assumes that the network is inse-
cure and could be exploited by attackers. However,
it assumes that GCKS and group members are all
trusted and secure. Any compromised group member
may enable attacker to reveal group policy and keying
material necessary to eavesdrop on network traffic.
Therefore, group members must have proper security
in place preventing unauthorized access to them.
GDOI consists of three different phases as de-
scribed in Section 5.2. From a security point of view,
attackers will most probably look for vulnerabilities
in Phase 1 ISAKMP authentication, GROUPKEY-
PULL and GROUPKEY-PUSH exchanges of secret
keying material. The effectiveness of these exchanges
is briefly described in the following.
5.3.1 Phase 1 ISAKMP Authentication
The authentication in Phase 1 is achieved via pre-
shared keys assuming secure GCKS and group mem-
bers. Any connection hijacking or MITM attack will
foil the authentication of one or more communicat-
ing peers during key establishment. An attacker may
launch replay or reflection attack between GCKS and
a group member and replays captured messages to a
group member. The replay of previous key manage-
ment messages could be detected as GDOI relies on
hash based message authentication along with Phase
1 nonce mechanism. Further, GDOI provides preven-
tion against DoS attacks by identifying spurious mes-
sages through a Phase 1 cookie mechanism prior to
processing cryptographic hash.
5.3.2 GROUPKEY-PULL Exchange
GROUPKEY-PULL exchange is used by group mem-
bers to request security policy and keying material
from GCKS. It is assumed that GCKS and group
members are secure and properly authenticated in
Phase 1. The GROUPKEY-PULL exchange is pro-
tected against connection hijacking and MITM at-
tacks as the authentication involves a secret known
only to GCKS and group members when construct-
ing HASH payload. Thus, the attacker could not alter
a message that goes undetected by GCKS or group
members. GCKS also keeps track of previously pro-
cessed GROUPKEY-PULL messages (e.g., message
HASH) and directly rejects messages previously pro-
cessed in order to not overload the computational re-
sources. This contributes to preventing against replay
and DoS attacks.
5.3.3 GROUPKEY-PUSH Exchange
GROUPKEY-PUSH exchange is used by GCKS to
update group members about new security policy and
keying material prior to the expiry of previous SAs.
The message is encrypted by KEK which is only
known to group members and distributed in previ-
ous GROUPKEY-PUSH exchange or GROUPKEY-
PULL exchange. The KEK is only known to GCKS
and group members (both are assumed secure) and
ICISSP 2016 - 2nd International Conference on Information Systems Security and Privacy
174
this provides protection against connection hijacking
and MITM attacks. The GROUPKEY-PUSH mes-
sages carry an increasing sequence number which
provides protection against reflection/replay attacks.
A group member will simply discard a GROUPKEY-
PUSH message if it contains sequence number the
same or lower than a previously received message.
Further, cookies provide protection against DoS at-
tacks for GROUPKEY-PUSH message.
6 PERFORMANCE EVALUATION
The implementation of the IEEE C37.118-2 library
was carried out in Linux OS using Python program-
ming language. A number of experiments were per-
formed to analyze the requirements, effectiveness and
limitations of IEEE C37.118-2 using different trans-
port protocols. Currently, research focuses on the ef-
ficient design of PMUs/PDCs on compact hardware.
To this aim, all the experimental results reported in
this section were performed on a low power pocket
PC i.e., Raspberry Pi v2 (CPU: ARMv6 700 MHz,
Memory 512 MB, Power consumption: 3.6 W (idle)
& 3.8 W (full load)).
It is worth noting that any synchrophasor applica-
tion based on IEEE C37.118-2 will have its own re-
source requirements and performance metrics based
on its size, complexity and capabilities. The re-
ported results in this section are performance metrics
only ascribable to IEEE C37.118-2 library in any de-
veloped application. For all the reported results, it
is assumed that the PMU/PDC sends data messages
each carrying 2 phasors, 2 analog values and 1 dig-
ital word, all expressed in integer format except fre-
quency deviation (FREQ) and rate of change of fre-
quency (DFREQ) in floating point format. The same
settings are also reflected in Configuration (Config)
messages.
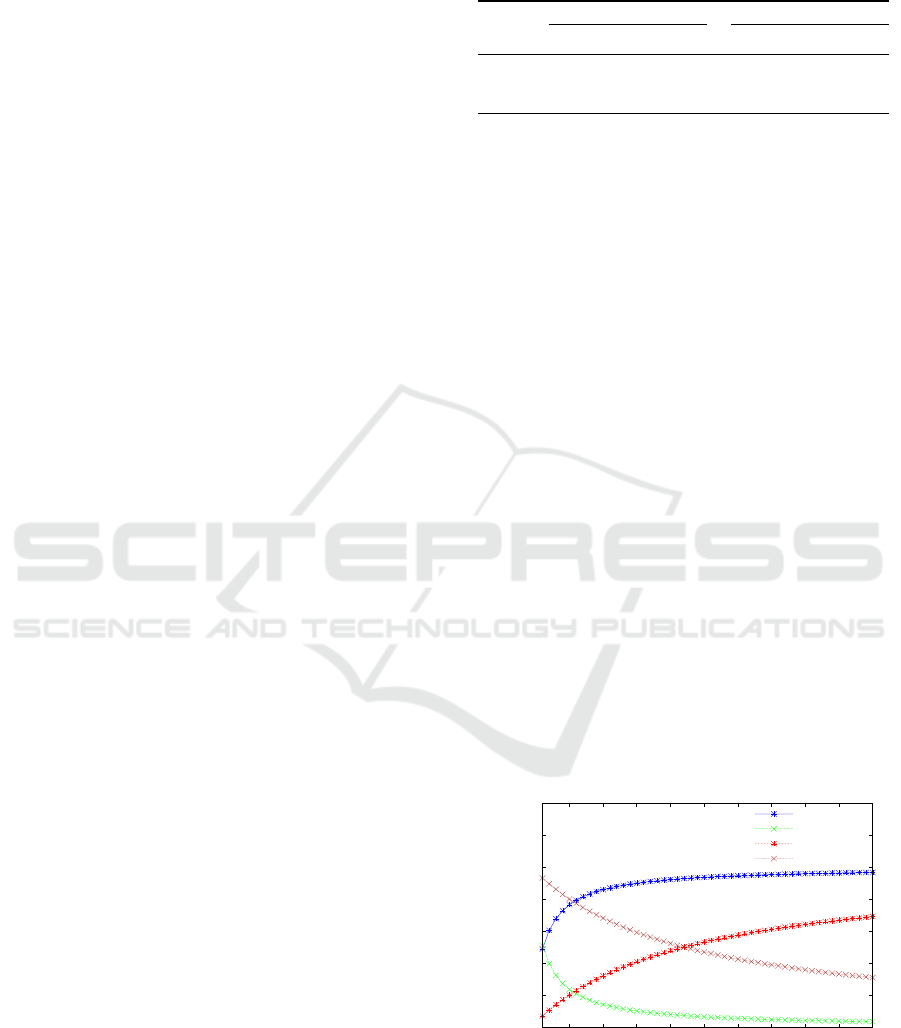
6.1 Communication Overhead
The communication overhead is a significant perfor-
mance metric for any protocol. It indirectly reflects
the maximum size of data that can be included inside
any packet. Further, it is also a factor affecting chan-
nel bandwidth requirements for transmission of mes-
sages. Normally, synchrophasor systems involve high
data transmission rates. This in turn requires more
channel bandwidth especially if the protocols com-
munication overhead is high.
The overhead for IEEE C37.118-2 is reported in
Table 1 considering different types of messages sent
Table 1: Size of real information and message formatting as
percentage of overall communication overhead (including
headers and protocol scemantics).
Using UDP Using TCP
RealInfo Formatting RealInfo Formatting
Data 26.83 % 21.95 % 3.77 % 3.08 %
Config 86.70 % 3.67 % 40.30 % 1.71 %
Command 3.33 % 26.67 % 0.36 % 2.85 %
Header 21.62 % 21.62 % 2.78 % 2.78 %
over UDP or TCP. It can be observed that the com-
munication overhead is significantly low for Data and
Config messages; the two most frequently exchanged
messages in IEEE C37.118-2 based communication
systems. Compared to UDP, TCP has quite high com-
munication overhead due to exchange of several ad-
ditional packets during connection establishment and
termination.
Fig. 5 depicts how the communication overhead
is affecting with the increasing size of data messages.
The size of real information inside the packet in-
creases when a PDC aggregates data from multiple
PMUs which in turn results in lower communication
overhead. The number of PMUs data inside a PDC
depends on its location. A local/substation PDC may
aggregate data from 10 PMUs whereas regional con-
trol center or super PDC may carry data from up to
1000 PMUs (Grigsby, 2012). Fig. 5 illustrates that
UDP is the most favorable choice to transmit small
size packets. Choosing a low communication over-
head option (i.e., UDP) could significantly reduce
channel bandwidth requirement. However, UDP is a
non-reliable protocol. The TCP could be a suitable
choice for transmission of large size packets (when its
overhead is not significantly high compared to UDP)
to achieve reliability and other benefits offered by
TCP in general.
0
20
40
60
80
100
120
140
5 10 15 20 25 30 35 40 45 50
Overhead Analysis (%)
Number of PMUs
Data + Formatting (UDP)
Communication (UDP)
Data + Formatting (TCP)
Communication (TCP)
Figure 5: Overhead analysis when PDC aggregates data
from multiple PMUs.
IEEE C37.118-2 Synchrophasor Communication Framework - Overview, Cyber Vulnerabilities Analysis and Performance Evaluation
175

6.2 Impact of Latencies
Latency is the critical factor that can impair the per-
formance of real-time applications in three ways: (i)
application latency which is ascribable to encoding
and decoding of different types of messages, (ii) net-
work latency which is time taken by packets to tra-
verse the network, and (iii) transport latency which
is time taken by transport protocol e.g., TCP to ac-
knowledge or retransmit data. Network and transport
latencies are linked with available bandwidth (low
latencies are observed on high bandwidth channels
and vice versa) whereas application latency depends
on the processing power of a given device. Table
2 presents the sum of all three latencies for differ-
ent types of IEEE C37.118-2 messages averaged over
100 transmissions. To avoid clock synchronization is-
sues between sender and receiver, latency measure-
ments were calculated from two-way time measure-
ments. The observed latencies are comparatively low
for UDP than TCP but the difference is not too signif-
icant. It is due to the fact that most of the latency is
ascribable to encoding and decoding of messages on
a low power device i.e., Raspberry Pi. Based on the
values reported in Table 2, there should be ideally no
packet loss if messages are transmitted at appropriate
rate (roughly 90 and 97 data messages per second for
TCP and UDP, respectively). Practically, high data
rates can be easily supported (especially for UDP) us-
ing parallel processing and large size socket buffer.
It can be observed in Table 2 that latencies are dif-
ferent for different types of messages. This is due to
different message size, format and structure. The la-
tencies are expected to increase with increase in mes-
sage size and complexity. Which will in turn affect
the maximum possible data transmission rate. Fig.
6 divides latencies into two parts: (i) time required
to encode the message and send it to receiver de-
vice, and (ii) time required to receive a message, an-
alyze/decode it and extract data. It is apparent from
Fig. 6 that encoding latencies are quite low compared
to decoding latencies. It is due to the fact that PDC
simply aggregates data from multiple PMUs during
the encoding process whereas control application in
decoding process performs deep inspection of re-
ceived packet to separate data of each PMU and ana-
lyze each and every bit according to Config. message.
This obviously depends on the processing power of
the devices performing PDC and control application
functionalities (Raspberry Pi in this case).
Compared to UDP, TCP provides several benefits
such as flow and error control, reliability and guaran-
teed delivery of data. However, TCP is normally not
suggested for high rate real-time transmission of mes-
50
100
150
200
250
300
350
400
10 20 30 40 50 60 70 80 90 100
Latency (ms)
Number of PMUs
Transmission & encoding latency
Transmission & decoding latency
Figure 6: Transmission & encoding/decoding latencies
when PDC aggregates data from multiple PMUs.
sages. To analyze the suitability of TCP for real-time
transmissions, Fig. 7 reports packet loss with increas-
ing data rate. For each data rate, 10,000 packets were
transmitted and number of lost packets were counted.
It can be observed in Fig. 7 that the packet loss in-
creases rapidly with increase in the data transmission
rate. This is due to the fact that each lost packet causes
an interval of packets loss. If TCP waits for the re-
covery of lost packets, data transmission rate will be
affected leaving worst effects on the performance of
real-time applications as well as throughput. Another
limitation of TCP is its incapability to support multi-
cast instead of establishing 1-1 connection which also
increases the network bandwidth requirements.
0
20
40
60
80
100
120
100 200 300 400 500 600 700 800 900 1000
Number of Lost Packets
Data Messages per second
Figure 7: Packet loss with increase in data transmission rate
using TCP as transport protocol.
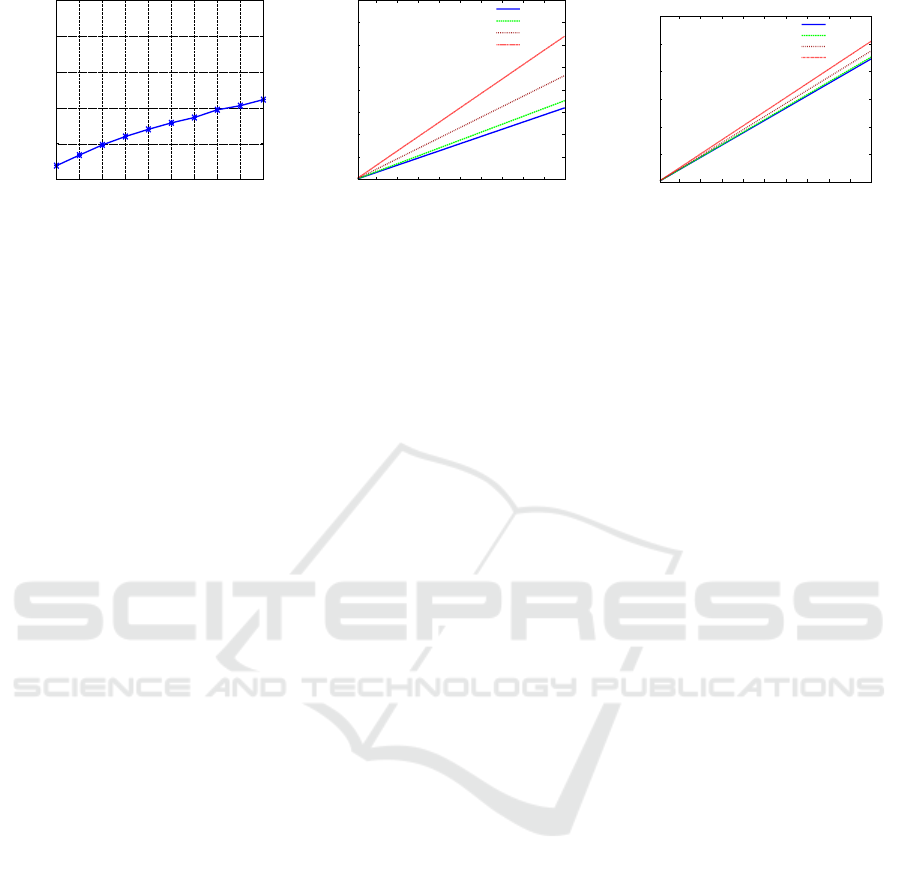
6.3 Resource Requirements
This section analyzes the resource requirements in
terms of CPU and bandwidth. For applications to per-
form well, the minimum required processing power
and bandwidth should be available. Fig. 8 presents
the minimum required resources with increase in data
transmission rate. It can be observed in Fig. 8(a)
ICISSP 2016 - 2nd International Conference on Information Systems Security and Privacy
176

Table 2: Latencies for different types of messages.
Using UDP Using TCP
Min Average Max Std. Dev. Min Average Max Std. Dev.
Data 4.83 ms 10.28 ms 19.71 ms 1.96 ms 9.62 ms 11.07 ms 15.03 ms 1.13 ms
Config 7 ms 8.74 ms 17.26 ms 1.42 ms 7.82 ms 9.57 ms 13.57 ms 1.19 ms
Command 4.07 ms 5.89 ms 9.75 ms 1.39 ms 4.79 ms 6.44 ms 11 ms 1.21 ms
Header 4.17 ms 6.28 ms 13.83 ms 1.54 ms 5.98 ms 7.03 ms 11.89 ms 1.34 ms
that CPU usage of the application increases with in-
crease in data transmission rate. Fig. 8(a) depicts re-
sults obtained on Raspberry Pi and will be different
for other types of devices depending on the available
CPU power. The device processing power also affects
the message encoding/decoding latencies as reported
in Section 6.3.
The bandwidth requirement is the most critical
factor for any communication protocol. High data rate
on low bandwidth links can cause traffic congestion
which will in turn result in packet loss. In computing,
bandwidth is the bit rate or maximum throughput that
can be supported by a given communication medium.
It can be observed in Fig. 8(b) and Fig. 8(c) that band-
width requirement increases linearly with increase in
data transmission rate. Further, the bandwidth re-
quirement depends on the message size. Large size
messages (e.g, including more phasors) have signif-
icant high bandwidth requirement especially at high
data transmission rates. Further, the bandwidth re-
quirement also has strong connection with the com-
munication overhead. TCP communication overhead
is higher than UDP resulting in 3-4 times increase
in bandwidth requirement at a given data rate. With
TCP, IEEE C37.118-2 based communication requires
roughly 500 kbps at 100 data messages per second
transmission rate which is lower than the maximum
bandwidth of most Internet access technologies ex-
cept the dialup (dialup/modem: 56 kbps, ADSL lite:
1.5 Mbps, ADSL1: 8 Mbps, ADSL2+: 24 Mbps,
wireless 802.11b: 11 Mbps, wireless 802.11g: 54
Mbps, wireless 802.11n: 600 Mbps, Gigabit Ethernet:
1 Gbps, etc). Some Internet access technologies may
not provide enough bandwidth for high synchropha-
sor data transmission rates (especially for PDC that
aggregates data from multiple PMUs).
6.4 Remarks
Based on the latencies, observed packet loss and
bandwidth requirement, TCP is an ideal choice only
for low data rate reliable transmissions. Its perfor-
mance gets worse under high data rates and low avail-
able channel bandwidth. On the other hand, UDP has
low bandwidth requirements, has low communication
overhead and does not cause incremental latency in
case of packet loss. This makes it suitable for high
data rate and real-time transmissions. However, it
is unreliable and does not guarantee the delivery of
data. Due to pros and cons of each transport proto-
col, the mixed approach will be ideal choice for IEEE
C37.118-2 based communication system. The mixed
approach will use reliable TCP for infrequent mes-
sages (Config, Command, Header) and non-reliable
UDP for frequent Data messages. The benefits of
mixed approach include reliable transmission of crit-
ical information (e.g., Config message is very impor-
tant for receiver to understand how to decode received
Data messages, Command messages which control
whole communication between two peers, etc) and
minimum latency and low packet loss for real-time
streaming (Data messages). Another advantage of
mixed approach is its suitability for both client-server
as well as multicast mode of transmission.
7 CONCLUSIONS
Synchrophasors have become an integral part of the
modern power system and their applications are con-
tinuously evolving. Many synchrophasor applica-
tions involve transmission of messages over the In-
ternet. IEEE C37.118-2 is the well tested and most
widely used communication standard for transmis-
sion of synchrophasors data. This paper presented
an overview of IEEE C37.118-2 standard highlighting
its main features and capabilities. IEEE C37.118-2
standard does not have any embedded security mech-
anism which makes it highly vulnerable to cyber at-
tacks. This paper analyzed how different types of cy-
ber attacks can exploit vulnerabilities and impact the
operations of any synchrophasor application based on
IEEE C37.118-2.
To overcome IEEE C37.118-2 vulnerabilities, this
paper recommended a GDOI based security mech-
anism and addressed its effectiveness. GDOI pro-
vides enhanced security and protection against man-
in-the-middle, connection hijacking, replay, reflec-
tion and denial-of-service attacks. Finally, the paper
presented detailed performance evaluation of IEEE
C37.118-2 and analyzed network overhead, resource
requirements (e.g., bandwidth, CPU), communication
IEEE C37.118-2 Synchrophasor Communication Framework - Overview, Cyber Vulnerabilities Analysis and Performance Evaluation
177
0
20
40
60
80
100
100 200 300 400 500 600 700 800 900 1000
CPU usage (%)
Data Messages per second
(a) CPU usage
0
20
40
60
80
100
120
140
160
10 20 30 40 50 60 70 80 90 100
Min required capacity (kbps)
Data Messages per second
1 phasor, all integers
1 phasor, all floats
10 phasors, all integers
10 phasors, all floats
(b) Bandwidth (using UDP)
0
100
200
300
400
500
600
10 20 30 40 50 60 70 80 90 100
Min required capacity (kbps)
Data Messages per second
1 phasor, all integers
1 phasor, all floats
10 phasors, all integers
10 phasors, all floats
(c) Bandwidth (using TCP)
Figure 8: Resource requirements with increase in data transmission rate.
latencies and their impact on the data transmission
rate. The reported results provide enough information
about the required resources and network characteris-
tics before designing any synchrophasor application
based on IEEE C37.118-2 standard.
ACKNOWLEDGEMENTS
This work was funded by the EPSRC CAPRICA
project (EP/M002837/1).
REFERENCES
Allgood, G., Bass, L., Brown, B., Brown, K., Griffin, S.,
Ivers, J., Kuruganti, T., Lake, J., Lipson, H., Nutaro,
J., Searle, J., and Smith, B. (2011). Security profile
for wide-area monitoring, protection, and control. In
The UCAIug SG Security Working Group.
Baumeister, T. (2010). Literature review on smart grid cyber
security. In University of Hawaii, Technical Report.
Beasley, C., Zhong, X., Deng, J., Brooks, R., and Ve-
nayagamoorthy, G. K. (2014). A survey of electric
power synchrophasor network cyber security. In 5th
IEEE PES Innovative Smart Grid Technologies Eu-
rope (ISGT Europe). IEEE.
Boyer, W. F. and McBride, S. A. (2009). Study of secu-
rity attributes of smart grid systemscurrent cyber secu-
rity issues. In INL, USDOE, Battelle Energy Alliance
LLC., Rep INL/EXT-09-15500.
Coppolino, L., DAntonio, S., and Romano, L. (2014). Ex-
posing vulnerabilities in electric power grids: An ex-
perimental approach. In International Journal of Crit-
ical Infrastructure Protection vol:7(1), pp:51-60. EL-
SEVIER.
D’Antonio, S., Coppolino, L., Elia, I., and Formicola, V.
(2011). Security issues of a phasor data concentrator
for smart grid infrastructure. In 13th European Work-
shop on Dependable Computing. ACM.
Grigsby, L. L. (2012). Wide-area monitoring and situational
awareness. In Power System Stability and Control -
Third Edition, Volume 5. CRC Press.
Martin, K. E., Hamai, D., Adamiak, M. G., Anderson, S.,
Begovic, M., Benmouyal, G., Brunello, G., Burger,
J., Cai, J. Y., Dickerson, B., Gharpure, V., Kennedy,
B., Karlsson, D., Phadke, A. G., Salj, J., Skendzic,
V., Sperr, J., Song, Y., Huntley, C., Kasztenny,
B., and Price, E. (2008). Exploring the ieee stan-
dard c37.1182005 synchrophasors for power systems.
In IEEE TRANSACTIONS ON POWER DELIVERY,
VOL. 23, NO. 4. IEEE.
Morris, T., Pan, S., Lewis, J., Moorhead, J., Younan, N.,
King, R., Freund, M., and Madani, V. (2011). Cy-
ber security risk testing of substation phasor measure-
ment units and phasor data concentrators. In Seventh
Annual Workshop on Cyber Security and Information
Intelligence Research (CSIIRW ’11). ACM.
Schweitzer, E., Gong, Y., and Donolo, M. (2008). Ad-
vanced real-time synchrophasor applications. In 35th
Annual Western Protective Relay Conference.
Shepard, D., Humphreys, T., and Fansler, A. (2012). Evalu-
ation of the vulnerability of phasor measurement units
to gps spoofing attacks. In International Journal of
Critical Infrastructure Protection.
Sikdar, B. and Chow, J. (2011). Defending synchrophasor
data networks against traffic analysis attacks. In IEEE
Transactions on Smart Grid, Vol:2, Issue: 4. IEEE.
Stewart, J., Maufer, T., Smith, R., Anderson, C., and Er-
sonmez, E. (2011). Synchrophasor security practices.
In 14th Annual Georgia Tech Fault and Disturbance
Analysis Conference.
Weis, B., Rowles, S., and Hardjono, T. (Oct. 2011). The
group domain of interpretation. In Internet Engineer-
ing Task Force (IETF) Request For Comments (RFC):
6407.
Yan, Y., Qian, Y., Sharif, H., and Tipper, D. (2012). A
survey on cyber security for smart grid communi-
cations. In Communications Surveys and Tutorials,
vol.14, no.4, pp.998-1010. IEEE.
Yu, D.-Y., Ranganathan, A., Locher, T., Capkun, S., and
Basin, D. (2014). Short paper: detection of gps spoof-
ing attacks in power grids. In Int. conference on Secu-
rity and privacy in wireless & mobile networks. ACM.
Zargar, S., Joshi, J., and Tipper, D. (2013). A survey of de-
fense mechanisms against distributed denial of service
(ddos) flooding attacks. In Communications Surveys
and Tutorials, vol. 15, no. 4, pp. 2046-2069. IEEE.
ICISSP 2016 - 2nd International Conference on Information Systems Security and Privacy
178
