
A Social-based Strategy for Memory Management in Sensor Networks
Basim Mahmood
1
and Ronaldo Menezes
2
1
Computer and Information Center, University of Mosul, Mosul, Iraq
2
BioComplex Laboratory, Department of Computer Sciences, Florida Institute of Technology, Melbourne, U.S.A.
Keywords:
Wireless Sensor Networks (WSNs), Social Networks, Human Mobility Model, Social Capital, Memory
Management.
Abstract:
The technological structure of today’s societies enables people to easily exchange and share their information.
This structure contains many sophisticated technologies such as mobile wireless devices (e.g., smartphones
and tablets). These devices are mainly used for connecting people with each other. As these devices grow in
usability, many issues have become apparent such as memory management, security, and power consumption.
In this paper, we propose a novel social-based strategy for memory management in mobile sensor networks.
This strategy is inspired from two concepts, namely, social capital in sociology and preferential return mech-
anism in human mobility. The findings show that the proposed strategy is quite effective in keeping up-to-date
information in each sensor/device about the sensor connections. We believe that this is the first work that
investigates the issue of memory management in this type of networks using concepts form social networks
and human mobility.
1 INTRODUCTION
Wireless devices (e.g., smartphones, tablets, laptops)
have become important tools to many aspects of our
lives. These devices support people in different tasks
related to education, business, and social interactions.
Recently, the use of wireless devices has significantly
been increased, especially, with the widespread avail-
ability of the communication technologies (e.g., Wi-
Fi). Therefore, an infrastructure that is formed from
wireless devices and the connections among them al-
ready exists around us. Since these devices are car-
ried by people who tend to be mobile, the considered
infrastructure represents a Dynamic Wireless Sensor
Network (DWSN) in which “sensors” are the mobile
wireless devices and the connections among them are
formed where these devices become in the commu-
nication range of each other. However, many issues
have been introduced when designing applications on
this infrastructure and many challenges have become
apparent such as memory management, power con-
sumption, connectivity, and security.
In the aforementioned DWSN, the connections
among sensors depend on the social relations and
interactions among people. Therefore, understand-
ing the social networks helps the understanding of
how information flows within the network which
eventually may contribute in overcoming connectiv-
ity in these types of networks. The flow of in-
formation within a social network is performed by
passing through the relations among network nodes.
Moreover, the decision of passing information from a
node to another one is more likely based on relation
strength between the individuals. Yet, the strength
of a relation between two individuals depends on the
type of relation they maintain (Burt, 1982)(Borgatti
et al., 1998)(Coleman, 1988). In social networks,
the relations among individuals can be in two types:
strong or weak depending on the behavior and the
level of interactions (e.g., frequency of encounters be-
tween the individual) (Granovetter, 1973). Further-
more, Social Capital is another characteristic in so-
cial networks, by which the importance of a relation
between two individuals can be quantified.
1.1 Social Capital and Homophily
In sociology, the concept of Social Capital refers to
the benefits (economic, political, cultural, etc.) de-
rived from the social relations and cooperation among
social actors (e.g., groups or individuals) (Putnam,
2000). The social capital of an individual, in its sim-
ple case, is the shared norms and values of a connec-
tion with a particular individual (Burt, 1997)(Burt,
2001)(Coleman, 1988). Moreover, (Lin, 1999) de-
fined social capital as “resources embedded in an in-
Mahmood, B. and Menezes, R.
A Social-based Strategy for Memory Management in Sensor Networks.
DOI: 10.5220/0005672600250034
In Proceedings of the 5th International Confererence on Sensor Networks (SENSORNETS 2016), pages 25-34
ISBN: 978-989-758-169-4
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
25

dividual’s social network, resources that can be ac-
cessed or mobilized through ties in the networks”.
Furthermore, social capital is not possessed by people
themselves, but it is embedded in the social relation-
ships among them (Wisconson Center for Education
Research, 2006). (Ehrlich and Carboni, 2005) pre-
sented social capital as the total sum of the resources
that an individual gains as a result of the interactions
and relationships. (Licamele et al., 2005) also defined
the social capital of an individual as the benefits that
are given or received by this individual. Finally, (Jo-
hannessen, 2012) described social capital as the rela-
tions among individuals including the reciprocal trust-
worthiness which makes them more powerful in their
social networks.
The concept of social capital has been used in dif-
ferent studies such as information dissemination in
social networks (Bosen and Gang, 2010). It also de-
scribes many of social ties characteristics (e.g., co-
operation among individuals, and the importance of
a particular social tie), and among these characteris-
tics one can include the classification of ties into weak
and strong as defined by (Granovetter, 1973); clearly
a high social capital needs to include some diversity
between weak and strong tie.
Social Capital however is not a unified concept
and the literature has introduced sub-classifications of
the concept such as public, private, formal, informal,
bonding, bridging, and linking social capital. How-
ever, the main types of social capital in social network
literature are (Adhikari, 2008)(Larsen et al., 2004): 1)
Bonding social capital exist among homogeneous ac-
tors (e.g., friends or family members) and this type is
comprised primarily of strong ties. Hence, bonding
social capital may be appropriate for internal infor-
mation dissemination (e.g., among same group mem-
bers). 2) Bridging social capital exists among hetero-
geneous actors (e.g., across groups). This type incor-
porates mostly the weak ties of an individual and can
be useful in external information dissemination (e.g.,
among different groups). 3) Linking social capital is
also comprised of weak ties but only long-distance
connections making linking social capital also impor-
tant for external information dissemination.
In social sciences and social networks, Homophily
is the tendency of one to associate and connect
with similar others (McPherson et al., 2001)(Ibarra,
1992)(Marsden, 1988). According to the seminal
work of (McPherson et al., 2001), there are two
main aspects of homophily, namely; status homophily
which refers to the fact that individuals with similar
social status features (e.g., race, gender, religion, and
age) are more likely to form ties, and value homophily
which whereby individuals tend to participate with
those who behave and think in similar ways regard-
less of differences in social status. However, value
homophily has more significant impact on homophily
than status homophily as presented in (Yuan and Gay,
2006). Moreover, there are many factors that lead
to homophily such as geography (e.g., people’s co-
location), social ties (e.g., strong and weak ties), or-
ganizational foci (e.g., school or work), isomorphic
sources (e.g., people who occupy equivalent roles),
and cognitive processes (e.g., people who have demo-
graphic similarity) (McPherson et al., 2001). More
importantly, (Lin, 1999) showed that homophily, as a
social characteristic, can affect social capital. (Bor-
gatti and Foster, 2003) and (Borgatti et al., 1998)
found that homophily, tie strength, and high rate of
knowledge transfer (i.e., information flow) between
two individuals have a significant impact on their so-
cial capital.
1.2 Human Mobility
In DWSNs, the term mobility refers to the ability of
nodes (sensors) to move in some way. One of the
ways that sensors move is following a mobility model
which describes the general spatio-temporal regulari-
ties of sensor node movements; more precisely, a mo-
bility model describes the movement of mobile nodes
and how their positions, directions, and speed change
over time (Lin et al., 2004)(Kesidis et al., 2003). Typ-
ically, to simulate and evaluate a DWSN, a particular
mobility model should be incorporated in the network
(Musolesi and Mascolo, 2009). In the context of so-
cial movement, we need to use models that have the
ability to describe most of human mobility character-
istics. (Song et al., 2010) proposed a model for human
mobility to that is able to precisely describe human
movement. Their model is based on two mechanisms:
Exploration: The tendency to explore new locations
decreases with time. This mechanism ensures that
the next step of an individual can be completely
independent of the previously visited locations.
Preferential Return: Humans behavior reflects an
important property, which is the tendency to re-
turn to the most visited locations in the past (e.g.,
home or work).
(Song et al., 2010) represents the state of the art in
modeling of human mobility. Recently other models
have been proposed to focus on irregularities of
human movement (e.g. (Barbosa et al., 2015)) but in
the context of sensor networks, the regularities are
more important because they represent the “normal”
pattern of movement and hence can be exploited in
information dissemination.
SENSORNETS 2016 - 5th International Conference on Sensor Networks
26

1.3 Problem Statement
In the beginning of Section 1, we described the frame-
work we are working with. In this framework, wire-
less devices are carried by people who encounter each
other as a part of their social activities. In the context
of sensor networks, as people encounter each other,
their devices also can establish connections each other
by one of the communication technologies available
(e.g., Bluetooth or Wi-Fi). These encounters should
be stored in the devices’ memories if one wants to
make use of the regularities of encounters in infor-
mation dissemination. The tracking of encounters
requires these devices to remember their history of
encounters. The ability to use this past information
of encounters efficiently depends considerably on the
size of devices’ history. People however are likely
to encounter many others as part of their daily activ-
ities and keeping track of all these encounters adds
a burden to the sensors since it may not be able to
store all the history due to strong memory constraints
in the devices. In our previous work (Mahmood
et al., 2015), we investigated the issue of memory
requirements and predicted the size of memory that
devices should use for tracking purposes. The find-
ings showed that a device needs to be able to track ≈
2.5% of the total number of devices in the environ-
ment (≈0.5% is dedicated for strong ties and ≈2.0%
for weak ties). Moreover, this approximation repre-
sents the maximum number of devices that can be
tracked by a device. When one uses a pre-defined size
of memory for tracking, it may become full and no
space may be available for the new incoming encoun-
ters to be reported during people movement. This
leads to loss some encounters that are perhaps im-
portant to devices and eventually affects, for exam-
ple, data spreading pattern. This situation introduces
the issue of memory management in sensor networks.
To deal with this issue, a decision should be made to
replace one (or more) of the existing item(s) in the
list of encounters with the incoming (new) ones. This
decision should avoid the loss the important encoun-
ters of devices. Therefore, in this work, we propose
a novel social-based approach for memory manage-
ment in sensor networks inspired from two concepts,
namely, social capital in sociology and preferential
return mechanism in human mobility model. In the
former, we calculate the social capital among indi-
viduals based on three indicators: Interaction Level,
Trust Level, and Homophily Level. For the latter, we
involve the recent location of an individual as an indi-
cator to also determine the importance of the current
encounters. Our claim in this work is that using the
aforementioned social concepts can efficiently con-
tribute in managing a device’s memory.
This paper is organized as follows: next section
presents the related works, in Section 3 we describe
the details of our memory management model, Sec-
tion 4, we present the main results, and then we con-
clude our paper in Section 5.
2 RELATED WORKS
The concept of social capital has been used in dif-
ferent network applications such as information dis-
semination in social networks (e.g., knowledge trans-
fer among network nodes). (Bosen and Gang, 2010)
explained the effect of social capital on knowledge
transfer and knowledge creation in organizations.
They studied the ability of organizations to use the
existing resources (e.g., knowledge) and the external
resources effectively for their success. In organiza-
tions, team interactions represent an important factor
in knowledge acquisition and creation within the or-
ganization or among organizations. The interactions
among individuals as proposed in (Smith, 2008) and
(Yao et al., 2014) can be incorporated to the forma-
tion social capital. Therefore, team social capital in
an organization represents the intensity of the inter-
actions within a team or among teams. (Bosen and
Gang, 2010) also showed that team social capital af-
fects team knowledge transfer; when teams promote
and develop their social capital using measures such
as trust, they can transfer knowledge effectively. Fur-
thermore, trust can help to decrease risks in the re-
lationships among team’s members and make them
more likely to share their knowledge (Bosen and
Gang, 2010)(Hsu et al., 2007).
(Lin, 1999) investigated the structural features
(e.g., density) of people relations based on the re-
sources that are embedded in them. He found that
networks can provide the necessary conditions for ac-
cessing and using embedded resources (e.g., knowl-
edge). In addition, he proposed a network theory of
social capital that integrates network structural fea-
tures such as density, reciprocity, openness, closeness,
and homophily. For instance, the density of a network
may increase resource sharing among participant in-
dividuals or groups.
Measuring the value of social capital can be
performed in different methods based on network
structure and available parameters. (Burt, 1997)
showed that social capital is affected by social com-
ponent size, density, and hierarchy between individ-
uals. (Larsen et al., 2004) measured the social capi-
tal among neighbors two neighbors interact and trust
each other in the daily activities. (Licamele et al.,
2005) proposed a friendship-event network which is
A Social-based Strategy for Memory Management in Sensor Networks
27

a specific form of a social network capturing features
of two inter-related networks (a friendship network
and an event network). The event network describes
events, event participants and organizers. Using these
networks, they infer social capital based on the actor-
organizer friendship relationship. Their dataset con-
tains information from three scientific conferences for
ten years. In the findings, they observed that hav-
ing few powerful friends (e.g., high value of social
capital) is more important than having many power-
less friends (e.g., low value of social capital), and this
power can be changed over time. In (Phung et al.,
2013). They proposed an approach to calculate the
social capital of an individual in online social net-
works which uses six indicators: number of friends,
number of community memberships, number of fol-
lowers, number of posts written, number of comments
made per day, and number of comments received per
day. For each indicator, three values are defined: low,
medium, and high based on the activity of an individ-
ual.
(Abdelaal and Ali, 2012) calculated the social
capital in a network out of different wireless networks
by considering three variables: network size, network
density, and the value of a transaction (e.g., collab-
oration) that occur among actors. They found that
social capital is mobilized to empowering communi-
ties to achieve collective telecommunication infras-
tructures. (Bosen and Gang, 2010) and (Zhao and
Wang, 2009) showed how team social capital can sup-
port knowledge transfer more effectively. They used
three social dimensions: structural (e.g., the intensity
of social interactions among team members), cogni-
tive (e.g., shared language, goals, and culture), and
relational (e.g., trust). (Law and Chang, 2012) in-
volved the same social capital factors used in Bosen
and Gang’s work—except the cognitive feature—to
calculate one’s social capital. They observed that
these factors have a significant impact on knowl-
edge transfer. (Smith, 2008) distinguished the con-
nections among individuals as follows: Explicit So-
cial Networks (ESNs) and Implicit Affinity Networks
(IANs). ESNs connect actors together based on a
well-defined relationship (e.g., many features in com-
mon). IANs connect actors based on loosely defined
affinities (e.g., less features in common). Smith also
mentioned that social capital is grounded on relation-
ships, individuals’ attributes, and available social re-
sources. Based on the ESNs and IANs, they calcu-
late two types of social capital; bonding and bridg-
ing social capital. (Subbian et al., 2013b)(Subbian
et al., 2013a) calculated social capital based on the
closeness centrality measurement in social networks.
(Sander and Teh, 2014) showed that social capital
can be determined between two individuals based on
three main characteristics: trust, reciprocity, and in-
vestment (e.g., information sharing).
Overall, the descriptions of the works here tell us
that social capital can be estimated. Despite the differ-
ences in the approaches above, what is important for
our work is that the social capital of individuals can
be extracted from their social network or network of
encounters. Our approach is hence quite general be-
cause one may be able to change how the social cap-
ital is calculated and get different results. This may
be useful in special-purpose scenarios in which social
capital may be better defined according to one of the
works above.
3 MODEL DESCRIPTION
As mentioned in Section 1.3, we propose a novel
social-based replacement strategy for managing
memory in sensor networks. This strategy is inspired
from two social concepts: social capital and prefer-
ential return. The main idea behind our approach is
to have a replacement mechanism, by which the im-
portance of an encounter between two nodes can be
determined and eventually helps the decision of re-
placing items in sensors’ memories.
3.1 Calculating Social Capital
(Burt, 2000) pointed that social capital is dynamic and
should consider indicators that also change of time.
Determining these indicators is subject to the nature
of the adopted infrastructure (see Section 2). In our
work, social capital is calculated based on three indi-
cators defined as follows (see also Figure 1):
Social Interactions (ι): This indicator expresses the
level of interactions among network devices that
contributes in measuring the strength of the rela-
tion between two devices. In this work, three as-
pects are used to measure this level:
• Frequency of Encounters (φ): The frequency of
encounters of a pair of device represents how
many times they encounter in a period of time.
• Duration of Encounters (δ): The duration of
a particular encounter represents how long en-
counters tend to last for.
• Regularity of Encounters (ρ): Provides us with
information about the regularity the encounters
of a pair of devices. More precisely, it repre-
sents the time it generally takes until the pairs
encounter each other again (waiting time).
SENSORNETS 2016 - 5th International Conference on Sensor Networks
28
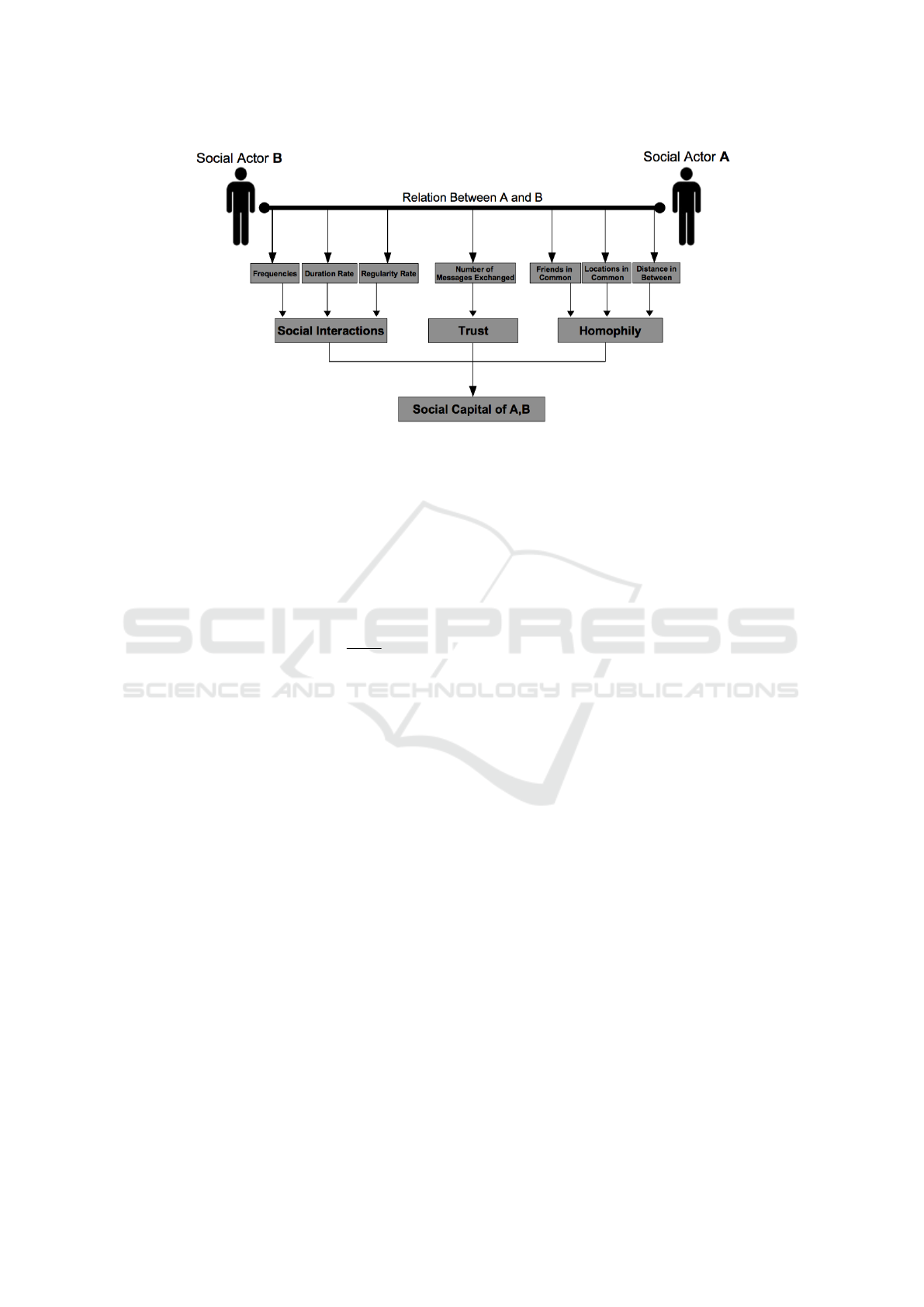
Figure 1: The definition of the social capital of a pair of social actors (individuals) A and B. It can be seen that many social
characteristics are embedded in the relation between A and B and the collective value of these characteristics forms social
capital of the pair A,B.
Based on the aforementioned aspects of social in-
teractions, a relation between two devices is con-
sidered strong when they have high rates of fre-
quency and duration, and low rate of regular-
ity. Now, the interaction level (ι
i j
(t)) between a
pair (i,j) can be calculated based on the following
equation:
ι
i j
(t) = φ
i j
(t) + δ
i j
(t) +
1
ρ
i j
(t)
. (1)
Trust (τ): This indicator reflects the amount of data
exchanged between two devices. This means how
trustworthy they are to share knowledge (Bosen
and Gang, 2010)(Hsu et al., 2007). In our model,
we measured trust of a pair by counting the num-
ber of messages that two devices have exchanged.
Homophily (η): In Section 1.1, we described the
concept of homophily and showed two aspects
of it; status and value homophily. However, us-
ing both aspects in calculating homophily leads
to our model to be over-parameterized. Based on
the study of (Borgatti et al., 1998) on the factors
that affect social capital, which stated that of sta-
tus homophily on social capital is not significant
, we decided to use only value homophily in our
approach:
• Friends In Common (α): Individuals tend to
consider that their friends are like them and also
tend to participate with those who have similar
orientations (McPherson et al., 2001). The ef-
fect of this feature can be on, for example, re-
source sharing among devices.
• Locations In Common (β): Structural posi-
tions of individuals can be used as a reference
of other groups (Festinger, 1950). Yet, indi-
viduals who are more structurally similar are
most likely to have similar vies. Also, they
are more likely to communicate, influence each
other (Burt, 1982)(Friedkin, 1993) and eventu-
ally form social connections (Cho et al., 2011).
• Distance In Between (γ): The distance between
two individuals plays an important role given
that the distance between individuals is a good
measure of how strong the friendship may be
(Preciado et al., 2012).
According to the description above, the ho-
mophily η
i j
(t) of a pair of devices p(i, j) at time
t is:
η
i j
(t) = α
i j
(t) + β
i j
(t) + γ
i j
(2)
Now, given the above three indicators the social
capital (SC) of a pair of devices p(i, j) at time t can
be calculated as follows:
SC
i j
(t) = ι
i j
(t) + τ
i j
(t) + η
i j
(t), (3)
3.2 Preferential Return
In the human mobility model that was proposed by
(Song et al., 2010), the movements of an individual
are based on either exploring new locations (explo-
ration) or return to the previously visited locations
(preferential return). However, according to the study
of (Barbosa et al., 2015), the concept of the second
mechanism (preferential return) can be seen in two
different points of view: return to frequently-visited
locations or return to recently-visited locations. Ac-
cording to their findings, they observed that, in addi-
tion to the tendency to return to the most frequently-
visited locations, the recently-visited locations have
A Social-based Strategy for Memory Management in Sensor Networks
29

also a high visitation probability. Accordingly, we
incorporated the idea of recently-visited locations as
an indicator in our replacement strategy for memory
management (as we will see in the next section). The
reason of using this indicator in our proposed strategy
is that when two individuals recently visited the same
location, the probability of both to visit this location is
high. Therefore, it is more likely for them to become
friends (Burt, 1982)(Friedkin, 1993)(Preciado et al.,
2012).
3.3 The Anticipatory Strategy
We named our approach Memory Anticipatory Strat-
egy (MAS) because it tries to anticipate whether a cur-
rent encounter is important and hence should be “re-
membered”. The main goal of proposing MAS is to
manage a device’s memory when it reaches the maxi-
mum allowable number of items (device IDs) in mem-
ory. The MAS strategy aims to remove one (or more)
of the current items from device’s memory and re-
place it with one (or more) of the new incoming ones.
Determining the maximum number of items that a
device can store in its memory is based on the number
of devices that can be tracked by a particular device.
In our previous work (Mahmood et al., 2015), we in-
vestigated the issue of memory requirements. We ob-
served that a device can keep track ≈2.5% of devices
in the environment (e.g., a city), we also observed that
strong ties take about ≈0.5% and ≈2.0% for weak
ties. Based on these results, we consider the maxi-
mum number of items that a device can store in its
memory to be ≈2.5% of the total number of devices
in the environment.
While devices move in the simulation environ-
ment, they encounter each other; some of these en-
counters are important while others are not. Ideally
one would prefer to have a a full history of encoun-
ters in the devices’ memories. However, a device’s
memory is limited may become full due to the large
number of encounters. The MAS strategy starts when
a device’s memory contains the maximum allowable
number of items. It performs two basic operations as
follows:
Add Operation: A device adds an item into its mem-
ory if both the current encountered devices re-
cently visited the same location—the most recent
one according to (Barbosa et al., 2015)–this is also
called the adding condition.
Remove Operation: A device removes the item that
has least value of social capital in its memory if
the adding condition holds true.
For a better understanding of how the MAS strategy
works, a scenario is considered as follows: Consider
A as a device with maximum allowable items in mem-
ory equal to 2. The current items in A’s memory are X
and Y with social capital values of 2.5 and 4.0 respec-
tively, and the recent location of A is `
i
. Furthermore,
consider that A currently encountered two other de-
vices in the environment B and C and their recent lo-
cations `
i
and `
j
respectively. The status of A’s mem-
ory is currently full. In such case, our model uses the
MAS strategy to decide whether adding B, C, both,
or neither is necessary. However, to add an item into
A’s memory, the recent-location of B and/or C must
be the same of A’s recent-location. In this scenario,
B has the same recent location of A which is `
i
. This
means, B is a candidate to be added into A’s memory.
Now, the item that should be removed from A’s mem-
ory must be chosen. MAS chooses the item that has
least value of social capital among A’s items: X in this
case. Finally, MAS removes X then adds B. The rea-
son of choosing B rather than C is the probability of B
to encounter A is high in the future (more important).
This means, the probability of them to be friends is
also high (as explained in Section 3.2). There are also
some other cases that MAS strategy performs, such
that, if two items D and E have the same recent loca-
tion of A, MAS removes two items from A’s memory
that have least value of social capital among A’s items
and adds both D and E.
Algorithm 1 shows the process of removing and
adding item(s) into a device’s memory. In this algo-
rithm, A is a device in the environment. The maxi-
mum number of items that each device can store is
Max
limit
. A contains items that were previously added
A
items
. Also, E
items
is a list that contains the devices
that are currently near the device A (the list of devices
encountered by A).
Algorithm 1: Illustrates the main steps of MAS strategy for
managing the memory of a device.
1: INPUT: E
items
, A
items
, and Max
limit
2: for each item ∈ (A
items
∩ E
items
) do
3: Update SocialCapital using Equation 3
4: end for
5: MinScItem = Minimum Social Capital ∈ A
items
6: if Length(A
items
) = Max
limit
then
7: for each item ∈ E
items
do
8: if RecentLocation(item) =
RecentLocation(A) then
9: remove MinScItem from A
items
10: add item into A
items
11: Initiate the social capital of item
12: end if
13: end for
14: end if
SENSORNETS 2016 - 5th International Conference on Sensor Networks
30

The MAS strategy can be summarized as follows:
• Only local information is used in the processes.
This means a device does not request any external
information (e.g., network level parameters) that
cannot be accessed directly by the device.
• The MAS strategy always provides devices with
weak ties, and avoid keeping only strong ties in
memory. More precisely, when adding an item to
a device’s memory, MAS does not take into con-
sideration its social capital value. The item that is
added may have a smaller social capital than the
removed one.
• MAS calculations are dynamic and on-the-fly, this
means at every time step a device uses the MAS
strategy if an encounter occurs.
• MAS is a social-inspired approach, in which two
social concepts are involved; social capital and the
social behavior of human movements.
4 EXPERIMENTAL RESULTS
4.1 Simulation Environment
The simulation environment we designed is imple-
mented as follows: a squared city of 10 × 10 km,
the city consists of 100 × 100 squared blocks. About
2000 mobile nodes are exponentially distributed in
the city because most metropolises follow this distri-
bution (Grossman-Clarke et al., 2005). Each mobile
node represents an individual who carries a wireless
mobile device (e.g., smartphone, tablet, or laptop).
Wi-Fi technology is used for connecting devices with
range of ≈50 meters, the communication type is peer-
to-peer based. In the environment, each node moves
at a fixed velocity of 1 block per tick. Given the en-
vironment dimensions, a tick is equal to 1.2 minute in
real time considering that each device is carried by
humans who have an average walking speed is ≈5
km/h (Metta et al., 2006). Finally, the nodes move
based on human mobility model (Song et al., 2010)
(as described in Section 1.2).
4.2 Benchmarking Approaches
In this work, two well-known approaches (FIFO and
LRU)
1
—that are used in page replacement algorithms
in operating systems—were used to benchmark the
our proposed approach (MAS):
1
We benchmark our approach against these two approaches
because they fit the social framework we are dealing with.
FIFO Algorithm: The first-in-first-out is the most
popular algorithm when it comes to memory man-
agement in operating systems. In this algorithm,
an item that is added first will be removed first
(Hopcroft et al., 1983). It is widely used as a base-
line by researchers to benchmark their approaches
(Galvin et al., 2013).
Marking-LRU Algorithm: Marking algorithms
represent a general class of replacement al-
gorithms that are based on the reference (e.g.,
reference bit) to recent use of a page (O’neil et al.,
1993). Least-Recently-Used (LRU) is a marking
algorithm in which a page that is recently used
is marked (e.g., reference bit is set). LRU is
also used for benchmarking other approaches. It
works based on two mechanisms; 1) it memorizes
the pages that has recently been used. 2) Replace
the pages that have not been used for longest time.
In our model, we implemented LRU by applying
its mechanisms as follows. For each device,
we use a list of recent encounters (recent-list),
in which we store only the IDs of the recent
encountered devices without considering other
encounter information
2
. When device’s memory
reaches the maximum limit and a new encounter
occur, LRU removes the least recent encounter
from device’s memory and adds an item from the
recent-list of that device under the condition that
there is at least one of the new encountered items
in the recent-list (candidate item). Practically,
this means that the candidate item is used more
frequently than the one that is removed.
4.3 Experimental Results
We have implemented the proposed approach (MAS)
plus two others used for comparison purposes:
Marking-LRU and FIFO. The replacement rate is the
metric used for benchmarking MAS. The replacement
rate represents the average replacements of all sensors
over times. Consider the number of replacements of
sensor i at time t is R
i
(t), then:
ReplacementRate(t) =
∑
n
i=1
R
i
(t)
n
, (4)
where n is the number of devices that are deployed in
the environment.
Figure 2 depicts the cumulative replacement rate
of the modeled approaches. Clearly, MAS reflects
lower replacement rate because it infrequently re-
places items in memory. This is a positive result be-
cause it reflects the known fact that our weak and
2
The recent-list is used only to support the decision of
which item in this list will be stored in the memory of that
device.
A Social-based Strategy for Memory Management in Sensor Networks
31
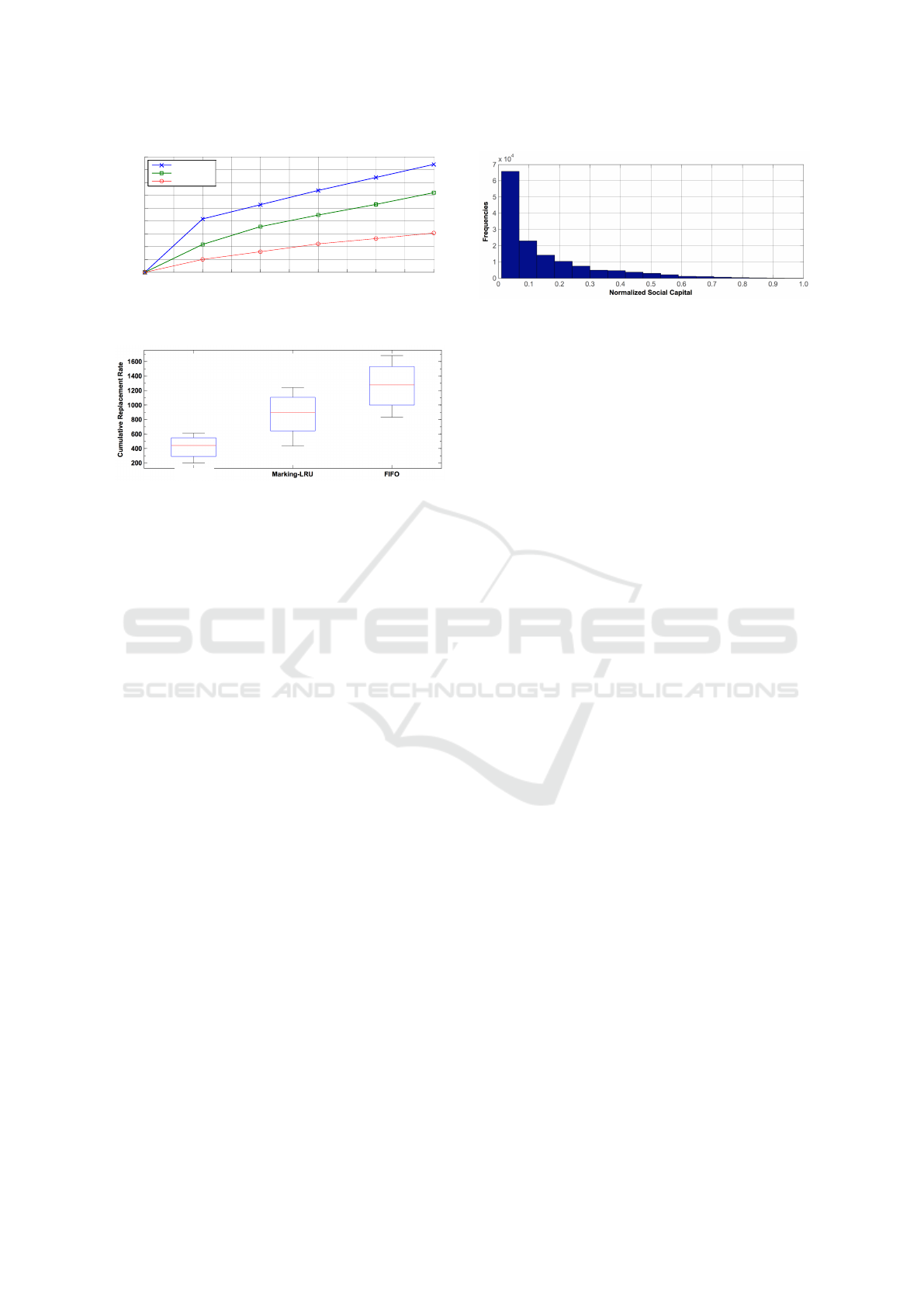
Figure 2: Cumulative replacement rate of MAS, Marking-
LRU, and FIFO approaches.
MAS
Figure 3: Showing the variations (variance) in dissemina-
tion distance for each of the modeled approaches. The vari-
ance for each approach is obtained from all the runs (100
runs for each approach).
strong ties do not to tend to change frequently. FIFO
replaces an item at every new encounter and Marking-
LRU is more likely to replace an item when encoun-
tering new devices leading to them displaying higher
rate of replacements.
Furthermore, we investigate the behavior of the
three approaches in terms of variance. Figure 3 shows
the variance of each approach. Note that MAS has a
smaller variance than the competitive ones.
However, the above findings are not significant be-
cause they do not provide details on the differences
among the approaches. Therefore, we decide to statis-
tically confirm these results. One-Way ANOVA is used
to show whether the means µ of the approaches are
similar. Our null hypothesis states that all the means
are equal while the alternative hypothesis states that
they are are not equal as follows:
H
0
: µ
(MAS)
= µ
(Marking-LRU)
= µ
(FIFO)
H
a
: µ
(MAS)
6= µ
(Marking-LRU)
6= µ
(FIFO)
The output of ANOVA shows that F-statistics =
11.26 and the p-value = 0.001. Given these results, we
cannot accept the null hypothesis which confirms that
there is a difference in the means of the approaches.
Now, we need to verify if these differences are sta-
tistically significant. To this end, we compute a pair-
wise multiple comparisons among the modeled ap-
proaches using Bonferroni’s Test (Bonferroni, 1936)
with 95% of confidence. It can be observed that the
difference between the pair (MAS, FIFO) with a p-
value of 0.004 is significant. Besides that, the p-
value of the pair (MAS, Marking-LRU) equals 0.003
Figure 4: The distribution of social capital among devices
follows a power-law distribution.
which is also significant. Therefore, it can be inferred
that our proposed approach (MAS) outperforms the
benchmarking approaches in terms of replacement
rate and variance.
Figure 4 shows the distribution of social capital
among devices in the environment. Clearly, it follows
a power-law distribution. Based on the framework we
are working on, the social interactions of a pair of
devices is symmetric (see Section 3.1). For example,
consider two devices A and B, and also that they are
in each other’s memory. After a while, A removed
B from its memory (A still in B’s memory) due to
an important encounter that causes B to be removed.
However, when A and B encounter again leading to A
adding B back into its memory, it can retrieve from B
all information about their history. This characteristic
is important insofar as it contributes in keeping a more
historical tie strength.
In our previous work (Mahmood et al., 2015), we
involved the interactions among nodes (e.g., frequen-
cies, duration, and regularities of encounters) in or-
der to measure the strength of relations among nodes.
In this work, the calculations of social capital also
include the interactions among network nodes—the
strength of a tie is embedded in the social capital of
the relation itself (Lin, 1999)(Borgatti et al., 1998).
This work then builds from our previous results to
generalize the concepts of interactions into the con-
cept of social capital value.
Our findings show that the Remove Operation in
the MAS approach avoids losing strong ties from
memory while the Add Operation provides memory
with weak ties in the same time. The overall outcome
is a good balance between weak and strong ties as
shown in Figure 4. The distribution shows few sen-
sors with high social capital (strong ties) and many
values with low social capital (weak ties).
5 CONCLUSIONS
In this work, we proposed a novel social-based re-
placement strategy (Memory Anticipatory Strategy)
SENSORNETS 2016 - 5th International Conference on Sensor Networks
32

for memory management in sensor networks. This
strategy is based on two social concepts: the idea
of Social Capital in sociology and the Preferen-
tial Return mechanism in human mobility model-
ing. The proposed strategy is benchmarked with two
well-known approaches (FIFO and Marking-LRU) in
memory management literature. The findings show
that our approach outperforms the comparative ap-
proaches in terms of replacement rate and variations
and that it can successfully maintain a 80-20 ratio be-
tween weak and strong ties. Our approach avoids los-
ing strong ties that are important to a particular device
and provides memory with weak ties.
ACKNOWLEDGEMENTS
The authors would like to thank Marcello Tomasini
for his invaluable inputs during the preparation of this
manuscript.
REFERENCES
Abdelaal, A. and Ali, H. (2012). Measuring social capital in
the domain of community wireless networks. In Sys-
tem Science (HICSS), 2012 45th Hawaii International
Conference on, pages 4850–4859.
Adhikari, K. P. (May 2008). Bridging, linking, and bonding
social capital in collective action. Collective Action
and property rights CAPRi.
Barbosa, H., de Lima Neto, F. B., Evsukoff, A., and
Menezes, R. (2015). The effect of recency to human
mobility. European Physical Journal Data Science (in
press).
Bonferroni, C. E. (1936). Teoria statistica delle classi e cal-
colo delle probabilita. Libreria internazionale Seeber.
Borgatti, S. P. and Foster, P. C. (2003). The network
paradigm in organizational research: A review and ty-
pology. Journal of management, 29(6):991–1013.
Borgatti, S. P., Jones, C., and Everett, M. G. (1998).
Network measures of social capital. Connections,
21(2):27–36.
Bosen, L. and Gang, Q. (2010). Relationship between
team social capital and knowledge transfer: The me-
diated effect of tms. In E-Product E-Service and E-
Entertainment (ICEEE), 2010 International Confer-
ence on, pages 1–4.
Burt, R. S. (1982). Toward a structural theory of action:
network models of social Structure, Perception, and
Action. Academic Press.
Burt, R. S. (1997). The contingent value of social capital.
Administrative science quarterly, pages 339–365.
Burt, R. S. (2000). Decay functions. Social networks,
22(1):1–28.
Burt, R. S. (2001). Structural holes versus network closure
as social capital. Social capital: Theory and research,
pages 31–56.
Cho, E., Myers, S., and Leskovec, J. (2011). Friendship
and mobility: user movement in location-based social
networks. In KDD ’11 Proceedings of the 17th ACM
SIGKDD international conference on Knowledge dis-
covery and data mining, pages 1082–1090, New York.
ACM.
Coleman, J. S. (1988). Social capital in the creation of hu-
man capital. American journal of sociology, pages
S95–S120.
Ehrlich, K. and Carboni, I. (2005). Inside social network
analysis. Boston College.
Festinger, L. (1950). Informal social communication. Psy-
chological review, 57(5):271.
Friedkin, N. E. (1993). Structural bases of interpersonal
influence in groups: A longitudinal case study. Amer-
ican Sociological Review, pages 861–872.
Galvin, P. B., Gagne, G., and Silberschatz, A. (2013). Op-
erating system concepts. John Wiley & Sons, Inc.
Granovetter, M. S. (1973). The strength of weak ties. Amer-
ican journal of sociology, pages 1360–1380.
Grossman-Clarke, S., Zehnder, J. A., Stefanov, W. L., Liu,
Y., and Zoldak, M. A. (2005). Urban modifications in
a mesoscale meteorological model and the effects on
near-surface variables in an arid metropolitan region.
Journal of Applied Meteorology, 44(9):1281–1297.
Hopcroft, J. E., Ullman, J. D., and Aho, A. V. (1983). Data
structures and algorithms. Addison-Wesley Boston,
MA, USA:.
Hsu, M.-H., Ju, T. L., Yen, C.-H., and Chang, C.-M. (2007).
Knowledge sharing behavior in virtual communities:
The relationship between trust, self-efficacy, and out-
come expectations. International Journal of Human-
Computer Studies, 65(2):153–169.
Ibarra, H. (1992). Homophily and differential returns: Sex
differences in network structure and access in an ad-
vertising firm. Administrative science quarterly, pages
422–447.
Johannessen, M. (2012). Social capital and the networked
public sphere: Implications for political social media
sites. In System Science (HICSS), 2012 45th Hawaii
International Conference on, pages 2573–2582.
Kesidis, G., Konstantopoulos, T., and Phoha, S. (2003).
Surveillance coverage of sensor networks under a ran-
dom mobility strategy. In Sensors, Proceedings, vol-
ume 2, pages 961–965. IEEE.
Larsen, L., Harlan, S. L., Bolin, B., Hackett, E. J., Hope, D.,
Kirby, A., Nelson, A., Rex, T. R., and Wolf, S. (2004).
Bonding and bridging understanding the relationship
between social capital and civic action. Journal of
Planning Education and Research, 24(1):64–77.
Law, S. and Chang, M.-K. (2012). Social capital and knowl-
edge sharing in online communities: A mediation
model. In System Science (HICSS), 2012 45th Hawaii
International Conference on, pages 3530–3539.
Licamele, L., Bilgic, M., Getoor, L., and Roussopoulos, N.
(2005). Capital and benefit in social networks. In Pro-
ceedings of the 3rd International Workshop on Link
A Social-based Strategy for Memory Management in Sensor Networks
33

Discovery, LinkKDD ’05, pages 44–51, New York,
NY, USA. ACM.
Lin, G., Noubir, G., and Rajaraman, R. (2004). Mobil-
ity models for ad hoc network simulation. In INFO-
COM 2004. Twenty-third AnnualJoint Conference of
the IEEE Computer and Communications Societies,
volume 1. IEEE.
Lin, N. (1999). Building a network theory of social capital.
Connections, 22(1):28–51.
Mahmood, B., Tomasini, M., and Menezes, R. (2015). Es-
timating memory requirements in wireless sensor net-
works using social tie strengths. In Local Computer
Networks Workshops (LCN Workshops), (SenseApp)
2015 IEEE 40th Conference on. IEEE.
Marsden, P. V. (1988). Homogeneity in confiding relations.
Social networks, 10(1):57–76.
McPherson, M., Smith-Lovin, L., and Cook, J. M. (2001).
Birds of a feather: Homophily in social networks. An-
nual review of sociology, pages 415–444.
Metta, G., Fitzpatrick, P., and Natale, L. (2006). Yarp: yet
another robot platform. International Journal on Ad-
vanced Robotics Systems, 3(1):43–48.
Musolesi, M. and Mascolo, C. (2009). Mobility mod-
els for systems evaluation. In Middleware for Net-
work Eccentric and Mobile Applications, pages 43–
62. Springer.
O’neil, E. J., O’neil, P. E., and Weikum, G. (1993). The lru-
k page replacement algorithm for database disk buffer-
ing. ACM SIGMOD Record, 22(2):297–306.
Phung, D., Gupta, S., Nguyen, T., and Venkatesh, S. (2013).
Connectivity, online social capital, and mood: A
bayesian nonparametric analysis. Multimedia, IEEE
Transactions on, 15(6):1316–1325.
Preciado, P., Snijders, T. A., Burk, W. J., Stattin, H., and
Kerr, M. (2012). Does proximity matter? distance de-
pendence of adolescent friendships. Social networks,
34(1):18–31.
Putnam, R. D. (2000). Bowling alone: The collapse and
revival of american community. In Proceedings of the
2000 ACM Conference on Computer Supported Coop-
erative Work, CSCW ’00, pages 357–, New York, NY,
USA. ACM.
Sander, T. and Teh, P.-L. (2014). Determining the indica-
tors of social capital theory to social network sites. In
User Science and Engineering (i-USEr), 2014 3rd In-
ternational Conference on, pages 264–268.
Smith, M. S. (2008). Social capital in online communities.
In Proceedings of the 2Nd PhD Workshop on Informa-
tion and Knowledge Management, PIKM ’08, pages
17–24, New York, NY, USA. ACM.
Song, C., Koren, T., Wang, P., and Barab
´
asi, A.-L. (2010).
Modelling the scaling properties of human mobility.
Nature Physics, 6(10):818–823.
Subbian, K., Sharma, D., Wen, Z., and Srivastava, J.
(2013a). Finding influencers in networks using so-
cial capital. In Advances in Social Networks Analy-
sis and Mining (ASONAM), 2013 IEEE/ACM Interna-
tional Conference on, pages 592–599.
Subbian, K., Sharma, D., Wen, Z., and Srivastava, J.
(2013b). Social capital: The power of influencers in
networks. In Proceedings of the 2013 International
Conference on Autonomous Agents and Multi-agent
Systems, AAMAS ’13, pages 1243–1244, Richland,
SC. International Foundation for Autonomous Agents
and Multiagent Systems.
Wisconson Center for Education Research (2006). Families
and school together. social capital: social capital as a
theoretical construct. Technical report, University of
Wisconsin-Madison.
Yao, C.-Y., Tsai, C.-C., and Fang, Y.-C. (2014). Under-
standing social capital, team learning, members’ e-
loyalty and knowledge sharing in virtual communities.
Total Quality Management and Business Excellence,
pages 1–13.
Yuan, Y. C. and Gay, G. (2006). Homophily of network ties
and bonding and bridging social capital in computer-
mediated distributed teams. Journal of Computer-
Mediated Communication, 11(4):1062–1084.
Zhao, Y. and Wang, Y. (2009). Research on the knowl-
edge transfer among enterprise network: A perspec-
tive from social capital. In Knowledge Acquisition and
Modeling, 2009. KAM ’09. Second International Sym-
posium on, volume 2, pages 379–382.
SENSORNETS 2016 - 5th International Conference on Sensor Networks
34
