
Modelling of Quantum Key Distribution Protocols in Communicating
Quantum Processes Language with Verification and Analysis in PRISM
Satya Kuppam
University of Massachusetts, Amherst, U.S.A.
Keywords:
PRISM, Modelling, Analysis, Verification, Quantum Cryptography, Communicating Quantum Processes,
π-calculus.
Abstract:
Proof of security of cryptography protocols theoretically establishes the strength of a protocol and the con-
straints under which it can perform, it does not take into account the overall design of the protocol. In the past
model checking has been successfully applied to classical cryptography protocols to weed out design flaws
which would have otherwise gone unnoticed. Quantum key distribution protocols differ from their classical
counterparts, in their ability to detect the presence of an eavesdropper while exchanging the key. Although
unconditional security has been proven for both BB84(Mayers, 2002) and B92(Quan and Chaojing, 2002) key
distribution protocols, in this paper we show that identifying an eavesdropper’s presence is constrained on the
number of qubits exchanged. We first model the protocols in Communicating Quantum Processes (CQP)(Gay
and Nagarajan, 2005)(Davidson, 2012) and then explain the mechanism by which we have translated this into
a PRISM model and how we analysed the protocols’ capabilities. We mainly focus on the protocols’ ability
to detect an active eavesdropper and the extent to which an eavesdropper can retrieve the shared key without
being detected by either party. We then conclude by comparing the performance of the protocols.
1 INTRODUCTION
Quantum cryptographic protocols have garnered
much acclaim in the last two decades for their ability
to provide unconditional security, which is not prac-
tically assured by their classical counterparts. Com-
mercial availability of quantum infrastructure in the
last decade has placed even more emphasis on de-
veloping methodologies to ascertain the reliability of
protocols in practice. Even though, protocols are the-
oretically secure, our experience with classical proto-
cols has shown that security can be compromised dur-
ing implementation. Since modelling, analysing and
verifying classical protocols have worked so well, de-
veloping techniques along these lines seems prudent
for quantum cryptography protocols as well.
The cornerstone of quantum cryptography proto-
cols is the inherent probabilistic nature. Unlike classi-
cal key distribution protocols (KD) which accommo-
dates a passive eavesdropper, wherein the eavesdrop-
per can copy the bits and analyse them later, quantum
key-distribution protocols (QKD) mandate an active
eavesdropper. This constraint is promulgated by the
no-cloning(Bu
ˇ
zek and Hillery, 1996) theorem which
handicaps the eavesdropper from copying qubits. In
trying to extract the bit value from the qubit the eaves-
dropper will make some ’measurements’ which will
’corrupt’ the qubits and make her presence known to
parties trying to establish a key (section 2). More-
over, quantum protocols also involve both classical
and quantum channels. Therefore we need a lan-
guage that is capable of modelling probabilistic phe-
nomenon and also takes into account both classical
and quantum communications.
Communicating Quantum Processes (CQP)(Gay
and Nagarajan, 2005) is a language developed with
the expert purpose of modelling quantum proto-
cols. CQP uses the communication primitives of pi-
calculus(Milner, 1999) and has capabilities for apply-
ing unitary operators, performing measurements, and
a static type system that differentiates between classi-
cal and quantum communications. Hence CQP seems
an obvious choice for modelling quantum protocols.
PRISM allows us to model probabilistic transitions,
as we show later, this allows to seamlessly translate a
CQP model into a PRISM model.
Previous work on analysis of BB84 by Papaniko-
laou (Gay et al., 2005) has reasoned about the prob-
ability of detecting an eavesdropper and corroborates
the claim made by Mayers in his proof of uncondi-
Kuppam, S.
Modelling of Quantum Key Distribution Protocols in Communicating Quantum Processes Language with Verification and Analysis in PRISM.
DOI: 10.5220/0006834500750082
In Proceedings of 8th International Conference on Simulation and Modeling Methodologies, Technologies and Applications (SIMULTECH 2018), pages 75-82
ISBN: 978-989-758-323-0
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
75

tional security of BB84. However, this work does not
model BB84 in CQP. We first model BB84 in CQP,
convert the CQP model into PRSIM and check the va-
lidity of the observations made by Papanikolaou(Gay
et al., 2005). We then proceed to show that B92’s
eavesdropping detection capabilities can be reasoned
along the same lines.
To ensure brevity we have refrained from explain-
ing Quantum Mechanical primitives like unitary op-
erators, measurements and no-cloning theorem. One
good resource is Nielsen and Chuang’s work(Nielsen
and Chuang, 2010). Also, we have only provided
an elementary introduction to CQP, only to the ex-
tent to which we use it in this paper. A better and
comprehensive resource would be Thimothy David-
son’s(Davidson, 2012) doctoral thesis.
2 PRELIMINARIES
The quantum counterparts of the classical bits are
called ’qubits’. We can consider bits as being voltages
with a high voltage representing a ’1’ bit and a low
voltage representing a ’0’ bit or vice-versa. Qubits on
the other hand represent some quantum mechanical
property of a photon, atom or a subatomic particle.
For example one can say that in a hydrogen atom if
the electron is in the ground state then it encodes a ’0’
bit, but if it is in an excited state it encodes a ’1’ bit. It
is not necessary that the electron has to reside in either
of these two states, it can also reside in a superposi-
tion of the ground state and the excited state. One can
perform a ’quantum measurement’ to determine if the
electron is present in the ground state or the excited
state.
2.1 Quantum Measurement
It is inherent with any quantum mechanical system
that any measurement done on the system will in-
duce some irreversible disturbances. We are going to
rely on this property of qubits heavily in any quantum
cryptographic protocols. Any quantum system can be
represented as a vector in an n dimensional complex
Hilbert space. Measuring this quantum system can
only give a set of priviliged results namely those as-
sociated with the basis vectors of the state space.
For example, consider a 2-dimensional complex
Hilbert space with
|
0
i
and
|
1
i
as basis vectors. Lets
say the vector
|
ψ
i
= α
|
0
i
+ β
|
1
i
describes the sys-
tem where α, β ∈ C. If we try to measure the system
in the basis {0,1}, then the system changes to a new
state, either
|
ψ
0
i
=
|
0
i
or
|
ψ
0
i
=
|
1
i
permanently. It
has a probability |α|
2
of changing into
|
ψ
0
i
=
|
0
i
and
a probability |β|
2
of changing into
|
ψ
0
i
=
|
1
i
. Also,
|α|
2
+ |β|
2
= 1. We can also measure the system in
whichever basis that we choose. Lets measure the sys-
tem in another basis {+,−}, where
|
+
i
=
1
√
2
(
|
0
i
+
|
1
i
and
|
−
i
=
1
√
2
(
|
0
i
−
|
1
i
, then
the quantum state can be represented as
|
ψ
i
=
(α+β)
√
2
(
|
+
i
) +
(α−β)
√
2
(
|
−
i
).
Measuring this system in the basis {+, −} will yield
|
+
i
and
|
−
i
with probability
(α+β)
2
2
and
(α−β)
2
2
re-
spectively.
2.2 BB84 QKD Protocol
A and B want to establish a secret for secure com-
munication. A sends the encoding of some bits in the
+,×basis to B on the quantum channel. The +basis is
called the rectilinear basis and the ×basis is called the
diagonal basis. B then chooses a random sequences of
bases and measures the qubit sent by A in that basis.
If the basis of Alice and Bob are equal then the B ob-
tains the classical bit chosen by Alice other wise she
randomly gets {0,1}. A and B then use the classical
channel to exchange some of the basis from the ran-
dom sequence and the corresponding measurements
of qubits to decide upon a shared key or to detect the
presence of an eavesdropper.
2.3 B92 QKD Protocol
Unlike BB84 where each classical bit has two differ-
ent encoding depending on the basis used, B92 has
only one. In other words there is a one to one cor-
respondence between the classical bits and qubits ex-
changed. If Alice wants to send a classical bit 0 to
Bob she sends →and if she wants to send 1 she sends
%. The rest of the steps involved are the same as in
BB84.
2.4 Eavesdropping Attacker
As mentioned earlier, whenever Eve measures the
qubits that are in transit to Bob from Alice, she
makes a permanent change to the state of qubits if she
doesn’t use the same basis as that of Alice. In BB84
protocol if on some qubits both Alice and Bob use the
same basis to encode and measure but Bob decodes
a classical bit different from what Alice encoded,
suggests the presence of Eve. In B92 as well, Al-
ice and Bob should obtain the opposite results when
the encoding basis is the same, then an attacker is
present. We are assuming the qubit channel shared
by all the participants noiseless. The eavesdropping
SIMULTECH 2018 - 8th International Conference on Simulation and Modeling Methodologies, Technologies and Applications
76

attacker has two capabilities, first of those is random-
substitution wherein the attacker’s main aim is to dis-
rupt the key exchange process by randomly dropping
qubits and introducing new ones and the second is
called intercept-resend wherein the attacker takes a
qubit makes an observation and re-sends the qubit to
the intended destination. In this type of attack the
main motive is to gain information about the key be-
ing exchanged. We analyse how the protocols per-
form in both these settings.
3 FORMALISING IN CQP
A brief overview of CQP calculus is provided and
then we proceed to formalise both the protocols in
CQP. An example of BB84-Bit Commitment Proto-
col in CQP(Gay and Nagarajan, 2005) was given by
Simon and Gay and our formalisation uses the same
techniques.
A protocol at any given point of time has mul-
tiple participants, like Alice and Bob which are le-
gitimate entities involved and also adversaries like
Eve. These entities are collectively known as agents.
Agents communicate with each other via communi-
cation channels to exchange information. The work-
ing of the agents is encapsulated by processes. Every
agent has more than one process, and at any given
time its possible that more than one process is in ac-
tion. These processes can be reasonably thought of as
states in finite state automata and every process tran-
sitions to another or terminates. CQP allows us to
impose a probabilistic distribution across these tran-
sitions. Also processes in CQP can be parameterised.
1. channels are declared by the new keyword.
For example to declare a new qubit channel, we
write (new qubitChannel:ˆ[Qbit]), where Qbit is
the data type qubitChannel is constrained to and
’ˆ’ identifies it as a channel.
2. variables can be declared within a process like so,
(qbit q).
3. Process Output: c![x].P
i+1
to send the data stored
by variable x along channel c and then proceed
with process P
i+1
.
4. Process Input: c?[x].P
i+1
to receive along channel
c and then proceed with process P
i+1
.
5. Process action: e.P
i+1
evaluates expression e and
then proceeds with process P
i+1
6. Process decision: if e thenP
i+1
elseP
i+2
if the
expression e evaluates to true then proceed with
process P
i+1
else P
i+2
7. Terminate: P
i
.0 the process terminates after P
i
.
3.1 Formalising BB84
We identify that Alice, Bob are the primary agents of
the protocol and to analyse the effects of an eaves-
dropper, Eve becomes an agent of the system as well.
As described above channels can only transport mes-
sages of a particular type. We have qubitChannel
to transport qubits, intChannel for integers and deci-
sionChannel, decisionFlagChannel, randomBitChan-
nel for bits. Technically one bit channel would suf-
fice.
However having two different channels that are
used at two different stages in the protocol helps us to
convert the CQP-model into PRISM as will be elab-
orated in the next section. We have also made use of
List type, with its associated functions of hd, tl, [] and
@ for reading the first element, dropping the first ele-
ment, an empty list and placing data at the tail of the
list respectively. The use of these functions is demon-
strated by Gay et al.(Gay and Nagarajan, 2005).
• System is parameterised by a bitList, which consti-
tutes the classical bits that need to be exchanged
between Alice and Bob Random agent creates a
random bit and sends it via the radomBitChannel
Alice first sends the length of the number of bits
to be exchanged with Bob, i.e the length of bitList.
Upon sending the length of the bit list, Alice con-
tinues with the process AliceSend. This is a recur-
sive process which terminates after sending all the
bits in bitList. AliceSend first receives a random
bit from randomBitChannel, if the value received
is equal to zero then the qubit q is encoded in the
rectilinear basis else it is encoded in the diagonal
basis. (qubit q) creates a new qubit q initialised to
|
0
i
. Hence an operation of X on q to create
|
1
i
and X or X,H to convert it into
|
+
i
and
|
−
i
re-
spectively. AliceSend then sends the qubit q via
qubitChannel to be received by Bob. The random
bits are stored in encodeBitList to be used later
when both the entities decide upon the key.
• Bob receives the length of the bitList and then con-
tinues with BobReceive process. Like AliceSend,
this is a recursive process which terminates after
receiving all the bits. BobReceive then uses a ran-
dom bit from randomBitChannel, if this bit is zero
then Bob measures the received qubit in the recti-
linear basis else in the diagonal basis. We used a
list that stores a couplet, where we store the ran-
dom bit and the corresponding measurement.
• After exchanging the qubits, Alice and Bob con-
tinue with AliceReveal and BobFinal respectively.
AliceReveal sends the basis that she used for en-
coding via the decisionBitChannel. BobFinal upon
Modelling of Quantum Key Distribution Protocols in Communicating Quantum Processes Language with Verification and Analysis in
PRISM
77

receiving this basis elements checks whether the
basis he measured in the same as of that of Alice in
which case, he sends an acknowledgement via de-
cisionFlagChannel to Alice and the corresponding
bit he measured. Alice checks if the measurement
that Bob made is the same as that of the intended
bit. Since we are dealing with channels without
any noise, if the measurement Bob made does not
match, Alice straight away confirms the presence
of an attacker and sends an eveDetect flag to Bob.
3.2 Formalising B92
Since B92 and BB84 only differ in how they encode
the qubits, we can modify the CQP formalisation of
BB84 for B92. AliceSend does not encode the qubit
in a random basis. If the bitList element is equal to
zero then she sends
|
0
i
else if the element in equal to
one then
|
+
i
is exchanged. With few modifications to
AliceSend in BB84, we can adopt it model B92.
4 MODELLING AND ANALYSIS
IN PRISM
Conversion from CQP to PRISM is a step by step
process. This conversion for a subset of commands
has been done by Ware in his Master’s thesis(Ware,
2008). We are going to use the same procedure. In
the previous section we have mentioned that we have
used List type. Unfortunately a parallel for this type
does not exist for PRISM. To overcome this handicap
we will have to modify the model, in both the proto-
cols the public discussion starts after both the parties
have exchanged all the qubits. Instead in the PRISM
model after every qubit exchange, both the parties
proceed to exchange the encoding basis and measured
bit to establish the validity of the qubit. This way we
can ensure that the original characteristics of the pro-
tocol remain intact.
• all the channels in the CQP model are defined as
global variables in the PRISM model.
• the PRISM model constitutes of three modules
representing the different agents in the CQP mod-
elling
• on the qbitChannel the messages to be exchanged
are limited to [0..3] with 0 representing
|
0
i
, 1 for
|
1
i
, 2 for
|
+
i
and 3 for
|
−
i
.
• when Eve is detected, both Alice and Bob cease
to exchange any more qubits and reach their end
state.
• like in the CQP model we do not create a module
for Random, rather all the parties create their own
random bits either zero or one with equal proba-
bility.
• after choosing a random basis to measure in there
is a one-fourth probability of any of the four out-
comes.
• the number of bits to be exchanged is set by N the
global variable. We check the properties of the
model by varying the value of N. Alice and Bob it-
erate constrained by the value N and are synchro-
nised by the label loop.
• Alice and Bob modules terminate either after ex-
changing N qubits or after detecting Eve and are
synchronised by stop.
4.1 Analysis of BB84
With the models we have made in PRISM we are
going to show there is a non zero probability with
which the eavesdropper can be detected and how
this probability varies with the number of photons
exchanged.
PRISM is capable of calculating probabilities of the
form P
σ,Φ
= Pr{σ |= Φ}, i.e, given a PRISM model
σ, we can calculate the probability with which the
property Φ holds. Φ is expressed in PCTL. We have
two models σ
1
and σ
2
for random-substitution and
intercept-resend, respectively. Both these models are
parametrised by N the number of qubits that both the
parties exchange.
Let P
n
ED
= Pr{σ
n
(N) |= Φ
1
} for n ∈ {1,2}, for
the probability of eavesdropper detection and
P
n
CM
= Pr{σ
n
(N) |= Φ
2
} for n ∈ {1, 2} for the
probability of the eavesdropper making correct mea-
surements for more than half of the qubits. n = 1 for
random-substitution and n = 2 for intercept resend.
We also have N ∈ [1, 20], i.e, we start to find these
probabilities starting from one qubit being exchanged
to twenty.
Φ
1
and Φ
2
are to be expressed in PCTL. Φ
1
is the
PCTL formula corresponding to when the eavesdrop-
per is detected. From the PRISM model for BB84,
whenever an eavesdropper is detected Alice is in al-
iceState=15 and Bob is in state bobState=10. The
corresponding expression for Φ
1
and their property
expression in PRISM:
Φ
1
= {(aliceState = 15) ∧(bobState = 10)} (1)
P=?[F(aliceState=15)&(bobState=10)] (2)
SIMULTECH 2018 - 8th International Conference on Simulation and Modeling Methodologies, Technologies and Applications
78
Similarly for Φ
2
which gives the probability of eaves-
dropper measuring more than half of the exchanged
qubits correctly is
Φ
2
= true U (correctMeasurement > N/2) (3)
P=?[F(correctMeasurement>
N
2
)] (4)
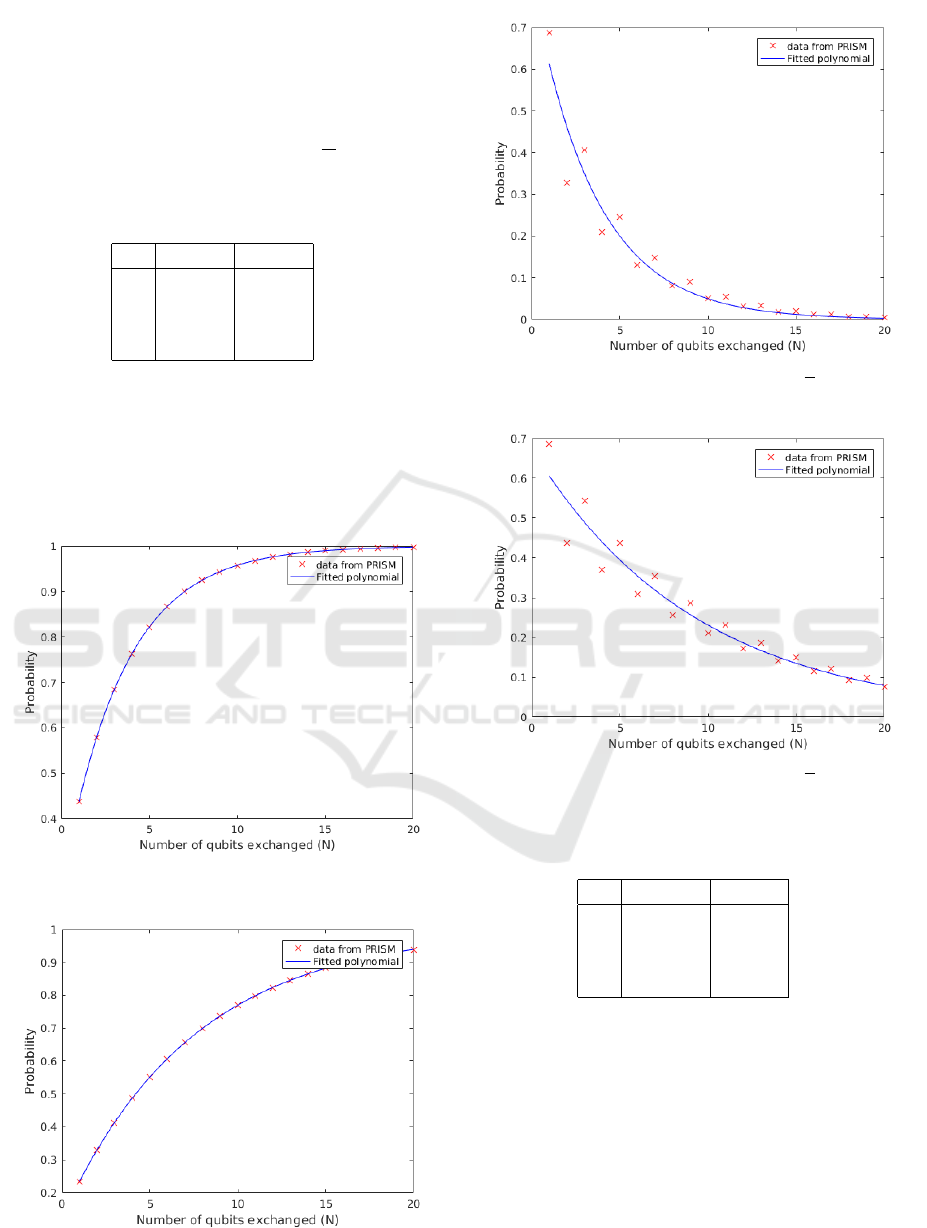
Table 1: Probability of detecting eavesdropper for BB84-
QKD.
N P
1
ED
P
2
ED
5 0.822 0.5512
10 0.9577 0.7698
15 0.9899 0.8819
20 0.9976 0.9394
TABLE I and TABLE II have probabilities that are
observed from PRISM. Using the Curve Fitting tool
of MATLAB, and using the Marquardt-Levenberg
nonlinear least squares algorithm for curve-fitting we
have come up with the equation that best fits these
probabilities.
Figure 1: Probability of detecting eavesdropper for BB84
Random Substitution.
Figure 2: Probability of detecting eavesdropper for BB84
Intercept Resend.
Figure 3: Probability of measuring more than
N
2
qubits cor-
rectly for BB84 Random Substitution.
Figure 4: Probability of measuring more than
N
2
qubits cor-
rectly for BB84 Intercept Resend.
Table 2: Probability of eavesdropper measuring more than
half of the qubits correct for BB84-QKD.
N P
1
CM
P
2
CM
5 0.2458 0.4370
10 0.0501 0.2111
15 0.0188 0.1510
20 0.00425 0.0756
We observed that
P
1
ED
≈ Pr{σ
1
(N) |= Φ
1
} = 1 −(0.75)e
−0.2877N
(5)
P
2
ED
≈ Pr{σ
2
(N) |= Φ
1
} = 1 −(0.8750)e
−0.1335N
(6)
and
P
1
CM
≈ Pr{σ
1
(N) |= Φ
2
} = (0.8108)e
−0.2795N
(7)
P
2
CM
≈ Pr{σ
2
(N) |= Φ
2
} = (0.6750)e
−0.1072N
(8)
Modelling of Quantum Key Distribution Protocols in Communicating Quantum Processes Language with Verification and Analysis in
PRISM
79
Since P
1
ED
> P
2
ED
, the probability of eavesdropper
getting detected is higher when the eavesdropper re-
sorts to random-substitution.
Also it has to be noted that:
lim
N→∞
P
1
ED
= lim
N→∞
P
2
ED
= 1 (9)
which suggests as the number of qubits exchanged in-
creases so does the chances of detecting an eavesdrop-
per.
lim
N→∞
P
1
CM
= lim
N→∞
P
2
CM
= 0 (10)
reaffirms the theoretical results obtained by May-
ers(Mayers, 2002), wherein he states
”amount of Shannon’s information available to Eve
must decrease exponentially fast as N increases.”.
Both these observations reaffirm the results obtained
by Papanikolaou(Gay et al., 2005).
4.2 Analysis of B92
We use the same notations as in the previous subsec-
tion. The only change being the PCTL expressions.
Referring to PRISM model for B92, eavesdropper is
detected when aliceState=11 and bobState=10.
Φ
1
= {(aliceState = 11) ∧(bobState = 10)} (11)
P=?[F(aliceState=15)&(bobState=10)] (12)
φ
2
= true U (correctMeasurement > N/2)
(13)
P=?[F(correctMeasurement>
N
2
)] (14)
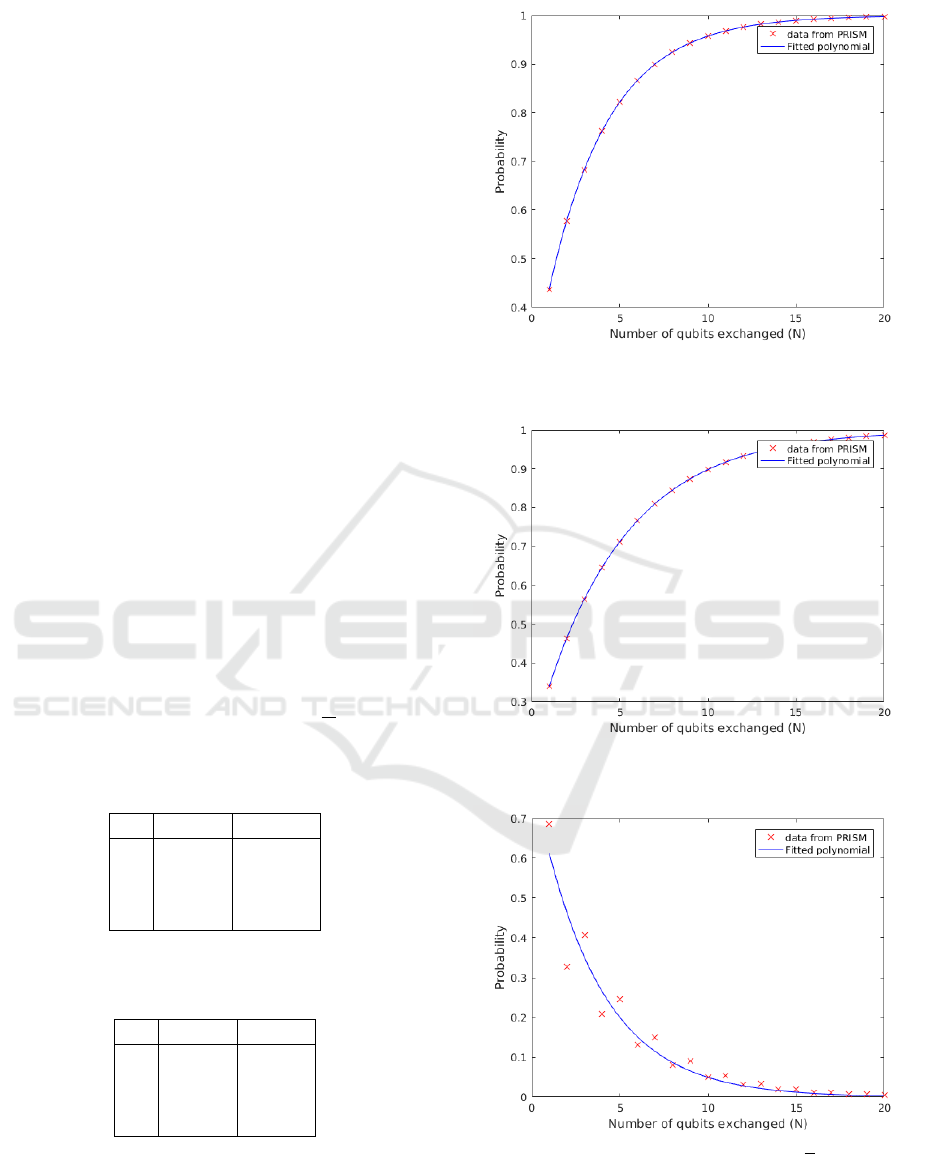
Table 3: Probability of detecting eavesdropper for B92-
QKD.
N P
1
ED
P
2
ED
5 0.8665 0.7123
10 0.9683 0.89812
15 0.9924 0.96392
20 0.9976 0.98722
Table 4: Probability of eavesdropper measuring more than
half of the qubits correct for BB84-QKD.
N P
1
CM
P
2
CM
5 0.2458 0.3345
10 0.0501 0.1083
15 0.0201 0.0592
20 0.0042 0.0199
After using the curve fitting algorithm to approxi-
mate the results to an equation we have:
P
1
ED
≈ Pr{σ
1
(N) |= Φ
1
} = (1 −(0.75)e
−0.2877N
)
(15)
Figure 5: Probability of detecting eavesdropper for B92
Random Substitution.
Figure 6: Probability of detecting eavesdropper for B92 In-
tercept Resend.
Figure 7: Probability of measuring more than
N
2
qubits cor-
rectly for B92 Random Substitution.
P
2
ED
≈ Pr{σ
2
(N) |= Φ
1
} = (1 −(0.8125)e
−0.2795N
)
(16)
SIMULTECH 2018 - 8th International Conference on Simulation and Modeling Methodologies, Technologies and Applications
80
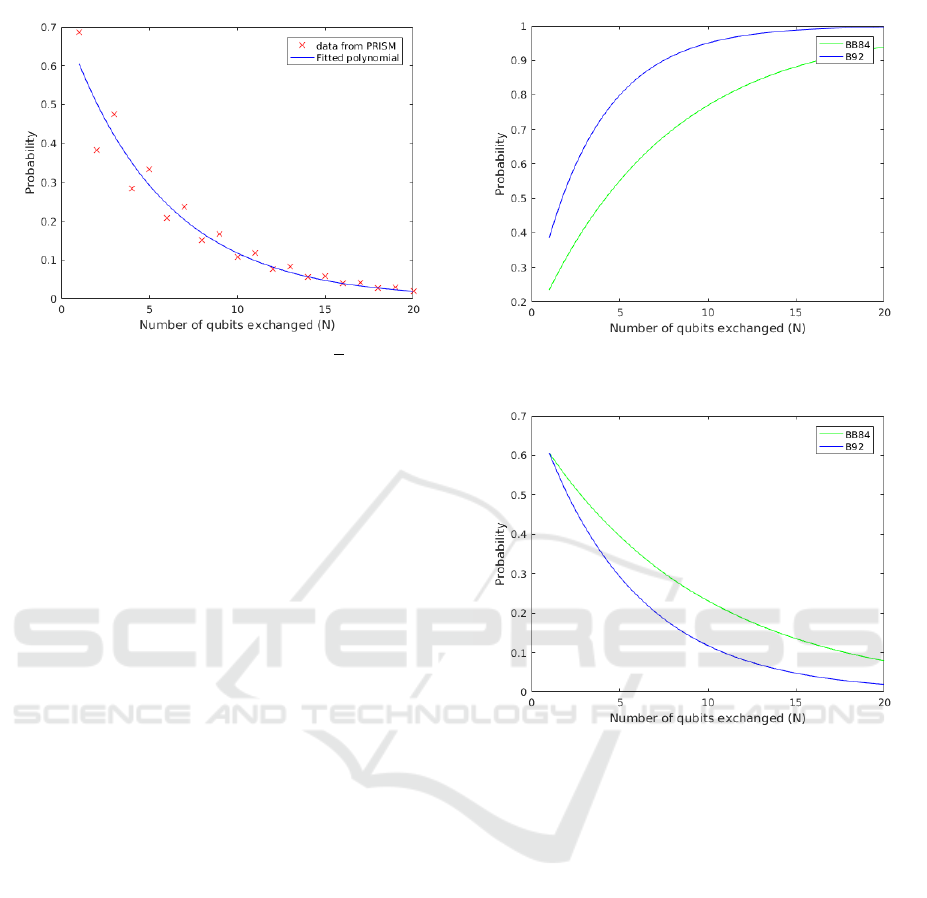
Figure 8: Probability of measuring more than
N
2
qubits cor-
rectly for B92 Intercept Resend.
and
P
1
CM
≈ Pr{σ
1
(N) |= Φ
2
} = (0.8108)e
−0.2795N
(17)
P
2
CM
≈ Pr{σ
2
(N) |= Φ
2
} = (0.7272)e
−0.1821N
(18)
We make the following observations:
lim
N→∞
P
1
ED
= lim
N→∞
P
2
ED
= 1 (19)
lim
N→∞
P
1
CM
= lim
N→∞
P
2
CM
= 0 (20)
Like the inferences made for BB84, the chances
of detecting an eavesdropper increases with the num-
ber of qubits exchanged and also the number of cor-
rect measurements that an eavesdropper can make
decreases exponentially with the number of qubits
exchanged. But unlike in BB84, for B92 we have
P
1
ED
< P
2
ED
, hence the probability of eavesdropper de-
tection is higher during intercept-resend than in ran-
dom substitution.
4.3 Comparison between BB84 and B92
Quite strangely we observe that with respect to ran-
dom substitution type of attack, both the protocols
perform identically. This is substantiated by the equa-
tions
P
1
CM
≈ Pr{σ
1
(N) |= Φ
2
} = (0.8108)e
−0.2795N
(21)
and
P
1
ED
≈ Pr{σ
1
(N) |= Φ
1
} = (1 −(0.75)e
−0.2877N
)
(22)
However with respect to intercept resend style attacks
they differ markedly, as evidenced by Fig. 12 and Fig.
13.
B92 performs better in terms of eavesdropper de-
tection as the probability approaches unity faster than
B92 and in terms of decreased number of correct mea-
surements that can be made by the eavesdropper.
Figure 9: BB84 and B92 Comparison for Intercept Resend
eavesdropper detection.
Figure 10: BB84 and B92 comparison for Intercept Resend
correct measurements by eavesdropper.
5 CONCLUSION
We have successfully modelled BB84 protocol in
CQP, showed the process in which we have created
PRISM models from the CQP models and analysed
the properties using PCTL. We also corroborate the
theoretical observations made in earlier research with
our analysis, namely the probability of correctly as-
certaining the presence of an eavesdropper increases
with the number of qubits exchanged. We also com-
pared the performance of BB84 and B92 and infer that
B92 is more resilient against an eavesdropper, with
its ability to take fewer qubits than BB84 in identi-
fying an eavesdropper and then potentially reducing
the number of correct measurements the eavesdropper
can make. Hence in practise B92 seems to be a more
viable protocol than BB84 because it is less complex
to implement and performs better.
Modelling of Quantum Key Distribution Protocols in Communicating Quantum Processes Language with Verification and Analysis in
PRISM
81

REFERENCES
Bu
ˇ
zek, V. and Hillery, M. (1996). Quantum copying: Be-
yond the no-cloning theorem. Physical Review A,
54(3):1844.
Davidson, T. A. (2012). Formal verification techniques us-
ing quantum process calculus. PhD thesis, University
of Warwick.
Gay, S., Nagarajan, R., and Papanikolaou, N. (2005). Prob-
abilistic model–checking of quantum protocols. arXiv
preprint quant-ph/0504007.
Gay, S. J. and Nagarajan, R. (2005). Communicating quan-
tum processes. In ACM SIGPLAN Notices, volume 40,
pages 145–157. ACM.
Mayers, D. (2002). Shor and preskill’s and mayers’s se-
curity proof for the bb84 quantum key distribution
protocol. The European Physical Journal D-Atomic,
Molecular, Optical and Plasma Physics, 18(2):161–
170.
Milner, R. (1999). Communicating and mobile systems: the
pi calculus. Cambridge university press.
Nielsen, M. A. and Chuang, I. L. (2010). Quantum compu-
tation and quantum information. Cambridge univer-
sity press.
Quan, Z. and Chaojing, T. (2002). Simple proof of
the unconditional security of the bennett 1992 quan-
tum key distribution protocol. Physical Review A,
65(6):062301.
Ware, C. J. (2008). Modeling and analysis of quantum cryp-
tographic protocols. PhD thesis.
SIMULTECH 2018 - 8th International Conference on Simulation and Modeling Methodologies, Technologies and Applications
82
