
Hash-Based Signature with Constant-Sum Fingerprinting and
Partial Construction of Hash Chains
Yuichi Kaji
1
, Jason Paul Cruz
2
and Yoshio Yatani
3
1
Nagoya University, Furo-cho, Chikusa-ku, Nagoya, 464-8601, Japan
2
Osaka University, 1-5 Yamadaoka, Suita, Osaka 565-0871, Japan
3
Nara Institute of Science and Technology, 8916-5 Takayama, Ikoma, Nara 630-0101, Japan
Keywords:
One-time Signature, Winternitz Scheme, Fingerprinting Function, Hash Chain, Security Proof, IoT Security,
Post-quantum Security.
Abstract:
A hash-based one-time signature (OTS) is a light-weight and quantum-immune alternative to conventional
digital signature schemes. This study focuses on the possible use of hash-based OTS in a wireless sensor net-
work and investigates techniques that improve the efficiency of Winternitz OTS. The improvement is made by
two means; introduction of a novel fingerprinting function and partial construction of hash chains. The tech-
niques contribute to a better trade-off between signature size and computational complexity, and they can be
used together with other improvement techniques on Winternitz OTS. This study also shows that the proposed
OTS is strongly existentially unforgeable if fingerprinting and hash functions are chosen appropriately.
1 INTRODUCTION
1.1 Background and Related Studies
Conventional digital signature schemes that are based
on number theoretic problems pose two possible
problems; large computational complexity and the
threat of quantum computers. It is not favorable
for small battery-operated devices to perform energy-
consuming computation over large numbers, and the
security of the scheme is fatally threaten by quantum
computers because they are able to solve number the-
oretical problems efficiently(Shor, 1997).
A hash-based digital signature is a light-weight
and quantum-immune alternative to conventional dig-
ital signature schemes(Buchmann et al., 2011b; Dods
et al., 2005). As the name suggests, the scheme makes
use of cryptographic hash functions instead of num-
ber theoretic problems. The scheme is light-weight
because the computation of a hash function can be
performed with much less time and energy than the
computation over large numbers. The scheme is
quantum-immune because a hash function involves
tricky mechanisms that make the function mathemat-
ically disordered and thus difficult to tackle even by
quantum computers(Bernstein et al., 2009).
In a typical hash-based digital signature, a secret
signing key is a set of elements randomly selected
from the domain of a hash function. These elements
are provided to an acyclic hash-network, and the out-
put of the network is used as a public verification key.
The message to be signed selects certain points in the
hash-network, and the hash values of those selected
points are used as the signature. A verifier confirms
the integrity of a signature by checking if the veri-
fication key that is reconstructed from the signature
coincides with the verification key that has been dis-
tributed in advance. In this framework, an issuance
of a signature discloses some secret, and a once used
key pair should not be reused. For this reason, a hash-
based digital signature is sometimes called a one-time
signature (OTS) in literature, although the practical-
ity issue of handling multiple keys can be mitigated
by using a Merkle tree(Merkle, 1990) which consoli-
dates several verification keys to a single key.
The first hash-based OTS was proposed in
(Lamport, 1979), which is improved in (Merkle,
1990). As described in (Merkle, 1990), Merkle OTS
can be generalized to Winternitz OTS. The hash-
network of Merkle OTS consists of hash chains of
length one, while Winternitz OTS allows the use
of longer hash chains than Merkle OTS. Bleichen-
bacher and Maurer extended the hash-network from
chains to complicated graphs(Bleichenbacher and
Maurer, 1996b)(Bleichenbacher and Maurer, 1996a)
Kaji, Y., Cruz, J. and Yatani, Y.
Hash-Based Signature with Constant-Sum Fingerprinting and Partial Construction of Hash Chains.
DOI: 10.5220/0006828202970304
In Proceedings of the 15th International Joint Conference on e-Business and Telecommunications (ICETE 2018) - Volume 2: SECRYPT, pages 297-304
ISBN: 978-989-758-319-3
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
297

(see also (Dods et al., 2005)). Other investiga-
tions include BiBa(Perrig, 2001) and HORS(Reyzin
and Reyzin, 2002). Among these OTS, Winter-
nitz OTS seems promising because it is simple, ex-
tensible(Buchmann et al., 2011b)(Hulsing, 2013),
and has become a basement of practical frame-
works such as XMSS(Buchmann et al., 2011a) and
SPHINCS(Bernstein et al., 2015).
We note that there are investigations that try to
realize data authentication by using hash functions
but in a different manner. For example, SPINS (Per-
rig et al., 2002) makes use of a hash chain, where
each hash value in the chain is used as a signing key.
The authorization issue of the data authentication is
controlled by gradually disclosing hash values in the
hash chain. A single key pair can be used several
times, but the verifier is not able to complete the in-
tegrity check of a signature until the signer discloses a
hash value that was used to make a signature. SPINS
has different characteristics and functionality from the
above described OTS, and this paper does not discuss
schemes of this type due to the page restriction.
1.2 Contribution of this Study
This study investigates another improvement of Win-
ternitz OTS. The improvement focuses possible use of
the scheme in a wireless sensor network, and the pro-
posed techniques can be combined with other investi-
gations, including (Buchmann et al., 2011b; Hulsing,
2013; Buchmann et al., 2011a; Bernstein et al., 2015).
A wireless sensor network (WSN) typically con-
sists of a power-provided server and battery-operated
sensor nodes. Sensor nodes are deployed in a target
field and constitute a wireless ad-hoc network. The
battery lifetime of nodes is a concern in WSN be-
cause the shutoff of a single node can disconnect a
major part of the network. A node is commonly a
tiny device that monitors its environment and sends
collected information to the server. If data authenti-
cation is needed in the communication from a node
to the server, then a simple message authentication
code (MAC) is available because the communication
is one-to-one. On the other hand, the server some-
times sends important messages, such as control com-
mands, to multiple nodes. MAC is not available
for the data authentication in the one-to-many com-
munication because MAC does not have the non-
repudiation property, and a digital signature is needed
in this case. In this framework, signed messages are
always constructed by the sever, and nodes just verify
signatures. To extend the battery lifetime of nodes,
the complexity of verification is more substantial than
the complexities of key generation and signing.
To reduce the complexity of verification, we con-
sider two modifications of Winternitz OTS. The first
modification includes a fingerprinting function called
constant-sum fingerprinting function, which has been
discussed in (Cruz et al., 2016). This function con-
tributes to reducing the complexity of verification to a
small constant amount, but it can increase the com-
plexities of key generation and signing(Cruz et al.,
2016). To avoid this problem, we introduce in this pa-
per the second modification of partially constructing
the hash chains and using a nonce in the signing pro-
cedure. Instead of fully constructing long hash chains,
we construct hash chains partially and use auxiliary
information of a nonce to avoid inconvenient access to
the unconstructed part of the hash chains. This tech-
nique is compatible with the mathematical property
of the constant-sum fingerprinting and suppresses the
complexities of key generation and signing.
Winternitz OTS is briefly reviewed in Sect. 2, and
the proposed OTS scheme is introduced in Sect. 3.
The complexity of the scheme is discussed in this sec-
tion also. It is proved in Sect. 4 that the proposed
OTS is strongly existentially unforgeable under some
assumptions of the fingerprinting and hash functions.
2 WINTERNITZ OTS
For the sake of clarity, we use slightly different defi-
nition of Winternitz OTS from (Merkle, 1990) at the
following two points: (i) The fingerprinting function
is explicit in this paper, while it is implicit in litera-
ture. (ii) Integers in a fingerprint indicate positions
from the head, not from the tail of hash chains.
A hash-based OTS has three algorithms KeyGen
for generating keys, Sign for the computation of sig-
natures, and Verify for the verification of signatures,
which are implemented as follows in Winternitz OTS.
• KeyGen(1
n
): Select a hash function h : {0, 1}
L
→
{0, 1}
L
, where L is the length of a hash image, and
a fingerprinting function f : {0, 1}
∗
→ {0, 1}
n
.
The hash function h and the fingerprinting func-
tion f are public information, and verifiers are as-
sumed to know h and f . Choose a positive inte-
ger parameter l and define w = w
1
+ w
2
, where
w
1
=
n log
l
2
and w
2
=
log
l
(w
1
(l − 1))
+ 1. Se-
lect s
1
, . . . , s
w
uniformly from {0, 1}
L
at random
and compute v
i
= h
l−1
(s
i
) for 1 ≤ i ≤ w. The
signing key and the verification key are defined
as SK = (s
1
, . . . , s
w
) and VK = (v
1
, . . . , v
w
), re-
spectively. We call the sequence of hash values s
i
,
h(s
i
), h
2
(s
i
), . . . , h
l−1
(s
i
) a hash chain (of length
l − 1), where s
i
and h
l−1
(s
i
) are called the head
and the tail of the chain, respectively.
SECRYPT 2018 - International Conference on Security and Cryptography
298

• Sign(SK, m): Compute the fingerprint f (m) of
m, and convert f (m) to a base-l representation
(a
1
, . . . , a
w
1
) by regarding f (m) as a binary in-
teger (note that w
1
digits in l-ary suffice to ac-
commodate an integer of n-bits binary). Then,
compute the check-sum C = w
1
(l − 1) −
P
w
1
i=1
a
i
and let (c
1
, . . . , c
w
2
) be the base-l representation
of C (note again that w
2
digits in l-ary suf-
fice to accommodate the value of C). Write
( f
1
, . . . , f
w
) = (a
1
, . . . , a
w
1
, c
1
, . . . , c
w
2
), and the
signature for the message m is defined as σ =
(h
l−1− f
1
(s
1
), . . . , f
l−1− f
w
(s
w
)).
• Verify(VK, m, σ): Determine ( f
1
, . . . , f
w
) as in
Sign(SK, m). Accept m and σ = (σ
1
, . . . , σ
w
) if
and only if VK = (h
f
1
(σ
1
), . . . , h
f
w
(σ
w
)).
The signing key, verification key, and signatures
of Winternitz OTS are all wL-bits in size. The cost
of an algorithm is defined as the number of compu-
tations of the hash function h performed in the al-
gorithm. The cost of KeyGen algorithm is always
w(l − 1), and the costs of Sign and Verify algorithms
are both w(l − 1) at the maximum. For several values
of l, the left part of Tab. 1 shows the values of w
1
, w
2
,
w, the cost of each algorithm, and the signature length
|σ| for the security parameter n = 160. Remind that
L is the length of a hash image. If we use SHA-1
as h for example, then L = 160 and the signature is
|σ| = 22L = 3520 bits in length for l = 256. From the
table, we can observe a trade-off relation between the
signature length |σ| and the costs of operations.
3 PROPOSED SCHEME
3.1 Fingerprinting Function
For positive integers l and w, define
T
l,w
= {(t
1
, . . . , t
w
) : t
i
∈ {0, . . . , l}, t
1
+ · · · + t
w
= l},
which is the set of tuples of w non-negative integers
that sum to l. We note that
T
l,w
= (l + w − 1)!/l!(w −
1)!. An (l, w)-constant-sum fingerprinting function is
a function that maps a message of an arbitrary length
to a tuple in T
l,w
. In this paper, an (l, w)-constant-
sum fingerprinting function is denoted by f
l,w
. Our
basic idea is to use f
l,w
to specify positions in the hash
chains in Winternitz OTS. Before proceeding to the
discussion of OTS, we first see that f
l,w
can be con-
structed from a usual fingerprinting function.
For a security parameter n, choose l and w so that
T
l,w
≥ 2
n
. Prepare a fingerprinting function f that
has exactly
T
l,w
fingerprints in its range. We as-
sume without loss of generality that the range of f
is I
l,w
= {0, . . . ,
T
l,w
− 1}. A constant-sum finger-
printing function f
l,w
is obtained by bijectively map-
ping integers in I
l,w
to tuples in T
l,w
. For this sake,
assign each tuple in T
l,w
with a unique integer in I
l,w
according to a descending dictionary order. For ex-
ample, if l = 4 and w = 3, then tuples in T
4,3
are or-
dered as (4, 0, 0), (3, 1, 0), (3, 0, 1), (2, 2, 0), . . . , and
they are assigned with integers 0, 1, 2, 3, . . . , respec-
tively. Note that if (l − k, t
2
, . . . , t
w
) ∈ T
l,w
, where
0 ≤ k ≤ l, then t
2
+ · · · + t
w
= k and hence T
l,w
con-
tains
T
k,w−1
= (k + w − 2)!/(k!(w − 2)!) tuples of the
form (l − k, t
2
, . . . , t
w
). This implies that any tuple of
the form (l − k, t
2
, . . . , t
w
) must be assigned with an
integer that is b
k
or more and b
k+1
− 1 or less where
b
k
=
P
k−1
i=0
T
i,w−1
for 0 ≤ k ≤ l + 1. Notice that b
k
can
be easily computed by using the recursion
T
i,w−1
=
(i + w − 2)!
i!(w − 2)!
=
i + w − 2
i
T
i−1,w−1
with
T
0,w−1
= 1 as a basis. To map an integer j ∈ I
l,w
to a tuple (t
1
, . . . , t
w
) ∈ T
l,w
, we first determine k that
satisfies b
k
≤ j < b
k+1
(i.e. j ∈ [b
k
, b
k+1
)) and set
t
1
= l − k. The other w − 1 components t
2
, . . . , t
w
are
determined by mapping j− b
k
(which is 0 or more and
T
k,w−1
− 1 or less) to a tuple in T
k,w−1
in a recursive
manner. This computation is summarized as follows.
Procedure 1. This procedure M
l,w
( j) maps j ∈ I
l,w
to (t
1
, . . . , t
w
) ∈ T
l,w
:
1. If w = 1, then terminate with (t
1
) = (l) as an out-
put. If w > 1, then continue to the next step;
2. i ← 0, a ← 1, b
L
= 0, b
R
← a;
/* a is used to record the value of
T
i,w−1
*/
3. while j < [b
L
, b
R
) {
4. i ← i + 1;
5. a ← a(i + w − 2)/i;
6. b
L
← b
R
, b
R
← b
R
+ a;
7. }
8. t
1
← l − i; /* because j ∈ [b
L
, b
R
) = [b
i
, b
i+1
) */
9. (t
2
, . . . , t
w
) ← M
i,w−1
( j − b
L
);
10. Output (t
1
, . . . , t
w
);
We remark that the constant-sum fingerprinting
function f
l,w
(m) = M
l,w
( f (m)) has the same statisti-
cal property as f because M
l,w
is a bijective mapping.
If f is collision-resistant, then so is f
l,w
, for example.
3.2 Tentatively Improved OTS
The following OTS is obtained by using a constant-
sum fingerprinting function in Winternitz OTS in a
straightforward manner. This OTS is still tentative
because we will subsequently employ a second mod-
ification. Nevertheless, this construction is important
Hash-Based Signature with Constant-Sum Fingerprinting and Partial Construction of Hash Chains
299

Table 1: Parameters of Winternitz OTS and tentatively improved OTS (Sect. 3.)
Winternitz tentatively improved
l w
1
w
2
w KeyGen Sign Verify |σ| l w KeyGen Sign Verify
16 40 3 43 645 ≤ 645 ≤ 645 43L 211 43 9, 073 8, 862 211
32 32 2 34 1, 054 ≤ 1, 054 ≤ 1, 054 34L 363 34 12, 342 11, 979 363
64 27 2 29 1, 827 ≤ 1, 827 ≤ 1, 827 29L 579 29 16, 791 16, 212 579
128 23 2 25 3, 175 ≤ 3, 175 ≤ 3, 175 25L 984 25 24, 600 23, 616 984
256 20 2 22 5, 610 ≤ 5, 610 ≤ 5, 610 22L 1, 695 22 37, 290 35, 595 1, 695
because it will help explain the idea of the improve-
ment that will be discussed in the next section.
• KeyGen(1
n
): Select parameters l and w, a hash
function h : {0, 1}
L
→ {0, 1}
L
, and a constant-
sum fingerprinting function f
l,w
. Select s
1
, . . . , s
w
uniformly from {0, 1}
L
at random, and compute
v
i
= h
l
(s
i
) for 1 ≤ i ≤ w. The signing key and the
verification key are defined as SK = (s
1
, . . . , s
w
)
and VK = (v
1
, . . . , v
w
), respectively.
• Sign(SK, m): The signature for the message m is
σ = (h
l− f
1
(s
1
), . . . , f
l− f
w
(s
w
)) where ( f
1
, . . . , f
w
) =
f
l,w
(m).
• Verify(VK, m, σ): The pair of the message m and
the signature σ = (σ
1
, . . . , σ
w
) is accepted if
and only if VK = (h
f
1
(σ
1
), . . . , h
f
w
(σ
w
)) where
( f
1
, . . . , f
w
) = f
l,w
(m).
The size of keys and the size of signatures are wL-
bits. The costs of KeyGen, Sign, and Verify are lw,
lw − l, and l, respectively, where the cost is measured
by the number of computations of the hash function
h. Remark however that we should not compare these
formulas naively with those of Winternitz OTS. Given
a security parameter n, the values of l and w in the
above scheme are determined according to a differ-
ent constraint from Winternitz OTS. For example, the
choice of l = 256 and w = 22 is allowed in Win-
ternitz OTS (See Tab. 1) for the security parameter
of n = 160, but we need to take l = 1695 in the
above scheme to make w = 22 for n = 160 because
T
1694,22
< 2
160
<
T
1695,22
. Long chains are needed
because T
l,w
is a small subset in the entire set of w-
tuples of integers. The right part of Tab. 1 shows the
parameters and costs of the above tentative scheme
for n = 160. Comparing the values in Tab. 1, we can
see that the cost of verification is reduced in this tenta-
tive OTS scheme, but the costs of key generation and
sign are much greater than those of Winternitz OTS
because of the long hash chains that are needed in the
scheme. This problem is tackled by introducing an-
other idea; partial construction of hash chains.
3.3 Partial Construction of Hash Chains
In the tentatively improved OTS, the i-th hash chain
consists of l + 1 hash values; s
i
, h(s
i
), . . . , h
l
(s
i
).
Each hash value in the i-th hash chain has the chance
to be used as an i-th component of a signature, but
that probability is not equally likely. For example,
s
i
= h
l−l
(s
i
) is used as a signature if and only if
f
l,w
(m) = (0, . . . , 0, l, 0 . . . , 0), which is taken with
very small probability. In general, hash values that
are close to the head of the chain (i.e., hash values
h
j
(s
i
) with small j) have small probabilities to be used
as a signature component. Based on this observation,
we consider constructing a hash chain from an inter-
mediate point, omitting the construction of the “head
portion” of the hash chain. In the Sign algorithm, we
can start tracing the hash chain from that intermedi-
ate point. The unconstructed hash values are hardly
needed by the Sign algorithm, and thus, a valid sig-
nature is likely to be computed in most of the cases.
Obviously, the trick does not work all of the time. The
computation fails if Sign accesses an unconstructed
hash value. To avoid this unfortunate case from hap-
pening, we use a nonce in the signing process and al-
low a message to not have an undesired fingerprint.
Let θ be an integer with θ ≤ l and define
T
[θ]
l,w
= {(t
1
, . . . , t
w
) : t
i
∈ {0, . . . , θ}, t
1
+ · · · + t
w
= l},
which is a subset of T
l,w
such that integer components
are upper-bounded by θ. Remark that T
[θ]
l,w
= ∅ if θ <
l/w, and we take θ so that T
[θ]
l,w
contains sufficiently
many tuples. We define a nonce of a message m as the
smallest positive integer r that makes f
l,w
(m||r) ∈ T
[θ]
l,w
,
where m||r denotes the concatenation of m and r. The
proposed OTS is described as follows.
• KeyGen(1
n
): The algorithm is the same as
KeyGen(1
n
) of the tentatively improved scheme
except that v
i
is computed as v
i
= h
θ
(s
i
) for
1 ≤ i ≤ w. In other words, s
i
is used as an in-
termediate value in the i-th hash chain.
• Sign(SK, m): Determine the nonce r of the mes-
sage m. The signature for the message m is
defined as σ = (h
θ− f
1
(s
1
), . . . , f
θ− f
w
(s
w
)) where
( f
1
, . . . , f
w
) = f
l,w
(m||r).
SECRYPT 2018 - International Conference on Security and Cryptography
300
• Verify(VK, m, σ): The pair of the message m and
the signature σ = (σ
1
, . . . , σ
w
) is accepted if
and only if VK = (h
f
1
(σ
1
), . . . , h
f
w
(σ
w
)) where
( f
1
, . . . , f
w
) = f
l,w
(m||r) with r as the nonce of the
message m.
Notice the following differences from the tentative
OTS in the previous section.
• KeyGen generates hash chains of length θ, which
is the “tail portion” of the original hash chains.
• Sign uses the nonce r to generate a fingerprint in
T
[θ]
l,w
. The signature is computed from SK because
all components of the fingerprint are θ or less.
The size of keys and the size of signatures are wL-
bits, and the costs of KeyGen, Sign, and Verify are
θw, θw − l, and l, respectively. Because θ < l, we
reduced the costs of KeyGen and Sign, while the cost
of Verify is the same as in the tentative scheme.
For the fairness of comparison, however, we need
to consider the computational burden of finding the
nonce r besides the number of computations of the
hash function h. Basically, there is no means of
determining the nonce r except through exhaustive
search; examine r = 1, 2, . . . in a sequential manner
until we get f
l,w
(m||r) ∈ T
[θ]
l,w
. Under the assumption
that f
l,w
(m||r) distributes uniformly over T
l,w
, the ex-
pected number of such examinations is 1/p
l,w,θ
, where
p
l,w,θ
=
T
[θ]
l,w
/
T
l,w
is the probability that f
l,w
(m||r)
belongs to T
[θ]
l,w
for an examined value of r. It is known
that
T
[θ]
l,w
is characterized by generalized Pascal tri-
angles(Bollinger and Burchard, 1990), and
T
[θ]
l,w
=
C
θ+1
(w, l), where
C
m
(n, r) =
min(n,br/mc)
X
j=0
(
−1
)
j
n
j
!
n + r − 1 − jm
n − 1
!
.
Using this formula, we can compute p
l,w,θ
and then es-
timate the expected number of examinations that are
needed to find the nonce r.
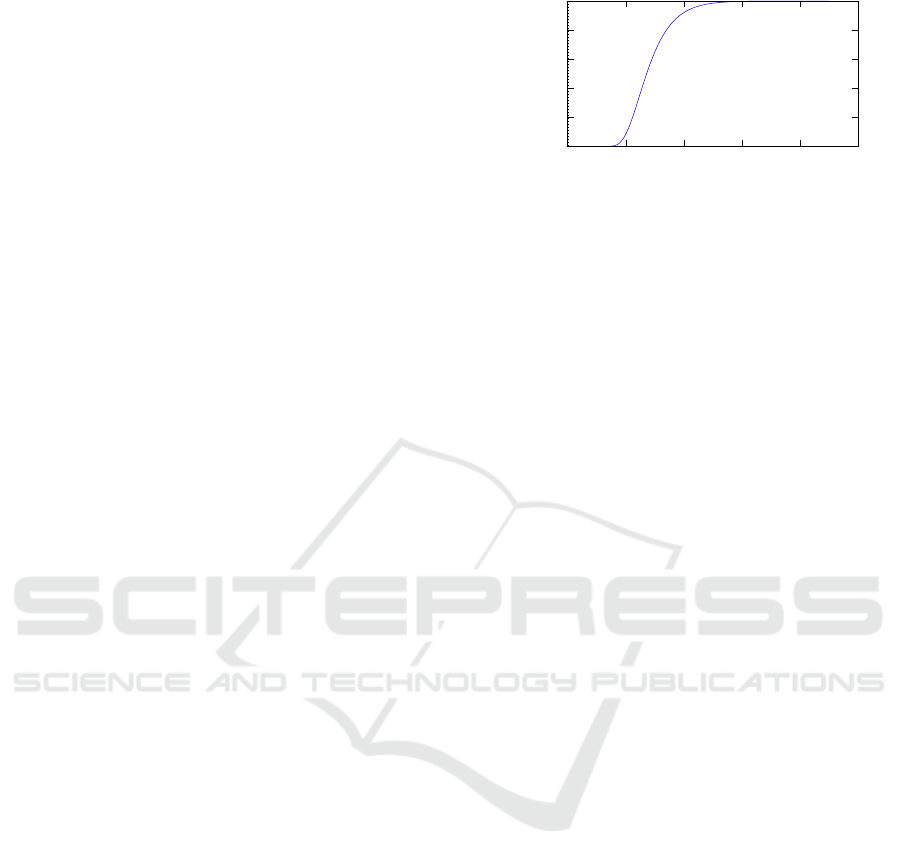
To illustrate the relationship between p
l,w,θ
and θ,
take l = 1695 and w = 22 for example (which are
from the bottom line of Tab. 1). Fig. 1 sketches the
value of p
1695,22,θ
where the horizontal axis is θ and
the vertical axis is p
1695,22,θ
. We can confirm from
the graph that p
1695,22,θ
converges to 1 with rather
small values of θ. Numerical computation shows that
p
1695,22,θ
approximately equals to 0.50, 0.25 and 0.125
at θ = 272, 232 and 209, respectively. If we take
θ = 209 for example, then KeyGen generates w = 22
hash chains of length θ = 209 each, and thus its cost
is θw = 4598. The cost of Sign is θw − l = 2903, and
the Sign algorithm needs to examine 1/p
1695,22,209
≈ 8
candidates of the nonce on average. The cost of Verify
p
l,w,θ
θ
0
0.2
0.4
0.6
0.8
1
0 200 400 600 800 1000
Figure 1: The probability p
1695,22,θ
.
is l = 1695 which remains the same as the tentatively
improved OTS as in Tab. 1. Parameters for θ = 272
and 232, and also parameters for w = 29 and 25 with
1/p
w,l,θ
≈ 2, 4 and 8, are shown in Tab. 2. The costs
of KeyGen and Sign are reduced from the tentatively
scheme while preserving the efficiency of Verify.
4 SECURITY OF THE PROPOSED
SCHEME
The security proof of the proposed scheme is provided
in this section. The basic idea of the proof is almost
the same as that for Winternitz OTS (Buchmann et al.,
2011b), but the proof must be generalized to cope
with the fingerprinting function which was implicit in
literature, and advantage (the success probability) of
the adversary must be revised. After reviewing re-
lated notions, the proposed OTS scheme is shown to
be strongly existentially unforgeable.
4.1 Formal Notions of Security
A function h is one-way if the probability
Pr
y = h(x
0
) : x ← {0, 1}
∗
; y ← h(x); x
0
← A(y)
(1)
is negligible(Goldwasser and M. Bellare, 2018) for
an arbitrary polynomial-time algorithm A. This defi-
nition is based on Definition 2.2 of (Goldwasser and
M. Bellare, 2018) but we allow x to have an arbitrary
length. A function h is collision-resistant if
Pr
h(z) = h(z
0
) : (z, z
0
) ← A
(2)
is negligible for an arbitrary polynomial-time algo-
rithm A. This definition coincides with the CR2-KK
property in (Goldwasser and M. Bellare, 2018) with
the small difference that a key (the definition of h) is
explicitly given to A in (Goldwasser and M. Bellare,
2018) while the key is implicit in (2).
The strong existential unforgeability is defined in
terms of a game between a challenger and an adver-
sary(Boneh et al., 2006).
Hash-Based Signature with Constant-Sum Fingerprinting and Partial Construction of Hash Chains
301
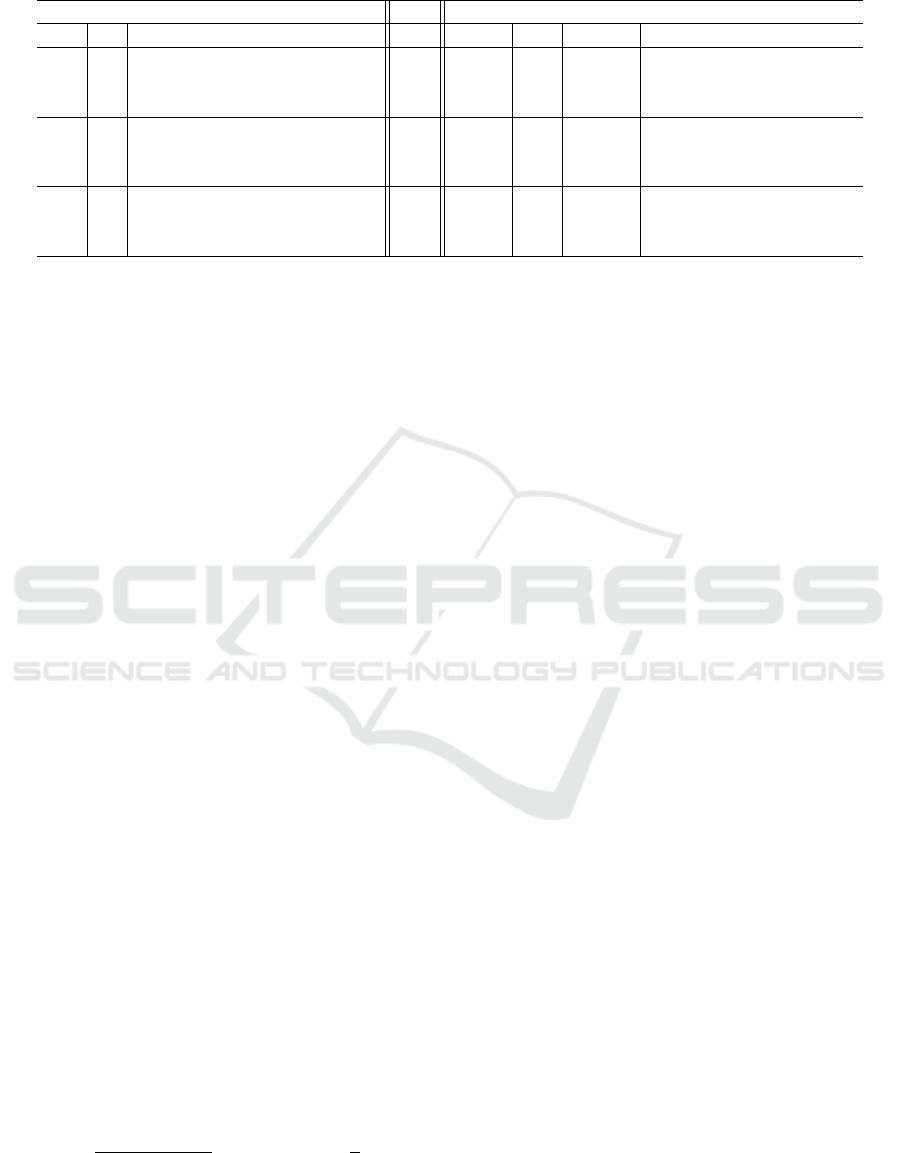
Table 2: Comparison of Winternitz OTS and the proposed OTS.
Winternitz proposed
l w KeyGen Sign Verify |σ| l θ 1/p
w,l,θ
KeyGen Sign Verify
64 29 1, 827 ≤ 1, 827 ≤ 1, 827 29L 579 76 2 2, 204 1, 625 579
579 66 4 1, 914 1, 335 579
579 59 8 1, 711 1, 132 579
128 25 3, 175 ≤ 3, 175 ≤ 3, 175 25L 984 144 2 3, 600 2, 616 984
984 123 4 3, 075 2, 091 984
984 111 8 2, 775 1, 791 984
256 22 5, 610 ≤ 5, 610 ≤ 5, 610 22L 1, 695 272 2 5, 984 4, 289 1, 695
1, 695 232 4 5, 104 3, 409 1, 695
1, 695 209 8 4, 598 2, 903 1, 695
Setup. The challenger runs KeyGen and provides the
public verification key VK to the adversary. The
private key SK is kept secret by the challenger.
Query. The adversary requests the challenger to
compute the signatures σ
1
, . . . , σ
q
for query mes-
sages m
1
, . . . , m
q
of its choice. The query can be
made adaptively, that is, m
i
can be determined af-
ter the adversary has obtained σ
1
, . . . , σ
i−1
.
Output. The adversary outputs (m
0
, σ
0
) expecting
that σ
0
is a valid signature of m
0
. It is required
that (m
0
, σ
0
) is different from any of (m
i
, σ
i
) with
1 ≤ i ≤ q (it is allowed that m
0
= m
i
but in that
case σ
0
must be different from σ
i
).
The adversary wins the game if (m
0
, σ
0
) is accepted
by Verify(VK, m
0
, σ
0
). A signature scheme is said
to be strongly existentially unforgeable if there is
no polynomial-time algorithm that plays the role of
the adversary and wins the game with non-negligible
probability. In the discussion of OTS schemes, a key
pair is used only once. Therefore, we restrict our-
selves to q = 1 in the Query phase in the game above:
the adversary chooses a message m, obtains a signa-
ture σ for m, and tries to forge (m
0
, σ
0
) , (m, σ).
4.2 Formal Security Proof
Assume that |T
[θ]
w,l
| > 1. The following lemma is
needed in the subsequent discussion.
Lemma 2. For ( f
1
, . . . , f
w
) and ( f
0
1
, . . . , f
0
w
) that are
chosen from T
[θ]
w,l
uniformly and independently, and
for any i with 1 ≤ i ≤ w;
1. Pr[ f
i
= f
0
i
] is not overwhelming (i.e., (1 − Pr[ f
i
=
f
0
i
]) is not negligible), and
2. Pr[ f
i
> f
0
i
] is bounded as
1 − Pr[ f
i
= f
0
i
]
2
≤ Pr[ f
i
> f
0
i
] <
1
2
.
Proof: Assume that Pr[ f
i
= f
0
i
] has overwhelming
probability. Write p
j
= Pr[ f
1
= j] for 0 ≤ j ≤ θ.
Notice that all of f
2
, . . . , f
w
, f
0
1
, . . . , f
0
w
obey the same
probability distribution as f
1
, and Pr[ f
i
= f
0
i
] is equal
to
P
θ
j=0
p
2
j
. Because Pr[ f
i
= f
0
i
] is overwhelming
as assumed, there is j with 0 ≤ j ≤ θ such that
p
j
is overwhelming. This implies that ( f
1
, . . . , f
w
) =
( f
0
1
, . . . , f
0
w
) = ( j, . . . , j) with overwhelming probabil-
ity, which contradicts the assumption that ( f
1
, . . . , f
w
)
and ( f
0
1
, . . . , f
0
w
) are chosen uniformly from T
[θ]
w,l
with
|T
[θ]
w,l
| > 1. This proves the (1) part of the lemma. The
(2) part is obvious because Pr[ f
i
> f
0
i
] = Pr[ f
i
< f
0
i
]
and Pr[ f
i
> f
0
i
] + Pr[ f
i
< f
0
i
] + Pr[ f
i
= f
0
i
] = 1.
We write p
w,l,θ
EQ
for Pr[ f
i
= f
0
i
]. It is difficult to
write down p
w,l,θ
EQ
in a simple formula, but Lemma 2(1)
guarantees that 1 − p
w,l,θ
EQ
is not negligible.
Theorem 3. If f
l,w
is collision-resistant and h is one-
way and collision-resistant, then the proposed OTS
scheme is strongly existentially unforgeable.
Proof: We show that if there is a polynomial-time al-
gorithm A
1
that wins the game of the strong existential
unforgeability, then we can construct A
2
that succeeds
in an attack on f
l,w
or h. The algorithm A
2
is given a
hash value y of the hash function h and attempts to
achieve either one of the following three goals.
• A
2
finds a collision of f
l,w
(i.e., A
2
makes (2) non-
negligible for f
l,w
).
• A
2
finds a pre-image of the given hash value y of
h (i.e., A
2
makes (1) non-negligible for h).
• A
2
finds a collision of h (i.e., A
2
makes (2) non-
negligible for h).
To make this possible, the algorithm A
2
plays the role
of the challenger of the game of the strong existential
unforgeability and let A
1
(which acts as the adversary
of the game) output a pair of a message and a sig-
nature. If A
1
succeeds in forging a valid signature,
then the signature contains essential information that
makes the attempts of A
2
succeed.
The algorithm A
2
performs the followings steps
for a given hash value y.
SECRYPT 2018 - International Conference on Security and Cryptography
302
e e e e e
6 6 6 6 6
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
6 6 6 6 6
e e u e e
6 6 6 6
.
.
.
.
.
.
.
.
.
.
.
.
6 6 6 6
e e e e e
· · · · · ·
· · · · · ·
· · · · · ·
v
0
1
s
1
v
0
α−1
s
α−1
v
0
α
y
s
α
v
0
α+1
s
α+1
v
0
w
s
w
6
?
6
?
β
θ
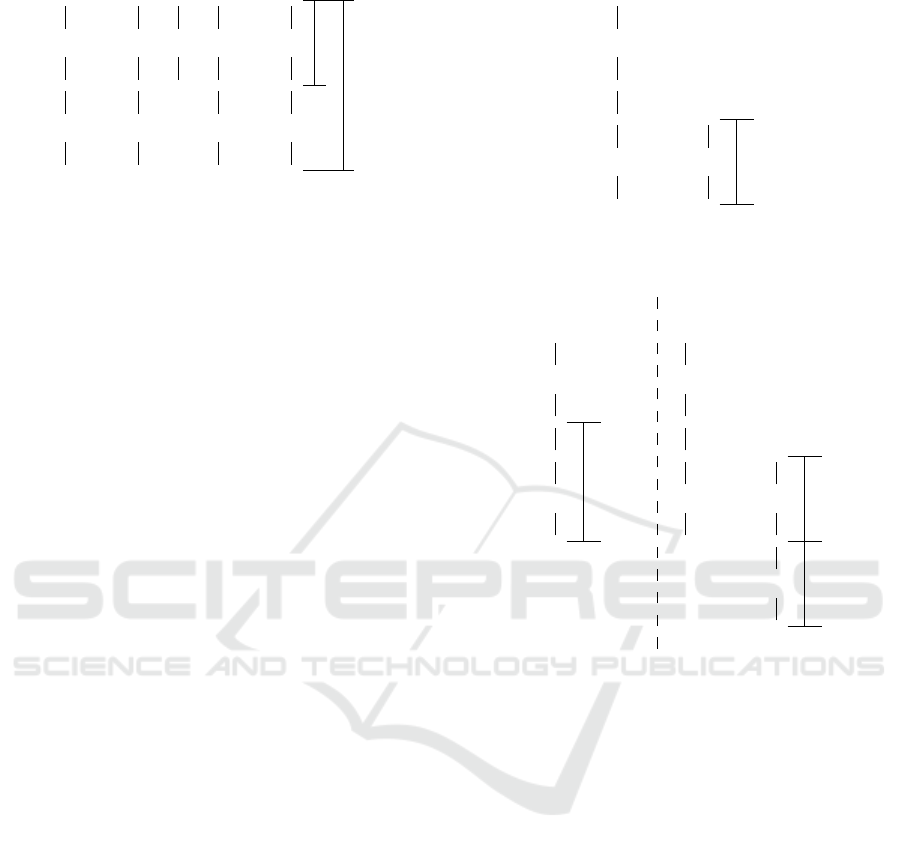
Figure 2: Modification of the verification key.
1. Run KeyGen and obtain a signing key SK =
(s
1
, . . . , s
w
) and a verification key VK =
(v
1
, . . . , v
w
), where v
i
= h
θ
(s
i
) for 1 ≤ i ≤ w.
2. Choose m
0
randomly, determine the nonce r
0
of m
0
, and also choose α uniformly at random
from {1, . . . , w}. Let β be the α-th component of
the constant-sum fingerprint f
l,w
(m
0
||r
0
). Define
VK
0
= (v
0
1
, . . . , v
0
w
), where
v
0
i
=
v
i
(i , α),
h
β
(y) (i = α),
and provide the altered verification key VK
0
to the
algorithm (adversary) A
1
as the outcome of the
Setup phase of the game. Fig. 2 illustrates the
construction of VK
0
where vertices represent hash
values and directed edges represent the applica-
tion of the hash function h.
3. Receive m from A
1
in the Query phase.
4. Find the nonce r of m and let f
l,w
(m||r) =
( f
1
, . . . , f
w
) ∈ T
[θ]
l,w
. If f
α
> β, then abort this
attack with failure. If f
α
≤ β, then compute
σ = (σ
1
, . . . , σ
w
), where
σ
i
=
h
θ− f
i
(s
i
) (i , α),
h
β− f
α
(s
α
) (i = α),
and return σ to A
1
as the signature of the query m.
5. Receive (m
0
, σ
0
) from the adversary A
1
in the Out-
put phase, and determine the nonce r
0
of m
0
. Con-
tinue one of the following options depending on
related values. We write σ
0
= (σ
0
1
, . . . , σ
0
w
) and
f
l,w
(m
0
||r
0
) = ( f
0
1
, . . . , f
0
w
).
(a) If m = m
0
, then we have r = r
0
and f
l,w
(m||r) =
f
l,w
(m
0
||r
0
). In this case, we must have σ , σ
0
due to the rule of the game, and there is i ∈
{1, . . . , w} with σ
i
, σ
0
i
. Note that different
hash chains starting from σ
i
and σ
0
i
eventually
converge to v
0
i
if (m
0
, σ
0
) is accepted by Verify
algorithm (see Fig. 3). Determine j such that
h
j
(σ
i
) , h
j
(σ
0
i
) and h
j+1
(σ
i
) = h
j+1
(σ
0
i
), and
output (z, z
0
) = (h
j
(σ
i
), h
j
(σ
0
i
)) as a pair that
causes a collision of h.
e
6
.
.
.
6
e
6
X
X
X
Xy
e e
6 6
.
.
.
.
.
.
6 6
e e
v
0
i
σ
i
σ
0
i
z z
0
6
?
j
Figure 3: Convergence of two hash chains.
e
6
.
.
.
6
u
6
e
6
.
.
.
6
e
v
0
α
y
x
0
σ
0
α
6
?
f
0
α
− β
(c)-i (c)-ii
e
6
.
.
.
6
e
6
X
X
X
Xy
e e
6 6
.
.
.
.
.
.
6 6
u e
6
.
.
.
6
e
y
0
σ
0
α
v
0
α
y
z z
0
6
?
6
?
j
f
0
α
− β
Figure 4: Relation among hash values.
(b) If m , m
0
and f
l,w
(m||r) = f
l,w
(m
0
||r
0
), then out-
put (z, z
0
) = (m||r, m
0
||r
0
) as a pair that causes a
collision of f
l,w
.
(c) If m , m
0
, f
l,w
(m||r) , f
l,w
(m
0
||r
0
) and f
0
α
> β,
then compute y
0
= h
f
0
α
−β
(σ
0
α
).
i. If y = y
0
, then output x
0
= h
f
0
α
−β−1
(σ
0
α
) as the
pre-image of y. The relation among hash val-
ues is illustrated in the left-part of Fig. 4.
ii. If y , y
0
, then determine j such that h
j
(y) ,
h
j
(y
0
) and h
j+1
(y) = h
j+1
(y), and output
(z, z
0
) = (h
j
(y), h
j
(y
0
)) as a pair that causes a
collision of h. This case is illustrated in the
right-part of Fig. 4.
(d) If none of the above conditions holds, then
abort this attack with failure.
Write the winning probability of A
1
as p
1
+ p
2
+ p
3
,
where p
1
is the probability that m = m
0
and A
1
wins
the game (we call this scenario A), p
2
is the probabil-
ity that m , m
0
, f
l,w
(m||r) = f
l,w
(m
0
||r
0
) and A
1
wins
the game (scenario B), and p
3
is the probability that
m , m
0
, f
l,w
(m||r) , f
l,w
(m
0
||r
0
) and A
1
wins the game
(scenario C). If A
1
wins the game with non-negligible
Hash-Based Signature with Constant-Sum Fingerprinting and Partial Construction of Hash Chains
303

probability, then at least one of p
1
, p
2
, and p
3
is non-
negligible. The algorithm A
2
may abort at Step 4,
but that probability is less than 1/2 by Lemma 2(2).
With probability more than 1/2, A
2
proceeds to Step
5. The algorithm A
2
performs Step 5(a) only if A
1
wins the game with the scenario A, and in this case,
the pair (z, z
0
) produced by A
2
is a collision pair of
h. The algorithm A
2
performs Step 5(b) only if A
1
wins the game with the scenario B, and in this case,
the pair (z, z
0
) produced by A
2
is a collision pair of
f
l,w
. The algorithm A
2
performs Step 5(c) only if A
1
wins the game with the scenario C, and furthermore,
f
0
α
> β is fulfilled simultaneously. This is an event
that occurs with probability p
3
1 − p
w,l,θ
EQ
/2 or more
by Lemma 2(2), and in this case, A
2
discovers a pre-
image x
0
of y or a collision pair (z, z
0
) of the hash func-
tion h. Summarizing the discussion, the algorithm A
2
succeeds in one of three attacks over f
l,w
and h with
probability is equal to or more than
1
2
p
1
+ p
2
+
p
3
2
1 − p
w,l,θ
EQ
.
If the winning probability of A
1
is non-negligible,
then so is the success probability of A
2
.
5 CONCLUSION
Constant-sum fingerprinting functions and partial
construction of hash chains are investigated to im-
prove Winternitz OTS. The constant-sum fingerprint-
ing function contributes to reduce the complexity of
the signature verification, which is advantageous in
certain services including wireless sensor networks.
The integer components of constant-sum fingerprints
distribute non-uniformly, which makes the partial
construction of hash chains an effective means to re-
duce the complexities of key generation and signing.
It is confirmed that the proposed scheme is more effi-
cient than Winternitz OTS in terms of the number of
computations of the hash function, while the scheme
is shown to be strongly existentially unforgeable. It
is noted that the technique that is investigated in this
study is compatible with other improvements that are
studied in (Buchmann et al., 2011b; Hulsing, 2013;
Buchmann et al., 2011a; Bernstein et al., 2015). We
can further improve the efficiency by combining the
investigated techniques with those in literature.
REFERENCES
Bernstein, D., Buchmann, J., and Dahmen, E. (2009). Post-
Quantum Cryptography. Springer.
Bernstein, D., Hopwood, D., Hulsing, A., et al. (2015).
Sphincs: Practical stateless hash-based signatures. In
EUROCRYPT 15, pages 368–397.
Bleichenbacher, D. and Maurer, U. (1996a). On the effi-
ciency of one-time digital signature schemes. In ASI-
ACRYPT 96, pages 145–158.
Bleichenbacher, D. and Maurer, U. (1996b). Optimal tree-
based one-time digital signature schemes. In Symp. on
Theoretical Aspects of Comp. Sci., pages 363–374.
Bollinger, R. and Burchard, C. (1990). Lucas’s theorem and
some related results for extended pascal triangles. The
American Math. Monthly, 97(3):198–204.
Boneh, D., Shen, E., and Waters, B. (2006). Strongly un-
forgeable signatures based on computational diffie-
hellman. In Intl. Conf. on Theory and Practice of
Public-Key Cryptography, pages 229–240.
Buchmann, J., Dahmen, E., , and Hulsing, A. (2011a).
Xmss—a practical forward secure signature scheme
based on minimal security assumptions. In Intl. Conf.
on Post-Quantum Cryptography, pages 117–129.
Buchmann, J., Dahmen, E., Ereth, S., et al. (2011b). On the
security of the winternitz one-time signature scheme.
In AFRICACRYPT 11, pages 363–378.
Cruz, J., Yatani, Y., and Kaji, Y. (2016). Constant-sum fin-
gerprinting for winternitz one-time signature. In Intl.
Symp. on Inf. Theory and Its App., pages 703–707.
Dods, C., Smart, N., and Stam, M. (2005). Hash based dig-
ital signature schemes. In Intl. Conf. on Cryptography
and Coding, pages 96–115.
Goldwasser, S. and M. Bellare, M. (2018). Lecture
notes on cryptography. https://cseweb.ucsd.edu/ ˜mi-
hir/papers/gb.pdf, accessed February 14.
Hulsing, A. (2013). W-ots
+
— shorter signatures for
hash-based signature schemes. In AFRICACRYPT 13,
pages 173–188.
Lamport, L. (1979). Constructing digital signatures from
a one-way function. Technical Report SRI-CSL-98,
SRI Intl. Computer Sci. Lab.
Merkle, R. (1990). A certified digital signature. In CRYPTO
89, pages 218–238.
Perrig, A. (2001). The biba one-time signature and broad-
cast authentication protocol. In ACM Conf. on Com-
puter and Communications Security, pages 28–37.
Perrig, A., Szewczyk, R., Wen, V., et al. (2002). Spins:
Security protocols for sensor networks. Wireless Net-
works J., 8(5):521–534.
Reyzin, L. and Reyzin, N. (2002). Better than biba: Short
one-time signatures with fast signing and verifying. In
Intl. Inf. Security and Privacy Conf., pages 1–47.
Shor, P. (1997). Polynomial-time algorithms for prime fac-
torization and discrete logarithms on a quantum com-
puter. SIAM J. of Computing, 26(5):1484–1509.
SECRYPT 2018 - International Conference on Security and Cryptography
304
