
Towards an Evolution Strategy Approach in Binary Image
Registration for Solving Digital Signature Recognition Tasks
Catalina Cocianu and Alexandru Stan
Computer Science Department, Bucharest University of Economics, Bucharest, Romania
Keywords: Digital Signature based Security Systems, Evolution Strategies, Image Registration, Mutual Information.
Abstract: This paper focuses on the development of an image registration methodology for digital signature
recognition. We consider two perturbation models, namely the rigid transformation and a mixture of shear
and rigid deformation. The proposed methodology involves three stages. In the first stage, both the acquired
image and the stored one are binarized to reduce the computational effort. Then an evolution strategy (ES)
is applied to register the obtained binary images. The quality of each chromosome belonging to a certain
population is evaluated in terms of mutual information-based fitness function. In order to speed up the
computation of fitness values, we propose a computation strategy based on the binary representation of
images and the sparsity of the image matrices. Finally, we evaluate the registration capabilities of the
proposed methodology by means of quantitative measures as well as qualitative indicators. The
experimental results and some conclusions concerning the capabilities of various methods derived from the
proposed methodology are reported in the final section of the paper.
1 INTRODUCTION
Digital image registration is one of the most
important tasks in various systems which evaluate
images, including sensed image recognition, global
land monitoring in satellite images, aligning medical
images. The main aim of any registration technique
is to align images acquired at different times, using
different sensors and from different viewpoints. In
the following we adopt the assumption that the
variations in the analysed images are due to the
acquisition system and can be removed by applying
various geometric transformations (Goshtasby,
2012; Modersitzki, 2004).
The most studied perturbation models involves
spatial transformations of rigid, affine, projective,
and respectivelly global polynomial type. In our
work we consider two perturbation model, the rigid
one and the affine transformation. The rigid
transformation is described in terms of translation,
rotation, and scale changes. The affine
transformation is more general than the rigid one
and is expressed as a mixture of rigid, shear and
aspect ratio changes.
So far, various classes of registration techniques,
mainly depending on the perturbation model, have
been presented in the literature (Goshtasby, 2012;
Zhuang et al., 2016; Yang, Papa, 2017). One of the
most popular classes of registration techniques is the
optimization-based class that includes, besides direct
optimization methods, evolutionary-based
approaches (Zhang, Wu, 2012; Khader, Hamza,
2012; Mohamed, Hamza 2010; Singhai, Singhai,
2012). The evalutionary approaches of image
registration are developed based on certain similarity
measure corresponding to the fitness function. The
methods involve heuristic search through the
registration parameter values space to compute the
variant maximizing the fitness function.
Our research work focuses on the development
of an image registration methodology for digital
signature recognition. More preciselly, we address
the problem of a particular component of banking
security systems using the client’s signature. In
order to process payments, the system should
recognize the client signature prior to finalizing the
operation. The process mainly consists of the
following steps: scan the payment order, identify the
client’s signature and compare it with its
corresponding stored version. In most of the cases
the sensed signature is different from the stored one
from the geometrical point of view. We restrict the
problem to two perturbation models, namely the
Cocianu, C. and Stan, A.
Towards an Evolution Strategy Approach in Binary Image Registration for Solving Digital Signature Recognition Tasks.
DOI: 10.5220/0006789504690476
In Proceedings of the 20th International Conference on Enterprise Information Systems (ICEIS 2018), pages 469-476
ISBN: 978-989-758-298-1
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
469

rigid transformation and a mixture of shear and rigid
deformation. The second model is considered in
order to suggest a viable methodology to register
images disturbed by affine transformations. The
proposed methodology involves three stages. To
reduce the computational complexity, in the first
stage, binary versions of both the acquired image
and the stored one are computed. Then an evolution
strategy (ES) is applied to register the obtained
binary images. The quality of each chromosome
belonging to a certain population is evaluated in
terms of mutual information-based fitness function.
The recombination schemes developed to compute
offspring populations involve standard local or
global convex and respectively discrete crossover
procedures as well as new hybrid methods. The
proposed hybrid approaches are set out taking into
account the geometric relationship between the
chromosome alleles. The mutation operator is of
uncorrelated multistep sizes type. Also, we propose
a computation strategy based on the binary
representation of images and the sparsity of the
image matrices to speed up the computation of
fitness values. Finally, we evaluate the registration
capabilities of the proposed methodology by means
of quantitative measures as well as qualitative
indicators.
Note that the proposed methodologies can be
used to register any binary images represented by
sparse matrices.
The rest of the paper is organized as follows: in
Section 2 we briefly present the affine spatial
transformations. The main characteristics of the
evolution strategies (ES) based on uncorrelated
multiple parameters mutation are provided in
Section 3. The proposed registration methodology is
described in the fourth section of the paper. The
obtained results and some experimentally
established conclusions are supplied in the final part
of the paper.
2 AFFINE SPATIAL
TRANSFORMATIONS
The rigid transformation is described in terms of
translation, rotation, and scale changes. Its main
property is that the objects in images hold their
relative shape and dimensions.
The general affine transformations consist of
more general geometric distortions and they are
linear in the sense that straight lines are mapped into
straight lines. (Brown, 1992)
The 2D rigid transformation having as inputs the
image
and the parameters
a,b,s,θ
produces the
output
defined by
I
2
x,y
=I
1
x
1
,y
1
(1)
x
1
y
1
=
a
b
+s
cos
θ
-
s
in
θ
s
in
θ
cos
θ
x
y
(2)
where
a
b
defines the translation, s stands for the
scale factor and R=
cos θ -sinθ
sin θ cos θ
is the rotation
matrix.
A 2D affine transformation characterised by the
parameters A=
a
11
a
12
a
21
a
22
and b=
b
1
b
2
maps the
input image
into image
such that
I
2
x,y
=I
1
x
1
,y
1
(3)
x
1
y
1
=
a
11
a
12
a
21
a
22
x
y
+
b
1
b
2
(4)
Besides the rigid spatial transformations, the affine
transformations consist of shear effect acting along
axes and changes in aspect ratio, as follows:
shear along and respectively, defined by
F
x
=
1 d
01
, F
y
=
10
h 1
(5)
changes in aspect ratio, given by the matrix
S
s
x
0
0
s
y
(6)
As we have mentioned before, the affine
transformations are obtained by applying any
sequence of rigid transformations, shears and
changes in aspect ratio. (Brown, 1992)
3 EVOLUTION STRATEGIES
Evolution strategies belong to evolutionary
algorithms class, being typically used for continuous
parameter optimization problems (Eiben, Smith,
2003). One of the most important characteristics of
ES is self-adaptability, a mechanism that adjusts the
mutation strategy as the search is progressing by
updating certain EA parameters during the evolution
process (
Edelkamp, Schrodl, 2012).
Self-adaptation involves the fact that some
parameters are included in the chromosome
representation, therefore the computation process
updates them too. If the phenotype space is
then
in a typical ES the chromosome representation is
ICEIS 2018 - 20th International Conference on Enterprise Information Systems
470

straightforward, each individual x∈
being given
by its variables x
1
,…,x
n
∈. In case of self-
adaptability, x=(x
1
,…,x
n
)
is only part of a genotype.
If we consider the standard uncorrelated multistep
mutation, each chromosome encoding a candidate
solution x=(x
1
,…,x
n
) is defined in terms of a
solution part,c
sol
, and a parameter part, c
step_size
as
follows (Eiben, Smith, 2003)
c= x
1
,…,x
n
c
sol
, σ
1
,…,σ
n
c
s
te
p_
size
(7)
ES methods usually use fixed size population model.
In ES the whole population produces offspring. The
offspring population should be significantly larger
than the current multiset. The recommended size of
offspring population is λ
≅7
·
μ, where μ denotes the
population size. The recombination is either local or
global. In case of local recombination each child is
computed based on a single pair of parents. The
global crossover involves more general computation
scheme. Each allele of a child is calculated using
pair of parents randomly drawn from the current
population. The procedures that implements the
computation of an allele is either discrete or convex
with a certain random weight α ∈ (0,1). (Beyer,
2001; Eiben, Smith, 2003)
The uncorrelated mutation with multiple step
sizes is developed such that the dimensions are
treated differently. In other words, different solution
alleles are affected by different white noises. The
mutated version of a chromosome
c=x
1
,…,x
n
,σ
1
,…,σ
n
is the genotype
c
'
=x
1
'
,…,x
n
'
,σ
1
'
,…,σ
n
'
computed as follows. First,
mutate the parameter variables of based on the
relation
σ
i
'
= σ·expr
τ,i
+r
τ
'
(8)
where r
τ
'
denotes a draw from the distribution
N(0,τ
'
), r
τ,i
is a distinct draw from the distribution
N0,τ) for each 1≤i
≤n. The most commonly used
settings of the parameters τ and τ
'
are
τ∝
1
2∙
√
n
(9)
τ
'
∝
1
√
2∙n
(10)
Next update the solution alleles of using the
relation
x
i
'
=x
i
+f
x
i
(11)
where f
x
i
is a separate draw from N0,σ
i
'
for each
1≤i
≤n. Finally, one can apply the rule
if
σ
i
'
ε
σ
then
σ
i
'
←
ε
σ
to avoid the use of very small step sizes.
The survivor selection is deterministic, the most
commonly used schemes being
μ
,
λ
and
μ
+
λ
(
Eiben, Smith, 2003).
4 THE PROPOSED ES
REGISTRATION
METHODOLOGY
Taking into account the characteristics of the
processed images, i.e. digital signatures, the
proposed methodology is developed using binary
images. Let I be a M ×
Ngray scale image. The
binary variant of I, BI, is computed using a threshold
function as follows
BI
x,y
=
1,
I
x
,y
>127
0, otherwise
(12)
We consider that the pixel
x,y
is of background
type if BI
x,y
=1, otherwise it belongs to one of the
objects represented in image I.
The following ES-based method solves the
alignment problem of two binary images, the target
T and the sensed image I.
Two different perturbation models are addressed
in our approach. The first degradation model is
defined in terms of rigid transformation only. Thus
the observed image I is given by
I
x,y
=T
f
0
x,y
T
(13)
where for each 1≤x
≤M and 1≤y
≤N
f
0
x,y
=
a
b
+s∙
cos
θ
-
s
in
θ
s
in
θ
cos
θ
∙
x
y
(14)
The second perturbation model is a sequence of a
shear transformation, acting along the x axis, and
respectively a rigid function. We consider this
second model to explain how the registration
methodology in case of rigid perturbation can be
extended to the more general case of affine
transformation. Note that the affine degradation is a
mixture of rigid, shear and aspect ratio changes,
each one of these being added to the first model
accordingly.
The function that expresses the above mentioned
degradation process is defined by
Towards an Evolution Strategy Approach in Binary Image Registration for Solving Digital Signature Recognition Tasks
471

f
1
x,y
=
1 d
01
∙f
0
x,y
(15)
and the sensed image I is computed as
I
x,y
=T f
1
x,y
T
(16)
In order to solve the registration problem, one has to
compute a function f
x,y
such that
I f
x,y
T
=T
x,y
. Note that R
-1
=R
T
, i.e. the
rotation matrix is orthogonal. In case of rigid
transformation the function f is defined in terms of
parameters
a,b,s,θ
by
f
a,b,s,θ
x,y
=
1
s
∙R
T
∙
x
y
-
a
b
(17)
If we consider the second model, the function f is
expressed using the parameters
d,a,b,s,θ
by
f
d,a,b,s,θ
x,y
=
1
s
∙R
T
∙
1-d
01
∙
x
y
-
a
b
(18)
Based on the uncorrelated multistep sizes mutation
idea, we design an evolution strategy in which the
solution sequence of an individual is either
c
sol
=
a
c
,b
c
,s
c
,θ
c
or c
sol
=
d
c
,a
c
,b
c
,s
c
,θ
c
.
The genotype space consists of vectors c
described by
c= a
c
,b
c
,s
c
,θ
c
c
sol
, σ
a
c
, σ
b
c
,σ
s
c
,σ
θ
c
c
s
te
p_
size
(19)
in case of model (14) and respectively by
c= d
c
,a
c
,b
c
,s
c
,θ
c
c
sol
, σ
d
c
,σ
a
c
, σ
b
c
,σ
s
c
,σ
θ
c
c
s
te
p_
size
(20)
in case of the degradation model (15). The
parameters σ
d
c
,σ
a
c
, σ
b
c
,σ
s
c
,σ
θ
c
stand for the step sizes
corresponding to the solution alleles. We adopt the
fixed size population model and we denote by μ the
population size.
One of the most important components of an ES
is represented by the fitness function. From the
evolutionary computing point of view, the role of the
fitness function corresponds to the requirements
each genotype should adapt to. From the
mathematical point of view, the fitness function is an
objective function to be maximized. In our work the
fitness value of each chromosome c representing the
similarity between the target image T and the
computed variantI
c
=I f
d
c
,a
c
,b
c
,s
c
,θ
c
is expressed in
terms of MI (Mutual Information) measure.
In the following we denote by the space of images
having the same sizes N and M, and L gray levels.
Let I
1
,I
2
∈.The mutual information MII
1
,I
2
is
defined in terms of Shannon entropy H∙ and joint
entropy H(∙,∙ by (Cover, Thomas, 2006)
MI
I
1
, I
2
=H
I
1
+H
I
2
-H
I
1
, I
2
(21)
where
H
I
=- p
i
∙logp
i
L
i
=1
(22)
H
I
1
, I
2
= - p
i,j
∙logp
i,j
1≤ i,
j
≤L
(23)
Obviously,
max
J
∈
MI
I, J
=MI
I, I
=H
I
(24)
The fitness function of a chromosome c is given by
fitness
c
=
MI
T,
I
c
MI
T,
T
=
MI
T,
I
c
H
T
(25)
Using (24) and (25) we get that the maximum fitness
value is 1 and it can be obtained when I
c
=T.
The recombination procedure enables self-
adaptability of the resulted ES method. Let us denote
by
the current population and let k be a constant,
k
>1. The offspring population
having λ
=k
∙μ
individuals is computed using either local or global
procedures described in Section 3, or hybrid
crossover mechanisms. The standard crossover is
usually used when k≤1, for example by genetic
algorithms. Typically, ES uses global recombination
strategies, but in case of very complex problems
these approaches could lead to intractable
algorithms. Thus we propose various hybrid
recombination methods to find a trade-off between
the quality of the results and the computational
complexity.
The proposed hybrid approaches are set out
taking into account the geometric relationship
between the chromosome alleles.
In case of the degradation model (14), two
hybrid recombination strategies can be considered.
The parameters are divided:
into two groups: the translation variables set and
the rotation and scale factors – strategy RHYB1;
into three classes: translation variables, scale
factor and rotation angle – procedure RHYB2;
In case of the degradation model (15), the most
natural ways to divide parameters are:
ICEIS 2018 - 20th International Conference on Enterprise Information Systems
472

into two classes, each group corresponding to one
of the perturbation transformations, share and
rigid respectively – strategy SRHYB1;
into three classes: share factor, translation
variables, and rotation and scale factors– strategy
SRHYB2;
into four groups: share factor, translation
variables, rotation angle and scale factor– strategy
SRHYB3.
The corresponding crossover procedure SRHYB1 is
presented below.
SRHYB 1
for i=1…λ c results as follows
randomly select p1,q1∈
and compute
d
c
,σ
d
c
←crossover between
d
p1
,σ
d
p1
and d
q1
,σ
d
q1
randomly select p2,q2∈
and compute
a
c
,b
c
,s
c
,θ
c
,σ
a
c
,σ
b
c
σ
s
c
,σ
θ
c
←
crossover betweena
p2
,b
p2
,s
p2
,θ
p2
,σ
a
p2
,σ
b
p2
,σ
s
p2
,σ
θ
p2
anda
q2
,b
q2
,s
q2,
θ
q2
,σ
a
q2
,σ
b
q2
,σ
s
q2
,σ
θ
q2
c=d
c
,a
c
,b
c
,s
c
,θ
c
,σ
d
c
,σ
a
c
,σ
b
c
,σ
s
c
,σ
θ
c
The proposed hybridization techniques perform the
recombination taking into account the grouping
strategy, similarly to procedure SRHYB1. The
survivor selection mechanism is applied in a
deterministic manner to obtain the next generation,
.
In the following we consider only the
degradation model (15), because of its generality.
From the implementation point of view, in case of
fitness function defined by (25), each chromosome
c=d
c
,a
c
,b
c
,s
c
,θ
c
,σ
d
c
,σ
a
c
,σ
b
c
,σ
s
c
,σ
θ
c
is evaluated
based on the procedure FITNESS as follows.
FITNESS(c)
F=
1
s
c
∙R
c
T
A=F ∙
1-d
c
01
;B=-F∙
a
c
b
c
for i=1….M
for j=1….N
x
y
=A∙
i
j
+B
I
C
i,j
=T
x,y
Compute
MIT,I
c
HT
Next we intend to speed up the computation of
FITNESS(c) by proposing an alternative procedure
based on the binary representation of images and the
sparsity of the image matrices. For a given
chromosome c we compute a new image I
c
new
by
I
c
new
x,y
=T
f
1
x,y
T
=Tx
T
,y
T
(26)
where
x
T
y
T
=
1 d
c
01
∙
a
c
b
c
+s
c
∙R
c
x
y
(27)
Obviously, MI
I
c
new
,I
=1 if I=I
c
new
. Let
be the
set of object pixels belonging to T. We get that
|
|
≪N·M. The image corresponding to c is
computed using the following procedure.
Step1. I
c
new
x,y
←1 , 1≤x
≤M, 1≤y
≤N
Step 2. I
c
new
x,y
←0 for all
x,y
such that
x
T
,y
T
∈
where
x
T
y
T
=
1 d
c
01
∙
a
c
b
c
+s
c
∙R
c
x
y
(28)
Consequently,
x
y
=
1
s
c
∙R
c
T
∙
1 -d
c
01
∙
x
T
y
T
-
a
c
b
c
(29)
The algorithm FITNESS can be replaced by
FITNESS1 described below.
FITNESS1(c)
I
c
new
x,y
←1 , 1≤x≤M, 1≤y≤N
F=
1
s
c
∙R
c
T
A=F ∙
1-d
c
01
;∙
for all x
T
,y
T
∈
x
y
=A∙
x
T
y
T
+B
I
c
new
x,y
←0
Compute MI
I
c
new
,I
It is worth to mention that the image I
c
new
computed
by FITNESS1(c) should be close to from the
similarity measure MI
I
c
new
,
I
point of view. The
algorithm first computes the best individual of the
current population, best, then computes I
best
and
finally applies the transform FITNESS(best) to
compute the fitness function
MI
T,I
best
H
T
. Note that, in
case of sparse matrices, the computation scheme
FITNESS1 is significantly faster than the procedure
FITNESS.
Towards an Evolution Strategy Approach in Binary Image Registration for Solving Digital Signature Recognition Tasks
473

5 EXPERIMENTAL RESULTS
We have performed an extensive testing work to
evaluate the performances of the proposed
methodology. In our work, the ES parameters are:
the initial values of σ-parameter, ε
σ
, the
minimum value of each step size, NMax, the
maximum number of generations, and τ, a threshold
parameter controlling the best fitness value, τ∈
0,1.
The quality of each resulted algorithm from the
accuracy point of view has been measured in terms
of success rates. We denote by NR the number of
algorithm executions and let NS be the number of
successful runs. An algorithm run is successful if the
fitness of the final best individual exceeds 0.9. The
success rate of a certain algorithm, SR, is given by
SR=
NS
NR
∙100%
(30)
We also used the SNR quantitative similarity
measure to evaluate the registration quality. Let
and T be M×N images. Then
SNR
S,T
=
10*log
10
∑∑
S
x,y
2
N
y=1
M
x=1
∑∑
T
x,y
-S
x,y
2
N
y=1
M
x=1
(31)
A. In case of rigid transformation, we used the
following setting of the parameters: μ=30, λ=200,
NMax=100, τ=0.925. The initial step sizes were
established taking into account the genotype space.
The corresponding translation step sizes were set to
1, while the step sizes associated to scale factor and
rotation angle respectively were set in
0.01,0.25
.
The minimum value of each step size was set to
0.005. The value of NR was set to 300. Each time
the convex recombination scheme is applied the
value of is randomly drawn in the interval
0,1
.
The results of applying the proposed
methodology on a large set of digital signature
images are displayed in Table 1. The tests pointed
out that the best success rate and SNR values were
obtained in case of using the proposed RHYB1
procedure, where only convex recombination
scheme was considered. Also, the survivor selection
mechanism should be (μ
+ λ)
.
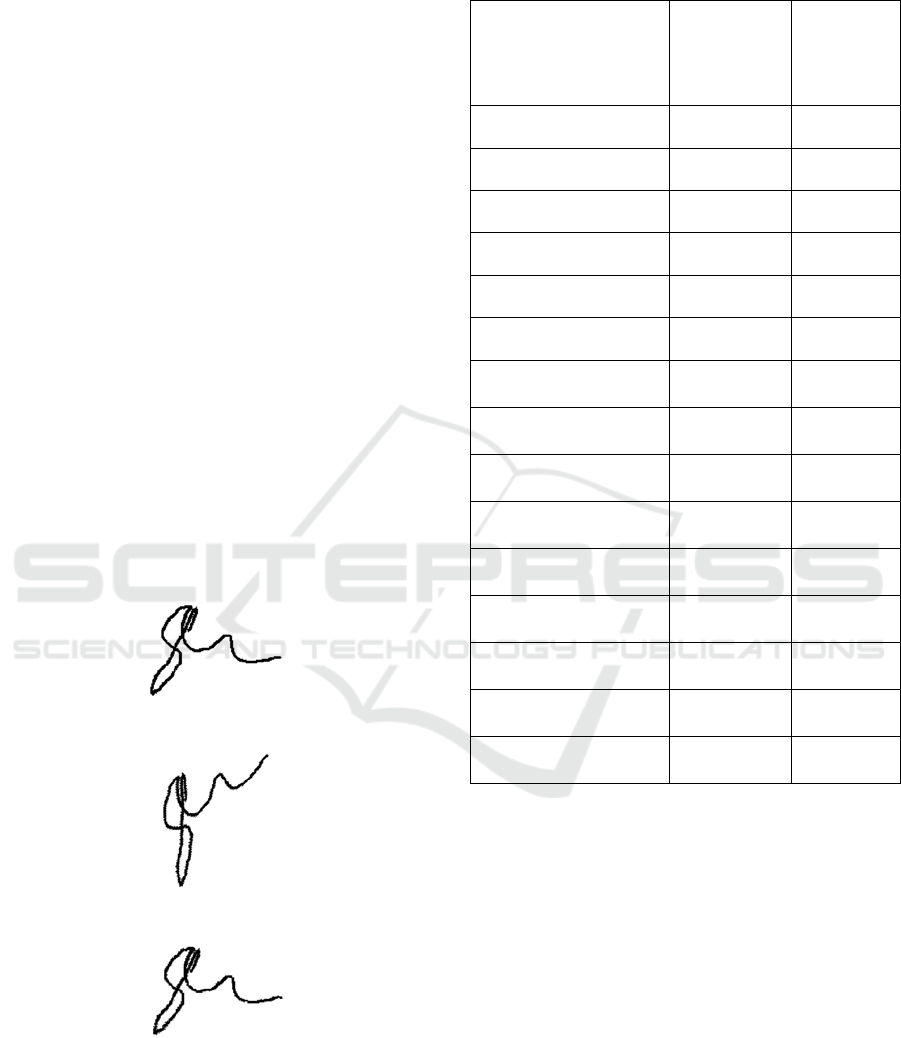
An instance of a digital signature representing
the target image is displayed in Figure 1 while its
corresponding sensed image is presented in Figure 2.
One of the results obtained when the proposed
RHYB 1 procedure is used together with the convex
recombination operator, and the survivor selection
scheme is (μ
+ λ), is supplied in Figure 3.
The experiments pointed out that the best SNR
value is around 29, while SNR
I,T
=10.9698
Figure 1: Target image.
Figure 2: Sensed image.
Figure 3: The result of the proposed alignment
methodology.
Table 1: The mean success rates for different ES
implementations.
Crossover Procedure
Solution part/ Parameter
part
Success rate
Survivor
Selection
(
μ
+ λ)
Success rate
Survivor
selection
(
μ
, λ)
Local Convex/Local
Convex
97%
90%
Local Convex/Local
Discrete
91.33%
48.33%
Local Discrete/Local
Convex
92.33%
87%
Global Convex/Global
Convex
97%
91%
Global Convex/Global
Discrete
90.33%
32.33%
Global Discrete/Global
Convex
94%
87.67%
RHYB1
Convex/
RHYB1
1 Convex
98.67%
91%
RHYB1
Convex/
RHYB1
Discrete
93%
29.33%
RHYB1
Discrete/
RHYB1
Convex
95.33%
89.33%
RHYB
2 Convex/
RHYB
2 Convex
94.33%
87%
RHYB
2 Convex/
RHYB
2 Discrete
89.67%
30.33%
RHYB
2 Discrete/
RHYB
2 Convex
95.33
90%
ICEIS 2018 - 20th International Conference on Enterprise Information Systems
474
B. If we consider the perturbation model (15), the
parameter settings are: μ=30, λ=200, NMax=120,
τ=0.9. The dispersions of the translation parameters
were set to 1, while the step sizes associated to scale
factor, rotation angle and shear factor respectively
were set in the range
0.01,0.05
. The minimum
value of each step size was 0.005. The value of NR
was set to 200. The parameter defining the convex
crossover is randomly drawn in
0,1
each time a
new allele is computed. In this case the procedure
SRHYB3 implemented based only the convex
crossover proved to be the most successful strategy
from both points of view of mutual information ratio
and SNR measure respectively. Note that similar
results are obtaining when a common global strategy
is applied, but with higher computational effort as
compared to the above mentioned procedure. The
results are provided in Table 2.
An instance of a digital signature representing
the target image is displayed in Figure 4 while its
corresponding sensed image is presented in Figure 5.
One of the results obtained when the proposed
SRHYB3 procedure is used together with the convex
recombination operator, and the survivor selection
scheme is (μ
+ λ), is supplied in Figure 6.
The experiments pointed out that the best SNR
value is around 26, while the SNR value between the
sensed image and the target one is 10.7737.
Figure 4: Target image.
Figure 5: Sensed image.
Figure 6: The result of the proposed alignment
methodology.
Table 2: The mean success rates for different ES
implementations.
Crossover Procedure
Solution part/ Parameter
part
Success rate
Survivor
Selection
(μ
+ λ)
Success
rate
Survivor
selection
(
μ
, λ)
Local Convex/Local
Convex
92%
59%
Local Convex/Local
Discrete
79%
44.5%
Local Discrete/Local
Convex
91%
81.5%
Global Convex/Global
Convex
98%
83.5%
Global Convex/Global
Discrete
85.5%
21%
Global Discrete/Global
Convex
98.5%
93%
SRHYB1
Convex/
SRHYB1
1 Convex
95%
86%
SRHYB1
Convex/
SRHYB1
Discrete
78%
49.5%
SRHYB1
Discrete/
SRHYB1
Convex
85.5%
87.5%
SRHYB
2 Convex/
SRHYB
2 Convex
97.5%
87.5%
SRHYB
2 Convex/
SRHYB
2 Discrete
79.5%
28.5%
SRHYB
2 Discrete/
SRHYB
2 Convex
89.5%
89.5%
SRHYB3 Convex/
SRHYB3 Convex
98.5%
90%
SRHYB 3 Convex/
SRHYB 3 Discrete
85%
29%
SRHYB 3 Discrete/
SRHYB 3 Convex
92.5%
92%
6 CONCLUSIONS
We have performed an extensive testing work to
evaluate the performances of the proposed
methodology. The effectiveness of our ES-based
strategies has been established by implementing it
using various crossover procedures as well as
different selection techniques to compute the next
generation.
The tests pointed out that the best success rate
and SNR values were obtained in case of using the
proposed hybrid procedures together with the
survivor selection scheme (μ
+ λ).
Taking into account the quality of the
experimental results, we conclude that more
Towards an Evolution Strategy Approach in Binary Image Registration for Solving Digital Signature Recognition Tasks
475

effective registration methods could be derived by
extending the proposed approach to other complex
degradation models.
REFERENCES
Beyer, H., 2001. The Theory of Evolution Strategies.
Berlin, Heidelberg: Springer Berlin Heidelberg.
Cover, T. and Thomas, J., 2006. Elements of information
theory. Chichester, Wiley-Interscience John Wiley &
Sons.
Edelkamp, S. and Schrödl, S., 2012. Heuristic search.
Amsterdam: Morgan Kaufmann.
Eiben, A. and Smith, J. 2003. Introduction to Evolutionary
Computing. Berlin, Heidelberg: Springer Berlin
Heidelberg.
Goshtasby, A.A., 2012. Image Registration: Principles,
Tools and Methods, Springer Science & Business
Media London.
Gottesfeld Brown, L., 1992 A Survey of Image
Registration Techniques ACM Computing Surveys,
Vol. 24, No. 4, pp.325-376.
Khader, M., Hamza, A.B., 2012. An information-theoretic
method for multimodality medical image registration.
Expert Syst. Appl. 39 (5), 5548–5556.
Modersitzki, J., 2004. Numerical Methods for Image
Registration, Oxford University Press.
Mohamed, W., Hamza, A., 2010. Medical image
registration using stochastic optimization. Opt. Laser.
Eng. 48 (12), 1213–1223.
Pluim, J., Maintz, J. and Viergever, M., 2003. Mutual-
information-based registration of medical images: a
survey. IEEE Transactions on Medical Imaging,
22(8), pp.986-1004.
Singhai, R., Singhai, J., 2012. Registration of satellite
imagery using genetic algorithm. Proceedings of the
World Congress on Engineering (WCE 2012),
London, UK,vol. 2, pp. 201–206.
Viola, P. and Wells, W., 1997. Alignment by
maximization of mutual information. Proceedings of
IEEE International Conference on Computer Vision,
24(2), pp.137-154.
Yang, X. and Papa, J., 2017. Bio-inspired computation
and applications in image processing. Elsevier.
Zhang, Y., Wu, L., 2012. A novel method for rigid image
registration based on firefly algorithm. Int. J. Res. Rev.
Soft Intell. Comput. 2 (2), 141–146.
Zheng, L., Tong, R., 2011. Image registration algorithm
using an improved PSO algorithm. ICCIC 2011, Part
IV, CCIS, 234, pp. 198–203.
Zhuang, Y., Gao, K., Miu, X., Han, L. and Gong, X.,
2016. Infrared and visual image registration based on
mutual information with a combined particle swarm
optimization – Powell search algorithm. Optik -
International Journal for Light and Electron Optics,
127(1), pp.188-191.
Wang, Z., Bovik, A., Sheikh, H. and Simoncelli, E., 2004.
Image Quality Assessment: From Error Visibility to
Structural Similarity. IEEE Transactions on Image
Processing, 13(4), pp.600-612.
ICEIS 2018 - 20th International Conference on Enterprise Information Systems
476
