
Crowdsourced System to Report Traffic Violations
RoadCop: Bi-Modular System
Maryam Jameela
1
, Hammad Afzal
2
, Khawar Khurshid
1
and Asad Waqar Malik
1
1
School of Electrical Engineering and Computer Science,
National University of Science and Technology, Islamabad, Pakistan
2
Department of Computer Software Engineering, National University of Science and Technology, Islamabad, Pakistan
Keywords:
Crowdsourcing, Mobile Crowdsourcing, Mobile Applications, Web Application, Traffic Violations, Data
Sciences, Traffic Surveillance, Internet-of-Things, Smart Cities, Transportation.
Abstract:
With increasing demand of transportation, implementation of the traffic regulations has become a major chal-
lenge for the developing countries. Most of the traffic accidents occur due to violation of traffic rules, thus,
resulting in loss of human lives and property. The developed countries have addressed the situation by deploy-
ing surveillance systems at intersection, but the solution can be expensive; therefore, due to the cost factor the
solution is out of reach for many underdeveloped countries. In order to overcome the situation, a framework is
proposed that is based on crowdsourced model to report violations supplemented by the video evidence. The
user reports are evaluated in multiple phases. In the first stage, spam is eliminated through evaluation, and as-
sociated user profiles are blocked. In the second stage, traffic law experts evaluate the report and on every valid
report the users are rewarded with incentive points while ensuring the anonymity. The system is evaluated for
usability, advantages to authorities, citizen involvement, skills and resources required and transparency. The
results of functional testing indicate that the participants appreciated the purpose of the application and found
it quite easy to use. With a large-scale deployment and an effective mechanism to identify offender, this system
can lead to much improved implementation of traffic regulations.
1 INTRODUCTION
Transportation is one of the basic necessities of life.
With technology advancement, new techniques have
been adopted to optimize the transportation system.
Moreover, with growing needs of user, one of core
objective is to build the system that is safe and easy
to manage large number of users. According to the
recent statistics
1
the average death rate in Pakistan
due to road accidents is approx. 20.22% in the year
2014.These statistics are also alarming in countries
such as Iraq, Iran, and Venezuela where the numbers
are as high as 43.545%, 41.415%and 41.065% respec-
tively (WHO, 2016). According to World Health Or-
ganizations (WHO) fact sheet in the year 2016 ,the
road traffic injuries are the leading cause of death
among young people. The traffic violations, careless
driving attitude and a weak infrastructure are the main
causes of traffic accidents resulting in higher casualty
rates. Further, according to WHO the road traffic ac-
cident will become the seventh leading cause of death
1
worldlifeexpectancy.com
by 2030. Therefore, necessary actions and precau-
tionary measures are needed (WHO, 2017).
The traffic accidents can be reduced by penalizing
violators. Different countries have addressed the is-
sue by installing surveillance systems to monitor traf-
fic violation at every intersection. However, such sys-
tems are expensive and require well installed infras-
tructure. It is convenient in developed countries due
to existing infrastructure; whereas, in underdeveloped
countries, the lack of budget and weak infrastructure
makes it unfeasible. The deployment of extensive
number of traffic constables to monitor violations is
not viable either. In the last decade,crowdsourcing
has become a widely used technique to solve the prob-
lems using end users input. The concept of crowd-
sourced system has been normalized by social me-
dia and smartphones. Today people around the world
can easily participate for the sustainable society de-
velopment without any special skill sets. The sensor
based data collection helps to retrieve credible and ac-
curate data. With the advancement in technology and
exponential growth of smart phones, users can eas-
Jameela, M., Afzal, H., Khurshid, K. and Waqar Malik, A.
Crowdsourced System to Report Traffic Violations.
DOI: 10.5220/0006680303150322
In Proceedings of the 4th International Conference on Vehicle Technology and Intelligent Transport Systems (VEHITS 2018), pages 315-322
ISBN: 978-989-758-293-6
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
315

ily share data at low cost. Thus, it enabled the role
of crowdsourcing to solve daily life problems. Due
to easy access to 3G/4G/5G technologies, multimedia
streaming is adopted to share real-time information to
help law enforcing agencies. These features and tech-
niques encourage developers to come up with cost ef-
ficient solutions for smart cities.
In order to provide a feasible solution, a system is
developed using crowdsourced model to report viola-
tions along with video evidence and GPS coordinates.
The motivation is to reduce the burden on traffic war-
dens and increase the involvement of general public
in law enforcement.
RoadCop is bi-modular solution (Mobile and Web
Application) to report traffic violations. These reports
are filtered on two stages. The first stage eliminates
the spam reports and blocks the spammer.In the sec-
ond stage of evaluation, the filtered reports are used
bu traffic law experts to decide the validity of these re-
ports. the traffic violations that can be reported by the
mentioned system are i) Red Light Violation (RLV)
ii) Reckless Driving (RD) iii) Illegal Parking (IP) iv)
Hit and Run (HR) v) Illegal Lane Change (ILC).
2 LITERATURE REVIEW
This section covers the detailed review of research in
this particular area. It discusses the methodologies
currently used for monitoring traffic violations and
usage of crowdsourced model, geo coordinates and
media evidences to solve different day to day prob-
lems.
Pakistan is a developing country and public sector
has yet to see the boom of information technology. IT
has begun to automate various manual processes. One
of such fields is transportation management. Traf-
fic Police deals with the offence and penalty of traf-
fic rule violations. Monitoring traffic violations have
become a challenge due to the increasing number of
vehicles and population over the last few years. In
the urban areas, controlling traffic has become a ne-
cessity. Traditional technique is traffic wardens iden-
tify violator which is used all over the country. It
has loopholes due to lack of evidence and human er-
rors. Moreover, it is also vulnerable to harassment
and bribes.
Punjab Traffic Police have been experimenting
with Traffic Violation Evidence System for more than
a year now. The system is installed over the inter-
section and automatically generates the e-Ticket on
violations which is later approved by authorities and
sent to doorstep of violator along with the picture of
violations, taken by CCTV cameras. Though, weak
infrastructure, lack of funds and absence of proper in-
tersections resulted in dependency of manual identifi-
cation of violators in other parts of the country.
Transportation and control on traffic accidents has
become one of the burning issues for the IT Indus-
try and academia. Different techniques are proposed
over the time, one of such techniques is to penalize the
violators of horn blowers in restricted areas (a.k.a Si-
lence Zone). Drivers receive a message to ”Not Blow
Horn” on LCD screen adjusted in the vehicle. On vi-
olation SMS along timestamp is generated from ve-
hicle to control station. Registration number is used
to penalize the offender. It is a flexible approach and
can be modified for different traffic violations (Biswas
et al., 2015).
India has digitized existing data under the digi-
tal India program and is using smartcards to store
registration and license information which is used to
provide VPC (Vahan Penalty Card) to drivers. VPC
contains penalties balance and license is cancel af-
ter crossing threshold and petrol pumps will deny
petrol to invalid VPC holders. System is operat-
ing on RFID readers installed at the sensitive areas
to identify RFID readable license plates of violators.
Intelligent Expert Penalty System requires sophisti-
cated equipment like RFID readers, RFID readable
number plates, VPC, VPC readers, VPC recharge-
able outlets. It also requires legislation and binding
agreements between government and petrol pumps
(Goel and Shukla, 2016). Another RFID based so-
lution uses RFID tags instead of license plates. Tags
store driver’s license, bio data and vehicle registra-
tion. RFID reader and camera components are used
to detect violations and generate warning messages.
Crossing threshold can result in cancellation of li-
cense. It is used to check speed limit, red light viola-
tions and can help reduce vehicle theft(K et al., 2016).
Another system is proposed and tested using a
toy car which uses infrared transmitter and receiver,
microcontroller, wireless communication and central
database of Bangladesh Road Transport Authority.
Proposed approach can be seen in Figure 1 (Hossain
et al., 2010).
A system for smart cars is proposed which em-
ploys VNDN
2
(Vehicle Named Data Network). It
uses ID instead of IP and protocol of data exchange
with simple interest and response messages. Sys-
tem uses OBUs (Onboard Units) to sense violations
and store it in Pending Ticket Entry Table maintained
by every Ordinary Vehicle. Cop Vehicles (CVs) re-
ceive PTE entries on broadcasting interest messages
and issue the ticket against the entry. Payment can
be deducted from the registered bank account of the
2
Vehicle Named Another system for smart cars
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
316
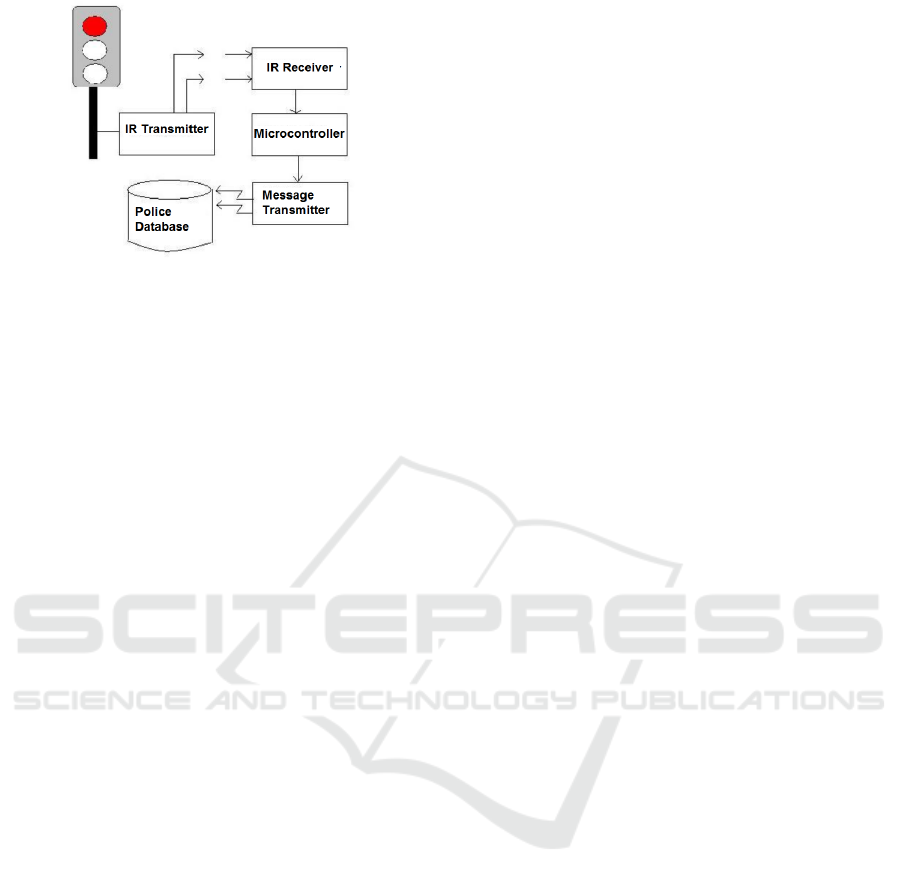
Figure 1: Block Diagram of proposed system in (Hossain
et al., 2010).
violator on the next toll booth automatically. This
approach targets the urban environment and unmon-
itored highways due to the pull mechanism. Func-
tional testing concludes that increase in violators will
increase the number of Tickets and CV will be re-
quired to send more interest messages(Ahmed et al.,
2016). Another Intelligent Transportation System
collects GPS data and sends it to server where web
application matches and calculates the speed of the
vehicle and checks it against the OSM speed limit of
the streets (Tarapiah et al., 2014).
Advanced Driver Assistance system was proposed
to gather data from various sensors and equipment in-
stalled in the vehicle and generates a profile for the
driver to view traffic violations, speed and other spa-
tial and geographical information on Google Maps
via a small monitored screen adjusted in the vehi-
cle(Nourdine Aliane, 2011).
2.1 Overview of Crowdsourcing
Crowdsourcing is a technique to collect data with
the help of volunteers, sometimes driven by incen-
tives (monetarily or entertainment)(Ali et al., 2012).
Today, there are many applications based on crowd-
sourcing as an underline mechanism for information
retrieval. Examples of such applications are social
media, Google Maps, Wikipedia and research jour-
nals. The social media collects users interest, opin-
ions and uses it for target advertisement and sugges-
tions. One of the major advantages of crowdsourced
applications is to facilitate generation of geographi-
cally distributed data. It can be useful in data col-
lection for transportation management(Santani et al.,
2015). The contributions in crowdsourced applica-
tions are of two types (Chatzimilioudis et al., 2012).
• Participatory Contribution:based on Users input
• Opportunistic Contribution:based on Sensors
The results derived from crowdsourced system are
dependent on the credibility of the contributors. Fol-
lowing are few techniques to ensure credibility (Cvi-
jikj et al., 2015). Crime-mapping a technique to dis-
play crime’s location over a map. Media Evidence
can help eliminating spamming. Incentives (Mon-
etary, Entertainment and etc) is a way to motivate
crowd.Assurance of user anonymity publicly may en-
courage users to report. On the other hand, system
can store credentials of the user to ensure its credi-
bility and most importantly reduce textual input and
restrict it to predefined range.
Following section discusses the crowdsourced ap-
plications and research in the transportation sector.
2.2 Crowdsourcing Applications in
Transportation
Crowdsourced systems uses citizens input and smart-
phones to collect transportation data, manage traffic
situations and exploit that information to make de-
cisions and plan infrastructure changes (Mostashari
et al., 2011). In the last few years, most of the
research and development of Intelligent Transporta-
tion System has shifted from sophisticated expensive
equipped framework to crowdsourced systems. It is a
cost efficient solution with great potential due to tech-
nology advancement. Transportation management is
linked to geographically distributed data and high mo-
bility so a crowdsourced solution is match made in
heaven.
CrowdITS is a mobile application to report and
notify traffic congestion, accidents, construction and
breakdown. This system does not use the exter-
nal sensors and equipment which makes it affordable
(Misra et al., 2014). Another crowdsourced system
is proposed to report road hazards along GPS co-
ordinates and media evidence for Nairobi, Kenya to
meet the development challenges and solve infras-
tructure problems. Media evidence is crossed check
by Amazon Mechanical Turk to eliminate spam (San-
tani et al., 2015). Another Mobile Application uses
GPS sensor, accelerometer, GSM radio and micro-
phones to collect data of traffic and road conditions
such as potholes, bumps, braking, and honking. It
is an experimental project deployed in Banglore, In-
dia and has delivered promising results(Mohan et al.,
2008).
Vehicular Ad-hoc Networks and Vehicular Named
Data Networking solutions can be used to send traffic
information to other vehicles and collected informa-
tion can be used to reroute dynamically in order to
save time. System was testing in Portland and pro-
duced good results (Leontiadis et al., 2011). Cloud
Crowdsourced System to Report Traffic Violations
317

computing can provide storage and computing facil-
ities to process big data collected through the crowd
for traffic model construction and congestion predic-
tion(Nourdine Aliane, 2011). We would like to men-
tion about a public sector app Public Eye: BTP Of-
ficial App Smart Mobile Application for managing
Traffic Violations that describes work similar to what
we have proposed but it lacks the location tracking
facility for traffic violations.To the best of our knowl-
edge most of the research did not cover the utilization
of crowdsourced model to report traffic violation us-
ing handheld smartphones.
Table 1: Comparison between existing approaches to report
traffic violations.
No Existing
Approach
Pros Cons
1 Manual
Violations
Identifi-
cation by
Traffic
Wardens
Useful in
absence of
technology.
Prone to
bribe and
harassment
Lack of
evidence
Prone to
Human error
2 CCTV
and e-
Ticketing
Systems
Efficient
Effective
Accurate
Expensive
Equipment
Unmonitored
areas
3 RFID
Sensors
and RFID
Tag Based
Solution
Sophisticated
Technique
Less prone
to Error
Accurate.
Easy Main-
tenance of
record due
to RFID.
Expensive
Equipment
Cost on
either Gov-
ernment or
Consumer
Maintenance
budget cost
3 PROPOSED SYSTEM
This section gives an overview of the proposed sys-
tem and need of such systems. Table 1 compares the
existing solutions for traffic management and control.
It concludes that sophisticated systems generate bet-
ter results in monitoring traffic situations and viola-
tions. In countries with appalling law and order situ-
ation, employing expensive equipment is not feasible
due to theft possibility.The role of general public is
very crucial for the development of sustainable soci-
ety. A crowdsourced system to counter the problem
is not only cost-efficient but also beneficial for devel-
opment of well-grounded society.The proposed sys-
tem enables general public to report traffic violations
along media evidence and its location. Mobile Ap-
plication enables users to report traffic violations. On
the other hand, Web Application is available for the
administration. It allows admin to filter spam, review
reports, view details of vehicles and vehicle registered
owner, total number of violations reported and reward
points/score in case of valid reports. The admin can
view all reports on Google Maps (type of violation,
area, timings or combination of all three). The graphs
generated gives results such as number of violations
in a specific area, number of violations in a specific
period of time and number of specific violations in a
certain time. These and other customized cubes can
help concerned departments to make decision regard-
ing infrastructure and traffic surveillance.
3.1 System Workflow and Architecture
Web Application can be hosted on existing data cen-
ters of public sector entities. Mobile Application can
be installed on the android smartphones. It launches
camera to record video. Reporter can choose to report
immediately or save it for later. Mobile application
uses background service to collect GPS coordinates
of traffic violations location while recording video.
User can add the license plate number and choose vi-
olation type from predefined list.User requires Wi-Fi
connection to submit report otherwise it is stored lo-
cally on SQLite database and sent along timestamp
when connected to Wi-Fi.It will avoid the cost of mo-
bile data. User transmit video to server in multime-
dia encrypted form and remaining fields of report (li-
cense plate number, traffic violation type, GPS coor-
dinates, and timestamp and user credentials) in JSON
(JavaScript Object Notation) format.Video files are
stored on server in directory instead of database to
avoid increasing size of database.Data is delivered to
the restful service which inserts it in central database
via hibernate query. Web application interacts via
Ajax calls to restful services for manipulation of the
database. Admin view of the web application gives
the status of reports on Google Maps with color coded
markers. Admin can review the reports. First Stage
Admin will block the spammer. Admin can validate
if the violation meets the legal criteria. If yes, then
the ticket along with the screenshot of the report and
time will be sent to the registered contact details of
the vehicle and valid reports point will be given to the
reporter. System Architecture can be seen in Figure 2.
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
318
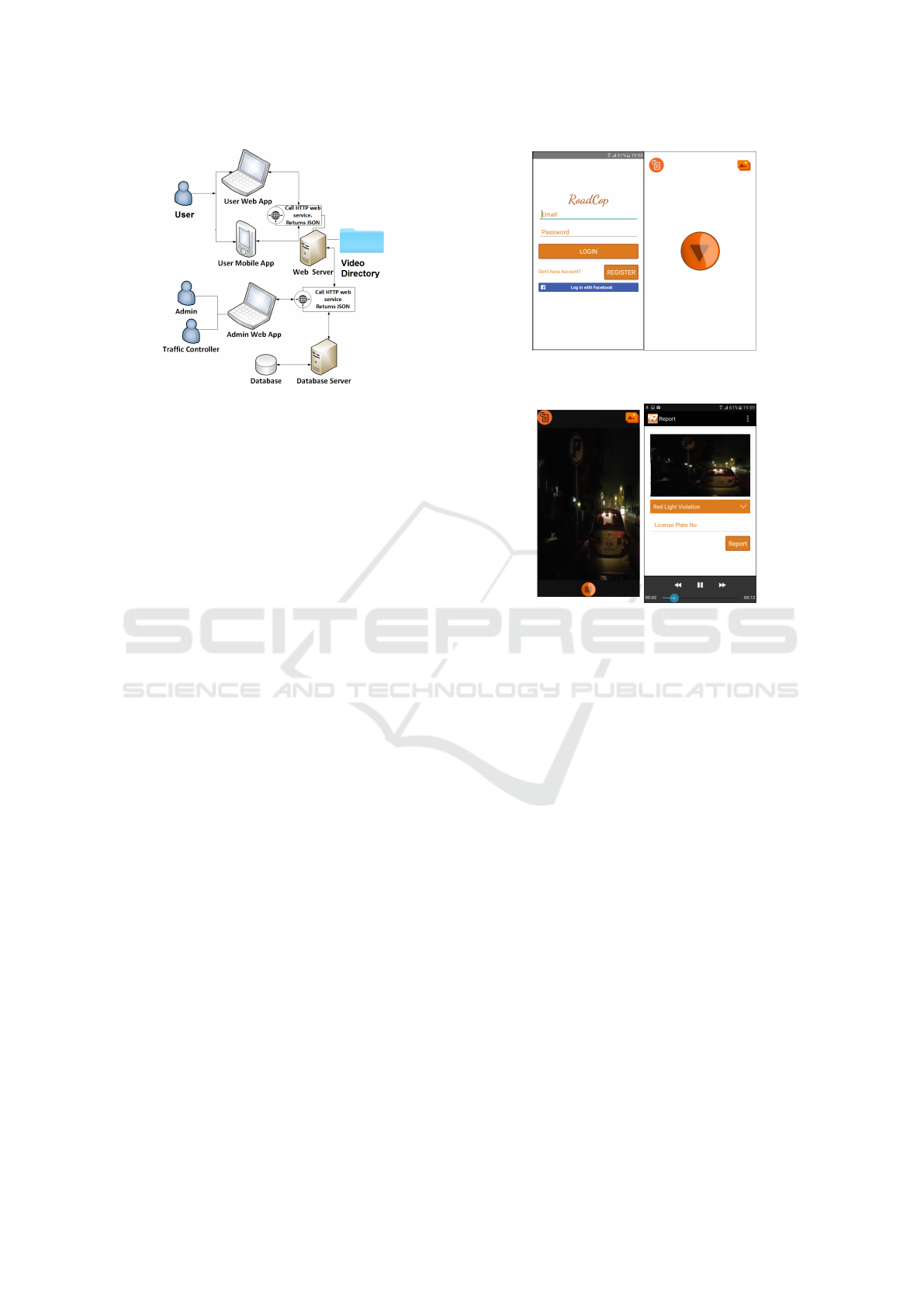
Figure 2: Architecture of Proposed System.
4 SYSTEM COMPONENTS AND
IMPLEMENTATION DETAILS
This section discusses the detail of systems compo-
nents their features and implementation details.
4.1 Mobile Application
Mobile Application is developed for Android Oper-
ating System. Basic requirement to run the proposed
application on the smartphones are i)Android OS Ver-
sion 2.3 (Gingerbread and above) ii) Wi-Fi iii) GPS
Sensor iii) Camera with minimum 2MP. The proposed
implementation has enrich UI which works on ma-
jor screen sizes such as LDPI, MDPI, HDPI, XHDPI,
XXHDPI, XXXHDPI. It also allows login via Face-
book which uses Graph API and Facebook SDK to
request public fields such as name, gender, user_id
and fullname of a particular user as shown in Fig-
ure 3a. After logging into the system, video recording
for traffic violation screen appear as shown in the Fig-
ure 3b. User can also view the already recorded but
not reported violations along with history of reports
status.
• GPS Coordinates: : These are integral part of
the system. It gives exact location of the traffic
violation. In case of a valid report, location can
be sent with the ticket to the violator.
• Video Evidence: Video Evidence is captured via
the camera in the application. It has VGA set-
tings with standard dimensions of 640x480 pixels.
It is stored in mp4 format with H.264 encoding
which is a block-oriented, motion-compensation
based video compression standard. Video size
limit of 15MB is enforced. Video is encrypted
using AES/CBC/PKCS5Padding which makes it
transmission safe and ensures end to end security.
(a) Login/Register (b) RoadCop Cam-
era
(c) Evidence Cap-
turing
(d) Reporting Traf-
fic Violations
Figure 3: Mobile Application.
• Type of Violations: Scope of the research is lim-
ited to i) Red Light Violation ii) Reckless Driving
iii) Illegal Parking iv) Hit and Run v) Illegal Lane
Change.
• Reward Points: Valid report is rewarded with
points. These points, in this study, are just like
scores but later can be used to offer some incen-
tives(monetary, entertainment or fuel) This can el-
evate the interest of reporter.
4.2 Web Application
Web application and webservices are deployed on
apache tomcat with hibernate support and JBoss data
services. Hibernate layer communicates with the cen-
tral database. It receives and sends data via restful
services on client side by jQueryAjax. JQueryAjax
then uses HTML5 markups and bootstrap to show and
format data. Layered Architecture can be seen in Fig-
ure 5. Web Application is developed for the Admin-
istration. It gives details of total violations reported
and total number of users registered with the system.
Administrators can perform first and second stage fil-
tering. Figure 4 shows web application view.
Crowdsourced System to Report Traffic Violations
319
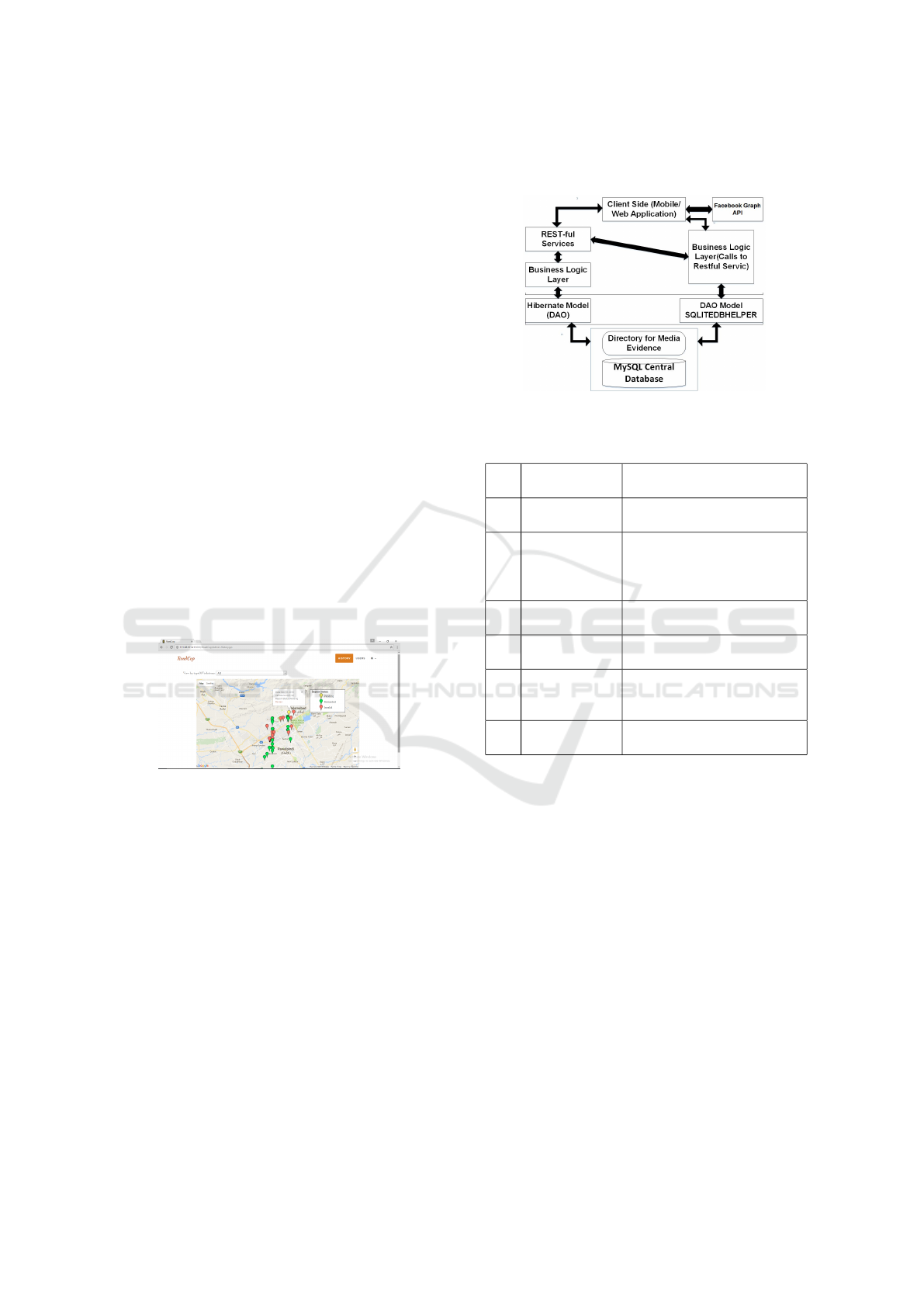
• View Violation Map: It gives the view of the re-
ports with color coded markers on Google Maps
which can be viewed by different dimensions such
as by area, timing and type of violations. It helps
in understanding the trends of violations by area.
Place on Google Map with maximum markers is
most vulnerable area.
• Eliminate and Block Spammers: There are two
levels of Administration Staff. First Stage Admin
will filter spam reports and block spammers.
• Review Reports and cross validate against the
registered Vehicles: Second Level Admin are the
Traffic Law Expert who can review ham reports
based on traffic rules and regulations while sys-
tem ensure reporters anonymity. Data is fetched
against the license plate number from the regis-
tered vehicles database for ticketing once report
is validated by traffic expert and reporter is re-
warded.
Central database contains tables user, report,reward
and vehicles. User has credentials and password
which is encrypted by MD5 encryption algorithm to
ensure privacy. Reported violations are stored in re-
port table, reward table has status of reported viola-
tions also rewardpoints and registered vehicles can be
fetched from vehicles table.
Figure 4: Map of Reported Violations.
4.3 Statistics for Decision Making
Crowdsourcing is a technique of information re-
trieval. Usually the data collected by the crowd in
this stage can later be used for different statistical
analysis. Statistics such as number of violations by
cities/area, number of violations by time (Date, Day,
Month and Year) and type of violations on differ-
ent parameters. Visual representation in the form
of graphs can give very promising trends that can
be used by transportation management department as
well as infrastructure planners. API used for visual
representation is an open source JavaScriptAPI called
Chart.js. It is used to generate client side visual aid
such as pie charts, histograms and barcharts. Data
sciences have changed the prospect of data collection
and analysis. Utilization of intelligent systems trained
on collected data can help overcome similar events in
the future to avoid mishaps or management failures.
Figure 5: Layered Architecture of Bi Modular System.
Table 2: Evaluation criteria of proposed system.
No Evaluation
Criteria
Description
1 Usability User-friendly and easy to
use Design
2 Advantage for
Authorities
(LEA,GOVT
officials)
Helps in locating violators
3 Citizen In-
volvement
Involving Citizens in pro-
cess law enforcement
4 Linkage and
Trust
Associating Trustworthy or-
ganization
5 Skills and
Resources
Required
What Kind of Skill set re-
quired for the usage of Ap-
plication
6 Transparency Ensuring privacy control of
user
5 FUNCTIONAL TESTING AND
CHALLENGES
In order to test the proposed system and evaluate it on
parameters shown in the Table 2; system is deployed
on a windows server. Mobile Application is provided
to 50 volunteers for testing and requested to report
a traffic violation at least once over the period of four
weeks. More than 53 reports are collected. Volunteers
are selected from Islamabad and Rawalpindi. Admin
evaluated the reports in the first stage and removed
total 15 reports (12 videos spams and 3 license plate
numbers spams) and blocked spammers. Total 35 re-
ports are sent for expert’s review known as the final
stage evaluation. The experts marked 23 reports in-
valid and rewarded 12 reports. The experts reviewed
and evaluated reports with the help of regional trans-
portation department.
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
320

Evaluation criteria of system mention in table 2.
A small survey was conducted among the volunteers
of functional testing to evaluate the system. It was
close ended questionnaire to get feedback regarding
usability and skills set required for app usage. Due
to the easy design, understanding the purpose of the
system was not a problem. 85% of the participants un-
derstood the main functionality of application. Users
did not feel the need of tutorials. Citizen involve-
ment can be increased by collaboration with the of-
ficial authorities. More than 76% of the people think
association of the application with concerned author-
ities can increase the frequency of reporting. Users
trust the system with frequent responses and actions
against violator. 60% of the users think that the appli-
cation gave them a sense of responsibility and contri-
bution towards law enforcement. Challenges faced in
the process of functional testing are of following four
types:
5.1 Design Challenges
Crowdsourced systems are for the people with min-
imum technological skills. Few of the major design
decisions are to reduce textual inputs and use affor-
dances icons.
5.2 Legal Challenges
For consideration of an evidence it must possess four
characteristics.i) Materiality ii) Relevance, iii) Au-
thenticity, and iv) Competence. In the proposed sys-
tem, one of the major challenges is to ensure authen-
ticity while keeping the reporter anonymous. The re-
ports authenticity is ensured by the GPS coordinates.
It is impossible for a reporter to change the GPS coor-
dinates values. Media Evidence can ensure both au-
thenticity and competence. During the research and
development phase, Traffic Police Department recom-
mended to ensure that evidence is captured through
app. Uploading a video can give user/reporter a
chance to edit it.
5.3 Adaptability Challenges
Crimes reporting crowdsourced systems are for the
public to contribute in collecting geographically dis-
tributed data. Such systems could support modern
ideas of open government. Popular crowdsourced ap-
plications, like social media are trendy and user con-
tribution in such systems are presumed to strengthen
their social standing. On the contrary, crowdsourced
applications by governments raise different concerns.
Anonymity: Insurance of reporter’s anonymity
Relevance: Will justice be served if reported?
Ensuring privacy while keeping authenticity of data
is a major challenge which can be solved by conceal-
ing the source of report on public view but keeping it
in the record. To increase the awareness and accep-
tance of such systems some measures are discussed
in Table 3. Adaption of the system by authorities
has been another major challenge because associa-
tion with authorities can make system reliable. On
the other hand, authorities are not easily convinced to
adopt new technology.(Cvijikj et al., 2015) Authori-
ties expect quality of contribution which is ensured
by media evidence. (Quinn and Bederson, 2011) Ac-
ceptance can also be achieved with the help of aca-
demic stakeholders and through capacity building of
government’s IT professionals.
5.4 Vehicle Registration Challenges
Complete Evaluation of such a system is not conve-
nient due to many reasons, particularly in Pakistan.
Vehicles are registered once and registrations are usu-
ally not transferred to new owners.Computerized reg-
istration of vehicles is the priority of interior ministry
and traffic police department. Process is at final stages
in Punjab and KPK. Motor Transport Management
Information System is the online vehicle verification
system which is functional in Punjab, KPK, Sindh and
Islamabad.
6 CONCLUSION
Research and development of proposed system con-
cluded that such systems can be very useful towards
the development of intelligent transportation systems
and information retrieval for decision making. It gives
a technique for collection of traffic violation reports
from general public to increase awareness of traffic
laws and awake the sense of responsibility in drivers.
It can help in publishing a real time map of violations
by area and time period. Functional testing gives in-
teresting inferences. It shows how people would pre-
fer such systems if they are associated with a trustwor-
thy organization such as Traffic Police or Communi-
cation and Works Departments. This system is novel
approach and opens many doors for future research.
If the proposed system is correctly and efficiently im-
plemented then it can not only produce better results
than manual capturing of violators but also help in
collection of data which can be useful in the future.
Crowdsourced System to Report Traffic Violations
321
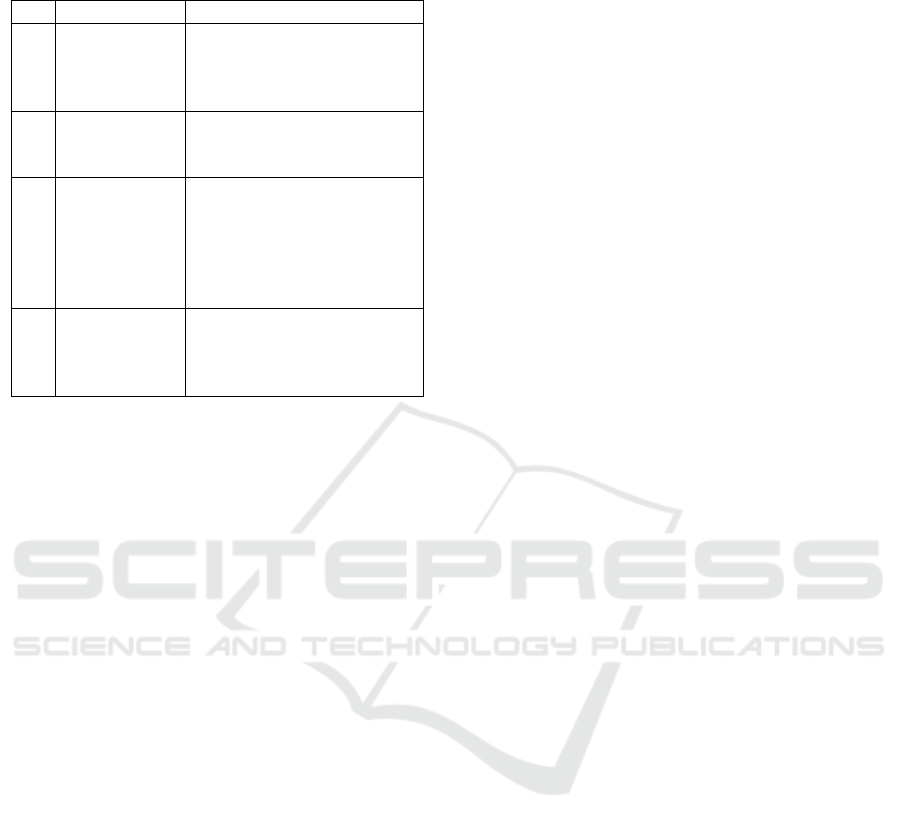
Table 3: Measures to increase adaptability of traffic viola-
tions reporting crowdsourced system.
No Measures Description
1 Incentives Reward for Users to mo-
tivate the participation also
shows seriousness of author-
ities.
2 Provision
of Valid
Information
Discard spams and public
availability of valid reports.
3 Frequent
Informa-
tion Update/
Quick Re-
sponse
Regular updated informa-
tion can increase interest
of public. Action on re-
ports and update regarding it
can increase trust and ensure
adaptability.
4 Association
of Trust-
worthy
Organization
Association of Government
entity can help build trust.
REFERENCES
Ahmed, S. H., Yaqub, M. A., Bouk, S. H., and Kim, D.
(2016). Smartcop: Enabling smart traffic violations
ticketing in vehicular named data networks. Mobile
Information System, pages 01–12.
Ali, K., Al-Yaseen, D., Ejaz, A., Javed, T., and Hassanein,
H. S. (2012). Crowdits: Crowdsourcing in intelligent
transportation systems. In IEEE Wireless Communica-
tions and Networking Conference, pages 3307–3311,
Shanghai, China. IEEE.
Biswas, R., Beed, R. S., Seth, D., Pal, P., KaustavBasu, and
Mukherjee, T. (2015). Traffic rule violation informa-
tion system truvisn. IJARCSSE, pages 1134–1139.
Chatzimilioudis, G., Konstantinidis, A., Laoudias, C., and
Zeinalipour-Yazti, D. (2012). Crowdsourcing with
smartphones. IEEE Internet Computing.
Cvijikj, I. P., Kadar, C., Ivan, B., and Te, Y.-F. (2015). To-
wards a crowdsourcing approach for crime prevention.
In Proceedings of ACM International Joint Confer-
ence on Pervasive and Ubiquitous Computing, pages
1367–1372, New York, USA. ACM.
Goel, S. K. and Shukla, D. M. K. (2016). Improved design
of e-penalty to control road and transport safety with
the help of ict and enforcement of e-governance a step
towards make in india. In International Conference
on Inventive Computation Technologies, Coimbatore,
India. IEEE.
Hossain, M. R. T., Bhuiya, M. M. K., Ahamed, J. U.,
Bhuiyan, T. H., and Bhowmik, S. (2010). Monitoring
and reporting of traffic rules violation using microcon-
troller through wireless communication system. Engi-
neering e-Transaction, pages 117–121.
K, M. D., S.Vandanaa, M.Varshini, and K.Tijitha (2016).
Automatic identification of traffic violations and theft
avoidance. In Second International Conference on
Science Technology Engineering and Management,
pages 72–76, Chennai, India. IEEE.
Leontiadis, Ilias, Marfia, G., Mack, D., Pau, G., Mascolo,
C., and Gerla, M. (2011). On the effectiveness of an
opportunistic traffic management system for vehicu-
lar networks. IEEE Transactions on Intelligent Trans-
portation Systems, pages 1537–1548.
Misra, A., Gooze, A., Watkins, K., Asad, M., and Dan-
tec, C. A. L. (2014). Crowdsourcing and its applica-
tion to transportation data collection and management.
Transportation Research Record, pages 1–8.
Mohan, P., Padmanabhan, V. N., and Ramjee, R. (2008).
Nericell: Rich monitoring of road and traffic condi-
tions using mobile smartphones. In Proceedings of
the 6th International Conference on Embedded Net-
worked Sensor Systems, pages 323–336, Raleigh, NC,
USA. ACM.
Mostashari, A., Arnold, F., Maurer, M., and Wade, J.
(2011). Citizens as sensors: The cognitive city
paradigm. In 2011 8th International Conference Expo
on Emerging Technologies for a Smarter World, New
York, NY, USA. IEEE.
Nourdine Aliane, Javier Fernndez, S. B. M. M. (2011).
Traffic violation alert and management. In 14th Inter-
national IEEE Conference on Intelligent Transporta-
tion Systems, Washington, DC, USA. IEEE.
Quinn, A. J. and Bederson, B. B. (2011). Human com-
putation: a survey and taxonomy of a growing field.
In Proceedings of the SIGCHI Conference on Human
Factors in Computing Systems, pages 1403–1412,
Vancouver, BC, Canada. ACM.
Santani, D., Njuguna, J., Bills, T., Bryant, A. W., Bryant,
R., Ledgard, J., and Gatica-Perez, D. (2015). Com-
munisense: Crowdsourcing road hazards in nairobi.
In Proceedings of the 17th International Conference
on Human-Computer Interaction with Mobile Devices
and Services, pages 445–456, Copenhagen, Denmark.
ACM.
Tarapiah, S., Atalla, S., Muala, N., and Tarabeh, S.
(2014). Offline public transportation management sys-
tem based on gps/wifi and open street maps. In Sixth
International Conference on Computational Intelli-
gence, Communication Systems and Networks, pages
182–185, Tetova, Macedonia, Macedonia. IEEE.
WHO (2016). World life expectancy (cause of death road
traffic accident.
WHO (2017). Road traffic injuries fact sheets.
VEHITS 2018 - 4th International Conference on Vehicle Technology and Intelligent Transport Systems
322
