
A Near Optimal Algorithm for Lifetime Optimization
in Wireless Sensor Networks
Karine Deschinkel and Mourad Hakem
DISC Laboratory, FEMTO-ST Institute - UMR CNRS, University of Franche-Comte, Belfort, France
Keywords:
Target Coverage, Wireless Sensor Networks, Centralized Method, Disjoint Cover Sets, Lifetime Optimization.
Abstract:
In this paper, we introduce an efficient energy-aware algorithm to enhance the lifetime of wireless sensor
networks (WSN) by i) organizing/clustering the sensor nodes into disjoint cover sets where each cover set
is capable of monitoring all the targets of the region of interest and ii) scheduling these cover sets succes-
sively/periodically. This study differs from previous works for the following reasons: i) it achieves near
optimal solutions compared to the optimal ones obtained by the exact method and ii) unlike existing algo-
rithms that construct gradually cover sets one after the other, our algorithm builds the different sets in parallel.
Simulation results show the efficiency of our algorithm.
1 INTRODUCTION
Recent years have witnessed significant advances in
wireless sensor networks which emerge as one of
the most promising technologies for the 21st cen-
tury (Akyildiz et al., 2002). In fact, they present huge
potential in several domains ranging from health care
applications to military applications. A sensor net-
work is composed of a large number of tiny sensing
devices deployed in a region of interest. Each device
has processing and wireless communication capabil-
ities, which enable to sense its environment, to com-
pute, to store information and to deliver report mes-
sages to a base station. These sensor nodes run on
batteries with limited capabilities. To achieve a long
life of the network, it is important to conserve battery
power. Therefore, lifetime optimisation is one of the
most critical issues in wireless sensor networks.
In this paper we concentrate on the target cover-
age problem. We assume that sensors are randomly
deployed for monitoring a set of targets with known
locations and we also assume that sensors have loca-
tion determination capabilities. We propose a central-
ized algorithm that selects mutually exclusive sets of
sensor nodes, where the members of each of those sets
together completely cover the monitored targets. The
intervals of activity are the same for all sets, and only
one of the sets is active at any time to provide contin-
uous service while the remaining sets are scheduled
to sleep. The objective, is to maximize the number of
cover sets to increase the system’s service life.
The major contribution of this paper is the de-
sign of a new near optimal algorithm for lifetime op-
timization in WSN. Unlike existing approaches that
construct gradually cover sets one after the other, the
proposed algorithm builds the different sets in paral-
lel. Indeed, at each step of the clustering process, the
algorithm attempts to add to each cover set a sensor
capable of monitoring the most critical target. The
choice of sensor to be clustered in each cover set is
based on solving a linear assignment problem in poly-
nomial time using the Hungarian algorithm. Our ap-
proach provides a lower bound K
min
of the optimal
number of disjoint cover sets K
opt
. Intuitively, the up-
per bound K
max
of the optimal value is given by the
size of the smallest set of sensors covering a target.
We deduce K
opt
by performing a binary search be-
tween K
min
and K
max
. At each step of the search pro-
cess we check if there exists a partition of the sensors
in K cover sets by solving an integer programming
problem.
The remainder of the paper is organized as fol-
lows. Section 2 reviews the related work in the field.
Section 3 is devoted to the description of the target
coverage problem and explains the basics of our al-
gorithm. Then we express the time complexity of the
algorithm. We also present how to compute the opti-
mal number of disjoint cover sets by solving integer
programmingproblemssuccessively. Section 4 shows
the simulation results, that fully demonstrate the use-
fulness of the proposed algorithm. Finally, we give
some concluding remarks in Section 5.
197
Deschinkel K. and Hakem M..
A Near Optimal Algorithm for Lifetime Optimization in Wireless Sensor Networks.
DOI: 10.5220/0004272701970202
In Proceedings of the 2nd International Conference on Sensor Networks (SENSORNETS-2013), pages 197-202
ISBN: 978-989-8565-45-7
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

2 RELATED WORK
First algorithms proposed in the literature consider
that the cover sets are disjoint: a sensor node ap-
pears in exactly one of the generated cover sets. For
instance Slijepcevic and Potkonjak (Slijepcevic and
Potkonjak, 2001) propose an algorithm which allo-
cates sensor nodes in mutually independent sets to
monitor an area divided into several fields. Their al-
gorithm constructs a cover set by including in pri-
ority the sensor nodes which cover critical fields,
that is to say fields that are covered by the small-
est number of sensors. The time complexity of their
heuristic is O(n
2
) where n is the number of sen-
sors. (Cardei et al., 2002) present a graph color-
ing technique to achieve energy savings by organizing
the sensor nodes into a maximum number of disjoint
dominating sets which are activated successively. The
dominating sets do not guarantee the coverage of the
whole region of interest. In (Cardei and Du, 2005),
the authors propose a heuristic to compute the disjoint
set covers (DSC). In order to compute the maximum
number of covers, they first transform DSC into a
maximum-flow problem , which is then formulated as
a mixed integer programming problem (MIP). Based
on the solution of the MIP, they design a heuristic
to compute the final number of covers. The results
show a slight performance improvement in terms of
the number of produced DSC in comparison to (Sli-
jepcevic and Potkonjak, 2001) but it incurs higher ex-
ecution time due to the complexity of the mixed in-
teger programming resolution. Zorbas et al. (Zorbas
et al., 2007) present B{GOP}, a centralized coverage
algorithm introducing sensor candidate categorisation
depending on their coverage status and the notion of
critical target to call targets that are associated with
a small number of sensors. The total running time
of their heuristic is 0(mn
2
) where n is the number
of sensors, and m the number of targets. Compared
to algorithm’s results of Slijepcevic and Potkonjak
(Slijepcevic and Potkonjak, 2001), their heuristic pro-
duces more cover sets with a slight growth rate in ex-
ecution time.
In the case of non-disjoint algorithms (Chaudhary
and Pujari, 2011), sensors may participate in more
than one cover set. In some cases this may prolong
the lifetime of the network in comparison to the dis-
joint coverset algorithms but designing algorithms for
non-disjoint cover sets generally incurs a higher order
of complexity. Moreover in case of a sensor’s failure,
non-disjoint scheduling policies are less resilient and
less reliable because a sensor may be involved in more
than one coversets. For instance, Cardei et al. (Cardei
et al., 2005) present a linear programming (LP) solu-
tion and a greedy approach to extend the sensor net-
work lifetime by organizing the sensors into a max-
imal number of non-disjoint cover sets. Simulation
results show that by allowing sensors to participate
in multiple sets, the network lifetime increases com-
pared with related work (Cardei and Du, 2005).
3 ALGORITHMS DESCRIPTION
We try to produce an adaptive scheduling which al-
lows sensors to operate alternatively so as to prolong
the network lifetime. For convenience, the notations
and assumptions are described first.
3.1 Notations and Assumptions
• m : the number of targets
• n : the number of sensors
• K : maximal number of cover sets
• i : index of target (i = 1..m)
• j : index of sensor ( j = 1..n)
• k : index of cover set (k = 1..K)
• T
0
: initial set of targets
• S
0
: initial set of sensors
• T : set of targets which are not covered by at least one
cover set
• S : set of available sensors
• S
0
(i) : set of sensors which cover the target i
• T
0
( j) : set of targets covered by sensor j
• C
k
: cover set of index k
• T(C
k
) : set of targets covered by the cover set k
• NS(i) : set of available sensors which cover the target i
• NC(i) : set of cover sets which do not cover the target i
• |.| : cardinality of the set
We assume that the lifetimes of sensors are iden-
tical. Lifetime of a sensor is time duration when the
sensor is in the active state all the time. In order to
achieve lifetime extension, sensors must be divided
into a number of subsets, called cover sets, where
each cover set is capable of monitoring all the targets.
Sensors belonging to a scheduled cover set are in ac-
tive mode, while the others are in sleep mode. If the
cover sets are disjoint, then each sensor is allowed to
participate only in one cover set. The maximal num-
ber of possible disjoint cover sets is given by :
K
max
= min
i=1..m
|S
0
(i)| (1)
since each cover set must cover all targets and each
sensor can only be part of one cover set.
SENSORNETS2013-2ndInternationalConferenceonSensorNetworks
198

3.2 Near Optimal Algorithm
The main idea of the algorithm is to build simultane-
ously the cover sets by adding gradually the sensors
capable of monitoring the most critical target. At each
iteration of the algorithm we compute the critical rate
(let call it R(i)) of a target i as follows :
R(i) =
|NS(i)|
|NC(i)|
(2)
Algorithm 1: Near optimal algorithm.
Require: An initial set of targets T
0
and an initial set of
sensors S
0
Ensure: A set of cover sets C
1
,..,C
K
1
1: {INITIALIZATION}
2: for all cover sets k = 1..K
max
do
3: C
k
←
/
0
4: T(C
k
) ←
/
0
5: end for
6: S ← S
0
7: T ← T
0
8: for all targets i = 1..m do
9: NC(i) ← {C
1
,..,C
K
max
}
10: NS(i) ← S
0
(i)
11: end for
12: {While there exists a target which is not covered by a
cover set and the set of available sensors is not empty}
13: while T 6=
/
0 and S 6=
/
0 do
14: for all targets i ∈ T do
15: Compute R(i) =
|NS(i)|
|NC(i)|
16: end for
17: {Choose the most critical target}
18: i
∗
= min
i∈T
R(i)
19: for all j ∈ NS(i
∗
) do
20: Compute p
jk
= |T
0
( j) ∩ {T
0
\ T(C
k
)}| for each
cover set C
k
∈ NC(i
∗
)
21: end for
22: Solve the linear assignment problem to assign one
sensor j ∈ NS(i
∗
) in each cover set k ∈ NC(i
∗
) with
costs p
jk
23: Update C
k
,T(C
k
) ∀k = 1..K
max
24: Update T,S and NS(i),NC(i) ∀i ∈ T
25: end while
26: K
1
← K
max
27: if T is not empty then
28: for all i ∈ T do
29: Delete the cover sets C
k
∈ NC(i)
30: K
1
← K
1
− 1
31: end for
32: end if
Some targets may have the same critical rate. In
this case, the choice of the most critical target is made
randomly among these targets. When the most critical
target has been identified, sensors monitoring this tar-
get have to be distributed in each cover set which does
not already cover this target. This distribution can be
made randomly or made soundly in order to cover a
maximum number of targets in each cover set. That
is why we give a cost p
jk
for the possible assignment
of the sensor j to a cover set C
k
which represents the
additional number of targets that the cover set C
k
is
able to monitor if the sensor j is added. We face a lin-
ear assignment problem where it is required to assign
exactly one sensor to each cover set in such a way that
the total cost of the assignment is maximized. In our
case, the number of sensors to be assigned can be dif-
ferent to the number of cover sets. If the number of
sensors is greater than the number of cover sets, we
artificially add a new cover set and null costs between
all sensors and this additional cover set to be reduced
to a classical linear assignment problem. In contrast,
if the number of sensors is less than the number of
cover sets, we add a dummy sensor and null costs be-
tween this dummy sensor and the cover sets. During
the process, if we face this second case, this means
that some cover sets may not cover all the targets in
the region of interest.
3.3 Algorithm’s Analysis
We express the time complexity of our algorithm 1 by
using the following notations :
v = max(|S|,|T|) = max(n,m) (3)
and :
S
max
= max
i=1..m
|S
0
(i)| (4)
The time complexity of our algorithm is at most
O
v(|T| + K
max
S
max
+ S
3
max
+ K
max
+ |T|)
(5)
Proof. The main computational cost of the algorithm
is spent in the while loop (lines 13 to 25). This loop
is executed v = max(|S|,|T|) times. The inner loop
(lines 14 to 16) cost at most O(|T|) since the criti-
calness of all the targets in T need to be computed
at each iteration. Line 18 takes O(|T|) for finding
the most critical target. The inner loop (lines 19 to
21) costs |NS(i
∗
)| × |NC(i
∗
)|,i
∗
∈ T, since the cost
p
jk
of each target j ∈ |NS(i
∗
)| needs to be computed
on each cover set k ∈ NC(i
∗
). However, we can
bound both |NS(i
∗
)| and |NC(i
∗
)| by S
max
and K
max
respectively. Thus, the cost of this loop is at most
O(S
max
K
max
). Finally, the line statement 22 is equiv-
alent to a linear assignment problem, which can be
found in polynomial time, for instance using the Hun-
garian method (Harold W. Kuhn, 1955). Thereby,
the linear assignment problem of line 22 takes at
most O
S
3
max
), since we can bound both |NS(i
∗
)| and
|NC(i
∗
)| by S
max
. Updating steps (lines 23 and 24)
require O(K
max
+ |T|) iterations. Thus, summing up
for the whole v loops/iterations, the algorithm’s cost
ANearOptimalAlgorithmforLifetimeOptimizationinWirelessSensorNetworks
199

is at most O
v(|T|+ K
max
S
max
+ S
3
max
+ K
max
+ |T|)
.
Since K
max
≤ S
max
≤ |S| ≤ v, and |T| ≤ v, we can de-
rive the upper bound O
v
4
.
3.4 Randomized Algorithm
Here, we give only a simple proposal of the algorithm
which constructs in parallel the elementary cover sets
as sketched in algorithm 2. Our goal is not to give the
best implementation, but only a possible implementa-
tion in order to compare the lower bounds to the ones
obtained by algorithm 1.
Unlike algorithm 1, the randomized algorithm
chooses randomly a non covered target and tries to
assign a sensor covering this target to each cover set
if necessary. We use the same structure of algorithm
1. This choice is made to demonstrate the relevance
of the selection/assignment policy of algorithm 1.
Algorithm 2: Randomized algorithm.
Require: An initial set of targets T
0
and an initial set of
sensors S
0
Ensure: A set of cover sets C
1
,..,C
K
2
1: {INITIALIZATION}
2: for all cover sets k = 1..K
max
do
3: C
k
←
/
0
4: T(C
k
) ←
/
0
5: end for
6: S ← S
0
7: T ← T
0
8: for all targets i = 1..m do
9: NC(i) ← {C
1
,..,C
K
max
}
10: NS(i) ← S
0
(i)
11: end for
12: {While there exists a target which is not covered by a
cover set and the set of available sensors is not empty}
13: while T 6=
/
0 and S 6=
/
0 do
14: Choose randomly a target i
∗
in T
15: Assign randomly one sensor j ∈ NS(i
∗
) in each
cover set k ∈ NC(i
∗
)
16: Update C
k
,T(C
k
) ∀k = 1..K
max
17: Update T,S and NS(i),NC(i), ∀i ∈ T
18: end while
19: K
2
← K
max
20: if T is not empty then
21: for all i ∈ T do
22: Delete the cover sets C
k
∈ NC(i)
23: K
2
← K
2
− 1
24: end for
25: end if
3.5 Exact Method
In this section, we present how to deduce the optimal
number of disjoint cover sets once we applied each of
the previous algorithms. We obtain an approximated
solution with algorithm 1 or with the randomized al-
gorithm and we denote by K
min
= max{K
1
,K
2
} the
achieved number of disjoint cover sets, where K
1
cor-
responds to the number of disjoint cover sets obtained
with algorithm 1 and K
2
to the number of disjoint
cover sets obtained with the randomized algorithm.
As the optimal number of disjoint cover sets K
opt
is
bounded by K
max
= min
1..m
|S
0
(i)|, we deduce that
K
min
≤ K
opt
≤ K
max
. The intuitive idea is to deduce
K
opt
by performing a binary search between K
min
and
K
max
. At each step of the search process, we check if
there exists a partition of the sensors in K cover sets.
Once the number of disjoint cover sets is fixed to K,
the distribution of sensors among the K cover sets is
given by the resolution of the following integer pro-
gramming (IP) problem:
min1
subject to :
∑
j∈S
0
(i)
y
jk
≥ 1, ∀i ∈ T
0
,∀k ∈ K
∑
k=1..K
y
jk
≤ 1, ∀ j ∈ S
0
y
jk
∈ {0,1}
(6)
The decision variables y
jk
are binary variables
which are equal to 1 if the sensor j belongs to the
cover set k and 0 otherwise. Note that there is no
real objective function. We only try to find a distri-
bution of the sensors over K cover sets which satisfies
some constraints. The first constraint ensures that all
targets are covered in each cover set k = 1..K. The
second constraint forces each sensor to be in only one
cover set. For a given number K of cover sets, it may
happen that the problem has no solution. In this case,
we decrement K and we solve again the problem (6).
To compute K
opt
, we perform a binary search as pre-
sented in algorithm 3.
Algorithm 3: Exact Method - binary search.
Require: A set of targets T
0
, a set of sensors S
0
Ensure: A set of cover sets C
1
,C
2
,...,C
K
opt
K
opt
← K
min
while K
min
! = K
max
do
K ← ⌈
K
min
+K
max
2
⌉ +1
Solve (6 )
if (6 ) has no solution then
K
max
← K
else
K
min
← K
K
opt
← K
Optimal solution y
∗
jk
of (6 ) are saved
end if
end while
for all k = 1..K
opt
do
C
k
← ∪
(s
j
/y
∗
jk
=1)
{s
j
}
end for
SENSORNETS2013-2ndInternationalConferenceonSensorNetworks
200
Note that the integer programming problem (6)
which is solved at each iteration of the binary search
process, to reach the optimal solution, is known to
be NP-hard (Garey and Johnson, 1990). We use
a Branch-and-Bound method to solve it, and we
have interest that algorithm 1 provides the best lower
bound to avoid additional iterations for the resolution
of the integer programming problem.
4 RESULTS
In this section we evaluate the performance of our al-
gorithms by way of simulations. We simulate a net-
work with sensor nodes and target points randomly
located in a 500m× 500m area. We assume the sens-
ing range is equal for all the sensors in the network
and is set to 150m. In the different scenarios we vary
the number of randomly deployed sensor nodes n be-
tween 50 and 200 with an increment of 50. The num-
ber m of targets to be covered varies between 30 and
120 with an increment of 30. The following require-
ments are satisfied: each sensor covers at least one
target and each target is covered by at least one de-
ployed sensor, the connectivity of the network is en-
sured and all sensors are capable of communicating
with the base station. For a given number of sensors
and targets, we generate 100 random topologies of
network. Our experiments have been conducted on a
regular Linux workstation with a AMD Athlon(tm) 64
X2 Dual Core Processor 4000+ of 2,1 GHz. The reso-
lution of the integer programming problem is carried
out by the Branch-and-Bound method implemented
in GLPK (GNU linear Programming Kit) (Mahkorin,
2010) available in the public domain.
Note that for convenience and sake of simplicity,
there is no need to conduct comparison with previous
works in the literature since the obtained results are
compared to the optimal ones achieved by the exact
method.
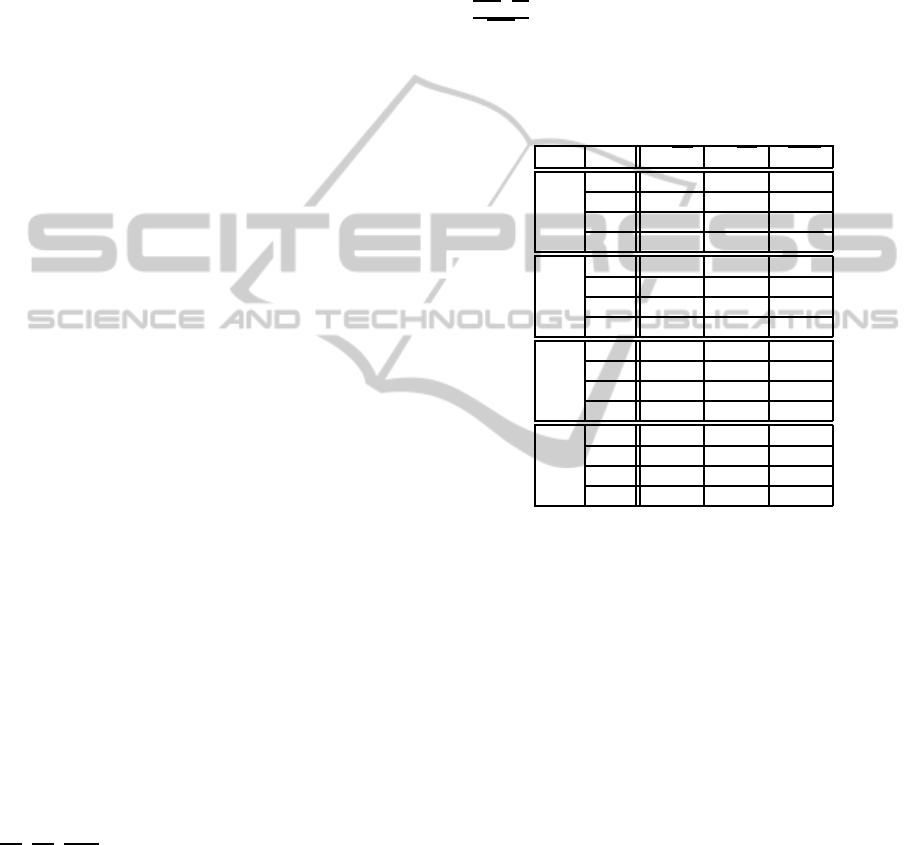
4.1 Number of Disjoint Cover Sets
We measure the average number of disjoint cover sets
K
1
, K
2
, K
opt
over the 100 instances for the algorithm
1, the randomized algorithm and the exact method.
As algorithm 1 and the randomized algorithm inte-
grate a random part, they are executed 50 times for
each network topology of each scenario. Table 1 sum-
marizes the obtained results. Results of table 1 are
consistent with those obtained in the literature (Cardei
and Du, 2005). The number of disjoint cover sets in-
creases with sensor density, and decreases as the num-
ber of targets goes up for a fixed number of sensors.
This is explained by the fact that sensors are more
requested. The obtained results show that our algo-
rithm 1 has a very good behavior because it is able
to achieve near optimal solution compared to the op-
timal one obtained by the exact method in almost all
simulated cases. On the other side a simple random-
ized algorithm provides solutions which are far more
than 15% of the optimum and this gap, computed as
K
opt
−K
2
K
opt
, grows when the number of sensors and tar-
gets increases to reach 38% with 200 sensors and 120
targets.
Table 1: Number of disjoint cover sets.
N M K
2
K
1
K
opt
50 30 2.97 3.46 3.46
60 2.44 2.96 2.96
90 2.19 2.60 2.60
120 2.06 2.49 2.49
100 30 7.16 8.84 8.84
60 5.54 7.54 7.54
90 4.97 6.99 6.99
120 4.65 6.70 6.70
150 30 10.75 13.50 13.50
60 8.80 12.03 12.03
90 7.89 11.34 11.34
120 7.42 10.91 10.91
200 30 14.53 19.03 19.03
60 11.65 16.94 16.98
90 10.44 16.11 16.11
120 9.67 15.53 15.59
4.2 Comparison of the Execution Times
In this section, we compare and comment the CPU
execution times of the different resolution methods.
Table 2 gives the distribution of the execution times
(in seconds) for the three methods over the 16 scenar-
ios. Note that the method called ”exact method” con-
sists in performing a binary search between K
min
and
K
max
and in solving an integer programming problem
at each iteration. To assess the efficiency of our al-
gorithm 1, we distinguish two cases for the reporting
execution times of the exact method. In the first case,
K
min
is given by the number of disjoint cover sets (K
2
)
obtained by the randomized algorithm, and in the sec-
ond case, the binary search begins with K
min
= K
1
.
From table 2, we can see that the running times in-
crease with both sensor and target density as expected
(see the time complexity value in section 3.3). If the
optimal value of the number of disjoint cover sets is
reached with our algorithm 1, then no resolution of
the integer programming is involved again. This leads
to the execution times which are equal to zero (col-
umn 5 of table 2). Moreover, the resolution of inte-
ANearOptimalAlgorithmforLifetimeOptimizationinWirelessSensorNetworks
201
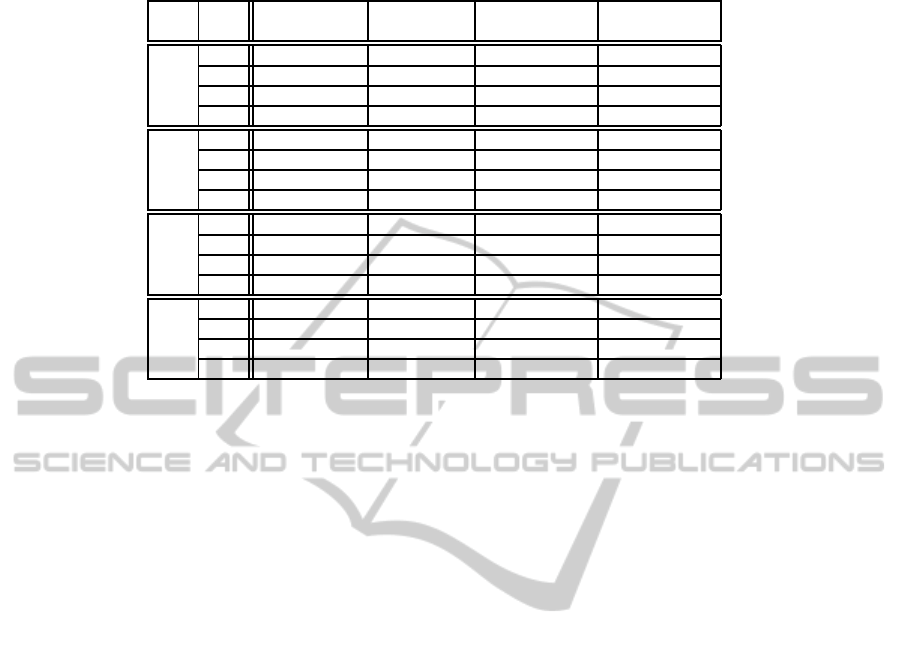
Table 2: Execution times (in seconds) for the 3 methods.
N M Randomized Heuristic Exact method Exact method
algorithm 2 algorithm 1 (K
min
= K
1
) (K
min
= K
2
)
50 30 0.010 0.023 0.000 0.026
60 0.019 0.031 0.000 0.053
90 0.026 0.037 0.000 0.058
120 0.036 0.046 0.000 0.030
100 30 0.026 0.145 0.000 1.445
60 0.056 0.176 0.000 2.443
90 0.086 0.205 0.000 3.540
120 0.118 0.227 0.000 4.070
150 30 0.041 0.503 0.000 17.478
60 0.100 0.653 0.000 25.733
90 0.160 0.698 0.000 42.646
120 0.222 0.768 0.000 58.182
200 30 0.063 1.270 0.000 123.600
60 0.150 1.660 16.190 251.467
90 0.250 1.730 0.000 345.877
120 0.352 1.936 83.26 543.568
ger programming is time consuming and the involved
binary search task to compute the optimal value by
starting with random solution may require more than
9 minutes as the number of sensors/targets goes up.
5 CONCLUSIONS
In this paper, we have addressed the problem of life-
time optimization in wireless sensor networks. This is
a very natural and important problem, as sensor nodes
have limited resources in terms of memory, energy
and computational power. To cope with this problem,
an efficient centralized energy-awarealgorithm is pre-
sented and analyzed. Our algorithm seeks to prolong
the network lifetime by organizing sensors into dis-
joint cover sets which operate successively in order to
monitor all targets.
The proposed algorithm involves a linear assign-
ment problem to generate mutually disjoint cover sets
containing a minimal number of sensors and covering
a maximal number of targets at each iteration. Simu-
lation results highlight the good behaviour of our al-
gorithm, which provides near optimal solutions (equal
to the optimal ones achieved by the exact method for
almost all scenarios) with minimum time complexity.
The quality of the obtained lower bound reduces sig-
nificantly the search for the optimal number of cover
sets, because this search process requires the reso-
lution of an integer programming problem which is
time-consuming.
REFERENCES
Akyildiz, I., Su, W., Y.Sankarasubramniam, and Cayirci, E.
(2002). A survey on sensor networks. IEEE Comm.
Magazine, pages 102–114.
Cardei, M. and Du, D.-Z. (2005). Improving wireless sensor
network lifetime through power aware organization.
Wirel. Netw., 11:333–340.
Cardei, M., MacCallum, D., Cheng, M. X., Min, M., Jia,
X., Li, D., and Du, D.-Z. (2002). Wireless sensor net-
works with energy efficient organization. Journal of
Interconnection Networks, 3(3-4):213–229.
Cardei, M., Thai, M. T., Li, Y., and Wu, W. (2005). Energy-
efficient target coverage in wireless sensor networks.
In INFOCOM, pages 1976–1984.
Chaudhary, M. and Pujari, A. K. (2011). High-energy-
first (hef) heuristic for energy-efficient target coverage
problem. International Journal of Ad hoc, Sensor and
Uniquitous computing (IJASUC), 2(1).
Garey, M. and Johnson, D. (1990). Computers and
Intractability; A Guide to the Theory of NP-
Completeness. W. H. Freeman & Co., NY, USA.
Harold W. Kuhn (1955). The Hungarian Method for the
assignment problem. Naval Research Logistics Quar-
terly, 2:83–97.
Mahkorin, A. (2010). GNU Linear Programming Kit, Ref-
erence Manual.
Slijepcevic, S. and Potkonjak, M. (2001). Power efficient
organization of wireless sensor networks. In IEEE Int.
conf. on Communications, pages 472–476.
Zorbas, D., Glynos, D., Kotzanikolaou, P., and Douligeris,
C. (2007). B{GOP}: an adaptive coverage algorithm
for wireless sensor networks. In Proceedings of the
13th European Wireless Conference, EW’07.
SENSORNETS2013-2ndInternationalConferenceonSensorNetworks
202
