
ON THE IMPORTANCE OF ONE-TIME KEY PAIRS IN
BUYER-SELLER WATERMARKING PROTOCOLS
David M. Williams, Helen Treharnea and Anthony T. S. Ho
∗
University of Surrey, GU2 7XH, Guildford, U.K.
Keywords:
Buyer-seller watermarking, Protocol, Security, Unbinding, Customers’ rights, One-time key pair.
Abstract:
In this paper we emphasize the importance of unique certified one-time key pairs in Buyer-Seller Watermark-
ing (BSW) protocols. We distinguish between reactive unbinding attacks, in which the seller reacts to illicit
file sharing by fabricating further evidence of such activity, and pre-emptive unbinding attacks, in which the
seller gains an advantage by taking action that pre-empts the file being shared. We demonstrate the importance
of certified one-time key pairs in the BSW protocol by Lei et al., for protecting against pre-emptive unbinding
attacks, and subsequently reveal a new attack on a recently published BSW protocol due to its omission of
unique key pairs.
1 INTRODUCTION
Copy deterrence mechanisms discourage illicit dupli-
cation and dissemination of copyrighted material by
embedding an imperceptible identifying mark within
content to trace any illicit file sharing back to the orig-
inal owner (Barni and Bartolini, 2004).
However, the buyer must be assured that the copy-
right owner has proof if and only if an illegal act has
taken place. The assurance that evidence cannot be
fabricated against a buyer is known in the literature as
customers’ rights (Qiao and Nahrstedt, 1998).
Qiao and Nahrstedt observed that previous
schemes, in which the seller chose the watermark,
failed to protect the copyright. Even if a seller had
acted honestly, and is convinced of the buyer’s illegal
activity, the seller remains unable to prove that it was
not they that had leaked the watermarked content.
Memon and Wong proposed a Buyer-Seller Wa-
termarking (BSW) protocol that aimed to resolve this
customers’ rights issue by withholding knowledge
of the watermark or watermarked content from the
seller (Memon and Wong, 2001). However, Lei et al.
later uncovered an issue present in the Memon-Wong
(MW) protocol that they termed the unbinding prob-
lem (Lei et al., 2004). They subsequently proposed
their own protocol, their approach to prevent unbind-
ing was twofold: bind a watermark to content using
some signed message; and use one-time key pairs to
∗
The authors’ work is sponsored by an EPSRC Thales
CASE Award.
avoid outdated information being used in subsequent
transactions.
In this paper we distinguish between two forms of
unbinding, reactive and pre-emptive, and emphasise
the importance of one-time key pairs in preventing the
latter of these.
In Section 2 we provide background material on
the MW protocol and the unbinding problem pre-
sented by Lei et al. and then distinguish between
two forms of unbinding in Section 3. The importance
of one-time key pairs is demonstrated in Section 4,
subsequently a pre-emptive unbinding attack on a re-
cently published protocol is presented in Section 5.
Finally we discuss the danger in entrusting buyer’s to
randomly generate key pairs in Section 6 before draw-
ing conclusions in Section 7. The Appendix provides
a summary of the notation used throughout this paper.
2 THE UNBINDING PROBLEM
In this section we describe the protocol proposed
in (Memon and Wong, 2001) and the associated un-
binding problem presented in (Lei et al., 2004).
The approach taken in (Memon and Wong, 2001)
to resolve the customers’ rights issue, was to restrict
the seller to conduct the watermark embedding in the
encrypted domain, using the properties of homomor-
phic encryption. Knowledge of the watermark and
watermarked content are withheld from the seller dur-
ing embedding and thus the buyer cannot claim that a
441
M. Williams D., Treharnea H. and T. S. Ho A. (2010).
ON THE IMPORTANCE OF ONE-TIME KEY PAIRS IN BUYER-SELLER WATERMARKING PROTOCOLS.
In Proceedings of the International Conference on Security and Cryptography, pages 441-446
DOI: 10.5220/0002978704410446
Copyright
c
SciTePress

copy was released by the seller.
During the watermark generation phase of the
protocol, the buyer receives encrypted watermarks
from a trusted third party, signed to certify they are
well-formed. The third party need not be involved in
transactions between the buyer and seller thus he is
said to be offline (Poh and Martin, 2007). Further-
more, the third party is not required to store any data.
In the watermark insertion phase of the protocol,
the buyer initiates a transaction sending to the seller
some encrypted watermark, S
sk
t
(E
pk
b
(w)), generated
and signed by a trusted third party during the water-
mark generation phase. The seller must also receive
an indication of what cover material the buyer wishes
to purchase, arg(c), and certification of the buyer’s
public key. The encrypted watermark signed by the
certification authority is also sent to the seller.
As the seller is now in possession of the encrypted
watermark E
pk
b
(w) and can calculate the encrypted
content E
pk
b
(c), they construct the encrypted digi-
tal content E
pk
b
(W
wk
s
(c, w)) by performing the em-
bedding in the encrypted domain
2
. The seller pro-
duces E
pk
b
(W
wk
s
(c, w)) without ever knowing the wa-
termark or the watermarked content in the clear.
It should be possible, once an illicitly shared file
is intercepted by the seller, for the original owner to
be traced and this proven to an arbitrator. The proto-
col relies on the buyer participating in the arbitration
process, however if a buyer refuses to do so it is con-
sidered admission of guilt.
The protocol was shown to be flawed in (Lei et al.,
2004). Lei et al. presented an unbinding problem
apparent once the user has illicitly shared content.
Should a single file be shared by a buyer, the seller
may react by embedding this watermark into any
other content in order to fabricate evidence of further
illicit file sharing against the buyer.
Upon completion of a transaction in which they
purchase the content C
1
with watermark W, the
buyer B receives the encrypted watermarked content
E
pk
B
(W
wk
S
(C
1
, W)). Should B upload the decrypted
content W
wk
S
(C
1
, W) onto some file sharing network
the seller S may later download the content and ex-
tract W in order to trace the piracy back to B. How-
ever, once S has extracted W they may embed it
within some other contentC
2
to produceW
wk
S
(C
2
, W).
Thus the evidence of illicit file sharing of C
2
(i.e.,
W
wk
S
(C
2
, W) and S
sk
T
(E
pk
B
(W))) can be obtained by
S at a time when C
2
has not been shared.
2
An indexing watermark v is first embedded to avoid an
exhaustive search being performed. A permutation function
σ is then applied whilst embedding the watermark c in the
encrypted domain such that the buyer cannot know the sig-
nal embedded.
3 REACTIVE AND PRE-EMPTIVE
UNBINDING
Lei et al. also describe another form of unbinding
attack in which the seller gains an advantage by taking
action that pre-empts a file being shared.
Upon completing a transaction in which they
purchase the content C
1
with watermark W
1
, the
buyer B receives the encrypted watermarked con-
tent E
pk
B
(W
wk
S
(C
1
, W
1
)). However, during a sec-
ond transaction, in which B wishes to purchase the
content C
2
with watermark W
2
, the seller S may
choose to distribute the encrypted watermarked con-
tent E
pk
B
(W
wk
S
(C
2
, W
1
)) to B. Should B ever share
the latter content then S may extract the watermark
W
1
and embed it within the content C
1
. Thus the ev-
idence of illicit file sharing of C
1
(i.e., W
wk
S
(C
1
, W
1
)
and S
sk
T
(E
pk
B
(W
1
))) can be obtained by S at a time
when C
1
has not been shared.
In the first attack scenario, described in Section 2,
the malicious seller reacts to the file sharing ma-
liciously by subsequently extracting the watermark
from the shared file and embedding it within another.
This is only possible after the file sharing event has
occurred. In this paper we shall refer to such an un-
binding attack as Reactive Unbinding. This is as op-
posed to what we shall refer to as Pre-emptive Un-
binding in which the seller gains an advantage by tak-
ing action that pre-empts the file being shared. The
two attacks are only subtly different in the MW pro-
tocol, but we shall see that Lei et al. adopt different
mechanisms to prevent each of the two forms of un-
binding.
4 THE IMPORTANCE OF
ONE-TIME KEY PAIRS
The approach taken in (Lei et al., 2004) to prevent un-
binding, as illustrated in Figure 1, was twofold: bind
a watermark to content using some signed message;
and use one-time key pairs to avoid outdated infor-
mation being used in subsequent transactions.
The one-time key pairs were proposed as a mech-
anism to prevent pre-emptive unbinding, although
other papers refer to them as anonymous keys such
as (Deng and Preneel, 2008), (Ju et al., 2003) and
(Shao, 2007). It is out of the scope of this paper to
consider anonymity; instead we will demonstrate the
importance of one-time key pairs for the overall secu-
rity of the scheme.
SECRYPT 2010 - International Conference on Security and Cryptography
442
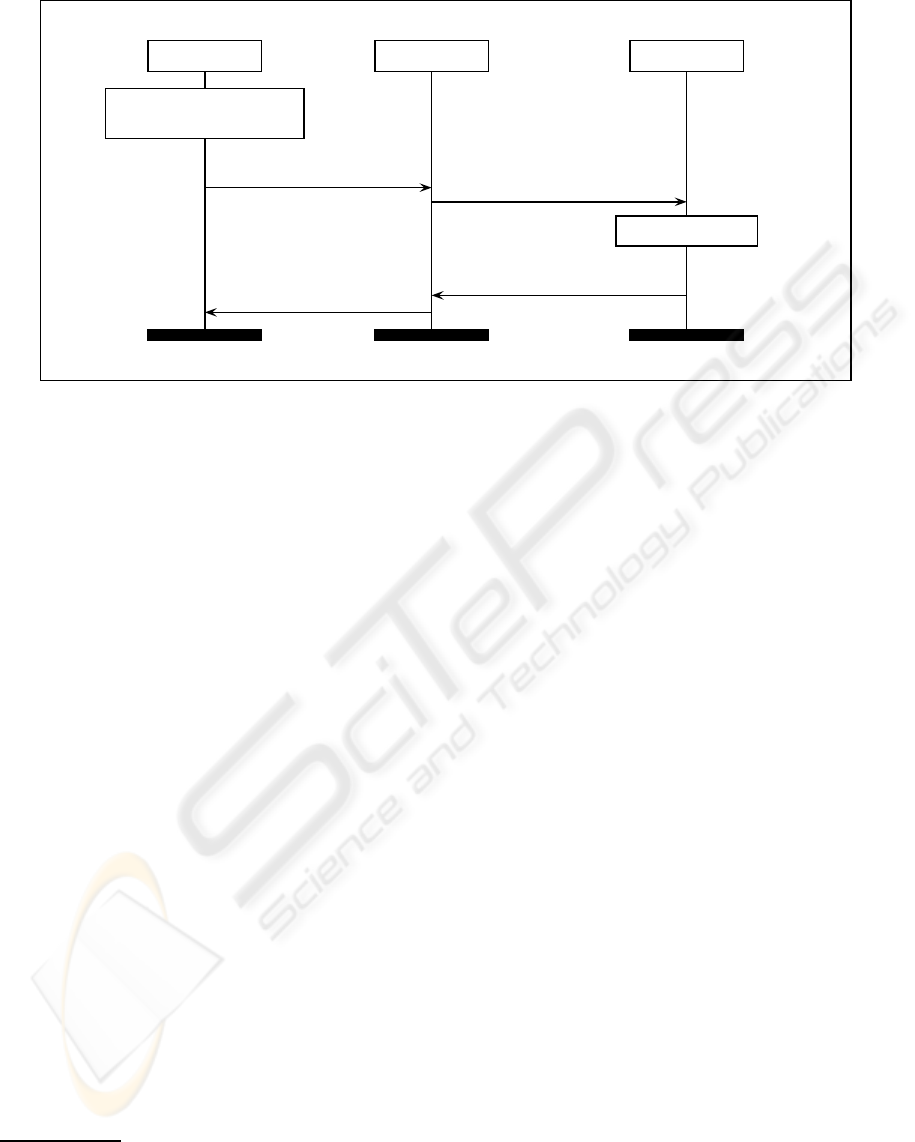
A, PK, sk
b
, C
sk
ca
(pk
b
), {arg(c)|c ← CV}, KP
∗
Buyer b
A, PK, sk
s
, wk
s
, CV
Seller s
A, PK, sk
t
, WM
TTP t
arg ∈ {arg(c)|c ← CV}
(pk
b
∗
, sk
b
∗
) ∈ KP
∗
C
sk
ca
(pk
b
), C
sk
b
(pk
b
∗
)
arg, S
sk
b
∗
(arg)
C
sk
b
(pk
b
∗
), char(c)
arg, S
sk
b
∗
(arg)
w ∈ WM
E
pk
b
∗
(w), E
pk
t
(w)
S
sk
t
(E
pk
b
∗
(w), pk
b
∗
, S
sk
b
∗
(arg))
E
pk
b
∗
(W
wk
s
(c, w))
Figure 1: LYTC protocol.
4.1 Lei-Yu-Tsai-Chan (LYTC) Protocol
Figure 1 illustrates the LYTC protocol. The trusted
third party is online during each run of the proto-
col, generating a unique watermark for each trans-
action. The buyer initiates the protocol by sending
S
sk
b
∗
(arg(c)) to the seller, indicating the content they
wish to receive. An anonymous certificate, signed by
a certification authority, is sent from the buyer to the
seller to certify the buyer’s public key, C
sk
ca
(pk
b
), al-
though a standard digital certificate may be used if
privacy is not a concern.
The buyer constructs a one-time public-secret key
pair (pk
b
∗
, sk
b
∗
) as the unique key pair used during
the current transaction. This ensures that outdated in-
formation cannot be used in subsequent transactions
and thus prevents pre-emptive unbinding. The buyer
certifies the public key by constructing a second digi-
tal certificate C
sk
b
(pk
b
∗
). The key pk
b
∗
is immediately
used to verify the signed agreement sent by the buyer.
Upon verification of the signed agreement, the
seller forwardsC
sk
b
(b
∗
, pk
b
∗
) and E
sk
b
∗
(arg(c)) to the
third party. In order to ensure the watermark is suit-
ably robust the seller also sends some characteristics
char(c) of the cover material
3
.
The trusted third party then constructs a robust
watermark that is unique to this transaction. They
use the public key received in the digital certificate
C
sk
b
(pk
b
∗
) to encrypt the watermark ready for use by
3
Lei et al. state that the seller may send the content c if
unconcerned about doing so. Evidence of illicit file sharing
can be fabricated by any agent in possession of the cover
material and watermark. Hence, the third party must not
know the cover material as they choose the watermark.
the seller. It is sent along with the public key used to
encrypt it and bound to the signed agreement by the
trusted third party by signing a message constructed
of all three components. It is this message that pre-
vents reactive unbinding. They also encrypt the wa-
termark under their own secret key in case they need
to verify the watermark in the arbitration process.
Finally, the seller constructs the watermarked con-
tent in the encrypted domain. Once the buyer has re-
ceived the encrypted, watermarked content they are
able to decrypt in order to gain the useful water-
marked content that they wished to purchase.
4.2 Omitting One-time Key Pairs
By binding the watermark to the cover material via the
signed message S
sk
t
(E
pk
b
∗
(w), pk
b
∗
, S
sk
b
∗
(arg)), Lei
et al. prevent the malicious seller from performing
a reactive unbinding attack. However, this message
alone does not protect against pre-emptive unbinding.
Let us suppose that the key pair need not be
unique, then a buyer B may use the same key pair
(pk
B
∗
, sk
B
∗
) in multiple transactions. Consider the
first piece of content C
+
purchased as more ex-
pensive than a second piece of content C
−
. In
the first transaction the seller S receives the signed
message S
sk
T
(E
pk
B
∗
(W), pk
B
∗
, S
sk
B
∗
(arg(C
+
))) be-
fore distributing the encrypted watermarked content
E
pk
B
∗
(W
wk
S
(C
+
, W)) to B.
Subsequently in a second run of the protocol B
purchases C
−
using the same key pk
B
∗
. As such, S
omits the communication with the trusted third party
T and instead embeds the same encrypted watermark
E
pk
B
∗
(W) as in the first transaction.
Should S ever intercept an illicitly shared
ON THE IMPORTANCE OF ONE-TIME KEY PAIRS IN BUYER-SELLER WATERMARKING PROTOCOLS
443

copy of the less expensive watermarked content
W
wk
S
(C
−
, W) then W can be extracted and em-
bedded into the higher priced content to produce
W
wk
S
(C
+
, W). This, along with the signed message
received signed message from the first transaction
S
sk
T
(E
pk
B
∗
(W), pk
B
∗
, S
sk
B
∗
(arg(C
+
))), is then consid-
ered sufficient evidence of illicit file sharing of the
more expensive content, when in fact the less expen-
sive watermarked content was illicitly shared.
Should the encryption key pk
B∗
be unique to each
transaction then it is not possible for the seller to per-
form the watermark embedding using an outdated en-
crypted watermark associated with a previous trans-
action. Hence, the uniqueness of the one-time key
pairs must be assured for the LYTC protocol is not
vulnerable to pre-emptive unbinding.
Before discussing how this impacts other BSW
protocols in Section 6, we first present a pre-emptive
unbinding attack on a recently published protocol.
5 A PRE-EMPTIVE UNBINDING
ATTACK ON THE HU-ZHANG
(HZ) PROTOCOL
Lei et al. included one-time key pairs to prevent pre-
emptive unbinding. In this section we shall identify,
for the first time, a pre-emptive unbinding attack on
the Hu-Zhang (HZ) protocol due to the omission of
one-time key pairs, as illustrated in Figure 2.
5.1 Hu-Zhang (HZ) Protocol
In (Hu and Zhang, 2009) a protocol was proposed
aiming to increase the efficiency of multiple transac-
tions. The trusted third party is not required to be on-
line during a transaction between the buyer and the
seller. As such the HZ protocol is subject to two
phases, similar to the MW protocol: the watermark
generation phase; and the watermark insertion phase.
In the watermark generation phase, Hu and Zhang
propose the novel idea of enabling the buyer to re-
quest multiple signed encrypted well-formed water-
marks at once. Upon receipt of the buyers digital cer-
tificate C
sk
ca
(b, pk
b
) and the quantity n of watermarks
required, the trusted third party randomly generates
n unique watermarks w
1
, w
2
, . . . w
n
∈ WM. Each is
encrypted using the public key pk
b
of the buyer and
signed, along with the same public key. Thus for each
watermark w
i
a message E
pk
b
(w
i
), S
sk
t
(pk
b
, E
pk
b
(w
i
))
is sent from the trusted third party to the buyer along
with certification of the buyer’s public key.
In the watermark insertion phase the buyer
chooses which watermark from the generation phase
to use for the current transaction. The buyer sends to
the seller a common agreement, along with a signa-
ture used to bind the watermark to the cover material,
in the message arg, S
sk
b
(E
pk
b
(w), arg). This is sent
with messages m
w
and m
b
, received in the watermark
generation phase. The seller verifies the signatures
and embeds the watermark in the encrypted domain,
sending the result E
pk
b
(W
wk
s
(c, w)) to the buyer.
5.2 A Pre-emptive Unbinding Attack
One-time key pairs are not used in (Hu and Zhang,
2009) and no alternative mechanism for preventing
pre-emptive unbinding is provided, which leads to the
following attack:-
Upon completing a transaction in which they
purchase the content C
+
with watermark W, the
buyer B receives the encrypted watermarked content
E
pk
B
(W
wk
S
(C
+
, W)). During a second transaction, in
which the B purchases less expensive content C
−
the
seller S ignores the watermark received but instead
embeds W received in the first transaction. Finally,
the seller distributes the encrypted watermarked con-
tent E
pk
B
(W
wk
S
(C
−
, W)).
Should the buyer share the less expensive content,
S may extract W and embed it within the more expen-
sive content C
+
. Thus evidence of illicit file sharing
of C
+
(i.e., W
wk
S
(C
+
, W), S
sk
B
(E
pk
B
(W), arg(C
+
))
and S
sk
T
(pk
B
, E
pk
B
(W))) can be obtained by the seller
at a time when C
+
has not been shared.
This attack closely follows the pre-emptive un-
binding attack on the MW protocol described in Sec-
tion 3. It differs only in what constitutes sufficient
evidence of file sharing. It demonstrates that signing
a message to bind the watermark to the cover mate-
rial does not alone prevent unbinding as a mechanism
also needs to be adopted to avoid outdated informa-
tion being used in subsequent transactions.
Any BSW protocol that fails to adopt a mecha-
nism for avoiding pre-emptive unbinding is vulnera-
ble to attack. It has been demonstrated in (Poh and
Martin, 2008) and (Deng and Preneel, 2008) that the
protocol proposed in (Ibrahim et al., 2007) is flawed,
however it is also vulnerable to the pre-emptive un-
binding attack described in this section.
6 ASSURING KEY PAIRS ARE
USED ONLY ONCE
From the customers’ right issue, Qiao and Nahrst-
edt observed that watermarking schemes in which the
seller chose the watermark to be embedded failed
SECRYPT 2010 - International Conference on Security and Cryptography
444
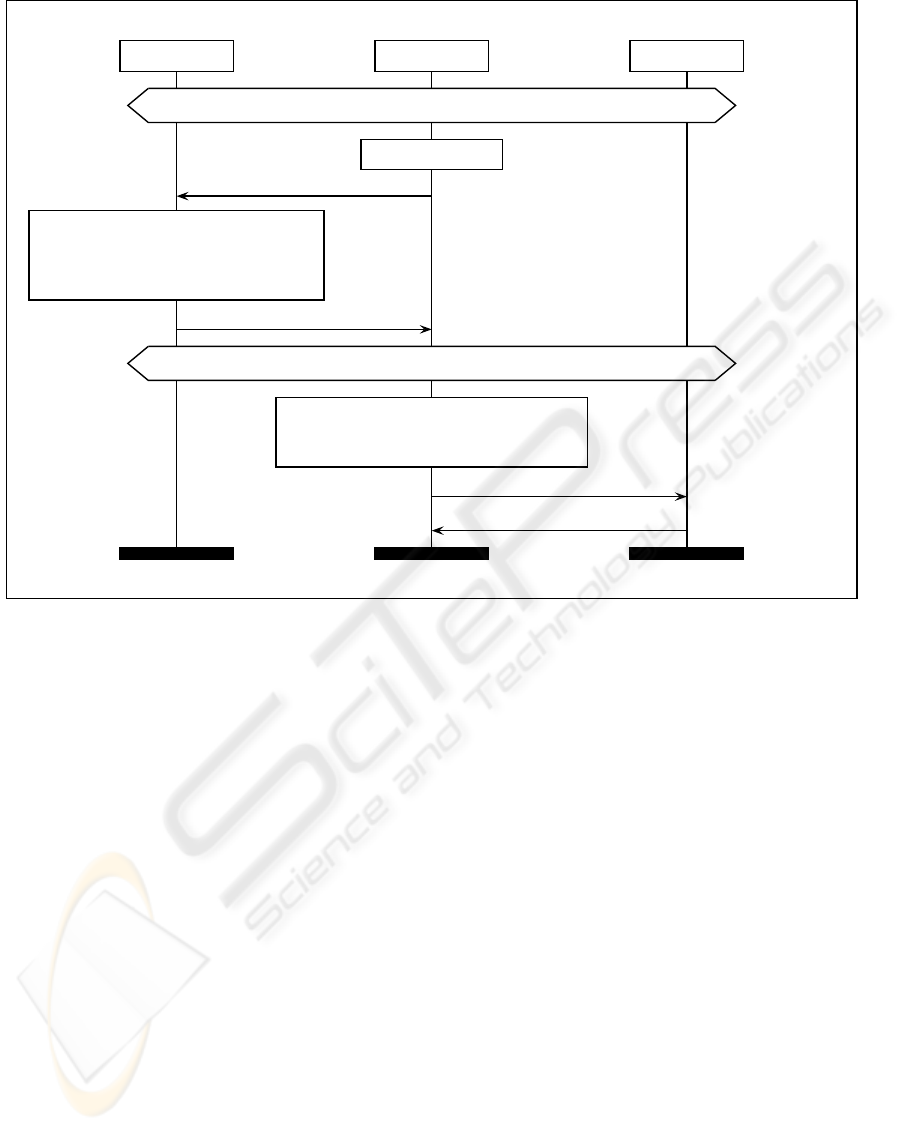
A, PK, sk
t
, WM
TTP t
A, PK, sk
b
, C
sk
ca
(b, pk
b
), {arg(c)|c ← CV}
Buyer b
A, PK, sk
s
, wk
s
, CV
Seller s
Watermark Generation Phase
n ∈ N
n, C
sk
ca
(pk
b
)
w
1
, w
2
, . . . w
n
∈ WM
m
w
i
:= E
pk
b
(w
i
), S
sk
t
(pk
b
, E
pk
b
(w
i
))
m
b
:=
pk
b
, E
pk
b
(C
sk
ca
(b, pk
b
)),
S
sk
t
(pk
b
, E
pk
t
(C
sk
ca
(b, pk
b
)))
m
w
1
, m
w
2
, . . . m
w
n
, m
b
Watermark Insertion Phase
w ∈ {w
1
, w
2
, . . . w
n
}
arg ∈ {arg(c)|c ← CV}
m
c
:= arg, S
sk
b
(E
pk
b
(w), arg)
m
c
, m
w
, m
b
E
pk
b
(W
wk
s
(c, w))
Figure 2: HZ protocol.
to protect the copyright (Qiao and Nahrstedt, 1998).
Should the seller fail to address this issue an arbitra-
tor is unable to discern whether it is the buyer or seller
that has acted maliciously. Thus, it is in the inter-
est of a dishonest buyer to act in a manner that ren-
ders themselves vulnerable to an attack as they may
as a consequence construct a plausible denial of the
illicit file sharing they wish to perform. In (Williams
et al., 2008a), the protocol proposed in (Ibrahim et al.,
2007) was shown to be vulnerable to unbinding if the
buyer leaves himself open to attack. The buyer can
then share files without the seller being able to prove
precisely which files were shared and escape prosecu-
tion. Although unbinding is only possible once a file
is shared, the fabrication of evidence implies a failure
to resolve the customers’ rights issue.
As it is in the interest of the buyer for the protocol
to fail to protect their rights, this implies it is in their
interest to leave themselves vulnerable to unbinding.
We demonstrated in Section 4.2 that the resolution of
the customers’ rights issue in (Lei et al., 2004) is de-
pendent upon the uniqueness one-time key pairs. An
unbinding attack is possible on the LYTC protocol
should the same key pair be used in multiple trans-
actions. A similar vulnerability in (Shao, 2007) was
presented in (Williams et al., 2008b) As preventing
pre-emptive unbinding is dependent upon the unique-
ness of the one-time key pairs it is apparent that en-
trusting the random generation of one-time key pairs
to the buyer puts the protocol’s security at risk.
A natural choice of whom ensures the uniqueness
of key pairs thus becomes the seller. The digital cer-
tificate C
sk
b
(pk
b
∗
) must be checked against all other
certificates used in previous transactions. Duplicate
certificates must be rejected and the seller may later
be required to prove this action to the arbiter. These
may not be trivial tasks if the protocolis deployed on a
large scale e-commerce system in which a great num-
ber of certificates must be stored and cross referenced
in each transaction.
7 CONCLUSIONS
One time key pairs are the mechanism adopted by Lei
et al. to avoid pre-emptiveunbinding attacks in which
the seller gains an advantage by taking action that pre-
empts the file being shared. We have demonstrated
that the omission of one time key-pairs from a BSW
protocol leaves it vulnerable to a pre-emptive unbind-
ON THE IMPORTANCE OF ONE-TIME KEY PAIRS IN BUYER-SELLER WATERMARKING PROTOCOLS
445

ing attack. This led to our discovery of an attack on
the recently published HZ protocol that had not pre-
viously been identified, as described in Section 5.
In Section 6 we justified why the buyer must not
be left to ensure that a unique key pair is used in each
transaction as it is in their interest to use duplicates.
We therefore conclude that the seller must verify the
uniqueness of key pairs unless such action becomes
unmanageable wherein an alternative approach to as-
suring key uniqueness must be proposed.
REFERENCES
Barni, M. and Bartolini, F. (2004). Watermarking Systems
Engineering. Marcel Dekker, Inc.
Deng, M. and Preneel, B. (2008). Attacks on two buyer-
seller watermarking protocols and an improvement for
revocable anonymity. Electronic Commerce and Secu-
rity, International Symposium, 0:923–929.
Hu, Y. and Zhang, J. (2009). A secure and efficient buyer-
seller watermarking protocol. Journal of Multimedia,
4(3):161–168.
Ibrahim, I. M., El-Din, S. H. N., and Hegazy, A. F. A.
(2007). An effective and secure buyer seller water-
marking protocol. In Third International Symposium
on Information Assurance and Security, pages 21–28.
Ju, H. S., Kim, H. J., Lee, D. H., and Lim, J. I. (2003). An
anonymous buyer-seller watermarking protocol with
anonymity control. In International Conference on In-
formation Security and Cryptology, pages 421–432.
Lei, C. L., Yu, P. L., Tsai, P. L., and Chan, M. H. (2004).
An efficient and anonymous buyer-seller watermark-
ing protocol. IEEE Transactions on Image Process-
ing, 13(12):1618–1626.
Mauw, S. and Bos, V. (2001). Drawing Message Sequence
Charts with L
A
T
E
X. TUGBoat, 22(1-2):87–92.
Memon, N. and Wong, P. W. (2001). A buyer seller water-
marking protocol. IEEE Transactions on Image Pro-
cessing, 10(4):643–649.
Poh, G. S. and Martin, K. M. (2007). A framework for
design and analysis of asymmetric fingerprinting pro-
tocols. In Third International Symposium on Informa-
tion Assurance and Security, pages 457–461.
Poh, G. S. and Martin, K. M. (2008). On the (in)security
of two buyer-seller watermarking protocols. In SE-
CRYPT 2008 - International Conference on Security
and Cryptography, pages 253–260.
Qiao, L. and Nahrstedt, K. (1998). Watermarking schemes
and protocols for protecting rightful ownership and
customer’s rights. Journal of Visual Communication
and Image Representation, 9(3):194–210.
Shao, M. H. (2007). A privacy-preserving buyer-seller wa-
termarking protocol with semi-trust third party. In
Trust, Privacy and Security in Digital Business, pages
44–53.
Williams, D. M., Treharne, H., Ho, A. T. S., and Culnane, C.
(2008a). Using a formal analysis technique to identify
an unbinding attack on a buyer-seller watermarking
protocol. In 10th ACM Workshop on Multimedia and
Security, pages 205–214.
Williams, D. M., Treharne, H., Ho, A. T. S., and Waller, A.
(2008b). Formal analysis of two buyer-seller water-
marking protocols. In 7th International Workshop on
Digital Watermarking, pages 278–292.
APPENDIX
The following notation is used throughout.
• A set of all agents
• WM, CV sets of all watermarks and cover material re-
spectively
• PK set of all public keys
• KP
∗
set of all one-time key pairs
• b, s, t, ca variables to model agents, respectively buyers,
sellers, trusted third parties and certification authorities
• w, c variables to model watermarks and content taken
from the set of all watermarks WM and set of all digital
content CV, respectively
• (pk
a
, sk
a
) public-secret key pair belonging to agent a
• wk
s
watermarking key belonging to seller s
• arg(c) common agreement identifying content c
• C
sk
ca
(a, pk
a
) digital certificate binding an agent to their
public key signed under sk
ca
• C
sk
ca
(pk
a
) anonymous certificate signed under sk
ca
• S
sk
a
(m) message m signed under sk
a
• E
pk
a
(m) message m encrypted under pk
a
• W
wk
s
(c, w) watermark w embedded within c using wa-
termarking key wk
s
Lowercase values are considered variable whereas
those in uppercase are concrete. Protocols are pre-
sented as message sequence charts (Mauw and Bos,
2001) in conjunction with this notation.
SECRYPT 2010 - International Conference on Security and Cryptography
446
