
BLIND DETECTION IN IDMA SYSTEMS
Hamza Abdelkrim, Kazem Ali, Salut Gerard
LAAS Laboratoire d’Analyse et d’Architecture des Systemes CNRS, LAAS
7 avenue du colonel Roche, F-31077 Toulouse, France
Chitroub Salim and Touhami Rachida
1
LCPTS Laboratoire de Communication et du Traitement du Signal, USTHB, 16111, Alger, Algeria
1
Laboratoire d’instrumentation, USTHB, 16111, Alger, Algeria
Keywords:
IDMA, Noisy independent component analysis, Multiuser detection.
Abstract:
Interleaved Division Multiple Access (IDMA) is a new access scheme that has been proposed in the literature
to increase the capacity of wireless channels. The performance of such systems depends on the accuracy of the
channel state information (CSI) at the receiver. In this paper, a Noisy-Independent Component Analysis (N-
ICA) based IDMA receiver for multiple access communication channels is proposed and compared to classical
receivers. The N-ICA component is applied as a post processor. The estimation of CSI will often have some
measurement errors, which degrade the accuracy of symbol detection. Using blind methods, this overhead
can be eliminated. Simulation results demonstrate that N-ICA post processor provides an improvement in
performance in terms of bit error rate (BER) in loaded systems and it offers an efficient alternative to systems
with block channel estimation. When the system is not loaded, the proposed post processor presents the same
performance as conventional IDMA receiver with less iterations leading to a complexity reduction.
1 INTRODUCTION
Recently proposed Interleave-Division Multiple-
Access (IDMA) communication system is one of the
most promising technologies for high data rate wire-
less networks. IDMA can be regarded as a special
case of Code Division Multiple Access (CDMA). In
CDMA systems, users are separated using signatures
or spreading codes; while in IDMA systems, dis-
tinct interleavers are employed to separate users. This
principle has been studied previously and its poten-
tial advantages have been demonstrated (Ping, 2006).
Moreover, since conventional IDMA detector is sen-
sitive to channel estimation errors, a good channel
tracking algorithm is mandatory. This might drasti-
cally increase the overall complexity at the receiver.
In order to overcome those drawbacks, in this pa-
per, we propose a new blind receiver for IDMA sys-
tems. In our approach, a Noisy Independent Compo-
nent Analysis (N-ICA) scheme is introduced as a post
processor. So, we propose to detect and separate the
transmitted symbols without channel tracking and by
including the noise in the global model; leading to the
N-ICA model. We will show that our model is very
suitable for symbol detection and separation in the
IDMA context. In terms of complexity, as a post pro-
cessor, the proposed solution starts the processing just
after conventional IDMA processing.The remainder
of this paper is organized as follows. The next sec-
tion is devoted to the IDMA system model. In section
3, we detail the proposed N-ICA model for IDMA.
In section 4, an estimation algorithm is presented for
N-ICA in an IDMA context. Using some evaluation
criteria, computer simulation results are presented in
section 5 to provide a comparativestudy. Conclusions
are drawn in section 6.
2 SYSTEM MODEL
As shown in figure 1, we consider an IDMA system
with K users. A single path channel and BPSK modu-
lation are considered here. The nth bit d
k
(n) in the se-
quence d
k
of kth user is spread, generating a sequence
vector denoted c
k
=[c
k
(1),c
k
(2),...,c
k
(J)]
T
where J is
the frame length C is the spreading factor and the su-
perscript T is the transpose operator. Then c
k
is per-
mutated by an interleaver π
k
. At the output of the
137
Abdelkrim H., Ali K., Gerard S., Salim C. and Rachida T. (2010).
BLIND DETECTION IN IDMA SYSTEMS.
In Proceedings of the International Conference on Wireless Information Networks and Systems, pages 137-141
DOI: 10.5220/0002934801370141
Copyright
c
SciTePress
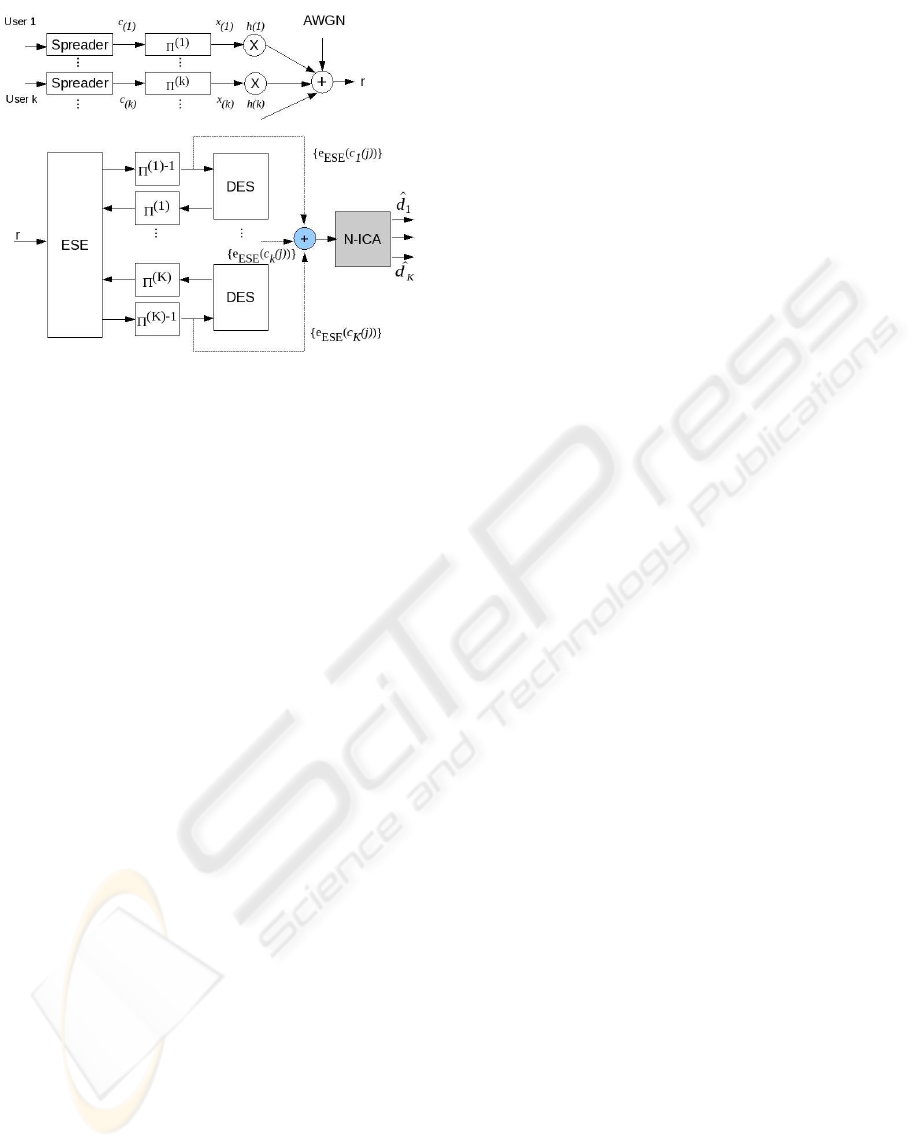
Figure 1: System model.
interleaver, the vector x
k
=[x
k
(1),x
k
(2),...,x
k
(J)]
T
is
obtained. The elements in c
k
and x
k
are considered as
chips. The chip rate is C times higher than the bit rate.
Users are distinguished mainly by their respective in-
terleavers π
k
. Each user can has its own signature se-
quence or all users can share the same spreading code
(Ping,2004). The received signal can be modeled as:
r(t) =
M
∑
m=1
K
∑
k=1
h
k
d
k
(m)s
k
(t − mT − τ
k
) + n(t) (1)
where h
k
is the path gain, d
k
(m) is the kth user’s mth
data bit, s
k
(.) is kth user’s binary interleaved chip
sequence (this is a specific feature for IDMA) used
in the interval [0,T];T is the bit duration, s
k
(t) ∈
{−1, 1}. The delay of the path is denoted by τ
k
and n( j) zero-mean Additive White Gaussian Noise
(AWGN) with variance σ
2
= No/2.
3 ICA AND N-ICA PRINCIPLE
The application of ICA consists of estimating the un-
known input signals from the output signals without
prior knowledge of the channel state information (Hy-
varinen,1999). Let’s suppose that the sources are sta-
tistically independent. This is a fundamental assump-
tion for using ICA that is generally verified in com-
munication systems (Huovinen, 2007). The extrac-
tion of the sources can be done by ICA by exploiting
the essential features of the sources and system. In
the simplest form of ICA, we observe n scalar vari-
ables r
1
,r
2
,...,r
n
which are linear combinations of l
unknown independent sources or components ICs de-
noted by b
1
,b
2
,...,b
l
. If we express the observed ran-
dom variables with the vector, r=(r
1
,r
2
,...,r
n
)
T
. and
the ICs variables b
j
with the vector b=(b
1
,b
2
,...,b
l
)
T
then the relationship is given by (Huovinen, 2007):
r = Gb (2)
In the noisy ICA model, the noise is assumed to be
additive and the observed data can be expressed as:
r
m
= Gb
m
+ n (3)
where r
m
is the mth observed data vector, G is an
unknown full rank mixing matrix, b
m
is an unknown
non gaussian source vector and n is an additive Gaus-
sian noise process. The goal is to estimate the noise
free ICs b
m
using only the observations r
m
and the
assumption of the independence of the sources. This
means that a set of vectors w
1
,w
2
.. should be esti-
mated such that W = [w
1
,w
2
,...] is the separating ma-
trix; therefore, the output source estimations w
T
1
r
m
,
w
T
2
r
m
... i.e.:
y
m
= W
T
r
m
(4)
are independent and each of them can be used to rep-
resent one of the sources.
3.1 Mathematical Representation of
IDMA by N-ICA Model
In this subsection, we develop the theoretical frame-
work and show the similarity between Noisy ICA
model and IDMA system model.
We focus our attention on synchronous IDMA
systems for simplicity and brevity. However, the
method can be extended to an asynchronous system
by extending the observation interval. Equation (1)
can be simplified to model the received signal of a
synchronous IDMA system by:
r
m
(t) =
K
∑
k=1
h
k
d
k,m
s
k
(t) + n(t) (5)
After chip rate sampling i.e. C equal spaced sam-
ples per symbol are taken, the sampled data is pro-
cessed within a window of specific size (Mahafenno,
2007). For synchronous model, data propagated
through a single path channel fall into the same win-
dow of size T for desired and interfering symbols.
The samples are then collected into a Cx1 vectors
r
m
.
r
m
=
K
∑
k=1
h
k
d
k,m
s
k
+ n
m
(6)
Here s
k
is the C x1 vector representation of kth
user’s interleaved signature sequence and n
m
denotes
the noise vector.
The last equation can be rewritten in a matrix
form:
b
m
= [d
1,m
,d
2,m
,...,d
K,m
]
WINSYS 2010 - International Conference on Wireless Information Networks and Systems
138

s
1
=
s
1,1
,s
2,1
,...,s
C,1
T
Cx1 vector
r
m
=
s
1
,s
2
,...,s
K
h
1
0 .. 0
0 h
2
.. 0
: : .. :
0 0 .. h
K
b
1,m
b
2,m
:
b
K,m
+
n
1
n
2
:
n
K
r
m
= [s
1
h
1
,s
2
h
2
,...,s
K
h
K
]b
m
+ n
m
(7)
Equation (7) can be represented in a more compact
form:
r
m
= Gb
m
+ n
m
(8)
where theCxK matrix G is assumed full rank. We can
see the similarity between the IDMA model of equa-
tion (8) and the N-ICA model of equation (3). The
goal of the Noisy-ICA based IDMA detection is to
recover the symbol vector b
m
for each user k without
knowing the parametric form of G which depends on
the channel coefficients. The objective is to estimate
the filter weight w such that the variable at the output
of the filter is one of the ICs(source signal):
y
m
= w
T
r
m
(9)
If BPSK modulation is used, the symbol of desired
user k can be obtained by using this decision formula:
ˆ
b
k,m
= sgn(w
T
r
m
) (10)
4 N-ICA ESTIMATION
ALGORITHM
The proposed system is a hybrid structure composed
of two parts where a classical IDMA receiver is com-
bined with a N-ICA block as shown in figure 1. Block
IDMA, described in the previous section, works for a
number of iterations (it) after which the block N-ICA
takes over. The proposed N-ICA will act as a post pro-
cessor attached to an IDMA receiver in the presence
of noise. The aim of our N-ICA block is to avoid con-
tinuous tracking of channel state information. In this
section, we will derive estimation algorithms for the
proposed N-ICA post processor in IDMA context.
4.1 Principal Component Analysis
based Processing
The Principal Component Analysis (PCA) based part
of the model consists of whitening the input signals.
This step of processing is achieved by using the PCA
in (Davies, 2004) to extract the Principal Components
(PCs). It is based on the diagonalization concept of
the input signals covariance matrix. This can be done
for the noiseless case as follows
Y = Λ
−1/2
U
T
GB (11)
where the matrix U corresponds to the Eigen vec-
tor of the data covariance matrix C and the diago-
nal matrix Λ that contains the related Eigen values:
Λ
−1/2
= diag[λ
−1/2
1
,λ
−1/2
2
,...,λ
−1/2
n
]. This PCA pro-
cessing can be extended to noisy data using bias re-
movaltechnique (Ekici,2004). In the regular ICA pro-
cess, the covariance matrix of the noise free data r
(nf)
m
can be given by:
C = E{r
(nf)
m
(r
(nf)
m
)
T
} = GG
T
(12)
On the other hand, the covariance matrix of the ob-
served noisy data can be written as:
Γ = E{r
m
(r
T
m
)} = GG
T
+ σ
2
I = C+ C
n
(13)
where σ
2
is the noise power and C
n
is the diagonal
noise covariance matrix. In the noise bias removal
technique, the Eigen values and vectors of matrix Γ−
C
n
is used for whitening instead of matrix Γ which
is called quasi-whitening (Hyvarinen,1999). In fact,
quasi whitening can be performed on the noisy data
as follows:
z = (Λ− σ
2
I)
−1/2
U
T
r
m
(14)
The covariance matrix of quasi white data is then
given by :
E{zz
T
} = I + σ
2
(Λ− σ
2
I)
−1
(15)
From (15), we notice that the covariance matrix is
different from the identity matrix. Therefore, we have
to take into account the non-whiteness of the data.
This is achieved by using the fast ICA algorithm that
is presented in the next subsection.
4.2 Fast ICA Algorithm
The purpose of this work is to establish a new
scheme in which the system can take into account
such random deformations in the detection step.
To improve the performance, the presence of the
noise should be reduced to the minimum using the
extracted PCs without additional prior knowledge of
their statistical properties. This is the purpose of the
ICA based part of the model. Therefore, the ICA
model should include a noise term as well in its linear
transform matrix. We have used two algorithms for
detecting and separating the received signals: IDMA
algorithm (Schoeneich,2005), and the fastICA in
IDMA in (Hamza, 2009). The second ICA approach
that we present here is our contribution to take into
account the noise in the ICA model. This means that
the bias due to noise should be removed, or at least
reduced. The N-ICA algorithm performs as follows:
Let k be the desired user, r
m
,m = 1,..,M the re-
ceived block data and
ˆ
b denotes the estimate of b.
BLIND DETECTION IN IDMA SYSTEMS
139
1. First perform PCA for dimension reduction
2. Quasi- whitened the noisy data using (15)
3. Start ICA
Let t=1 and update
w(t) = Γ
−1
E{z
m
(w(t − 1)
T
z
m
)
3
} −
3E{(w(t − 1)
T
z
m
)
2
}w(t − 1)
where Γ = I + σ
2
(Λ− σ
2
I)
−1
Normalize w(t) : w(t) w(t)/
p
w(t)
T
Γw(t)
If |w(t)
T
w(t
1
)| < (1− 10
−4
), let t= t+1 and go to
step 3.
4. Output the estimated desired user’s bit:
ˆ
b
k,m
= sgn(z
m
)
The blind nature of our proposed scheme presents
the advantage of not altering the capacity of the chan-
nel. Moreover, the N-ICA block starts once the num-
ber of iterations of the classical IDMA receiver fin-
ishes. Hence, it does not generate additional com-
plexity.
5 NUMERICAL RESULTS
To evaluate the detection and separation ability of the
proposed N-ICA model, performances are presented
in terms of raw Bit Error Rate (BER) before decoding
for different Signal to Noise Ratios (SNR). We con-
sider a time varying single path channel (extension
to multipath case can be obtained via state augmen-
tation), BPSK modulation and Gold spreading codes
of length C. Among the parameters that influence the
performances are the effect of load rate and the num-
ber of iterations for IDMA block. The obtained re-
sults are presented in figures 2 to 4.
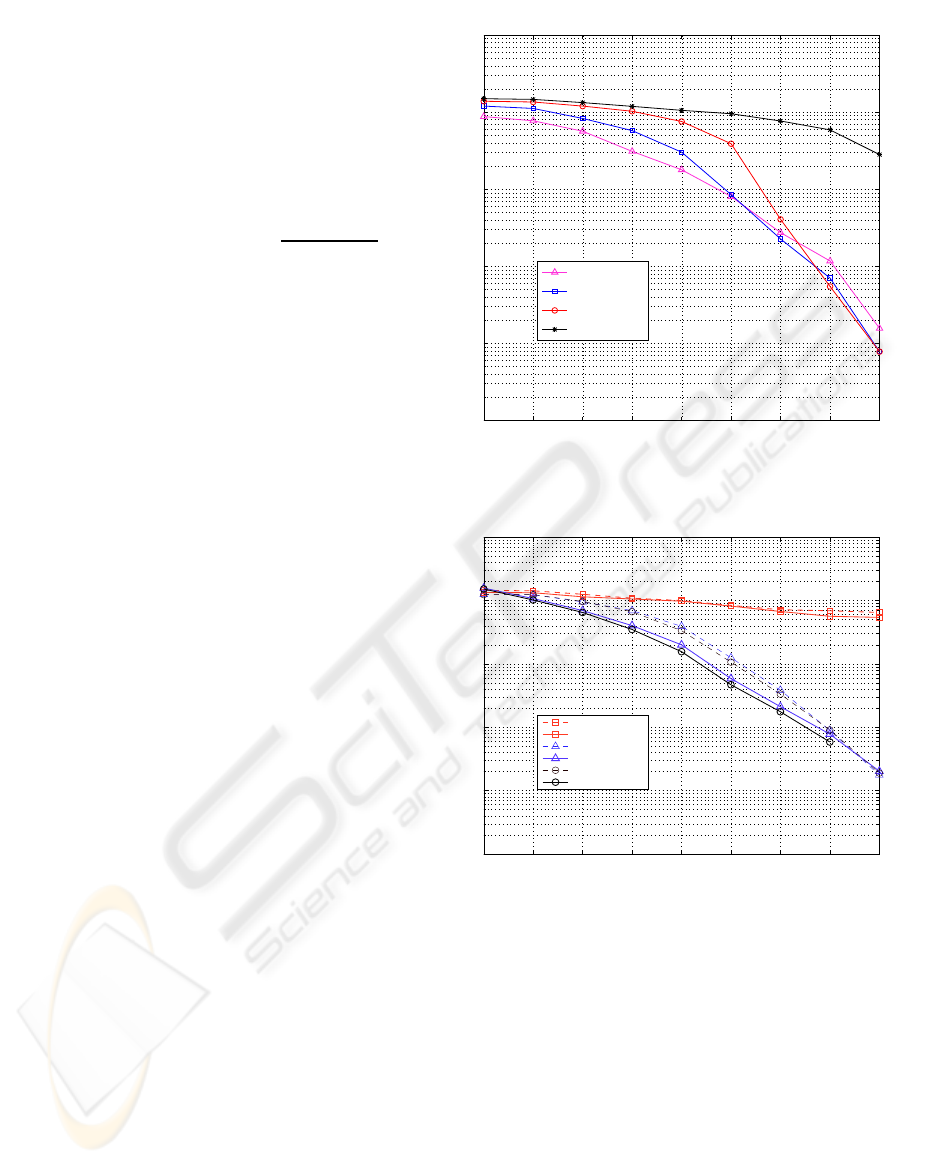
In Figure 2, performances of our proposed re-
ceiver are presented for different values of τ (rate of
load) and a sprading factor of 63. We notice that our
proposed scheme handles very well the Multi Access
Interferences (MAI) since convergence is warranted
even at very loaded systems (τ ≥ 100%).
Figure 3 shows the added value of our proposed
post-processor N-ICA when compared to the con-
ventional IDMA receiver for loading rate 100% and
a spreading factor of 31. We notice that both con-
vergence speed and better BER performances are
achieved. Therefore, the proposed N-ICA approach
can be employed in high loading rates in order to im-
prove the performance of the system in terms of qual-
ity of service. Moreover, in case of low loading rate
(≤ 50%), the proposed post processor allows a reduc-
tion in the number of iterations needed by the IDMA
0 1 2 3 4 5 6 7 8
10
−5
10
−4
10
−3
10
−2
10
−1
10
0
SNR(dB)
BER
τ=50%, it=3
τ=100%, it=30
τ=150%, it=30
τ=200%, it=30
Figure 2: IDMA-N-ICA performance comparison for dif-
ferent rate load and C=63.
0 1 2 3 4 5 6 7 8
10
−5
10
−4
10
−3
10
−2
10
−1
10
0
SNR(dB)
BER
IDMA, it=2
IDMA−N−ICA, it=2
IDMA, it=5
IDMA−N−ICA, it=5
IDMA, it=10
IDMA−N−ICA, it=10
Figure 3: Performance comparison between IDMA and
IDMA-N-ICA receivers when τ=100% and C=31.
block leading to complexity reduction of the overall
receiver.
In the last simulation scenario, we evaluate the
added value of the noisy ICA post processor over
the ICA post processor. Figure 4 provides a com-
parison between IDMA, IDMA-ICA and IDMA-N-
ICA receivers with a spreading factor of 31 and a
load rate of 100%. When SNR is low, N-ICA outper-
forms the ICA post processor. However, when SNR
is high, both receivers present the same performance.
These observations are expected since N-ICA takes
into account the presence of noise. It is worth not-
ing also that both IDMA-ICA and IDMA-N-ICA re-
ceivers outperforms the conventional IDMA receiver.
WINSYS 2010 - International Conference on Wireless Information Networks and Systems
140
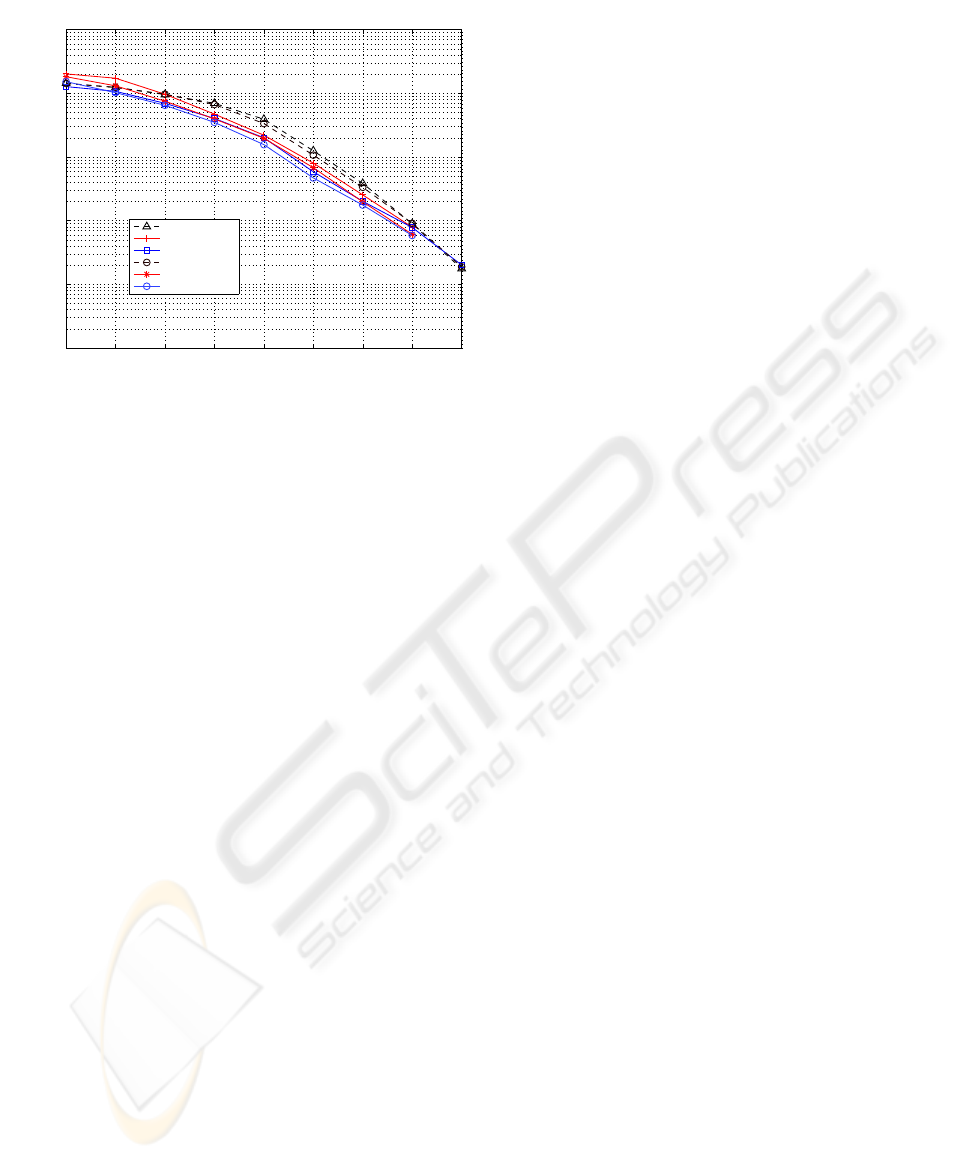
0 1 2 3 4 5 6 7 8
10
−5
10
−4
10
−3
10
−2
10
−1
10
0
BER
SNR(dB)
IDMA, it=5
IDMA−ICA, it=5
IDMA−N−ICA, it=5
IDMA, it=10
IDMA−ICA, it=10
IDMA−N−ICA, it=10
Figure 4: Performance comparison between IDMA, IDMA-
ICA and IDMA-N-ICA receivers.
6 CONCLUSIONS
In this paper, N-ICA post processor is proposed in
IDMA context. N-ICA algorithm constitutes an ef-
ficient tool for symbol recovery and it offers an ef-
ficient alternative to the IDMA systems with block
channel estimation. The major contribution of this
work is the application of blind detection technique
in the IDMA context. The proposed algorithm has
better performance compared to the IDMA receiver
in loaded systems because it allows dimension reduc-
tion (PCA) which helps to reduce the amount of noise
in the system. For unloaded systems, the proposed
post processor allows a complexity reduction by re-
ducing the number of iterations needed by the IDMA
block. In future work, to better analyze the complex-
ity of the proposed scheme, FPGA implementation of
IDMA and proposed post processor will be realized.
REFERENCES
Ping, L. and Liu, L. (2006). Interleave Divison Multiple
Access. IEEE Transactions on Wireless Communica-
tion.
Ping, L. and Liu, L. (2004). Analysis and Design of IDMA
Systems Based on SNR Evolution and Power Alloca-
tion VTC’04, IEEE Transactions on Wireless Commu-
nication.
Mahafeno, I. (2007). Reduced Complexity Iterative Multi-
User Detector for IDMA (Interleave Division Multi-
ple Access) System, GLOBECOM06, Proceedings of
IEEE Global Telecom. Conference
Schoeneich, H. and Hoeher, P. (2005) Semi-Blind
Pilot-layer Aided Channel Estimation with Empha-
sis on Interleave Division Multiple Access Systems.
GLOBECOM05, Proceedings of IEEE Global Tele-
com.Conference.
Ekici, O. and Yongacoglu, A. (2004) Application of Noisy
Independent Component Analysis for CDMA Signal
Separation. Proceedings of IEEE-DSP Workshop.
Hyvarinen, A. (1999) Fast and robust fixed-point algorithms
for independent component analysis IEEE Transac-
tions on Neural Networks.
Hamza, A. and Chitroub, S. (2009) Independent Compo-
nent Analysis in IDMA systems. Proceedings of IEEE
(NEWCAS-TAISA’09).
Huovinen, T. and Shahed, A. (2007) Blind Diversity Recep-
tion and Interference Cancellation Using ICA. Pro-
ceedings of ICASSP.
Davies, M. E. (2004) Identifiability Issues in Noisy ICA.
Proceedings of IEEE Signal..
BLIND DETECTION IN IDMA SYSTEMS
141
