
QUANTUM SECURE DIRECT COMMUNICATION USING
ENTANGLEMENT AND SUPER DENSE CODING
Ola M. Hegazy, Ayman M. Bahaa Eldin and Yasser H. Dakroury
Computer and Systems Eng. Department, Ain Shams University, Cairo, Egypt
Keywords: Entanglement, Quantum secure direct communication (QSDC), Super dense coding.
Abstract: This paper introduces a new quantum protocol for secure direct communication. This protocol is based on
Entanglement and Super-Dense coding. In this paper we present some basic definitions of entanglement in
quantum mechanics, present how to use the maximally entangled states known as Bell States, and super
dense coding technique to achieve secure direct message communication. Finally, we will apply some error
models that could affect the transmission of the quantum data on the quantum channels, and how to treat
these errors and acquire a safe transmission of the data.
1 INTRODUCTION
The aim of cryptography is to ensure that a secret
message is transmitted between two users in a way
that any eavesdropper cannot read it. Since classical
cryptography relies on difficulty and infeasibility of
computation to find the plain text, it is losing
security more and more as computational power is
increasing by technical innovations. In classical
cryptography, it is generally accepted that one-time
pad, which utilizes a previously shared secret key to
encrypt the message transmitted in the public
channel, is the only cryptosystem with proved
security. Fortunately, quantum key distribution
(QKD) (Bennett, 1984), the approach using quantum
mechanics principles for distribution of secret key,
can overcome this obstacle skillfully. Since both
(QKD) and one-time pad have been proved secure
(Lee, 2005), the cryptosystem of “QKD & one-time
pad” is a perfect one when the security is concerned.
Previously proposed QKDPs are the theoretical
design (Bennett, 1984), security proof (Massey,
1988), and physical implementation (Bennett, 1992).
Quantum secure direct communication (QSDC)
(Boström, 2002, Deng, 2008) is another branch of
quantum cryptography. Different from QKD, QSDC
allows the sender to transmit directly the secret
message (not a random key) to the receiver in a
deterministic and secure manner. If it is designed
carefully, a QSDC protocol can also attain
unconditional security (Deng, 2003).
The main objective of our research is to
introduce a new protocol that guarantees more
security of the transmission than the QKD and also
saves more time, cost and gives more efficiency for
the transmission, as it is using the super dense
coding technique that transmit two classical bits by
sending one quantum bit. In our protocol of the
quantum secure direct communication we use the
maximally entangled Bell states to encode the
message bits on the basis of the super dense coding
theorem, and then transmitting them on two
quantum channels to the other side with less
probability of the eavesdropping, and with no need
for a pre-shared key that in turn needs many rounds
to distribute, and also a public discussions to verify
the correctness of the key.
2 BACKGROUND
The most important and interesting characteristics of
the quantum mechanics is that the quantum state
could not be measured without disturbing and
changing the state of the particles (photons). So the
use of quantum phenomenon will help in
overcoming one of the most important
eavesdropping problems; that is measuring the
information without being discovered, so any
attempt of Eve to measure the data during
transmission will be known to Alice and Bob.
175
M. Hegazy O., M. Bahaa Eldin A. and H. Dakroury Y. (2009).
QUANTUM SECURE DIRECT COMMUNICATION USING ENTANGLEMENT AND SUPER DENSE CODING.
In Proceedings of the International Conference on Security and Cryptography, pages 175-181
DOI: 10.5220/0002186501750181
Copyright
c
SciTePress
Also, another interesting feature of the quantum
phenomenon is that any arbitrary quantum state
cannot be cloned or copied and that is known as No-
Cloning theorem (Nielsen, 2000). Of course, this
will help in overcoming another eavesdropping
problem which is copying the transmitted signal, so
Eve cannot take a copy of the message during
transmission. These two characteristics of the
quantum phenomenon make it a stronger mechanism
in securing the transmission path more than the
classical transmission.
Quantum mechanics violates everyday intuition
not only because the measured data can only be
predicted probabilistically but also because of a
quantum specific correlation called entanglement.
Entanglement can be used to cause non local
phenomenon. States possessing such correlations are
called entangled states. Among these states, the
states with the highest degree of entanglement
(correlation) are called maximally entangled states
or EPR states, as historically, the idea of a non local
effect due to entanglement was pointed out by
Einstein, Podolsky, and Rosen (Hayashi, 2006).
The pure quantum nature of entanglement is the
property of non-local correlations between widely
separated particles which have interacted in the past.
To make particles entangled, it is necessary for them
to interact at a point. In other words, the non-local
property of entanglement is arisen from the local
property of interaction (Lee, 2005).
3 THE SUPER DENSE CODING
PROCEDURE
The super dense coding is a simple example of the
application of quantum entanglement
communication. The goal of this procedure is to
transmit two classical bits by sending one quantum
bit (qubit), so increasing the efficiency of the
transmission.
Before starting the transmission, it is assumed
that a third party has generated an entangled state,
one of the Bell entangled state, for example
()
1100
2
1
+=
+
φ
, and then sends one of the
two pairs of the entangled qubits to the sender
‘Alice’ and the other to the receiver ‘Bob’.
When starting the transmission, Alice could send
the single qubit in her possession to Bob after
operating on it in such a way to encode two bits of
the classical information to Bob.
As there are four possible values of the two
classical bits Alice wishes to send to Bob: 00, 01, 10
and 11, then if Alice wants to send the two bits ‘00’,
she does nothing to her qubit just simply send it as it
is. If she wants to send ‘10’, she applies the phase
flip Z to her qubit. If she wants to send ‘01’, she
applies the quantum NOT gate X, to her qubit. If she
wants to send ‘11’, she applies the iY gate to her
qubit. The four quantum gates that are used here are:
the Pauli matrices I, Z, X, iY, and combinations of
them are applied as the U unitary operation that
Alice performs on her half of the EPR pairs
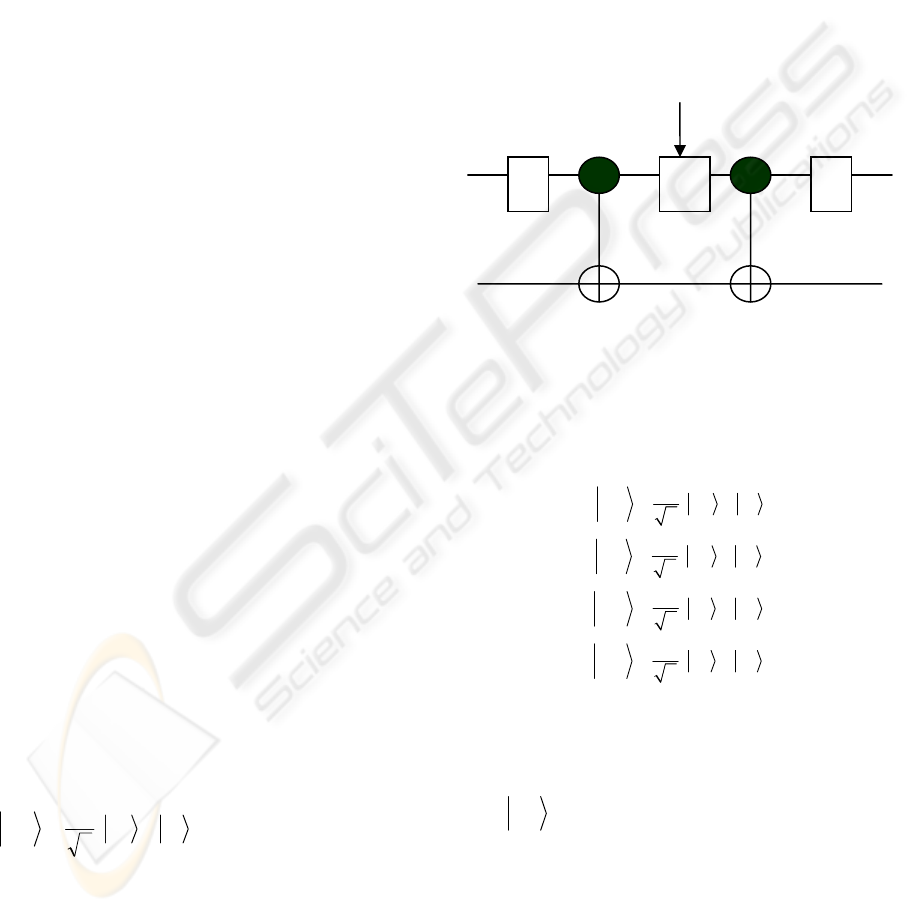
according to the diagram in fig.(1) (Benenti, 2004).
Message classical bits
Figure 1: A quantum circuit implementing the super dense
coding.
The use of these four different transformations
results in the four states of Bell states as in the
following equations:
()
1
00 00 11
2
ϕ
+
→= +
(1)
()
1
10 00 11
2
ϕ
−
→= −
(2)
()
1
01 01 10
2
ψ
+
→= +
(3)
()
1
11 01 10
2
ψ
−
→= −
(4)
Of course, the kind of the transformation of the
operator
U will change according to the state that is
generated in the first half of the circuit before the
U
operator box, as we took an example of the
state
+
φ
, but it could be any other Bell state. In all
cases the generated state after the operator
U (the
encoding circuit) will be also any other one of the
Bell states but in different order according to the
classical bits that will be sent.
H U H
SECRYPT 2009 - International Conference on Security and Cryptography
176
4 THE NEW PROPOSED QSDC
PROTOCOL USING
SUPER-DENSE CODING
Our new protocol of the quantum secure direct
communication uses the maximally entangled Bell
states to encode the message bits using super dense
coding that was mentioned above, and then transmit
them on two quantum channels to the other side with
less probability of the eavesdropping and more
efficiency by sending two classical bits using one
quantum bit (qubit).
4.1 Basic Idea of the Protocol
Using the idea of the super dense coding theorem,
the message bits are input to the operator U selector,
then according to their value (one of the four
possible values 00, 01, 10 or 11), and also according
to the state of the entangled pair that will be
generated randomly (one of the Bell states) due to
the inputs of the quantum selector
),(
01
ii
, the
inputs to the
U Pauli operator will drive it to perform
one of the four unitary operations mentioned above,
the
U Pauli operators could be I, X, iY or Z and their
matrix representations are as follows:
⎥
⎦
⎤
⎢
⎣
⎡
−
=
⎥
⎦
⎤
⎢
⎣
⎡
−
=
⎥
⎦
⎤
⎢
⎣
⎡
=
⎥
⎦
⎤
⎢
⎣
⎡
=
10
01
,
0
0
,
01
10
,
10
01
Z
i
i
YXI
These steps are applied using the block diagram of
figure 2.
4.2 Assumptions of the Protocol
Alice will be the one who will produce the EPR
pairs (Bell states carriers) in her side not a third
party. Then she keeps one half for herself (and apply
the encoding of operator U on it) and sends the other
half to Bob.
The Bell states that will be generated by Alice
will be chosen on random basis using a random
generator, so we can get one of the different four
maximally entangled Bell states,
−
−++
ψφψφ
and,,, .
4.3 Steps of the Protocol
1) Alice inputs the message bits (M), 2-bits by 2-
bits, as one input to select the U operator as
mentioned above with the other input that is
one of the Bell states which is randomly
generated.
2) Then after applying the unitary operator on the
qubit of Alice, the result that is the output of
the Alice encoding circuit
o
ψ
will be sent
on one of the public quantum channel and on a
spatially separated quantum channel the Bob’s
qubit (the half of Bell state).
3) So according to the different generated Bell
states we will have the function matrix of U
operator according to the following table and
analysis:
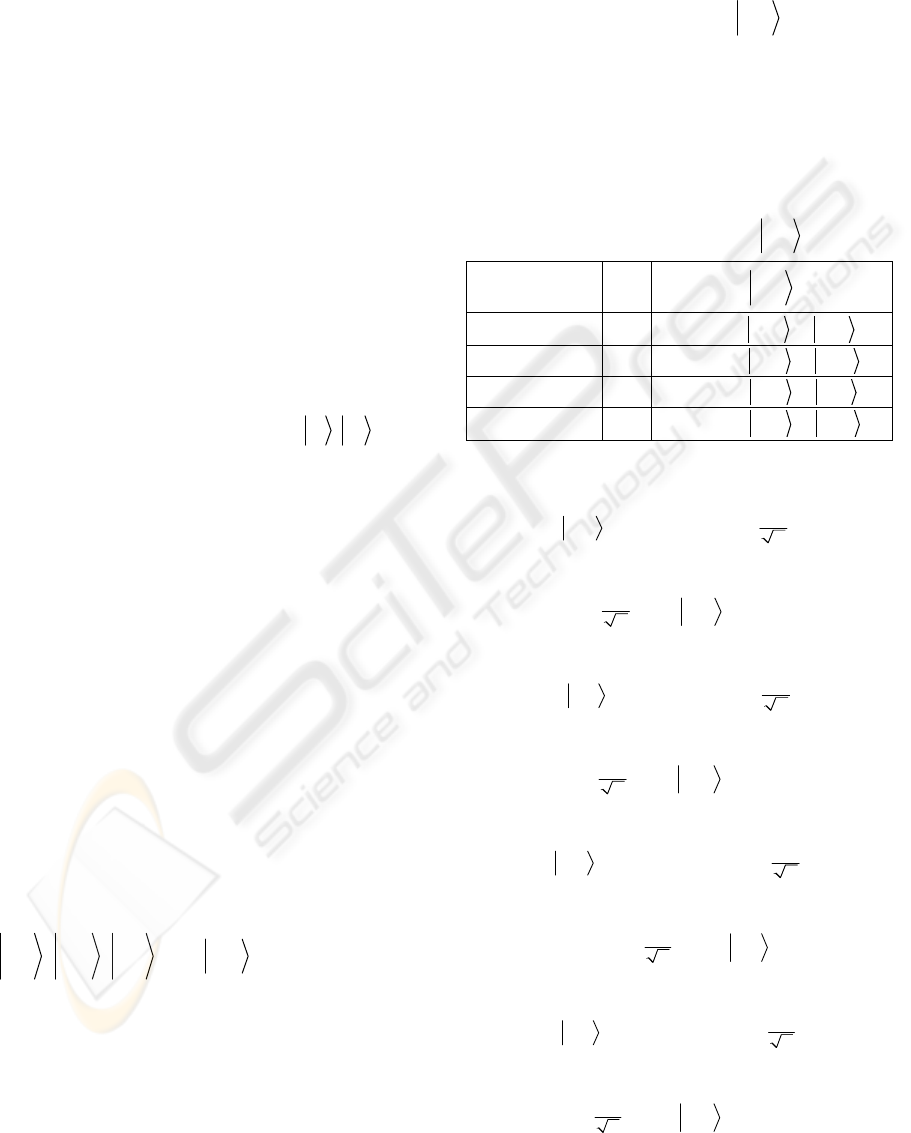
a)
In case of the carrier Bell state
+
φ
:
2-bit element
U
o
ψ
00 I
(
)
+
=
+
⊗
φ
φ
II
01 X
(
)
+
=
+
⊗
ψ
φ
IX
10 Z
(
)
−
=
+
⊗
φ
φ
IZ
11 iY
(
)
−
=
+
⊗
ψ
φ
IiY
According to the following analysis:
()
1000 1
0100 0
1
0010 0
2
0001 1
1
0
1
0
2
1
II
ϕ
ϕ
⎡
⎤⎡⎤
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎣
⎦⎣⎦
⎡⎤
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎣⎦
+
⊗= •
+
==
(5)
()
0010 1
0001 0
1
1000 0
2
0100 1
0
1
1
1
2
0
XI
ϕ
ψ
+
⎡
⎤⎡⎤
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎣
⎦⎣⎦
⎡⎤
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎣⎦
⊗= •
+
==
(6)
()
10 0 0 1
01 0 0 0
1
00 1 0 0
2
00 0 1 1
ZI
ϕ
⎡
⎤⎡⎤
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎣
⎦⎣⎦
+
⊗= •
−
−
1
0
1
02
1
ϕ
⎡⎤
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎣⎦
−
==
−
(7)
()
0010 1
0001 0
1
1000 0
2
0100 1
0
1
1
12
0
iY I
ϕ
ψ
⎡
⎤⎡⎤
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎢
⎥⎢⎥
⎣
⎦⎣⎦
⎡⎤
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎣⎦
+
⊗= •
−
−
−
==
−
(8)
QUANTUM SECURE DIRECT COMMUNICATION USING ENTANGLEMENT AND SUPER DENSE CODING
177
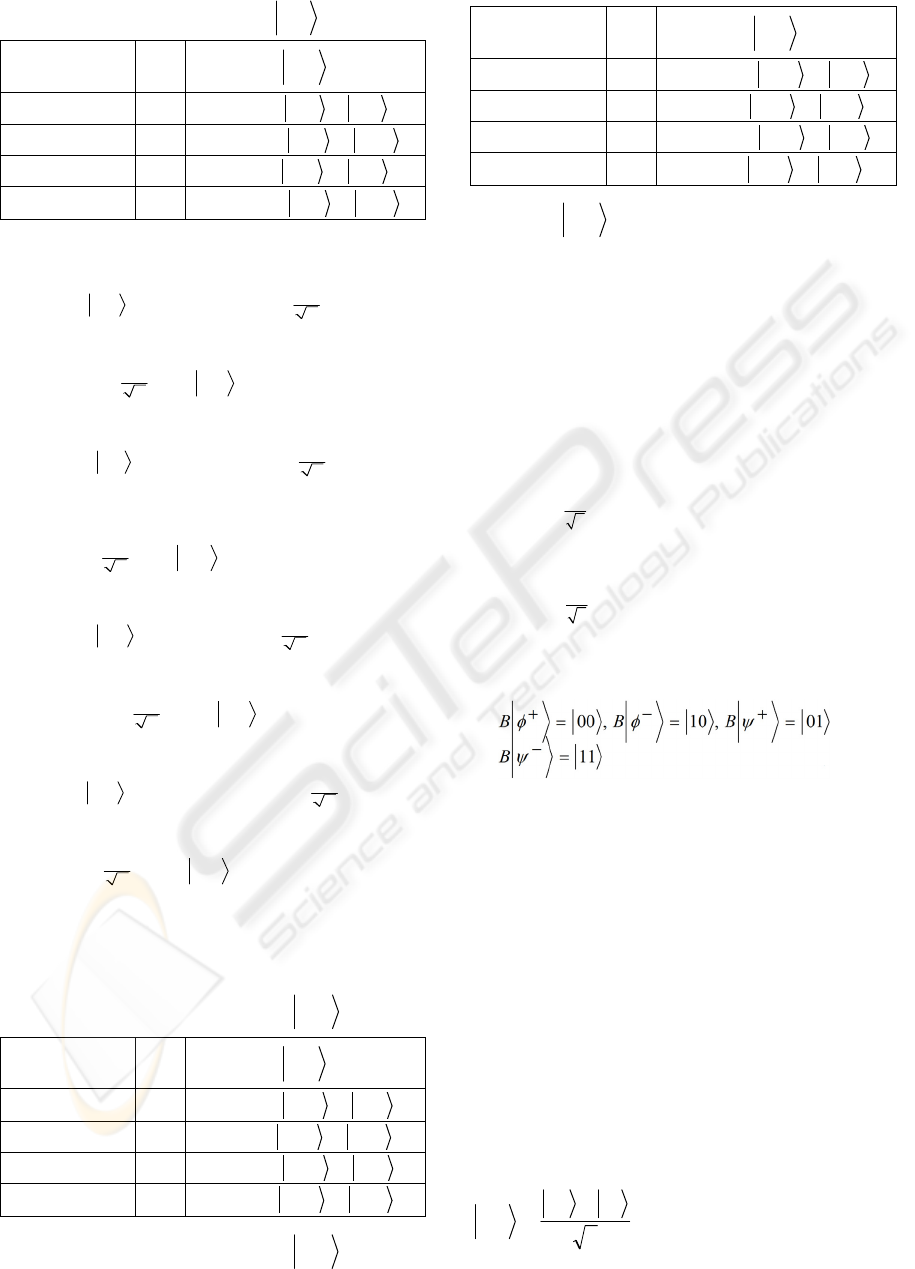
b)
In case of the carrier Bell state
−
φ
:
2-bit element
U
o
ψ
00 Z
(
)
+
=
−
⊗
φ
φ
IZ
01 XZ
(
)
+
=
−
⊗
ψ
φ
IXZ
10 I
(
)
−
=
−
⊗
φ
φ
II
11 iYZ
(
)
−
=
−
⊗
ψ
φ
IiYZ
According to the following analysis:
()
10 0 0 1
01 0 0 0
1
00 1 0 0
2
00 0 1 1
1
0
1
0
2
1
ZI
ϕ
ϕ
⎡⎤⎡⎤
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎣⎦⎣⎦
⎡⎤
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎣⎦
−
⊗= •
−
−−
+
==
(9)
()
00 1 0 1
00 0 1 0
1
10 0 0 0
2
01 0 0 1
0
1
1
1
2
0
XZ I
ϕ
ψ
−
⎡⎤⎡⎤
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎣⎦⎣⎦
⎡⎤
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎣⎦
−
−
⊗= •
−
+
==
(10)
()
1000 1
0100 0
1
0010 0
2
0001 1
1
0
1
0
2
1
II
ϕ
ϕ
⎡⎤⎡⎤
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎣⎦⎣⎦
⎡⎤
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎣⎦
−
⊗= •
−
−
==
−
(11)
()
00 10 1
000 1 0
1
1000 0
2
0100 1
0
1
1
1
2
0
iYZ I
ϕ
ψ
⎡⎤⎡⎤
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎢⎥⎢⎥
⎣⎦⎣⎦
⎡⎤
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎢⎥
⎣⎦
−
−
−
⊗= •
−
−−
−
==
−
(12)
And similar to the same analyses the following
carriers will take the following operators to get the
same results.
c)
In case of the carrier Bell state
+
ψ
:
2-bit element
U
o
ψ
00 X
(
)
+
=
+
⊗
φ
ψ
IX
01 I
(
)
+
=
+
⊗
ψ
ψ
II
10 iY
(
)
−
=
+
⊗
φ
ψ
IiY
11 Z
(
)
−
=
+
⊗
ψ
ψ
IZ
d) In case of the carrier Bell state
−
ψ
:
2-bit element
U
o
ψ
00 XZ
(
)
+
=
−
⊗
φ
ψ
IXZ
01 Z
(
)
+
=
−
⊗
ψ
ψ
IZ
10 iYZ
(
)
−
=
−
⊗
φ
ψ
IiYZ
11 I
(
)
−
=
−
⊗
ψ
ψ
II
4) After
o
ψ
reached Bob, he starts to apply the
appropriate unitary operations on the Bell
states, measuring the two qubits and obtaining
the 2-bit message element.
5) Bob performs the reverse operation of the
encoding circuit, (decoding circuit) as:
()
(
)
()
1
CNOT H I H I CNOT
−
⊗=⊗
(13)
That is having the matrix representation:
10 1 0 1000
01 0 1 0100
1
10 1 0 0001
2
01 0 1 0010
10 0 1
01 1 0
1
10 0 1
2
01 1 0
B
⎡
⎤⎡ ⎤
⎢
⎥⎢ ⎥
⎢
⎥⎢ ⎥
=•
⎢
⎥⎢ ⎥
−
⎢
⎥⎢ ⎥
−
⎣
⎦⎣ ⎦
⎡⎤
⎢⎥
⎢⎥
=
⎢⎥
−
⎢⎥
−
⎣⎦
(14)
Therefore:
(15)
4.4 Comments
• In the implementation of the above
protocol, it is essential that the two
quantum channels used should be spatially
separated all the way from Alice to Bob.
This prevents an eavesdropper from
accessing the two channels in one location
and using the same procedure that should
be used by Bob to get the original message.
• The following analysis illustrates the
effectiveness of the protocol in
counteracting the efforts of the
eavesdropper.
All the Bell states used are pure maximally
entangled states since if we consider one of them;
2
1100 +
=
+
φ
, then its density matrix ρ is:
SECRYPT 2009 - International Conference on Security and Cryptography
178
2
00 00 11 00 00 11 11 11
1001
0000
1
0000
2
1001
ρ
+++
=
=
(16)
Since Tr(ρ
2
) =1, then this is a pure state.
The partial trace over the first qubit is:
ρ
1
= I/2
Since Tr((
ρ
1
)
2
) = ½ which is less than 1, then the
first qubit is in a mixed state. Similarly, for the
second qubit the same conclusion will be held. And
as long as there is no unique mixed state for each
separate quantum channel, then let assume each of
them will be represented by one of these, called
privileged mixed state. This could be obtained from
the eigenvalues and eigenvectors of
ρ
1
or ρ
2
. The
eigenvalues are equal to ½ and the eigenvectors
are
10 and
, so if we choose this specific case as
the mixed state, then
11
12
00 11
22
or
ρρ
=+
(17)
If the eavesdropper Eve has access to one quantum
channel only, and makes a measurement she gets 0
or 1 with probability ½ for each case.
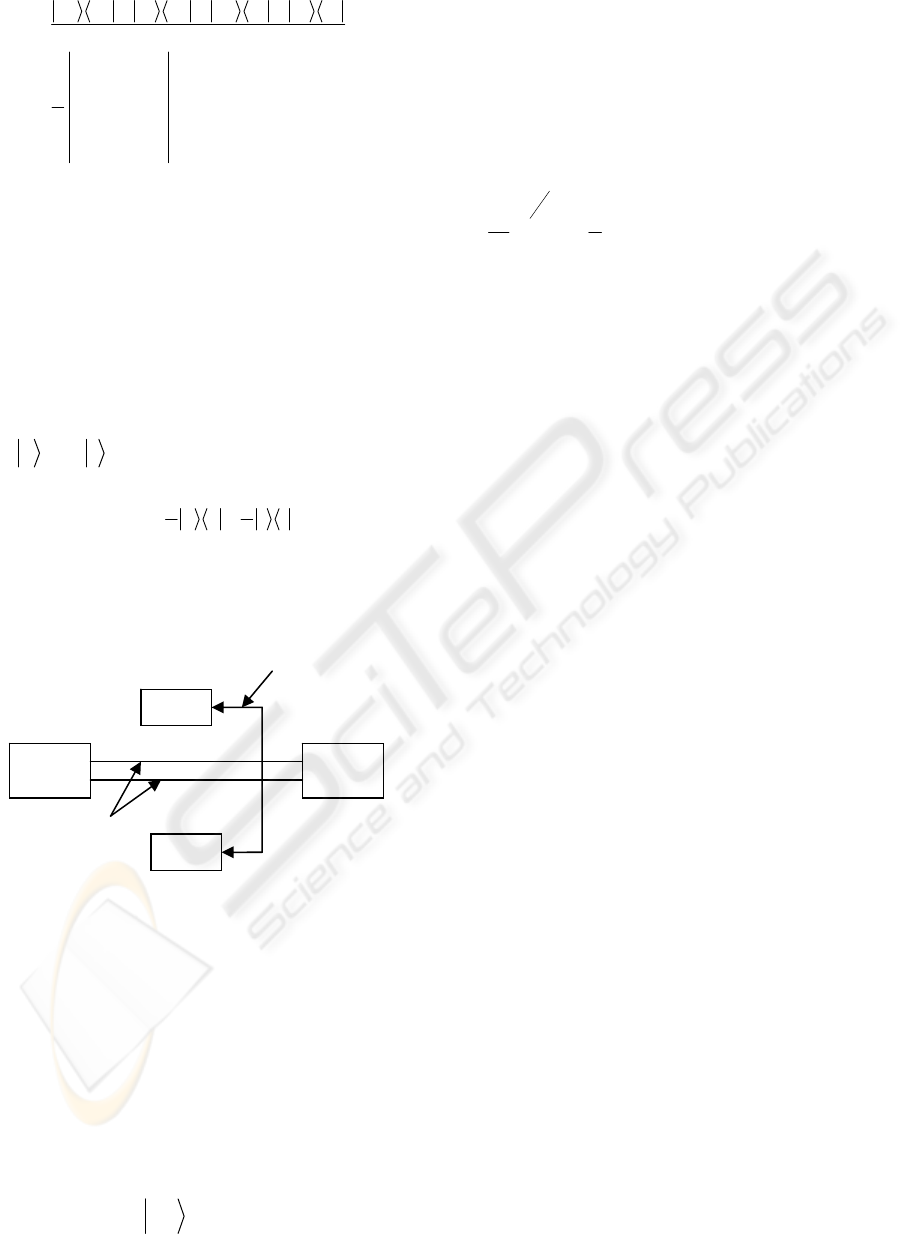
Figure 2: Synchronized attack with a classical link.
Let us, therefore assume that Eve can use the
following attack which is rather difficult to
implement. We call this attack “Synchronized attack
together with a classical communication link”, fig
(3).
If Eve measure the qubit on quantum channel 1 she
gets 0 with a probability ½, and assuming that a
synchronized measurement is performed on quantum
channel 2 she gets 0 with a probability ½. Therefore,
for the Bell state
+
φ
, she gets 00 on the two
quantum channels with probability ¼. Assuming
that the Bell states used are uniformly distributed
then each will have a probability of ¼. Then for
message bits 00 Eve will get this result with
probability 1/16. Similarly, for the other three
combinations Eve will get the same results with the
same probability. So if the message has length
N,
then the probability that Eve get the correct result
is
N
N
⎟
⎠
⎞
⎜
⎝
⎛
⎟
⎠
⎞
⎜
⎝
⎛
=
4
1
2
16
1
.
5 EXAMPLES OF QUANTUM
NOISE AND ITS EFFECT ON
THE QUANTUM CHANNEL
In this section we examine some examples of
quantum noise that could affect a quantum channel.
These models are important in understanding the
practical effects of the noise on quantum systems,
and how noise can be controlled by techniques such
as error-correction. Those models are bit flip; phase
flip and both together (bit flip and phase flip). Of-
course those models do not include all kinds of noise
that could affect the quantum channel, there are
others, but we chose these to analyze as they are
more likely to occur. In our protocol we have two
quantum channels, so the models of noise we
mentioned above will be applied on both channels at
random, i-e, we cannot know which model will
affect which channel at a time, therefore we will
study all different combinations of different models
on the two channels, and then will analyze the last
one in detail as it contains the greater combinations
of the two other kinds.
In the first model (bit flip); the first qubit of
Alice on the first channel after encoding the classical
bits, could be flipped with probability (
p), with the
second qubit transmitted correctly. The second case
is when the second qubit on the second channel, the
half qubit of Bob, could be flipped with probability
(p) where the first qubit transmitted correctly. The
third case, if both qubits on both channels are
flipped with probability
(p
2
).
In the second model (phase flip); also we have
three cases as above, i-e, (anyone of the qubits will
flip with probability
(p), where the second will not),
or the two qubits will flipped with probability
(p
2
).
In the third and last model (both bit and phase
flip); all different combinations could happen; for
example the first qubit could have a bit flip when the
Alice Bob
Eve
Eve
Two spatially
separated
quantum
channels
Classical communication lin
k
QUANTUM SECURE DIRECT COMMUNICATION USING ENTANGLEMENT AND SUPER DENSE CODING
179

second qubit has a phase flip; or vice versa, and each
of which will occur with probability
(p
2
), etc. so we
will introduce the analysis of this one as the most
general one. Anyway, as we are using maximally
entangled Bell states, all the models of quantum
noise will just change the transmitted state to
another one of the Bell states also, which makes it
more confusing and harder to discover.
To protect the quantum state from the effect of
the noise we would like to develop quantum error-
correcting codes based upon similar idea of the
classical error correcting codes. This idea is the
repetition code, as that used by shor code (Nielsen,
2000).
In the following analysis we will consider the Bell
state
2
1100 +
=
+
φ
as an example since the
other cases could be analyzed in a similar manner.
1.
if the 1
st
bit has both bit flips and phase-
flips and the 2
nd
bit remains as it is with
10 01
2
ϕψ
−−
++
⇒=−
(18)
probability (
p
2
) so
2.
if the 2nd bit has both bit flips and phase-
flips and the 1st bit remains as it is with
probability (p2) so
01 10
2
ϕψ
−−
++
⇒=−
(19)
3. if both bits have bit flips with only one of
them has phase-flips with probability (p3)
so
11 00
2
ϕ
ϕ
−−
++
⇒=−
(20)
4.
if both bits have both bit flips and phase-
flips and the with probability (p4) so
11 00
2
ϕ
ϕ
+
++
⇒=
(21)
5.
if the 1st bit has bit flip and the 2nd bit has
phase flip, with probability (p2) so
10 01
2
ϕψ
−
+−
⇒=−
(22)
6.
if the 1st bit has phase flip and the 2nd bit
has bit flip, with probability (p2) so
01 10
2
ϕψ
−
+−
⇒=
(23)
Note that the (–) sign in all the above relations
introduced a global phase shift with no observable
effect and could be dropped. So errors are
introduced in 4 out of 6 cases above with appropriate
probabilities. An error-correcting code scheme, like
Steane code could then be used (Nielsen, 2000).
6 CONCLUSIONS
This paper introduced a new protocol for direct
quantum communication making use of pure
maximally entangled Bell states. Also, for efficiency
purposes super dense coding is used, which is also
based on entanglement, to double the transmission
speed by sending two classical bits over one
quantum channel. This protocol uses one step or one
pass to end the message in a secure manner. It is
essential that the two quantum channels used in the
implementation be spatially separated all the way
from Alice to Bob. To illustrate the security of the
protocol, a hypothesized attack procedure used by
Eve was considered that is called “synchronized
attack together with a classical communication”.
Analysis was given to indicate that the probability of
Eve getting the message is extremely small. Also,
this type of attack is very difficult to implement. The
effect of some quantum noise models was also
considered, indicating the errors introduced. In this
case some form of error-correcting procedure should
be used.
7 FUTURE WORK
There are many aspects that could be considered to
complete the above study. A few of them will be
presented here:
1.
Since the protocol is based on using pure
maximally entangled Bell states, then it is
essential to study procedure that could be used to
get such states either from pure non entangled
states, a process called concentration, or
distillation and purification for mixed states.
2.
It is essential to study entanglement degradation
which depends on the length of the quantum
channel. In particular,study of what is called
Entanglement Sudden Death (ESD) phenomenon,
which should be given appropriate attention,
since it reduced sharply the distance over which
entanglement is effective.
3.
Other quantum noise effect should also be given
due attention such as: depolarizing channel,
amplitude damping, and phase damping.
SECRYPT 2009 - International Conference on Security and Cryptography
180
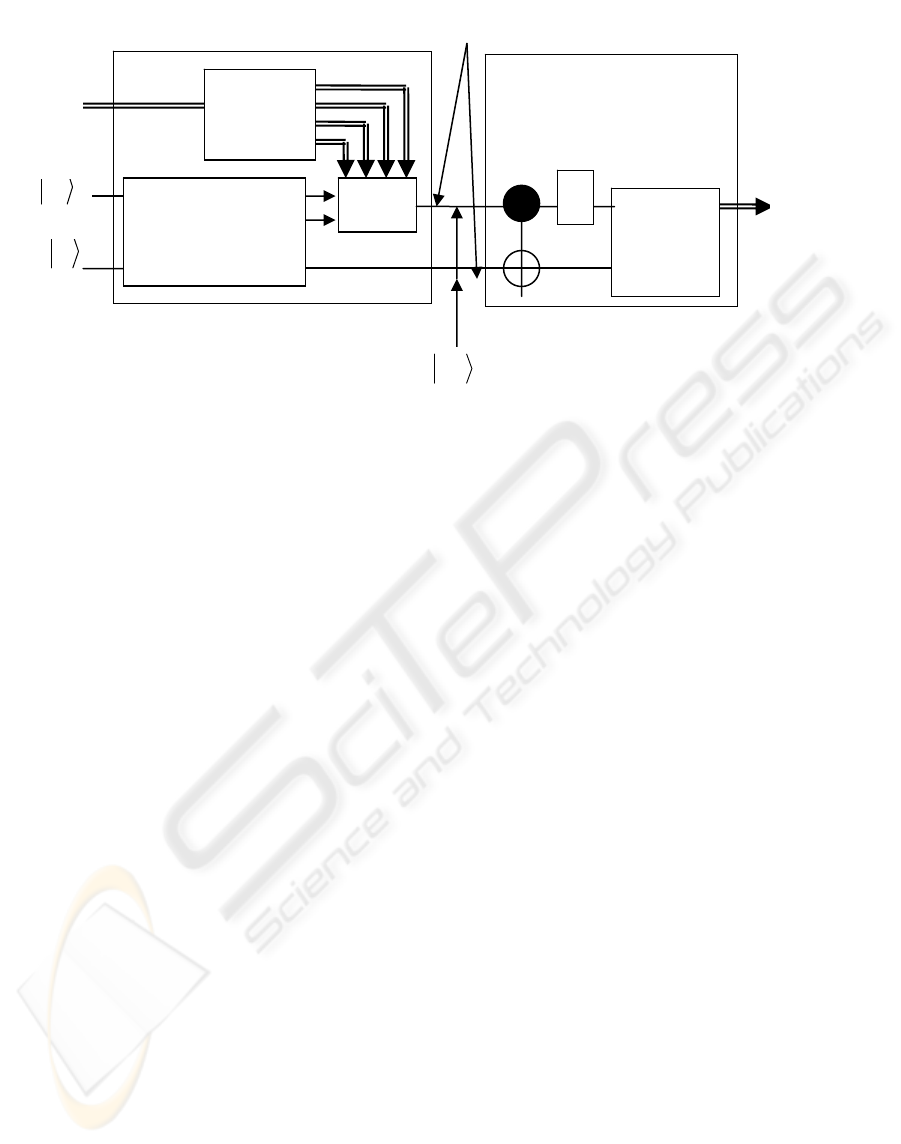
Figure 3: The block diagram of the coding and decoding circuit of the proposed protocol.
REFERENCES
Benenti, G., Casati, G., Strini, G., 2004 . “Princples of
Quantum Computation and Information”, Volume I:
Basic Concepts, World Scientific Publishing Co.
Bennett, C., Bessette, F., Brassard, G., Salvail, L. and
Smolin, J., 1992. “Experimental Quantum
Cryptography”, J. Cryptology, 5 (1992) 3.
Bennett, C.H. and Brassard, G., 1984. “Quantum
Cryptography: Public Key Distribution and Coin
Tossing”. In:
Proceedings of IEEE International
Conference on Computers, Systems and Signal
Processing, p. 175.
Boström, K., Felbinger, T., 2002. “Eavesdropping on the
Two-Way Quantum Communication Protocols with
Invisible Photons”,
Phys. Rev. Lett.89 (2002) 187902.
Deng, F.G., Li, X.H., Li, C.Y., et al., 2008. “Quantum
Secure Direct Communication Network with Einstein-
Podolsky-Rosen Pairs”,
quant-ph/0508015 (2008).
Deng, F.G., Long, G.L., Liu, X.S. 2003. “Two-Step
Quantum Direct Communication Protocol Using the
Einstein-Podolsky-Rosen Pair Block”,
Phys. Rev. A 68
(2003) 042317.
Hayashi, M., 2006. “Quantum Information, An
Introduction”, Springer.
Lee, H. at el, 2005. “Entanglement Generates
Entanglement: Entanglement transfer by interaction”,
Physics letters A 338 (2005), 192-196.
Massey, J.L., 1988. “An introduction to contemporary
Cryptology”. In:
Proc. IEEE 76 (1988) 533.
Nielsen, M.A., Chuang, I.L., 2000. “Quantum
computation and quantum information”, Cambridge
University press, Cambridge.
Two spatially separated channels
U
Decoder
circuit
H
M
M
1
i
Operator
selector
Uniformly
Random Bell state
generator
o
ψ
o
i
QUANTUM SECURE DIRECT COMMUNICATION USING ENTANGLEMENT AND SUPER DENSE CODING
181
