
ANONYMOUS BUYER-SELLER WATERMARKING PROTOCOL
W
ITH ADDITIVE HOMOMORPHISM
Mina Deng, Li Weng
IBBT-COSIC, K. U. Leuven, ESAT/SCD, Kasteelpark Arenberg 10, bus 2446, B-3001 Leuven-Heverlee, Belgium
Bart Preneel
IBBT-COSIC, K. U. Leuven, ESAT/SCD, Kasteelpark Arenberg 10, bus 2446, B-3001 Leuven-Heverlee, Belgium
Keywords:
Security, Watermarking protocol, e-Commerce, Cryptography.
Abstract:
Buyer-seller watermarking protocols integrate multimedia watermarking and fingerprinting with cryptogra-
phy, for copyright protection, piracy tracing, and privacy protection. We propose an efficient buyer-seller
watermarking protocol based on dynamic group signatures and additive homomorphism, to provide all the
required security properties, namely traceability, anonymity, unlinkability, dispute resolution, non-framing,
and non-repudiation. Another distinct feature is the improvement of the protocol’s utility, such that the double
watermark insertion mechanism is avoided; the final quality of the distributed content is improved; the com-
munication expansion ratio and computation complexity are reduced, comparing with conventional schemes.
1 INTRODUCTION
Today’s information technology permits perfect du-
plication and cheap distribution for digital works.
Copyright protection has become an important issue.
In the realm of security, encryption and digital water-
marking are recognized as promising techniques for
copyright protection. Encryption is used to provide
confidentiality. The limitation is that once the con-
tent is decrypted, it doesn’tpreventillegal replications
by an authorized user. Digital watermarking, com-
plementing encryption, provides provable copyright
ownership by imperceptibly embedding the seller’s
information in a digital content. Similarly, finger-
printing is used to identify copyright violators by em-
bedding the buyer’s information in the digital content.
The fingerprinting literature can be categorized as:
fingerprinting for generic data, such as c-secure code
by Boneh et al. (Boneh and Shaw, 1995), fingerprint-
ing for multimedia data (Wang et al., 2005; Trappe
et al., 2003; Liu et al., 2005), and fingerprinting pro-
tocols, such as those base on secure two-party compu-
tations (Pittzmann and Schunter, 1996; Pfitzmann and
Waidner, 1997) or coin-based constructions (Pfitz-
mann and Sadeghi, 1999; Pfitzmann and Sadeghi,
2000; Camenisch, 2000). The shortcoming of these
fingerprinting schemes is implementation inefficiency
(Ju et al., 2002). On the other hand, the literature can
also be categorized as: symmetric schemes, asymmet-
ric schemes, and anonymous schemes. In symmetric
schemes (Blakley et al., 1985; Boneh and Shaw, 1995;
Cox et al., 1997), both the seller and the buyer know
the watermark and the watermarked content. As a
consequence, it is possible for a malicious seller to
frame an innocent buyer, or an accused buyer to re-
pudiate the guilt. This customer’s rights problem in
symmetric schemes was first pointed out by Qiao and
Nahrstedt (Qiao and Nahrstedt, 1998). The problem
can be solved by asymmetric schemes (Pittzmann and
Schunter, 1996; Pfitzmann and Waidner, 1997; Biehl
and Meyer, 1997), where only the buyer knows the fi-
nal watermarked content, and hence the seller cannot
fabricate piracy. To provide the buyer’s anonymity,
anonymous schemes (Pfitzmann and Sadeghi, 1999;
Pfitzmann and Sadeghi, 2000) further use a regis-
tration service to eliminate the need of exposing the
buyer’s identity to the seller.
A buyer-seller watermarking protocol combines
encryption, digital watermarking and fingerprinting,
to ensure copyrights protection, privacy, and security
for both the buyer and the seller simultaneously. The
following security properties should be provided:
Traceability: A copyright violator should be able to
be traced and identified.
300
Deng M., Weng L. and Preneel B. (2008).
ANONYMOUS BUYER-SELLER WATERMARKING PROTOCOL WITH ADDITIVE HOMOMORPHISM.
In Proceedings of the International Conference on Signal Processing and Multimedia Applications, pages 300-307
DOI: 10.5220/0001934303000307
Copyright
c
SciTePress

Non-framing: N
obody can accuse an honest buyer.
Non-repudiation: A guilty buyer cannot deny his re-
sponsibility for a copyright violation caused by him.
Dispute resolution: The copyright violator should be
identified and adjudicated without him revealing his
private information, e.g. private keys or watermark.
Anonymity: A buyer’s identity is undisclosed until
he is judged to be guilty.
Unlinkability: Nobody can determine whether two
watermarked contents are purchased by the same
buyer or not.
The first known asymmetric buyer-seller water-
marking protocol was introduced by Memon and
Wong (Memon and Wong, 2001) by applying pri-
vacy homomorphic cryptosystems, and it was ex-
tended by Ju et al. (Ju et al., 2002). Since the
introduction of the concept, several alternative de-
signs have been proposed (Jae-Gwi Choi, 2003; Goi
et al., 2004; Lei et al., 2004; Zhang et al., 2006;
Ibrahim et al., 2007). Choi et al. (Jae-Gwi Choi,
2003) pointed out the conspiracy problem in (Memon
and Wong, 2001; Ju et al., 2002), where a malicious
seller can collude with an untrustworthy third party to
fabricate piracy to frame an innocent buyer. Goi et
al. (Goi et al., 2004) found the conspiracy problem
couldn’t be solved through commutative cryptosys-
tems in (Jae-Gwi Choi, 2003). Lei et al. (Lei et al.,
2004) addressed the unbinding problem in (Memon
and Wong, 2001; Ju et al., 2002; Jae-Gwi Choi, 2003;
Goi et al., 2004) and provided a mechanism to bind
a specific transaction of a digital content to a spe-
cific buyer, such that a malicious seller cannot trans-
plant the watermark embedded in a digital content to
another higher-priced content. Zhang et al. (Zhang
et al., 2006) presented a scheme, derived from (Lei
et al., 2004), where no trusted third party (TTP) is
required in the watermark generation phase and the
conspiracy problem is solved. Unfortunately, we find
the existence of dispute resolution problem: in (Zhang
et al., 2006), in order to resolve disputes the buyer
is required to cooperate and reveal his secret key or
his secret watermark to the judge or to the CA, which
is unrealistic in real-life applications. Ibrahim et al.
(Ibrahim et al., 2007) recently proposed a scheme
claiming that all the above problems has been solved.
In this paper, we propose a new anonymous buyer-
seller watermarking protocol. Different from prede-
cessors, our improvements are as follows:
Group Signature. Traceability, anonymity and un-
linkability properties are essentially provided by de-
ployment of group signature. We assume that a pub-
lic key infrastructure PKI is available, such that each
party has a public and private key pair certified by the
CA. The CA is trustworthy and maintains the link be-
tween the buyer’s private key and identity.
Support Multi-transactions. The buyer needs to
register at the CA once before transactions, and there
can be multiple transactions with the seller.
Avoid Double Watermark Insertion. Existing
schemes all require double watermark insertions, and
it has the drawback to cause a degradation of the fi-
nal quality of the distributed contents, thus end up
reducing their commercial value. When applied in-
dependently, the second watermark could confuse or
discredit the authority of the first watermark, thus act-
ing as an actual ”ambiguity attack” (Frattolillo, 2007).
We avoid it by designing a composite watermark,
which is composed of the buyer’s secret watermark,
the seller’s secret watermark, and a transaction index.
No Linear Watermark Limitation. The protocol is
not limited to linear or permutation tolerant water-
marks. As long as privacy homomorphism is pre-
served, any types of watermarking schemes can be
adopted.
The rest of the paper is organized as follows. A
model of anonymous buyer-seller watermarking pro-
tocol is defined in Sect. 2. The proposed protocol is
explained in Sect. 3, with an example illustrated in
Sect. 4. The protocol’s security is analyzed in Sect.
5. Sect. 6 provides a conclusion.
2 PROTOCOL MODEL
Let X
0
∈ {0,1}
∗
be the cover data, X be the set of
watermarked copies of X
0
, and k be a security param-
eter. An anonymous buyer-seller watermarking pro-
tocol involves four parties: a seller and the copyright
holder Alice A , a buyer Bob B , a certificate authority
CA that functions as a group manager, and a judge J
that adjudicates lawsuits against the infringement of
copyrights. It consists of three subprotocols.
Reg-BCA: The registration protocol consists of an
algorithm
Set-CA
and a protocol
Reg
.
Set-CA
is
a probabilistic key setup algorithm to generate the
CA’s public key gpk and private keys (ok, ik).
Reg
is
a probabilistic two-party protocol
(Reg-CA, Reg-B)
between the CA and B . Their common input are B ’s
identity B and gpk. The CA’s secret input is (ok,ik).
B ’s output is his group signature key gsk
B
. The CA
stores B ’s certificate cert
B
and identity B in a regis-
tration table as reg[B].
WK-BS: A two-party protocol
(WK-S,WK-B)
between
A and B . Their common input is gpk. A ’s secret
input are the cover data X
0
and a transaction number
φ, and A ’s output is a transaction record in Table
A
.
ANONYMOUS BUYER-SELLER WATERMARKING PROTOCOL WITH ADDITIVE HOMOMORPHISM
301

Table 1: Notations and abbreviations.
B Buyer’s identification information
X
0
Original content
X The set of watermarked content of
X
0
X
′
A watermarked content of X
0
, X
′
∈
X
Det
(X
0
,Y) Non-blind watermark extraction
ARG Transaction agreement
E
pk
i
(·) Encryption with the public key of i
D
sk
i
(·) Decryption with the private key of i
(pk
B
,sk
B
) B ’s verification and signing keys
(pk
∗
B
,sk
∗
B
) B ’s one-time anonymous key pair
sig
B
B ’s signature to pk
B
signed with
upk
B
cert
B
B ’s certificate from the issuer.
gsk
B
B ’s group signature key
reg[i] Registration table of group member
i
1
k
For k ∈ N, the string of k ones.
µ B ’s group signature to pk
∗
B
E
esc
, p f
sk
∗
B
B ’s key escrow cipher and its proof
W
A
Seller’s secret watermark
W
B
Buyer’s secret watermark
φ Index of seller’s transaction record
ε Empty string
B ’s secret input is B ’s group signature key gsk
B
, and
B ’s output is a watermarked copy X
′
∈ X.
Arb-SJCA: A three-party protocol (
Arb-S, Arb-J,
Arb-CA
) among A , J , and the CA. A and J ’s input are
a pirated copy Y ∈ X, the cover data X
0
, and a record
in Table
A
. The CA’s input are (gpk, ok,ik) and the list
of cert
B
’s in reg. The CA’s output is the identity id of
a buyer with a proof τ. J verifies τ and provides A the
id or an empty string ε in case of failure.
The registration protocol
Reg-BCA
is performed
once in the setup-phase by the CA for each new buyer.
The watermarking protocol
WK-BS
is executed multi-
ple times for multiple transactions between the buyer
and the seller. The arbitration protocol
Arb-SJCA
is
executed for dispute resolution.
3 PROPOSED SCHEME
In this section, we elaborate on the three subprotocols.
We assume the CA is trustworthy and consists of a
group key generator, an issuer for group member join-
ing, and an opener for group signature opening. Note
that the protocol’s security depends on the security of
the underlying watermarking and cryptographic prim-
itives. As a consequence, the watermarking scheme
employed is required to be collusion resistant. In par-
ticular, no colluded parties can remove or tamper the
watermarking scheme, and nobody is able to detect or
delete the embedded watermark from a content with-
out knowing the watermark. As an example, we em-
ploy Bellare et al.’s dynamic group signature (Bellare
et al., 2005), and Camenisch et al.s verifiable encryp-
tion scheme (Camenisch and Damg˚ard, 1998) for key
escrow of the buyers private key at the CA. Notations
are depicted in Table 1.
3.1 Registration Protocol
The registration protocol performed between the
buyer B and the CA is depicted in Fig.1. The CA
executes the group-key generation algorithm
GKg
to
produce the group public key gpk, the issuer key ik,
and the opener key ok. Then B begins with the user-
key generation algorithm
UKg
to obtain a key pair
(upk
B
,usk
B
). To join the group, B generates a key
pair (sk
B
, pk
B
), signs pk
B
with usk
B
resulting sig
B
,
and sends (pk
B
,sig
B
) to the issuer of the CA. If sig
B
is verified, the CA issues B a certificate cert
B
. Then
(pk
B
,sig
B
) are stored in a registration table reg[B],
and sig
B
can be used later by the opener to prove
opening claims. Otherwise, the issuer returns an
empty string ε and the protocol halts. Upon receiv-
ing cert
B
, B generates his private group signature key
gsk
B
from the tuple (B, pk
B
,sk
B
,cert
B
).
3.2 Watermark Generation and
Embedding Protocol
The watermarking protocol between the seller A and
the buyer B is depicted in Fig.2. A and B first ne-
gotiate an agreement ARG on rights and specifica-
tions of a digital content X
0
. After generating a one-
time key pair (pk
∗
B
,sk
∗
B
), B executes the group sign-
ing algorithm
GSig
to create a signature µ to pk
∗
B
, as
µ =
GSig
(gpk,gsk
B
, pk
∗
B
). Next, B computes an es-
crow cipher E
esc
= E
pk
RC
(sk
∗
B
), to recover sk
∗
B
from
the CA in case of disputes. The verifiable proof p f
sk
∗
B
assures A that E
esc
is valid without compromising
the secret key sk
∗
B
. B generate a secret watermark
W
B
and encrypts W
B
as ew
B
= E
pk
∗
B
(W
B
). B sends
(pk
∗
B
,µ, ARG, ew
B
, p f
sk
∗
B
,E
esc
) and a signature λ to A .
After A verifies B ’s group signature µ using gpk
with the group signature verification algorithm
GVf
,
she generates a secret watermark W
A
, and an index φ
to locate this transaction record in Table
A
. Let W
AB
=
W
A
+ W
B
, W = W
AB
+ φ2
n
. W consists of the n-bit
W
AB
and the ℓ-bit φ. W can be decomposed into ℓ + n
SIGMAP 2008 - International Conference on Signal Processing and Multimedia Applications
302

Certificate authority (CA) B
uyer (B )
1. group key generation (g
pk, ok, ik) ←
GKg
(1
k
)
SecureChannel
- 2
. user key generation (upk
B
,usk
B
) ←
UKg
(1
k
)
3. group joining
if Vf
(upk
B
, pk
B
,sig
B
) = 1,
then
pk
B
,sig
B
(p
k
B
,sk
B
) ← K
s
(1
k
), sig
B
←
Sig
usk
B
(pk
B
)
cert
B
←
Sig
ik
(B, pk
B
), reg[B] ← (pk
B
,sig
B
),
else
cert
B
← ε
cert
B
- g
sk
B
← (B, pk
B
,sk
B
,cert
B
)
Figure 1: The registration protocol
Reg-BRC.
performed between the buyer B and the certificate authority CA.
Seller (A ) Bu
yer (B )
ARG
- 1
. (pk
∗
B
,sk
∗
B
) ← K
B
(1
k
), µ =
GSig
(gpk, gsk
B
, pk
∗
B
), E
esc
= E
pk
RC
(sk
∗
B
),
Vf
(p f
sk
∗
B
,E
esc
)
2.
GVf
(gpk, (pk
∗
B
,µ)),
Vf
(λ, pk
∗
B
),
Vf
(p f
sk
∗
B
,E
esc
)
m,λ
g
enerate W
B
,ew
B
= E
pk
∗
B
(W
B
), m ← (pk
∗
B
,µ, ARG,ew
B
, pf
sk
∗
B
,E
esc
), λ =
Sig
sk
∗
B
(m)
generate W
A
,φ, W
A
B
← (W
A
,W
B
),W ← (W
AB
,φ)
ew = E
p
k
∗
B
(X
′
) = E
pk
∗
B
(X
0
⊕W), Table
A
← [φ, m,λ,W
A
]
E
pk
∗
B
(X
′
)
- 3
. get X
′
with sk
∗
B
Figure 2: The watermark generation and embedding protocol
WK-BS.
performed between the seller A and the buyer B .
binary numbers, with W
i
,W
AB
i
,φ
i
∈ {0,1}, satisfying:
W =
n+ℓ−1
∑
i=0
W
i
2
i
=
n−1
∑
i=0
W
AB
i
2
i
+
n+ℓ−1
∑
j=n
φ
j
2
j
(1)
W
AB
=
n−1
∑
i=0
W
AB
i
2
i
(2)
φ =
ℓ−1
∑
j=0
φ
j
2
j
(3)
A embeds the watermark in the encrypted domain,
with additive homomorphism, E (·) denotes E
pk
∗
B
(·):
E (W) = E (W
A
+W
B
+ φ2
n
)
= E (W
A
) · E (W
B
) · E (φ2
n
) (4)
E (X
′
) = E (X
0
) ⊗ E (W) = E (X
0
⊕W) (5)
Thereafter, A stores (φ,m,λ,W
A
) in Table
A
, and de-
livers E
pk
∗
B
(X
′
) to B . As a result, B obtains the water-
marked content X
′
by decryption D
sk
∗
B
(E
pk
∗
B
(X
′
)).
3.3 Identification and Arbitration
Protocol
The identification and arbitration protocol among the
seller A , the judge J , and the CA, is depicted in Fig.
3. Once a pirated copy Y of X
0
is found, A extracts
the watermark U from Y and retrieves the most sig-
nificant ℓ bits of U as the index φ
′
in order to search
the Table
A
. It is accomplished by choosing the value
φ from Table
A
that is most correlated with φ
′
. Then,
A provides the collected information to J .
If λ is verified with the provided key pk
∗
B
, J sends
the escrow cipher E
esc
to the CA. Otherwise, the pro-
tocol halts. Next, the CA decrypts E
esc
to recover
the suspected buyer’s private key sk
∗
B
= D
sk
RC
(E
esc
),
and sends E
pk
J
(sk
∗
B
) back to J . J recovers sk
∗
B
=
D
sk
J
(E
pk
J
(sk
∗
B
)),W
B
= D
sk
∗
B
(ew
B
), and calculatesW
AB
from W
A
and W
B
provided by A . Meanwhile, J ex-
tracts the watermark U
′
from the pirated copy Y and
retrieve the n least significant bits of U
′
as W
′
AB
. If
W
′
AB
and W
AB
match with a high correlation, the sus-
pected buyer is proven to be guilty. Otherwise, the
buyer is innocent. Note that until now, the buyer has
stayed anonymous. To recover the buyer’s identity, J
orders the opener of the CA to execute the group sig-
nature open algorithm
Open
, to retrieve the identity
B with a claim proof τ. J verifies B and τ with the
group signature judging algorithm
Judge
. If verified,
J adjudicates that the buyer with identity B is guilty.
Otherwise, the protocol halts.
4 SCHEME EXAMPLE
In this section, we provide an example of the pro-
posed protocol and employ the additive homomor-
phism of Damg˚ard-Jurik cryptosystem (Jurik, 2001)
and the watermarking scheme by Kuribayashi and
Tanaka (Kuribayashi and Tanaka, 2005). Note that
anti-collusion fingerprintings by Wu et al. (Wang
et al., 2005; Trappe et al., 2003; Liu et al., 2005) can
be applied for the coding of watermark values, in or-
der to prevent complete removal or tampering of the
watermarking by colluded parties. In this section, we
focus on the watermarking embedding and detection
scheme, but we will not explain anti-collusion finger-
prints further.
The probabilistic encryption function of
Damg˚ard-Jurik cryptosystem (Jurik, 2001) is
E : G → Z
∗
n
s+1
, with Z
∗
n
s+1
∼
=
G × H, G a cyclic group
of order n
s
, and H
∼
=
Z
∗
n
. Choose an RSA modulus
n = pq and s ∈ N. Choose λ = lcm(p − 1,q − 1);
g ∈ Z
∗
n
s+1
such that g = (1 + n)
j
x mod n
s+1
for
gcd( j,n) = 1 and x ∈ H; d mod n ∈ Z
∗
n
and d ≡ 0
ANONYMOUS BUYER-SELLER WATERMARKING PROTOCOL WITH ADDITIVE HOMOMORPHISM
303
Seller (A ) Judge (J ) Certificate authority (CA)
1. U ←
Det
(X
0
,Y), φ
′
← U
[Table
A
]
Y
- 2.
Vf
(λ, pk
∗
B
)
E
esc
- 3. sk
∗
B
= D
sk
RC
(E
esc
)
4. W
B
= D
sk
∗
B
(ew
B
), W
AB
← (W
A
,W
B
)
E
pk
J
(sk
∗
B
)
W
′
AB
←
Det
(X
0
,Y), W
′
AB
?
= W
AB
µ, pk
∗
B
- 5. open group signature
B
6.
Judge
(gpk, B,upk[B], pk
∗
B
,µ, τ)
B,τ
(B,τ) ←
Open
(gpk, ok,reg, pk
∗
B
,µ)
Note: µ =
GSig
(gpk,gsk
B
, pk
∗
B
)
Figure 3: The copyright violator identification and arbitration protocol
Arb-SJRC.
performed among A , J , and the CA.
mod λ (using the Chinese Remainder Theorem). The
public key is (n,g), the private key is d. Given a
plaintext m ∈ Z
n
s
, choose a random r ←
R
Z
∗
n
s+1
,
and the ciphertext is c = g
m
r
n
s
mod n
s+1
. In
decryption, given a ciphertext c, first compute
c
d
mod n
s+1
= (1+n)
jmd mod n
s
. Let L(b) = (b−1)/n,
and jmd is obtained by applying a recursive version
of Paillier’s decryption scheme (Paillier, 1999). Since
jd is known, m = ( jmd).(jd)
−1
mod n
s
.
The watermark W = W
B
+ W
A
+ φ2
n
is a binary
vector W = {w
1
,w
2
,...,w
m
}, with w
i
= w
B
i
+ w
A
i
+
φ
i
2
n
∈ {0,1}. Note that in order to be collusion re-
sistant, W is embedded into m low frequency DCT
coefficients {x
1
,x
2
,...,x
m
} of the host image by the
following basic steps:
1. Divide the image into 16 × 16 non-overlapping
blocks;
2. Transform each block by two-dimensional DCT;
3. Quantize each block;
4. Embed the watermark by adjusting least signif-
icant bits of chosen DCT coefficients in each
block;
5. Inverse transform each block.
The 16× 16 quantization matrix Q is expanded from
the standard 8× 8 JPEG quantization matrix by a pro-
cedure introduced in (Kuribayashi and Tanaka, 2005).
In order to adjust the embedding strength, a parame-
ter q
w
is defined. The final quantization matrix Q
′
is
derived from Q according to:
Q
′
x,y
=
100− q
w
50
Q
x,y
.
To increase security, a few DCT coefficients in each
block are chosen secretly for watermark embedding.
Their indices are generated by a secure pseudo-
random number generator according to a secret key.
For each block, the candidate DCT coefficients are
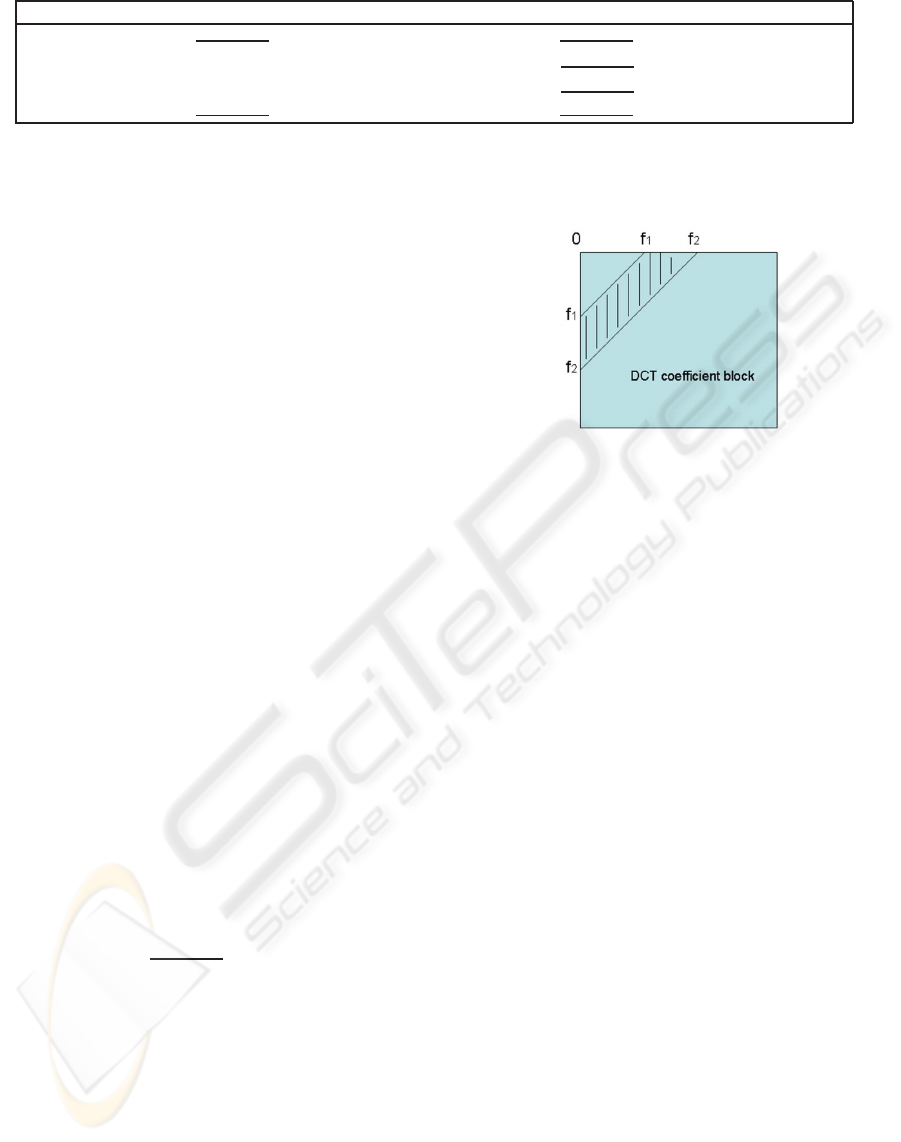
chosen from a limited low frequency band, as shown
in Figure 4. In the simulation, the low frequency band
is from f
1
= 0.2 to f
2
= 0.6 (normalized frequency).
The embedding method is modifying the least signif-
icant bit (LSB) of a DCT coefficient after quantiza-
tion. Conventional LSB-based watermarking meth-
ods modify the LSB in such a way that if watermark
Figure 4: Frequency band for watermark embedding.
bit is 1, then the LSB is made odd, otherwise even.
This approach cannot be directly used here because
the watermark is encrypted and thus unknown to the
embedder. Instead, some modification is made, as
proposed by (Kuribayashi and Tanaka, 2005). A DCT
coefficient is always quantized to the nearest even in-
teger if it is chosen to embed one bit. To insert the
watermark in the encrypted domain, we apply the ad-
ditive homomorphism of (Jurik, 2001) over m ∈ Z
n
s
,
E (m
1
) · E (m
2
) = g
m
1
+m
2
(r
1
r
2
)
n
s
mod n
s+1
= E (m
1
+ m
2
) (6)
In order to preserve the image quality, if the re-
quantized DCT coefficient is larger than the original
one, the watermark bit is subtracted from the quan-
tized coefficient in the encrypted domain, otherwise
it is added to the quantized coefficient. In order to
increase robustness, the same watermark message is
embedded repetitively for α times in the same image.
After watermark detection, a majority voting is used
to decide the watermark bit. Watermark detection is
straightforward: each image block is transformed by
DCT and then quantized; if the specified coefficient is
even after quantization, the embedded bit is 0, other-
wise it is 1.
Simulation is carried out to show the performance
of this watermarking scheme. A 512× 512 gray scale
Lena image is used in the simulation, as shown in Fig-
ure 6(a). Assuming that the watermark contains 200
random bits and α = 75, the peak signal to noise ra-
tio (PSNR) is shown in Figure 5 for various embed-
ding strength q
w
. The watermark embedded version
for q
w
= 75 (PSNR=36.9 dB) is shown in Figure 6(b).
SIGMAP 2008 - International Conference on Signal Processing and Multimedia Applications
304
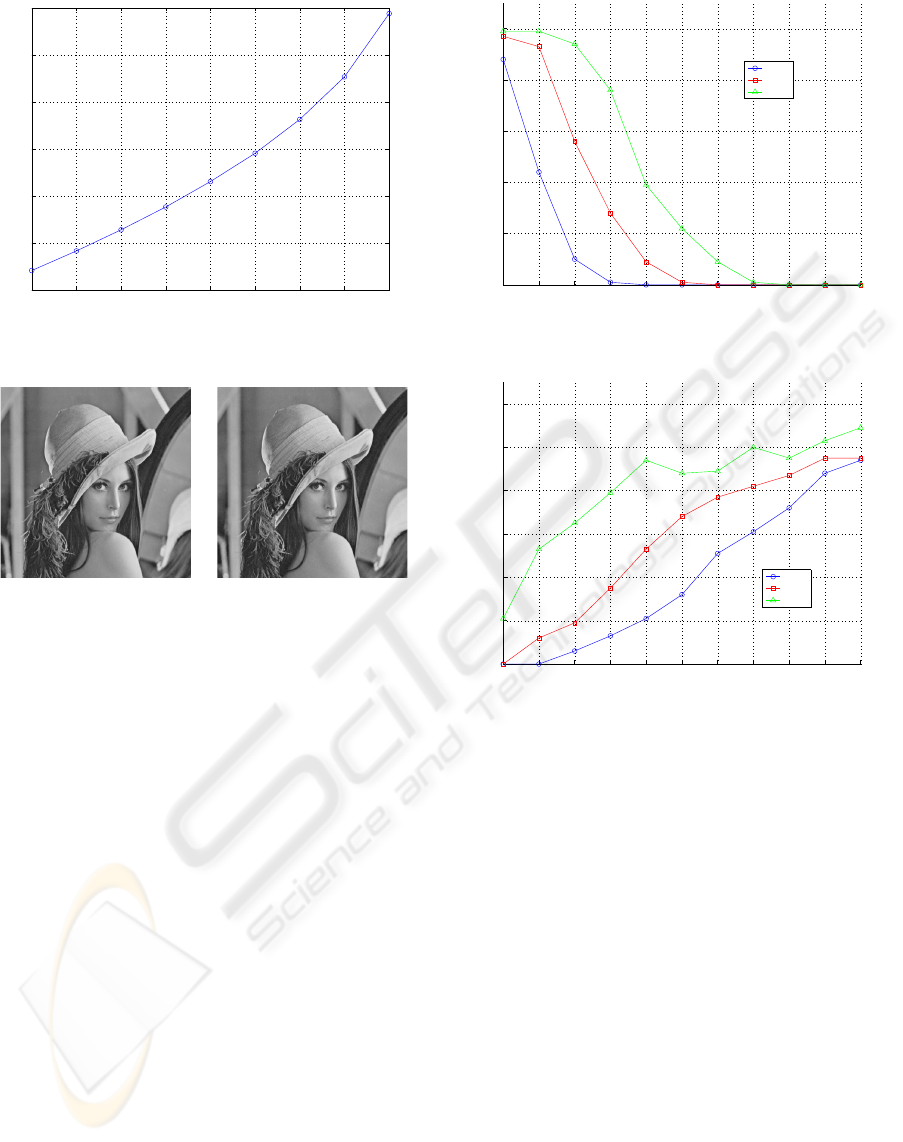
50 55 60 65 70 75 80 85 90
34
35
36
37
38
39
40
q
w
PSNR (dB)
Figure 5: PSNR for different embedding strengths, α = 75.
(a) Original (
b) Embedded
Figure 6: Lena before and after watermark embedding
(q
w
= 75,α = 75, PSNR = 36.9 dB).
Each image block contains on average 15 watermark
bits.
In order to examine the robustness of the water-
mark, JPEG compression and Gaussian noise addition
are applied to the embedded image. For the embed-
ding strengths of q
w
= 55,65,75, the bit error rates
of the watermark after JPEG compression are plotted
in Figure 7; the bit error rates for Gaussian noise are
plotted in Figure 8; more experiments have been done
for average filtering, gaussian filtering, and median
filtering respectively (due to space constraint, plots
are omitted here). The results show that, this scheme
is robust against JPEG compression and Gaussian fil-
tering; besides, it can resist weak Gaussian noise and
slight filtering by average or median method.
5 SECURITY ANALYSIS
In this section, we analyze how the proposed protocol
fulfills the design requirements.
Traceability. Once a pirated copy is found, the proto-
col enables A to trace the related transaction record,
and J to identify the privacy violator.
25 30 35 40 45 50 55 60 65 70 75
0
0.1
0.2
0.3
0.4
0.5
JPEG quality [%]
Bit error rate
q
w
=55
q
w
=65
q
w
=75
Figure 7: Robustness to JPEG compression.
5 6 7 8 9 10 11 12 13 14 15
0
0.1
0.2
0.3
0.4
0.5
0.6
Standard deviation of Gaussian noise
Bit error rate
q
w
=55
q
w
=65
q
w
=75
Figure 8: Robustness to Gaussian noise.
N
on-framing (Buyer’s Security). Since A only
knows the encrypted content E
pk
B
∗
(X
′
) but not B ’s
watermark W
B
and anonymous private key sk
B
∗
, A
doesn’t know the watermarked content X
′
for B .
Therefore, the customer’s rights problem is solved be-
cause A cannot frame B by distributing replicas of
X
′
herself. The unbinding problem is solved as fol-
lows. If A manages to obtain a copy sold to B as
Y = X
0
⊕ (W
A
+W
B
+ φ2
n
), A can obtain W
B
anyhow
since she knows W
A
and φ. Then A can insert the
extracted W
B
to another content to fabricate a copy.
Even if this fabricated piracyis possible, A can’tforge
B ’s signature λ that explicitly binds E
pk
∗
B
(W
B
), pk
∗
B
to ARG, which in turn binds to a particular trans-
action with specifications of X. Furthermore, since
B ’s anonymous key (pk
∗
B
,sk
∗
B
) is one-time, A cannot
trick B by sending outdated information from previ-
ous transactions. Hence, framing attack is impossible.
Non-repudiation (Seller’s Security). B only knows
W
B
but not A ’s watermarkW
A
nor the original content
X
0
. Therefore, B cannot removeW
B
from X
′
. Neither
ANONYMOUS BUYER-SELLER WATERMARKING PROTOCOL WITH ADDITIVE HOMOMORPHISM
305

Table 2: Comparison of the plaintext space, the ciphertext space, and the expansion ratio of various probabilistic ”decisional
composite residuosity assumption” (DCRA)-based homomorphic cryptosystems.
E : G →
˜
G G
˜
G Expansion ratio
Goldwasser-Micali (Goldwasser and Micali, 1982) {0,1} Z
∗
n
lg(n)
Benaloh (Benaloh, 1994) Z/rZ (Z/nZ)
∗
lg(n)/lg(r)
Naccache-Stern (Naccache and Stern, 1998) Z/rZ (Z/nZ)
∗
lg(n)/lg(r)
Okamoto-Uchiyama (Okamoto and Uchiyama, 1998) Z/pZ Z/p
2
qZ lg(p
2
q)/lg(p) > 2
Paillier (Paillier, 1999) Z
n
Z
∗
n
2
lg(n
2
)/lg(n) = 2
Damg˚ard-Jurik (Jurik, 2001) Z
n
s
Z
∗
n
s+1
(s+ 1)/s ≤ 2 (s ∈ N)
can he claim that a piracy was created by A , because
no one else can forge B ’s copy.
Conspiracy Resistance. B generates his ownW
B
and
there is no third party involved in the watermark gen-
eration and insertion protocol. It enables the scheme
to be resistant against conspiracy attacks.
Dispute Resolution. When a dispute occurs, J can
recover sk
∗
B
from the CA, without B exposing sk
∗
B
and
W
B
. After sk
∗
B
is recovered, J can obtain W
B
and he
can further arbitrate the dispute.
Anonymity. B ’s anonymity is preserved because of
the underlying group signature. It is computationally
infeasible for an adversary, not in possession of the
CA’s opening key ok, to recover the identity of B . A
can only know some buyer with an anonymous key
pk
∗
B
has bought a product but not the identity.
Unlinkability. Transaction unlinkability is intro-
duced by B ’s one-time key pair and the unlinkability
property of the underlying group signature scheme.
Quality and Complexity Improvement. In the pro-
posed scheme, only one composite watermark is re-
quired to be inserted, which reduces the computation
complexity. Another obvious advantage over double
watermark embedding schemes is to prevent content
quality degradation and to improve robustness.
Moderate Expansion Ratio. Early anonymous
fingerprinting protocols (Pfitzmann and Waidner,
1997; Pfitzmann and Sadeghi, 1999; Pfitzmann and
Sadeghi, 2000) employ bit-commitment, which lead
to an expansion ratio of at least 10
3
to achieve secu-
rity, hence are inefficient (Kuribayashi and Tanaka,
2005). Therefore, a smaller expansion ratio, i.e., the
ratio between the length of the ciphertext and the cor-
responding plaintext, is required. Expansion ratios
of serval DCRA-based homomorphic cryptosystems
are evaluated in Table 2. The Damg˚ard-Jurik cryp-
tosystem has the smallest expansion ratio of (s+1)/s,
which closes to 1 if s is sufficiently large.
6 CONCLUSIONS
We introduced a new anonymous buyer-seller water-
marking protocol based on group signatures and ad-
ditive homomorphism. One improvement is to pro-
vide all the required security properties, such as re-
vocable anonymity for the buyer, transaction unlink-
ability, and copyright violator traceability with the
help of a trusted authority. Another improvement of
our scheme is on utility. Double-watermark insertion
from conventional schemes is avoided, in order to im-
prove the product’s quality, to reduce the computation
complexity, and to enhance the robustness of the un-
derlying watermark. The protocol gives the flexibility
to adopt all kinds of watermarking schemes, as long
as privacy homomorphism is preserved. We showed
how to apply additive homomorphism, such that wa-
termark can be embedded in the encrypted domain by
adapting the quantized frequency coefficients. Fur-
thermore, we reduce the expansion ratio from 10
3
of
the conventional schemes, to 2 as the theoretical up-
per bound of the Damg˚ard-Jurik cryptosystem, which
is reasonable for cipher communication.
ACKNOWLEDGEMENTS
This work was supported by the Concerted Research
Action (GOA) AMBioRICS 2005/11 of the Flem-
ish Government and by the IAP Programme P6/26
BCRYPT of the Belgian State (Belgian Science Pol-
icy). The authors were supported by the Interdis-
ciplinary institute for BroadBand Technology, Bel-
gium.
REFERENCES
Bellare, M., Shi, H., and Zhang, C. (2005). Foundations of
group signatures: the case of dynamic groups. In Top-
SIGMAP 2008 - International Conference on Signal Processing and Multimedia Applications
306

ics in Cryptology - CT-RSA 2005,
LNCS 3376, pages
136–153. Springer-Verlag.
Benaloh, J. (1994). Dense probabilistic encryption. In Proc.
Selected Areas of Cryptography (SAC’94), pages 120–
128.
Biehl, I. and Meyer, B. (1997). Protocols for collusion-
secure asymmetric fingerprinting. In Proc. 14th
STACS, LNCS 1200, pages 213–222. Springer-Verlag.
Blakley, G. R., Meadows, C., and Prudy, G. B. (1985). Fin-
gerprinting long forgiving messages. In Advances in
Cryptology - CRYPTO 85, LNCS 218, pages 180–189.
Springer-Verlag.
Boneh, D. and Shaw, J. (1995). Collusion-secure finger-
printing for digital data. LNCS 963, pages 452–465.
Camenisch, J. (2000). Efficient anonymous fingerprinting
with group signatures. In ASIACRYPT, LNCS 1976,
pages 415–428. Springer-Verlag.
Camenisch, J. and Damg˚ard, I. (1998). Verifiable encryp-
tion and applications to group signatures and signature
sharing. In Technical Report RS-98-32, BRICS, De-
partment of Computer Science, University of Aarhus.
Cox, I., Kilian, J., Leighton, T., and Shamoon, T. (1997).
Secure spread spectrum watermarking for multimedia.
IEEE Transactions on Image Processing, 6(12):1673–
1687.
Frattolillo, F. (2007). Watermarking protocol for web con-
text. IEEE Transactions on Information Forensics and
Security, 2(3):350–363.
Goi, B.-M., Phan, R. C.-W., Yang, Y., Bao, F., Deng, R. H.,
and Siddiqi, M. U. (2004). Cryptanalysis of two
anonymous buyer-seller watermarking protocols and
an improvement for true anonymity. In Applied Cryp-
tography and Network Security, LNCS 2587, pages
369–382.
Goldwasser, S. and Micali, S. (1982). Probabilistic encryp-
tion and how to play mental poker hiding all partial
information. In Proceedings of the 14th Annual ACM
Symposium on the Theory of Computing, pages 365–
377.
Ibrahim, I. M., El-Din, S. H. N., and Hegazy, A. F. A.
(2007). An effective and secure buyer-seller wa-
termarking protocol. In Third International Sympo-
sium onInformation Assurance and Security, 2007.
IAS 2007, pages 21–28.
Jae-Gwi Choi, Kouichi Sakurai, J.-H. P. (2003). Does it
need trusted third party? design of buyer-seller wa-
termarking protocol without trusted third party. In
Applied Cryptography and Network Security, LNCS
2846, pages 265–279.
Ju, H.-S., Kim, H.-J., Lee, D.-H., and Lim, J.-I. (2002). An
anonymous buyer-seller watermarking protocol with
anonymity control. Information Security and Cryptol-
ogy - ICISC, pages 421–432.
Jurik, I. D. M. (2001). A generalisation, a simplification and
some applications of paillier’s probabilistic public-key
system. In 4th International Workshop on Practice
and Theory in Public-Key Cryptography, LNCS 1992,
pages 119–136. Springer-Verlag.
Kuribayashi, M. and Tanaka, H. (2005). Fingerprinting
protocol for images based on additive homomorphic
property. IEEE Transactions on Image Processing,
14(12):2129–2139.
Lei, C.-L., Yu, P.-L., Tsai, P.-L., and Chan, M.-H. (2004).
An efficient and anonymous buyer-seller watermark-
ing protocol. IEEE Transactions on Image Process-
ing, 13(12):1618–1626.
Liu, K., Trappe, W., Wang, Z., Wu, M., and Zhao, H.
(2005). Multimedia Fingerprinting Forensics for
Traitor Tracing. EURASIP Book Series on Signal
Processing and Communications. Hindawi Publishing
Co.
Memon, N. D. and Wong, P. W. (2001). A buyer-seller
watermarking protocol. IEEE Transactions on Image
Processing, 10(4):643–649.
Naccache, D. and Stern, J. (1998). A new public-key cryp-
tosystem based on higher residues. In 5th ACM Con-
ference on Computer and Communications Security,
pages 59–66. ACM.
Okamoto, T. and Uchiyama, S. (1998). A new public-
key cryptosystem as secure as factoring. In Advances
in Cryptology - EUROCRYPT’98, LNCS 1403, pages
308–318. Springer-Verlag.
Paillier, P. (1999). Public-key cryptosystems based on
composite degree residuosity classes. In Advances
in Cryptology - EUROCRYPT’99, LNCS 1592, pages
223–238. Springer-Verlag.
Pfitzmann, B. and Sadeghi, A.-R. (1999). Coin-based
anonymous fingerprinting. In Advances in Cryptol-
ogy - EUROCRYPT’99, LNCS 1592, pages 150–164.
Springer-Verlag.
Pfitzmann, B. and Sadeghi, A.-R. (2000). Anonymous fin-
gerprinting with direct non-repudiation. In Advances
in Cryptology - ASIACRYPT ’00, LNCS 1976, pages
401–414. Springer-Verlag.
Pfitzmann, B. and Waidner, M. (1997). Anonymous fin-
gerprinting. In Advances in Cryptology - EURO-
CRYPT’97, pages 88–102.
Pittzmann, B. and Schunter, M. (1996). Asymmetric
fngerprinting. In Advances in Cryptology - EU-
ROCRYPT’96, LNCS 1070, pages 84–95. Springer-
Verlag.
Qiao, L. and Nahrstedt, K. (1998). Watermarking schemes
and protocols for protecting rightful ownership and
customer’s rights. Journal of Visual Communication
and Image Representation, 9(3):194 – 210.
Trappe, W., Wu, M., Wang, Z. J., and Liu, K. J. R. (2003).
Anti-collusion forensics of multimedia fingerprinting
using orthogonal modulation. IEEE Transactions on
Image Processing, 51(4):1069 – 1087.
Wang, Z. J., Wu, M., Zhao, H. V., Trappe, W., and Liu,
K. J. R. (2005). Anti-collusion forensics of multime-
dia fingerprinting using orthogonal modulation. IEEE
Transactions on Image Processing, 14(6):804 – 821.
Zhang, J., Kou, W., and Fan, K. (2006). Secure buyer-seller
watermarking protocol. In IEE Proceedings Informa-
tion Security, volume 153, pages 15–18.
ANONYMOUS BUYER-SELLER WATERMARKING PROTOCOL WITH ADDITIVE HOMOMORPHISM
307
