
SECURE AND ROBUST COPYRIGHT PROTECTION FOR
H.264/AVC BASED ON SELECTED BLOCKS DCT
K. Ait Saadi
1
, A. Bouridane
2
and H. Meraoubi
1
1
Centre de Développement des Technologies Avancées, Division Architecture des Systèmes
Cité 20 Août 1956, Baba Hassen, Alger, Algeria
2
School of Electronics, Electrical Engineering and Computer Science, Institute of Electronics
Communications and Information Technology, Queen's UniversityBelfast, Belfast BT7 7NN, U.K.
Keywords: Copyright protection, H.264/AVC, digital watermarking.
Abstract: This paper proposes a new block based DCT selection and a robust video watermarking algorithm to hide
copyright information in the compressed domain of the emerging video coding standard H.264/AVC. The
watermark is first quantized and securely inserted. To achieve invisibility and robustness, the high entropy
DCT 4x4 blocks within the macroblocks are selected to minimise the distortion caused by the embedded
watermark and then scrambled using Linear Congruential Generator (LCG) technique. This approach leads
to a good robustness by maintaining good visual quality of the watermarked sequences. The experimental
results demonstrate the effectiveness of the algorithm against some attacks such as re-compression by the
H.264 codec, transcoding and scaling.
1 INTRODUCTION
Nowadays, most digital applications such as Internet
multimedia, wireless video, personal video
recorders, video-on-demand, videophone and
videoconference face two main problems: (i) to
improve the computation speed of the compression
to meet bandwidth criteria and best video quality as
possible; (ii) how to protect the copyright of the
digital products. To address the first point,
H.264/AVC video compression standard, which is
the latest and most advanced video system to date
and developed jointly by ITU and MPEG, provides a
far more efficient solution for compressing video
than any other compression method available. It
typically outperforms all existing standards by a
factor of three to four especially in comparison to
MPEG-2 (Wiegand, 2003). For the second point,
there has been significant interest in watermarking
which is used for owner identification, royalty
payments, and authentication by determining
whether the data has been tampered with in any
manner from its original form (Sang-Kwang, 2000).
As a result, a large number of watermarking
schemes have been proposed to hide copyright
marks and other information for different video
codecs, however a few works related to H.264/AVC
can be found in the literature. Recent research into
H.264/AVC included the fast implementation of
integer discrete cosine transform (DCT) and variable
block size motion compensation (Fan, 2006).
However, higher compression ratio leads to the
difficulty in balancing among trade-off requirements
for watermarking H.264/AVC video data (Zhang,
2003) (Qiu, 2004).
The idea of compressed-domain watermarking of
videos is not new (Zhang, 2005) (Zhang, 2007) and
this paper proposes a new scheme of blocks DCT
selection and a robust video watermarking
algorithms to hide copyright information in the
compressed domain of the emerging video coding
standard H.264/AVC. The greyscale watermark can
be treated as watermarks for copyright protection of
company trademarks or logos.
2 THE PROPOSED VIDEO
WATERMARKING SYSTEM
Our proposed H.264 watermarking algorithm is
based on Qiu et al. technique (Qiu, 2004) where they
proposed a hybrid watermarking scheme in the DCT
351
Ait Saadi K., Bouridane A. and Meraoubi H. (2008).
SECURE AND ROBUST COPYRIGHT PROTECTION FOR H.264/AVC BASED ON SELECTED BLOCKS DCT.
In Proceedings of the International Conference on Signal Processing and Multimedia Applications, pages 351-355
DOI: 10.5220/0001932203510355
Copyright
c
SciTePress
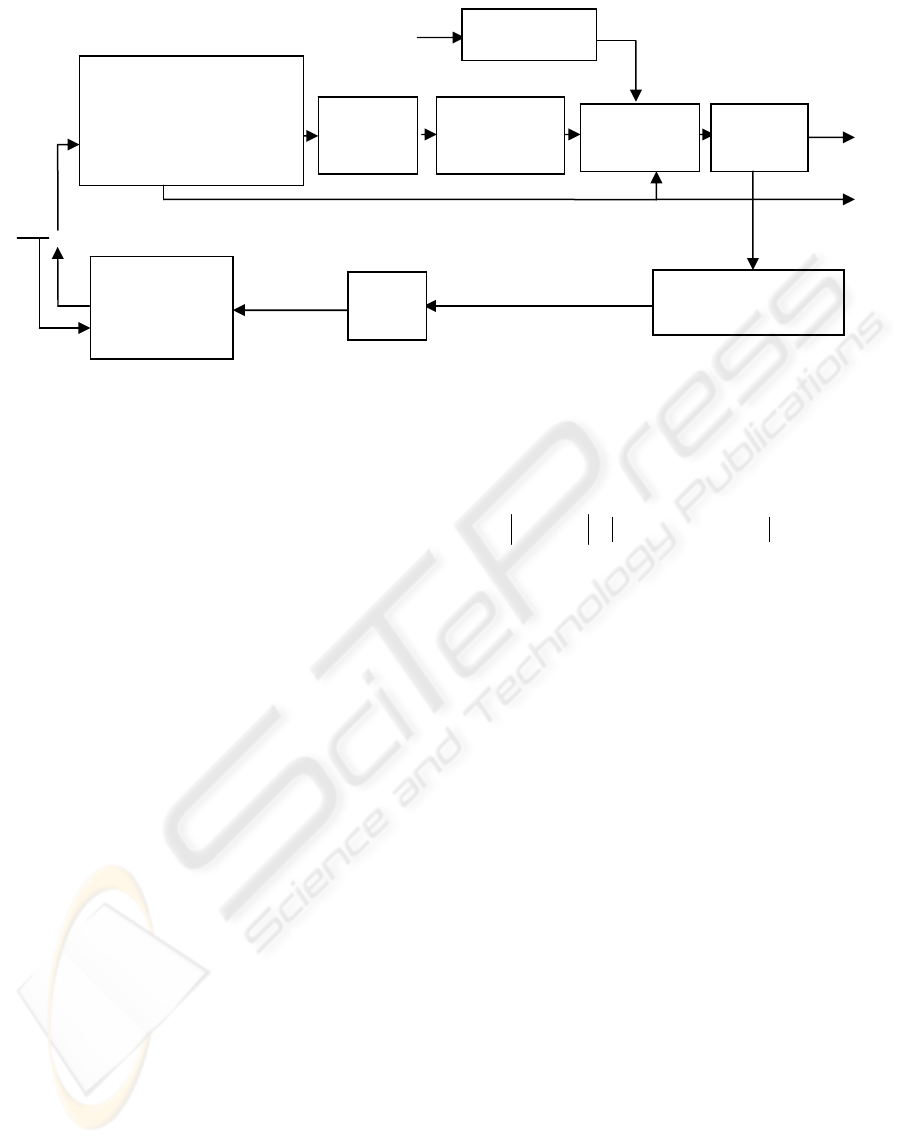
Figure 1: Watermark embedding scheme.
domain and a fragile watermarking in motion
vectors. Our approach operates in the DCT domain
at the macroblock level of I-frames. I-frames are
chosen for watermark embedding because their
existence is crucial for the video signal. Also, P- and
B-frames are highly compressed by motion
compensation and there is less capacity for
embedding a watermark into them. The luminance
component of macroblocks in an I-frame is intra-
coded in 16×16 or 4×4 intra-prediction modes. Each
4 × 4 block of residual data is transformed by an
integer transform after the intra-prediction stage. If
the macroblock is coded in the 16 × 16 intra-
prediction mode, the dc coefficients of all 4 × 4
blocks are transformed by a 4 × 4 Hadamard
transform after the 4 × 4 integer transform to further
decorrelate these coefficients [1]. We only embed
the watermark in the quantized ac residuals of the
luminance component of 4 × 4 intra-predicted
macroblocks. We do not embed the watermark in the
16 × 16 intra-predicted macroblocks for two reasons.
First, the 16×16 intra-prediction mode is used for
smooth regions of the frame, and watermark
embedding causes visible artefacts there. Second,
the extra Hadamard transform for this macroblock
decorrelates the dc coefficients much further so that
many of these coefficients are set to zero.
2.1 Embedding Process
The overall scheme of the proposed embedding
process is shown in Figure. 1. The proposed
algorithm embeds the watermark in one quantized ac
coefficient Xq(u,v) in the high frequency along the
diagonal positions (i.e., u=v) of a high entropy and
scrambled blocks within a macroblock. In order to
survive the recompression, the watermark signal
W(u,v) must be strong enough to survive the
quantization (Qiu, 2004), so that:
1]QP),v,u(W[quant)v,u(W
q
≥=
(1)
where the quant[.] denotes the quantization
parameter, QP denotes the quantization parameter
and (u, v) denotes a position in a 4x4 block Bk.
The watermark W(u,v) is quantized with
different Qp where each is associated to different
Qstep. The embedding is done with the Qstep giving
the minimum distance d
min
between the coefficient
quantified Xq(u,v) and the Wq(u,v). Our experiments
show that the ac coefficients in diagonal positions
are more stable than others. Effectively, we tested
the insertion with all the quantized ac coefficients
within the block and the best ac coefficient that
verifies the invisibility of the watermark is found at
position (1,1). The insertion is performed by
replacing the Xq(1,1) by the watermarked coefficient
as follow :
{
}
⎩
⎨
⎧
=
=
=
0 Wnif 0
1Wn if )v,u(W),v,u(Xmax
X
qq
*
q
(2)
where wn is the bit to be embedded. We notice the
ac coefficient Xq(u, v) is cleared if ‘0’ is embedded.
It can be justified by the fact that the Xq(u, v) is zero
in most cases. It will not introduce significant
artefacts
To obtain robust and invisible watermarks, the
blocks with high entropy are selected for
embedding.
Define a finite set of data D = {x
1
, ..., x
N
}
generated according to a probability distribution P =
Bitstrea
m
4x4
Block
Key
4x4
Integer
DCT
Intra/Inter
Prediction &
Mode Decision
Entropy
coding
Quantization
Watermark
Quantization
Embedding
process
⊕
Calculationofentropy,
Selection and Scrambling
of the high entropy
blocks
Inverse Entropy,
Quantization & DCT
Frame
Buffer
SIGMAP 2008 - International Conference on Signal Processing and Multimedia Applications
352

{p
1
, ..., p
N
}. Shannon’s entropy (Thiemer, 2006) of P
is given by:
j2
N
1j
j
plog.p)P(H
∑
=
−=
(3)
From the source-channel point of view H(P)
stands for the average size of the code necessary to
transmit data from D when these are generated by P.
In our experiments D is the set of gray level values
taken from a current block (in practice N=256).
Given a block B(u, v), where (u, v) is its location in
a macroblock of 16×16 pixels. Let H(B(u, v)), be the
entropy of the gray level distribution in B(u, v). We
derive a slight variation of (3) as following:
j2
255
0j
j
plog.p))v,u(B(H
∑
=
−=
(4)
{pj} is the probability distribution of the gray level
values in B(u, v).
Once the entropies blocks of each macroblock
are calculated, they are ranked in descending order
to choose those blocks with high value of entropy.
To improve the robustness of this approach, the
position G(i) of the selected high entropy blocks
within a macroblock are randomly scrambled using
the simplest and fastest random generator called
“Linear Congruential Generator” (LCG) (Raymond,
2006) such as:
M mod )cr )1i(G*m()i(G +−=
(5)
where m, cr and M represent the multiplier, the
increment and the modulus, respectively. They are
chosen to maximise the period which cannot exceed
M and which is equal to 16 in our case. G(0) is a key
for the insertion and extraction of the watermark.
2.2 Detection Process
Watermark detection is performed after entropy
decoding: the bitstream is partially decoded to obtain
the transformed ac coefficients. This is followed by
applying the LCG with the same key used in the
insertion process to select the watermarked blocks.
For each selected block containing DCT coefficients
in the I-frames, the watermark bit is determined as
follows:
(6)
3 EXPERIMENTS AND RESULTS
The proposed watermarking technique has been
integrated into the H.264 J-M-7.6 reference software
(H.264/AVC Joint Model 7.6 (JM-7.6) Reference
Software). The standard test video clips include
Foreman, Claire, Stefan. All frames are coded at 30
frames/s at 372 kbits/s.
All video clips are coded in QCIF format
(176x144). P and B frames are not used in our
experiments because there are very few nonzero
DCT coefficients due to the efficient compression
performance. A small 16x16 grayscale watermark is
used for the experiment (Figure. 2). In each I-
frames, the watermark to be inserted must be
adjusted with the blocks into the macroblock. By
embedding the watermark in the higher entropy
blocks within a macroblock, a total of 256 bits are
embedded as copyright owner’s signature in a frame
QCIF (176x144) resolution according to the position
of the blocks generated by the LCG. By comparing
to [5] where the total of 99 bits are embedded in a
frame, the embedding process developed increases
the capacity of insertion about 157 bits by frame
while still maintaining a high visual quality. The
experiment shows us that only the QP = [28,32,36],
corresponding to typical QPs for low bit-rate
applications are suitable to obtain the
imperceptibility and the integrity of the watermark.
Figure. 3 shows the insertion tests performed on
different values of QP: for QP less than 28, the
watermark is not completely removed, beyond QP =
36 the watermark is visible.
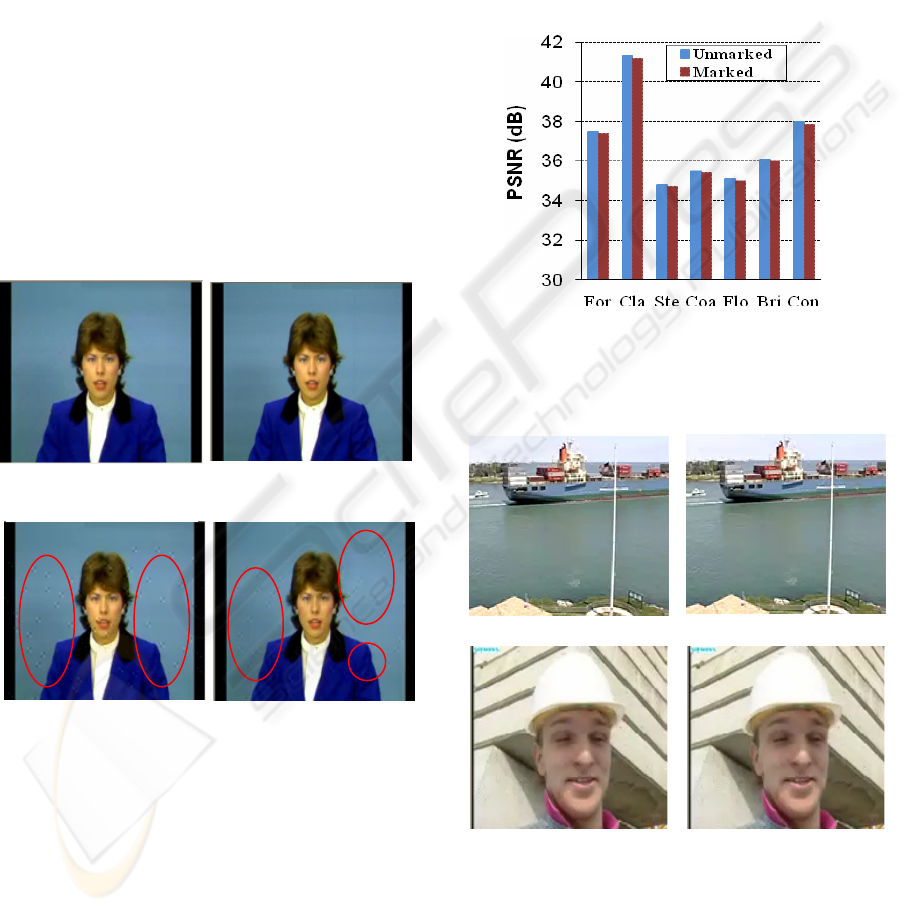
Figure 2: Logo image as watermark.
Figure 3: Extracted watermark with different values of
QP.
Figure. 4 shows the insertion tests performed on
different values of QP for the videos "Claire" and
"Container" and their correspondent PSNR (dB),
respectively. The quality degradation is clearly
shown on the picture for the insertion performed
with QP greater than 36. Figure. 5 illustrates the
average PSNR comparison results for a set of test
sequences.
QP = 16 QP = 24 QP = 26 QP = 28
⎩
⎨
⎧
≥
=
∧
otherwise 0
0)v,u(X if 1
W
q
SECURE AND ROBUST COPYRIGHT PROTECTION FOR H.264/AVC BASED ON SELECTED BLOCKS DCT
353
QP = 24
PSNR= 40.38 dB
QP = 28
PSNR= 40.00 dB
QP = 40
PSNR= 39.02 dB
QP =48
PSNR= 36.28 dB
On average, the watermarking leads to a
decrease of approximately 0.06 dB to 0,13 dB and in
the experiments, no visible noise can be observed in
the test video sequences. Figure. 6 shows Foreman
and Container as examples of video watermarked
sequences with PSNR (dB).
Some of general video manipulations are
performed as attacks to evaluate the effectiveness of
the robust watermark: two codecs video H.264/AVC
and H.263 are applied to re-compress the
watermarks videos, the transcoding from the YUV
(4:2:0) to RGB (4:4:4) format and in the third
experiment, we investigated robustness to scaling.
This attack rescales the video sequences from the
QCIF (276x144) resolution to the CIF (352×288)
resolution. Table 1 shows the reconstructed
watermark from the marked and attacked Claire and
Container sequences with the PSNR (dB). The
reconstructed watermark after watermarking is
highly correlated to the original pattern. This
demonstrates and supports the feasibility of the
proposed approach.
Figure 4: Watermarked Claire sequence with different
values of QP.
4 CONCLUSIONS
In this paper, we have proposed a watermarking
algorithm for H.264 that is robust to some general
video manipulations. We have achieved this goal by
calculating the entropy of the gray level distribution
in the blocks to determine which of these are well
textured and thus suitable for watermark embedding.
To improve the robustness, we used a key-dependent
algorithm (LCG) to randomly select the high entropy
blocks within the macroblock. The simulation results
shows that we increased the payload about of 157
bits by frame comparing to (5) where the total of bits
are 99 without a noticeable change in perceptual
quality. Thus, future work leads to verify the
robustness of the proposed approach against others
common image processing.
Figure 5: PSNR (dB) of marked and unmarked CIF-size of
Foreman, Claire, Stefan, Coastguard, Flower, Bridge,
Container (denoted by For, Cla, Ste, Coa, Flo, Bri, Con in
the horizontal axis) at 372 kbit/s.
Figure 6: The 3
th
frames of unmarked and marked
Container (a) and Foreman (b) sequences (at 372 kbits/s,
QCIF size).
Unmarked (37,94dB) (a) Marked (37, 85 dB)
Unmarked (37,45 dB) (b) Marked (37, 39 dB)
SIGMAP 2008 - International Conference on Signal Processing and Multimedia Applications
354
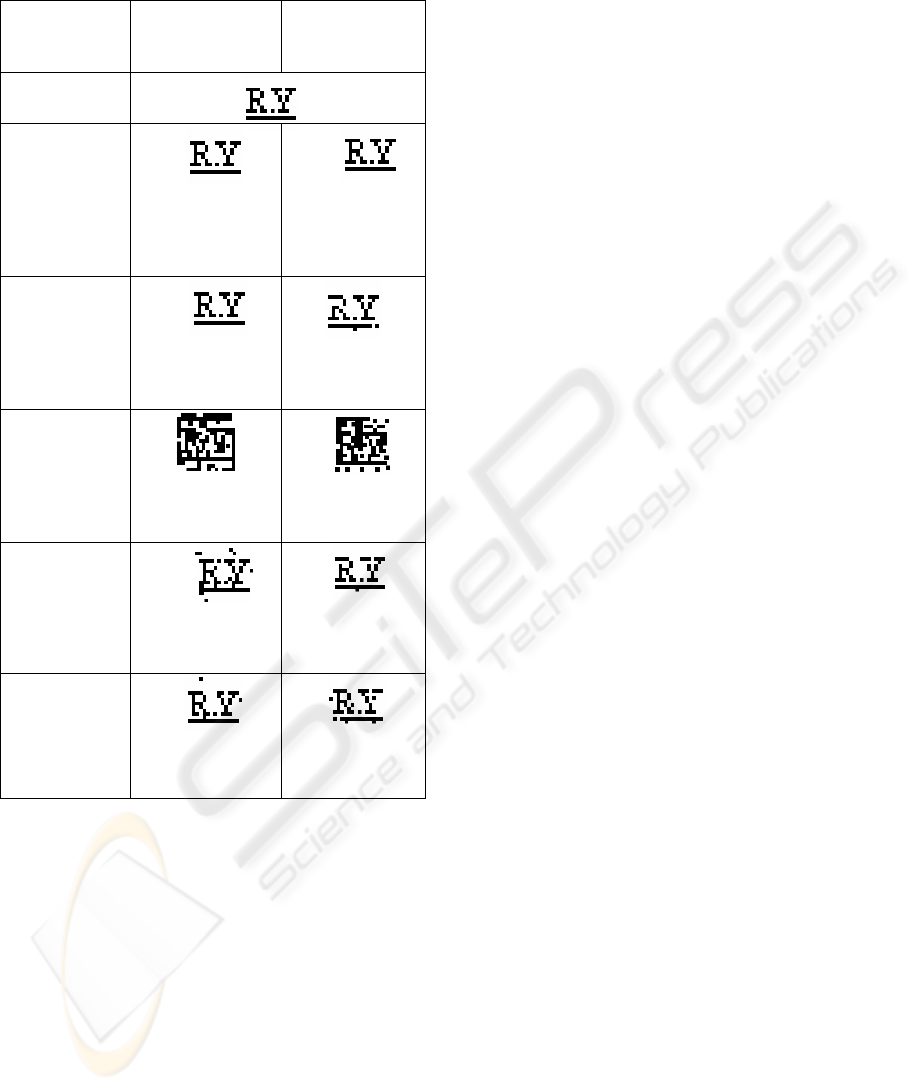
Table 1: Reconstructed watermark after manipulations and
the corresponding correlations.
Unmarked
Test
Sequences
Claire
PSNR=41.29
dB
Container
PSNR=37.9
4 dB
Original
watermark
Extracted
from
watermarked
video
ρ=1
PSNR=41,00 dB
ρ=1
PSNR=37.88
dB
Extracted
after re-
compressed
with H.264
coder
ρ=1
PSNR=39.47dB
ρ=0.97
PSNR=37.65
dB
Extracted
after re-
compressed
with H.263
coder
ρ=0.35
PSNR =35.69dB
ρ=0.44
PSNR=32.02
dB
Extracted
after
transcoding in
the RVB
(
4:4:4
)
format
ρ=0.93
PSNR= 38.08dB
ρ=0.97
PSNR=37.58
dB
Extracted
after scaling
ρ=0.97
PSNR=38.62 dB
ρ=0.94
PSNR=37.36dB
REFERENCES
Wiegand, T., Sullivan, G. J., Bjøntegaard, G., and Luthra,
G. J. 2003. Overview of the H.264/AVC video coding
standard. IEEE Trans. Circuits Syst. Video
Technol.13, 7 (Jul. 2003), 560–576.
Sang-Kwang, L., and Yo-Sung, H., 2000. Digital Audio
Watermarking In the Cepstnun Domain. IEEE
Transactions on Consumer Electronics. 46, 3 (Aug.
2000).
Fan, C. P. 2006. Fast 2-dimensional 4x4 forward integer
transform implementation for H.264/AVC. IEEE
Trans. Circuits Syst. II. Exp. Briefs. 53, 3 (Mar.2006),
174–177.
Zhang, J. and Ho, A. T. S. 2003. An efficient digital
image-in-image watermarking algorithm using the
integer discrete cosine transform (IntDCT). In Proc.
IEEE Joint Conf. 4th Int. Conf. Info. Commun. Signal
Process. and 4th Pacific-Rim Conf. Multimedia. 2
(Dec. 2003), 1163–1167.
Qiu, G., Marziliano, P., Ho, A. T. S. D., He, J., and Sun,
Q. B. 2004. A hybrid watermarking scheme for
H.264/AVC video. In Proc. 17th Int. Conf. Pattern
Recogn., Cambridge, U.K., (Aug. 2004).
Zhang, J., and Ho, A. T. S. 2005. Robust Digital Image-in-
video Watermarking for the, Emerging H.264/AVC
Standard. IEEE Workshop on Signal Processing
Systems Design and Implementation. (Nov. 2005),
657-662.
Zhang, J., and Ho, A. T. S. 2007. Robust video
watermarking of H.264/AVC. IEEE Trans. Circuit and
Systems. 54, 2 (Feb. 2007), 205–209.
Thiemer, H., Sahbi, S., and Steinebach, M. 2006. Using
Entropy for Image and Video Authentication
Watermarks. In IS and T/SPIE Conference on
Security, Steganography and Watermarking of
Multimedia Contents (SPIE), San Jose, California,
6072-607218 (Jan. 2006).
Raymond, S., Lee, T., and Lam, H. W. S. A. 2006.
Chaotic Real-time Cryptosystem using a Switching
Algorithmic-based Linear Congruential Generator
(SLCG). IJCSNS International Journal of Computer
Science and Network Security, 6, 8B (Aug. 2006).
H.264/AVC Joint Model 7.6 (JM-7.6) Reference Software.
[Online].Available:
http://iphome.hhi.de/suehring/tml/download/ol.
Bowman,
SECURE AND ROBUST COPYRIGHT PROTECTION FOR H.264/AVC BASED ON SELECTED BLOCKS DCT
355
