
PHYSICAL-VIRTUAL CONNECTION IN UBIQUITOUS
BUSINESS PROCESSES*
Pau Giner, Manoli Albert and Vicente Pelechano
Department of Information Systems and Computation, Technical University of Valencia
46022 Valencia, Spain
Keywords: Ubiquitous Computing, Business Process, Model Driven Engineering.
Abstract: Ubiquitous Computing (Ubicomp) when applied to organizations can improve their Business Processes. An
example of improvement is the integration of real world objects in the Information System. This reduces
inconsistencies in the information and improves information acquisition rates. Automatic identification is
the key technology to achieve this paradigm shift. The present work inspects the relevance of the
identification concept for Business Processes supported by Ubicomp technologies and presents a conceptual
framework to define the elements involved in the identification process. Taking into account that Business
Processes tend to be very dynamic, it is important to have technological-independent definitions in order to
enable the evolution of systems. The presented framework is independent of the underlying technology, in
order not to be locked with one particular solution.
1 INTRODUCTION
Business Processes in organizations usually involve
real-world objects. Information Systems need
mechanisms to connect those elements at the
physical space with the information about them at
the digital space. Maintaining the connection
between both in sync is essential. Baggage loss is a
common problem in aviation industry that illustrates
the consequences of breaking this linkage. During
2006 the Association of European Airlines reported
that they had mishandled more than five million
bags (AEA, 2006). Concerned with this problem,
International Air Transport Association is
considering the usage of Radio Frequency ID
(RFID) technology
1
to improve logistics.
Ubiquitous Computing (Ubicomp) technologies
such as automatic identification (Auto-ID),
localization, sensor and wireless connectivity can
help to bridge physical and digital spaces. Ubicomp
represents a computation paradigm where services
are seamlessly integrated into the environment and
accessed in a natural way.
Ubiquitous Business Processes (UBPs) result from
the application of Ubicomp to support Business
Processes in organizations. The introduction of
Ubicomp in organizations is promising and
numerous benefits have been detected in economic
terms (Langheinrich, 2002), and process
improvement terms (Fleisch, 2001), (Sandner 2005),
(Strassner, 2002).
In UBPs, real world elements participating in the
process turn into intelligent interconnected objects
and the information flow between the real world and
the Information System gets automated. Without the
need for humans to act as information carriers,
information could be acquired automatically, with
more precision and at higher rates.
Identification of real-world objects is the
prerequisite for “smart” behavior (Römer, 2004).
Therefore, Auto-ID is considered the core element
for the Ubicomp enablement of systems. Auto-ID
acts as a foundation for other technologies such as
localization and moreover it represents the
automation in the linkage between real world objects
and their computational counterparts at the
Information System. This linkage constitutes the
process of identification and it is the central subject
of interest for the present work.
Different technologies can be applied to
implement Auto-ID mechanisms. Due to the
dynamic nature of Business Processes, the change in
____________________________
*
This work has been developed with the support of MEC under the
project SESAMO TIN2007-62894 and cofinanced by FEDER.
1
http://www.iata.org/stbsupportportal/rfid/
266
Giner P., Albert M. and Pelechano V. (2008).
PHYSICAL-VIRTUAL CONNECTION IN UBIQUITOUS BUSINESS PROCESSES.
In Proceedings of the Tenth International Conference on Enterprise Information Systems - ISAS, pages 266-271
DOI: 10.5220/0001697102660271
Copyright
c
SciTePress

requirements can have a technological impact in the
system, and the introduction –or replacement– of a
particular technology should not suppose a burden to
the evolution of the system. Defining the
identification process in an abstract way favours this
evolution, since the concepts defined become
independent of the technology used for their
implementation.
This paper is concerned with the development of
appropriate identification modelling concepts for
UBPs to treat automated and non-automated
identification in a homogeneous manner. The
contribution of this work is a conceptual framework
to reason about identification independently of the
underlying technology. In this way concepts
common to any identification technology are
defined, so the Information System can migrate
seamlessly from one technology to another.
The remainder of the paper is structured as
follows. Section 2 presents the conceptual
framework and the theoretical background in which
it relies. Section 3 defines the functionality and
components an Information system should offer to
support the presented framework. In Section 4, some
insights are given about a prototype implementation
to verify the applicability of the framework. Section
5 presents related work. Finally, Section 6 presents
some conclusions and further work.
2 THE IDENTIFICATION
CONCEPT
Identification implies to cover the gap between real
world elements and the information about them in
the Information System. Auto-ID is a particular kind
of identification process where technology is used to
automate certain operations. Different technologies
such as barcodes, infrared beacons or RFID tags
offer identification capabilities at different levels of
automation. Identification process can even be
completely manual, as it occurs in most Information
Systems nowadays. Human users are in charge of
identifying the real world elements and transmit this
information to the Information System.
Whatever physical method is used to store and
communicate the identity of an element, this
information should follow a certain codification.
Numbering schemas such as Universal Product Code
(UPC) or Electronic Product Code (EPC) are
commonly used in the consuming goods industry
and define the formats that a product identifier could
follow.
In the following sections, elements involved in
the identification process will be described. In order
to abstract technical details and formalize their
definition, concepts from the modeling area are
used.
2.1 Theoretical Basis
Our characterization of the identification idea is
based on the precise definition of the model concept
and how it is related to systems. The concept of
model is defined by Bézivin as “a simplification of a
system built with an intended goal in mind. The
model should be able to answer questions in place of
the actual system” (Bézivin, 2001). Following the
previous definition, an Information System can be
considered a model as it is a computable
simplification of a system under study used for
answering questions about it.
Favre establishes a basic taxonomy for systems
and some relation kinds among them (Favre, 2004).
Systems are classified as Physical Systems –
observable elements or phenomenons pertaining to
the physical world–, Digital Systems –residing in
computer memories and processed by computers–
and Abstract Systems –ideas and concepts that
eventually reside in human mind to be processed by
human brains–.
The most relevant relation between systems is
the RepresentationOf relation, noted as μ. This
relation establishes two roles between systems, one
system is considered the system under study and the
opposite acts as a model. Thus no system is a model
per se, being a model is a role played by a system in
relation to another system.
The concept of set and two additional
relationships are also introduced by Favre. The Set,
as defined by the set theory, is considered in the
framework as a kind of Abstract System. The
ElementOf (ε) relation is used to express the
inclusion of a system in a set. The ConformsTo (χ)
relationship is a derived relation expressing the
concept of metamodel as “a model of a modelling
language”.
These relationships presented are used to define
the concepts involved in the identification process.
The conceptual framework that includes these
concepts is presented below.
2.2 A Conceptual Framework for
Identification
The concepts involved in the identification
framework are depicted in Figure 1. The framework
defines concepts at physical, digital and abstract
spaces. An Element is part of the Physical Space. It
represents any real-world object such as a bottle in a
PHYSICAL-VIRTUAL CONNECTION IN UBIQUITOUS BUSINESS PROCESSES
267
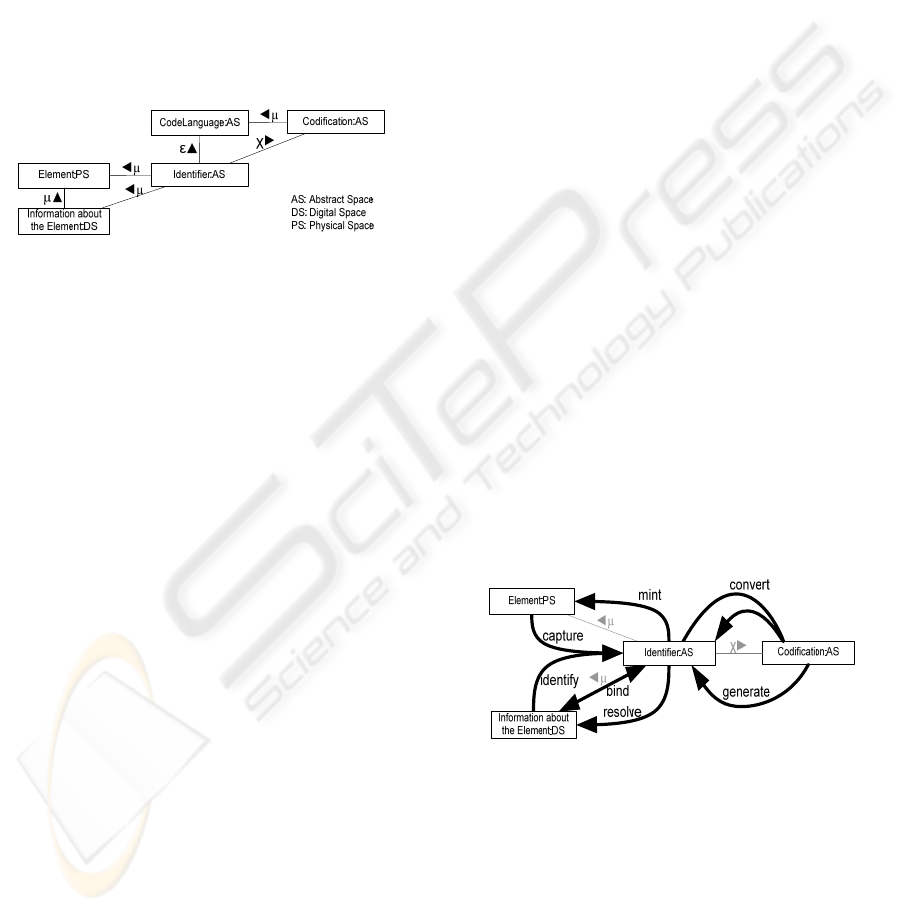
supermarket or a package in a warehouse. The
Information System can contain information about
an element such as its price or its manufacturer. This
information is a representation of the current
element at the Digital Space. The information in the
system can be considered a projection of the
physical element in the digital space as only relevant
characteristics are present in the Information
System. An Identifier is a representation of both the
element and its digital counterpart. The Identifier is
a member of a likely infinite set of identifiers
constituting a language, a model of which is a
Codification (the Identifier is then, conformant to
this codification).
Figure 1: Conceptual framework for identification.
The common scenario is to move from the physical
space to the digital space. Identifier retrieval can be
done using a barcode reader, an RFID antenna or by
typing the element code by hand. Information in the
system should be searchable using this identifier.
And the codification used to encode the identifier
should be known.
However, the identification process involves
several transitions in both directions thru the
presented relationships. Thus the relationships
defined in the framework are bidirectional to allow
other scenarios. For example, prior to detection,
identifiers should be transferred to the physical
world.
In addition, there are no restrictions of
cardinality in the relationships presented in the
framework. An element, for example, can have
multiple identifiers. In the example, a human-
readable code (a sequence of digits printed on the
bottle label) can complement the barcode-based
identifier. Using multiple physical representations of
an identifier can help to maintain the identification
process in case of degradation of the physical
supports.
A more detailed analysis of the needed
operations that an Information System should offer
to cover the indicated transitions is presented in the
following section.
3 IMPLICATIONS FOR THE
INFORMATION SYSTEM
When the presented framework is applied to define
the identification mechanisms of an Information
System, the architecture of the identification system
should be defined. This section detects the
operations needed, which software elements should
be defined to support the framework in a modular
way and some requirements that should be fulfilled
by the Information System regarding the
identification process.
According to Kindberg, an identification-
resolution system is composed by five essential
tasks:
“Identifiers are minted, captured and converted;
and they are bound to resources. Bindings are
created and looked up. Resolution is the process of
looking up bindings from identifiers and returning
the bindings or the resources to which they refer.”
(Kindberg, 2002).
These tasks are consistent with the conceptual
framework we have previously defined. Each task
can be seen as a transition through the relations
defined in the framework, as depicted in Figure 2.
ID creation has been defined in two different steps,
the generation of the identifier following a certain
codification and the assignment to the physical
object (or minting); Identifiers can be obtained by
capturing them from the physical element or by
identifying a piece of information. Binding supposes
the creation of an association between Identifiers
and information in the system. The conversion of
identifiers produces a new identifier of a different
codification.
Figure 2: Identification tasks.
In order to keep physical and digital spaces
connected, mechanisms supporting these tasks
should be defined. Information Systems should
provide means to support them either manual or
automatically. Which components should be
considered in the design of an identification system
in conformance with the presented framework and
some remarks about their integration are given
below.
ICEIS 2008 - International Conference on Enterprise Information Systems
268

3.1 Architectural Components
The presented elements and tasks forming the
conceptual framework involve different spaces.
However, the Information System is only present at
digital space. Therefore some components at digital
space should provide the connection to physical
space, and some others should represent concepts of
abstract space. In order to support the defined tasks
in a modular way, the components defined to cover
each of these tasks are the following:
– Minters, elements capable of obtaining a
physical representation of an identifier such as a
barcode printer.
– Capturers, elements capable of obtaining an
identifier from the physical space. Barcode
readers, or RFID receivers, are some examples.
– Codifications, elements capable of producing
new identifiers in a computable form. They
contain the information limitations that the
identifier has such as a range of allowed values.
– Mediums, possible representations that a
codification can have. A barcode-based
codification can be represented by a barcode or
by a sequence of printed numbers. Barcode
readers are able to read the former while humans
are capable of reading the later.
– Transformations: define directional
transformations between two codifications.
– Information Registry: it is in charge of the
binding and information retrieval tasks.
3.2 Information System Requirements
In order to integrate the defined components and
support the identification process, the Information
System has to satisfy several requirements detailed
below.
3.2.1 Manage Codification Dependencies
Not every minter can be used to produce any
codification for any medium. There is also no
universal receiver capable of reading any identifier.
The limitation in the number of codifications a
mint, resolution or conversion system can handle
should be managed. The software component
representing any of those elements should contain
metadata indicating the supported codifications and
mediums.
Information System should allow the usage of
the elements that support a certain codification or
have a sequence of transformations to obtain this
codification.
3.2.2 Allow Complex Information Retrieval
The relation between physical elements and their
virtual counterpart is not always one to one. Physical
elements can share the same identifier or contain
multiple identifiers.
In supply stores, being impossible to tag the
product type (as it is an abstract concept), all its
members are tagged instead to represent it to retrieve
information such as prize which is not assigned in an
individual basis.
The opposite situation is also common. People
for example can be identified using email addresses,
fingerprints or organization specific identity card
numbers. Therefore, information registry should
support the possibility of having multiple identifiers,
and multiple information pieces per identifier when
information is resolved or binded.
3.2.3 Offer User-Valuable Operations
In addition to provide the basic mechanisms for
covering the essential identification tasks, more
complex operations –resulting from the composition
of the basic ones– should be considered.
Since physical elements are subjected to
degradation, Information Systems should offer
mechanisms to offer common sequences of
operations. In this way users can perform –or
program– maintenance tasks easily.
Identification regeneration is an example.
Identification regeneration consists in identifying a
piece of information and minting the identifier it has.
4 IMPLEMENTATION DETAILS
A prototype implementation was developed to prove
that the presented framework is expressive enough
to deal with different identification technologies. For
the development, RFID, fiducials, and manual
identification where chosen as identification
technologies.
The software elements supporting the different
identification tasks were componentized to promote
reusability. In this way, codifications can be used
independently of the underlying technology, as far
as the types supported by the technology form a
superset of the required for that codification. For
example, Serial Shipping Container Code (SSCC) is
a eighteen digit codification that can be used in
EPC-based RFID systems as well as in barcodes.
However, the standard fiducial set contains only 90
symbols, so it cannot support this codification.
Web Services technology has been chosen to
form the architecture of the system as it is transport
PHYSICAL-VIRTUAL CONNECTION IN UBIQUITOUS BUSINESS PROCESSES
269
independent and enables the definition of distributed
systems following a Service Oriented Architecture.
This allows the integration of identification systems
from different vendors.
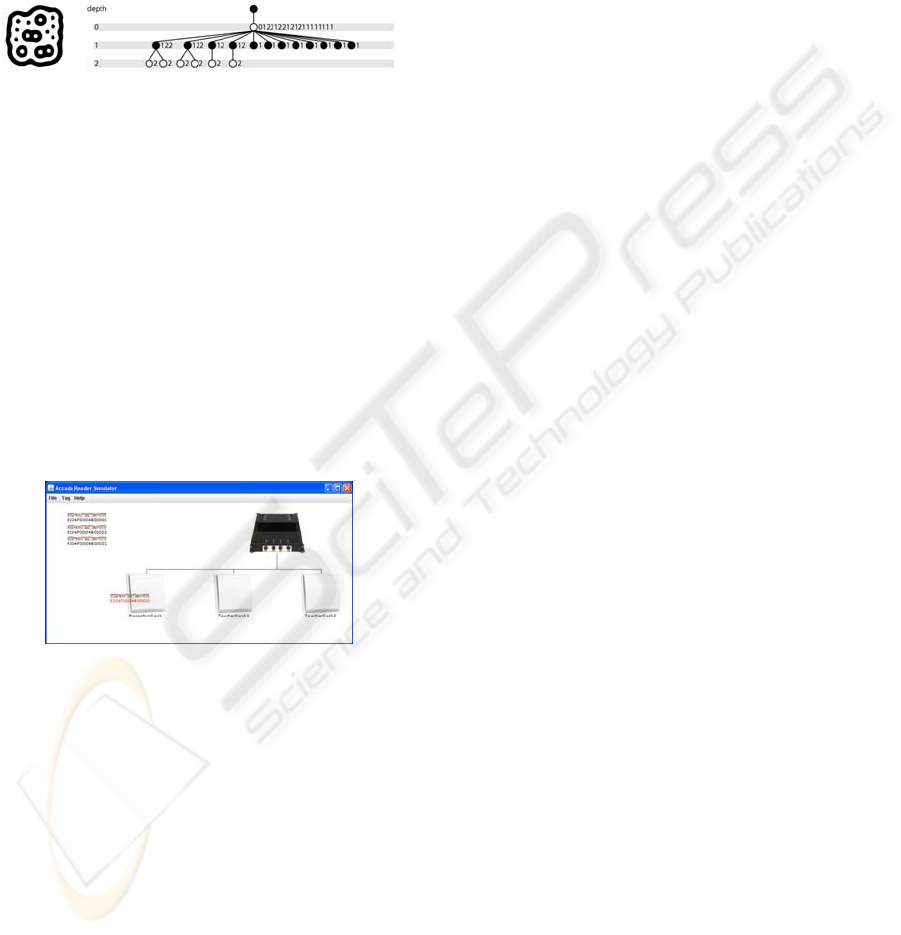
The fiducial based identification subsystem is
based on reacTIVision
2
. Fiducials –specially
designed markers recognizable in a real time video
stream– are used to identify elements (Bencina,
2005).
Figure 3: A fiducial and its left heavy depth sequence
(Bencina, 2005).
The usage of fiducials results in an intuitive and
affordable identification solution. The complete
Auto-ID system is composed by a USB video
camera as a capturer, a common printer as a minter
and the reacTIVision framework to handle the
encoding and decoding tasks. The codification
consists in a module that generates numerical values
from 0 to 90. The printer supports two mediums for
this codification, one corresponding to the fiducial
image corresponding to the code in the standard
fiducial set, and another just by printing the number.
These components of the infrastructure have been
correspondingly wrapped in order to be accessed as
Web Services.
Figure 4: Accada Reader Simulator.
Identification subsystem supporting RFID is based
on Accada
3
, an open source RFID prototyping
platform. The Accada platform deals with readers,
filters and RFID data aggregation following
EPCglobal standards, the predominant
standardization effort of the RFID community. The
usage of such middleware eases the development
and reduces the technological heterogeneity. In
Figure 4 the simulation tool used to validate the case
study is shown.
Web services are also used as a wrapper for the user
interaction when acting as an identification system.
In this last scenario a web application was used to
allow the user to introduce a numeric code and to
obtain system information.
5 RELATED WORK
The idea of automating the linkage between real and
virtual elements is nothing new. Research has
considered the application of printed markers (Ishii,
1997), (Ljungstrand, 2000), (Rekimoto, 1995), RFID
technology (Floerkemeier, 2005), (Römer, 2004),
(Want, 1999) or infrared beacons (
Kindberg et al.,
2002) as a way to enforce this linkage.
Some frameworks for the development of
Ubicomp applications such as One.world (Grimm,
2002), Interactive Workspaces (Johanson, 2002),
Cooltown (Kindberg et al., 2000) or Gaia OS
(Roman, 2002) have been developed to abstract this
technological heterogeneity. Auto-ID specific
middleware has been also developed such as
Accada, SAP’s Auto-ID infrastructure (Bornhövd,
2004), Java RFID Api (Sun 2006) or OAT C4
Architecture (OATSystems 2006). These
infrastructures provide useful programming
primitives to filter and aggregate information from
Auto-ID devices and transmit application-relevant
events. The APIs provided by these frameworks
supply relevant information at application level
allowing developers to build their systems on top on
them.
Providing constructs to represent the needed
mechanisms in a technological agnostic way is what
this work tries to address, so these infrastructure
elements are complementary to the objectives of the
present work.
6 CONCLUSIONS
The present work introduces a conceptual
framework to define in a precise way the elements
involved in the identification process and the
relationships among them. This is useful to
determine the operations and components that an
Information System supporting identification should
provide independently of the used technology.
In the present work the identifier is not considered to
have a meaning. In some numeric schemas, it has
several parts to indicate company, location reference
and other information and the like. With the present
implementation, the elements in charge of
codification should format the identifier correctly.
_____________________________________
2
http://www.iua.upf.es/mtg/reacTable/?software
3
http://www.accada.org
ICEIS 2008 - International Conference on Enterprise Information Systems
270

How these elements are linked with the specific
information constitutes further work.
The capabilities to store information that
technologies such as RFID have, has not been
considered in the present work. Considering the
possibility of distributed information across different
Information systems – or storing devices such as the
RFID tag– requires the definition of mechanisms to
maintain information consistency.
REFERENCES
Association of European Airlines (AEA) (2006) Consumer
report.
Bencina, R.; Kaltenbrunner, M.; Jorda, S. (2005),
Improved Topological Fiducial Tracking in the
reacTIVision System, Computer Vision and Pattern
Recognition, 2005 IEEE Computer Society
Conference on , vol.3, pp. 99-99, 20-26.
Bézivin, J., Gerbé, O. (2001), Towards a Precise
Definition of the OMG/MDA Framework. In:
Proceedings of ASE’01
Bornhövd, C., Lin, T., Haller, S., Schaper, J. (2004),
Integrating Automatic Data Acquisition with Business
Processes - Experiences with SAP’s Auto-ID
Infrastructure. In Proceedings of the 30st international
conference on very large data bases (VLDB), pages
1182–1188, Toronto, Canada.
Favre, J.M. (2004), Foundations of Model (driven)
(Reverse) Engineering: Models - Episode I: Stories of
the Fidus Papyrus and of the Solarus. In: post-
proceedings of Dagsthul Seminar on Model Driven
Reverse Engineering.
Fleisch, E. (2001). Bussiness Perspectives on Ubiquitous
Computing. M-Lab Working Paper No. 4. University
of St. Gallen, Switzerland, 2001.
Floerkemeier C., Lampe, M. (2005), RFID middleware
design – addressing application requirements and
RFID constraints. In Proceedings of SOC’2005, pages
219–224, Grenoble, France.
Grimm, R., (2002), System support for pervasive
applications, Ph.D. Thesis, University of Washington,
Department of Computer Science and Engineering.
Ishii, H., Ullmer, B. (1997), Tangible Bits: Towards
Seamless Interfaces between People, Bits and Atoms.
In: CHI ’97: Proc. of the SIGCHI conference on
Human factors in computing systems, ACM Press
234–241
Johanson, B., Fox, A., Winograd, T., (2002), The
interactive workspaces project: Experiences with
ubiquitous computing rooms, IEEE Pervasive
Computing 1(2) 71–78.
Kindberg, T. (2002), Implementing physical hyperlinks
using ubiquitous identifier resolution, in 'WWW '02:
Proceedings of the 11th international conference on
World Wide Web', ACM Press, New York, NY, USA,
pp. 191—199
Kindberg, T., Barton, J., Morgan, J., Becker, G., Caswell,
D., Debaty, P., Gopal, G., Frid, M., Krishnan, V.,
Morris, H., Schettino, J., Serra, B., Spasojevic, M.
(2000), People, Places, Things: Web Presence for the
Real World. Mob. Netw. Appl. 7(5) (2002) 365–376
Langheinrich, M., Coroama, V., Bohn, J., Rohs, M.
(2002), As we may live - Real world implications of
ubiquitous computing. Technical Report, Institute of
Information Systems, Swiss Federal Institute of
Technology, Zurich, Switzerland.
Ljungstrand, P., Redström, J., Holmquist, L.E. (2000),
WebStickers: Using Physical Tokens to Access,
Manage and Share Bookmarks to the Web. In: Proc. of
DARE 2000 on Designing augmented reality
environments, ACM Press 23–31
OATsystems (2006). OAT C4 Architecture.
Rekimoto, J., Nagao, K. (1995): The World through the
Computer: Computer Augmented Interaction with
Real World Environments. In: UIST ’95: Proc. of the
8th annual ACM symposium on User interface and
software technology, ACM Press 29–36
Roman, M., Hess, C., Campbell, R. (2002), Gaia: An OO
middleware infrastructure for ubiquitous computing
environments. In: ECOOP Workshop on Object-
Orientation and Operating Systems (ECOOP-
OOOSWS). Malaga, Spain.
Römer, K., Schoch, T., Mattern, F., Dübendorfer, T.
(2004): Smart Identification Frameworks for
Ubiquitous Computing Applications. Wireless
Networks 10(6) 689–700.
Sandner, U., Leimeister, J. M., Krcmar, H. (2005),
Business Potentials of Ubiquitous Computing. In:
Proceedings of the Falk Symposium. No. 146 Gut-
Liver Interactions: Basic and Clinical Concepts.
Innsbruck, Austria.
Strassner, M., Schoch, T. (2002), Today’s Impact of
Ubiquitous Computing on Business Processes. In:
Pervasice Computing. First Int. Conf. Pervasive
Computing 2002, Zurich, Switzerland.
Sun Microsystems (2006). Java System RFID Software
3.0 Developer Guide. www.sun.com.
Want, R., Fishkin, K. P., Gujar, A., Harrison, B.L. (1999),
Bridging Physical and Virtual Worlds with Electronic
Tags. In: CHI ’99: Proc. of the SIGCHI conference on
Human Factors in Computing Systems, Pittsburgh,
PA, USA 370–377
PHYSICAL-VIRTUAL CONNECTION IN UBIQUITOUS BUSINESS PROCESSES
271
