
SEAMLESS COMMUNICATION AND ACCESS TO
INFORMATION FOR MOBILE USERS IN A WIRELESS
ENVIRONMENT
Golha Sharifi, Julita Vassileva and Ralph Deters
University of Saskatchewan, Computer Science Department,
57 Campus Drive, Saskatoon, Saskatchewan S7N 5A9, Canada
Keywords: Mobile Devices, Agents
Abstract: Providing mobile workers with mobile devices such as a Compaq iPaq with a CDPD card can support them
in retrieving information from centralized information systems. More specifically, mobile devices can
enable mobile users to make notifications for schedule changes and add new data into the information
system. In addition these devices can facilitate group communication anytime and anywhere. This paper
presents different ways of providing non-critical information in a timely fashion for nomadic users of
mobile devices using a wireless network. A distributed application prototype to support nomadic users is
proposed, and a simulated environment is used to evaluate the prototype. Since solutions for seamless
access are highly domain specific, the study involves homecare workers at Saskatoon District Health
(SDH). By keeping track of the users’ current context (time, location etc.) and a user task model, it is
possible to predict the information needs of mobile users and to provide context dependent adaptation of
both the content and the functionality. Moreover, to avoid interrupts in the user’s interaction with the main
information sources, methods for mobile transactions management using agent-based smart proxies that
buffer, delay or pre-fetch information/data are introduced.
1 INTRODUCTION
The development of wireless technology and the
commercial success of small screen appliances,
especially cellular phones and Personal Digital
Assistants (PDAs) have advanced the development
of mobile and ubiquitous computing (Weiser, 1991).
Mobile and ubiquitous computing allows nomadic
users to remain “connected” without depending on a
wired infrastructure.
Nomadic workers who use mobile and small
screen devices often need access to existing
information services to enable them to browse
multimedia information anytime and anywhere with
ease. Nomadic workers in specific domains who
might require these services include healthcare,
emergency services, sales, and education. However,
a major problem for the nomadic user using a thin
client is the varying quality of the connection.
Though connections remain fairly stable and good in
areas close to network stations, for instance, Cellular
Digital Packet Data (CDPD) towers, it is not
uncommon to have zones of low connectivity or
even no connection due to physical structures, for
example, high concrete buildings blocking the
signals.
We have investigated different ways of enabling
seamless access of non-critical information for
nomadic users. In this paper we focus on the needs
of homecare workers of the Saskatoon District
Health (SDH). The rest of the paper is organized as
follows: in the next section the domain for this study
and the current problems faced by mobile users are
introduced; next, the general approach to solving
these problems is described, which is explained in
more detail in the third, fourth and fifth sections; the
sixth section outlines an evaluation procedure; a
comparison with other work is presented in the
seventh section; the final section concludes the
paper.
2 RESEARCH DOMAIN
The SDH was chosen as a result of an ongoing
collaboration between Sasktel, TR-Labs and the
University of Saskatchewan. Currently, the focus of
this research is on the use of resource rich devices,
122
Sharifi G., Vassileva J. and Deters R. (2004).
SEAMLESS COMMUNICATION AND ACCESS TO INFORMATION FOR MOBILE USERS IN A WIRELESS ENVIRONMENT.
In Proceedings of the Sixth International Conference on Enterprise Information Systems, pages 122-129
DOI: 10.5220/0002624901220129
Copyright
c
SciTePress

like the Compaq iPaq and the CDPD network to
support homecare workers in SDH.
Our research focuses on the problems of
nomadic homecare workers in SDH. In SDH each
patient has a team of homecare workers assigned to
him or her, which consists of nurses,
physiotherapists, home health aides, social workers,
and dieticians responsible for looking after the
patient. Each team meets on a periodic basis to
discuss and coordinate necessary treatment for an
individual patient. Tasks and duties are divided
among the homecare workers based on skills and
available time slots. The relation between patients
and homecare workers can be described as M:N.
Though each of the homecare team members
has different tasks and responsibilities, they all have
one task in common: treatment of a patient.
Homecare workers visit their patients in their homes.
The offices of the homecare workers are usually
scattered throughout different buildings and
maintain separate scheduling and information
systems. To date there has been no centralized
information system for their use, which limits their
ability to share and exchange information regarding
schedules and patients’ medical records.
Homecare workers provide health care services
in different district areas in SDH. The wireless
network’s bandwidth they use is low (< 1 megabits
per second (Mbps)) and varies significantly from
one area to another. Currently, Saskatoon mobile
homecare workers do not have access to patients’
information outside the office, i.e. there is no
available remote access to data files, such as health
records and daily schedules.
A preliminary study was conducted on the
usability of the electronic health records system for
homecare at the SDH (Pinelle and Gutwin, 2001).
The study describes the way that groups of
homecare workers care for a patient and identifies
the existing problems. Results from this study
suggest that there are several obstacles for
communication between the members of a group,
which have led to difficulties in making changes in
the treatment of patients, coordination among
homecare workers, and the scheduling of patient
visits. These difficulties are also observed in
accessing information while the groups of homecare
workers are mobile. In order to address these
problems two approaches are proposed: increasing
awareness and supporting communication.
Following the recommendations given (Pinelle
and Gutwin, 2001), we would like to create a system
that supports the access to information and the
communication between homecare workers. Because
of data-security and safety reasons, we decided not
to focus on core health care data but on ways to
improve the availability of non-critical information,
such as scheduling information and personal patient
data, e.g., address and phone number. Access to the
patient medical record data requires, according to
the general regulation, permission from the patients,
which is hard to obtain.
In SDH, homecare workers work in a variety of
contexts, such as in the office, on the road, and at the
patient’s home. When an office scheduler or a
homecare worker makes a schedule, she must have
knowledge of the other team members’ schedules in
order to avoid conflicts in visiting the same patient.
However, since there is no access to a centralized
scheduling system, it is difficult to coordinate
schedule changes and take into account new data
regarding the patient. For instance, if a homecare
worker visits a patient and notices that the patient’s
condition has worsened, ideally, s/he would
immediately enter this information into the patient’s
record so that the other team members of the group
can access the information and perhaps revise their
schedules. However, this is not possible due to
absence of centralized data storage. We classify the
problems encountered by the homecare workers in
two categories. The first category has to do with lack
of efficient communication between homecare
workers, and the second is related to the inefficient
system of accessing and updating information.
Providing homecare personnel with mobile
devices e.g. iPaq and access to the wireless network
based on CDPD will allow them to retrieve
information, receive and send notification of
schedule changes, update the data/information
system and communicate with other workers.
Mobile devices come in varieties of types and
capabilities. For instance, small screen computing
devices differ in their features and abilities
compared to desktop computers. Their most notable
limitations are their smaller screen size, less
powerful processors, less main memory and limited
bandwidth because of the wireless network. To
ensure scalability, performance, and speed, it is
necessary to develop tools and techniques to
compensate for these limitations.
In this paper we introduce tools and techniques
that enable content and presentation adaptation to
improve the access of workers to information/data.
In particular, we have introduced the use of proxies
that create the illusion of a seamless connection.
Moreover, the adaptation is based on user, task, and
context models. Further, to ensure that the users
have the illusion of seamless access, intelligent
agent-based (Jennings et al., 1998) proxies are used,
which can delay write operations, pre-fetch data and
cache data, as well as use the task, context, and user
models to decide when and how to cache, pre-fetch
or delay.
SEAMLESS COMMUNICATION AND ACCESS TO INFORMATION FOR MOBILE USERS IN A WIRELESS
ENVIRONMENT
123

3 GENERAL APPROACH
In order to address these problems, we propose
combining techniques from agent technologies,
distributed database transaction management, and
user and task modeling. One of the goals is to ensure
seamless access to the information despite the
frequent interruptions in the connection caused by
the mobility of the homecare workers and the
unequal coverage of the area. The interface has to
be designed for small wireless devices allowing
homecare workers to conveniently perform typical
operations, including the following:
- Retrieving information from the system
(downloading files)
- Entering new data into the health records
(uploading/updating files)
- Accessing the schedule (reading schedules
and making appointments)
- Communicating with other members of the
home care division (sending/receiving messages)
It has been noted (Vassileva, 1996) that
healthcare and homecare workers have typical tasks,
which have standard information needs, e.g., the task
of visiting a patient requires information regarding
the patient’s address. Therefore, it is possible to (1)
predict what kind of information will be needed by
the homecare worker using her schedule and (2) pre-
fetch and/or adapt information appropriate for the
task and (3) present it according to the user’s
preferences and the limitations of the device on
which the information is going to be viewed. More
specifically, the techniques proposed to achieve the
goals stated in the previous section are listed below:
The use of agents: we use agents to give the
users the impression of seamless connection. Agents
hide the changes in the network bandwidth from the
user by providing the needed information for the
users before their information needs arise by the
means of task, user, and context modeling and
adaptation techniques.
The identification of read/write operations:
To ensure data consistency, we identified two
different kinds of read and write operations in the
SDH domain. The first kind is reading or writing to
data types needing a lock which prevents users from
accessing and/or modifying the data simultaneously
(e.g. a schedule); the second kind is information that
will not be updated simultaneously and therefore
does not require a lock (e.g. a patient’s record).
Providing only necessary functionalities:
When the context (time, location) and the current
task of the user is known, the interface can provide
only the functionalities needed by the user to
perform the task in the specific context. In this way,
the interface can be adapted to the constraint of the
small device.
4 USER AND TASK MODELING
The combination of techniques described in the
previous section is integrated in an application
architecture called “Mobi-Timar” (Farsi for “mobile
caregiver”), which has an interface for homecare
workers, an agent middleware and a server side. The
following assumptions are made to help us
undertake the design:
- There is a centralized schedule for all
homecare workers.
- The mobile devices are resource-rich, e.g.,
have at least 64 megabytes (MB) RAM, a wireless
connection with a bandwidth of at least 19.2 kilobits
per second (kbps), and the ability to run third party
applications.
- Patient and schedule-related data is stored in a
centralized repository.
- The wireless network coverage in the area has
varying but known bandwidth and latency.
The next sections describe the main components
of the Mobi-Timar architecture.
4.1 User Model
In the SDH, the homecare workers can be classified
based on their profession as nurses, physiotherapists,
social workers, home aide workers and dieticians.
Therefore, the user models are based on the
stereotype approach, as there are stereotypes
corresponding to the professions of the homecare
workers. There is a general stereotype for “homecare
workers” which has subclass stereotypes
corresponding to the professions. The stereotype
user model is retrieved and initialized when the user
logs in for the first time (she has to enter her
profession). The stereotype user model does not
change over time i.e., it is a long-term model, since
the profession of a homecare worker remains the
same. The individual user models are instances of
the stereotype user classes containing specific
individual preferences that may change over time,
for example, “personal info”, “Chief” or “expert” in
Figure 2.
Figure 1 shows an example of the stereotype
hierarchy. There are two different relations in this
hierarchy. One relation is the inheritance between a
subclass stereotype and the general stereotype, e.g.,
all nurses are homecare workers (see Figure 1). The
other relationship that is shown in the stereotype
hierarchy is the relation between a type of profession
referred to as “user class” and its task hierarchies,
e.g. the user class “Nurse” has a nurse task
hierarchy.
ICEIS 2004 - SOFTWARE AGENTS AND INTERNET COMPUTING
124
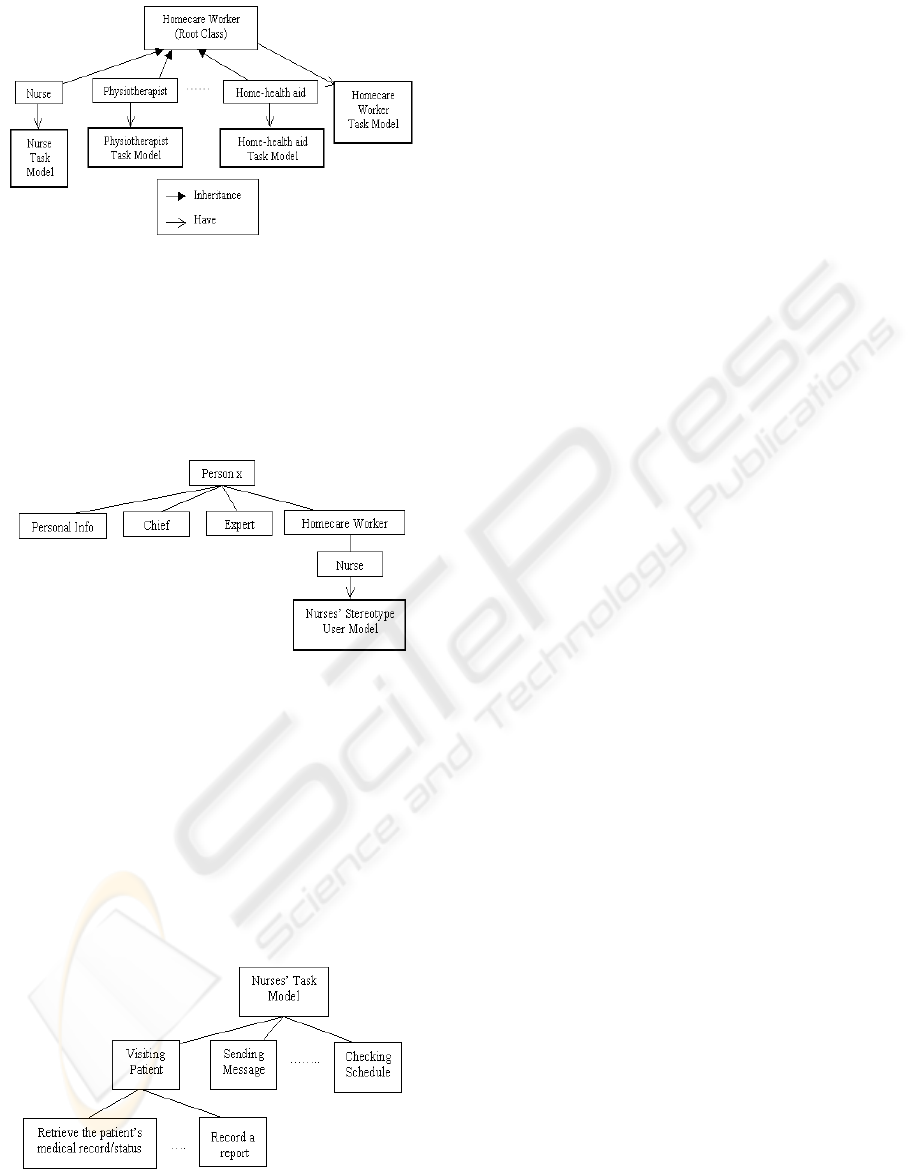
Figure 1: A Stereotype Hierarchy
The individual user model extends the
stereotype of the particular user class with the
personal information, preferences, rank and the
experience of the user. Figure 2 shows an example
of an individual user model and illustrates the
relationship between this model and the stereotype
user model.
Figure 2: An Example of Individual User Model
4.2 Task Model
In SDH each class of users has to perform
standardized tasks. Each task in this domain needs
specific types of information to be successfully
performed, and the information needs of tasks
typically do not vary over time. The task hierarchies
for each profession contain all the tasks that can be
performed by that class of users. Figure 3 shows the
task hierarchy for the user class “Nurse.”
Figure 3: The Task Hierarchy of Nurses Stereotype Class
A detailed view of one task from this task model
is shown in Figure 4. The task model is designed
hierarchically, and each task is decomposed to
subtasks (see Figures 3 and 4). Some of the subtasks
are restricted to certain user classes. For the task
“Visiting patient” in Figure 4, if the user is a nurse,
he needs to perform the following three tasks
sequentially:
- Retrieve the patient’s medical record
- Retrieve the patient’s personal information
- Record the report.
However, if the user is a home-health aide, she
will perform only the latter two subtasks. The reason
for having task hierarchies defined separately from
user task hierarchies is that there can be more than
one class of users performing this task. Depending
on the user class, different subtasks and different
information may be relevant. For example, when a
nurse and physiotherapist perform the same task, i.e.
retrieving a patient’s record, the information that is
provided to them is different. Again, depending on
the users’ profession, access rights to different
information are given in each task. For example, in
Figure 4, if the user is in the nurse class, he has the
right to access the patient’s medical record while
other classes of users (e.g. social aide workers) do
not have access to that information. The lower levels
of the task model contain the detailed
decompositions for each task and the information
needed to perform each subtask. The description of
each subtask includes information, such as the users’
class and context in which the task can be
performed.
As can be seen from Figure 4, each successive
level in the task model differentiates subtasks based
on either user type or context parameters. At the
second level in Figure 4, the task hierarchy is user
profession-specific because each task can be carried
out differently and can provide different information
based on the user’s class. In the second level task
decomposition takes place. At the third level in
Figure 4, the subtasks are organized based on
network bandwidth because different available
bandwidth allows the task to be carried out
differently. Depending on the current bandwidth
SEAMLESS COMMUNICATION AND ACCESS TO INFORMATION FOR MOBILE USERS IN A WIRELESS
ENVIRONMENT
125
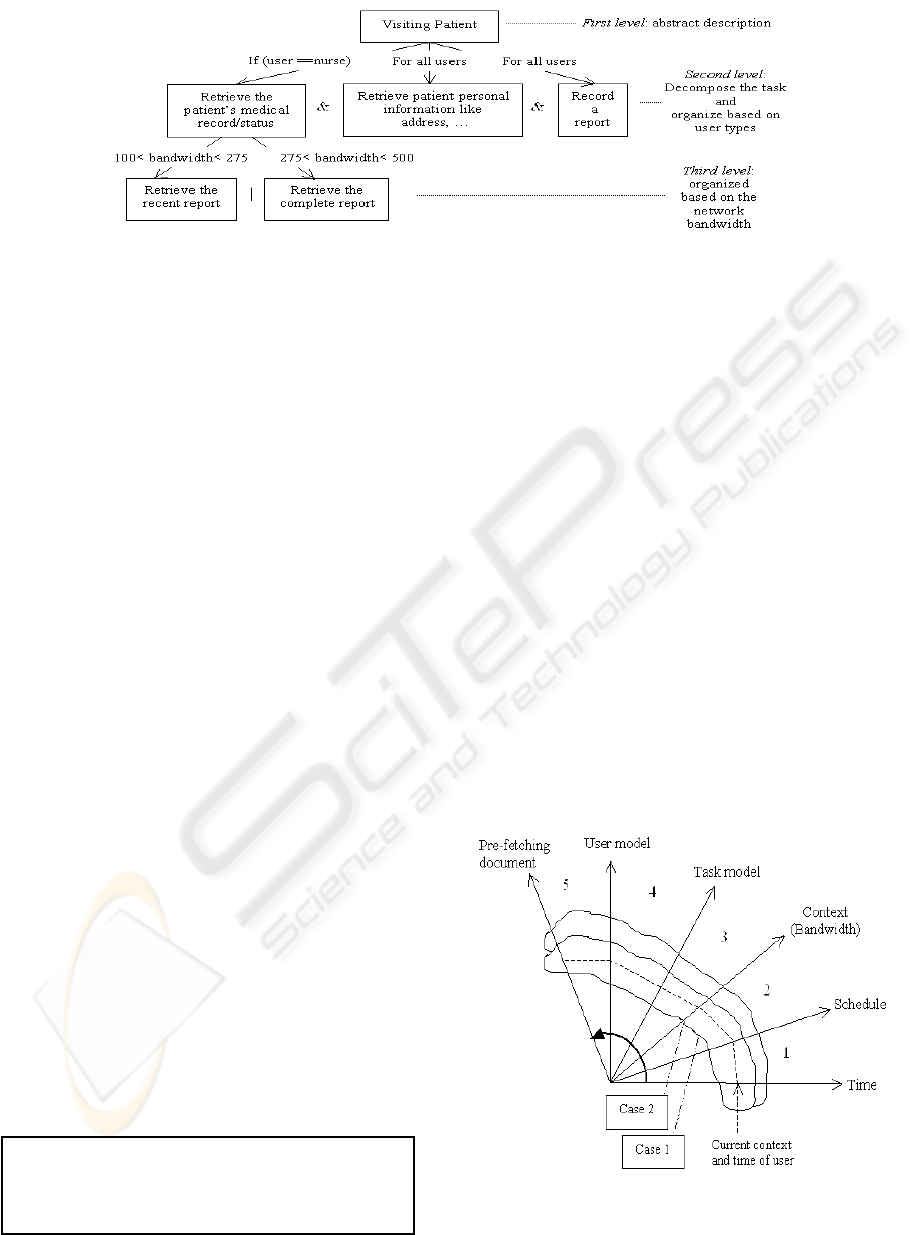
Figure 4: Task Hierarchy for Task “Visiting Patient”
availability, only one of the subtasks will be
performed. The changes of task structures and the
required information for tasks are regulated and can
be changed only by the system administrator.
4.3 Schedule
The schedule is used to predict the task that a user
will perform and the context (time, location), so the
needed information can be pre-fetched according to
the task model. Therefore, based on the schedule,
which gives the time and location in which a task
will be performed, the system uses the context
model to predict the network bandwidth at a specific
location.
4.4 Connectivity Model
The system’s connectivity model contains a map of
the network connectivity in the various known
locations shown as an interval of available
bandwidth for each location.
4.5 Library of Cases
Case-based reasoning (CBR) binds user model, task
model and connectivity model together. It is possible
to create a library of cases based on the task and the
type of location of homecare workers. Figure 5
shows the way a case is constructed. In Figure 5, the
User description represents the stereotype user
model, Task represents the task model and
Connection interval represents the connection
model. The cases are indexed by task-ID (t4 in
Figure 5) and
the bandwidth necessary to achieve
the task.
Figure 5: An Example of Case
The process of pre-fetching consists of
predicting network connectivity using the
connectivity model and the user's schedule (time,
location and task) and pre-fetching/hoarding the
needed information
using the user's task model.
Figure 6 shows this
process of pre-fetching
information. The current
location of the user and the
current time is used to find the next appointment
from the user's schedule (step 1). Knowing the
current location and the next location, the bandwidth
is retrieved from the connectivity model (step2).
When the task is known from the schedule, the
necessary information for the completion of the task
is retrieved from the task model (step 3). Having
knowledge of the bandwidth and the task, the user
model is checked for any specific preferences (step
4). These four steps represent the process of
retrieving an appropriate case from the case library.
The fifth step is to pre-fetch/hoard the necessary
information. In Mobi-Timar if a user performs
different tasks which are not included in her/his
schedule, the system will not guarantee the
availability of information in disconnected
condition.
Figure 6: The Process of Pre-Fetching Information
Case1:User description: nurse, physiotherapist
Task: (t4) retrieve the patient’s personal information
Connection interval: [100,375]
Result: load the address and the name of the patient
ICEIS 2004 - SOFTWARE AGENTS AND INTERNET COMPUTING
126
5 ADAPTATION
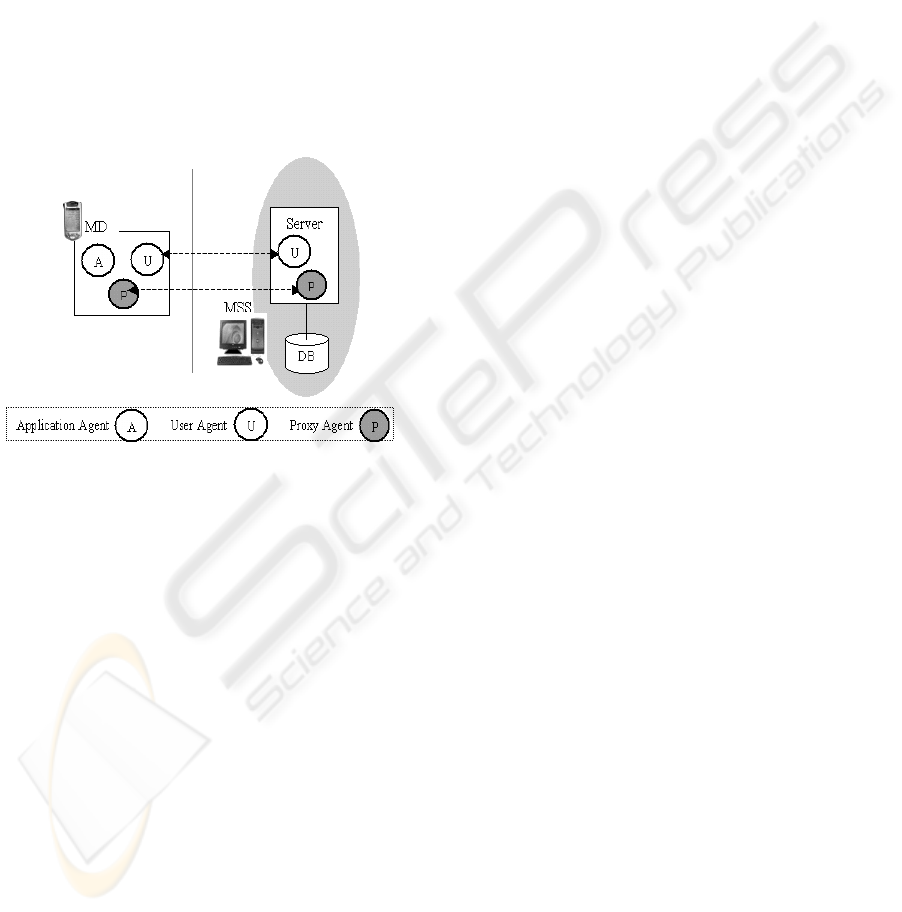
The proposed Mobi-Timar is based on client-server
architecture in which the agents are the middleware.
The client is a Mobile Device (MD) and the server
runs on a desktop computer. The server side contains
the adaptation mechanism, the library of cases, the
schedule, the user model, the task model, the context
model, the user agents and proxy agents. The server
side is encoded in Java and uses the JADE [4]
platform. A proxy agent and a user agent on the
server side represent each client. The client side
contains a proxy agent, user agent, an application
agent and an individual user model. The client side
is encoded in C#. The agents in C# and Java
communicate through ACL messages. Figure 7
illustrates the communication architecture.
Figure 7: The Mobi-Timar Architecture
5.1 The Use of Agents
To give the users the impression of a seamless
connection, agents are used. Agents hide changes in
the network bandwidth from the user by
automatically pre-fetching/hoarding the needed
information from/to the server ahead of time (as
shown in Figure 6).
5.2 The Identification of Read/Write
Operations
To ensure that the read and write operations are
transparent, we use two sets of agents (user agent
and proxy agent) and two copies of data, one on the
MD and the other on the server (data on the MD is a
copy of the data on server). The user agent on the
server side looks at any changes and updates on the
server side. In the case of disconnection the user
agent on the client and the server side will priorize
the queue of tasks and messages that are waiting to
be executed based on the user’s preferences from the
user model. The proxy agent of a client on the server
side plays the client role during disconnection mode,
while the proxy agent on the MD plays the server
role during disconnection mode. The proxy agent
receives the messages from server/client, waits for
the connection, and then forwards the messages to
the client/server. The user agent performs automatic
hoarding, and the proxy agent performs automatic
reintegration. The needed data for the user is cached
on the MD, and the primary copy of the data is
stored on the server. If the client side is disconnected
and the client is executing a write operation, the
client will continue with the task on MD. When the
client is finished with the task on MD, the agents
will wait for the connection and then execute the
task on the server side and let the user know the
result of the task. The status of the network
bandwidth is also available for the user, so the user
knows the accuracy of the data that she is using.
There are two different kinds of read and write
operations, one that needs a lock and one that does
not need a lock. When a user reads/writes to the
schedule or the agent is pre-fetching/updating the
schedule, the server side will lock the schedule to
avoid any inconsistencies, such as the loss of
information updates. If the client gets disconnected
while reading the schedule, the schedule lock will be
broken after a certain amount of time. If the client
stays connected or only has a brief disconnection,
the schedule stays locked until the client finishes the
transaction. For agents/clients that are writing to the
schedule, the schedule is locked and will not be
updated until the transaction is committed. In case of
an abort, the client on the MD will be notified.
Access to patient records does not require
locking since information cannot be deleted or
modified by homecare workers, who can only add
more data. But adding the new information to the
existing information cannot change the old content
due to SDH policy, which states that all transactions
related to homecare workers and patients should be
recorded and archived. This is illustrated in Figure 8.
After visiting a Patient at time t1, the Physiotherapist
adds information to the Patient’s record using her
mobile device in an area of poor connection. Some
time later at time t2 in an area of good connection, a
Nurse adds information to the Patient’s record. Her
transaction is committed on the server side fairly
quickly at time t3. Therefore, at a later time, t4,
when the Physiotherapist’s transaction is finally
committed on the server side, the additions to the
Patient’s record will be ordered based on the time
when each transaction was originally performed on
the client’s mobile device. For this reason the clocks
of all mobile devices are synchronized with server’s
clock.
SEAMLESS COMMUNICATION AND ACCESS TO INFORMATION FOR MOBILE USERS IN A WIRELESS
ENVIRONMENT
127

Transaction committed
on client side
(On MD)
Transaction committed
on server side
(On MSS)
Time
T1 t2 t3 t4
Nurse
Write to
Patient A
Write to
Patient A
Physio-
therapist
Write to
Patient A
Write to
Patient A
Figure 8: An Example for Second Type of Read/Write
5.3 Providing Only Necessary
Functionalities
The user agent can predict the next type of
information access to be performed by the homecare
worker using the task model (known from the user
class), the connection model, the schedule and a
library of cases. Based on the screen size limitation
of mobile devices, the user agent provides only the
suitable functionalities for the homecare worker’s
current access to information and not the full
functionality of Mobi-Timar since it knows which
operations are going to be performed. This allows a
consistent way to design the user interface around
specific user tasks.
6 EVALUATION
The evaluation of the Mobi-Timar architecture is
done using a simulation environment for the location
and available bandwidth. This simulation depicts a
virtual world that provides the location and the
network bandwidth. The movement of each user
with her MD is represented with a moving avatar in
the virtual world. Each user has a pre-assigned
schedule, which instructs her to move to certain
locations (visit patients) and perform certain tasks.
The user moves her avatar in the simulated location
and performs the tasks requiring access to the patient
data and schedule on her MD.
Figure 9 illustrates one of the network coverage
models for this simulation. Since it is important to
test the ability of Mobi-Timar to adapt quickly to
drastic changes in network coverage, different
models are considered, which allows for a more
realistic discontinuous pattern of coverage.
The simulation shows the movement of the user
through different network areas, which allows
testing the transparent read and write operations and
the availability of data access regardless of the
location and the network bandwidth. By testing
these two aspects, we will be able to evaluate the
functionality of Mobi-Timar.
Figure 9: Different Network Coverage in the Simulation
GUI
The evaluation of Mobi-Timar will be
conducted by running experiments involving a
centralized database containing information for four
patients. Two graduate students will take the roles of
a nurse and a physiotherapist. Each homecare
worker will perform either a full-day or a half-day
schedule, which includes all six types of operations:
downloading files, updating and uploading files,
sending messages, receiving messages, reading
schedules, making or changing appointments. All
these operations will be performed in two different
conditions: connected and disconnected mode. This
will allow us to evaluate the process of pre-fetching
information based on the available bandwidth,
accessing information during disconnection,
reintegrating information and maintaining the
consistency of data and user preferences on both
client and server side.
The evaluation procedure involves the
following two steps:
• Analyzing log data drawn from running the
Mobi-Timar in several different bandwidth
simulation models. The log file contains the
homecare workers and agents transactions
plus all the information transferred between
the clients’ devices and the server with time
stamp allowing the computation of the
speed of task execution.
• Using interviews to perform a usability
study based on the following criteria:
- Ease of use
- User satisfaction
- Interface design and the availability of
information and tasks
The evaluation process will enable us to
determine the number of failures and successful
read/write operations. It will also be possible to
deduce how well the system performs when the
design assumptions made earlier are valid. We will
also be able to ascertain how transparent the
read/write operations were by looking at the
consistency of data on both client and server side
and the numbers of failed and successful operations.
ICEIS 2004 - SOFTWARE AGENTS AND INTERNET COMPUTING
128

7 RELATED WORK
There is a great deal of research on adaptation of the
application and web infrastructure for mobile
devices. Most of this research, for example
CRUMPET (Poslad et al., 2001a; Poslad et al.,
2001b), MyCampus (Sadeh et al., 2002) and Hippie
(Oppermann et al., 1999; Specht and Oppermann,
1999), focuses on content adaptation, information
retrieval, interface adaptation and representation
adaptation. Furthermore, the focus of most of this
research is on adaptation based on the user type and
the level of experience of the user. In contrast,
Mobi-Timar adapts also based on context (e.g.
current time, user task, and connection availability).
Projects, such as Broad-Car (Console et al., 2002),
propose adaptation based on the context of the user
and use multimedia output, e.g. voice, video or text,
for presenting the data to the user. In these studies,
parameters used for adaptation are bandwidth, user
type, task, screen size, output channels of the device,
and the location. However, there are no write
transactions performed in any of these systems, and
synchronization and transaction management are not
needed. Unlike previous approaches, as in
CRUMPET, Hippie and MyCampus, our Mobi-
Timar addresses the problem of disconnection.
Agents are used to pre-fetch information relevant to
the user task and context. This research doesn’t
focus on just-in-time retrieval; instead, it aims to
support seamless access to information and
modification in a timely fashion.
8 CONCLUSIONS
In this paper we described Mobi-Timar, an
architecture for a mobile communication and
information system for homecare workers, which
uses a variety of techniques including user
modeling, task modeling, case-based adaptation,
multi-agent systems and mobile transaction
management.
The result of this research is an application and a
middleware for a mobile environment that can be
used in other domains with similar characteristics,
for example, supporting mobile technicians,
salespeople, real estate agents, etc. The application
ensures seamless access to data by using mobile
transaction management performed by the user agent
and the proxy agent. The user model, task model and
context model allow the agents to select and pre-
fetch relevant information needed for the user’s next
task and to create the illusion of seamless connection
for the users even when the bandwidth is low or the
user is disconnected.
ACKNOWLEDGEMENT
This research has been supported by TR-Labs.
REFERENCES
CDPD (Cellular Digital Packet Data),
http://www2.picante.com:81/~gtaylor/cdpd.html
Compaq iPaq,
http://athome.compaq.com/showroom/static/ipaq/hand
held_jumppage.asp
Console, L., Gioria, S., Lombardi, I., Surano, V., Torre, I.,
2002. Adaptation and Personalization on Board Cars:
A Framework and Its Application to Tourist Services.
In 2nd International Conference on Adaptive
Hypermedia and Adaptive Web Based Systems, AH
2002, 112-121.
JADE: http://sharon.cselt.it/projects/jade/
Jennings, N., Sycara, K. and Wooldridge, M., 1998. A
RoadMap of Agent Research and Development.
Journal on Autonomous Agents and Multi-Agent
Systems, 1, 275-306.
Oppermann, R., Specht, M., Jaceniak, I., 1999. Hippie: A
Nomadic Information System. Gellersen. W. (Ed.):
Proceedings of the First International Symposium
Handheld and Ubiquitous Computing (HUC'99),
Karlsruhe, September 27 - 29, 330 - 333.
Pinelle, D. and Gutwin, C., 2001. Collaboration
Requirements for Home Care. Research Report,
University of Saskatchewan,
http://hci.usask.ca/publications/index.xml
Poslad S., Laamanen H., Malaka R., Nick A., Buckle P.
and Zipf, A., 2001a. CRUMPET: Creation of User-
friendly Mobile Services Personalised for Tourism.
Proceedings of: 3G 2001 - Second International
Conference on 3G Mobile Communication
Technologies. London, UK, 26-29.
Poslad S., Charlton P. In Marik V., Stepankova O., 2001b.
Standardizing agent interoperability: the FIPA
approach. Proceedings of the Multi-Agent Systems &
Applications Conference, ACAI-01 (invited paper).
Sadeh, N., Chan, E., Shimazaki, Y., Van, 2002.
MyCampus: An Agent-Based Environment for Context-
Aware Mobile Services. In AAMAS02 Workshop on
Ubiquitous Agents on Embedded, Wearable, and
Mobile Devices, Bologna, Italy.
Specht, M., and Oppermann, R., 1999. User Modeling and
Adaptivity in Nomadic Information Systems.
Proceedings of the 7. GI-Workshop Adaptivität und
Benutzermodellierung in Interaktiven
Softwaresystemen (ABIS99), Universität Magdeburg,
September 27 - October 1, 325 -328.
Vassileva, J., 1996. A Task-Centered Approach for User
Modeling in a Hypermedia Office Documentation
System. User Modeling and User Adapted Interaction,
6, 2-3, 185-223.
Weiser, M., 1991. The computer for the twenty-first
century. Scientific American, September, 94-100.
SEAMLESS COMMUNICATION AND ACCESS TO INFORMATION FOR MOBILE USERS IN A WIRELESS
ENVIRONMENT
129
